A QoS Based Adaptive Backoff Scheme for Vehicular Ad Hoc Networks
Abstract
1. Introduction
2. System Model
2.1. Estimating the Number of Contention Nodes
2.2. Transmission Process
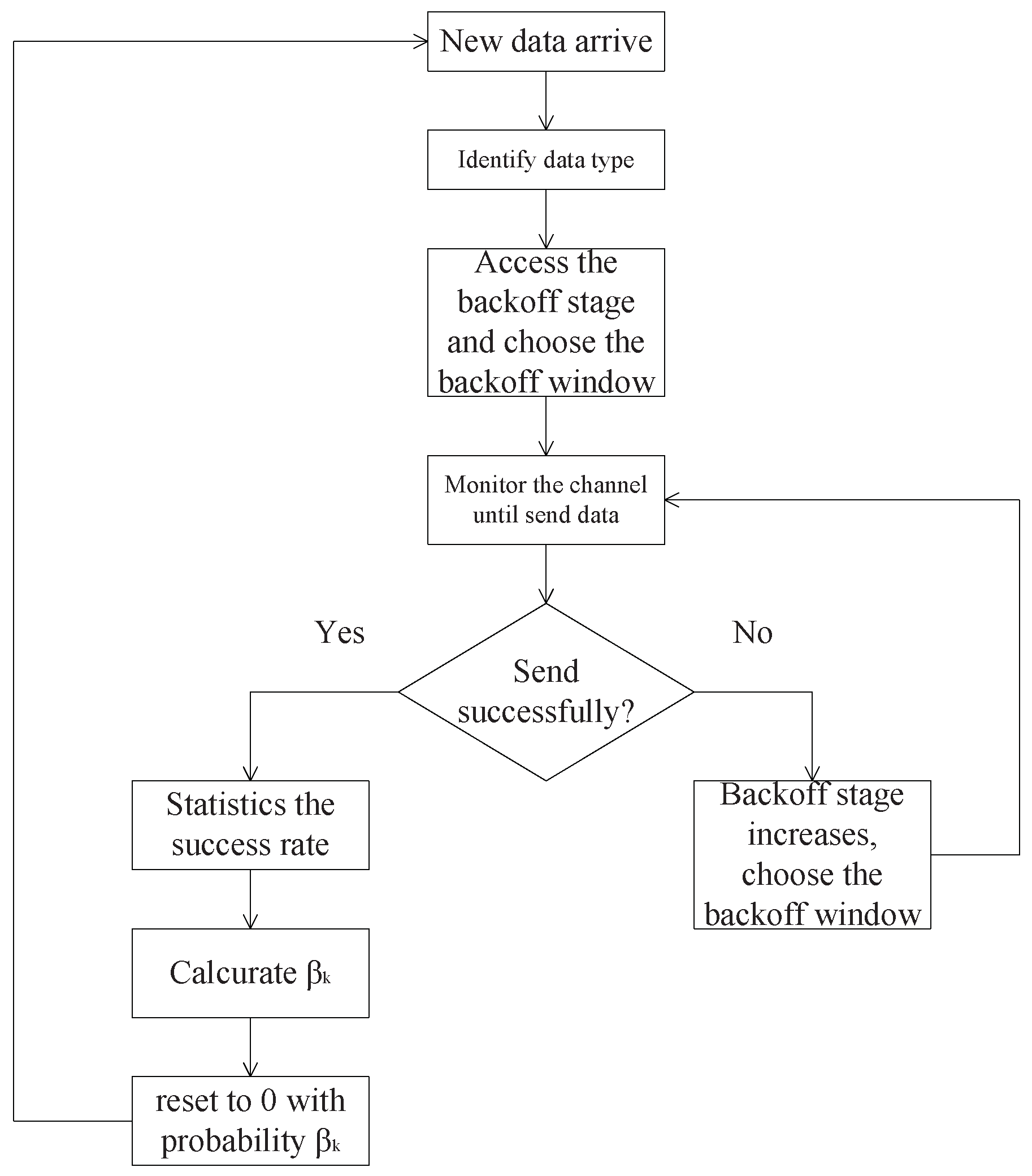
3. Backoff Algorithm
- The vehicle node identifies the type of data k;
- The backoff process of the current data starts with the backoff series of the previous backoff process of similar data. Assuming that after similar data are transmitted successfully, the backoff stage sets to i, then the initialized contention window of the new data is ;
- The node monitors the channel and does the backoff. When the backoff window decreases to 0, the node sends the data.
- If a channel collision occurs at the backoff stage , the backoff stage adds 1. If a channel collision occurs at the backoff stage , the backoff stage remains m. The node chooses the backoff window again and does the backoff;
- If the data are transmitted successfully, the vehicle node calculates according to the previous success rate and resets the backoff stage to 0 with a probability of . (Calculating the is introduced in the next section).
4. Modeling and Performance Analysis
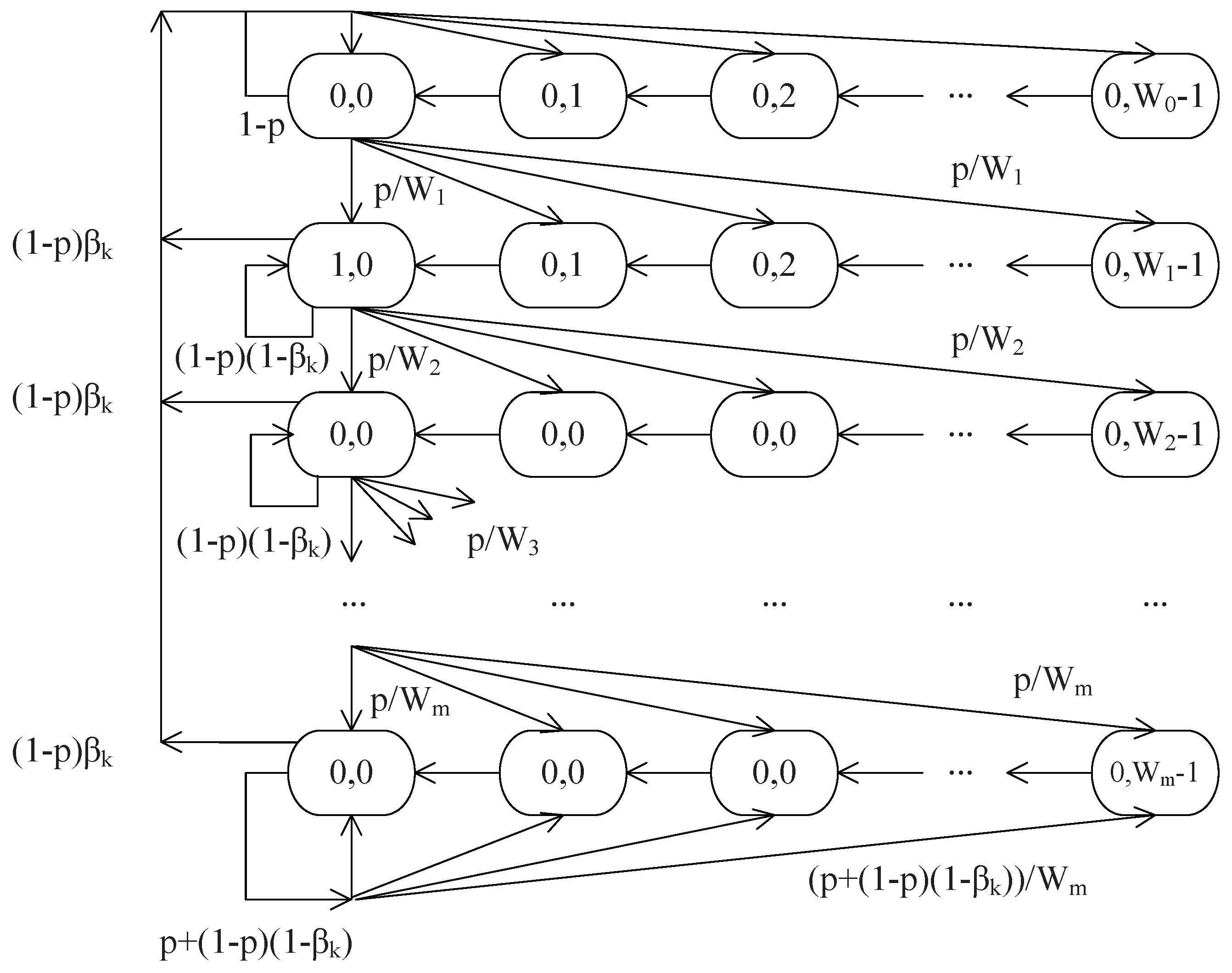
4.1. State Transition Probability
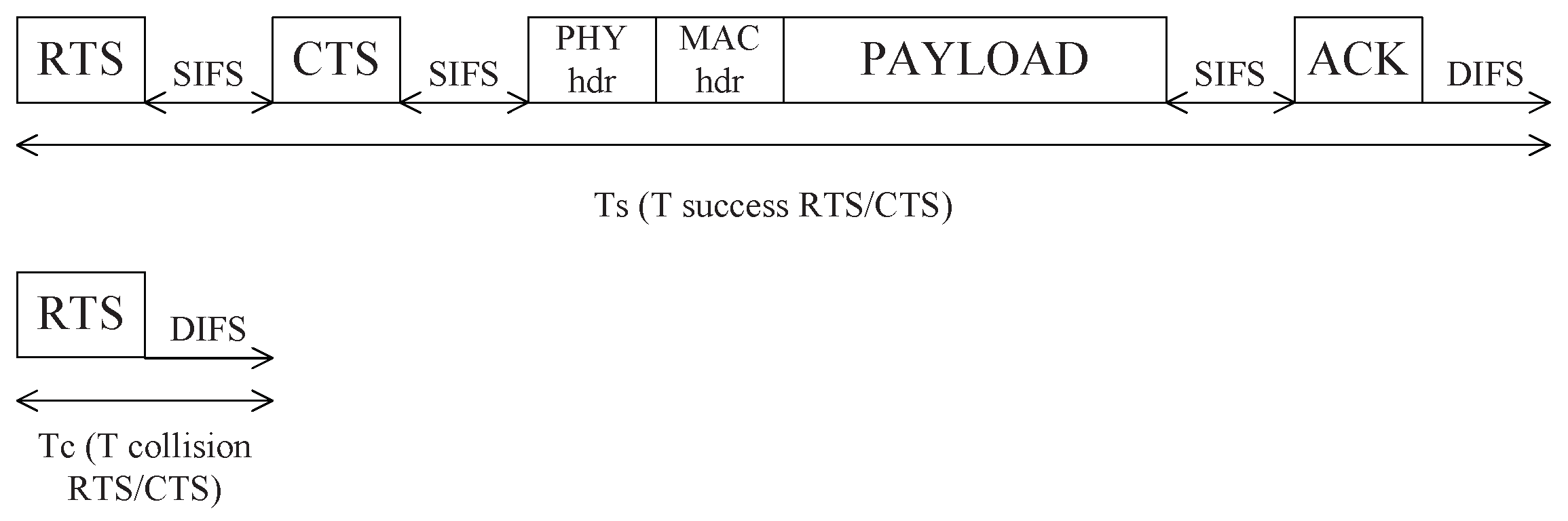
4.2. Throughput and Delay
4.3. Delay Optimization
- The searching solution at current time;
- The searching speed at current time
- ;
- The best solution at current time
- ;
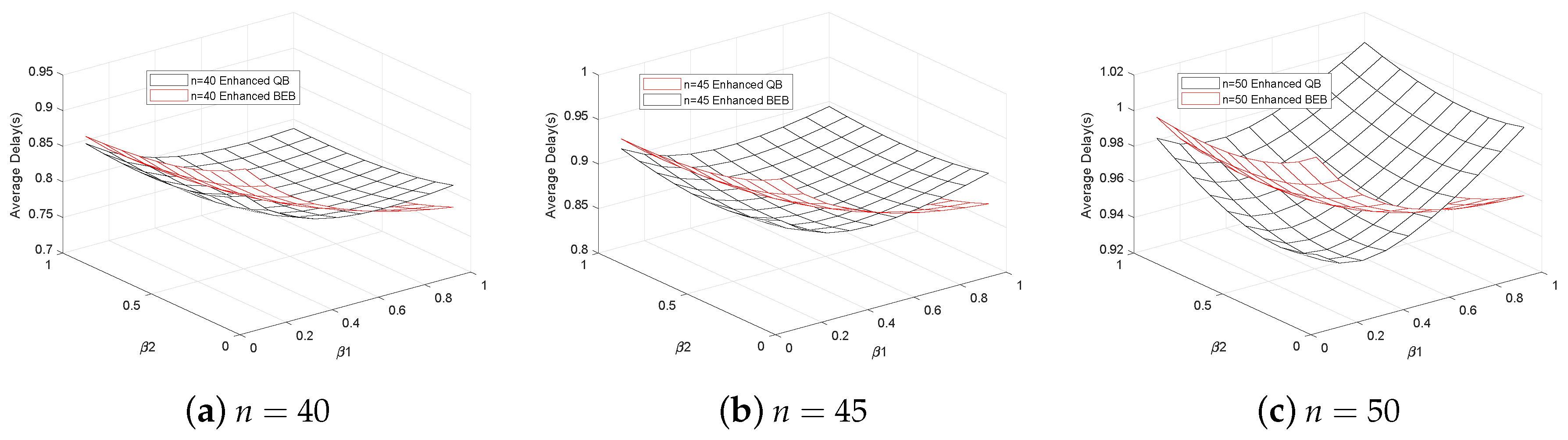
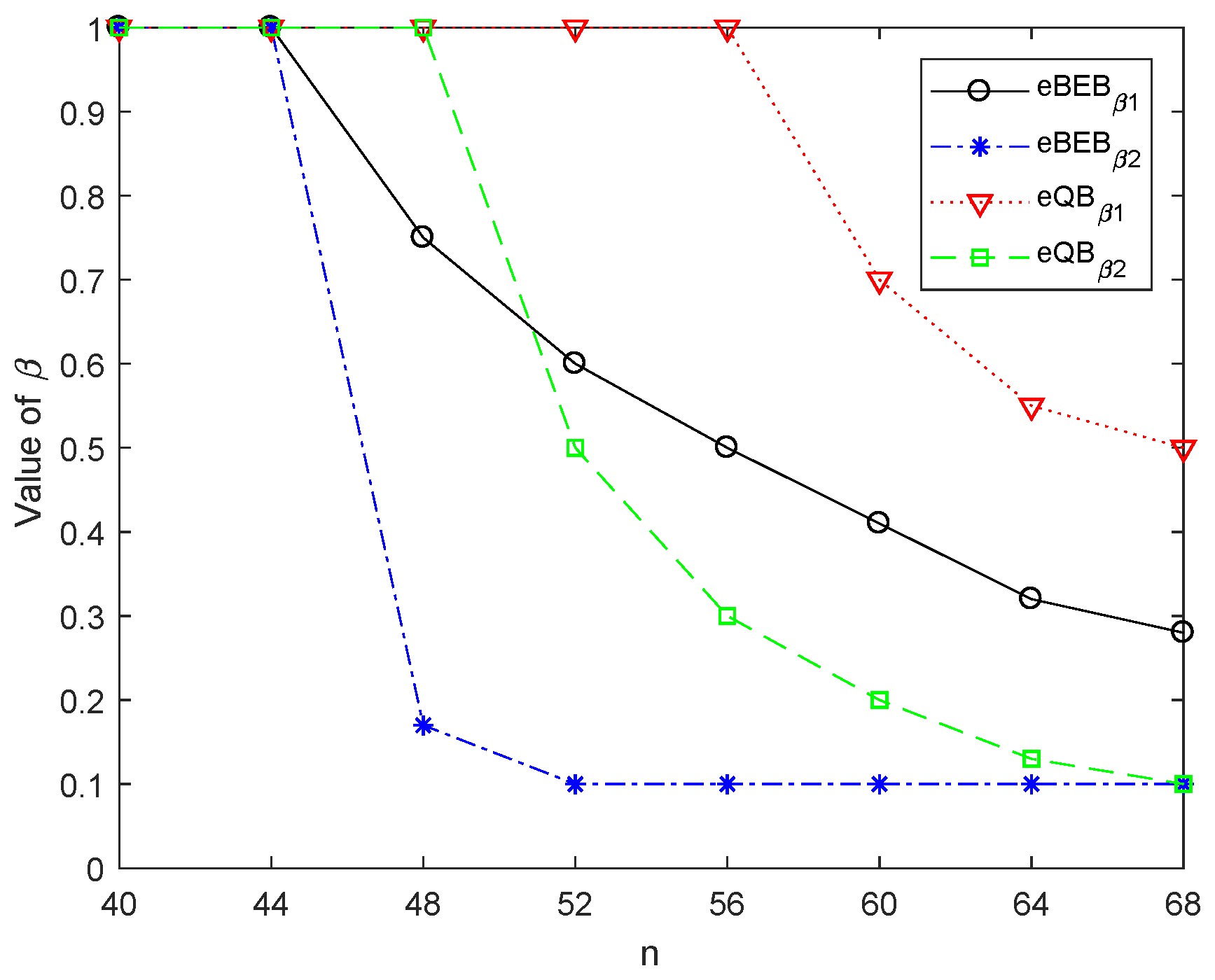
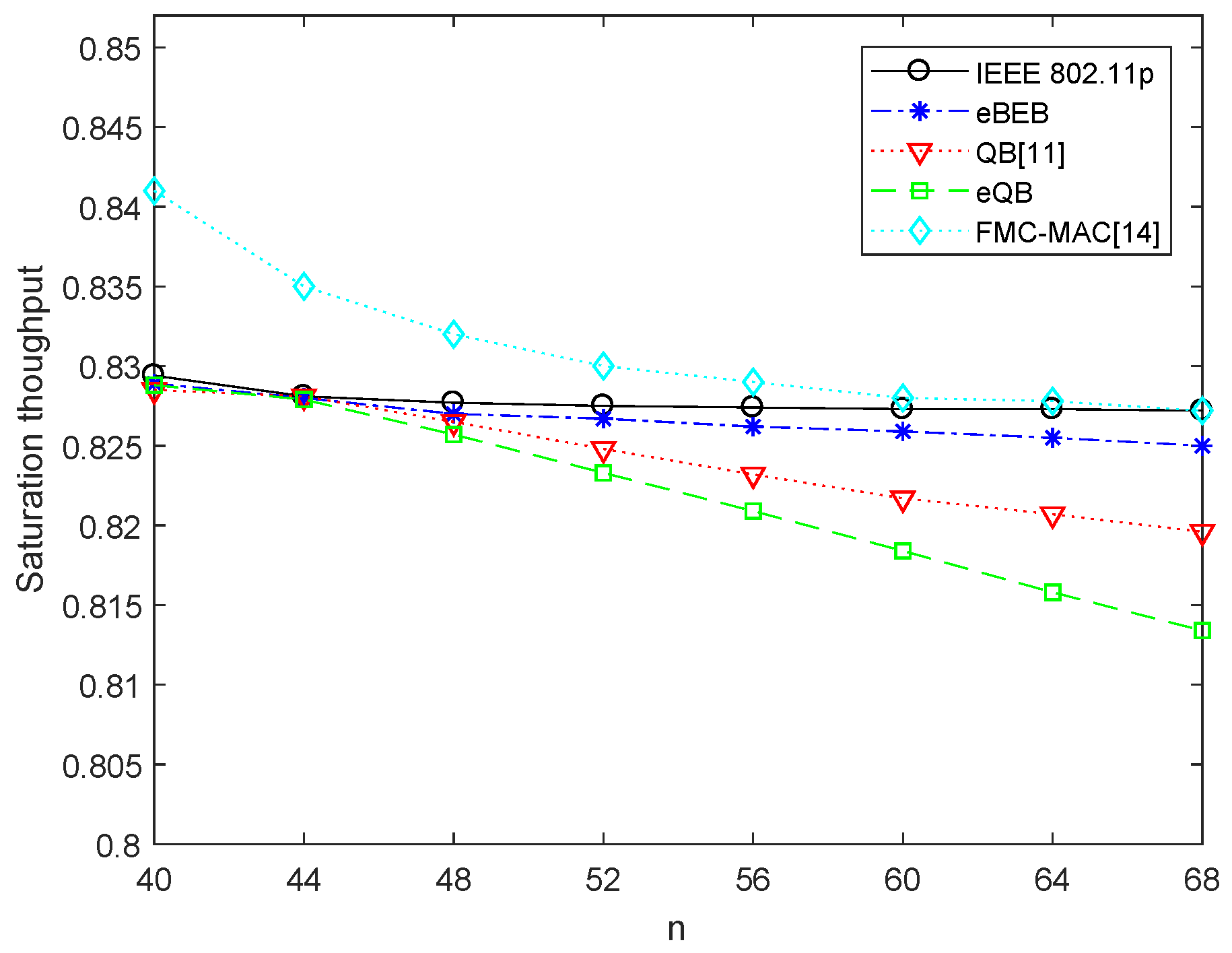
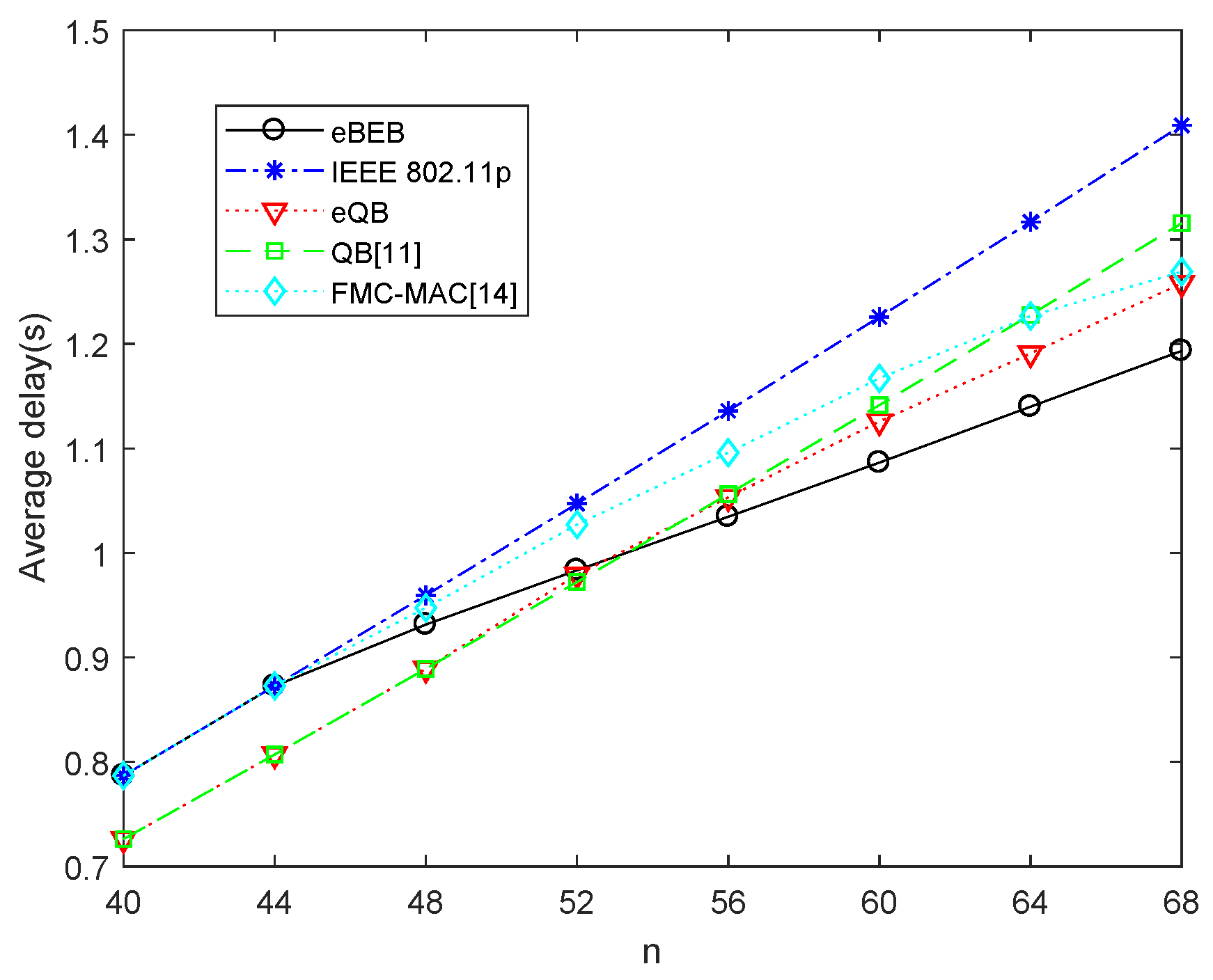
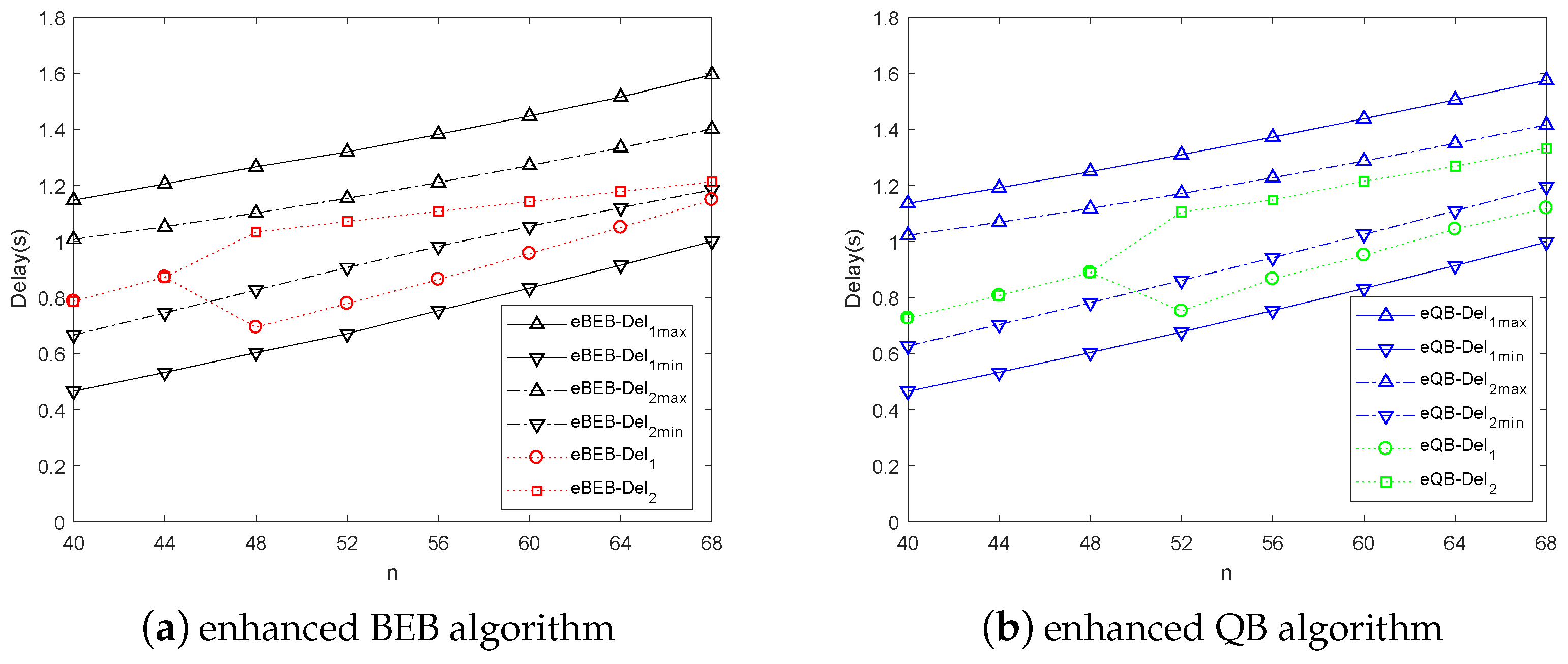
5. Simulation Results and Analysis
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Mehta, K.; Malik, L.L.G.; Bajaj, P. VANET: Challenges, Issues and Solutions. In Proceedings of the 2013 6th International Conference on Emerging Trends in Engineering and Technology (ICETET), Nagpur, India, 16–18 December 2013; pp. 78–79. [Google Scholar]
- IEEE Std 802.11-2007 (Revision of IEEE Std. 802.11-1999). Standard for Information Technology-Tele-Communications and Information Exchange between Systems-Local and Metropolitan Area Networks-Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications; IEEE: New York, NY, USA, 2007; pp. 1–1184. [Google Scholar]
- IEEE Std 802.11p-2010. Standard for Information Technology-Tele-Communications and Information Exchange between Systems-Local and Metropolitan Area Networks-Specific Requirements Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications Amendment 6: Wireless Access in Vehicular Environments; IEEE: New York, NY, USA, 2010; pp. 1–51. [Google Scholar]
- Xiao, Y. QoS guarantee and provisioning at the contention-based wireless MAC layer in the IEEE802.11e wireless LANs. IEEE Wirel. Commun. 2006, 13, 14–21. [Google Scholar] [CrossRef]
- IEEE Std 802.11-1997. Part 11: Wireless LAN Medium Access Control (MAC) and Physical Layer (PHY) Specifications [s]. 1997. Available online: www.ieee.org (accessed on 30 November 2018).
- Giuseppe, B. Performance analysis of the IEEE 802.11 distributed coordination function. IEEE J. Sel. Areas Commun. 2000, 18, 535–547. [Google Scholar]
- Ye, S.R.; Tseng, Y.C. A multichain backoff mechanism for IEEE 802.11 WLAN. IEEE Trans. Veh. Technol. 2006, 55, 1613–1620. [Google Scholar] [CrossRef]
- Zhao, Q.L.; Tsang, D.H.K.; Sakurai, T. Modeling nonsaturated IEEE 802.11 DCF networks utilizing an arbitrary buffer size. IEEE Trans. Mob. Comput. 2010, 10, 1–15. [Google Scholar] [CrossRef]
- Li, R.F.; Luo, J.; Li, R.F. Backoff algorithm in MAC layer for wireless multimedia sensor networks. J. Commun. 2010, 31, 107–116. [Google Scholar]
- Bansal, G.; Kenney, J.B.; Rohrs, C.E. LIMERIC: A Linear Adaptive Message Rate Algorithm For DSRC Congestion Control. IEEE Trans. Veh. Technol. 2013, 62, 4182–4197. [Google Scholar] [CrossRef]
- Sun, X.; Dai, L. Backoff Design for IEEE 802.11 DCF Networks: Fundamental Tradeoff and Design Criterion. IEEE/ACM Trans. Netw. 2015, 23, 300–316. [Google Scholar] [CrossRef]
- Sun, X.; Dai, L. Performance Optimization of CSMA Networks With a Finite Retry Limit. IEEE Trans. Wirel. Commun. 2016, 15, 5947–5962. [Google Scholar] [CrossRef]
- Sun, X.; Dai, L. Fairness-Constrained Maximum Sum Rate of Multi-rate CSMA Networks. IEEE Trans. Wirel. Commun. 2017, 16, 1741–1754. [Google Scholar] [CrossRef]
- Yao, Y.; Zhang, K.; Zhou, X. A Flexible Multi-Channel Coordination MAC Protocol for Vehicular Ad Hoc Networks. IEEE Commun. Lett. 2017, 21, 1305–1308. [Google Scholar] [CrossRef]
| Algorithm Process |
|---|
| 1. Initialize the search step , parameters , weight value w and accuracy requirement ; |
| 2. Let , , calculate . In the same way, calculate other ; |
| 3. Set , perform the first search, , , , ; |
| 4. Do while ; |
| 5. ; |
| 6. Compute the initial optimal solution , ; |
| 7. Computer the search step, ; |
| 8. Compute the parameter ; |
| 9. If the constraint conditions cannot be satisfied, go back to step 7, or else go on; |
| 10. End do |
| 11. Return and |
| Parameter | City |
|---|---|
| Number of lanes | 4 |
| Length of road | 1 km |
| number of directions | 2 |
| Width of lanes | 5 m |
| Mean speed | 40 km/h |
| Variance of speed | 10 km/h |
| GPS time interval | 0.1 s |
| Communication range | 200 m |
| Number of vehicles (N) | 0∼68 |
| Parameter | Value |
|---|---|
| DIFS (s) | 128 |
| SIFS (s) | 28 |
| MAC header (bits) | 272 |
| PHY header (bits) | 128 |
| ACK | 112 + PHY header |
| Propagation delay (s) | 1 |
| Timeslot length (s) | 20 |
| packet size E(P) (bytes) | 1024 |
| Channel data rate (Mbit·s) | 1 |
| 6∼96 |
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, T.; Zhu, Q. A QoS Based Adaptive Backoff Scheme for Vehicular Ad Hoc Networks. Sensors 2018, 18, 4421. https://doi.org/10.3390/s18124421
Zhang T, Zhu Q. A QoS Based Adaptive Backoff Scheme for Vehicular Ad Hoc Networks. Sensors. 2018; 18(12):4421. https://doi.org/10.3390/s18124421
Chicago/Turabian StyleZhang, Tianjiao, and Qi Zhu. 2018. "A QoS Based Adaptive Backoff Scheme for Vehicular Ad Hoc Networks" Sensors 18, no. 12: 4421. https://doi.org/10.3390/s18124421
APA StyleZhang, T., & Zhu, Q. (2018). A QoS Based Adaptive Backoff Scheme for Vehicular Ad Hoc Networks. Sensors, 18(12), 4421. https://doi.org/10.3390/s18124421




