Accurate Indoor Localization Based on CSI and Visibility Graph
Abstract
1. Introduction
- We propose a novel passive indoor localization algorithm, which combines both intra-subcarrier statistics features and inter-subcarrier network features. It can greatly improve the localization performance.
- We develop a modified VG based method to process the frequency-series subcarrier data. Our approach can explore the intra-subcarrier and inter-subcarrier correlations between adjacent subcarriers.
- We validate our theories and techniques in real-world deployments. The results confirm that our technique can significantly outperform state-of-the-art indoor localization techniques and are more robust as well.
2. Related Work
2.1. Indoor Localization Techniques
2.2. Complex Network Techniques
3. Preliminaries
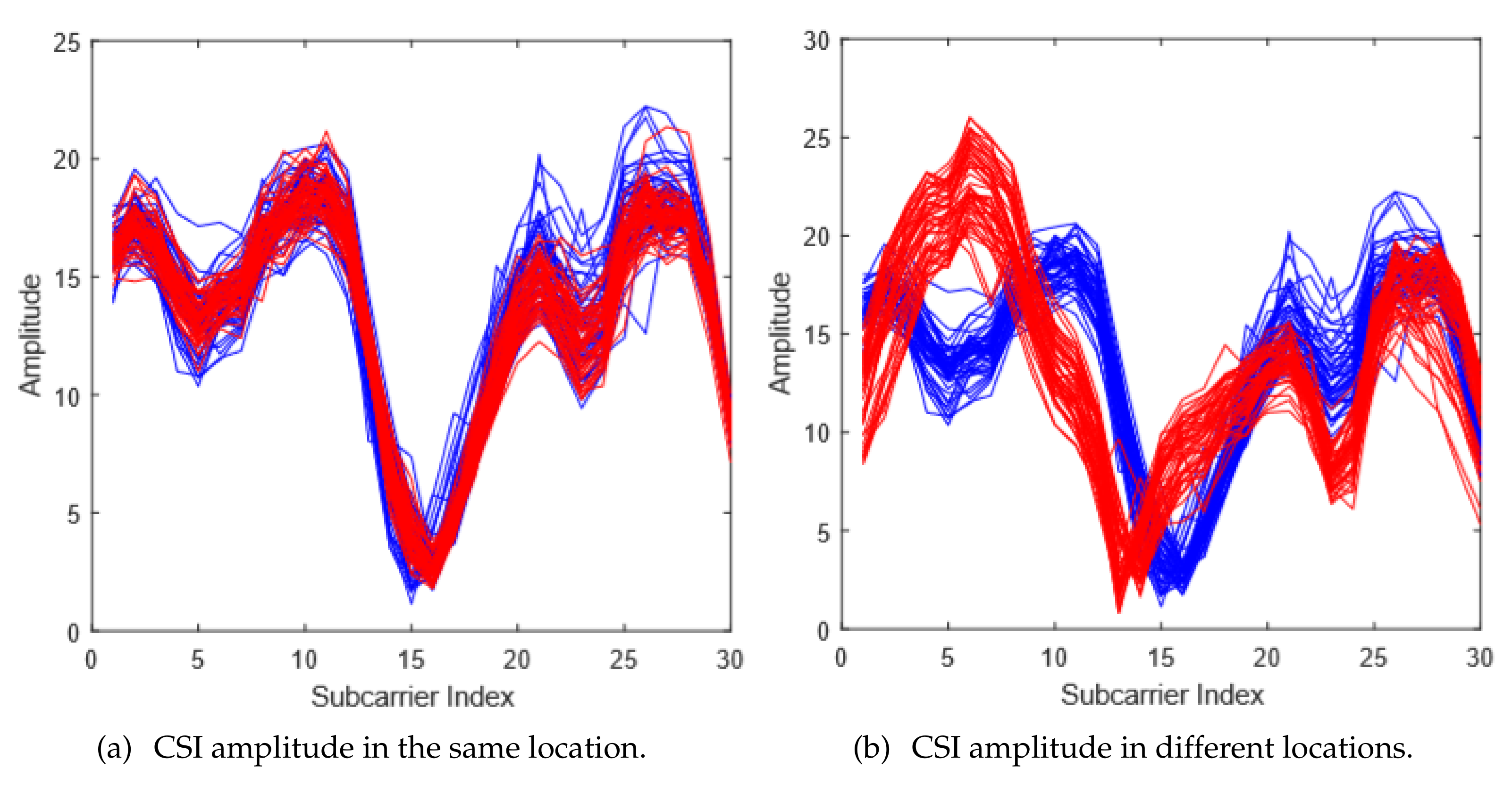
3.1. CSI and Localization
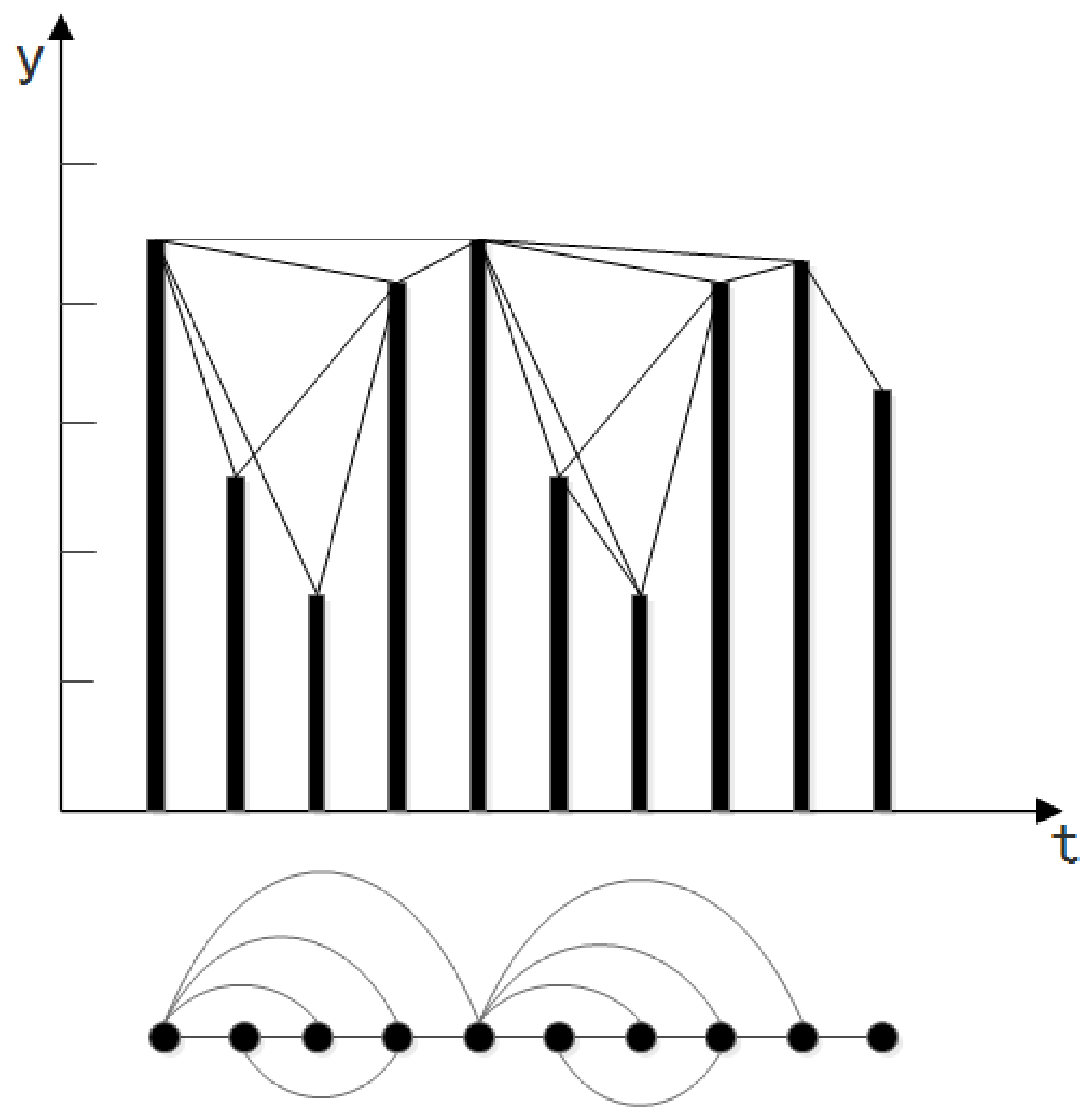
3.2. VG Introduction
3.3. Machine Learning Algorithms
3.3.1. Bayesian Network
3.3.2. Support Vector Machine
3.3.3. Random Forest
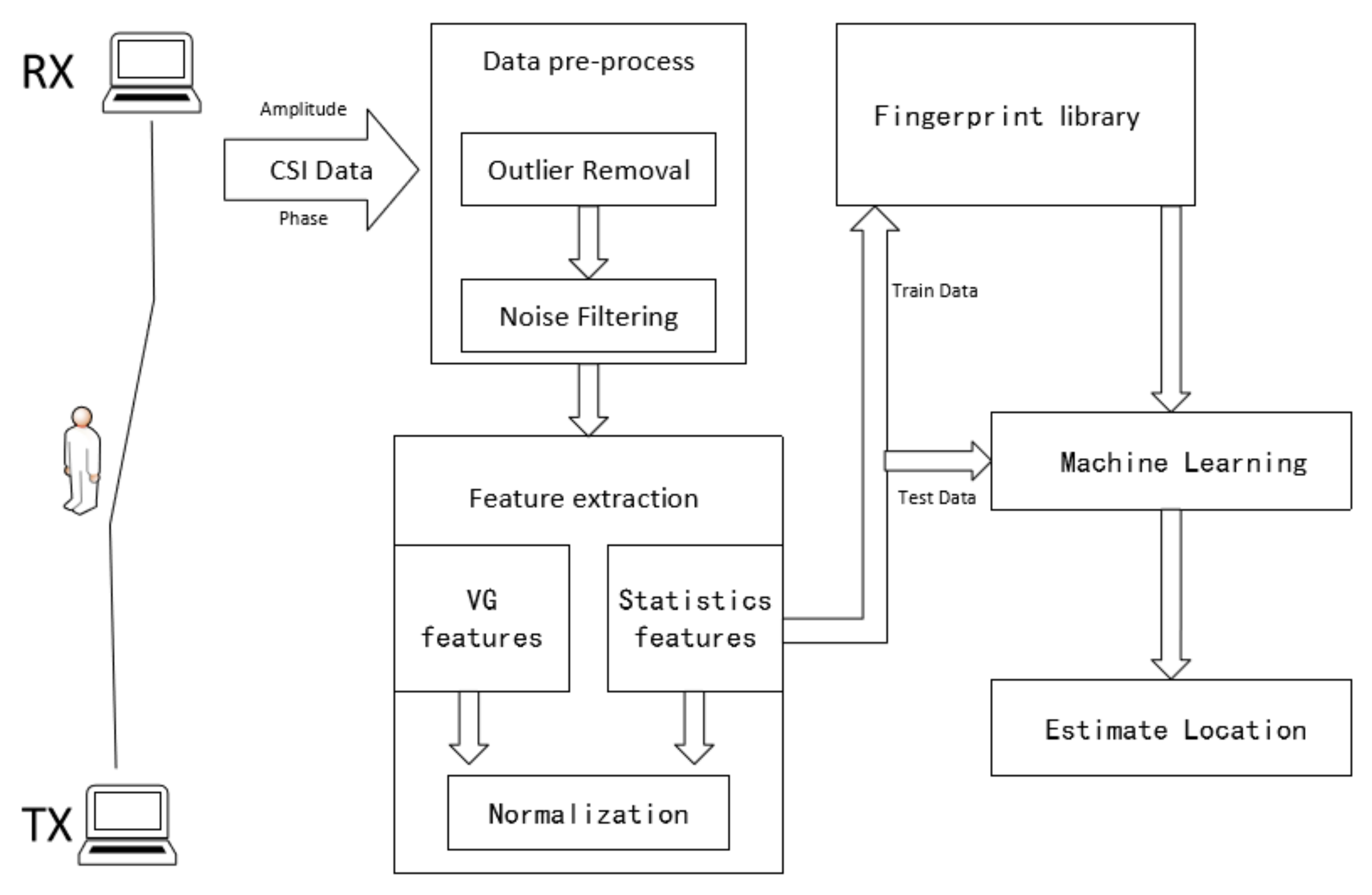
4. VG Based Indoor Localization Method
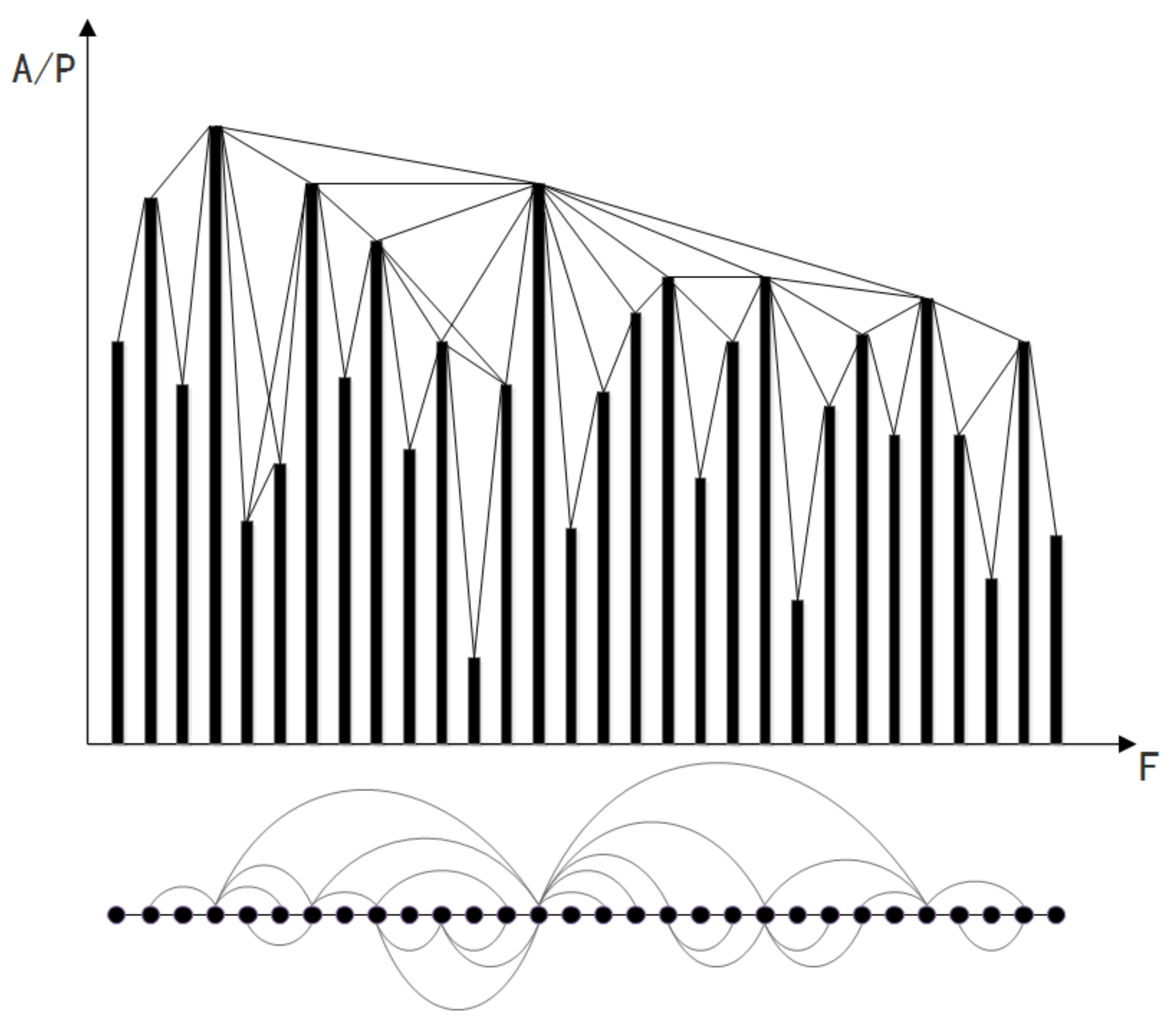
4.1. VG Network Construction
4.2. Network Feature Extraction
- Degree deviation [25]The degree deviation can be calculated using the following equation:where represents the number of nodes connecting to node i, represents the degree deviation, represents the average degree, and N is the total number of nodes in the network.
- Degree assortativity coefficient [30]. The Degree assortativity coefficient feature can be extracted using the following equation:where and is the degree of the two nodes connected by edge i and M is the total number of edges.
- Clustering coefficient entropy [25] The clustering coefficient entropy feature is extracted as follows:where, for node i, is its local clustering coefficient, is the total number of edges connecting to all the neighboring nodes of i, is the the number of edges connecting to node i, is the clustering coefficient probability, N is the total number of nodes in the network, and is the clustering coefficient entropy.
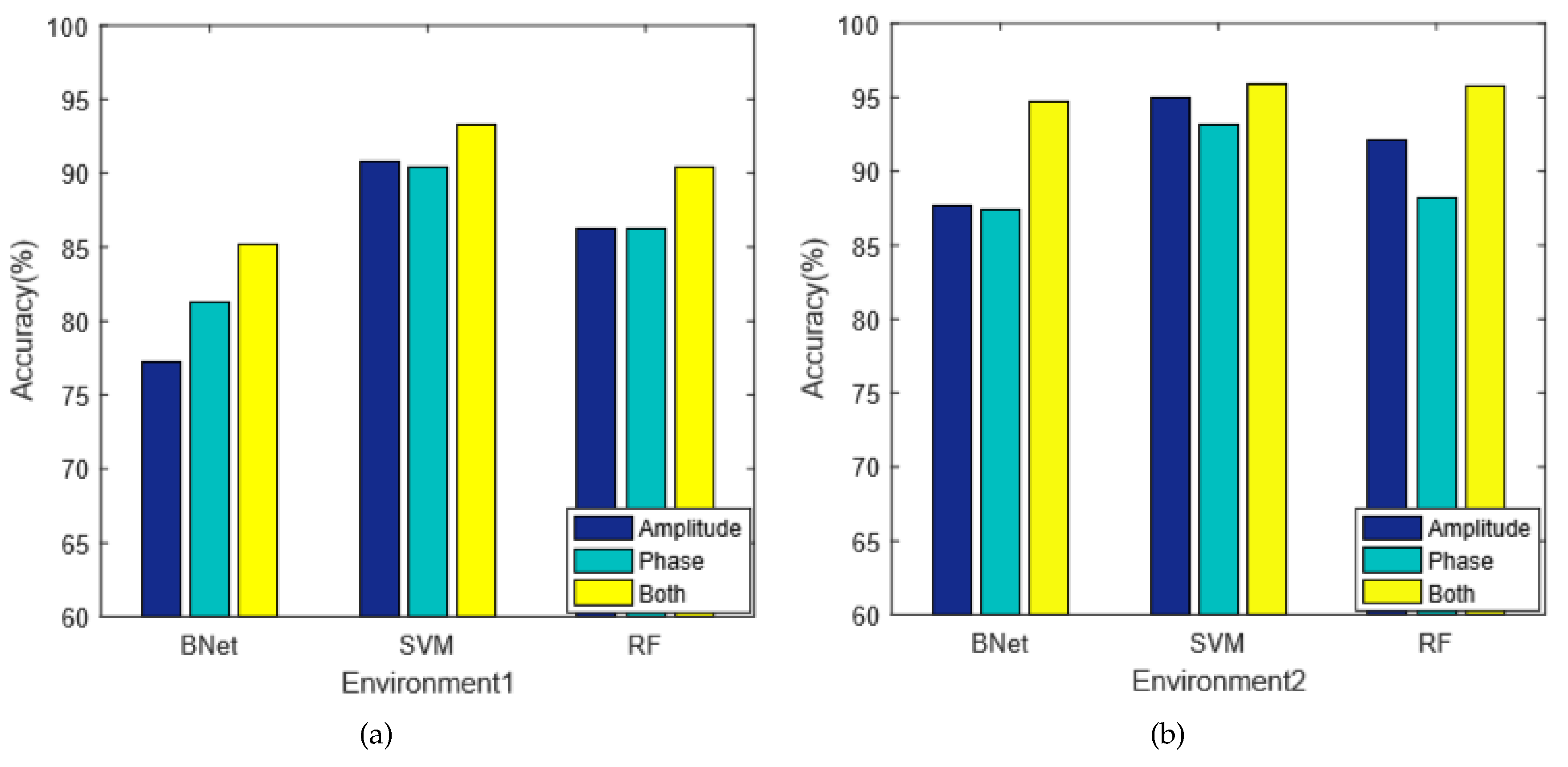
- Average weighted degree [31]. The average weighted degree feature can be extracted as follows:where a and b are two separate nodes, x is the corresponding subcarrier frequency, y is amplitude or phase, and M is the total number of edges.
4.3. Fingerprint Library Creation
4.3.1. Statistical Feature Extraction
4.3.2. Fingerprint Library
5. Experimental Results
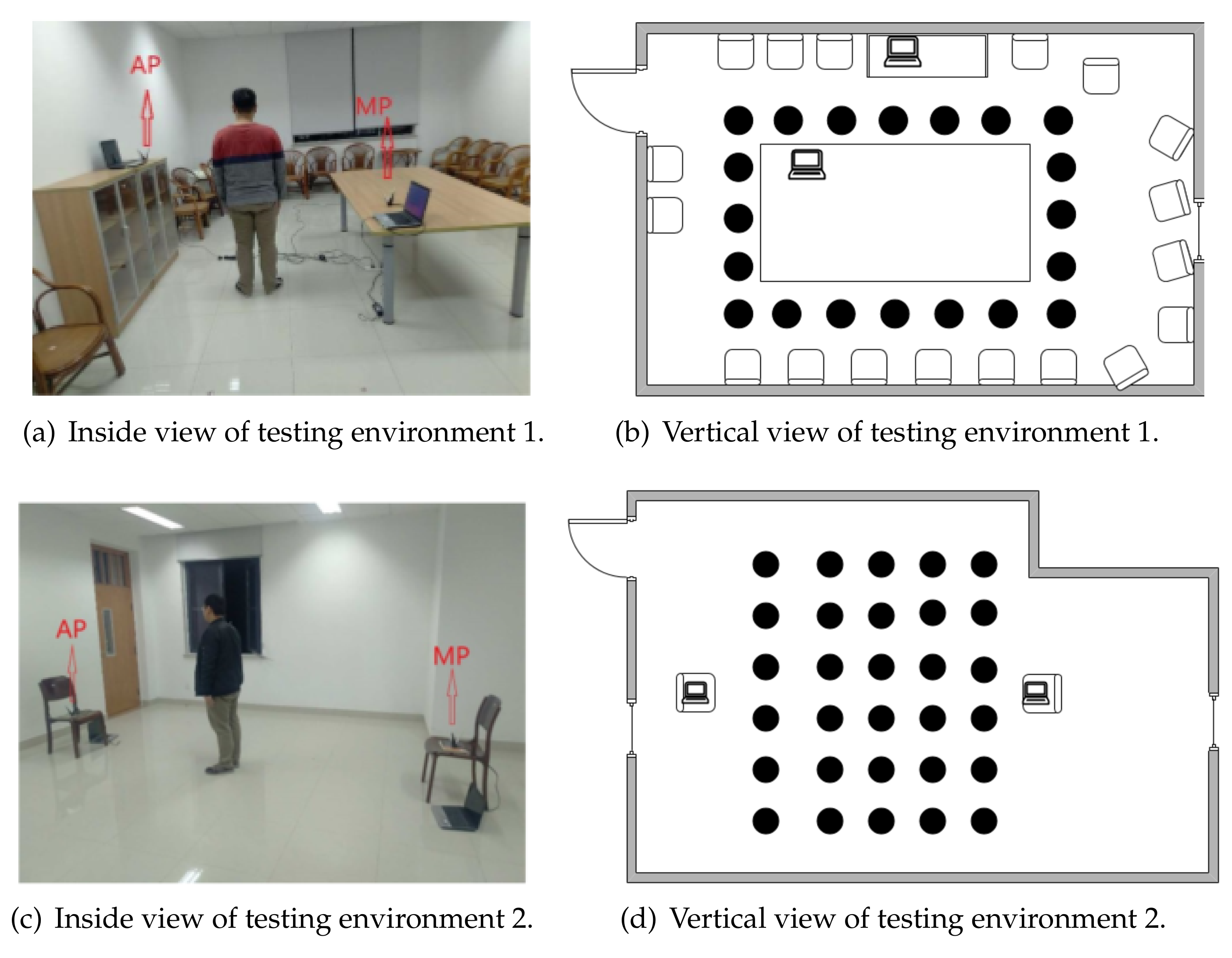
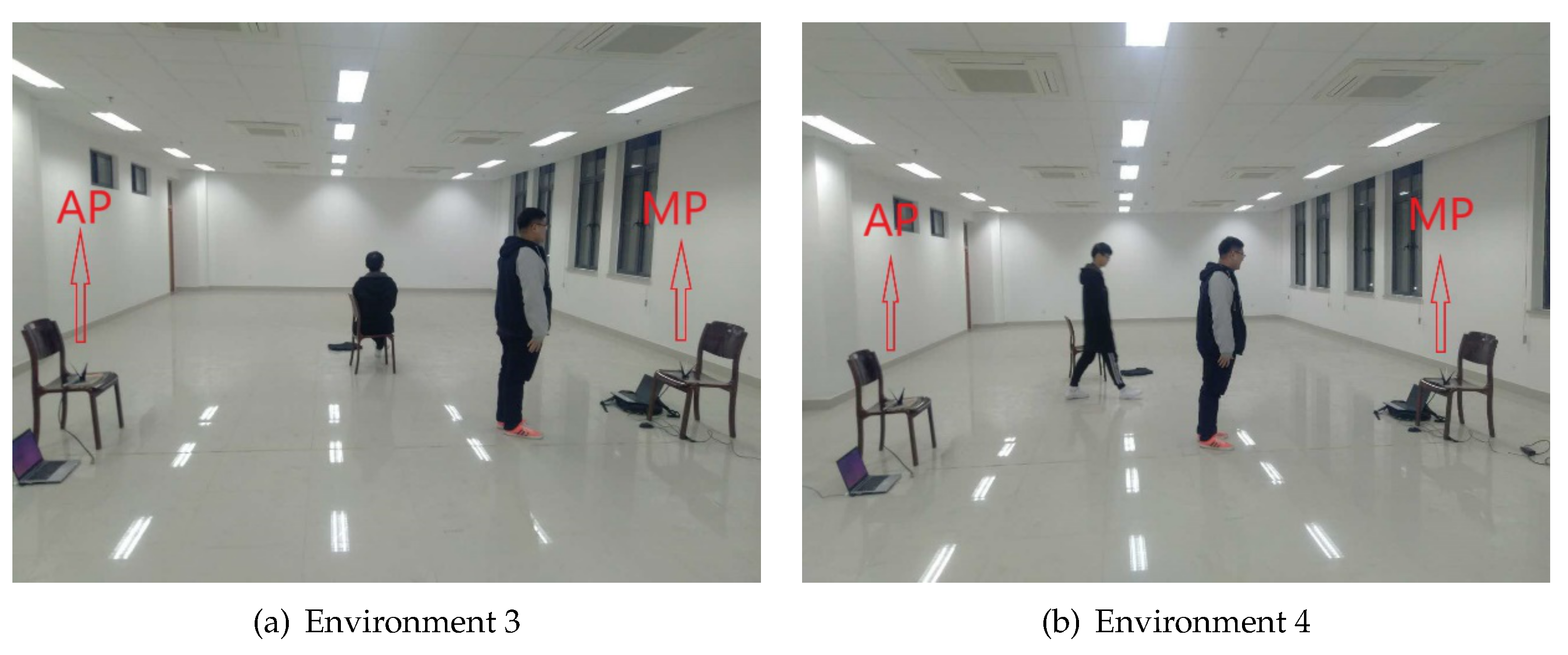
5.1. Experiment Setup
5.2. Data Pre-Processing
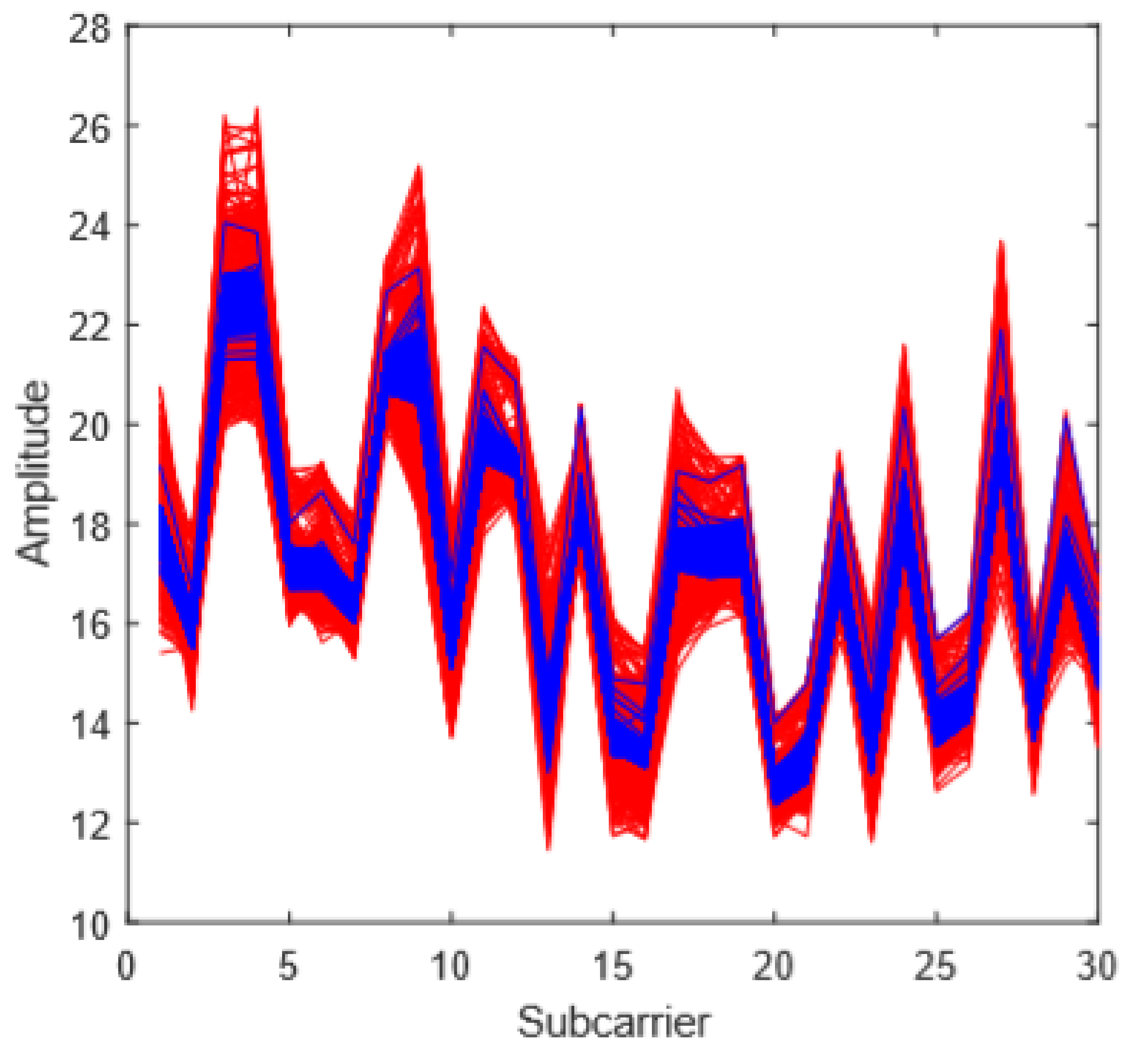
5.2.1. Amplitude and Phase Extraction
5.2.2. Abnormality Processing
5.2.3. Data Smoothing
5.3. Result Analysis
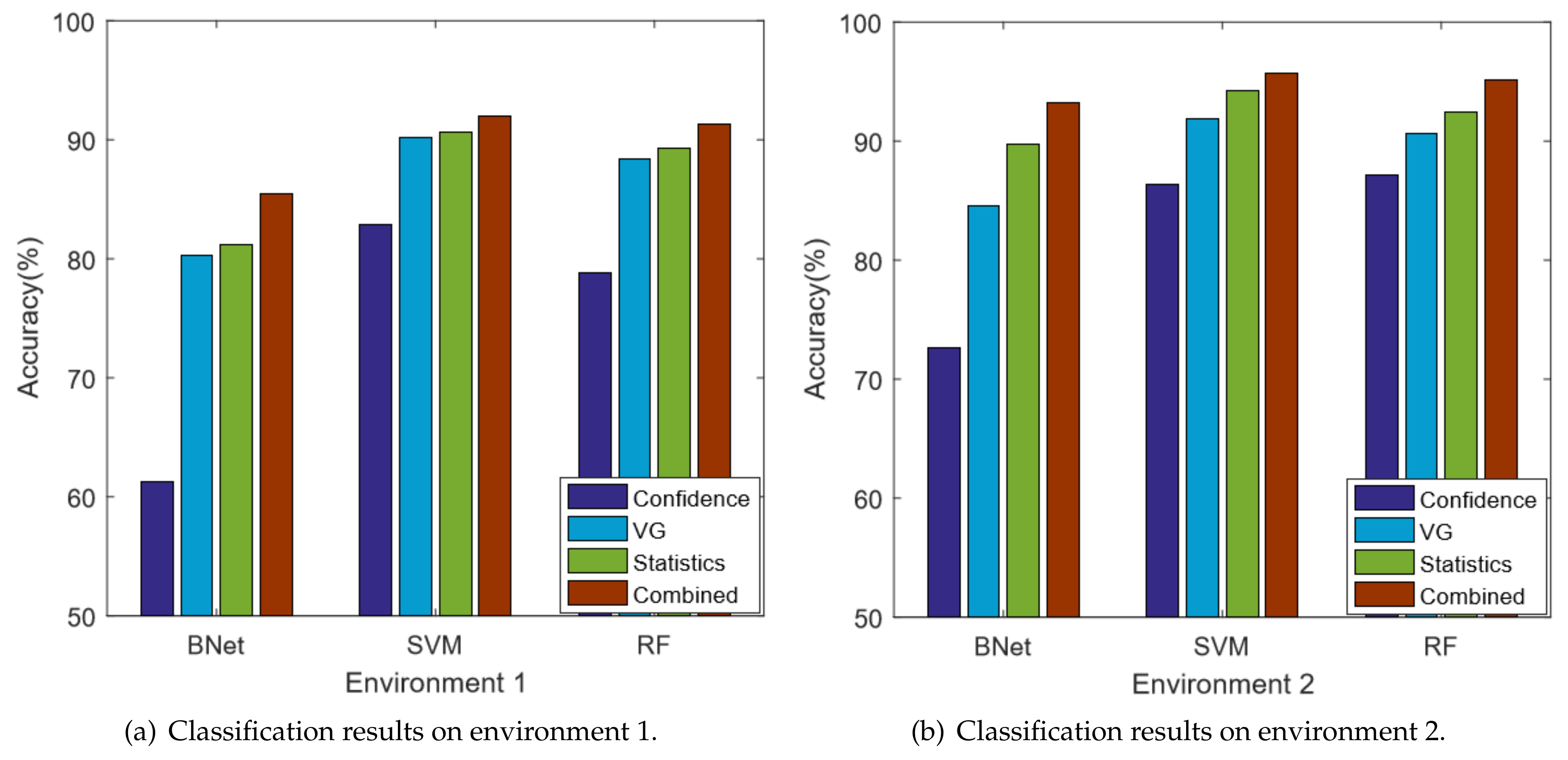
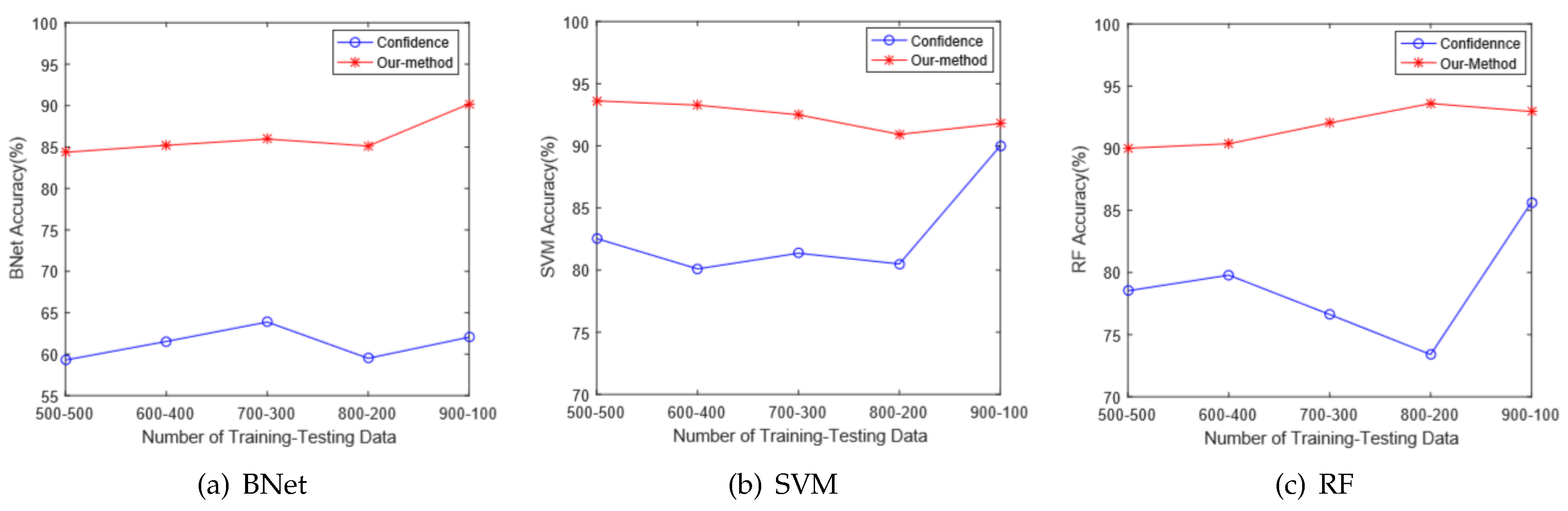
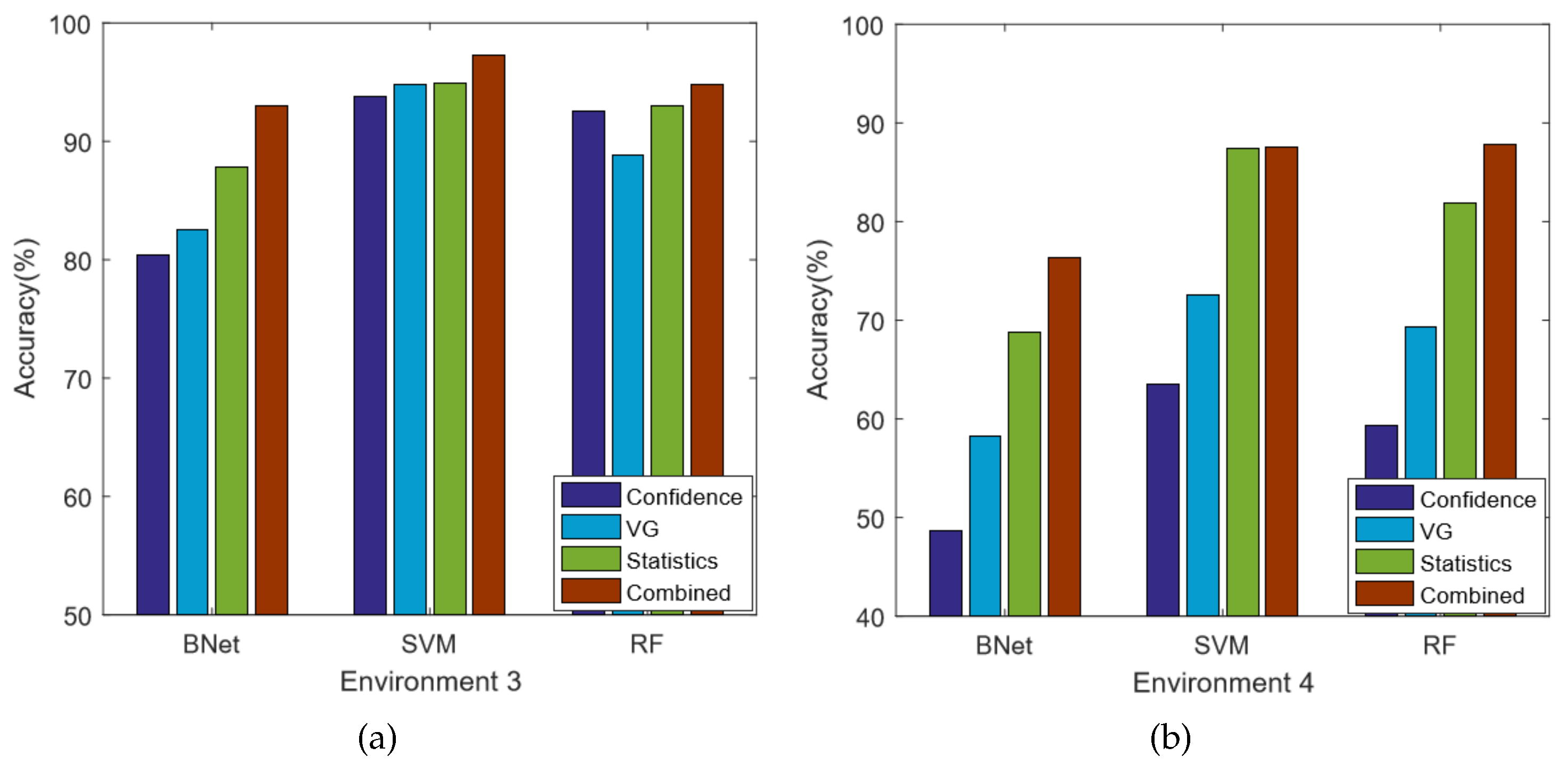
5.3.1. Performance Comparison
- Confidence: the state-of-the-art CSI based localization method [20], which uses the mean and standard deviation features extracted from CSI amplitude.
- Statistics: a technique similar to the confidence method but employs four amplitude features and four phase features.
- VG: a localization technique using only VG network features.
- Combined: our technique which utilizes both VG and statistics features.
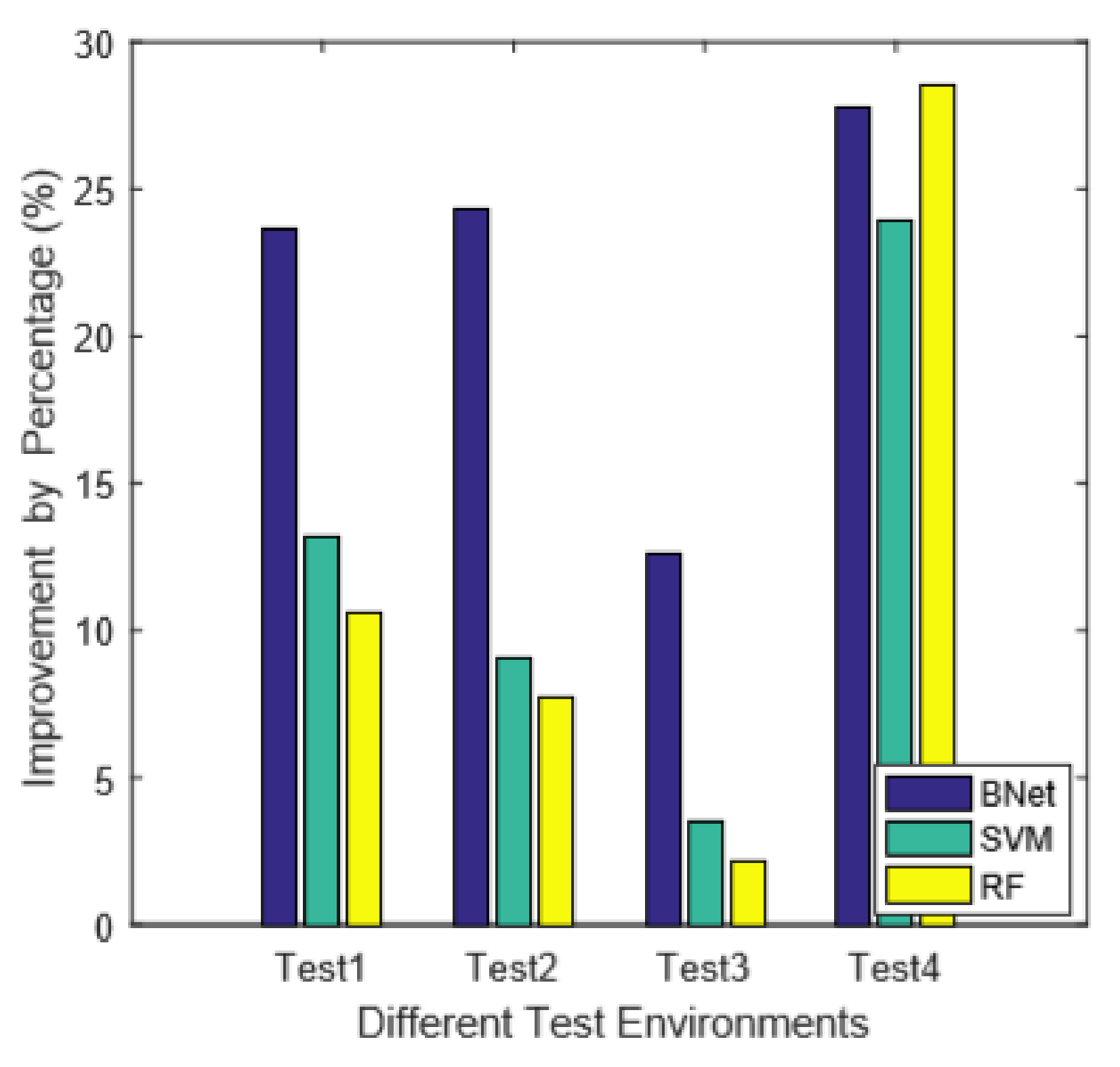
5.3.2. Performance Analysis
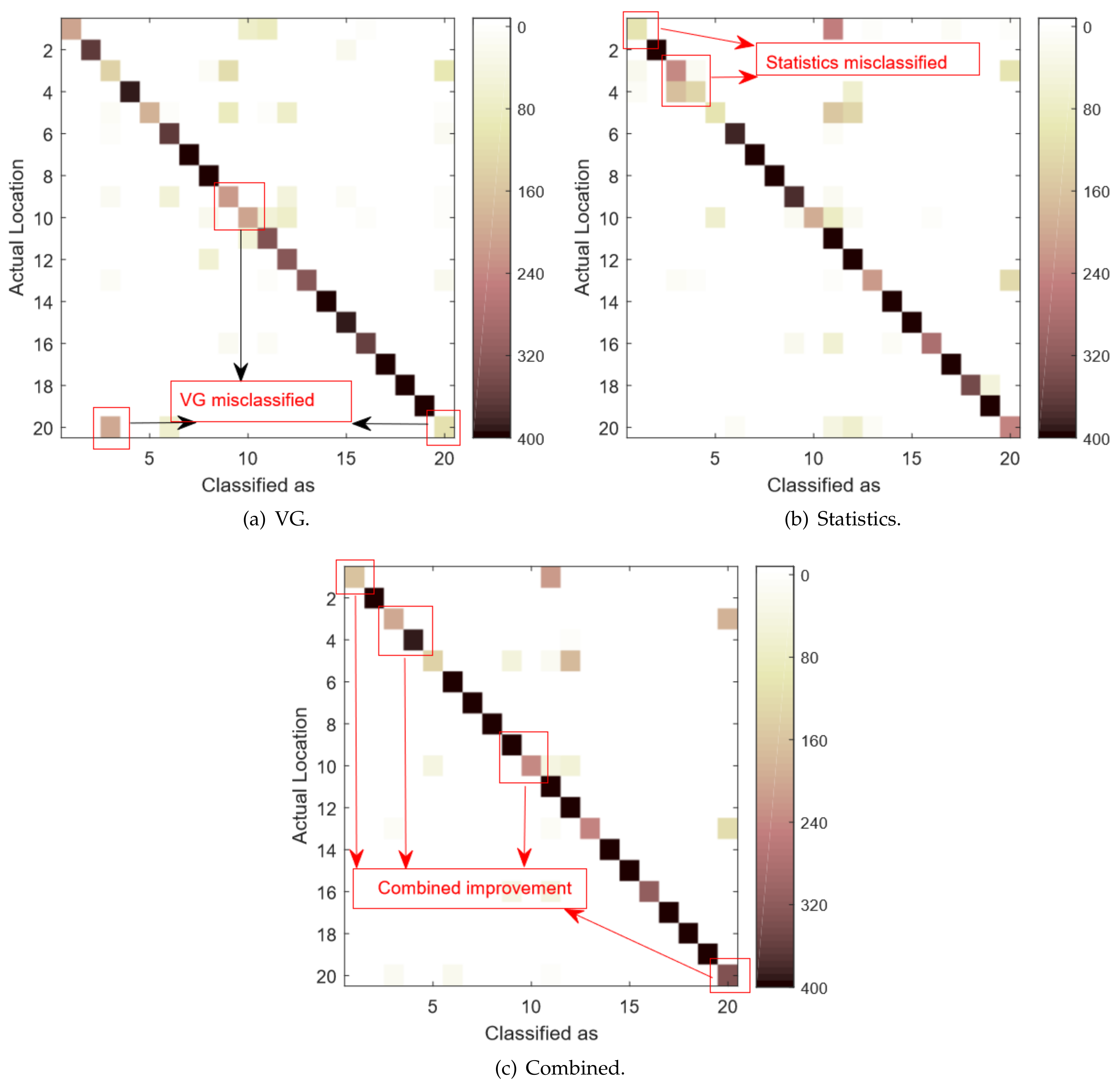
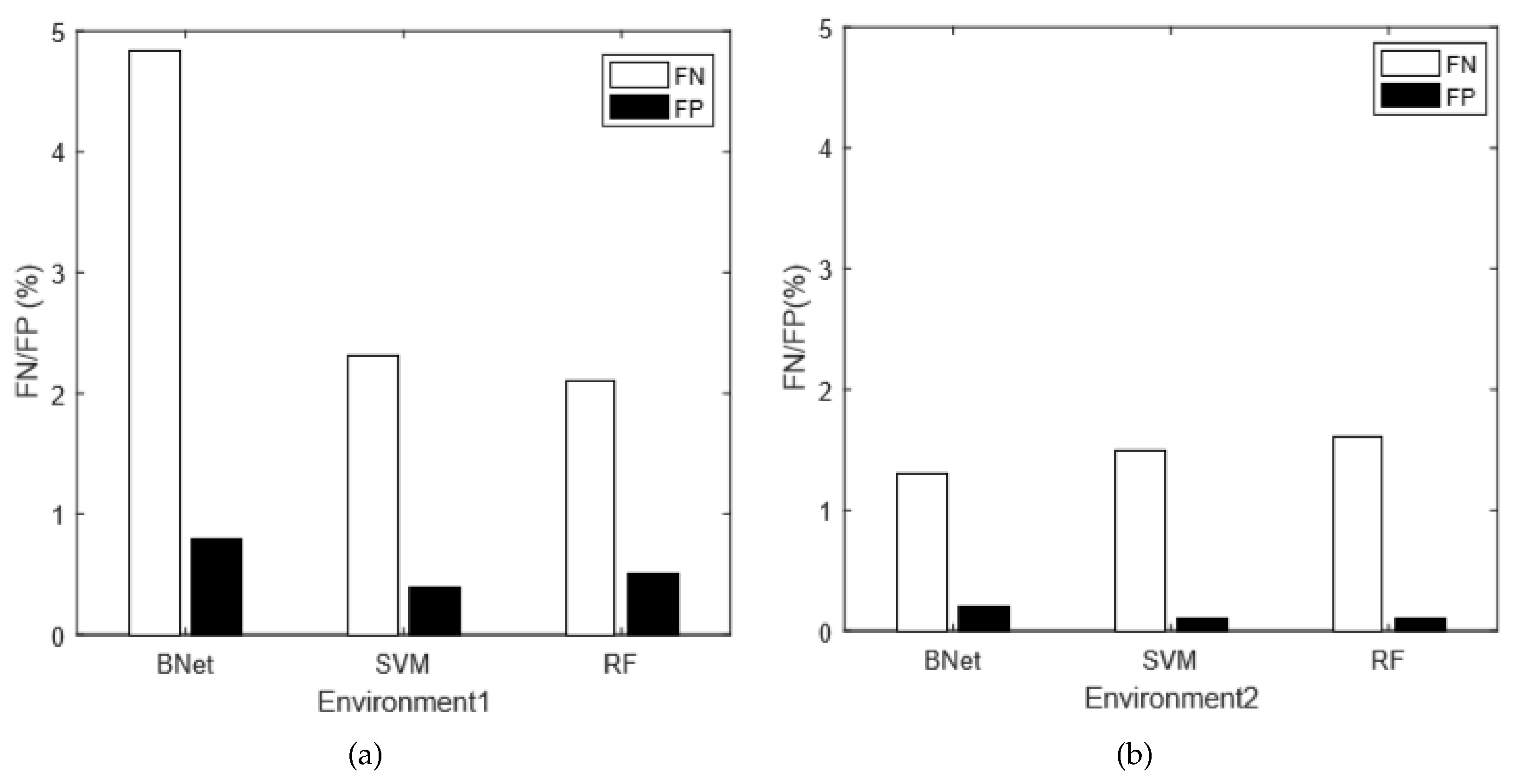
- The CSI signatures contain significant noises. Because of environment variations and multi-path effects, the CSI signals are usually unpredictable and fluctuating, which can greatly affect the localization accuracy. For example, in many scenarios, we observe that the CSI signatures of a person standing in certain locations in the middle are very close to the signatures where one stands in the corner. In that case, those two locations are indistinguishable for any CSI based techniques. Therefore, there are always possibilities for misclassifications.
- The feature selection methods can also cause misclassifications. In this work, we do not use raw CSI data directly. Instead, we extract features from them. Features can filter out the noises and simplify the calculation. However, it is also possible to omit useful information. Our technique is based on two feature sets, which are Statistical and VG features. They stand for the intra and inter correlations of subcarriers, respectively. It is demonstrated in Figure 7 that both feature sets can cause misclassifications. Therefore, for the locations where both feature sets predict incorrectly simultaneously, our technique also misclassifies.
5.3.3. Parameter Selection
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Kemper, J.; Linde, H. Challenges of passive infrared indoor localization. In Proceedings of the 2008 5th Workshop on IEEE Positioning Navigation and Communication, Hannover, Germany, 27 March 2008; IEEE: Piscataway, NJ, USA, 2008; pp. 63–70. [Google Scholar]
- Liu, Y.; Yang, Z. Location, Localization, and Localizability: Location-Awareness Technology for Wireless Networks; Springer: Berlin, Germany, 2011. [Google Scholar]
- Gonçalves, R.; Reis, J.; Santana, E.; Carvalho, N.B.; Pinho, P.; Roselli, L. Smart floor: Indoor navigation based on RFID. In Proceedings of the 2013 IEEE Wireless Power Transfer (WPT), Perugia, Italy, 15–16 May 2013; IEEE: Piscataway, NJ, USA, 2013; pp. 103–106. [Google Scholar]
- Li, X.; Li, S.; Zhang, D.; Xiong, J.; Wang, Y.; Mei, H. Dynamic-MUSIC: Accurate device-free indoor localization. In Proceedings of the ACM International Joint Conference on Pervasive and Ubiquitous Computing, Heidelberg, Germany, 12–16 September 2016; pp. 196–207. [Google Scholar]
- Wu, Z.; Fu, K.; Jedari, E.; Shuvra, S.R.; Rashidzadeh, R.; Saif, M. A Fast and Resource Efficient Method for Indoor Positioning Using Received Signal Strength. IEEE Trans. Veh. Technol. 2016, 65, 9747–9758. [Google Scholar] [CrossRef]
- Mazuelas, S.; Bahillo, A.; Lorenzo, R.M.; Fernandez, P.; Lago, F.A.; Garcia, E.; Blas, J.; Abril, E.J. Robust Indoor Positioning Provided by Real-Time RSSI Values in Unmodified WLAN Networks. IEEE J. Sel. Top. Signal Process. 2009, 3, 821–831. [Google Scholar] [CrossRef]
- Chapre, Y.; Ignjatovic, A.; Seneviratne, A.; Jha, S. CSI-MIMO: Indoor Wi-Fi fingerprinting system. In Proceedings of the 2014 Local Computer Networks, Edmonton, AB, Canada, 8–11 September 2014; pp. 202–209. [Google Scholar]
- Wu, K.; Xiao, J.; Yi, Y.; Chen, D.; Luo, X.; Ni, L.M. CSI-Based Indoor Localization. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 1300–1309. [Google Scholar] [CrossRef]
- Li, F.; Al-Qaness, M.A.A.; Zhang, Y.; Zhao, B.; Luan, X. A Robust and Device-Free System for the Recognition and Classification of Elderly Activities. Sensors 2016, 16, 2043. [Google Scholar] [CrossRef] [PubMed]
- Lacasa, L.; Luque, B.; Ballesteros, F. From time series to complex networks: the visibility graph. Proc. Natl. Acad. Sci. USA 2008, 105, 4972–4975. [Google Scholar] [CrossRef] [PubMed]
- Zanca, G.; Zorzi, F.; Zanella, A.; Zorzi, M. Experimental comparison of RSSI-based localization algorithms for indoor wireless sensor networks. In Proceedings of the 2008 Workshop on Real-World Wireless Sensor Networks, Glasgow, UK, 1–4 April 2008; pp. 1–5. [Google Scholar]
- Paul, A.S.; Wan, E.A. RSSI-Based Indoor Localization and Tracking Using Sigma-Point Kalman Smoothers. IEEE J. Sel. Top. Signal Process. 2009, 3, 860–873. [Google Scholar] [CrossRef]
- Ahn, H.S.; Yu, W. Environmental-Adaptive RSSI-Based Indoor Localization. IEEE Trans. Autom. Sci. Eng. 2009, 6, 626–633. [Google Scholar]
- El-Din, R.A.Z.; Rizk, M. Accurate indoor localization based on RSSI with adaptive environmental parameters in wireless sensor networks. In Proceedings of the First International Conference on Innovative Engineering Systems, Alexandria, Egypt, 7–9 December 2012; pp. 177–183. [Google Scholar]
- Sen, S.; Radunovic, B.; Choudhury, R.R.; Minka, T. Precise indoor localization using PHY information. In Proceedings of the 2011 International Conference on Mobile Systems, Applications, and Services, Washington, DC, USA, 28 June–1 July 2011; pp. 413–414. [Google Scholar]
- Sen, S.; Choudhury, R.R.; Minka, T. You are facing the Mona Lisa: Spot localization using PHY layer information. In Proceedings of the 2012 International Conference on Mobile Systems, Applications, and Services, Lake District, UK, 26–29 Jun 2012; pp. 183–196. [Google Scholar]
- Wu, K.; Xiao, J.; Yi, Y.; Gao, M.; Ni, L. FILA: Fine-grained indoor localization. Proc. IEEE INFOCOM 2012, 131, 2210–2218. [Google Scholar]
- Xiao, J.; Wu, K.; Yi, Y.; Wang, L.; Ni, L.M. Pilot: Passive Device-Free Indoor Localization Using Channel State Information. In Proceedings of the 2013 IEEE 33rd International Conference on Distributed Computing Systems, Philadelphia, PA, USA, 8–11 July 2013; pp. 236–245. [Google Scholar]
- Abdel-Nasser, H.; Samir, R.; Sabek, I.; Youssef, M. MonoPHY: Mono-Stream-based Device-free WLAN Localization via Physical Layer Information. In Proceedings of the 2013 IEEE Wireless Communications and Networking Conference (WCNC 2013), Shanghai, China, 7–10 April 2013; pp. 4546–4551. [Google Scholar]
- Wu, Z.; Xu, Q.; Li, J.; Fu, C.; Xuan, Q.; Xiang, Y. Passive Indoor Localization Based on CSI and Naive Bayes Classification. IEEE Trans. Syst. Man Cybern. Syst. 2017, PP, 1–12. [Google Scholar] [CrossRef]
- Xuan, Q.; Zhou, M.; Zhang, Z.Y.; Fu, C.; Xiang, Y.; Wu, Z.; Filkov, V. Modern Food Foraging Patterns: Geography and Cuisine Choices of Restaurant Patrons on Yelp. IEEE Trans. Comput. Soc. Syst. 2018, 5, 508–517. [Google Scholar] [CrossRef]
- Fu, C.; Zhao, M.; Fan, L.; Chen, X.; Chen, J.; Wu, Z.; Xia, Y.; Xuan, Q. Link Weight Prediction Using Supervised Learning Methods and Its Application to Yelp Layered Network. IEEE Trans. Knowl. Data Eng. 2018. [Google Scholar] [CrossRef]
- Hu, H.X.; Wen, G.; Yu, W.; Xuan, Q.; Chen, G. Swarming Behavior of Multiple Euler-Lagrange Systems With Cooperation-Competition Interactions: An Auxiliary System Approach. IEEE Trans. Neural Netw. Learn. Syst. 2018, PP, 1–12. [Google Scholar] [CrossRef] [PubMed]
- Xuan, Q.; Zhang, Z.Y.; Fu, C.; Hu, H.X.; Filkov, V. Social Synchrony on Complex Networks. IEEE Trans. Cybern. 2018, 48, 1420–1431. [Google Scholar] [CrossRef] [PubMed]
- Gao, Z.K.; Cai, Q.; Yang, Y.X.; Dong, N.; Zhang, S.S. Visibility Graph from Adaptive Optimal Kernel Time-Frequency Representation for Classification of Epileptiform EEG. Int. J. Neural Syst. 2017, 27, 1750005. [Google Scholar] [CrossRef] [PubMed]
- Gao, Z.K.; Cai, Q.; Yang, Y.X.; Dang, W.D. Time-dependent limited penetrable visibility graph analysis of nonstationary time series. Phys. A Stat. Mech. Appl. 2017, 476, 43–48. [Google Scholar] [CrossRef]
- Yan, Y.; Zhang, S.; Tang, J.; Wang, X. Understanding characteristics in multivariate traffic flow time series from complex network structure. Phys. A Stat. Mech. Appl. 2017, 477, 149–160. [Google Scholar] [CrossRef]
- Zhu, G.; Li, Y.; Wen, P.P. Analysis and classification of sleep stages based on difference visibility graphs from a single-channel EEG signal. IEEE J. Biomed. Health Inform. 2014, 18, 1813–1821. [Google Scholar] [CrossRef] [PubMed]
- Halperin, D.; Hu, W.; Sheth, A.; Wetherall, D. Tool release: Gathering 802.11 n traces with channel state information. In ACM SIGCOMM Computer Communication Review; ACM Digital Library: New York, NY, USA, 2011; Volume 41, p. 53. [Google Scholar]
- Newman, M.E. Mixing patterns in networks. Phys. Rev. E Stat. Nonlinear Soft Matter Phys. 2003, 67, 026126. [Google Scholar] [CrossRef] [PubMed]
- Supriya, S.; Siuly, S.; Wang, H.; Cao, J.; Zhang, Y. Weighted Visibility Graph With Complex Network Features in the Detection of Epilepsy. IEEE Access 2016, 4, 6554–6566. [Google Scholar] [CrossRef]
- Wu, C.; Yang, Z.; Zhou, Z.; Qian, K. PhaseU: Real-time LOS identification with WiFi. In Proceedings of the 2015 Computer Communications, Hong Kong, China, 26 April–1 May 2015; pp. 2038–2046. [Google Scholar]
- Han, C.; Wu, K.; Wang, Y.; Ni, L.M. WiFall: Device-free fall detection by wireless networks. In Proceedings of the IEEE INFOCOM 2014—IEEE Conference on Computer Communications, Toronto, ON, Canada, 27 April–2 May 2014; pp. 271–279. [Google Scholar]
| Environment | BNet | SVM | RF | |||
|---|---|---|---|---|---|---|
| Acc(%) | Time(s) | Acc(%) | Time(s) | Acc(%) | Time(s) | |
| Env1 | 85.21 | 0.56 | 93.28 | 1.79 | 90.70 | 4.92 |
| Env2 | 84.74 | 1.15 | 95.90 | 3.21 | 95.74 | 8.84 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, Z.; Jiang, L.; Jiang, Z.; Chen, B.; Liu, K.; Xuan, Q.; Xiang, Y. Accurate Indoor Localization Based on CSI and Visibility Graph. Sensors 2018, 18, 2549. https://doi.org/10.3390/s18082549
Wu Z, Jiang L, Jiang Z, Chen B, Liu K, Xuan Q, Xiang Y. Accurate Indoor Localization Based on CSI and Visibility Graph. Sensors. 2018; 18(8):2549. https://doi.org/10.3390/s18082549
Chicago/Turabian StyleWu, Zhefu, Lei Jiang, Zhuangzhuang Jiang, Bin Chen, Kai Liu, Qi Xuan, and Yun Xiang. 2018. "Accurate Indoor Localization Based on CSI and Visibility Graph" Sensors 18, no. 8: 2549. https://doi.org/10.3390/s18082549
APA StyleWu, Z., Jiang, L., Jiang, Z., Chen, B., Liu, K., Xuan, Q., & Xiang, Y. (2018). Accurate Indoor Localization Based on CSI and Visibility Graph. Sensors, 18(8), 2549. https://doi.org/10.3390/s18082549




