1. Introduction
Fifth generation (5G) wireless networks are expected to support higher spectral efficiency, lower end-to-end latency, and more connection nodes [
1]. In accordance with this trend, many promising techniques are being considered [
2]. Among them, a non-orthogonal multiple access (NOMA) technique has been proposed to improve the spectral efficiency of the 5G network [
3]. The basic idea of the NOMA technique is to serve multiple users at the same time-frequency-space resource block via power domain or code domain multiplexing [
4]. It has been known that the NOMA technique increases the spectrum efficiency and efficiently accommodates a massive number of nodes in cellular networks [
5,
6].
As noted before, the NOMA techniques are, in general, classified into two categories: code-domain NOMA and power-domain NOMA [
7]. With the code-domain NOMA techniques, a codeword is allocated to each user and a near optimal multi-user detection algorithm, such as a message passing algorithm, is used at the receiver. The code-domain NOMA techniques include trellis-coded multiple access (TCMA), interleave-division multiple access (IDMA), low-density signature (LDS) sequence-based code division multiple access (CDMA), sparse-code multiple access (SCMA), pattern-division multiple access (PDMA), multi-user shared access (MUSA), etc. [
8]. On the other hand, with the power domain NOMA techniques, multiple users are served within a given time-frequency-space resource block by using superposition coding (SC) at the transmitter and successive interference cancellation (SIC) at the receivers, respectively, which has recently been proposed in 3GPP LTE [
3].
Multi-user superposition transmission (MUST) is a special case of the NOMA techniques, which has been studied in 3GPP LTE standards [
9]. Various NOMA techniques have been proposed and studied, focusing on multi-user non-orthogonal transmission schemes, receiver designs, and related signaling strategies in [
9]. The MUST techniques are divided into three categories according to adaptive power control and bit-labeling at the transmitter side as shown in
Table 1. The adaptive power ratio on each component constellation is utilized in MUST categories 1 and 2, and Gray-mapped composite constellation is adopted in MUST categories 2 and 3. The MUST techniques typically assume asymmetric downlink scenarios consisting of active cell-edge and cell-center users. At the receiver side, the cell-center user with higher received signal power decodes a super-imposed signal with SIC, while the cell-edge user with lower received signal power decodes the super-imposed signal by treating the interference signal as noise. To implement SIC at the cell-center user, codeword-level (channel coding block) SIC results in better performance than symbol-level SIC, but the signaling overhead and implementation complexity of the codeword-level SIC is much higher that of the symbol-level SIC [
10,
11]. Thus, the codeword-level SIC may not be suitable in the cellular downlink, especially when the low-cost and low-power user terminals/devices are considered.
Recently, several receiver designs of the NOMA techniques, including codeword-level SIC and symbol-level SIC, have been compared with each other. In particular, a log-likelihood ratio (LLR)-based low-complexity receiver design was proposed [
12]. Although the LLR-based receiver design does not include the codeword-level SIC operation which accompanies high implementation complexity, it can still achieve similar performance to the codeword-level SIC receiver as well as the ideal SIC receiver. However, the performance of the proposed technique was evaluated only through link-level simulations. In addition, another low-complexity MUST technique was proposed in [
13], where a NOMA transmitter sends signals to a single cell-center user over multiple (frequency) resource blocks, each of which is also occupied by a cell-edge user. Thus, the cell-center user can obtain the frequency diversity, and we call this scheme
diversity-controlled MUST technique in this paper. However, in [
13], the rate outage performance was mathematically analyzed when there exist only two cell-edge users and each user is equipped with a single receive antenna.
In this paper, we extend the diversity-controlled MUST technique to the case where multiple cell-edge users are multiplexed with a single cell-center user and each user is equipped with multiple antennas. Henceforth, we define the user with a higher signal-to-noise ratio (SNR) as MUST-based user equipment (UE) and the user with a lower SNR as MUST-enhanced UE since the received SNR depends on not only the location of users but also the allocated power in the diversity-controlled MUST technique. In general, cell-center users become the MUST-based UEs and cell-edge users become the MUST-enhanced UEs. In particular, we derive the closed-form expressions on the bit error rate (BER) of both MUST-based UEs and MUST-enhanced UEs in Rayleigh fading channels for a given power allocation ratio. Based on the mathematical analysis, we also optimize the power allocation ratio on the component constellation to minimize the power consumption at the NOMA transmitter for given BER requirements. The mathematical analysis is validated via link-level simulations.
The remainder of the paper is organized as follows. In
Section 2, the system model is described; in
Section 3, we explain the overall procedures of both the transmitter and receiver with the proposed diversity-controlled MUST technique in detail and derive the BER of the proposed technique; in
Section 4, we formulate an optimization problem of the power allocation ratio to minimize the power consumption at the NOMA transmitter; simulation results are shown in
Section 5; finally, conclusions are drawn in
Section 6.
2. System Model
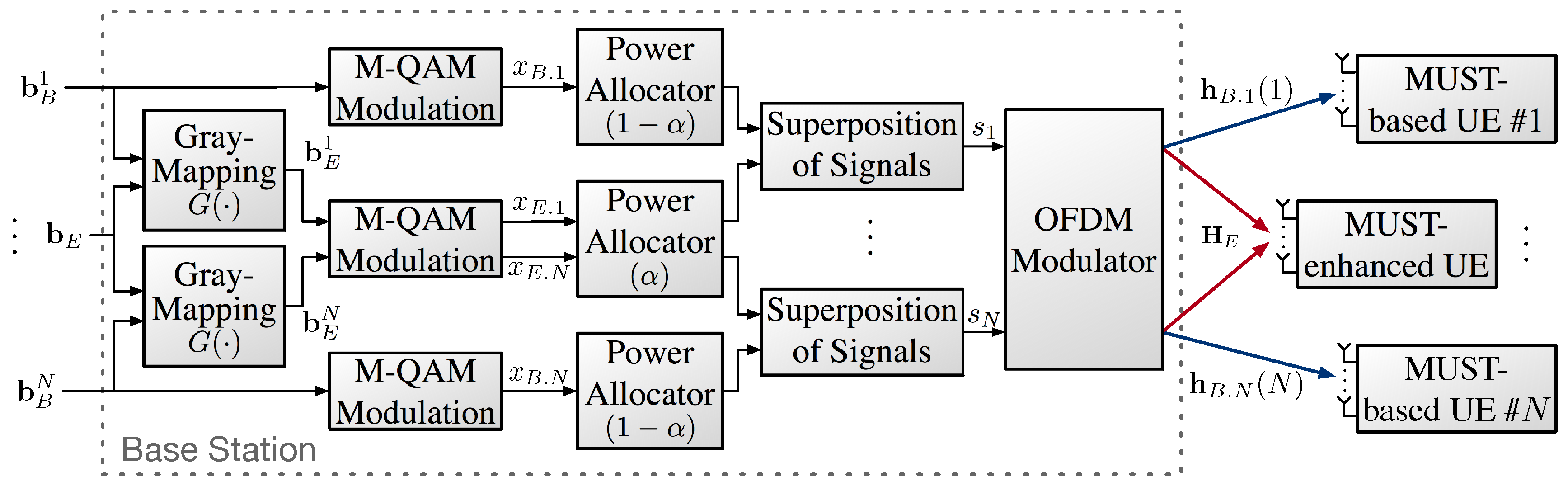
We consider a downlink cellular network consisting of a single base station (BS), a single MUST-enhanced UE, and N MUST-based UEs. We assume that the BS is equipped with a single transmit antenna but each user is equipped with antennas. Hence, the wireless channel from the BS to each user is modeled as a single-input multiple-output (SIMO) channel. We consider that the orthogonal frequency division multiple access (OFDMA) and the system bandwidth are assumed to be equally divided into N sub-carriers for simplicity.
At the BS, a composite modulation symbol is generated by superposing two signals of an MUST-based UE and an MUST-enhanced UE. We adopt the MUST category 2 when generating the composite symbol, and thus the power ratio between two component signals can be adaptively adjusted and Gray-mapping is used for bit-labeling. An adaptive power allocation coefficient,
, is introduced to determine powers of the two signals. Hence, the
value needs to be carefully adjusted, depending on the channel conditions of users. Each superposed signal is transmitted to both the MUST-based UE and the MUST-enhanced UE over a certain sub-band.
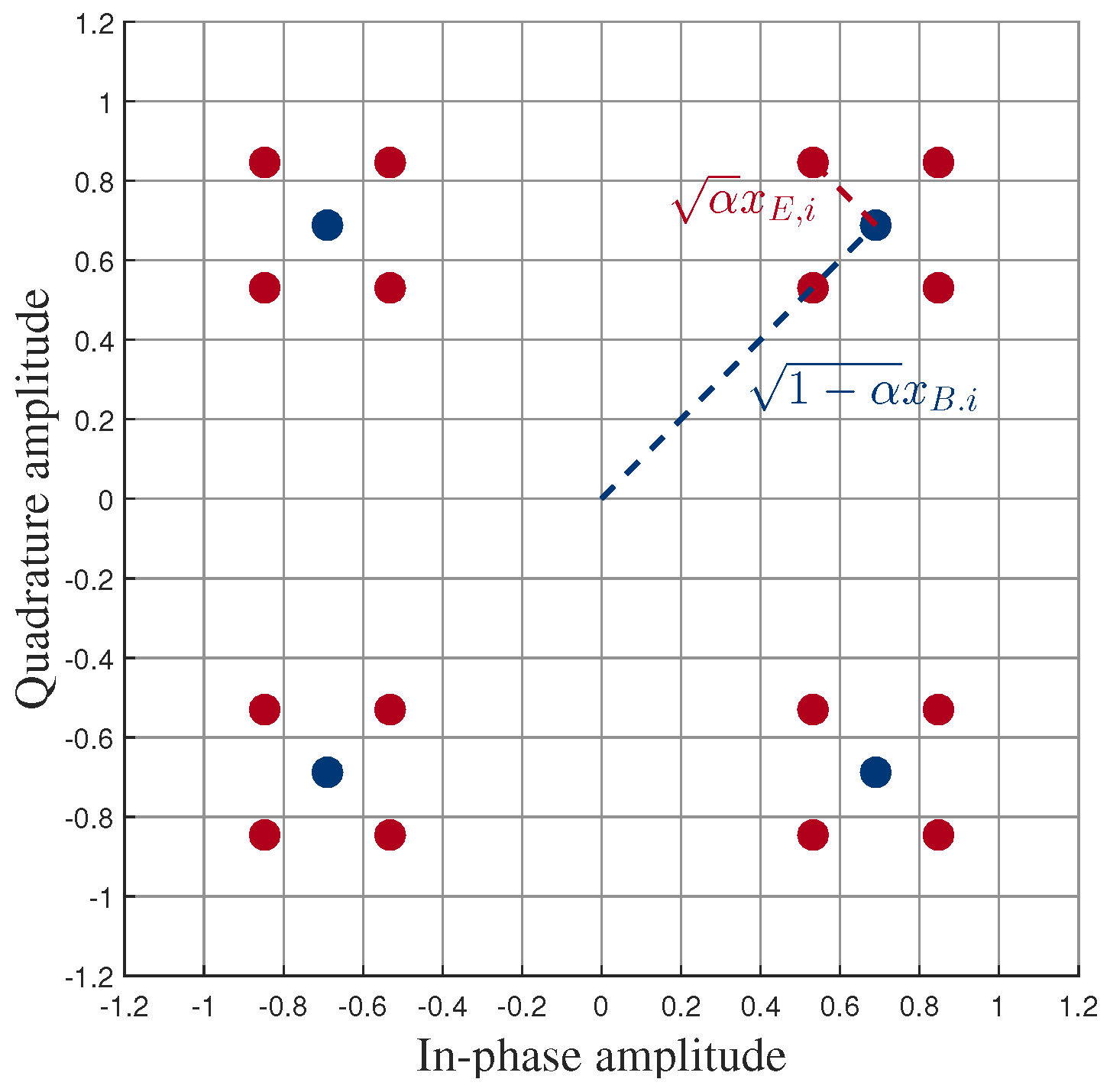
Figure 1 shows an example of a composite constellation of the MUST technique with quadrature phase shift keying (QPSK) modulation for both users. The blue dots represent QPSK constellation points of the MUST-based UE whose power is equal to
and the red dots around each blue dot represent the composite constellation points, consisting of QPSK constellations of both MUST-based and MUST-enhanced UEs, whose power is equal to 1. As shown in
Figure 1,
indicates the power portion that is allocated to the MUST-enhanced UE. As noted before, the signal of the MUST-enhanced UE is transmitted over multiple frequency bands (sub-carriers), while the signal of the MUST-based UE is sent over a single frequency band (sub-carrier) with the diversity-controlled MUST technique [
13].
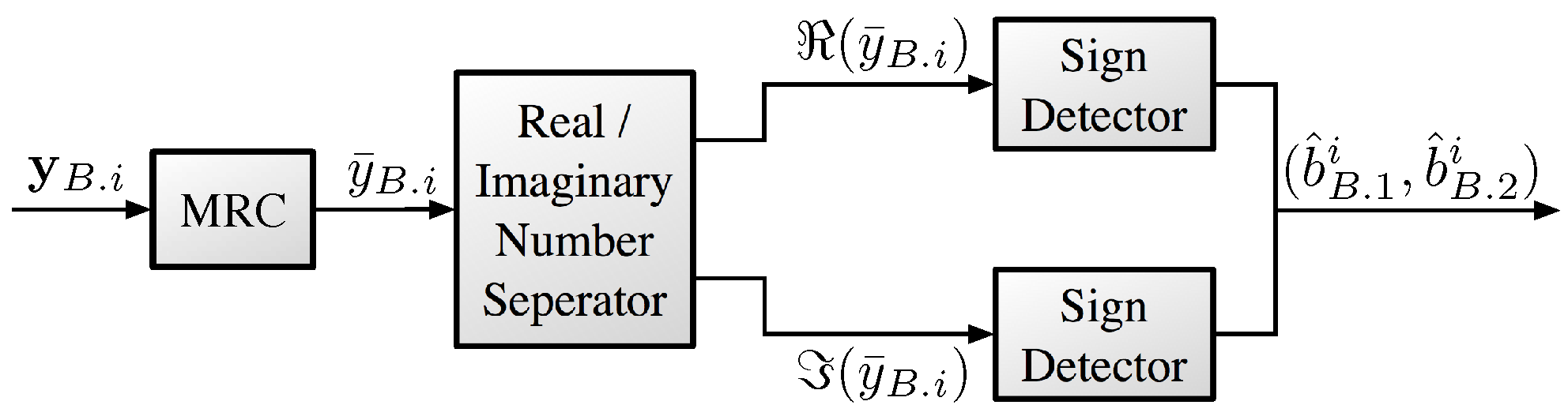
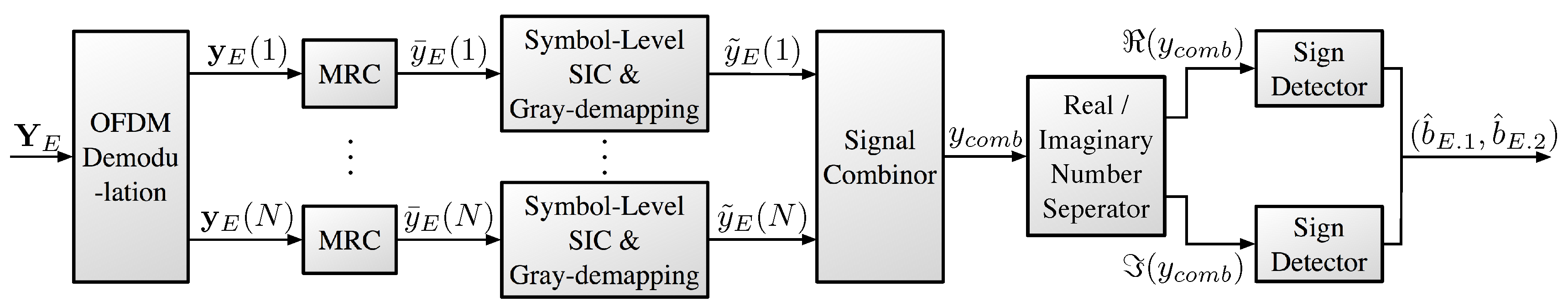
At the MUST-based UE, the received signal is decoded by treating the signal of the MUST-enhanced UE as noise. On the other hand, at the MUST-enhanced UE, the received signal is obtained after the symbol-level SIC operation for each frequency band. Then, the obtained signals over multiple frequency bands (sub-carriers) are combined to obtain the frequency diversity gain.
4. Optimal for Minimizing Power Consumption
In Equations (
8) and (
22), the power allocated to each user’s signal determines its point-to-point BER performance. Of cause, using a lot of power may guarantee the BER requirements of the users. However, the available energy of the BS is limited in general, and thus it is necessary to use the power efficiently. This can be accomplished by transmitting the signal with the minimum power at the BS while satisfying the required BER performance of each user. For given BER requirements for users, there exists the optimal power allocation coefficient,
, to minimize the required energy,
, at the BS. In general, the BER performance of the MUST-enhanced UE becomes improved as
increases for a given
, while that of the MUST-based UE becomes improved as
decreases for a given
. Thus, there exists a trade-off between the BER performances of the MUST-based UE and the MUST-enhanced UE according to
.
In this section, we formulate the optimization problem to minimize the power consumption at the BS for given BER requirements for users.
is defined as the required power at the BS to satisfy the BER requirement of the MUST-based UE
for a given
. Similarly,
is defined as the required power at the BS to satisfy the BER requirement of the MUST-enhanced UE
for a given
. Then, the optimal power allocation coefficient to minimize the power consumption of the BS is given as:
The optimization problem shown in Equation (
23) can be solved easily as follows. For given BER requirements
and
,
is a monotonically increasing function
, while
is a monotonically decreasing function of
since
denotes the power portion allocated to the MUST-enhanced UE. Thus, the optimal power allocation coefficient
can be obtained by solving the following equation:
5. Simulation Results
In this section, we show the performance of the proposed diversity-controlled MUST technique. In particular, we evaluate the average BER performances of both the MUST-based UE and the MUST-enhanced UE. We show the minimum required power at the BS for satisfying the BER requirement according to . In all link-level simulations, we utilize QPSK modulation and Rayleigh fading channels.
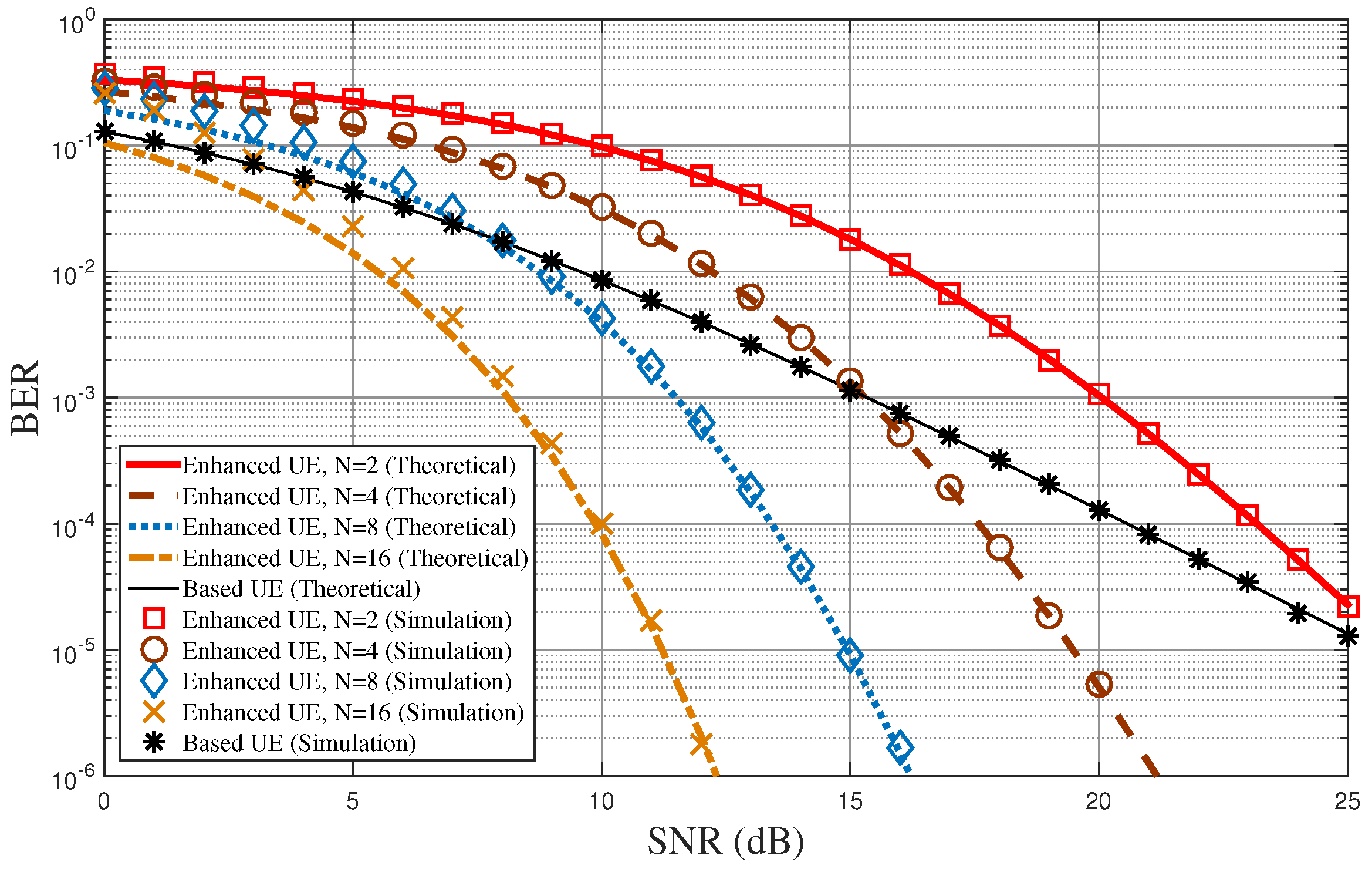
Figure 5 shows the BER performance of the proposed diversity-controlled MUST technique for varying SNR values when
,
, and
. In the figure, lines represent the analytical results obtained from Equations (
8) and (
22), while symbols represent link-level simulation results. The mathematical analysis derived in this paper matches well with the computer simulations over all SNR values. As
N increases, the BER performance of the MUST-enhanced UE becomes improved due to the frequency diversity. Note that the lower bound of the average BER of the MUST-enhanced UE in Equation (
22) is almost the same as the computer simulation especially when the SNR is high. The BER performance of the MUST-based UE is better than that of the MUST-enhanced UE in low SNR values due to the larger power allocation to the MST-based UE. On the other hand, it becomes worse than the BER of the MUST-enhanced UE for high SNR values due to the diversity gain of the MUST-enhanced UE.
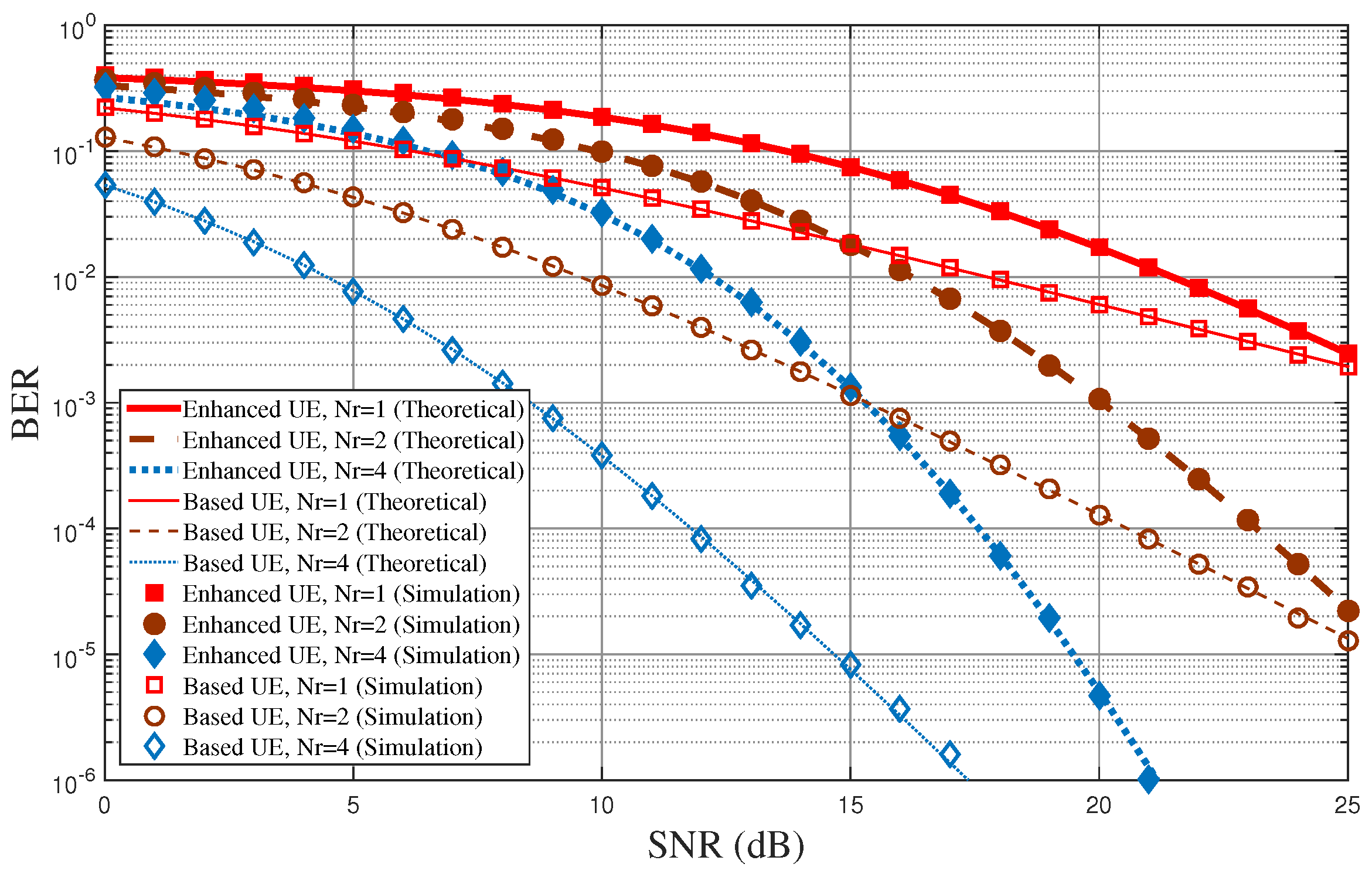
Figure 6 shows the BER performance of the proposed diversity-controlled MUST technique for varying SNR values when
,
, and
.
Figure 5 shows the BER performance according to the number of frequencies used for the MUST-enhanced UE for a given number of receive antennas at UEs, but
Figure 6 shows BER performance according to the number of receive antennas at UEs for a given number of frequencies used for the MUST-enhanced UE. The performance tendencies in both
Figure 5 and
Figure 6 are quite similar. The diversity order of the MUST-based UE is approximately equal to
, while that of the MUST-enhanced UE is approximately equal to
.
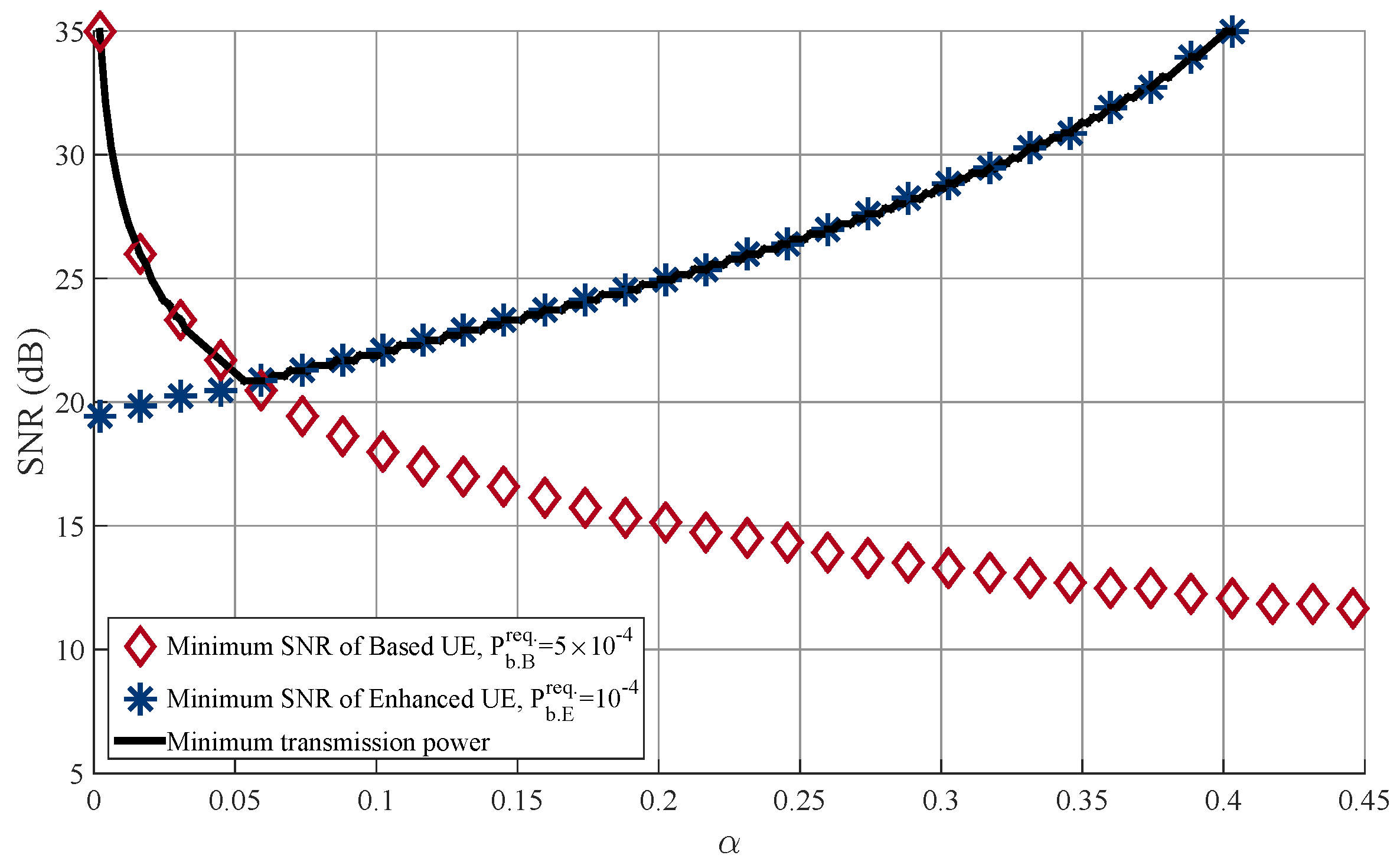
Figure 7 shows the transmit SNR at the BS over varying
where the transmit power of the BS is adapted to satisfy the BER requirements when
and
. We assume that
and
. As expected, the required SNR for the MUST-based UE decreases as
increases, while that for the MUST-enhanced UE increases as
increases. In this figure, the optimal
is equal to
and the minimum required SNR is equal to 21 dB.