A Survey of Anomaly Detection in Industrial Wireless Sensor Networks with Critical Water System Infrastructure as a Case Study
Abstract
1. Introduction
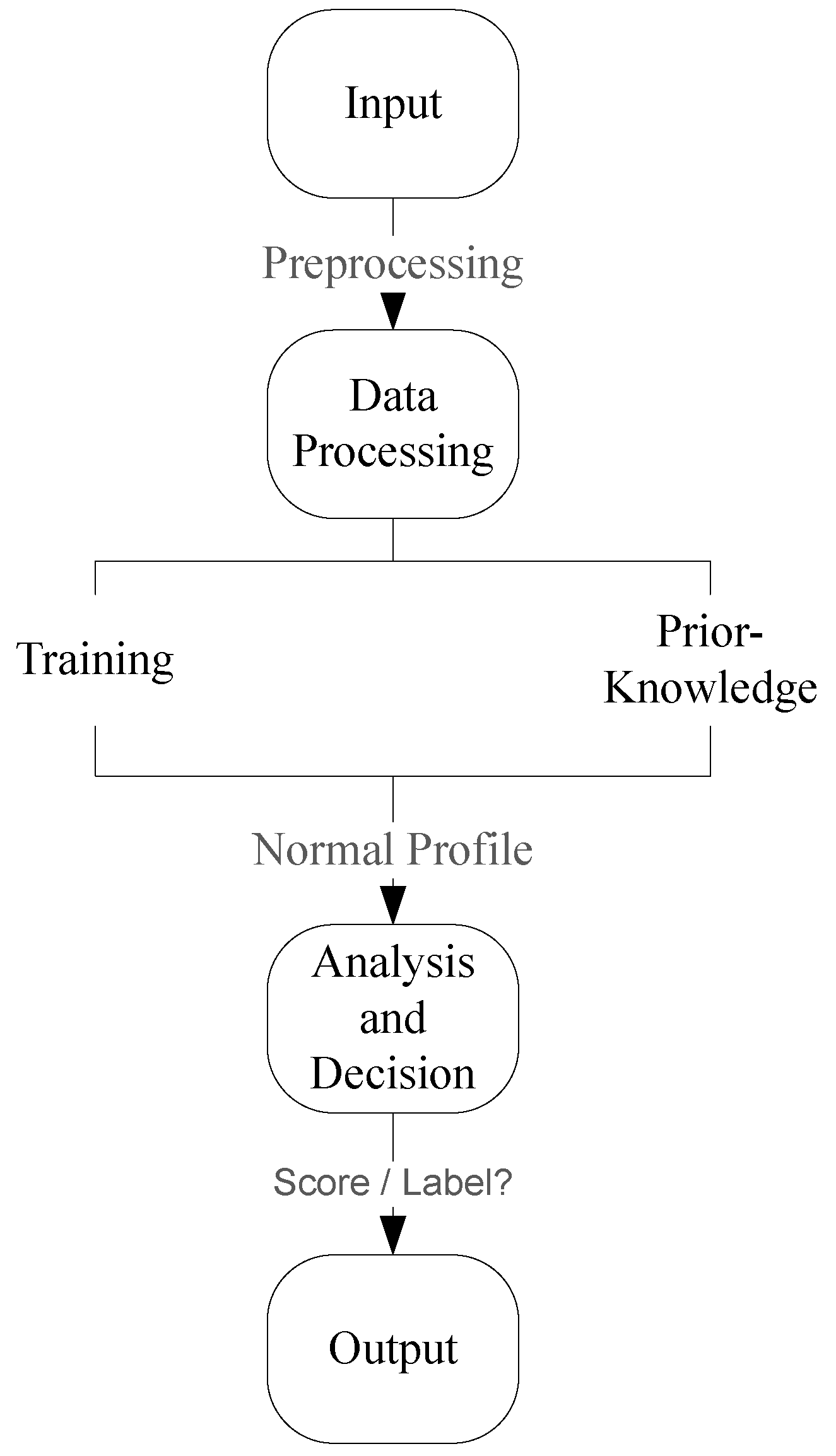
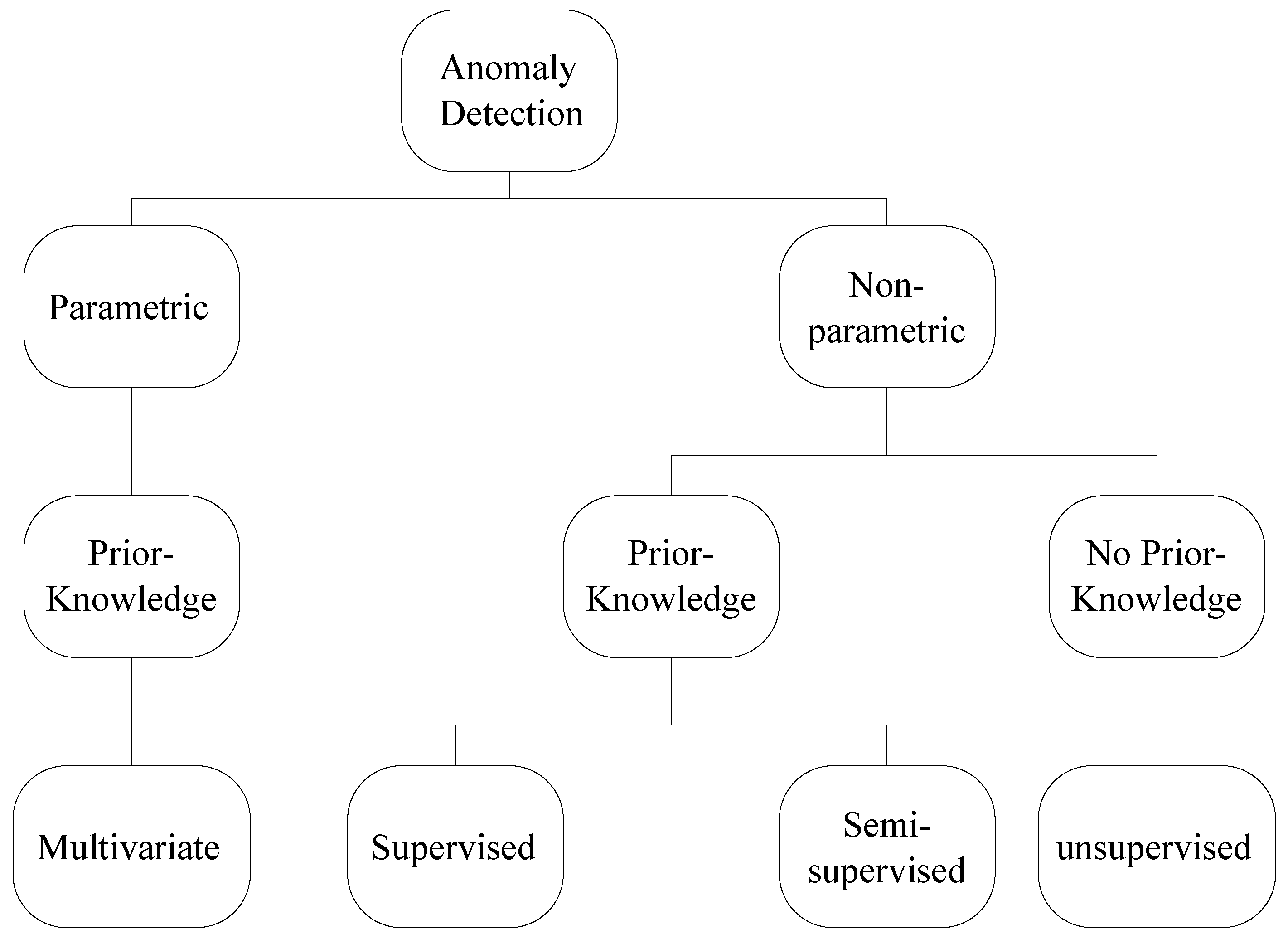
2. Anomaly Detection
3. Parametric Methods
Multivariate Distribution Functions
4. Non-Parametric Methods
4.1. K-Nearest Neighbour
4.2. Support Vector Machines
4.3. Artificial Neural Networks
4.4. Genetic Algorithms
4.5. Hybrid Systems
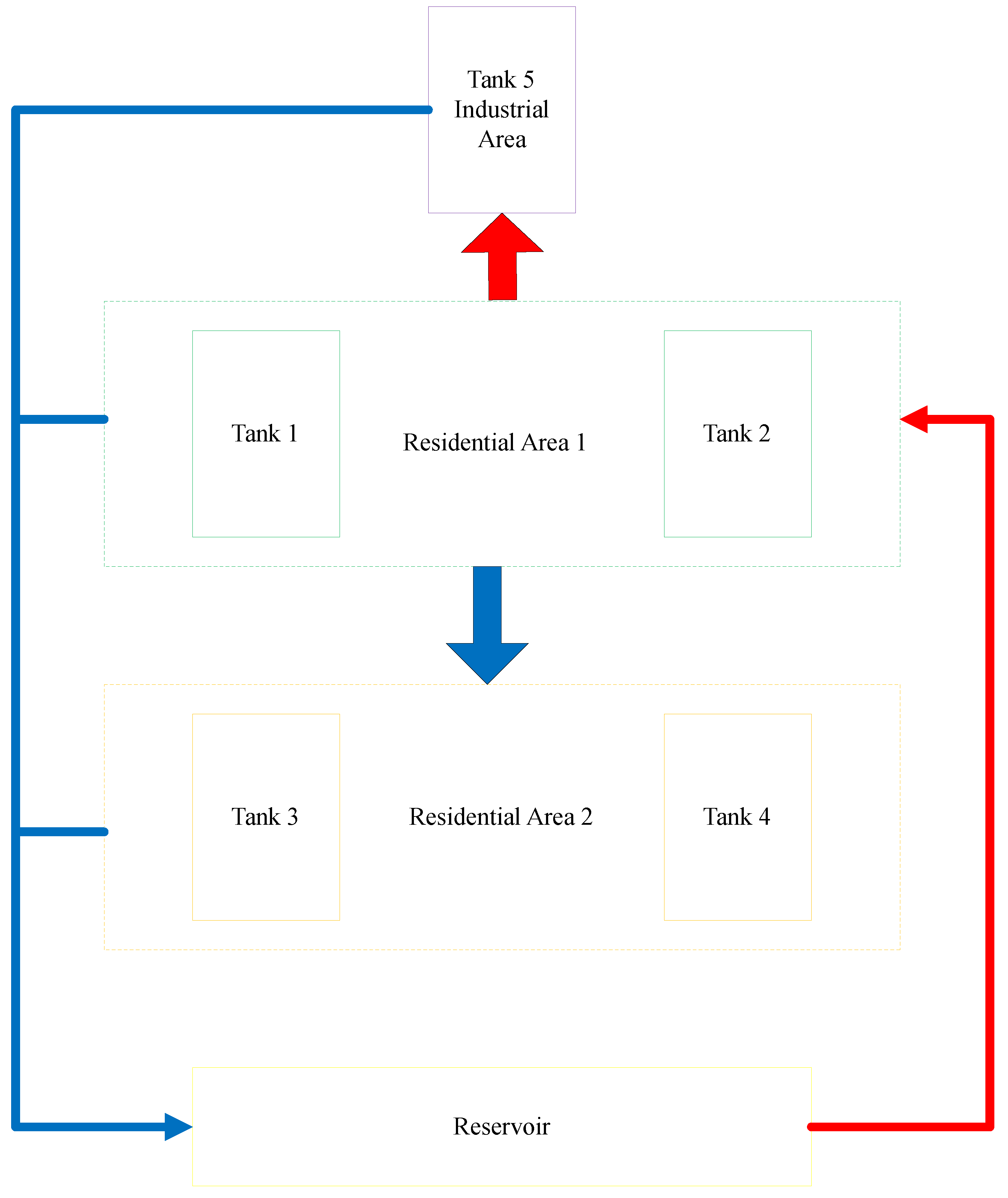
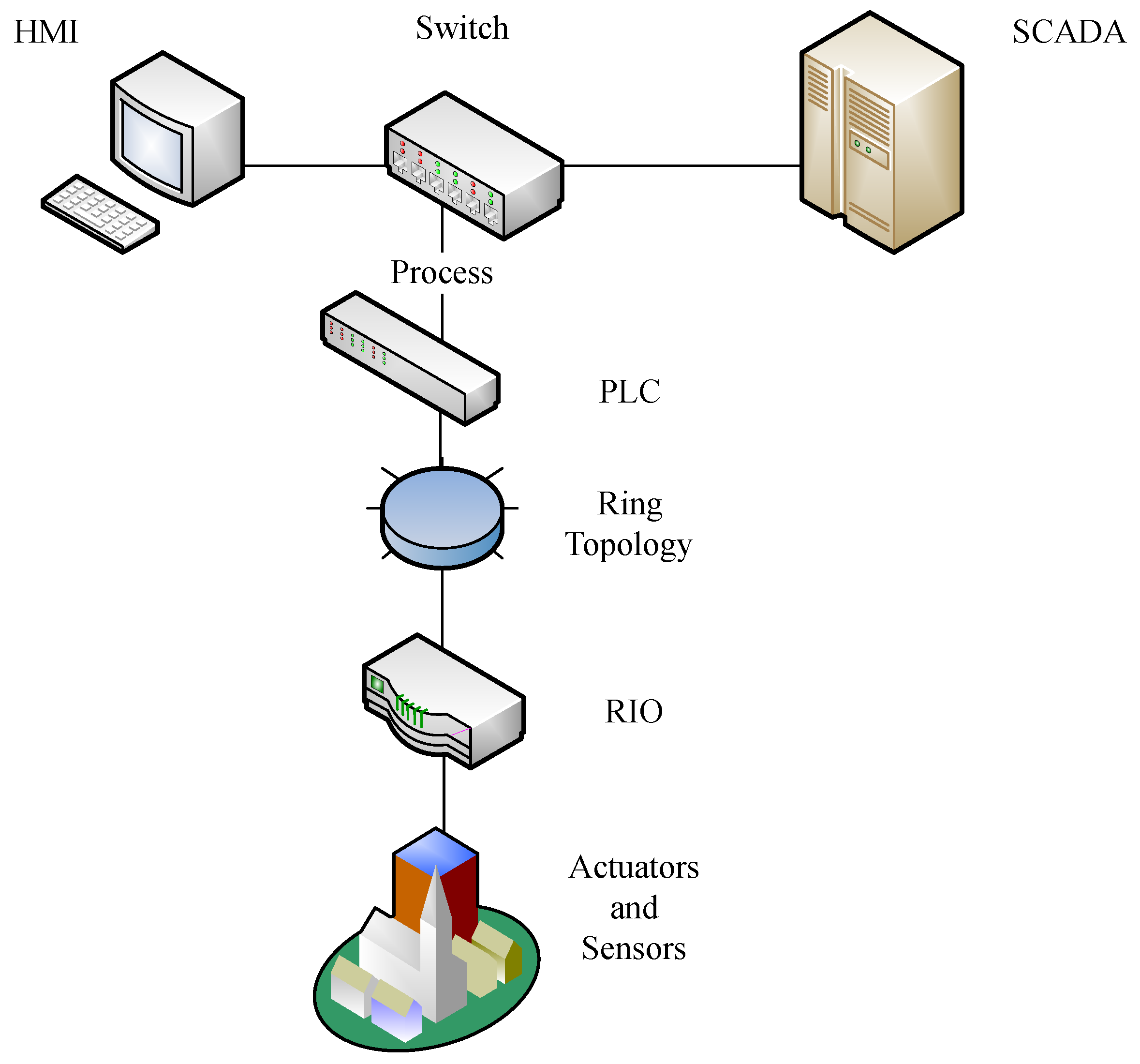
5. Anomaly Detection in Water Systems
6. Applying Anomaly Detection in Water Systems
6.1. Data Integrity Attack
6.2. Feature Selection
6.3. Training Methods
6.4. Algorithm Evaluation
7. Observations and Recommendations
7.1. Summary Comparison
7.2. Discussion on Performance/Issues
7.3. Recommendations and Research Challenges
7.3.1. Practical Evaluation
7.3.2. Complex Malicious Attack Protection
7.3.3. Data Recovery
7.3.4. Online Learning
7.3.5. Benchmarking
7.3.6. Hybrid Schemes
7.3.7. Critical Infrastructure Applications
7.3.8. Harsh Environments
8. Conclusions
Author Contributions
Funding
Acknowledgments
Conflicts of Interest
Abbreviations
| IWSN | Industrial Wireless Sensor Networks |
| SCADA | Supervisory Control And Data Acquisition |
| IoT | Internet of Things |
| FD | Fault Detection |
| DoS | Denial of Service |
| kNN | K-Nearest Neighbours |
| LOF | Local Outlier Factor |
| COF | Connectivity-based Outlier Factor |
| ULOF | Uncertain Local Outlier Factors |
| WNaNG | Weighted Natural Neighbour Graph |
| SVM | Support Vector machines |
| SRM | Structural Risk Minimisation |
| RKHS | Reproducing Kernel Hilbert Space |
| RBF | Radial Basis Function |
| CS-SVM | Conic Segmentation SVM |
| ANN | Artificial Neural Networks |
| OS-ELM | Online Sequential Extreme Learning Machine |
| SLFN | Single Layer Feed-Forward Neural Networks |
| GS | Genetic Algorithms |
| NS-2 | Network Simulator 2 |
| NSA | Negative Selection Algorithm |
| AIS | Artificial Immune System |
| SC | Spectral Clustering |
| DNN | Deep Neural Networks |
| PLC | Programmable Logic Controller |
| SWaT | Secure Water Treatment |
| MitM | Man-in-the-Middle |
| ICS | Industrial Control Systems |
| RIO | Remote Input/Output |
| ROC | Receiver Operating Characteristic |
| AUC | Area Under the Curve |
References
- Akpakwu, G.A.; Silva, B.J.; Hancke, G.P.; Abu-Mahfouz, A.M. A survey on 5G networks for the Internet of Things: Communication technologies and challenges. IEEE Access 2018, 6, 3619–3647. [Google Scholar] [CrossRef]
- Abu-Mahfouz, A.M.; Olwal, T.O.; Kurien, A.M.; Munda, J.L.; Djouani, K. Toward developing a distributed autonomous energy management system (DAEMS). In Proceedings of the AFRICON 2015, Addis Ababa, Ethiopia, 14–17 September 2015; pp. 1–6. [Google Scholar]
- Ogbodo, E.U.; Dorrell, D.; Abu-Mahfouz, A.M. Cognitive radio based sensor network in smart grid: Architectures, applications and communication technologies. IEEE Access 2017, 5, 19084–19098. [Google Scholar] [CrossRef]
- Phala, K.S.E.; Kumar, A.; Hancke, G.P. Air Quality Monitoring System Based on ISO/IEC/IEEE 21451 Standards. IEEE Sens. J. 2016, 16, 5037–5045. [Google Scholar] [CrossRef]
- Cheng, B.; Cui, L.; Jia, W.; Zhao, W.; Gerhard, P.H. Multiple region of interest coverage in camera sensor networks for tele-intensive care units. IEEE Trans. Ind. Inform. 2016, 12, 2331–2341. [Google Scholar] [CrossRef]
- Alcaraz, C.; Lopez, J. A security analysis for wireless sensor mesh networks in highly critical systems. IEEE Trans. Syst. Man Cybern. Part C (Appl. Rev.) 2010, 40, 419–428. [Google Scholar] [CrossRef]
- Sheng, Z.; Mahapatra, C.; Zhu, C.; Leung, V. Recent advances in industrial wireless sensor networks towards efficient management in IoT. IEEE Access 2015, 3, 622–637. [Google Scholar] [CrossRef]
- Gungor, V.C.; Hancke, G.P. Industrial wireless sensor networks: Challenges, design principles, and technical approaches. IEEE Trans. Ind. Electron. 2009, 56, 4258–4265. [Google Scholar] [CrossRef]
- Pritchard, S.W.; Hancke, G.P.; Abu-Mahfouz, A.M. Security in software-defined wireless sensor networks: Threats, challenges and potential solutions. In Proceedings of the 2017 IEEE 15th International Conference on Industrial Informatics (INDIN), Emden, Germany, 24–26 July 2017; pp. 168–173. [Google Scholar]
- Ntuli, N.; Abu-Mahfouz, A. A Simple Security Architecture for Smart Water Management System. Procedia Comput. Sci. 2016, 83, 1164–1169. [Google Scholar] [CrossRef]
- Louw, J.; Niezen, G.; Ramotsoela, T.D.; Abu-Mahfouz, A.M. A key distribution scheme using elliptic curve cryptography in wireless sensor networks. In Proceedings of the 2016 IEEE 14th International Conference on Industrial Informatics (INDIN), Poitiers, France, 19–21 July 2016; pp. 1166–1170. [Google Scholar]
- Abu-Mahfouz, A.M.; Hancke, G.P. Evaluating ALWadHA for providing secure localisation for wireless sensor networks. In Proceedings of the 2013 Africon, Pointe-Aux-Piments, Mauritius, 9–12 September 2013; pp. 1–5. [Google Scholar]
- Cheng, B.; Zhang, J.; Hancke, G.P.; Karnouskos, S.; Colombo, A.W. Industrial Cyberphysical Systems: Realizing Cloud-Based Big Data Infrastructures. IEEE Ind. Electron. Mag. 2018, 12, 25–35. [Google Scholar] [CrossRef]
- Lee, R.M.; Assante, M.J.; Conway, T. Analysis of the Cyber Attack on the Ukrainian Power Grid; SANS Industrial Control Systems: Santa Monica, CA, USA, 2016. [Google Scholar]
- Slay, J.; Miller, M. Lessons learned from the maroochy water breach. In Critical Infrastructure Protection; Springer: Boston, MA, USA, 2007; pp. 73–82. [Google Scholar]
- Can, O.; Sahingoz, O.K. A survey of intrusion detection systems in wireless sensor networks. In Proceedings of the 2015 6th International Conference on Modeling, Simulation, and Applied Optimization (ICMSAO), Istanbul, Turkey, 27–29 May 2015; pp. 1–6. [Google Scholar]
- Xie, M.; Han, S.; Tian, B.; Parvin, S. Anomaly detection in wireless sensor networks: A survey. J. Netw. Comput. Appl. 2011, 34, 1302–1325. [Google Scholar] [CrossRef]
- Kobo, H.I.; Abu-Mahfouz, A.M.; Hancke, G.P. Fragmentation-based Distributed Control System for Software Defined Wireless Sensor Networks. IEEE Trans. Ind. Inform. 2018. [Google Scholar] [CrossRef]
- Kobo, H.I.; Hancke, G.P.; Abu-Mahfouz, A.M. Towards a distributed control system for software defined Wireless Sensor Networks. In Proceedings of the IECON 2017—43rd Annual Conference of the IEEE Industrial Electronics Society, Beijing, China, 29 October–1 November 2017; pp. 6125–6130. [Google Scholar]
- Abu-Mahfouz, A.; Hancke, G. ALWadHA Localisation Algorithm: Yet More Energy Efficient. IEEE Access 2017, 5, 6661–6667. [Google Scholar] [CrossRef]
- Abu-Mahfouz, A.; Hancke, G. Localised Information Fusion Techniques for Location Discovery in Wireless Sensor Networks. Int. J. Sensor Netw. (IJSNET) 2017, 26, 12–25. [Google Scholar] [CrossRef]
- Zhang, Y.; Meratnia, N.; Havinga, P. Outlier detection techniques for wireless sensor networks: A survey. IEEE Commun. Surv. Tutor. 2010, 12, 159–170. [Google Scholar] [CrossRef]
- Garcia-Teodoro, P.; Diaz-Verdejo, J.; Maciá-Fernández, G.; Vázquez, E. Anomaly-based network intrusion detection: Techniques, systems and challenges. Comput. Secur. 2009, 28, 18–28. [Google Scholar] [CrossRef]
- Patcha, A.; Park, J.M. An overview of anomaly detection techniques: Existing solutions and latest technological trends. Comput. Netw. 2007, 51, 3448–3470. [Google Scholar] [CrossRef]
- Tsai, C.F.; Hsu, Y.F.; Lin, C.Y.; Lin, W.Y. Intrusion detection by machine learning: A review. Expert Syst. Appl. 2009, 36, 11994–12000. [Google Scholar] [CrossRef]
- Wang, J.; Rossell, D.; Cassandras, C.G.; Paschalidis, I.C. Network anomaly detection: A survey and comparative analysis of stochastic and deterministic methods. In Proceedings of the 2013 IEEE 52nd Annual Conference on Decision and Control (CDC), Florence, Italy, 10–13 December 2013; pp. 182–187. [Google Scholar]
- Butun, I.; Morgera, S.D.; Sankar, R. A survey of intrusion detection systems in wireless sensor networks. IEEE Commun. Surv. Tutor. 2014, 16, 266–282. [Google Scholar] [CrossRef]
- Rajasegarar, S.; Leckie, C.; Palaniswami, M. Anomaly detection in wireless sensor networks. IEEE Wirel. Commun. 2008, 15, 34–40. [Google Scholar] [CrossRef]
- Garitano, I.; Uribeetxeberria, R.; Zurutuza, U. A review of SCADA anomaly detection systems. In Soft Computing Models in Industrial and Environmental Applications, 6th International Conference SOCO 2011; Springer: Berlin, Germany, 2011; pp. 357–366. [Google Scholar]
- Taormina, R.; Galelli, S.; Tippenhauer, N.O.; Salomons, E.; Ostfeld, A. Characterizing cyber-physical attacks on water distribution systems. J. Water Resour. Plan. Manag. 2017, 143, 04017009. [Google Scholar] [CrossRef]
- Garcia-Font, V.; Garrigues, C.; Rifà-Pous, H. A Comparative study of anomaly detection techniques for smart city wireless sensor networks. Sensors 2016, 16, 868. [Google Scholar] [CrossRef] [PubMed]
- Chandola, V.; Banerjee, A.; Kumar, V. Anomaly detection: A survey. ACM Comput. Surv. (CSUR) 2009, 41, 15. [Google Scholar] [CrossRef]
- Görnitz, N.; Kloft, M.M.; Rieck, K.; Brefeld, U. Toward supervised anomaly detection. J. Artif. Intell. Res. 2013, 46, 235–262. [Google Scholar] [CrossRef]
- Xie, M.; Hu, J.; Guo, S.; Zomaya, A.Y. Distributed Segment-Based Anomaly Detection With Kullback–Leibler Divergence in Wireless Sensor Networks. IEEE Trans. Inf. Forensics Secur. 2017, 12, 101–110. [Google Scholar] [CrossRef]
- Magán-Carrión, R.; Camacho, J.; García-Teodoro, P. Multivariate statistical approach for anomaly detection and lost data recovery in wireless sensor networks. Int. J. Distrib. Sens. Netw. 2015, 11, 672124. [Google Scholar] [CrossRef]
- Magán-Carrión, R.; Pulido-Pulido, F.; Camacho, J.; García-Teodoro, P. Tampered data recovery in WSNs through dynamic PCA and variable routing strategies. J. Commun. 2013, 8, 738–750. [Google Scholar] [CrossRef]
- Gowri, M.; Paramasivam, B. Anomaly detection in wireless sensor network using rule-based technique. Int. J. Appl. Eng. Res. 2015, 10, 24179–24187. [Google Scholar]
- Yu, Q.; Jibin, L.; Jiang, L. An improved ARIMA-based traffic anomaly detection algorithm for wireless sensor networks. Int. J. Distrib. Sens. Netw. 2016, 12, 9653230. [Google Scholar] [CrossRef]
- Alsheikh, M.A.; Hoang, D.T.; Niyato, D.; Tan, H.P.; Lin, S. Markov decision processes with applications in wireless sensor networks: A survey. IEEE Commun. Surv. Tutor. 2015, 17, 1239–1267. [Google Scholar] [CrossRef]
- Egilmez, H.E.; Ortega, A. Spectral anomaly detection using graph-based filtering for wireless sensor networks. In Proceedings of the 2014 IEEE International Conference on Acoustics, Speech and Signal Processing (ICASSP), Florence, Italy, 4–9 May 2014; pp. 1085–1089. [Google Scholar]
- Xie, M.; Hu, J.; Han, S.; Chen, H.H. Scalable hypergrid k-NN-based online anomaly detection in wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 1661–1670. [Google Scholar] [CrossRef]
- Liu, J.; Deng, H. Outlier detection on uncertain data based on local information. Knowl.-Based Syst. 2013, 51, 60–71. [Google Scholar] [CrossRef]
- Zhu, Q.; Feng, J.; Huang, J. Weighted natural neighborhood graph: An adaptive structure for clustering and outlier detection with no neighborhood parameter. Cluster Comput. 2016, 19, 1385–1397. [Google Scholar] [CrossRef]
- Rajasegarar, S.; Leckie, C.; Bezdek, J.C.; Palaniswami, M. Centered hyperspherical and hyperellipsoidal one-class support vector machines for anomaly detection in sensor networks. IEEE Trans. Inf. Forensics Secur. 2010, 5, 518–533. [Google Scholar] [CrossRef]
- Martins, H.; Palma, L.; Cardoso, A.; Gil, P. A support vector machine based technique for online detection of outliers in transient time series. In Proceedings of the 2015 10th Asian Control Conference (ASCC), Kota Kinabalu, Malaysia, 31 May–3 June 2015; pp. 1–6. [Google Scholar]
- Salem, O.; Guerassimov, A.; Mehaoua, A.; Marcus, A.; Furht, B. Anomaly Detection in medical wireless sensor networks using SVM and linear regression models. Int. J. E-Health Med. Commun. (IJEHMC) 2014, 5, 20–45. [Google Scholar] [CrossRef]
- Shilton, A.; Rajasegarar, S.; Palaniswami, M. Combined multiclass classification and anomaly detection for large-scale wireless sensor networks. In Proceedings of the 2013 IEEE Eighth International Conference on Intelligent Sensors, Sensor Networks and Information Processing, Melbourne, Australia, 2–5 April 2013; pp. 491–496. [Google Scholar]
- Guo, W.; Zhang, W. A survey on intelligent routing protocols in wireless sensor networks. J. Netw. Comput. Appl. 2014, 38, 185–201. [Google Scholar] [CrossRef]
- Kameswari, U.S.; Babu, I.R. Sensor data analysis and anomaly detection using predictive analytics for process industries. In Proceedings of the 2015 IEEE Workshop on Computational Intelligence: Theories, Applications and Future Directions (WCI), Kalyanpur, India, 14–17 December 2015; pp. 1–8. [Google Scholar]
- Cannady, J. An adaptive neural swarm approach for intrusion defense in ad hoc networks. In SPIE Defense, Security, and Sensing; International Society for Optics and Photonics: Washington, DC, USA, 2011; p. 80590P. [Google Scholar]
- Bosman, H.H.W.J.; Liotta, A.; Iacca, G.; Wortche, H.J. Online extreme learning on fixed-point sensor networks. In Proceedings of the 2013 IEEE 13th International Conference on Data Mining Workshops (ICDMW), Dallas, TX, USA, 7–10 December 2013; pp. 319–326. [Google Scholar]
- Yusuf, S.A.; Brown, D.J.; Mackinnon, A.; Papanicolaou, R. Application of dynamic neural networks with exogenous input to industrial conditional monitoring. In Proceedings of the 2013 International Joint Conference on Neural Networks (IJCNN), Dallas, TX, USA, 4–9 August 2013; pp. 1–8. [Google Scholar]
- Radhika, B.; Raja, P.; Joseph, C.; Reji, M. Node attribute behavior based intrusion detection in sensor network. Int. J. Eng. Technol. 2013, 5, 3692–3698. [Google Scholar]
- Bankovic, Z.; Fraga, D.; Vallejo, J.C.; Moya, J.M. Improving reputation systems for wireless sensor networks using genetic algorithms. In Proceedings of the 13th Annual Conference on Genetic and Evolutionary Computation, Dublin, Ireland, 12–16 July 2011; pp. 1643–1650. [Google Scholar]
- Rizwan, R.; Khan, F.A.; Abbas, H.; Chauhdary, S.H. Anomaly detection in wireless sensor networks using immune-based bioinspired mechanism. Int. J. Distrib. Sens. Netw. 2015, 11, 684952. [Google Scholar] [CrossRef]
- Maleh, Y.; Ezzati, A. Lightweight intrusion detection scheme for wireless sensor networks. IAENG Int. J. Comput. Sci. 2015, 42, 347–354. [Google Scholar]
- Ma, T.; Wang, F.; Cheng, J.; Yu, Y.; Chen, X. A Hybrid Spectral Clustering and Deep Neural Network Ensemble Algorithm for Intrusion Detection in Sensor Networks. Sensors 2016, 16, 1701. [Google Scholar] [CrossRef] [PubMed]
- Bosman, H.H.W.J.; Iacca, G.; Tejada, A.; Wörtche, H.J.; Liotta, A. Ensembles of incremental learners to detect anomalies in ad hoc sensor networks. Ad Hoc Netw. 2015, 35, 14–36. [Google Scholar] [CrossRef]
- Mustard, S. Security of distributed control systems: The concern increases. Comput. Control Eng. J. 2005, 16, 19–25. [Google Scholar] [CrossRef]
- Goh, J.; Adepu, S.; Tan, M.; Lee, Z.S. Anomaly Detection in Cyber Physical Systems Using Recurrent Neural Networks. In Proceedings of the 2017 IEEE 18th International Symposium on High Assurance Systems Engineering (HASE), Singapore, 12–14 January 2017; pp. 140–145. [Google Scholar]
- Miciolino, E.E.; Setola, R.; Bernieri, G.; Panzieri, S.; Pascucci, F.; Polycarpou, M.M. Fault Diagnosis and Network Anomaly Detection in Water Infrastructures. IEEE Des. Test 2017, 34, 44–51. [Google Scholar] [CrossRef]
- Haimi, H.; Mulas, M.; Corona, F.; Marsili-Libelli, S.; Lindell, P.; Heinonen, M.; Vahala, R. Adaptive data-derived anomaly detection in the activated sludge process of a large-scale wastewater treatment plant. Eng. Appl. Artif. Intell. 2016, 52, 65–80. [Google Scholar] [CrossRef]
- Vries, D.; van den Akker, B.; Vonk, E.; de Jong, W.; van Summeren, J. Application of machine learning techniques to predict anomalies in water supply networks. Water Sci. Technol. Water Supply 2016, 16, 1528–1535. [Google Scholar] [CrossRef]
- Adepu, S.; Mathur, A. An investigation into the response of a water treatment system to cyber attacks. In Proceedings of the 2016 IEEE 17th International Symposium on High Assurance Systems Engineering (HASE), Orlando, FL, USA, 7–9 January 2016; pp. 141–148. [Google Scholar]
- Alcaraz, C.; Zeadally, S. Critical infrastructure protection: requirements and challenges for the 21st century. Int. J. Crit. Infrastruct. Prot. 2015, 8, 53–66. [Google Scholar] [CrossRef]
- Weinberger, S. Computer security: Is this the start of cyberwarfare? Nat. News 2011, 474, 142–145. [Google Scholar] [CrossRef] [PubMed]
- Urbina, D.I.; Giraldo, J.A.; Tippenhauer, N.O.; Cárdenas, A.A. Attacking Fieldbus Communications in ICS: Applications to the SWaT Testbed. Proc. Singap. Cyber-Secur. Conf. (SG-CRC) 2016, 14, 75–89. [Google Scholar]
- Taormina, R.; Galelli, S.; Tippenhauer, N.; Ostfeld, A.; Salomons, E. Assessing the effect of cyber-physical attacks on water distribution systems. World Environ. Water Resour. Congr. 2016, 2016, 436–442. [Google Scholar]
- Urbina, D.I.; Giraldo, J.A.; Cardenas, A.A.; Tippenhauer, N.O.; Valente, J.; Faisal, M.; Ruths, J.; Candell, R.; Sandberg, H. Limiting the impact of stealthy attacks on industrial control systems. In Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security, Vienna, Austria, 24–28 October 2016; pp. 1092–1105. [Google Scholar]
- Alsheikh, M.A.; Lin, S.; Niyato, D.; Tan, H.P. Machine learning in wireless sensor networks: Algorithms, strategies, and applications. IEEE Commun. Surv. Tutor. 2014, 16, 1996–2018. [Google Scholar] [CrossRef]
- Beutel, J.; Dyer, M.; Lim, R.; Plessl, C.; Wohrle, M.; Yucel, M.; Thiele, L. Automated wireless sensor network testing. In Proceedings of the INSS’07 Fourth International Conference on Networked Sensing Systems, Braunschweig, Germany, 6–8 June 2007; p. 303. [Google Scholar]
- Steyn, L.P.; Hancke, G.P. A survey of wireless sensor network testbeds. In Proceedings of the AFRICON 2011, Livingstone, Zambia, 13–15 September 2011; pp. 1–6. [Google Scholar]
- Tonneau, A.S.; Mitton, N.; Vandaele, J. A survey on (mobile) wireless sensor network experimentation testbeds. In Proceedings of the 2014 IEEE International Conference on Distributed Computing in Sensor Systems (DCOSS), Marina Del Rey, CA, USA, 26–28 May 2014; pp. 263–268. [Google Scholar]
- Horneber, J.; Hergenröder, A. A survey on testbeds and experimentation environments for wireless sensor networks. IEEE Commun. Surv. Tutor. 2014, 16, 1820–1838. [Google Scholar] [CrossRef]
- Dludla, A.G.; Abu-Mahfouz, A.M.; Kruger, C.P.; Isaac, J.S. Wireless sensor networks testbed: ASNTbed. In Proceedings of the IST-Africa Conference and Exhibition (IST-Africa), Nairobi, Kenya, 29–31 May 2013; pp. 1–10. [Google Scholar]
- Abu-Mahfouz, A.M.; Steyn, L.P.; Isaac, S.J.; Hancke, G.P. Multi-level infrastructure of interconnected testbeds of large-scale wireless sensor networks (MI2T-WSN). In Proceedings of the International Conference on Wireless Networks (ICWN), London, UK, 4–6 July 2012; p. 1. [Google Scholar]
- Levis, P.; Lee, N.; Welsh, M.; Culler, D. TOSSIM: Accurate and scalable simulation of entire TinyOS applications. In Proceedings of the 1st International Conference on Embedded Networked Sensor Systems, Los Angeles, CA, USA, 5–7 November 2003; pp. 126–137. [Google Scholar]
- Abu-Mahfouz, A.M.; Hancke, G.P.; Isaac, S.J. Positioning system in wireless sensor networks using NS-2. Softw. Eng. 2012, 2, 91–100. [Google Scholar]
- Fawcett, T. An introduction to ROC analysis. Pattern Recognit. Lett. 2006, 27, 861–874. [Google Scholar] [CrossRef]
- UCI Center for Machine Learning and Intelligent Systems. UCI Machine Learning Repository; UCI Center for Machine Learning and Intelligent Systems: Irvine, CA, USA, 2006. [Google Scholar]
- Giani, A.; Bitar, E.; Garcia, M.; McQueen, M.; Khargonekar, P.; Poolla, K. Smart grid data integrity attacks: characterizations and countermeasures. In Proceedings of the 2011 IEEE International Conference on Smart Grid Communications (SmartGridComm), Brussels, Belgium, 17–20 October 2011; pp. 232–237. [Google Scholar]
- Osunmakinde, I.O. Towards safety from toxic gases in underground mines using wireless sensor networks and ambient intelligence. Int. J. Distrib. Sens. Netw. 2013, 9, 159273. [Google Scholar] [CrossRef]
- Zhou, X.; Ji, X.; Chen, Y.C.; Li, X.; Xu, W. LESS: Link Estimation with Sparse Sampling in Intertidal WSNs. Sensors 2018, 18, 747. [Google Scholar] [CrossRef] [PubMed]
- Shahid, N.; Naqvi, I.H.; Qaisar, S.B. Characteristics and classification of outlier detection techniques for wireless sensor networks in harsh environments: A survey. Artif. Intell. Rev. 2015, 43, 193–228. [Google Scholar] [CrossRef]
- Zhou, X.; Ji, X.; Wang, B.; Cheng, Y.; Ma, Z.; Choi, F.; Helmuth, B.; Xu, W. Pido: Predictive Delay Optimization for Intertidal Wireless Sensor Networks. Sensors 2018, 18, 1464. [Google Scholar] [CrossRef] [PubMed]
| Parametric | Non-Parametric | |
|---|---|---|
| Prior-Knowledge? | Statistical distribution | Labelled training data |
| Environment? | Static | Dynamic |
| Detection speed? | fast | Moderate/slow |
| Detection generality? | No | Yes |
| Supervised | Semi-Supervised | Unsupervised | |
|---|---|---|---|
| Prior-Knowledge? | Yes | Yes | No |
| Environment? | Static | Dynamic | Dynamic |
| Detection speed? | Fast | Fast/moderate | Moderate/slow |
| Detection generality? | No | Yes | Yes |
| Scheme | Technique | Prior Knowledge | Complexity | Practical Consideration | Accuracy | Data Prediction | Anomaly | Drawback |
|---|---|---|---|---|---|---|---|---|
| Xie et al. [34] | Multivariate | Yes | Low | No | High | No | DOS | Dimensionality/PK |
| Magan-Carrion et al. [35] | Multivariate | Yes | Low | Yes | High | Yes | Data Loss/Modification | Affected by Routing/PK |
| Magan-Carrion et al. [36] | Multivariate | Yes | Low | No | High | Yes | Tampered Data | Traffic Imbalance/PK |
| Xie et al. [41] | kNN | No | Moderate | No | High | No | Generic | No Regression |
| Liu et al. [42] | kNN | Yes | High | No | High | No | Generic | Dimensionality |
| Zhu et al. [43] | kNN | No | High | No | High | No | Misbehaving Nodes | Complexity |
| Martins et al. [45] | SVM | No | High | No | High | No | Generic | Complexity |
| Salem et al. [46] | SVM | Yes | High | No | High | Yes | Data Integrity | Complexity/PK |
| Shilton et al. [47] | SVM | Yes | High | No | High | No | Generic | Complexity/PK |
| Cannady [50] | ANN | No | High | No | N/A | No | DOS | Complexity |
| Bosman et al. [51] | ANN | No | Moderate | Yes | High | No | Generic | Detection Bias |
| Yusuf et al. [52] | ANN | Yes | High | Yes | High | Yes | Data Integrity | Complexity/PK |
| Radhika et al. [53] | GA | Yes | High | No | Average | No | Misbehaving Nodes | Complexity/PK |
| Bankovic et al. [54] | GA | No | High | Yes | High | No | Misbehaving Nodes | Complexity |
| Rizwan et al. [55] | GA | Yes | High | No | High | No | Generic | Complexity/PK |
| Maleh et al. [56] | Hybrid | Yes | Moderate | Yes | High | No | DOS | PK |
| Ma et al. [57] | Hybrid | Yes | High | No | High | No | Generic | Complexity/PK |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Ramotsoela, D.; Abu-Mahfouz, A.; Hancke, G. A Survey of Anomaly Detection in Industrial Wireless Sensor Networks with Critical Water System Infrastructure as a Case Study. Sensors 2018, 18, 2491. https://doi.org/10.3390/s18082491
Ramotsoela D, Abu-Mahfouz A, Hancke G. A Survey of Anomaly Detection in Industrial Wireless Sensor Networks with Critical Water System Infrastructure as a Case Study. Sensors. 2018; 18(8):2491. https://doi.org/10.3390/s18082491
Chicago/Turabian StyleRamotsoela, Daniel, Adnan Abu-Mahfouz, and Gerhard Hancke. 2018. "A Survey of Anomaly Detection in Industrial Wireless Sensor Networks with Critical Water System Infrastructure as a Case Study" Sensors 18, no. 8: 2491. https://doi.org/10.3390/s18082491
APA StyleRamotsoela, D., Abu-Mahfouz, A., & Hancke, G. (2018). A Survey of Anomaly Detection in Industrial Wireless Sensor Networks with Critical Water System Infrastructure as a Case Study. Sensors, 18(8), 2491. https://doi.org/10.3390/s18082491







