A Residual Analysis-Based Improved Particle Filter in Mobile Localization for Wireless Sensor Networks
Abstract
:1. Introduction
- (1)
- The residual analysis is used several times to ensure the effectiveness of the localization results.
- (2)
- The beacon nodes work together so that the particle filter process is simplified and the negative effect of NLOS errors can be decreased. The computational complexity of the proposed method is lower than that of the PF algorithm.
- (3)
- The proposed algorithm doesn’t make any assumption on the distribution of the NLOS error.
2. Related Works
3. Problem Statement
3.1. Signal Model
3.2. A Brief Introduction to PF
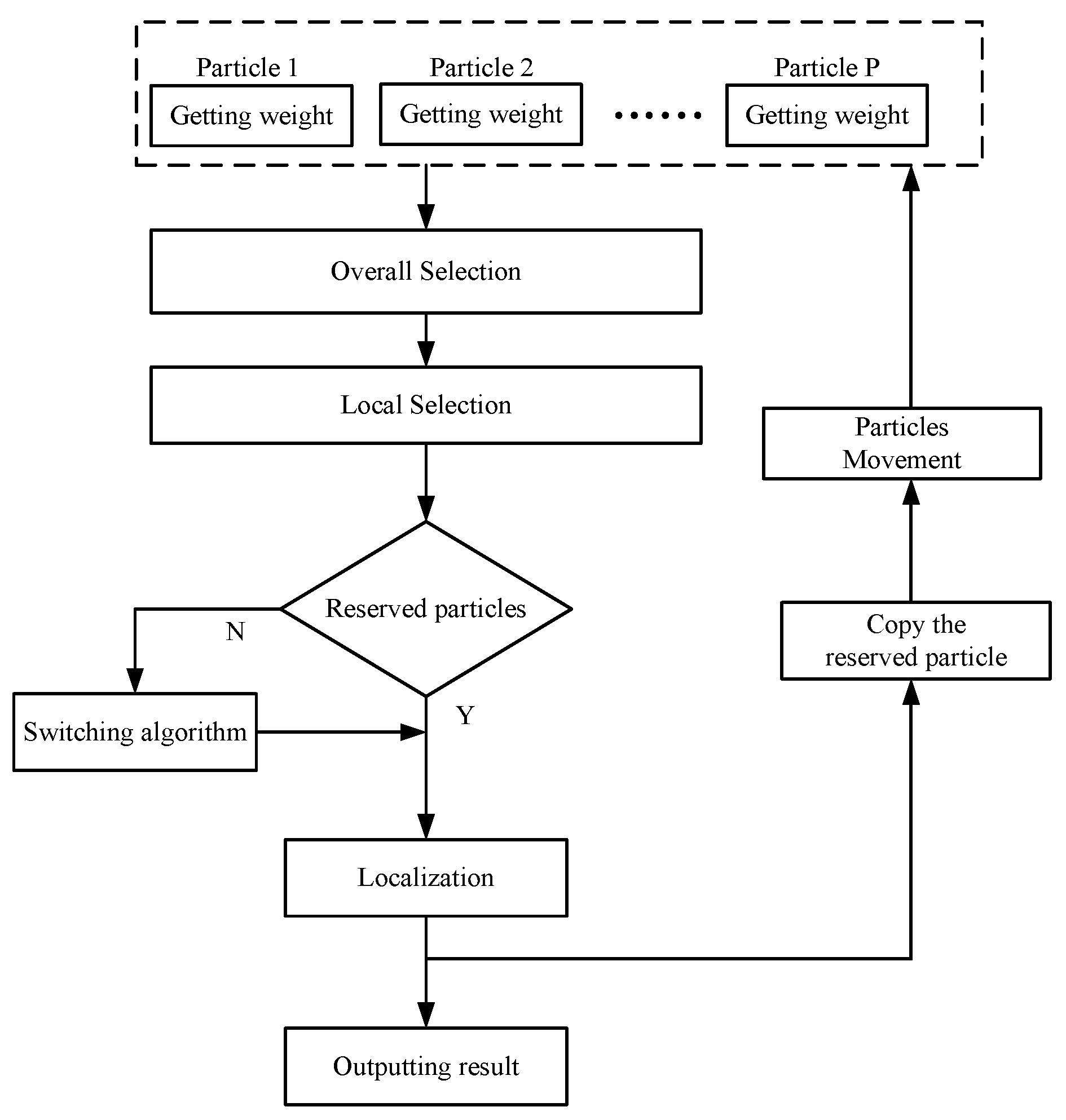
4. Proposed Method
4.1. General Concept
4.2. Weighting Particles
| Algorithm 1. Weighting particles. |
for j = 1:P for i = 1:N end for for j = 1:P end for end for |
4.3. Overall Selection
| Algorithm 2. Overall Selection. |
| for j = 1:P particle reserved; else particle discard; end for |
4.4. Local Selection
| Algorithm 3. Local Selection. |
| Input: Reserved particles from Selection I and their weight Output: Particles and their weight m = 0; for i = 1:N for j = 1:P m = m + 1; end for end for for j = 1:P n = 0; for i = 1:N n = n + 1; end for if (n>thr) particle reserved; else particle discard; end for |
4.5. Location Estimation
4.6. Particle Copy and Movement
| Algorithm 4. Particle copy. |
| for m = 1:P Generate rand number r; for j = 1:L copy particle j; break; end for end for |
5. Simulation and Experiment Results
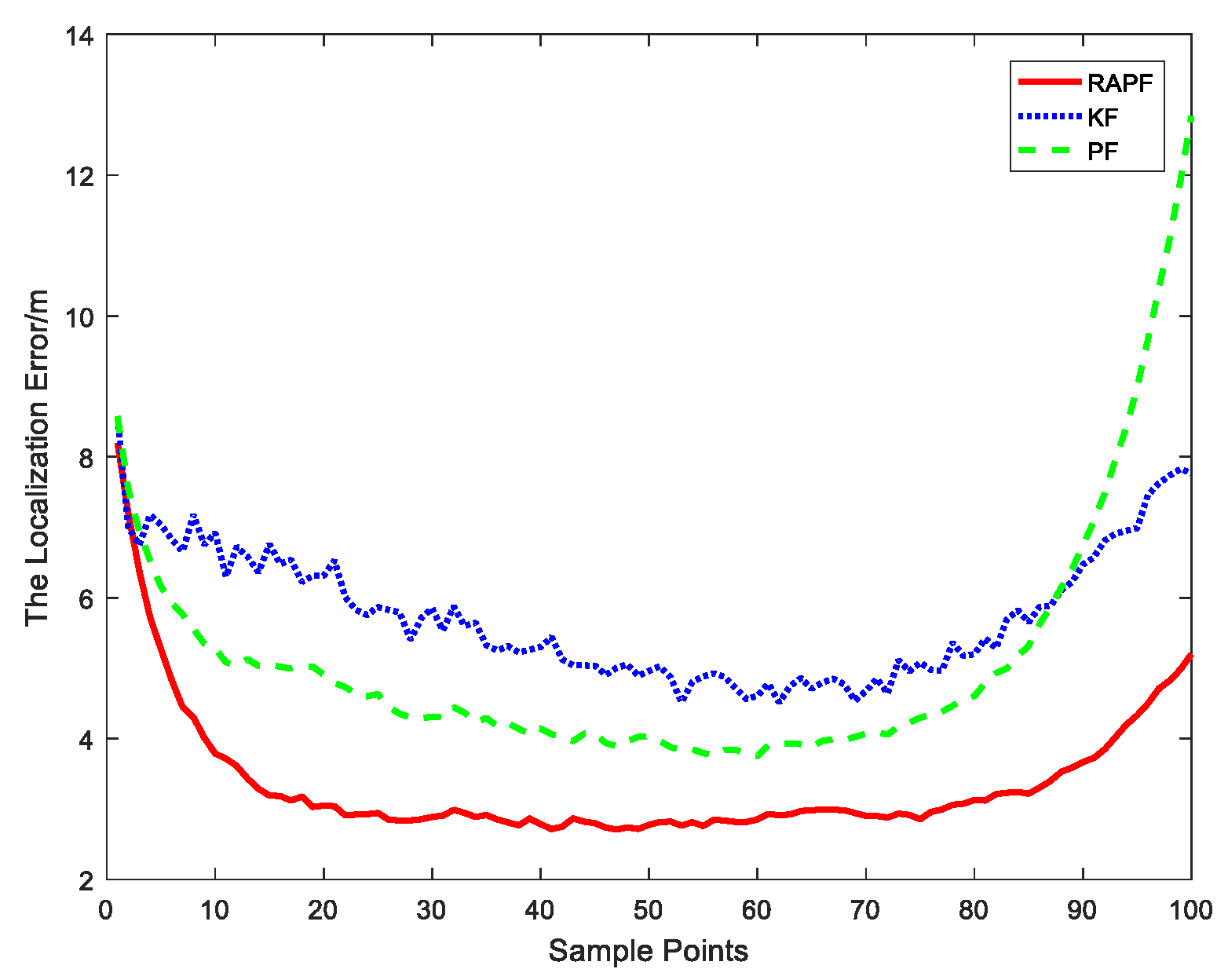
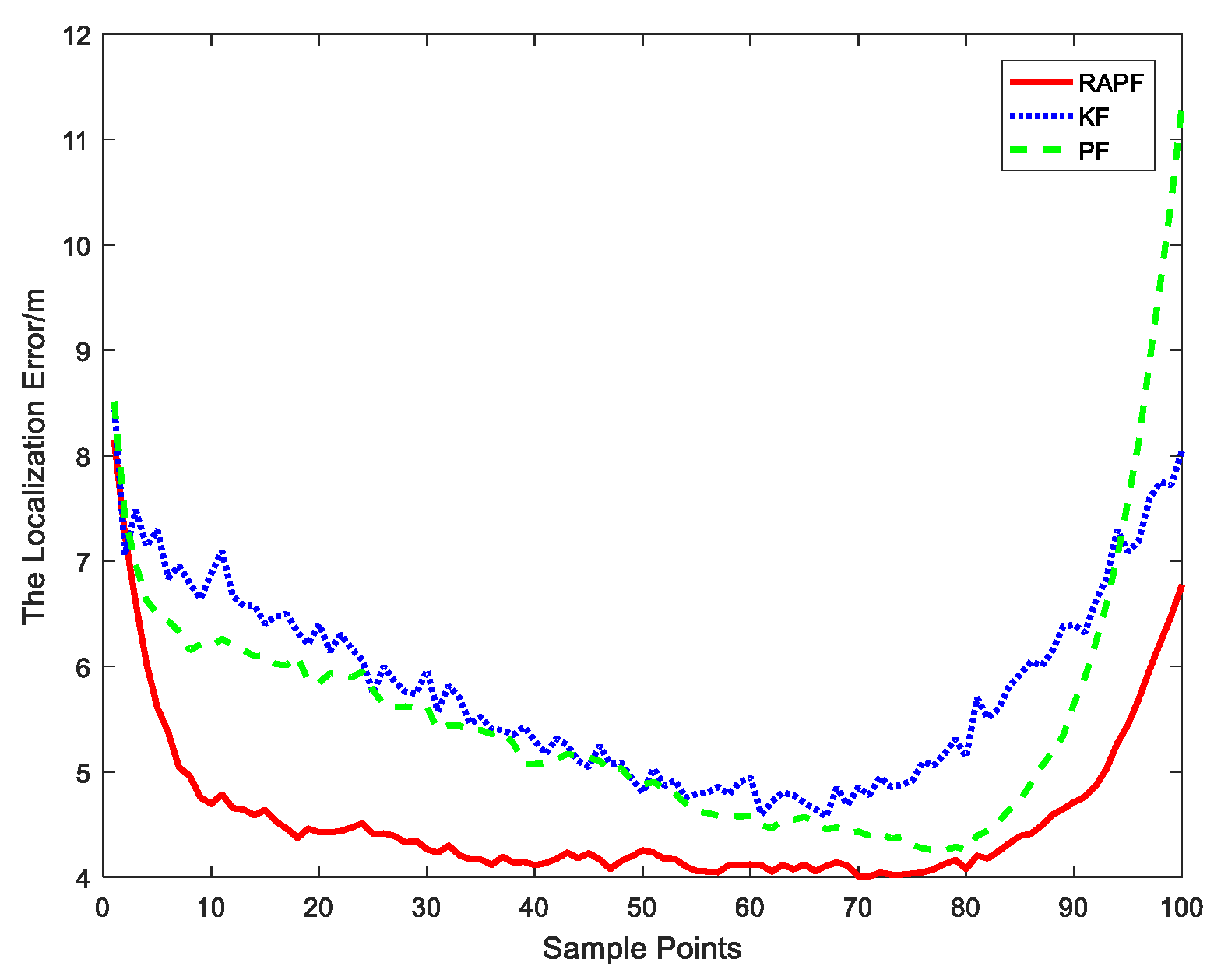
5.1. Simulation Results
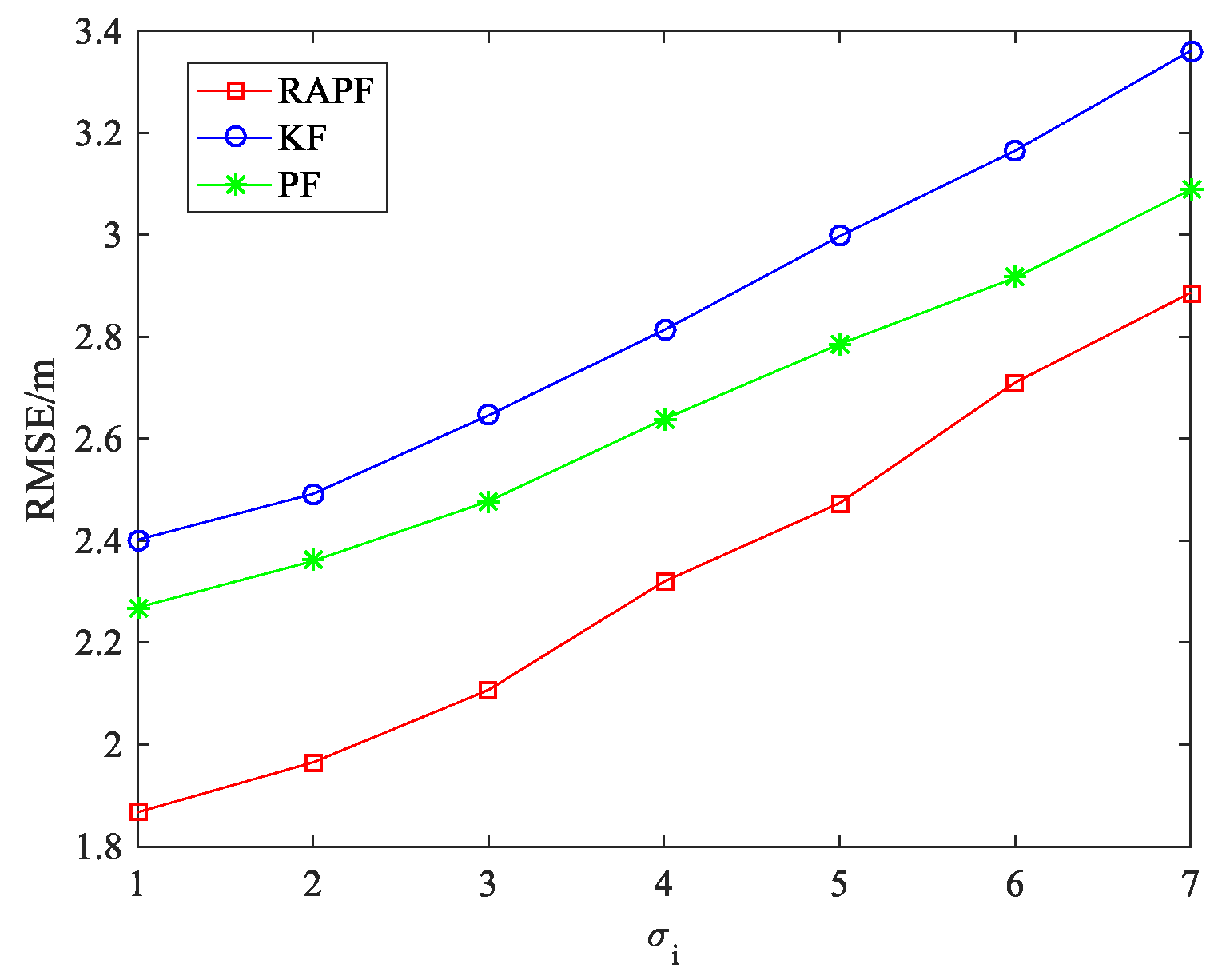
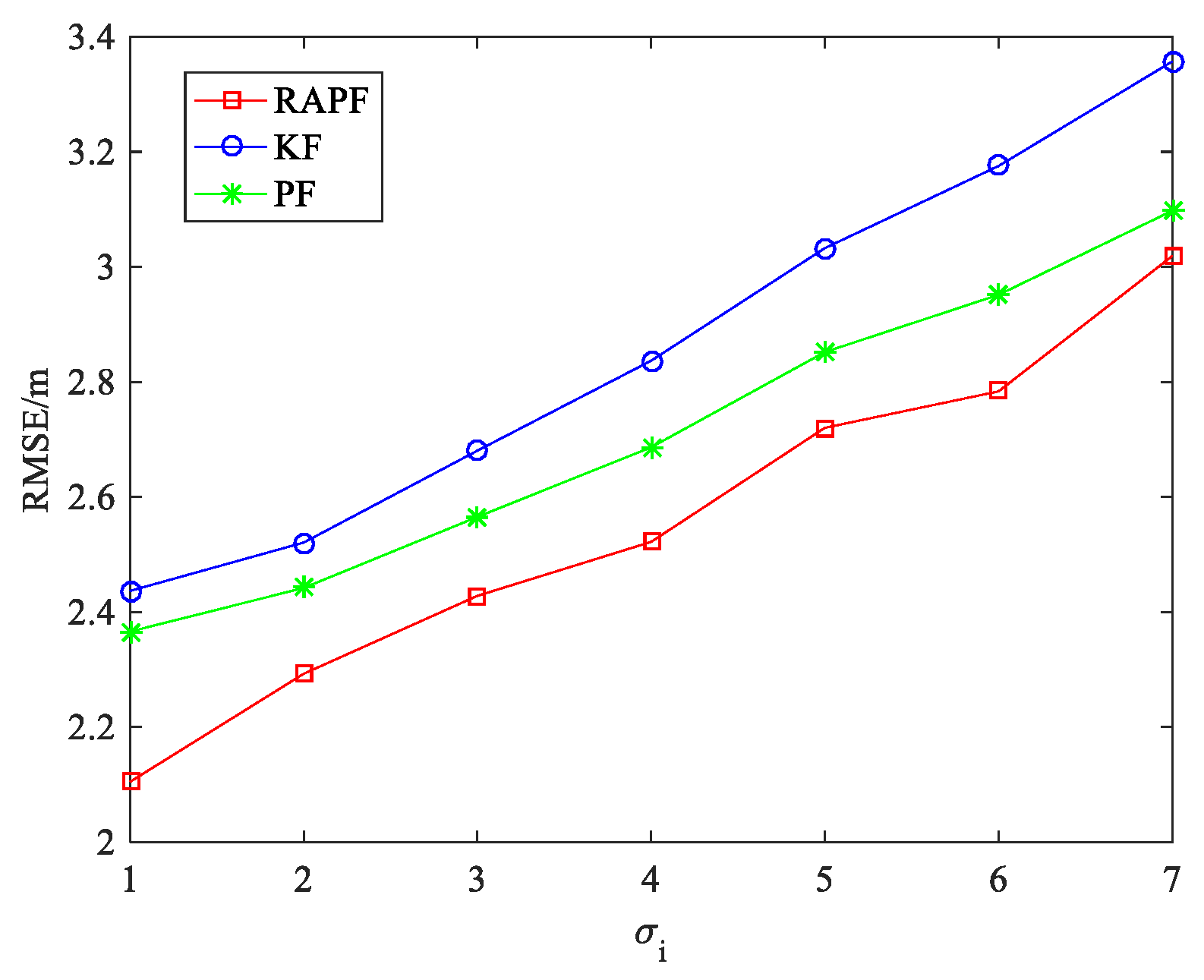
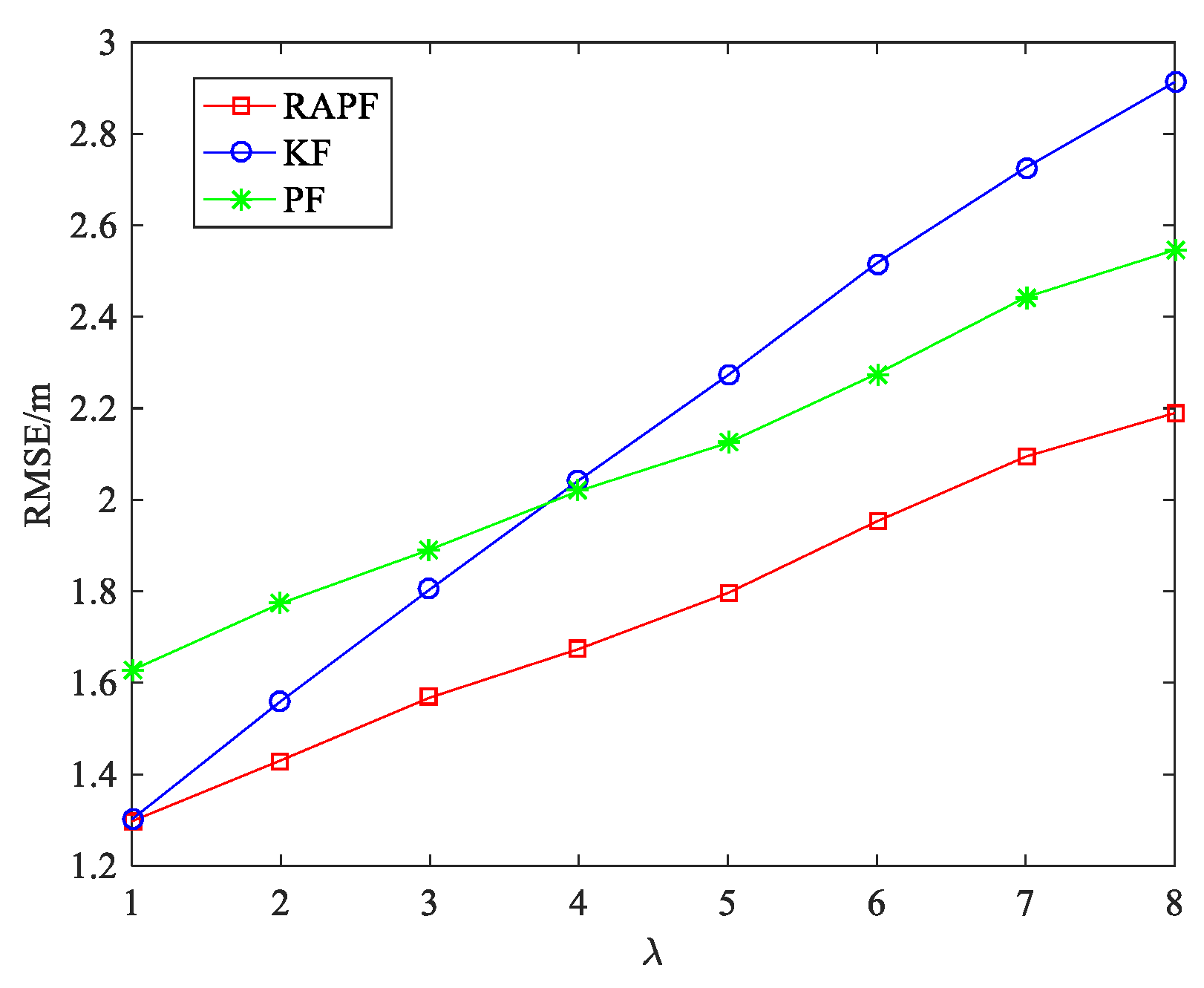
5.1.1. The NLOS Errors Obey a Gaussian Distribution
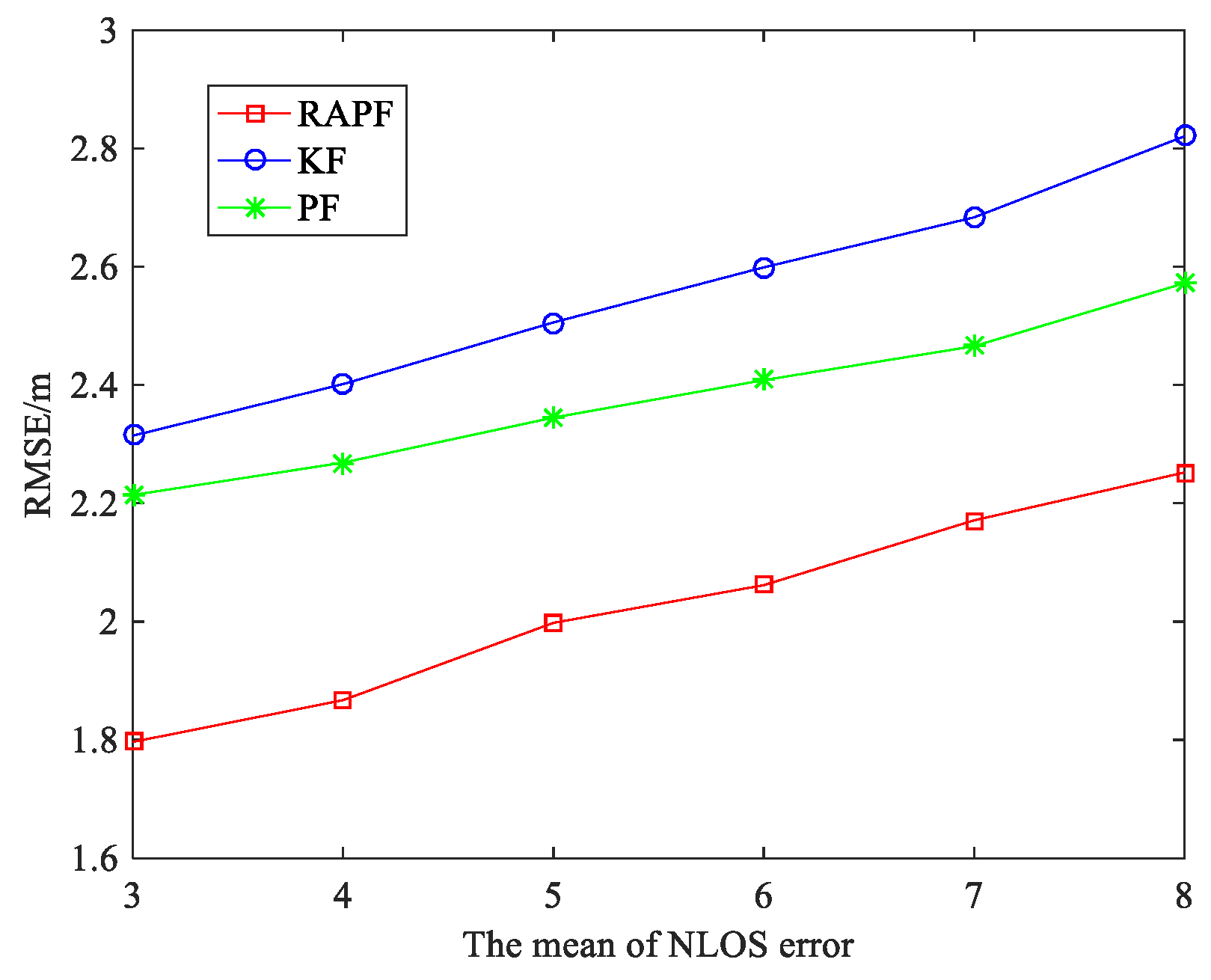
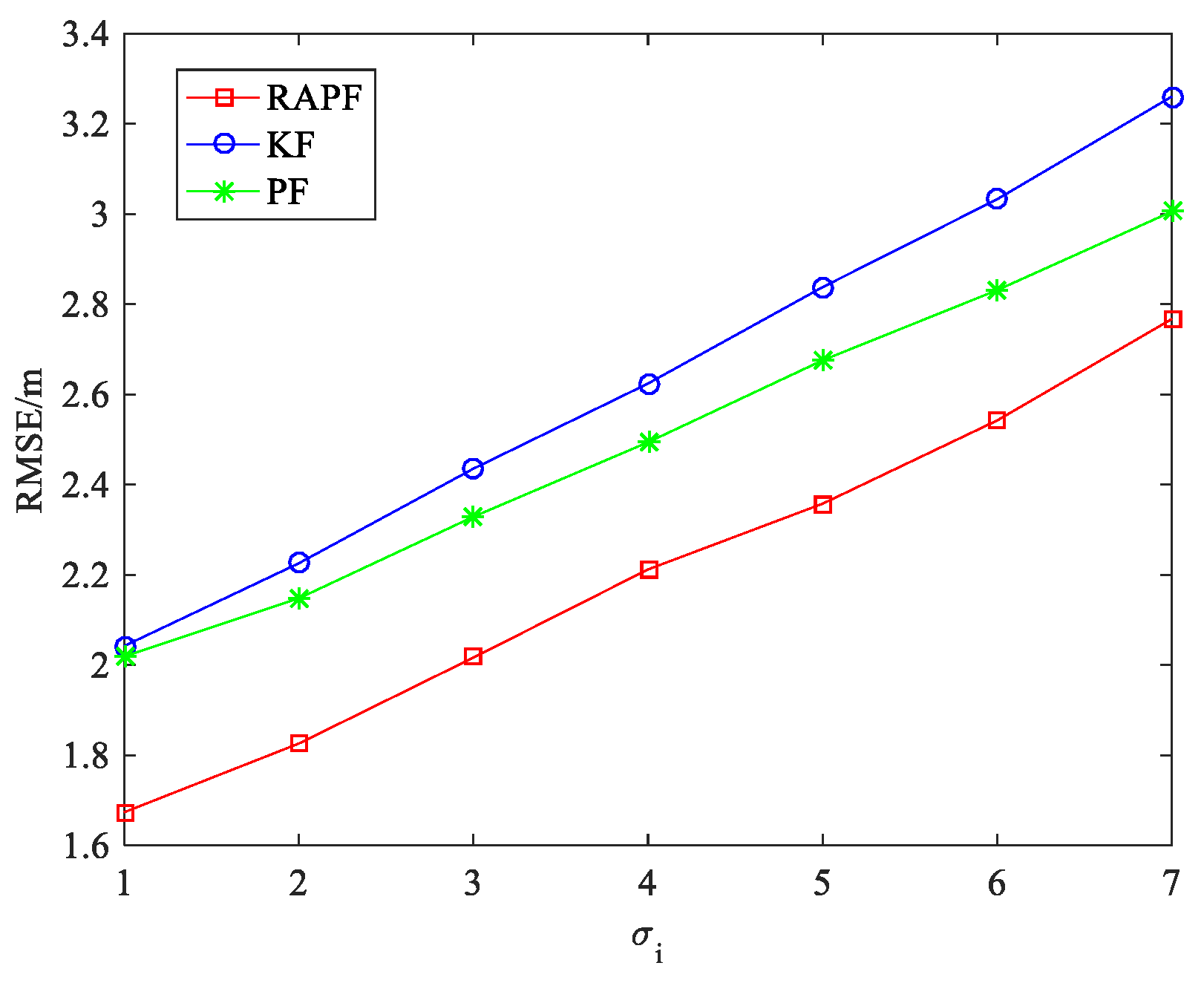
5.1.2. The NLOS Errors Obey a Uniform Distribution
5.1.3. The NLOS Errors Obey Exponential Distribution
5.1.4. Computational Complexity Analysis
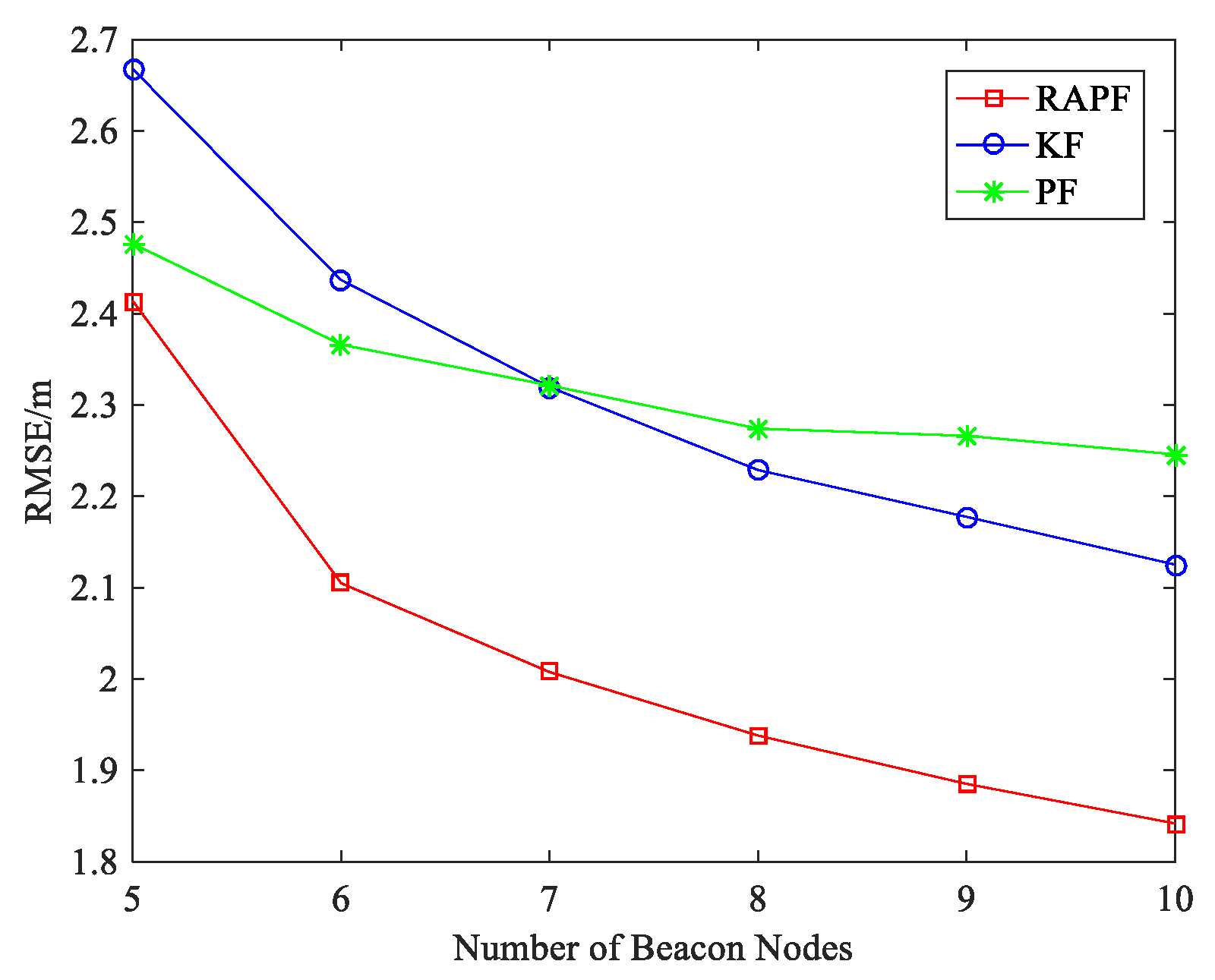
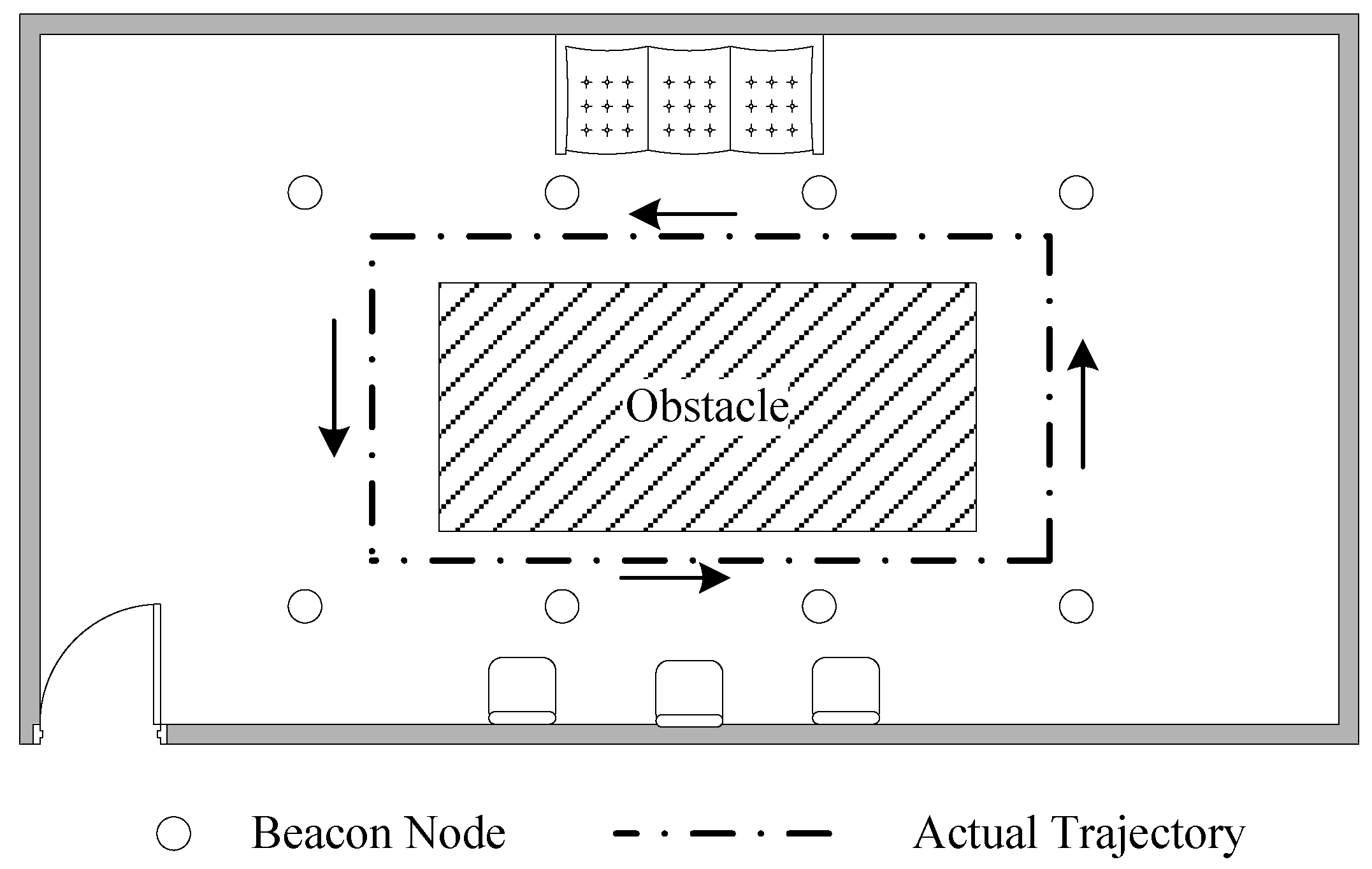
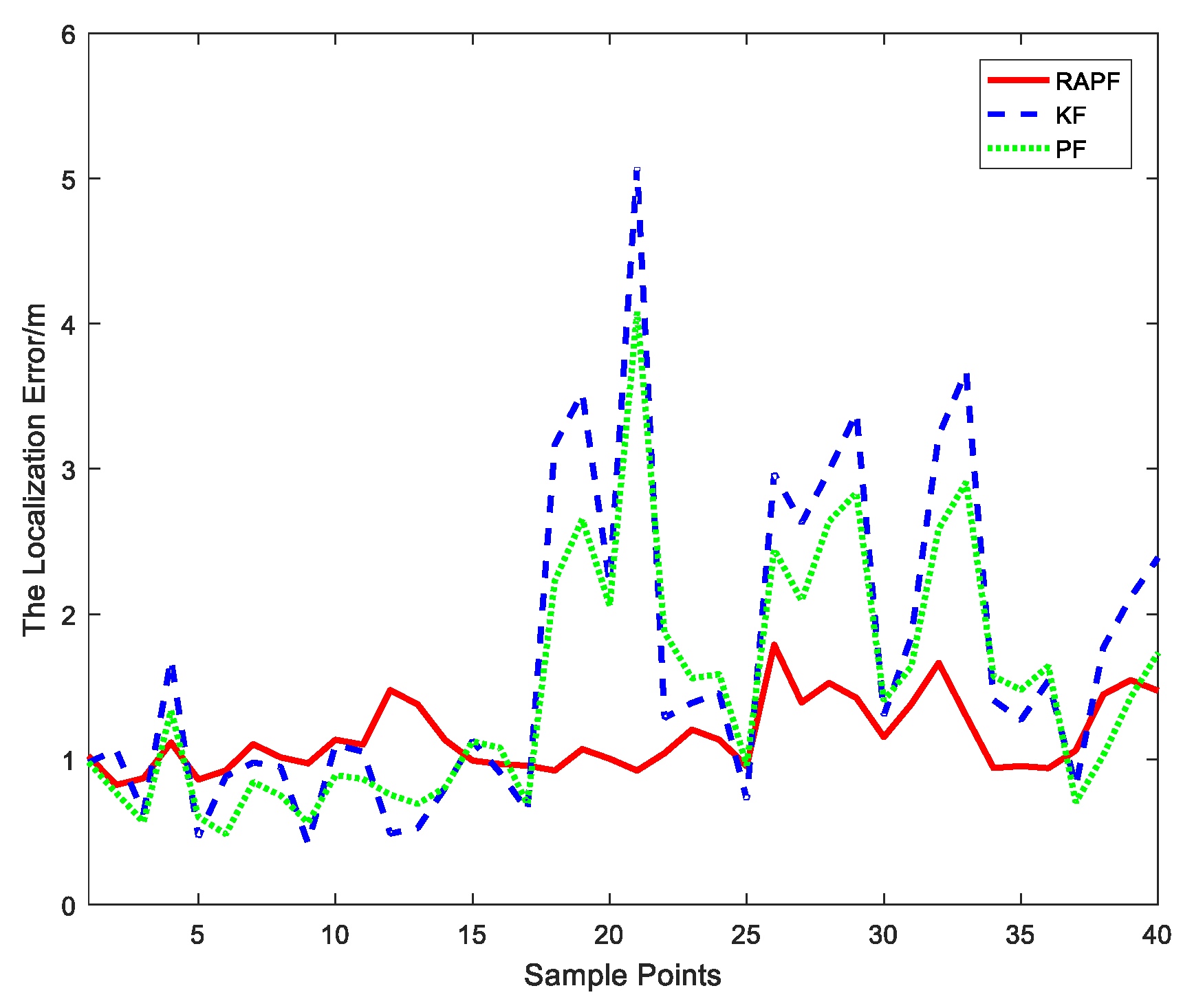
5.2. Experiment Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Buehrer, R.M.; Wymeersch, H.; Vaghefi, R.M. Collaborative Sensor Network Localization: Algorithms and Practical Issues. Proc. IEEE 2018, 106, 1089–1114. [Google Scholar] [CrossRef]
- Shi, X.F.; Chew, Y.H.; Yuen, C.; Yang, Z.Y. A novel mobile target localization algorithm via HMM-based channel sight condition identification. Peer-to-Peer Netw. Appl. 2017, 10, 808–822. [Google Scholar] [CrossRef]
- Zhang, L.; Huang, D.J.; Wang, X.H.; Schindelhauer, C.; Wang, Z. Acoustic NLOS Identification Using Acoustic Channel Characteristics for Smartphone Indoor Localization. Sensors 2017, 17, 727. [Google Scholar] [CrossRef] [PubMed]
- Yan, L.B.; Lu, Y.; Zhang, Y.R. An Improved NLOS Identification and Mitigation Approach for Target Tracking in Wireless Sensor Networks. IEEE Access 2017, 5, 2798–2807. [Google Scholar] [CrossRef]
- Ma, T.Y.; Wang, B.B.; Pei, S.Y.; Zhang, Y.L.; Zhang, S.; Yu, J.X. An Indoor Localization Method Based on AOA and PDOA Using Virtual Stations in Multipath and NLOS Environments for Passive UHF RFID. IEEE Access 2018, 6, 31772–31782. [Google Scholar] [CrossRef]
- Choi, J.S.; Lee, W.H.; Lee, J.H.; Kim, S.C. Deep Learning Based NLOS Identification with Commodity WLAN Devices. IEEE Trans. Veh. Technol. 2018, 67, 3295–3303. [Google Scholar] [CrossRef]
- Pak, J.M.; Ahn, C.K.; Shi, P.; Shmaliy, Y.S.; Lim, M.T. Distributed Hybrid Particle/FIR Filtering for Mitigating NLOS Effects in TOA-Based Localization Using Wireless Sensor Networks. IEEE Trans. Ind. Electron. 2017, 64, 5182–5191. [Google Scholar] [CrossRef]
- Gazzah, L.; Najjar, L.; Besbes, H. Hybrid RSS/AOA hypothesis test for NLOS/LOS base station discrimination and location error mitigation. Trans. Emerg. Telecommun. Technol. 2016, 27, 626–639. [Google Scholar] [CrossRef]
- Pandey, O.J.; Sharan, R.; Hegde, R.H. Localization in Wireless Sensor Networks Using Visible Light in Non-Line of Sight Conditions. Wirel. Pers. Commun. 2017, 97, 6519–6539. [Google Scholar] [CrossRef]
- Shi, X.F.; Mao, G.Q.; Yang, Z.Y.; Chen, J.M. MLE-based localization and performance analysis in probabilistic LOS/NLOS environment. Neurocomputing 2017, 270, 101–109. [Google Scholar] [CrossRef]
- Yang, X.F.; Zhao, F.; Chen, T.J. NLOS identification for UWB localization based on import vector machine. Int. J. Electron. Commun. 2018, 87, 128–133. [Google Scholar] [CrossRef]
- Momtaz, A.A.; Behnia, F.; Amiri, R.; Marvasti, F. NLOS Identification in Range-Based Source Localization: Statistical Approach. IEEE Sens. J. 2018, 18, 3745–3751. [Google Scholar] [CrossRef]
- Tomic, S.; Beko, M.; Dinis, R.; Bernardo, L. On Target Localization Using Combined RSS and AoA Measurements. Sensors 2018, 18, 1266. [Google Scholar] [CrossRef] [PubMed]
- Tomic, S.; Beko, M. A bisection-based approach for exact target localization in NLOS environments. Signal Process. 2018, 143, 328–335. [Google Scholar] [CrossRef]
- Abu-Shaban, Z.; Zhou, X.Y.; Abhayapala, T.D. A Novel TOA-Based Mobile Localization Technique under Mixed LOS/NLOS Conditions for Cellular Networks. IEEE Trans. Veh. Technol. 2016, 65, 8841–8853. [Google Scholar] [CrossRef]
- Ding, C.; Qi, H.D. Convex Euclidean distance embedding for collaborative position localization with NLOS mitigation. Comput. Optim. Appl. 2017, 66, 187–218. [Google Scholar] [CrossRef]
- Wang, J.; Zhang, L.M.; Gao, Q.H.; Pan, M.; Wang, H.Y. Device-Free Wireless Sensing in Complex Scenarios Using Spatial Structural Information. IEEE Trans. Wirel. Commun. 2018, 17, 2432–2442. [Google Scholar] [CrossRef]
- Yang, X.F. NLOS Mitigation for UWB Localization Based on Sparse Pseudo-Input Gaussian Process. IEEE Sens. J. 2018, 18, 4311–4316. [Google Scholar] [CrossRef]
- Vilà-Valls, J.; Closas, P. NLOS mitigation in indoor localization by marginalized Monte Carlo Gaussian smoothing. EURASIP J. Adv. Signal Process. 2017, 62, 1–11. [Google Scholar] [CrossRef]
- Wang, G.; So, A.M.; Li, Y.M. Robust Convex Approximation Methods for TDOA-Based Localization Under NLOS Conditions. IEEE Trans. Signal Process. 2016, 64, 3281–3296. [Google Scholar] [CrossRef]
- Park, C.H.; Chang, J.H. Robust time-of-arrival source localization employing error covariance of sample mean and sample median in line-of-sight/non-line-of-sight mixture environments. EURASIP J. Adv. Signal Process. 2016, 89, 1–11. [Google Scholar] [CrossRef]
- Li, W.L.; Jia, Y.M.; Du, J.P. TOA-based cooperative localization for mobile stations with NLOS mitigation. J. Frankl. Inst. 2016, 353, 1297–1312. [Google Scholar] [CrossRef]
- Gaber, A.; Omar, A. Utilization of Multiple-Antenna Multicarrier Systems and NLOS Mitigation for Accurate Wireless Indoor Positioning. IEEE Trans. Wirel. Commun. 2016, 15, 6570–6587. [Google Scholar] [CrossRef]
- Biswas, P. Semidefinite Programming for Ad Hoc Wireless Sensor Network Localization. In Proceedings of the 3rd International Symposium on Information Processing in Sensor Networks, Berkeley, CA, USA, 26–27 April 2004; pp. 46–54. [Google Scholar]
- He, S.; Hu, T.; Chan, S.-H.G. Contour-based Trilateration for Indoor Fingerprinting Localization. In Proceedings of the 13th ACM Conference on Embedded Networked Sensor Systems, Seoul, Korea, 1–4 November 2015; pp. 225–238. [Google Scholar]
- Tomic, S.; Beko, M.; Dinis, R.; Tuba, M.; Bacanin, N. RSS-AoA-Based Target. Localization and Tracking in Wireless Sensor Networks, 1st ed.; River Publishers: Alsbjerg, Denmark, 2017; pp. 113–155. [Google Scholar]
- Tomic, S.; Beko, M.; Dinis, R.; Tuba, M.; Bacanin, N. Bayesian methodology for target tracking using combined RSS and AoA measurements. Phys. Commun. 2017, 25, 158–166. [Google Scholar] [CrossRef] [Green Version]
- Vicente, D.; Tomic, S.; Beko, M.; Dinis, R.; Tuba, M.; Bacanin, N. Kalman Filter for Target Tracking Using Coupled RSS and AoA Measurements. In Proceedings of the International Wireless Communications and Mobile Computing Conference (IWCMC), Valencia, Spain, 26–30 June 2017; pp. 2004–2008. [Google Scholar]
- Wang, W.; Wang, G.; Zhang, J.; Li, Y.M. Robust Weighted Least Squares Method for TOA-Based Localization under Mixed LOS/NLOS Conditions. IEEE Commun. Lett. 2017, 21, 2226–2229. [Google Scholar] [CrossRef]
- Wang, W.; Wang, G.; Zhang, F.; Li, Y.M. Second-Order Cone Relaxation for TDOA-Based Localization under Mixed LOS/NLOS Conditions. IEEE Signal. Process. Lett. 2016, 23, 1872–1876. [Google Scholar] [CrossRef]
- Arulampalam, M.S.; Maskell, S.; Gordon, N.; Clapp, T. A Tutorial on Particle Filters for Online Nonlinear/Non-Gaussian Bayesian Tracking. IEEE Trans. Signal Process. 2002, 50, 174–188. [Google Scholar] [CrossRef]












| Notation | Explanation | Notation | Explanation |
|---|---|---|---|
| the number of beacon nodes | the coordinates of beacon nodes | ||
| the position of unknown node | the measurement error | ||
| the measured distance measurement of the beacon node at time k | the true distance between the beacon node and the unknown node at time k | ||
| the NLOS error | the deviation of measurement error | ||
| the number of particles | the coordinate of particles at time k | ||
| the true distance between the beacon node and the particle at time k | the weight of particle to beacon node at time k | ||
| the residual of the particle to the beacon node at time k | the sum of the residuals particle to all the beacon node at time k | ||
| the number of the reserved particles after the first selection | the number of the reserved particles after the second selection | ||
| the estimated NOLS error probability | the number of the reserved particles after two-time selection | ||
| the weight of particle to beacon node at time k after normalization | beacon node at time k | ||
| the deviation of particle movement |
| Parameters | Symbol | Default Values |
|---|---|---|
| The number of beacon nodes | 6 | |
| The probability of LOS propagation | 0.6 | |
| The standard deviation of measurement noise | 1 | |
| The NLOS error | ||
| The standard deviation of particle movement | 3 | |
| The number of sample points | 100 | |
| The number of Monte Carlo runs | 1000 |
| Parameters | Symbol | Default Values |
|---|---|---|
| The number of beacon nodes | 6 | |
| The probability of LOS propagation | 0.6 | |
| The standard deviation of measurement noise | 1 | |
| The NLOS error | ||
| The standard deviation of particle movement | 3 | |
| The number of sample points | 100 | |
| The number of Monte Carlo runs | 1000 |
| Parameters | Symbol | Default Values |
|---|---|---|
| The number of beacon nodes | 6 | |
| The probability of LOS propagation | 0.6 | |
| The standard deviation of measurement noise | 1 | |
| The NLOS error | ||
| The standard deviation of particle movement | 3 | |
| The number of sample points | 100 | |
| The number of Monte Carlo runs | 1000 |
| Algorithms | Running Times |
|---|---|
| KF | 0.01196 s |
| PF | 0.12832 s |
| RAPF | 0.05548 s |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Cheng, L.; Feng, L.; Wang, Y. A Residual Analysis-Based Improved Particle Filter in Mobile Localization for Wireless Sensor Networks. Sensors 2018, 18, 2945. https://doi.org/10.3390/s18092945
Cheng L, Feng L, Wang Y. A Residual Analysis-Based Improved Particle Filter in Mobile Localization for Wireless Sensor Networks. Sensors. 2018; 18(9):2945. https://doi.org/10.3390/s18092945
Chicago/Turabian StyleCheng, Long, Liang Feng, and Yan Wang. 2018. "A Residual Analysis-Based Improved Particle Filter in Mobile Localization for Wireless Sensor Networks" Sensors 18, no. 9: 2945. https://doi.org/10.3390/s18092945
APA StyleCheng, L., Feng, L., & Wang, Y. (2018). A Residual Analysis-Based Improved Particle Filter in Mobile Localization for Wireless Sensor Networks. Sensors, 18(9), 2945. https://doi.org/10.3390/s18092945





