EPPRD: An Efficient Privacy-Preserving Power Requirement and Distribution Aggregation Scheme for a Smart Grid
Abstract
1. Introduction
- It may be necessary to adjust a user’s power distribution in the next time slot to flatten demand peaks based on the power consumption in the current time slot, because power changes dynamically over time. During peak demand, the Control Center (CC) reduces the total distribution to users to adjust power consumption from peak time to non-peak time in the next time slot. Therefore, our demand message is divided into two parts: an individual user requirement based on RSA encryption for the next time slot and the total user consumption based on Paillier encryption in the current time slot, which is one significant reference of power distribution at the next time slot for the CC.
- To reduce the volume of transmitted traffic, we locate a regional concentrator in the BAN for regional storage, aggregation, transmission, and distribution. After the BAN receives the distributed regional power ratio from the CC, it immediately distributes individual power to the users according to the stored requirement and the distributed regional power ratio.
- To ensure message confidentiality and integrity, we employ the Public–Private, Paillier homomorphic cryptography and Hash-based Message Authentication Code authentication in the HAN Smart Meter (HSM), BAN Gateway (BGW), and NAN Gateway (NGW). This scheme can resist various attacks, such as replay attacks, man-in-the-middle attacks, eavesdropping attacks, and so forth. This scheme offers stringent security and reliability guarantees.
- The remainder of the paper is organized as follows. In Section 2, we introduce related work with EPPRD. In Section 3, we introduce an EPPRD communication model and security goal. In Section 4, we introduce the basic preliminaries such as Computational Diffie-Hellman (CDH) Problem and Paillier cryptosystem. In Section 5 we propose the EPPRD scheme and security analysis and proof. After that we present our performance analysis and discussion in Section 6 and Section 7, respectively. Finally, we draw conclusions in Section 8.
2. Related Work
- Our scheme focuses on preserving the privacy of individual power requirement and distribution instead of on individual power billing. We adopt two different encryption modes for individual power requirement and distribution, while [21] employs only Paillier homomorphic encryption for its power requirement.
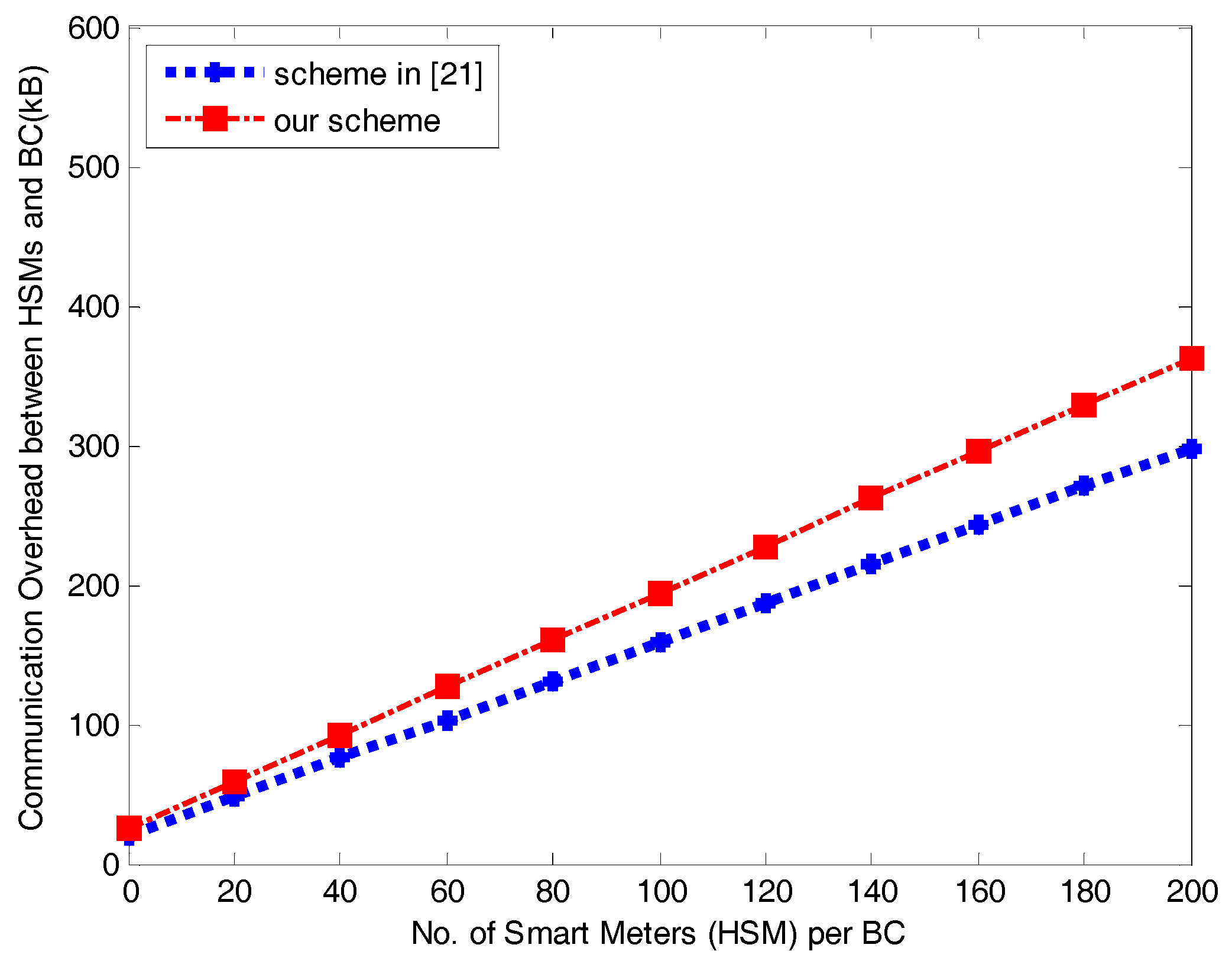
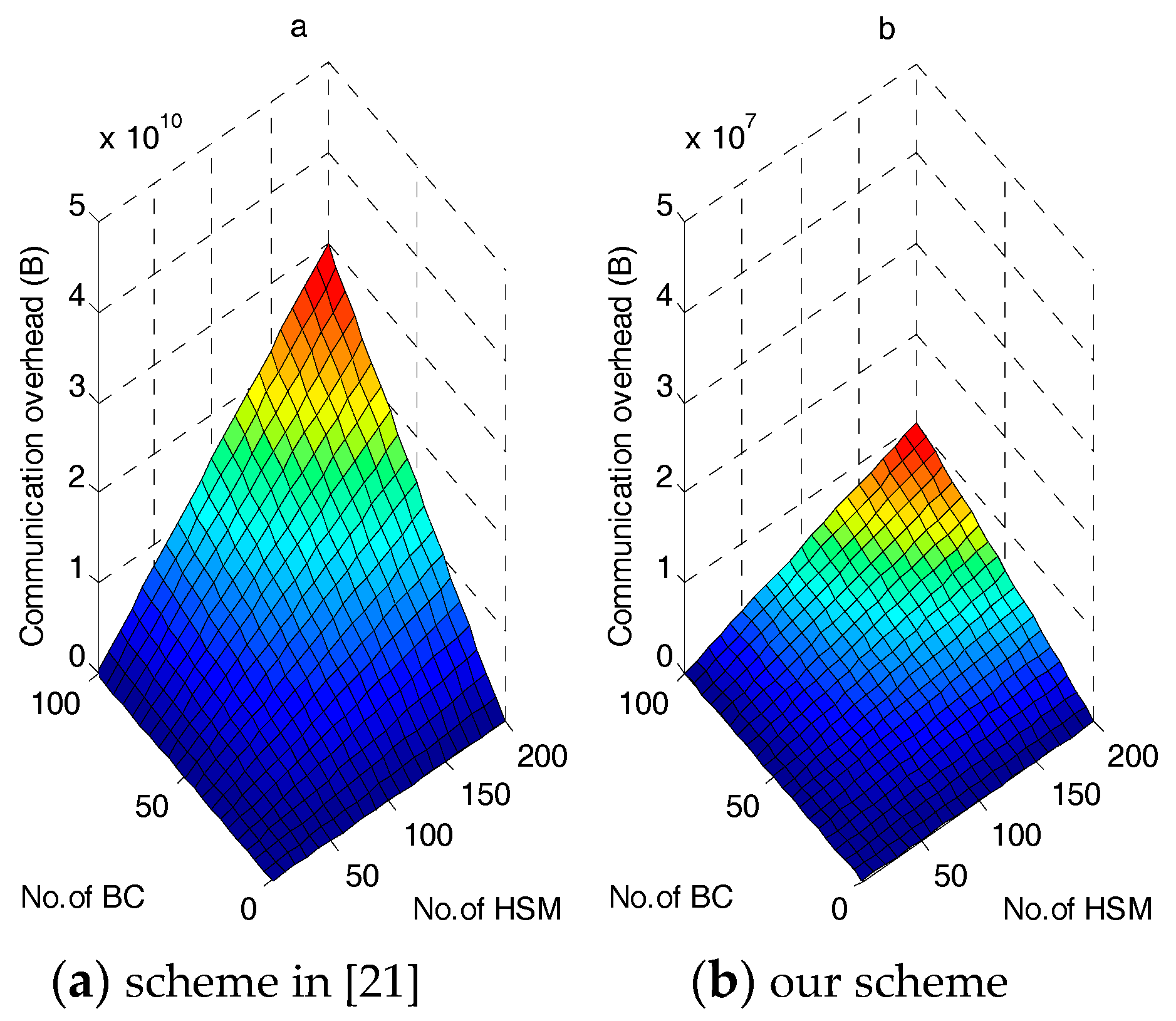
- Zhong et al. in [21] employ commitments to store an individual power requirement and transmits it upward through nodes to the CC, which generates excessive communication overhead, while we employ a regional concentrator to store and distribute the individual power requirement.
- From a security and data integrity perspective, [21] employs only one authentication key throughout the entire authentication process; however, as is well known, a user’s smart meter is more vulnerable to attack than a gateway is. Therefore, if the authentication key is compromised, all the subsequent authentication processes are vulnerable to a man-in-the-middle attack. Our scheme strengthens this aspect by adopting a stringent method of authentication between the HSM and the BAN Concentrator (BC) to reduce the vulnerability of the HSM. In our scheme, a new authentication key is generated randomly based on the Diffie-Hellman key establishment protocol in every communication session. In comparison with [21], we show that when the number of smart meters is very large, our protocol is more efficient and more stringent than competing schemes.
3. Models and Goals
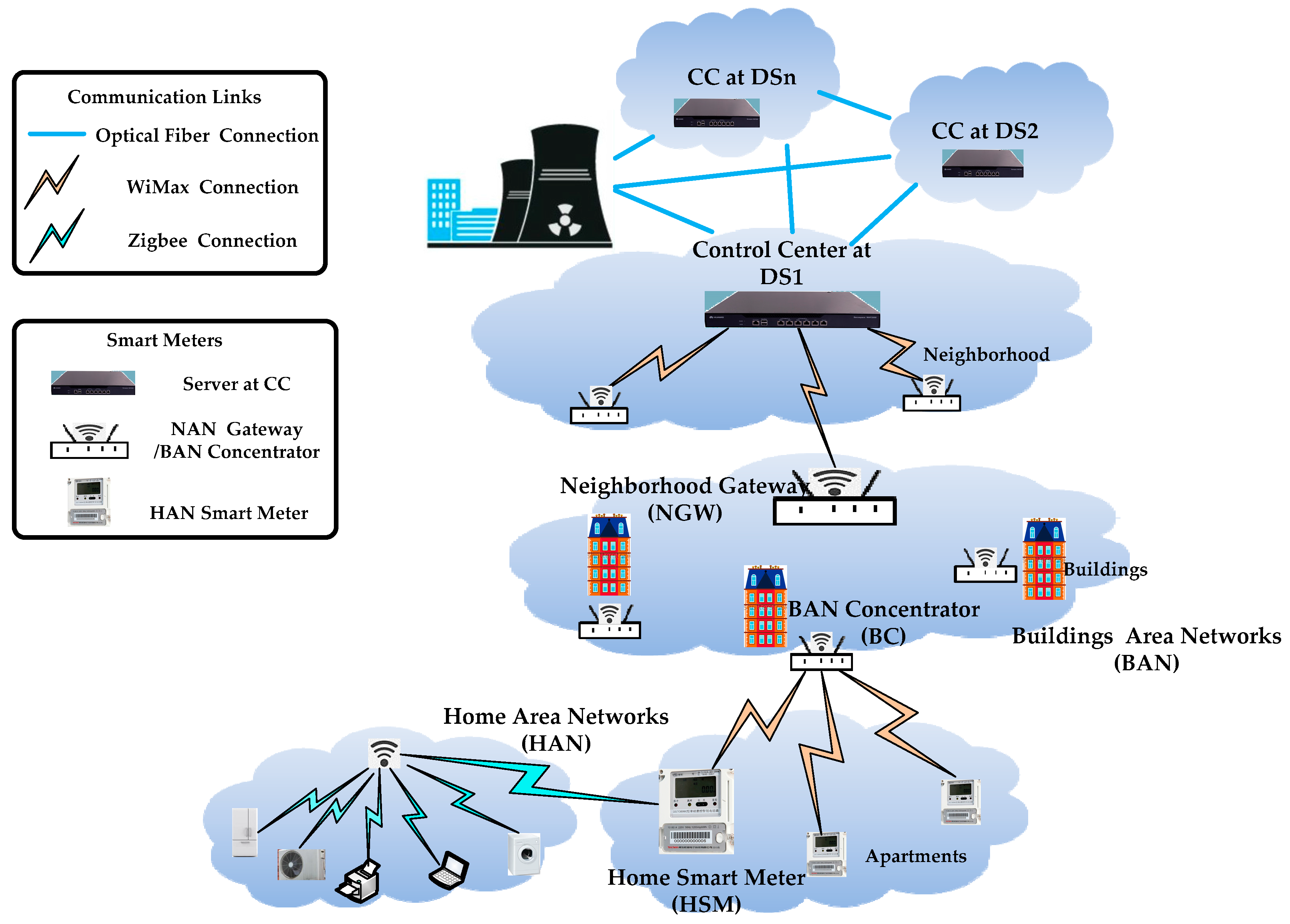
3.1. System Communication Model
- CC: we assume CC is a highly trusted and powerful entity in charge of managing the whole system. Its duty is to initialize the system and to collect, process, analyze the real-time data, and provide power distribution according to the power level and real-time data.
- BC: we assume BC is a highly trusted gateway in charge of collecting, storing, aggregating, and distributing real-time data. BC can also store regional individual power requirements and aggregate regional power consumption and transmit it with regional requirement summation through the NAN to the CC and distribute individual power to every user according to the power ratio from the CC. BC needs enough secure storage, which can be used to handle the long-term keys described above and protect their private reading; this can be achieved, for example, by TPM chips to store the specific power requirements of HSM.
- NGW: NGW is a power gateway, which connects real-time data from BC and CC. The duty of NGW is to relay and aggregate real-time data. The duty of aggregation is aggregate the regional consumption data from BC, whereas the duty of relay is to relay the regional requirement data from BC in a secure way.
- HSM: we refer to HSM as a user with a smart meter and the HAN is made up of various smart applications. The real-time data of HSM is collected and processed by BC and transmitted into CC via NGW. Although HSM is tamper-resistant and interfering with measurements is not trivial, it is not as powerful as the gateway (e.g., BC, NGW), so it may be vulnerable to attackers.
3.2. Security Goals
- Confidentiality. Authorized limitation to access data and encryption is critical to protect personal privacy and information—in other words, only the granted entity can receive the individual user data or access the databases of the GWs, i.e., an attacker cannot decrypt the communication flows between GWs and CC.
- Data integrity, authentication, and access control. Authentication and access control verify authorized communication entity and ensure access to the power information, which prevent an ungranted attacker from modifying and destructing the power data integrity and availability.
- Forward secrecy. Forward secrecy is a property of secure communication protocols in which compromise of long-term keys does not compromise past session keys.
3.3. Attack Model
- We consider the following possible attack types in EPPRD.
- External Attack: The external attacker tries to infer the individual information by eavesdropping on the communication and data flow from the HSM to the BC, from the BC to the NGW, and from the NGW to the CC.
- Internal Attack: Internal attackers are usually participants of the protocol (e.g., NGW) who may collude with as many compromised HSMs as possible to learn about the individual user’s privacy, or a curious HSM who attempts to infer the private data of another HSM.
- Man in the middle attack: The attacker forges or alters the communication data once he is authorized by any communication party, so the authentication key between HSM and BC should be different from that between BC and NGW to prevent the authenticated attacker from altering the communication data between BC and NGW.
- Replay Attack: Attacker tries to repeat or delay a valid data transmission while misleading the honest sender into thinking they have successfully finished the data transmission.
4. Preliminaries
4.1. Computational Diffie–Hellman (CDH) Problem
4.2. Paillier Cryptosystem
5. Our Scheme
5.1. System Initialization
- Given the security parameter , CC first generates (p,q) by running , and calculates the Paillier Cryptosystem’s public key denoted, (n = pq, g) and the corresponding private key (), where p and q are two large prime numbers for which . The is distributed to each node in the network model, and the is kept private;
- For each user’s smart meter, generates a pair of public and private keys and respectively. Then, is stored at the control center and distributed to each user after initialization, while is preloaded into the and kept private.
- Each generates a pair of public and private keys, and respectively. Then, is stored at the control center and distributed to each user after initialization, while is preloaded into the and kept private.
- Each generates a pair of public and private keys, and , respectively. Then is stored at the control center and distributed to each NGW after initialization, while is preloaded into the and kept private.
- CC generates an authentication key, s, encrypts it with the BC’s and the NGW’s public ciphertext, and transmits it to the BC and NGW, respectively.
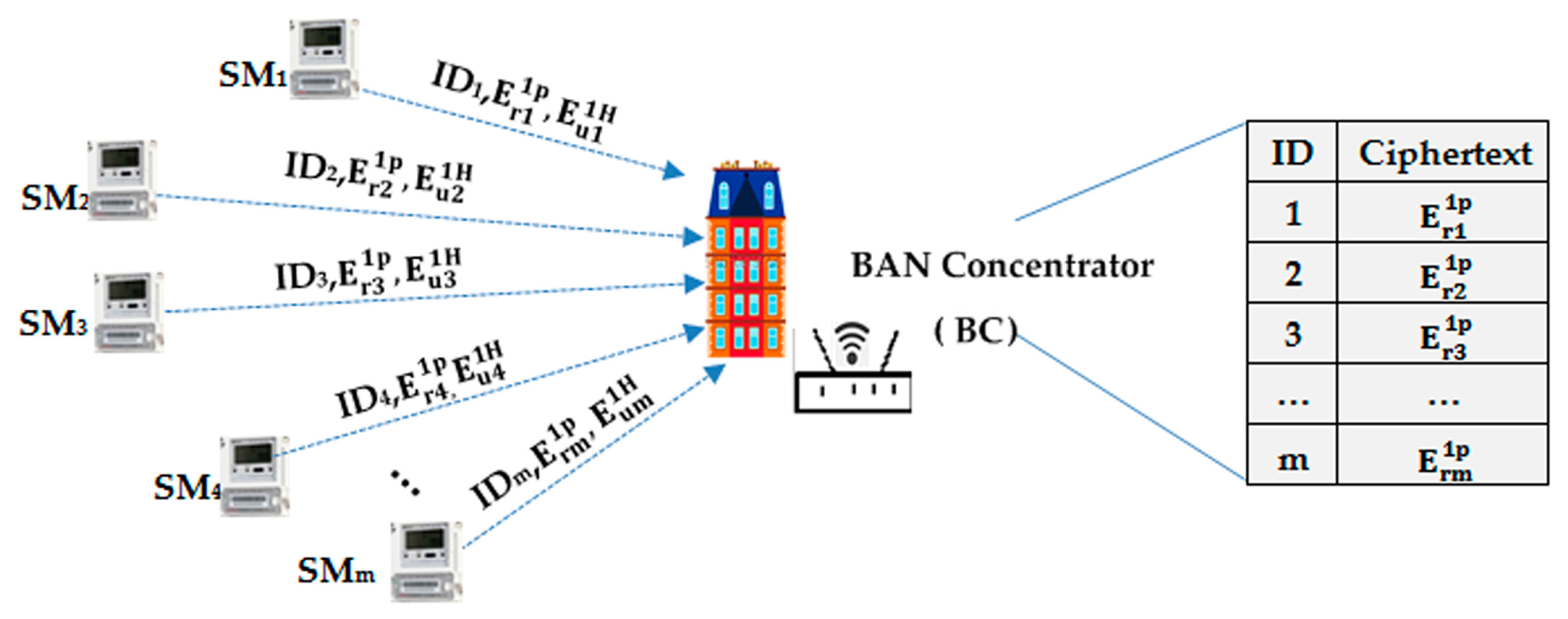
5.2. Upward Message Form
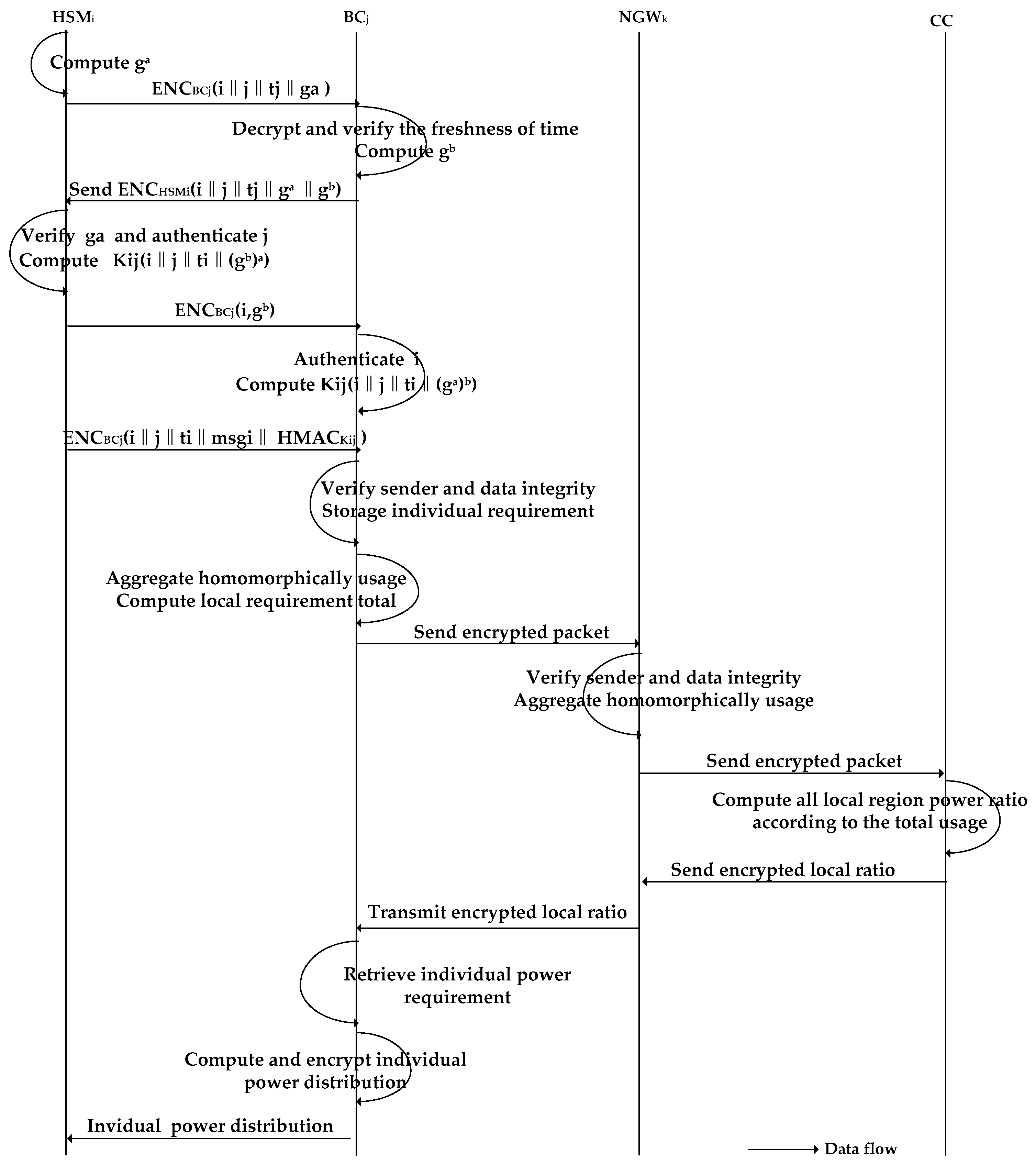
5.3. Communication between and
5.3.1. Authentication Part
5.3.2. Upward Transmission
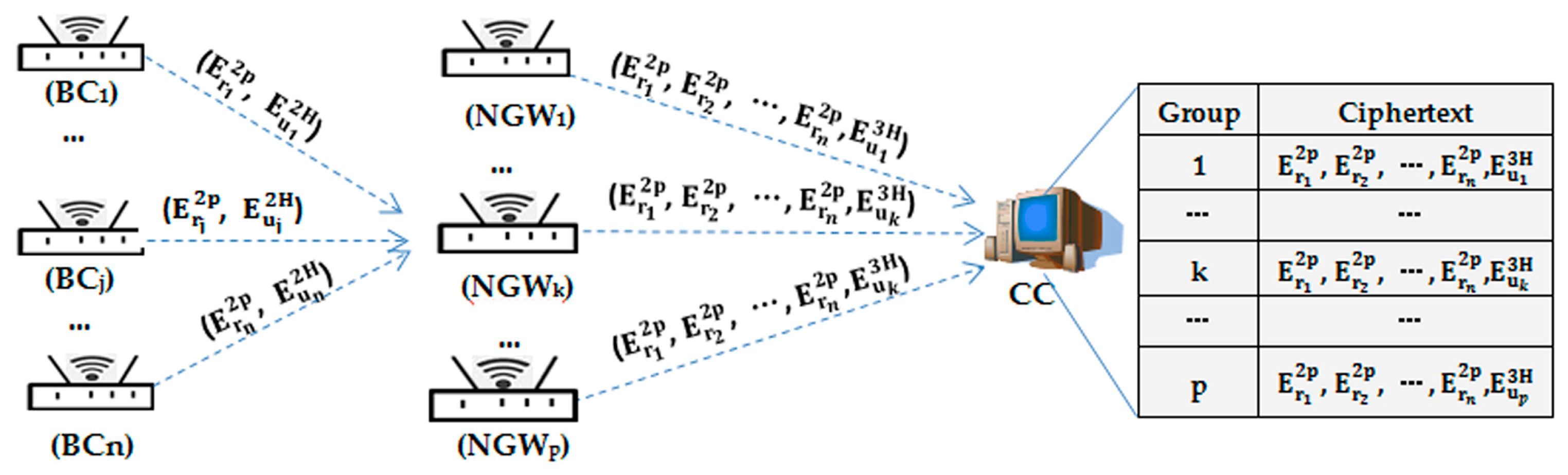
5.4. Authentication and Communication in BC, NGW, and CC
5.5. Power Distribution Generation
6. Security Analysis
6.1. Mutual Authentication and Data Integrity
6.2. Protection against Eavesdropping Attack
6.3. Protection against Internal Attack
6.4. Protection against Replay and Man-in-the-Middle Attack
6.5. Security Proof
- Setup: The challenger initializes the smart meters set to participant aggregation process. The challenger generates their keys including public and private keys during the secret key generation phase in Section 5.1 and gives the public keys to the adversary.
- Queries: can make “compromise” queries for private keys or plaintext to users. It can compromise at most n − 1 meters. The challenger returns the private key and plaintext of compromised smart meters. may also compromise the aggregator NSM and receives the aggregation from the challenger.
- Challenge: The specifies an uncompromised set , in which specifies randomly two smart meters and . The challenger flips a random coin b. If b = 0, the challenger return to the , else return {}.
- Guess: The guesses . The wins if . The advantage of in attacking the scheme is defined as follows:
7. Performance Analysis
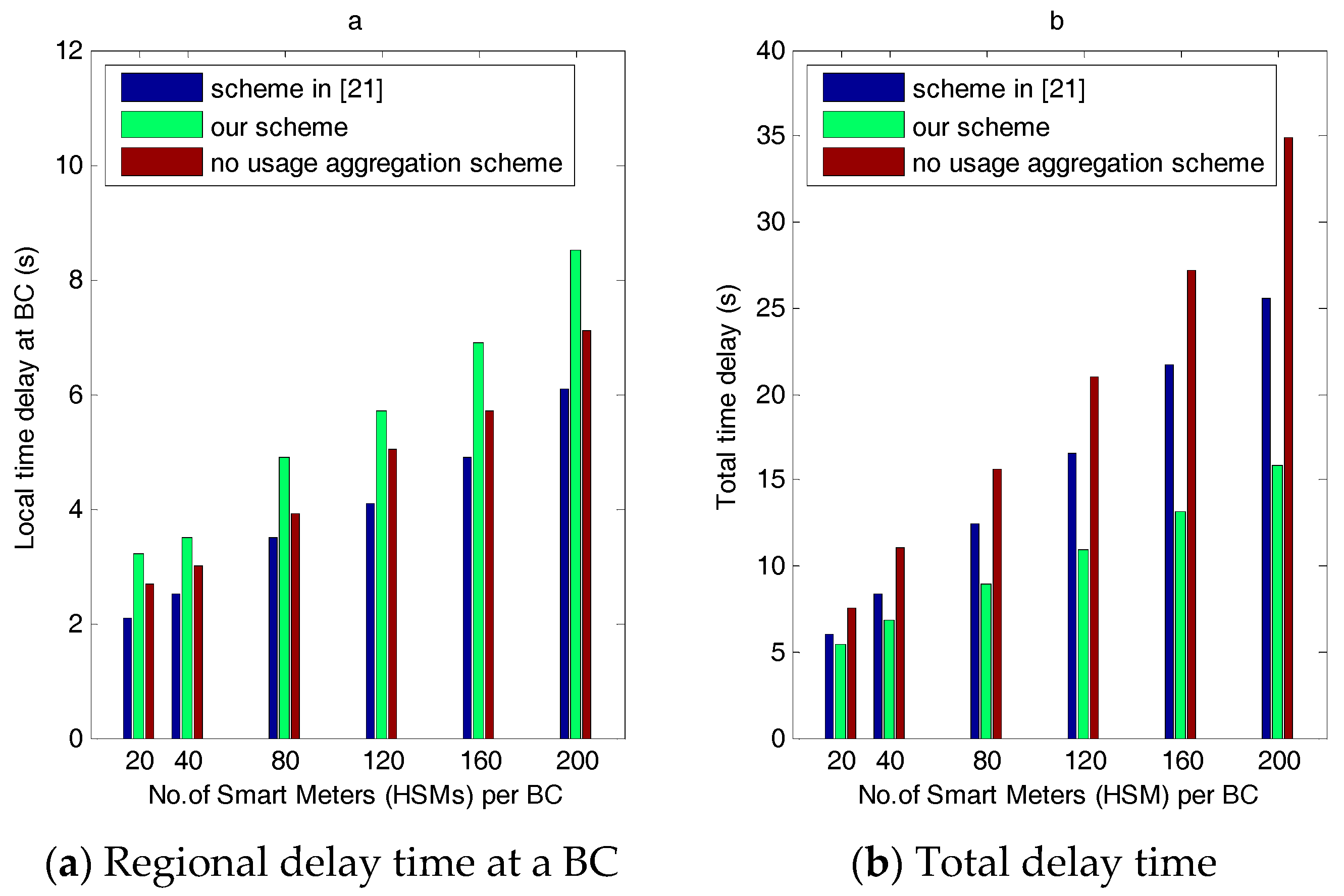
- The no-consumption aggregation scheme. In this scheme, the BC receives publicly encrypted consumption messages rather than homomorphic encryption from all the HSMs and transmits them to the CC via NGW. The CC decrypts the encrypted messages based on its public key successively rather than decrypting the message once as in our scheme. As we can imagine, the no-consumption aggregation scheme requires excessive communication overhead, and its security is not rigorous enough because it lacks the protection of homomorphic encryption.
- The no-regional-requirement aggregation scheme in [21]. In this scheme, the homomorphically encrypted power requirements estimating the future time period and commitments are transmitted upward. In these messages, the commitment is the evidence of the user power consumption plan at each billing period. Thus, it obtains the same requirement object for individual users as in our scheme. However, as described in the Related Works (Section 2), we propose some improvements from various perspectives.
7.1. Communication Volume
7.2. Computation Overhead
- For :
- For :
- For :
- For the CC:
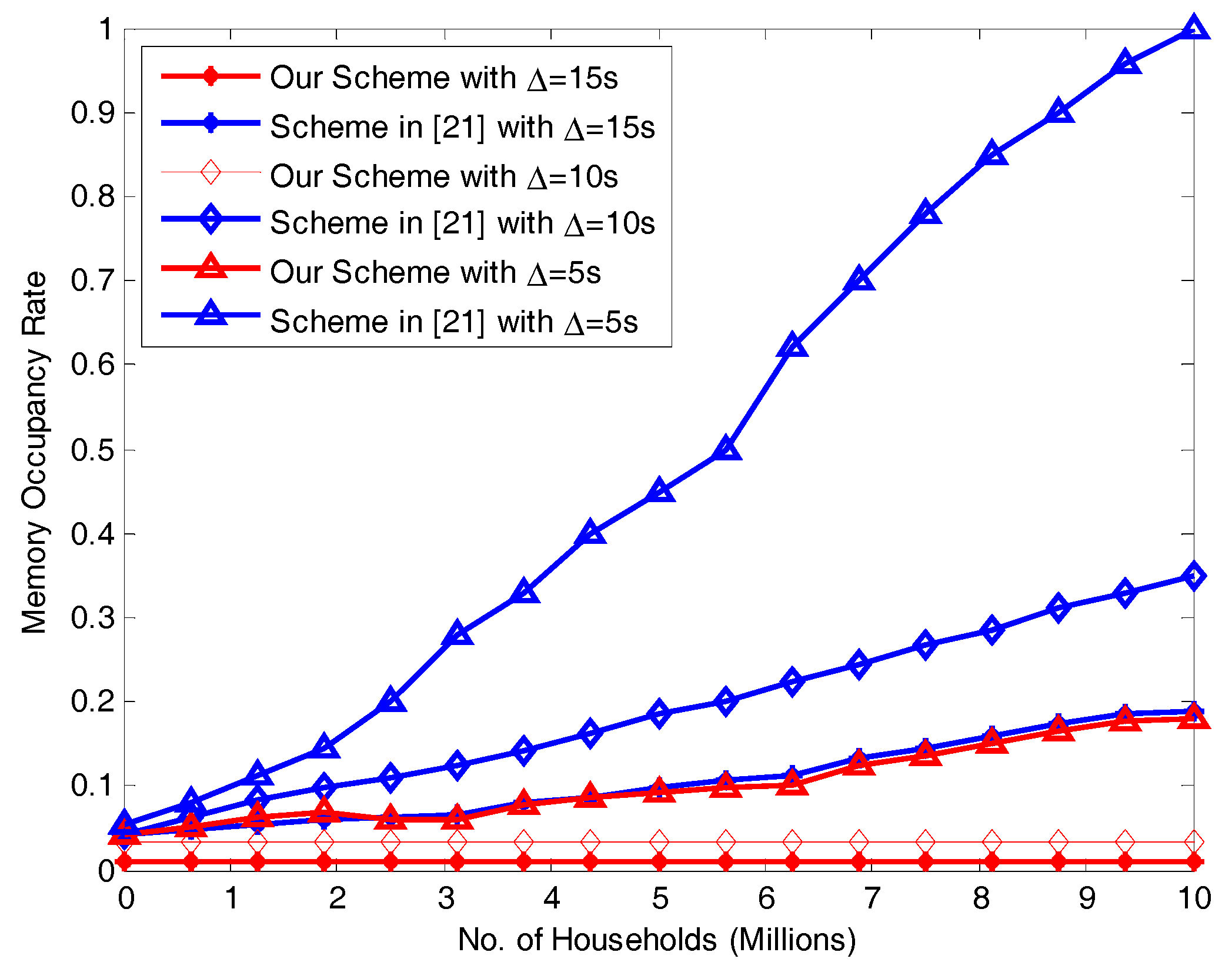
7.3. Memory Occupancy Rate for Different Transmission Intervals ∆
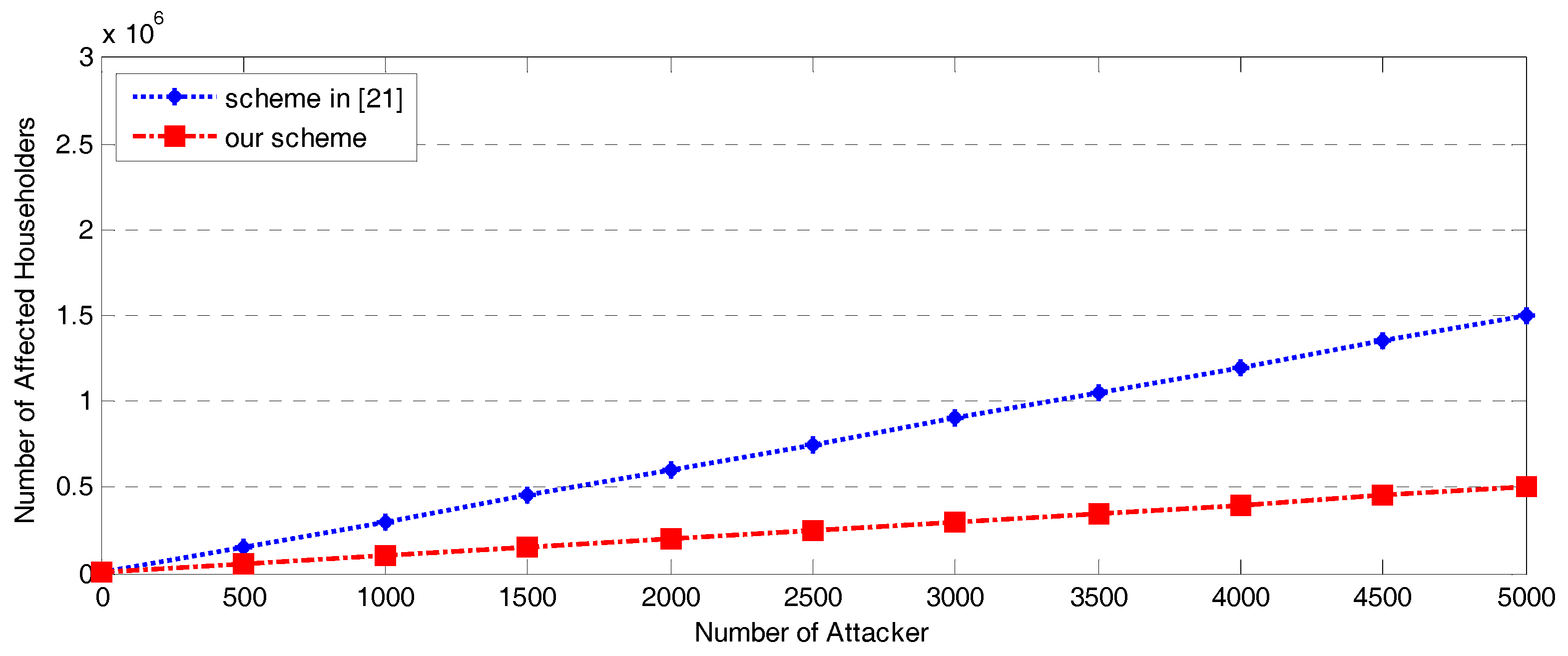
7.4. Affected Householders with Different Numbers of Attackers
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
Abbreviations
| HSM | User Smart Meter |
| BC | Building Gateway Smart Meter |
| NGW | Neighborhood Gateway Smart Meter |
| GWs | the collection of HSM, BC, and NGW |
References
- Kabalci, Y. A survey on smart metering and smart grid communication. Renew. Sustain. Energy Rev. 2016, 57, 302–318. [Google Scholar] [CrossRef]
- Finster, S.; Baumgart, I. Privacy-Aware Smart Metering: A Survey. IEEE Commun. Surv. Tutor. 2014, 16, 1732–1745. [Google Scholar] [CrossRef]
- Kuzlu, M.; Pipattanasomporn, M.; Rahman, S. Communication network requirements for major smart grid applications in HAN, NAN and WAN. Comput. Netw. 2014, 67, 74–88. [Google Scholar] [CrossRef]
- Li, D.; Aung, Z.; Williams, J. P2DR: Privacy-Preserving Demand Response system in smart grids. In Proceedings of the IEEE International Conference on Computing, Networking and Communications, Honolulu, HI, USA, 3–6 February 2014; pp. 290–315. [Google Scholar]
- Bae, M.; Kim, K.; Kim, H. Preserving privacy and efficiency in data communication and aggregation for AMI network. J. Netw. Comput. Appl. 2016, 59, 333–334. [Google Scholar] [CrossRef]
- Kursawe, K.; Danezis, G.; Kohlweiss, M. Privacy-Friendly Aggregation for the Smart-Grid. In Proceedings of the ACM Workshop on Smart Energy Grid Security ACM, Berlin, Germany, 4–8 November 2011; pp. 65–74. [Google Scholar]
- Bartoli, A.; Hernandez-Serrano, J.; Soriano, M. Secure Lossless Aggregation for Smart Grid M2M Networks. In Proceedings of the IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 333–338. [Google Scholar]
- Fan, C.I.; Huang, S.Y.; Lai, Y.L. Privacy-Enhanced Data Aggregation Scheme against Internal Attackers in Smart Grid. IEEE Trans. Ind. Inf. 2014, 10, 666–675. [Google Scholar] [CrossRef]
- Li, F.; Luo, B.; Liu, P. Secure Information Aggregation for Smart Grids Using Homomorphic Encryption. In Proceedings of the IEEE International Conference on Smart Grid Communications, Gaithersburg, MD, USA, 4–6 October 2010; pp. 327–332. [Google Scholar]
- Chen, L.; Lu, R.; Cao, Z. PDAFT: A privacy-preserving data aggregation scheme with fault tolerance for smart grid communications. Peer-to-Peer Netw. Appl. 2015, 8, 1122–1132. [Google Scholar] [CrossRef]
- Garcia, F.D.; Jacobs, B.; Garcia, F.D.; Jacobs, B. Privacy-Friendly Energy-Metering via Homomorphic Encryption. Lect. Notes Comput. Sci. 2011, 6710, 226–238. [Google Scholar] [CrossRef]
- Lu, R.; Liang, X.; Li, X. EPPA: An Efficient and Privacy-Preserving Aggregation Scheme for Secure Smart Grid Communications. IEEE Trans. Parallel Distrib. 2012, 23, 1621–1631. [Google Scholar] [CrossRef]
- Borges, F.; Mühlhäuser, M. EPPP4SMS: Efficient Privacy-Preserving Protocol for Smart Metering Systems and Its Simulation Using Real-World Data. IEEE Trans. Smart Grid 2014, 5, 2701–2708. [Google Scholar] [CrossRef]
- Jaures, M.; Kerschbaum, F. Fault-tolerant privacy-preserving statistics. IEEE Trans. Smart Grid 2012, 221–238. [Google Scholar] [CrossRef]
- Erkin, Z.; Tsudik, G. Private Computation of Spatial and Temporal Power Consumption with Smart Meters. In Proceedings of the International Conference on Applied Cryptography and Network Security (ACNS 2012), Singapore, 26–29 June 2012; pp. 561–577. [Google Scholar]
- Shi, E.; Chan, T.H.H.; Rieffel, E. Privacy-Preserving Aggregation of Time-Series Data. In Proceedings of the Annual Network & Distributed System Security Symposium (NDSS Symposium 2011), San Diego, CA, USA, 6–9 February 2011; pp. 57–59. [Google Scholar]
- Gong, Y.; Cai, Y.; Guo, Y. A Privacy-Preserving Scheme for Incentive-Based Demand Response in the Smart Grid. IEEE Trans. Smart Grid 2016, 7, 1304–1313. [Google Scholar] [CrossRef]
- Dimitriou, T.; Awad, M.K. A Secure and scalable aggregation in the smart grid resilient against malicious entities. Ad Hoc Netw. 2016, 50, 58–67. [Google Scholar] [CrossRef]
- Fouda, M.M.; Fadlullah, Z.M.; Kato, N. A Lightweight Message Authentication Scheme for Smart Grid Communications. IEEE Trans. Smart Grid 2011, 2, 675–685. [Google Scholar] [CrossRef]
- Liu, Y.; Cheng, C.; Gu, T. A Lightweight Authenticated Communication Scheme for Smart Grid. IEEE Sens. J. 2015, 16, 836–842. [Google Scholar] [CrossRef]
- Zhong, J.; Chim, T.W.; Hui, C.K. PRGA: Privacy-preserving Recording & Gateway-assisted Authentication of Power Usage Information for Smart Grid. Dependable & Secure Computing. IEEE Trans. Dependable Secur. Comput. 2015, 12, 85–97. [Google Scholar] [CrossRef]
- Mahmood, K.; Chaudhry, S.A.; Naqvi, H. A lightweight message authentication scheme for Smart Grid communications in power sector. Comput. Electr. Eng. 2016, 52, 114–124. [Google Scholar] [CrossRef]
- Wang, X.; Mu, Y.; Chen, R. An efficient privacy-preserving aggregation and billing protocol for smart grid. Secur. Commun. Netw. 2016, 9, 4536–4547. [Google Scholar] [CrossRef]
- Fouda, M.M.; Fadlullah, Z.M.; Kato, N. Towards a light-weight message authentication mechanism tailored for Smart Grid communications. In Proceedings of the IEEE Conference on Computer Communications Workshops (INFOCOM), Shanghai, China, 10–15 April 2011; pp. 1018–1023. [Google Scholar]
- Li, H.; Lu, R.; Zhou, L. An Efficient Merkle-Tree-Based Authentication Scheme for Smart Grid. IEEE Syst. J. 2014, 8, 655–663. [Google Scholar] [CrossRef]
- Khalifa, T.; Abdrabou, A.; Shaban, K.B. Transport layer performance analysis and optimization for smart metering infrastructure. J. Netw. Comput. Appl. 2014, 46, 83–93. [Google Scholar] [CrossRef]
- Oviedo, R.M.; Ramos, F.; Gormus, S. A Comparison of Centralized and Distributed Monitoring Architectures in the Smart Grid. IEEE Syst. J. 2013, 7, 832–844. [Google Scholar] [CrossRef]
- Paillier, P. Public-key cryptosystems based on composite degree residuosity classes. In Proceedings of the International Conference on Theory and Application of Cryptographic Techniques, Prague, Czech Republic, 2–6 May 1999; pp. 223–238. [Google Scholar]
- FriendlyARM. Friendly ARM [Online]. Available online: http://www.friendlyarm.net/ (accessed on 25 June 2011).
- Jonsson, J.; Kaliski, B. Public-Key Cryptography Standards (PKCS) #1: RSA Cryptography Specifications Version 2.1; RFC Editor United States; Network Working Group (NTWG): Gatineau, QC, Canada, 2003; Volume 29, pp. 79–195. [Google Scholar]
- Rivest, R. The MD5 Message-Digest Algorithm; RFC Editor; Network Working Group (NTWG): Gatineau, QC, Canada, 1992; Volume 11, pp. 121–129. [Google Scholar]
| Symbol | Meaning |
|---|---|
| CC | Control Center |
| GW | All Gateways |
| NGW | Neighborhood Smart Meter |
| BC | BAN Concentrator |
| HSM | Home Smart Meter |
| Public key of the control center | |
| Private key of the control center | |
| The ith HSM | |
| The | |
| The | |
| Public key of | |
| Private key of | |
| Public key of | |
| Private key of | |
| Public key of | |
| Private key of | |
| Public encryption of the requirement for next time slot | |
| Homomorphic encryption of a user’s power consumption | |
| Encryption of plaintext M using key | |
| HMAC of message M using key x |
| Notations | Descriptions | Time Cost |
|---|---|---|
| addition | ≈0.004 ms | |
| multiplication | ≈0.13 ms | |
| asymmetric encryption | ≈3.57 ms | |
| asymmetric decryption | ≈0.0032 ms | |
| symmetric encryption | ≈0.0054 ms | |
| symmetric decryption | ≈0.0014 ms | |
| Homomorphic encryption | ≈2.7 ms | |
| Homomorphic decryption | ≈0.59 ms | |
| Hash | ≈0.0025 ms | |
| HMAC | ≈0.0043 ms |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhang, L.; Zhang, J. EPPRD: An Efficient Privacy-Preserving Power Requirement and Distribution Aggregation Scheme for a Smart Grid. Sensors 2017, 17, 1814. https://doi.org/10.3390/s17081814
Zhang L, Zhang J. EPPRD: An Efficient Privacy-Preserving Power Requirement and Distribution Aggregation Scheme for a Smart Grid. Sensors. 2017; 17(8):1814. https://doi.org/10.3390/s17081814
Chicago/Turabian StyleZhang, Lei, and Jing Zhang. 2017. "EPPRD: An Efficient Privacy-Preserving Power Requirement and Distribution Aggregation Scheme for a Smart Grid" Sensors 17, no. 8: 1814. https://doi.org/10.3390/s17081814
APA StyleZhang, L., & Zhang, J. (2017). EPPRD: An Efficient Privacy-Preserving Power Requirement and Distribution Aggregation Scheme for a Smart Grid. Sensors, 17(8), 1814. https://doi.org/10.3390/s17081814




