Unequal Probability Marking Approach to Enhance Security of Traceback Scheme in Tree-Based WSNs
Abstract
:1. Introduction
2. System Model and Problem Statement
2.1. System Model
2.2. Energy Consumption Model and Related Definitions
2.3. Problem Statement
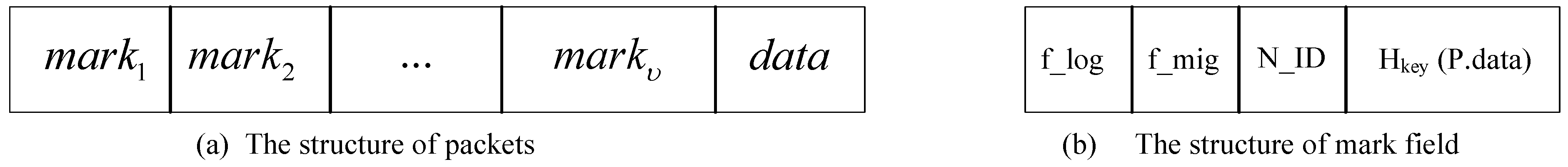
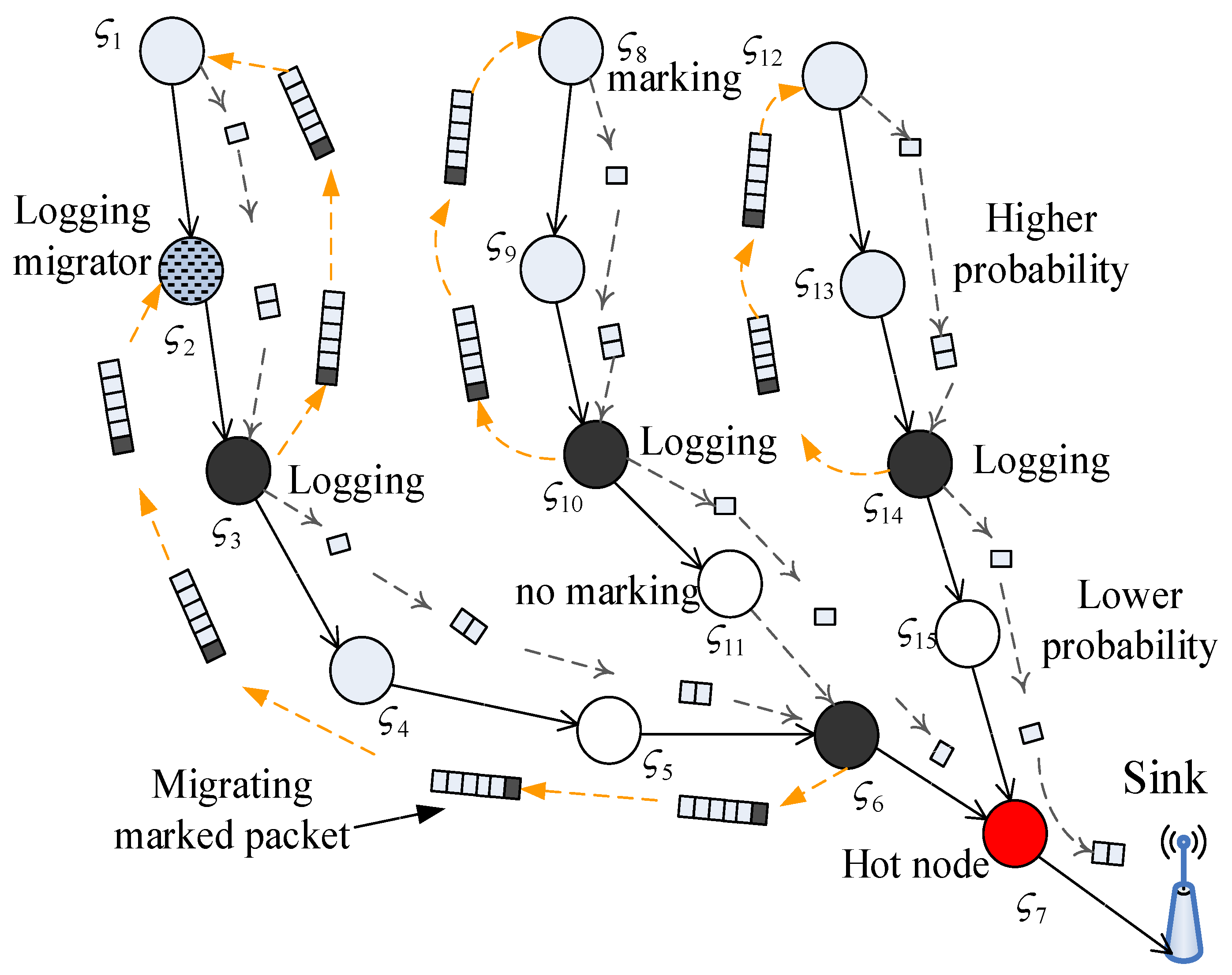
3. UPLM Scheme
3.1. Research Motivation
3.2. The Pseudocode of the UPLM Scheme
| Algorithm 1. Unequal probability marking logging and migration (UPLM) scheme. | |
| 1: | For each packet of node received |
| 2: | node computes marking probability using Equation (6); |
| 3: | marks packet with probability ; |
| 4: | If the number of markings storage in node ; |
| 5: | node marks packet with his probability; |
| 6: | = ; |
| 7: | While > 0 Do |
| 8: | The marking information of packet is forwarded backward with 1-hop; |
| 9: | = − 1; |
| 10: | End while |
| 11: | End if |
| 12: | node sends packet to next node; |
| 13: | End for |
3.3. The Probability Analysis of the UPLM Scheme
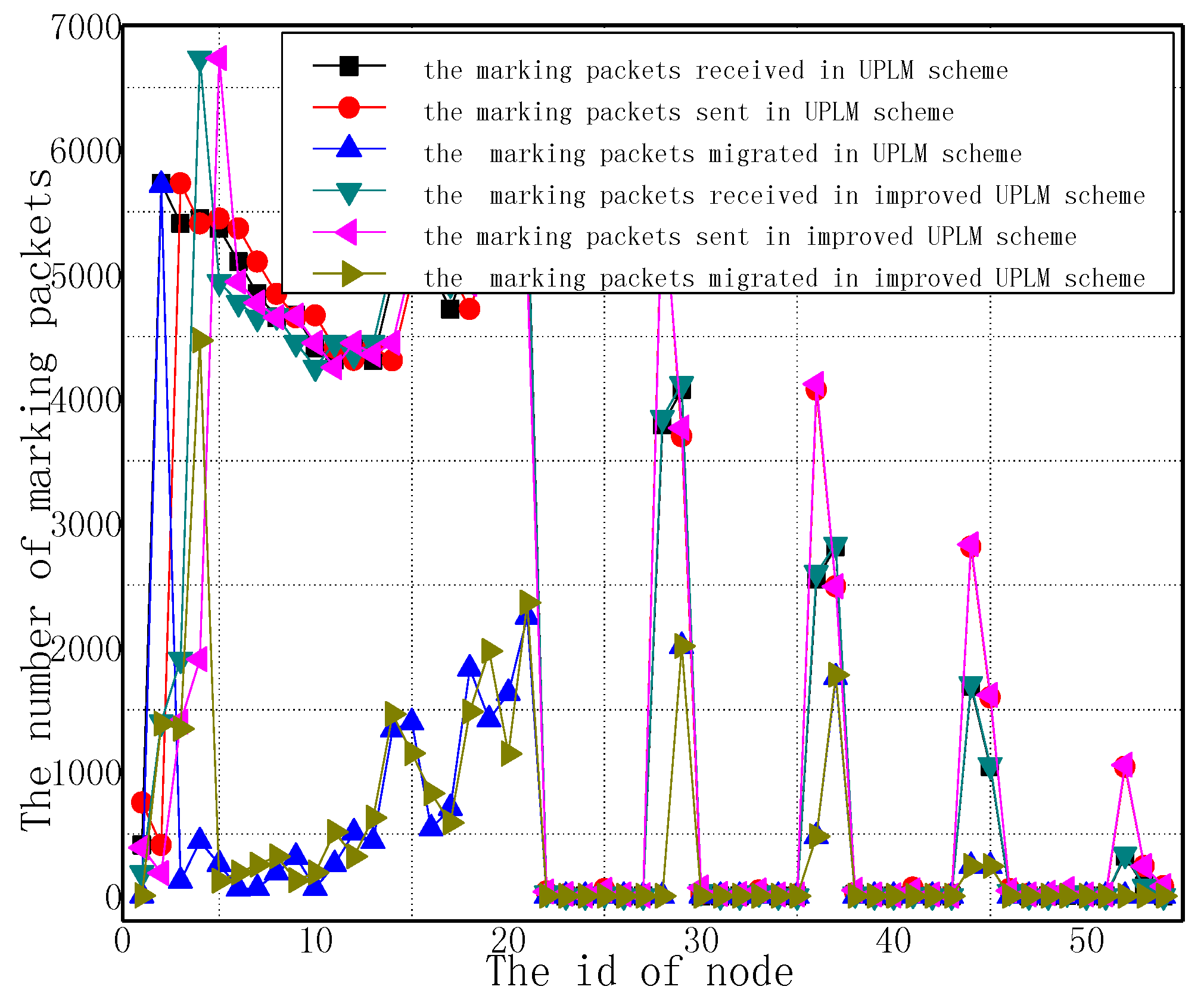
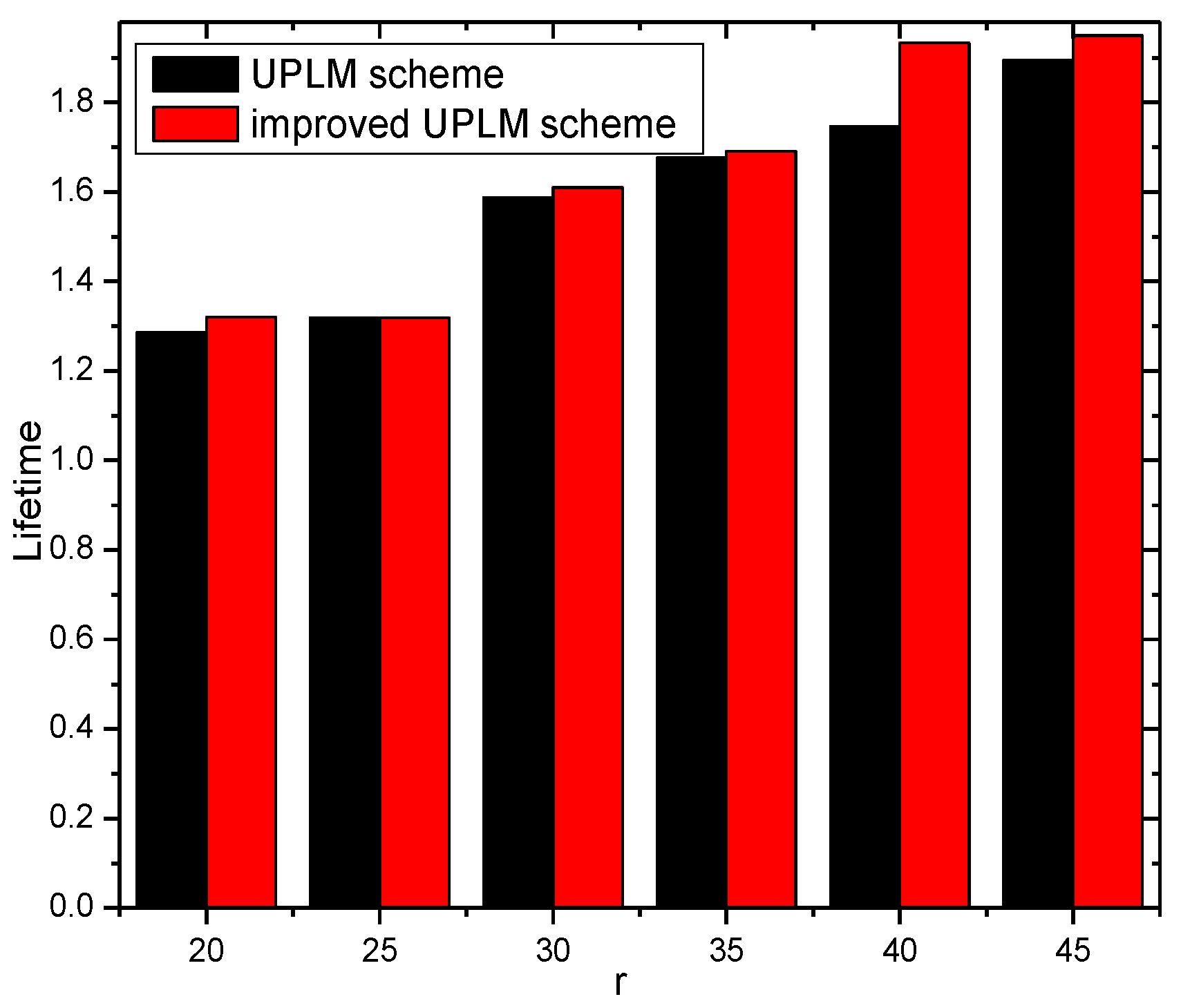
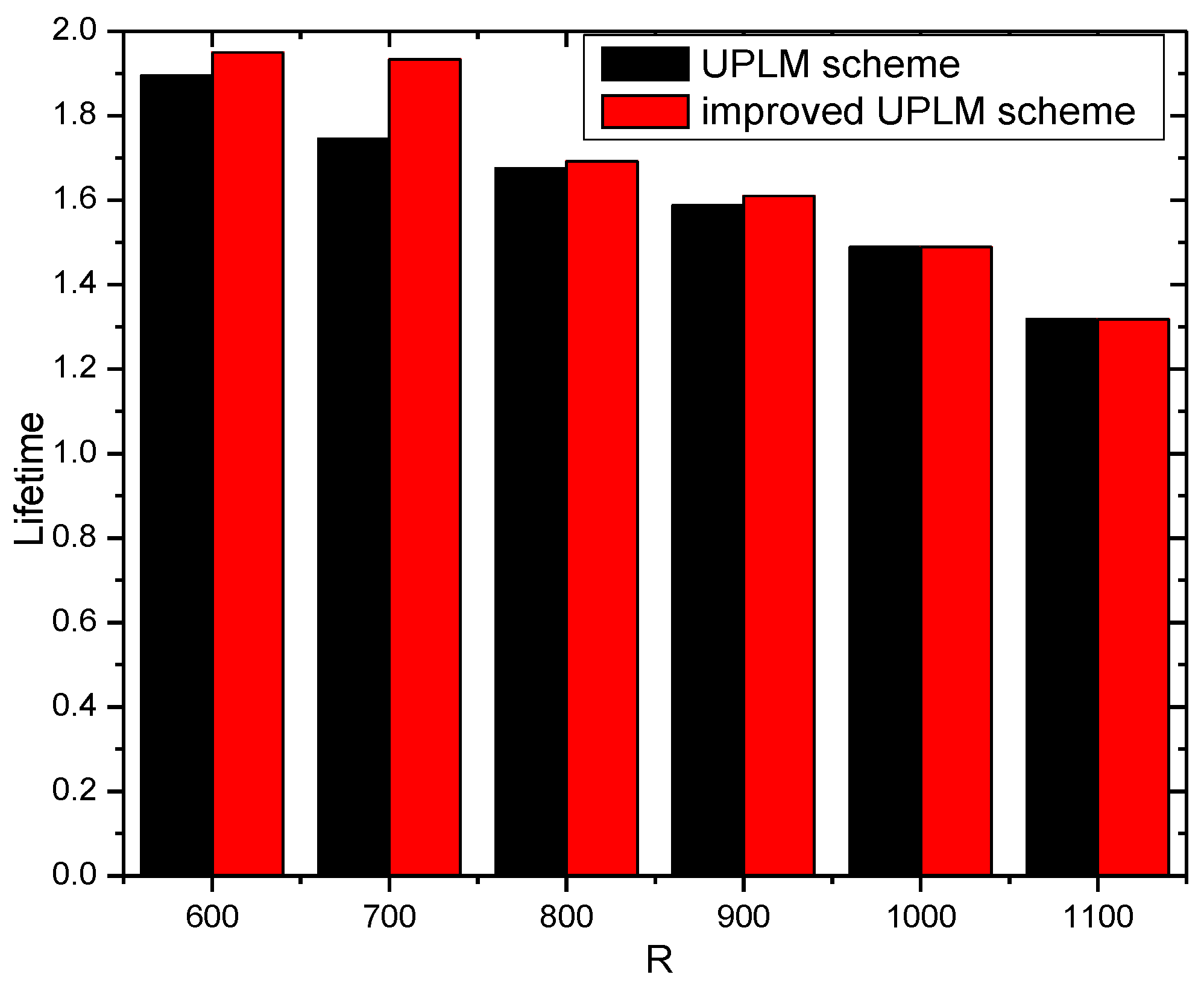
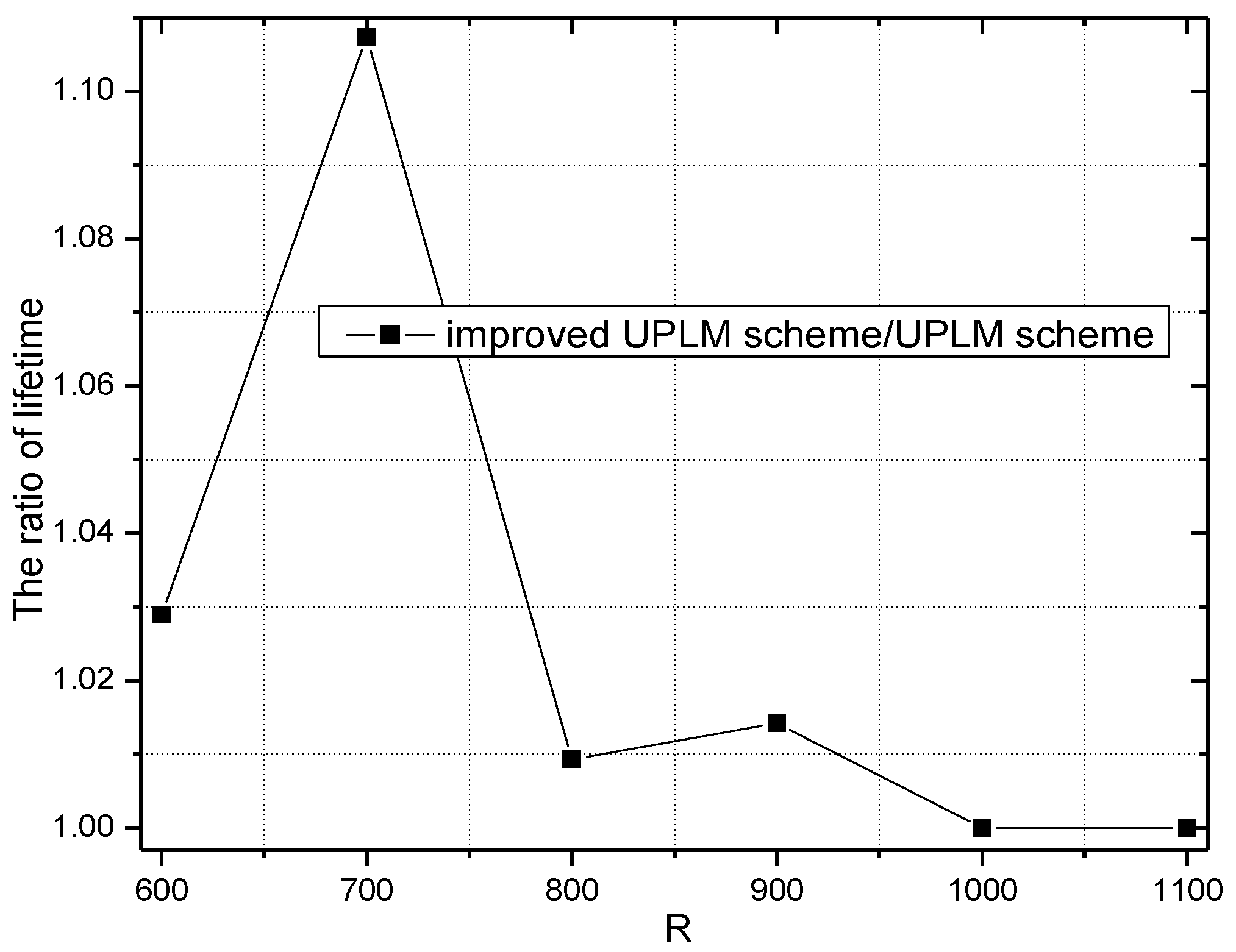
3.4. The Improved UPLM Scheme
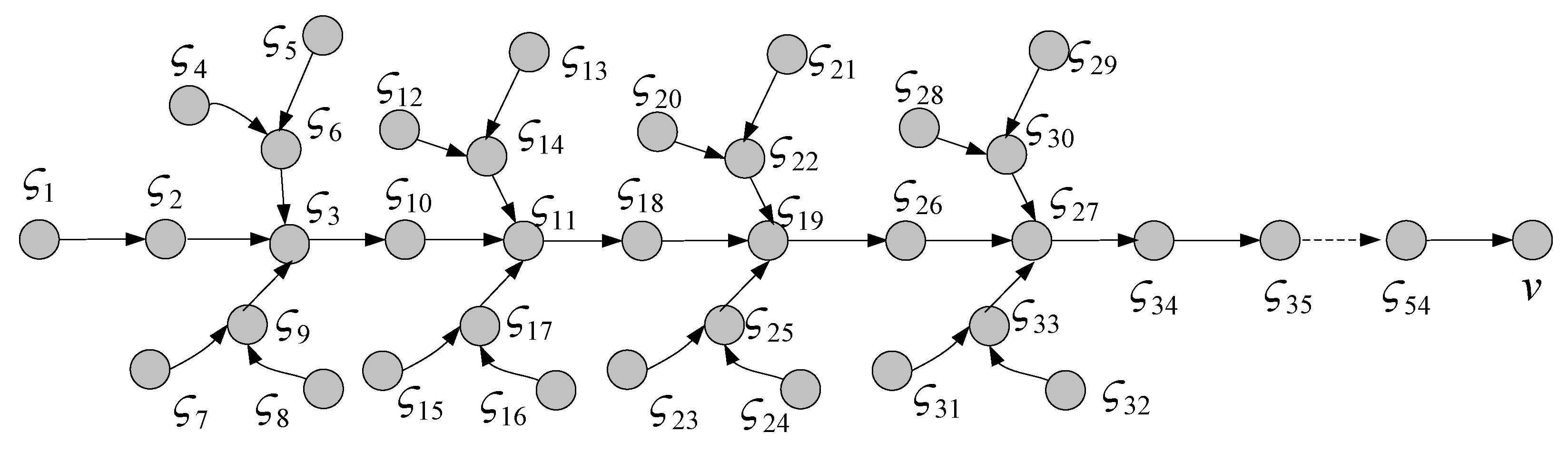
4. Performance Analysis
4.1. Analysis of the Amount of Marking Information Processed by Nodes
4.2. Energy Consumption and Network Lifetime
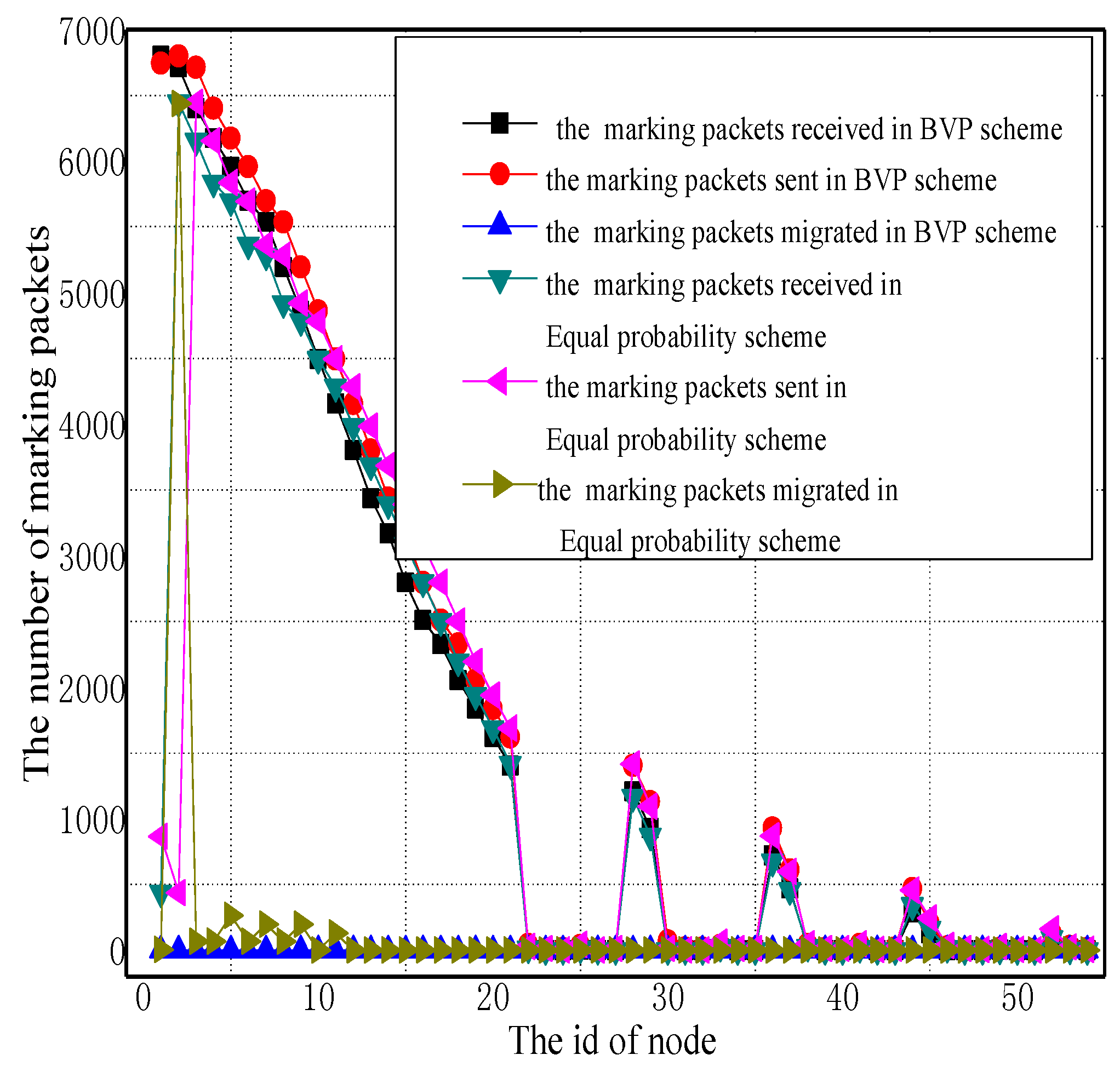
5. Experiment Results
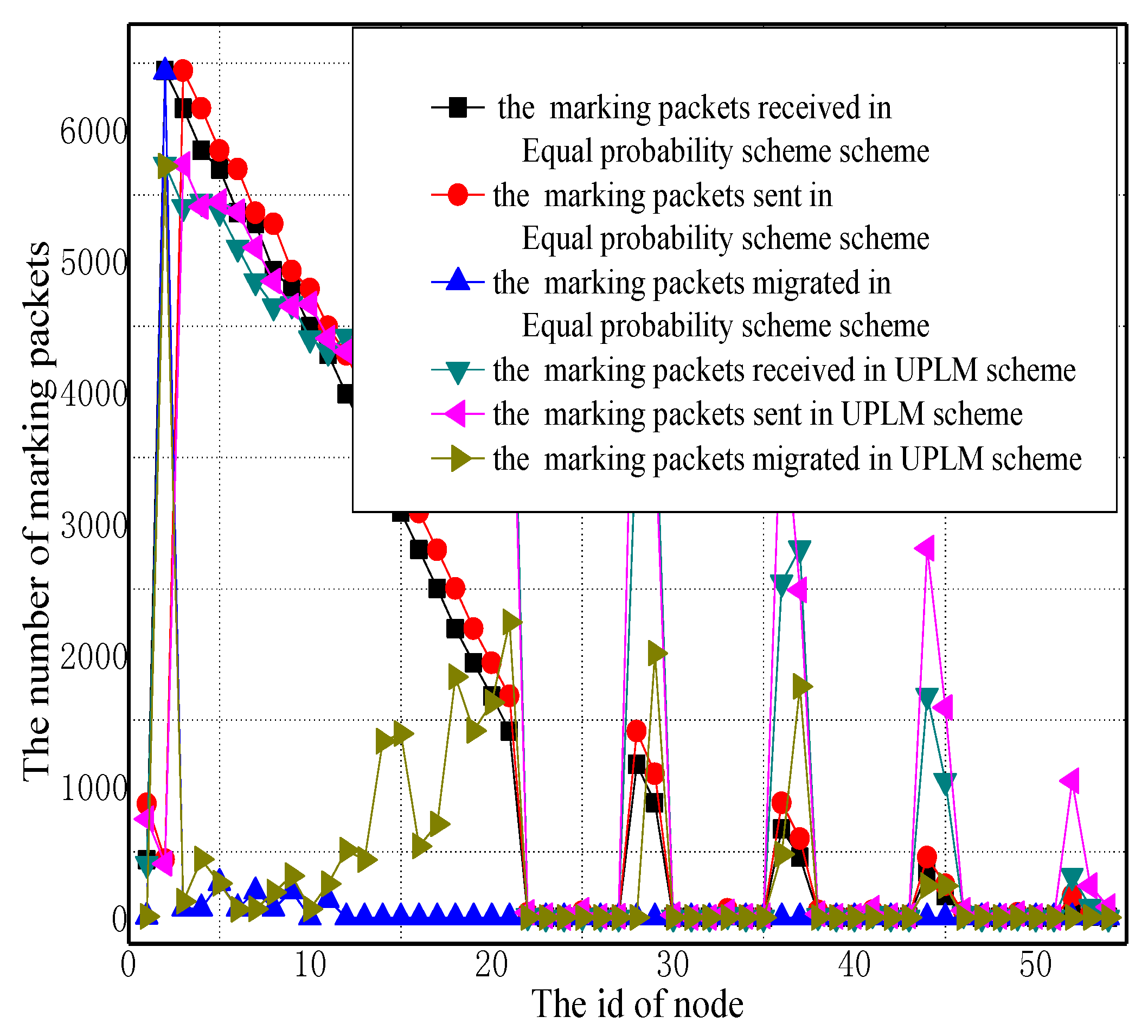
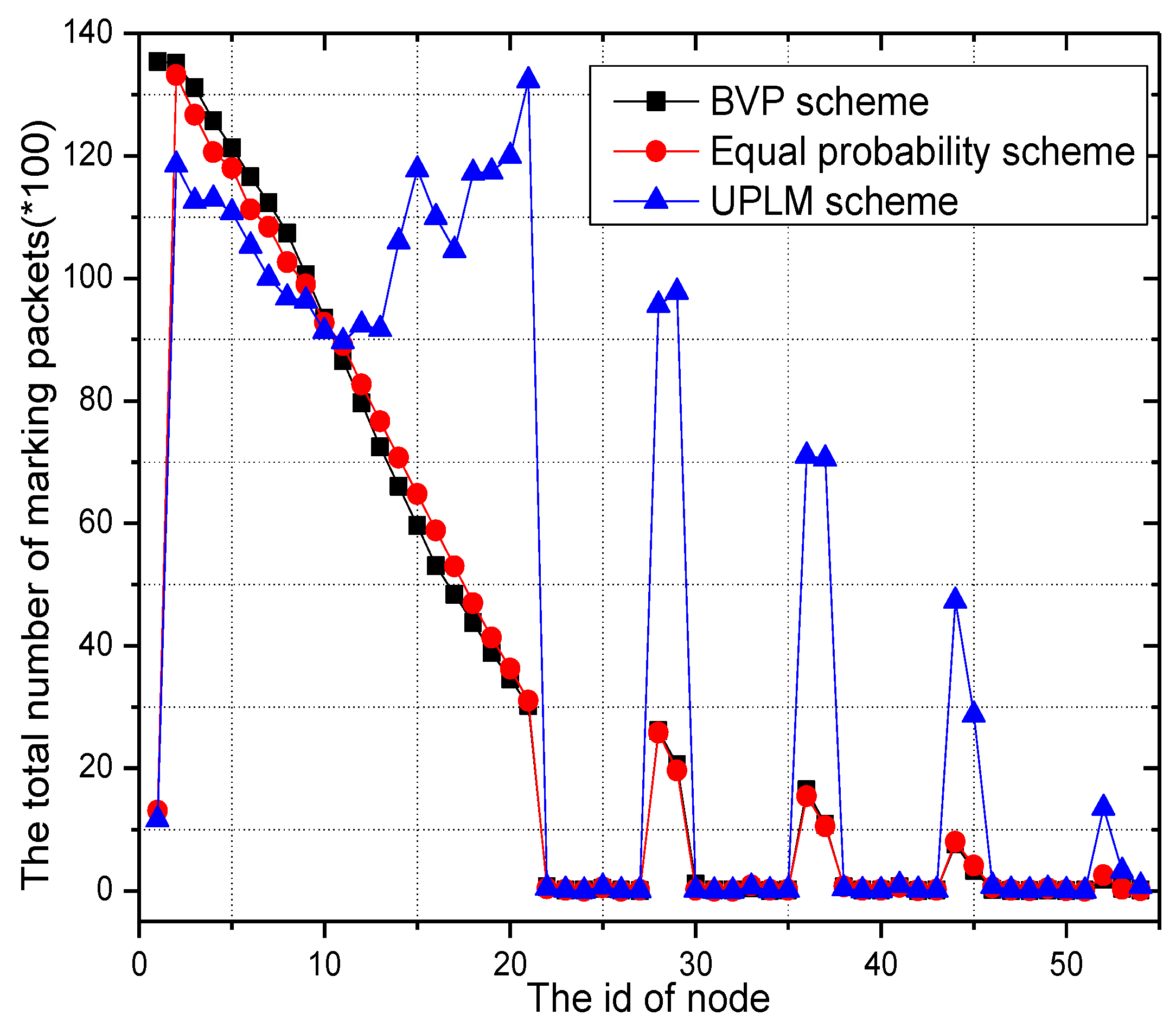
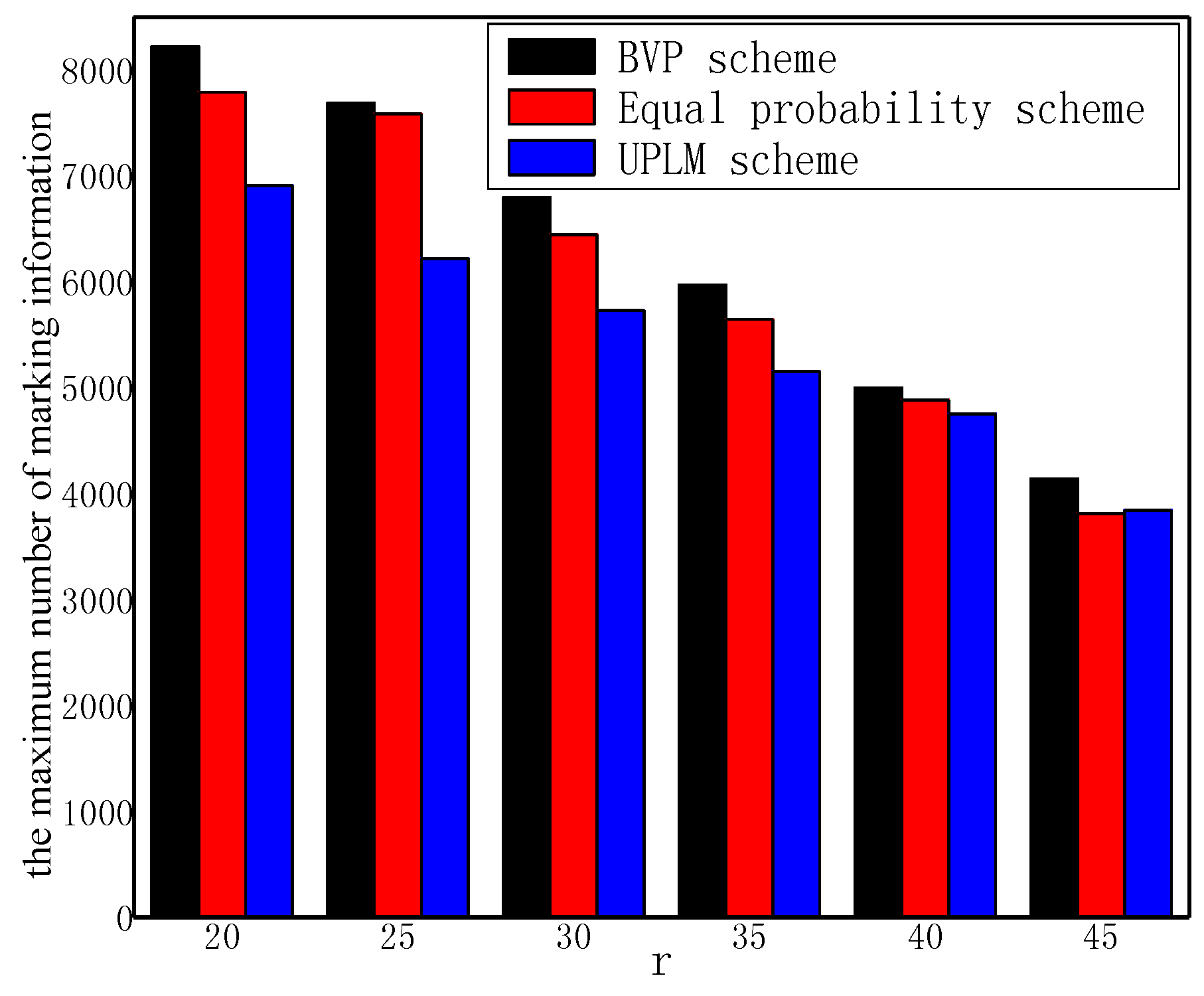
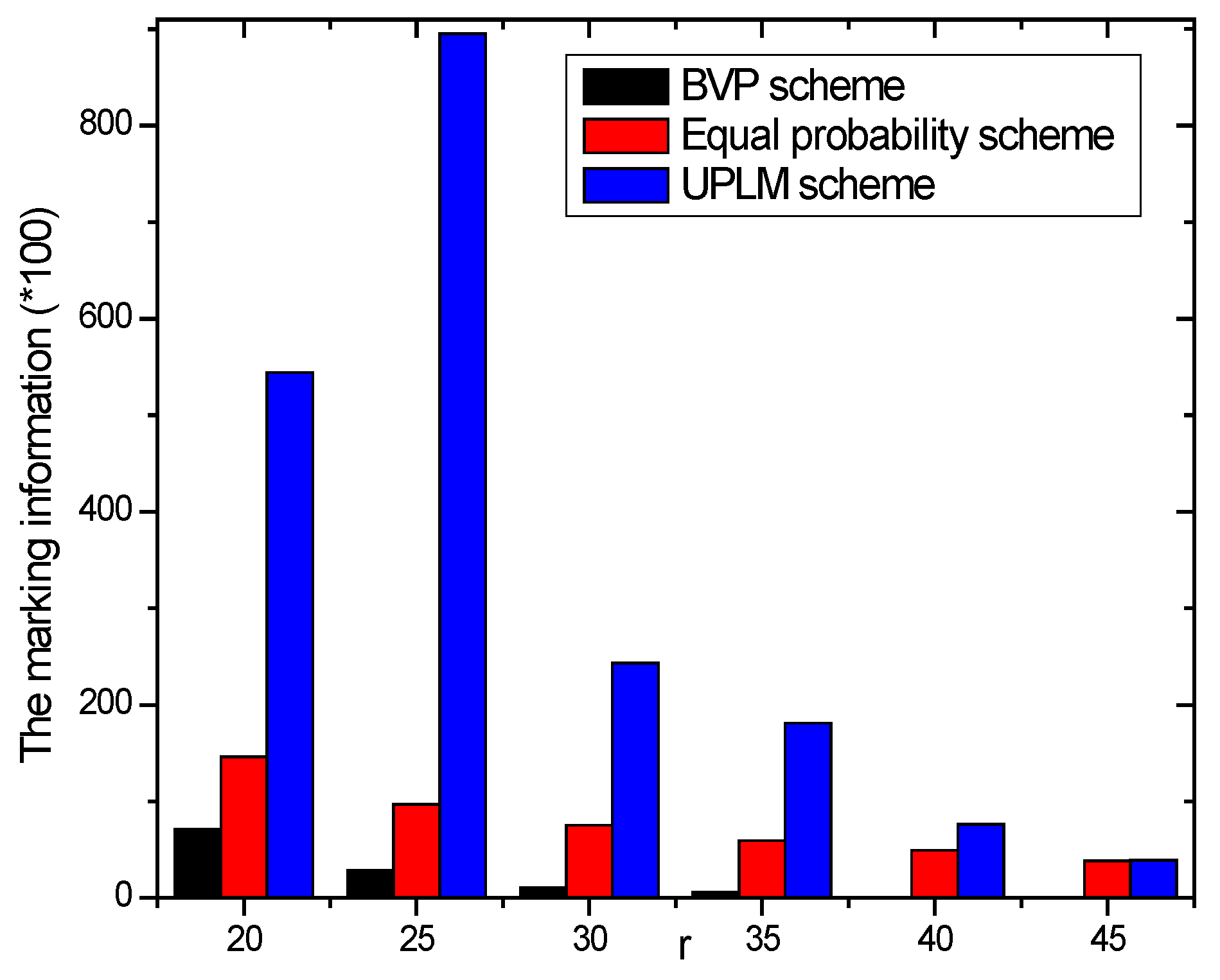
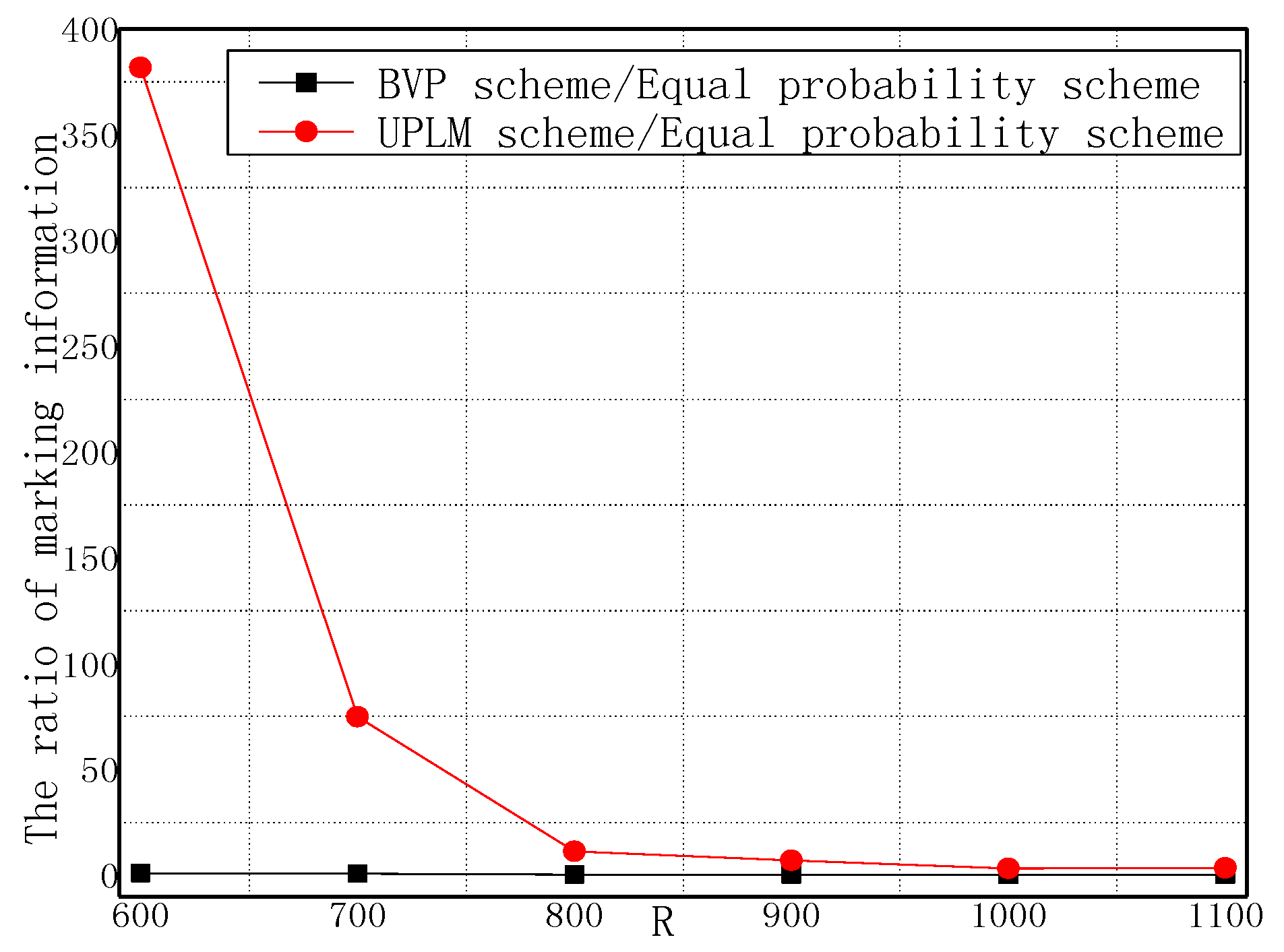
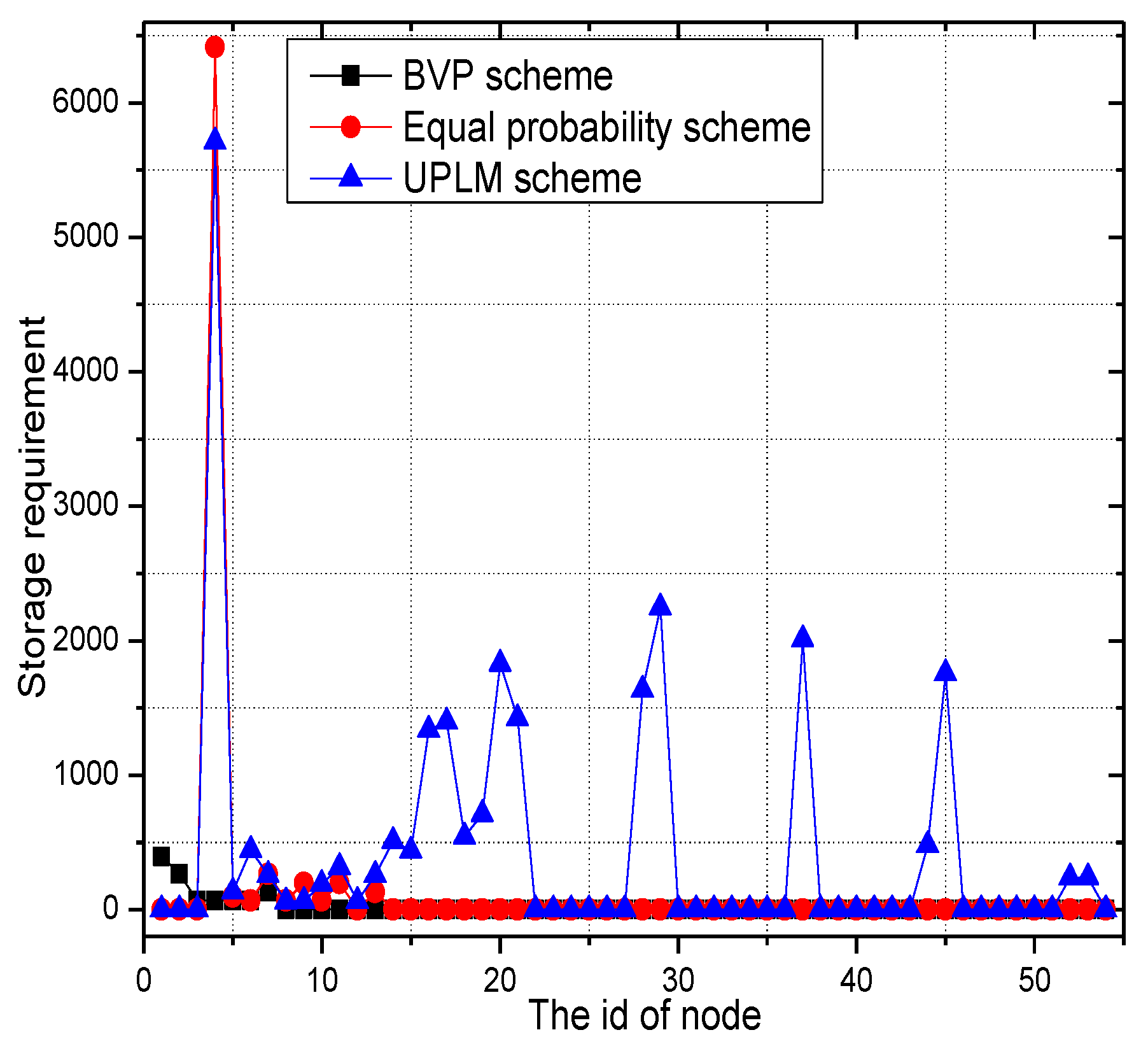
5.1. Analysis of the Amount of Marking Information Processed by Nodes
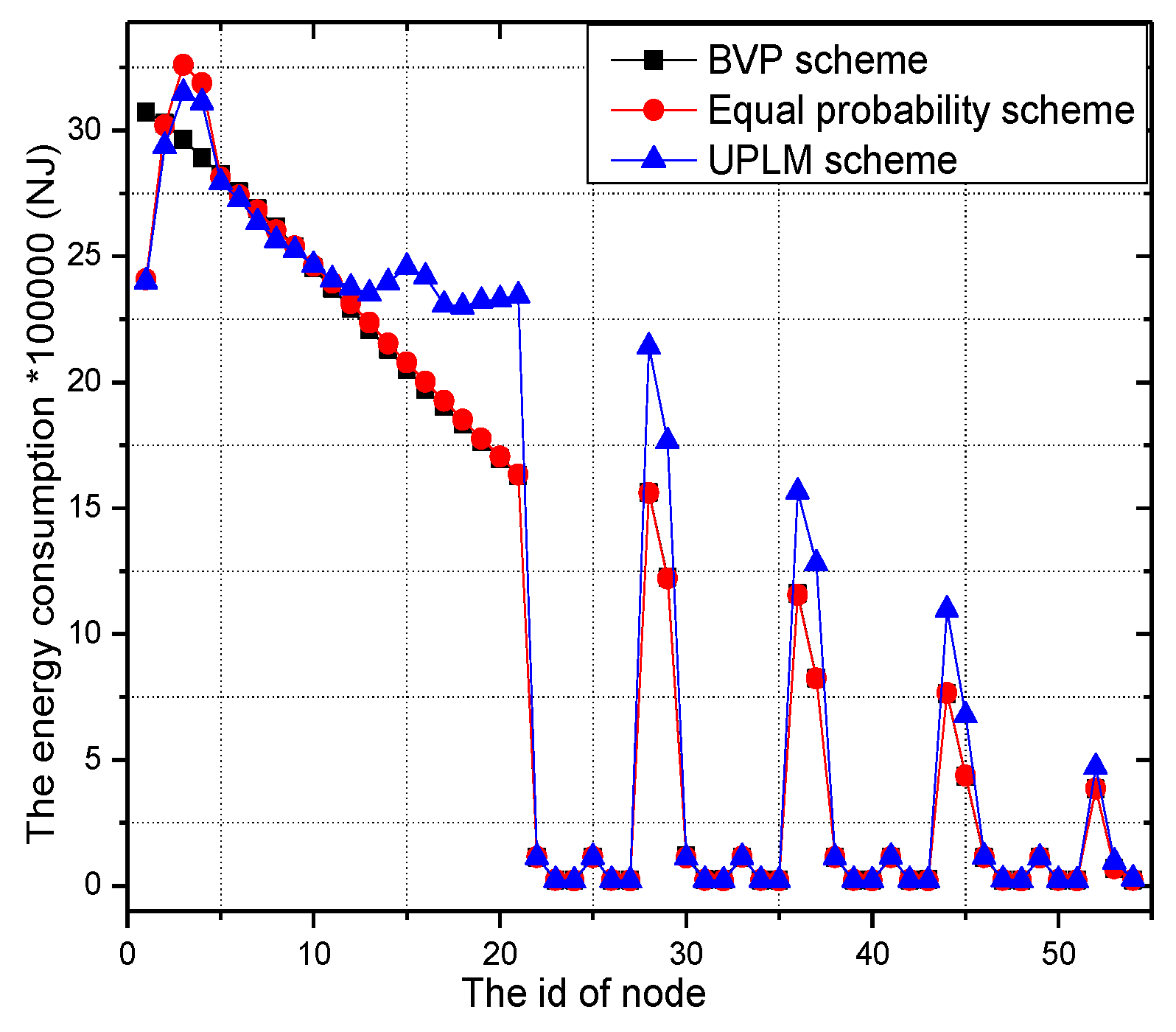
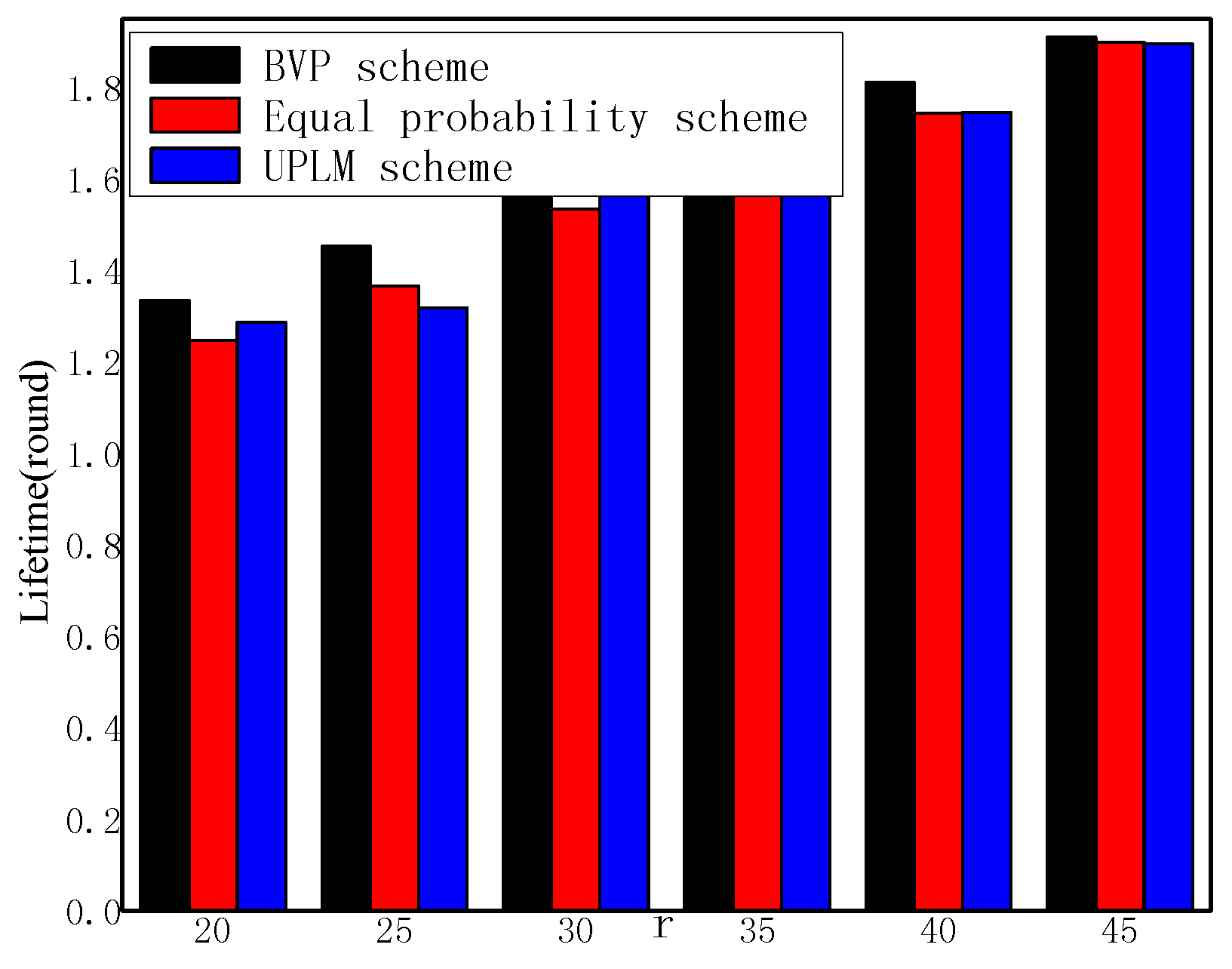
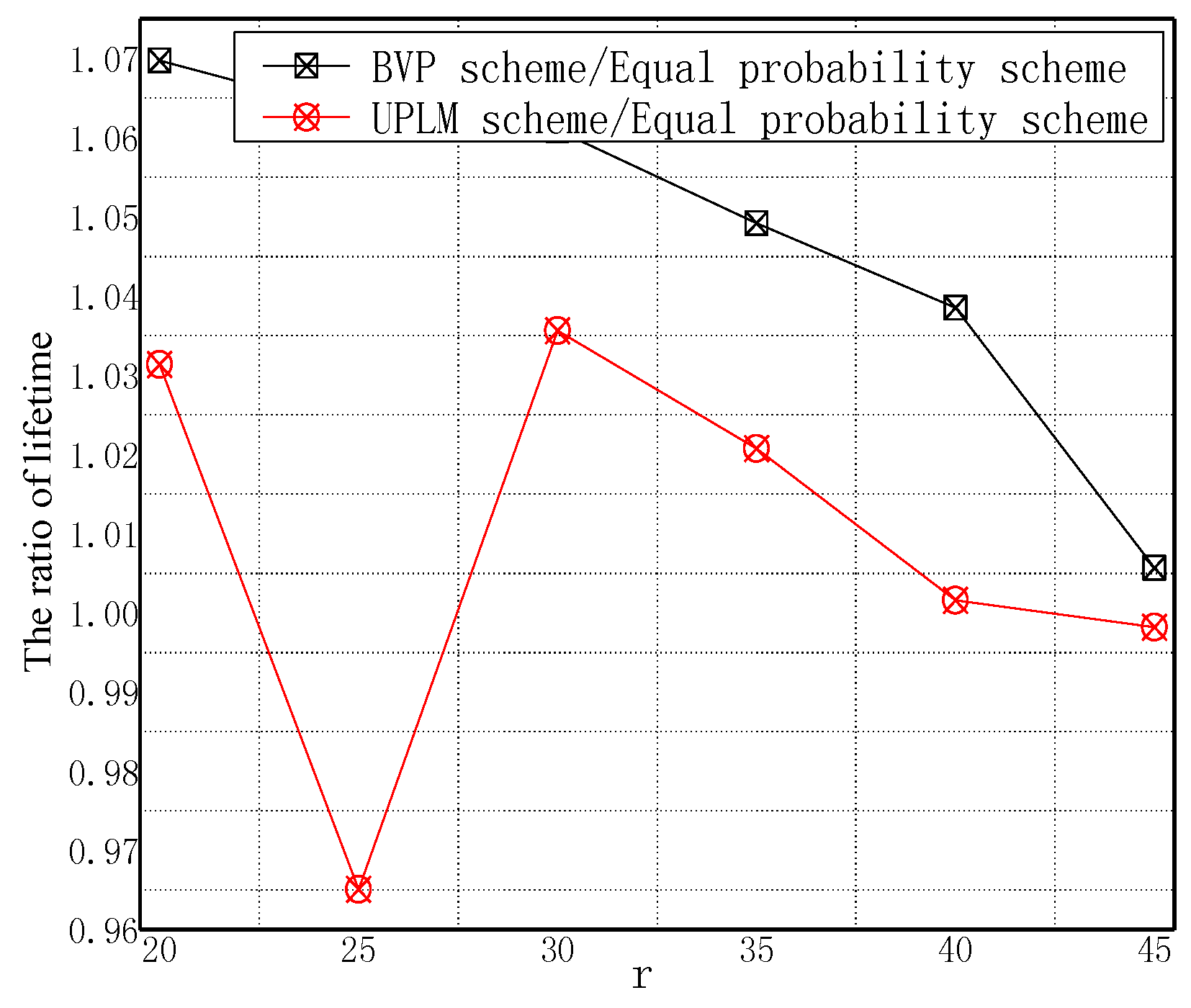
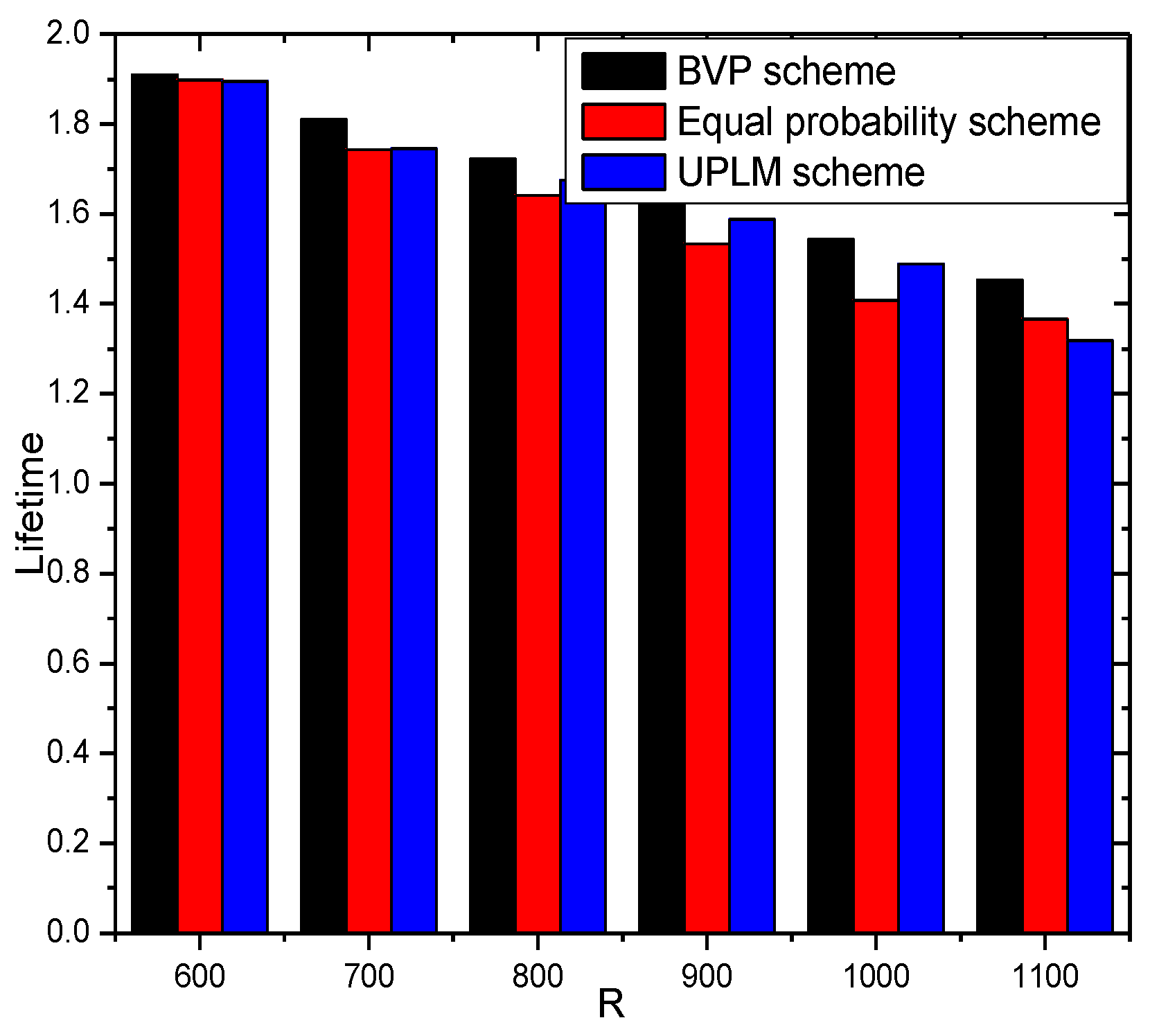
5.2. Energy Consumption and Network Lifetime
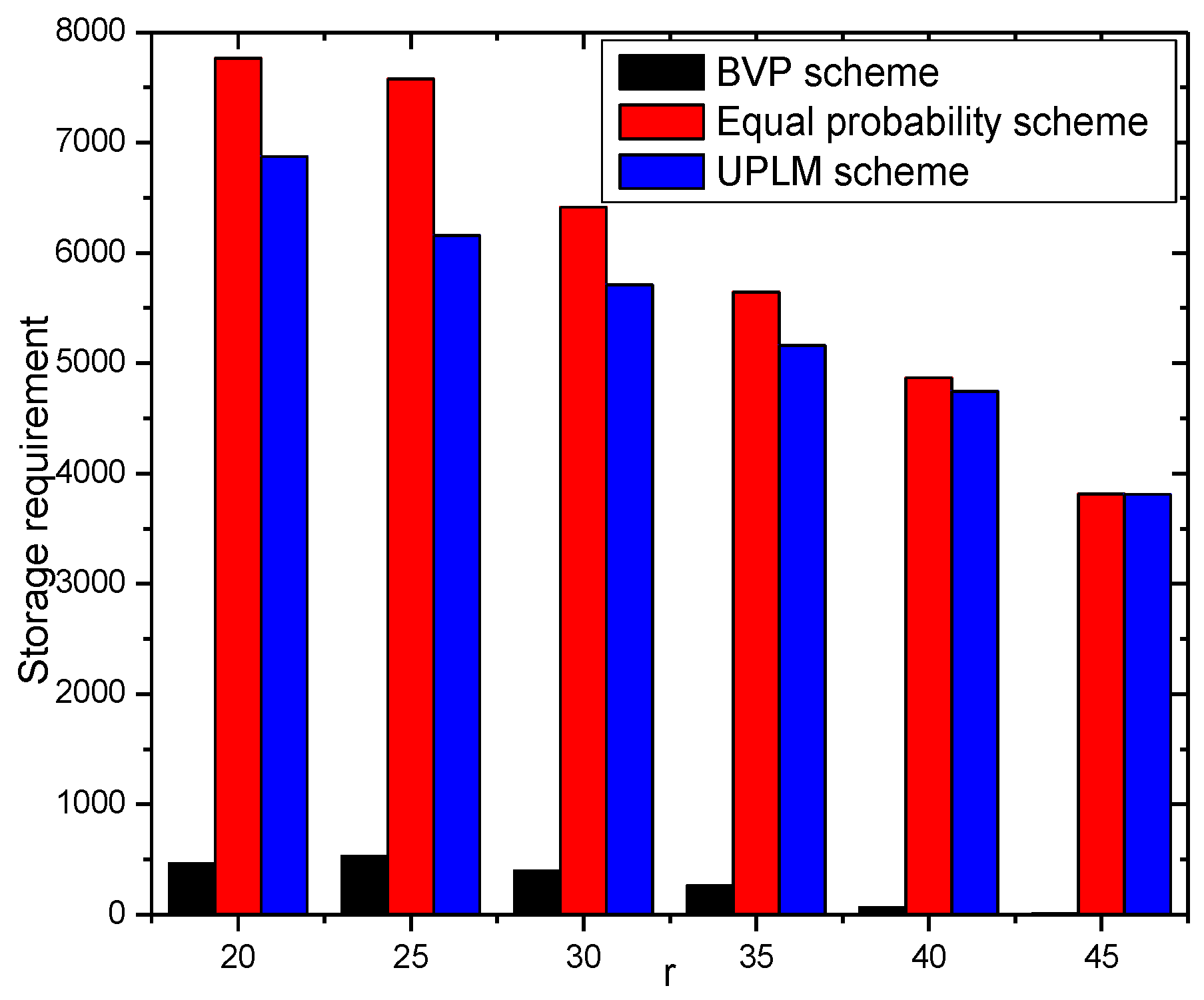
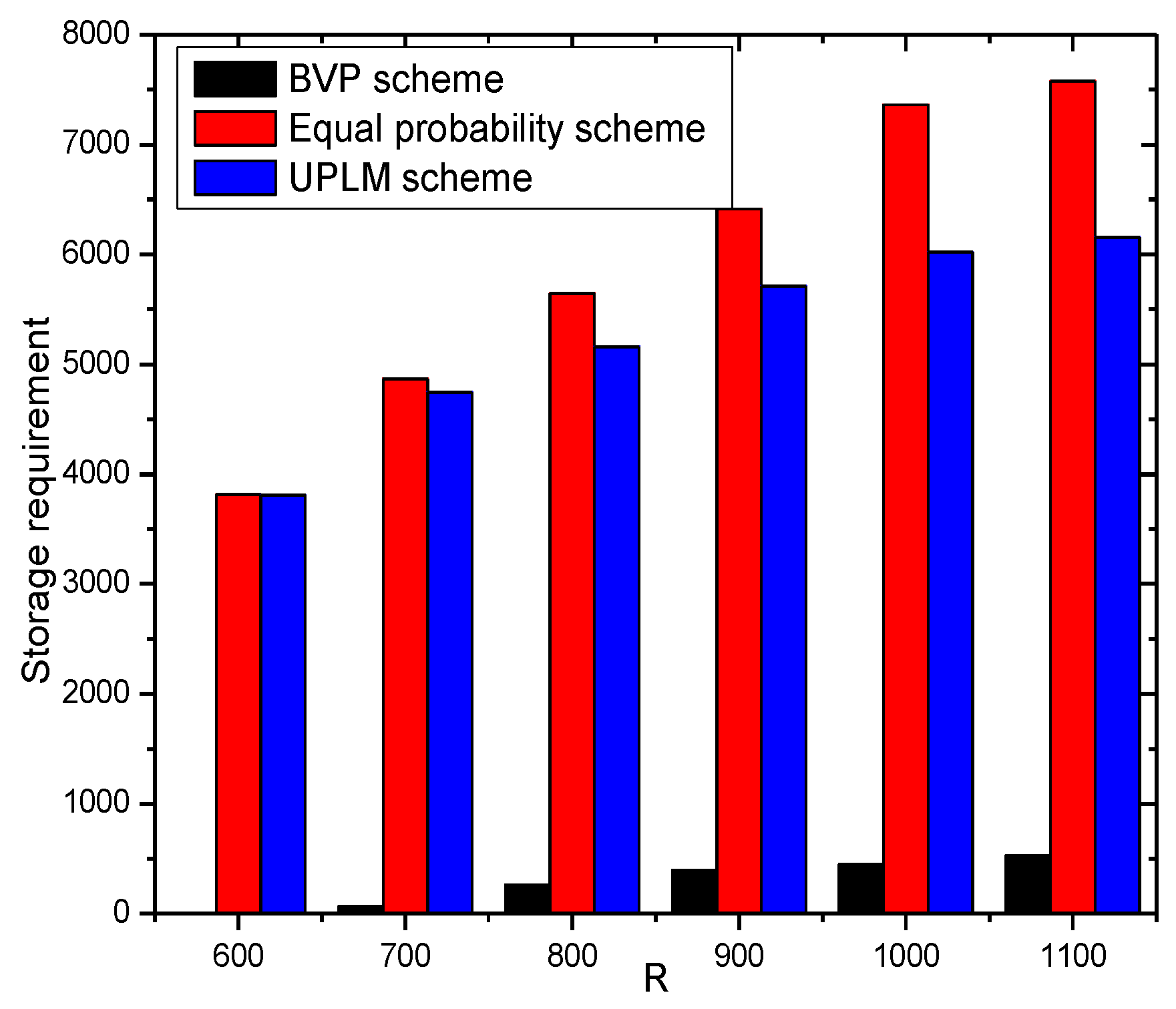
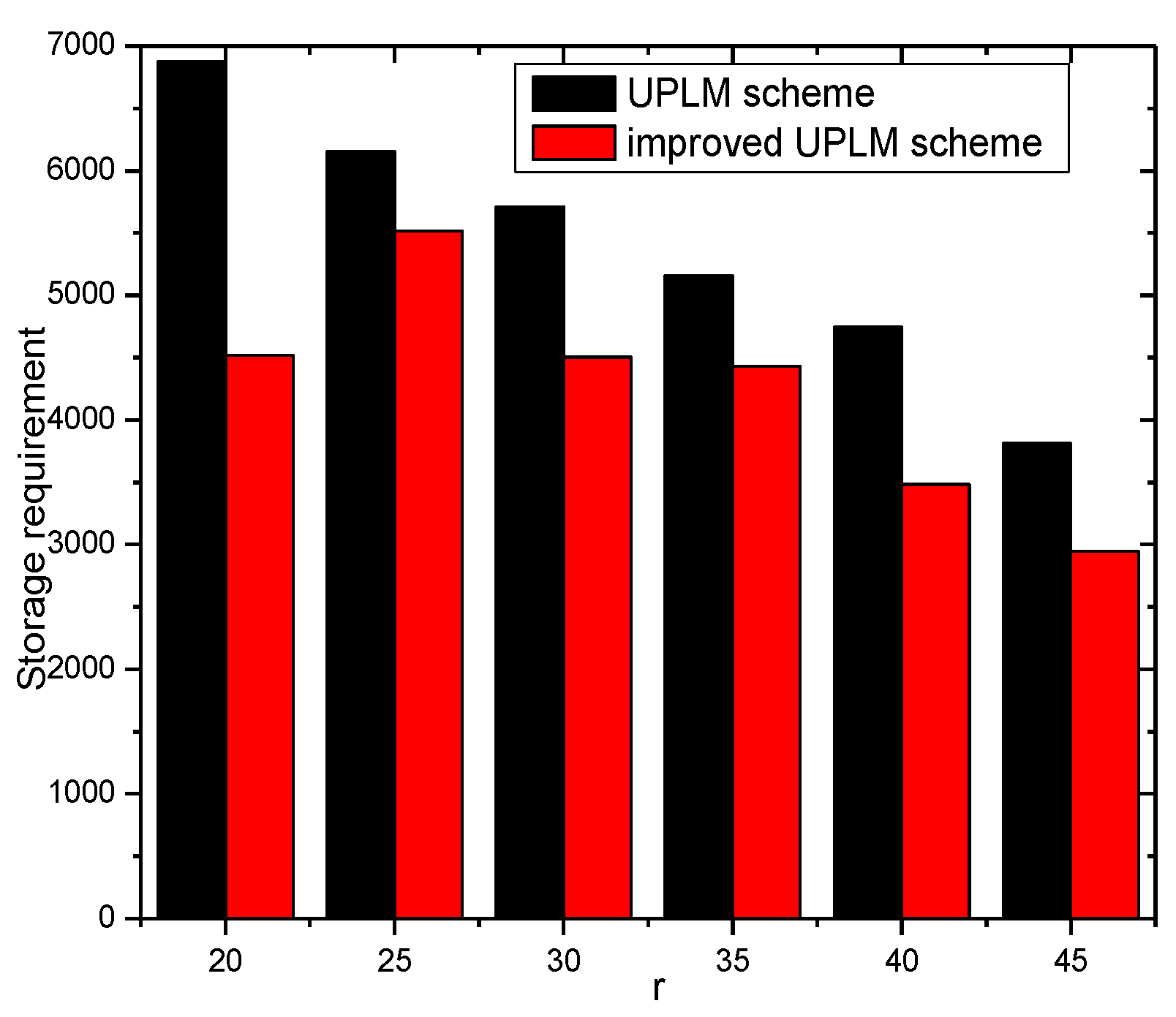
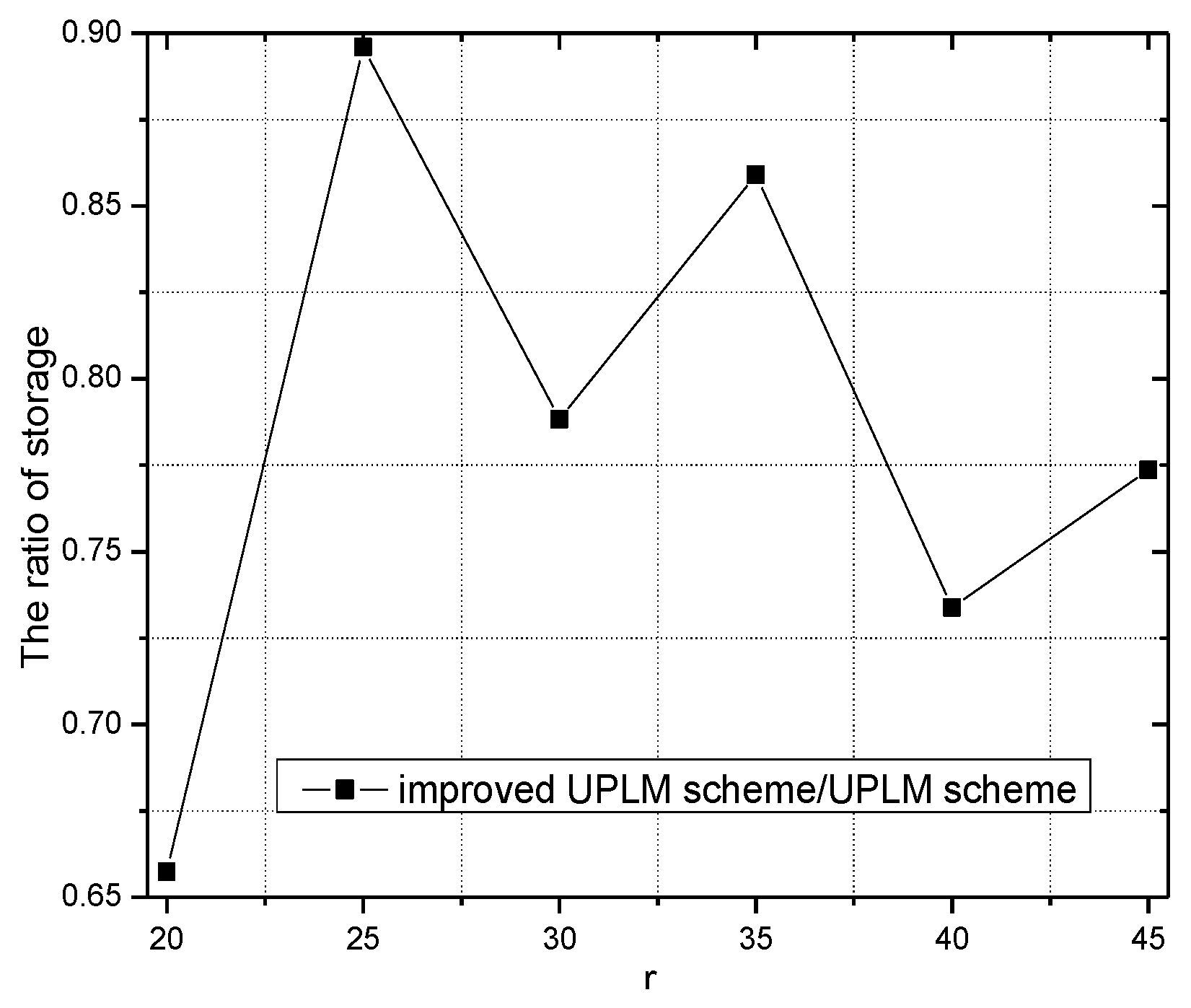
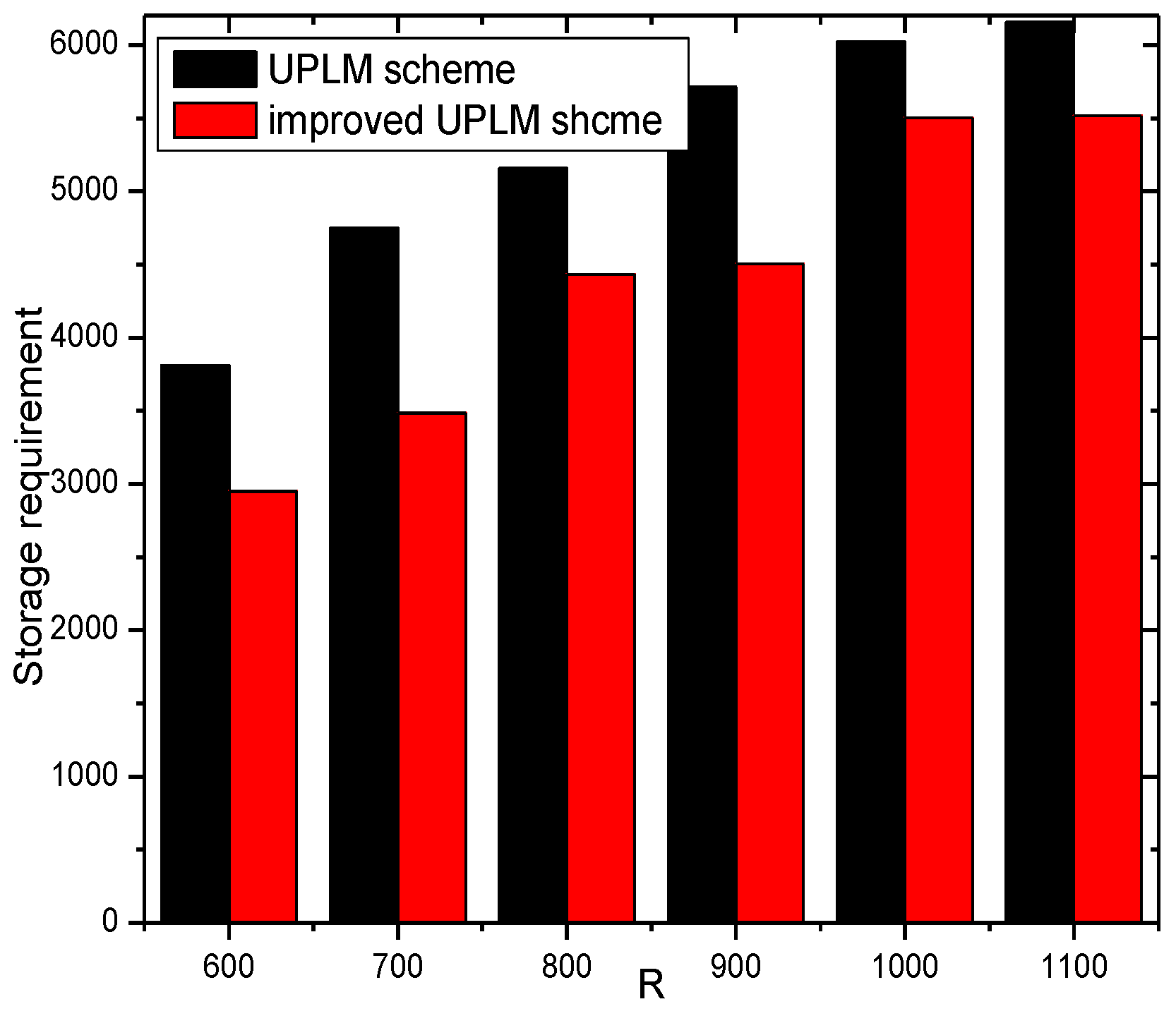
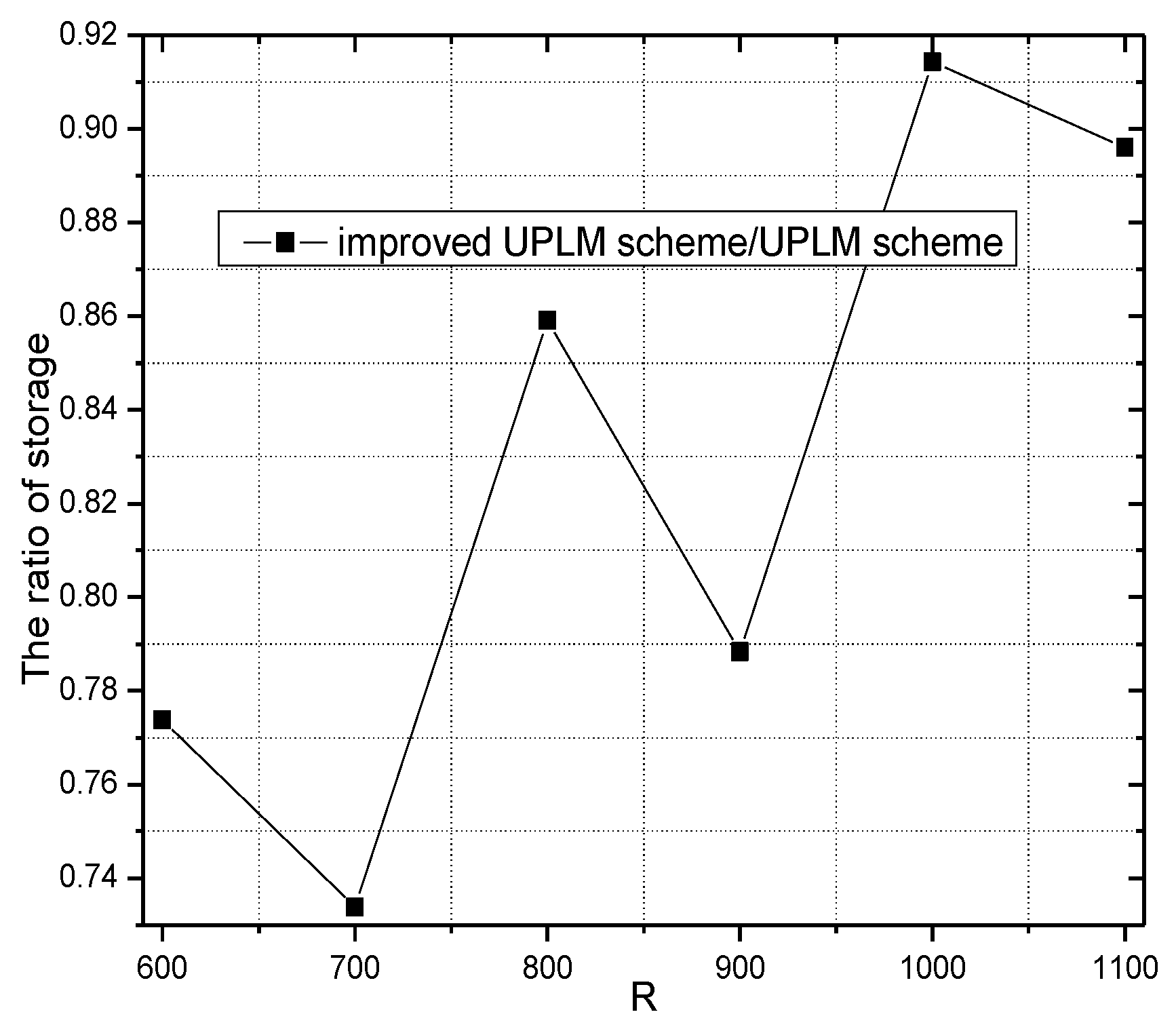
5.3. Analysis of Storage Capacity
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Sarkar, S.; Misra, S. Theoretical modelling of fog computing: A green computing paradigm to support IoT applications. IET Netw. 2016, 5, 23–29. [Google Scholar] [CrossRef]
- Hu, Y.; Dong, M.; Ota, K.; Liu, A.; Guo, M. Mobile Target Detection in Wireless Sensor Networks with Adjustable Sensing Frequency. IEEE Syst. J. 2016, 10, 1160–1171. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Zhu, H.; Liang, X.; Shen, X. BECAN: A bandwidth-efficient cooperative authentication scheme for filtering injected false data in wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 32–43. [Google Scholar]
- Liu, A.; Liu, X.; Wei, T.; Yang, T.; Rho, S.; Paul, A. Distributed Multi-representative Re-Fusion approach for Heterogeneous Sensing Data Collection. ACM Trans. Embed. Comput. Syst. 2017. [Google Scholar] [CrossRef]
- Li, H.; Yang, Y.; Luan, T.H.; Liang, X.; Zhou, L.; Shen, X.S. Enabling fine-grained multi-keyword search supporting classified sub-dictionaries over encrypted cloud data. IEEE Trans. Depend. Secur. Comput. 2016, 13, 312–325. [Google Scholar] [CrossRef]
- Liu, X.; Dong, M.; Ota, K.; Hung, P.; Liu, A. Service Pricing Decision in Cyber-Physical Systems: Insights from Game Theory. IEEE Trans. Serv. Comput. 2016, 9, 186–198. [Google Scholar] [CrossRef]
- Su, Z.; Xu, Q.; Fei, M.; Dong, M. Game Theoretic Resource Allocation in Media Cloud with Mobile Social Users. IEEE Trans. Multimed. 2016, 18, 1650–1660. [Google Scholar] [CrossRef]
- Xu, Y.; Liu, A.; Huang, C. Delay-Aware Program Codes Dissemination Scheme in Internet of Everything. Mob. Inf. Syst. 2016. [Google Scholar] [CrossRef]
- Liu, X.; Liu, A.; Deng, Q.; Liu, H. Large-scale Programing Code Dissemination for Software Defined Wireless Networks. Comput. J. 2017. [Google Scholar] [CrossRef]
- Li, H.; Liu, D.; Dai, Y.; Luan, T.H. Engineering searchable encryption of mobile cloud networks: When QoE meets QoP. IEEE Wirel. Commun. 2015, 22, 74–80. [Google Scholar] [CrossRef]
- He, S.; Shin, D.; Zhang, J.; Chen, J.; Sun, Y. Full-view area coverage in camera sensor networks: Dimension reduction and near-optimal solutions. IEEE Trans. Veh. Technol. 2016, 65, 7448–7461. [Google Scholar] [CrossRef]
- Gui, J.; Hui, L.; Xiong, N. A Game-Based Localized Multi-Objective Topology Control Scheme in Heterogeneous Wireless Networks. IEEE Access 2017, 5, 2396–2416. [Google Scholar] [CrossRef]
- He, S.; Chen, J.; Li, X.; Shen, X.; Sun, Y. Mobility and intruder prior information improving the barrier coverage of sparse sensor networks. IEEE Trans. Mob. Comput. 2014, 13, 1268–1282. [Google Scholar]
- Xu, Q.; Su, Z.; Guo, S. A game theoretical incentive scheme for relay selection services in mobile social networks. IEEE Trans. Veh. Technol. 2016, 65, 6692–6702. [Google Scholar] [CrossRef]
- Li, T.; Liu, A.; Huang, C. A Similarity Scenario-based Recommendation Model with Small Disturbances for Unknown Items in Social Networks. IEEE Access 2016. [Google Scholar] [CrossRef]
- Chen, Z.; Liu, A.; Li, Z.; Choi, Y.; Li, J. Distributed Duty Cycle Control for Delay Improvement in Wireless Sensor Networks. Peer Peer Netw. Appl. 2017, 10, 559–578. [Google Scholar] [CrossRef]
- Chen, X.; Xu, Y.; Liu, A. Cross Layer Design for Optimal Delay, Energy Efficiency and Lifetime in Body Sensor Networks. Sensors 2017, 17, 900. [Google Scholar] [CrossRef]
- Liu, X.; Liu, A.; Huang, C. Adaptive Information Dissemination Control to Provide Diffdelay for Internet of Things. Sensors 2017, 17, 138. [Google Scholar] [CrossRef]
- Zeng, D.; Li, P.; Guo, S.; Miyazaki, T.; Hu, J.; Xiang, Y. Energy minimization in multi-task software-defined sensor networks. IEEE Trans. Comput. 2015, 64, 3128–3139. [Google Scholar] [CrossRef]
- Liu, X.; Dong, M.; Ota, K.; Yang, L.T.; Liu, A. Trace malicious source to guarantee cyber security for mass monitor critical infrastructure. J. Comput. Syst. Sci. 2016. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, A.; He, S. A novel joint logging and migrating traceback scheme for achieving low storage requirement and long lifetime in WSNs. AEU-Int. J. Electron. Commun. 2015, 69, 1464–1482. [Google Scholar] [CrossRef]
- Lu, R.; Lin, X.; Liang, X.; Shen, X. A dynamic privacy-preserving key management scheme for location-based services in vanets. IEEE Trans. Intell. Transp. Syst. 2012, 13, 127–139. [Google Scholar] [CrossRef]
- Dong, M.; Ota, K.; Yang, L.T.; Liu, A.; Guo, M. LSCD: A Low Storage Clone Detecting Protocol for Cyber-Physical Systems. IEEE Trans. Comput. Aided Des. Integr. Circuits Syst. 2016, 35, 712–723. [Google Scholar] [CrossRef]
- Li, H.; Lin, X.; Yang, H.; Liang, X.; Lu, R.; Shen, X. EPPDR: An efficient privacy-preserving demand response scheme with adaptive key evolution in smart grid. IEEE Trans. Parallel Distrib. Syst. 2014, 25, 2053–2064. [Google Scholar] [CrossRef]
- Wong, T.Y.; Law, K.T.; Lui, J.C.; Wong, M.H. An efficient distributed algorithm to identify and traceback ddos traffic. Comput. J. 2006, 49, 418–442. [Google Scholar] [CrossRef]
- Liu, Y.; Dong, M.; Ota, K.; Liu, A. ActiveTrust: Secure and Trustable Routing in Wireless Sensor Networks. IEEE Trans. Inf. Forensics Secur. 2016, 11, 2013–2027. [Google Scholar] [CrossRef]
- Jeong, E.; Lee, B. An IP Traceback Protocol using a Compressed Hash Table, a Sinkhole router and data mining based on network forensics against network attacks. Future Gener. Comp. Syst. 2014, 33, 42–52. [Google Scholar] [CrossRef]
- Siddiqui, M.S.; Obaid, A.S.; Hong, C.S. Hop-by-hop traceback in wireless sensor networks. IEEE Commun. Lett. 2012, 16, 242–245. [Google Scholar] [CrossRef]
- Xu, J.; Zhou, X.; Yang, F. Traceback in wireless sensor networks with packet marking and logging. Front. Comput. Sci. China 2011, 5, 308–315. [Google Scholar] [CrossRef]
- Cheng, B.C.; Chen, H.; Li, Y.J.; Tseng, R.Y. A packet marking with fair probability distribution function for minimizing the convergence time in wireless sensor networks. Comput. Commun. 2008, 31, 4352–4359. [Google Scholar] [CrossRef]
- Huang, C.; Ma, M.; Liu, Y.; Liu, A. Preserving Source Location Privacy for Energy Harvesting WSNs. Sensors 2017, 17, 724. [Google Scholar] [CrossRef]
- Lin, X.; Lu, R.; Shen, X.; Kato, N. SAGE: A strong privacy-preserving scheme against global eavesdropping for ehealth systems. IEEE J. Sel. Areas Commun. 2009, 27, 365–378. [Google Scholar]
- Dong, M.; Ota, K.; Liu, A. RMER: Reliable and Energy Efficient Data Collection for Large-scale Wireless Sensor Networks. IEEE Internet Things J. 2016, 3, 511–519. [Google Scholar] [CrossRef]
- He, S.; Li, X.; Chen, J.; Cheng, P.; Sun, Y.; Simplot-Ryl, D. EMD: Energy-Efficient P2P Message Dissemination in Delay-Tolerant Wireless Sensor and Actor Networks. IEEE J. Sel. Areas Commun. 2013, 31, 75–84. [Google Scholar]
- Chen, Z.; Liu, A.; Li, Z.; Choi, Y.-J.; Sekiya, H.; Li, J. Energy-efficient Broadcasting Scheme for Smart Industrial Wireless Sensor Networks. Mob. Inf. Syst. 2017. [Google Scholar] [CrossRef]
- Xu, Y.; Chen, X.; Liu, A.; Hu, C. A Latency and Coverage Optimized Data Collection Scheme for Smart Cities Based on Vehicular Ad-hoc Networks. Sensors 2017, 17, 888. [Google Scholar] [CrossRef]
- Hsueh, C.H.; Wen, C.; Ouyang, Y.C. A. Secure Scheme against Power Exhausting Attacks in Hierarchical Wireless Sensor Networks. IEEE Sens. J. 2015, 15, 3590–3602. [Google Scholar] [CrossRef]
- Liu, A.; Zheng, Z.; Zhang, C.; Chen, Z.; Shen, X. Secure and energy-efficient disjoint multipath routing for WSNs. IEEE Trans. Veh. Technol. 2012, 61, 3255–3265. [Google Scholar] [CrossRef]
- Villas, L.A.; Boukerche, A.; Ramos, HS.; de Oliveira, H.A.B.F.; de Araujo, R.B.; Loureiro, A.A.F. DRINA: A lightweight and reliable routing approach for in-network aggregation in wireless sensor networks. IEEE Trans. Comput. 2013, 62, 676–689. [Google Scholar] [CrossRef]
- Wang, J.; Hu, C.; Liu, A. Comprehensive Optimization of Energy Consumption and Delay Performance for Green Communication in Internet of Things. Mob. Inf. Syst. 2017. [Google Scholar] [CrossRef]
- Li, T.; Zhao, M.; Liu, A.; Huang, C. On Selecting Vehicles as Recommenders for Vehicular Social Networks. IEEE Access 2017. [Google Scholar] [CrossRef]
- Liu, A.; Li, X.; Tang, Z.; Yang, L.T.; Shao, Z. Preserving Smart Sink Location Privacy with Delay Guaranteed Routing Scheme for WSNs. ACM Trans. Embed. Comput. Syst. 2017, 16, 68. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, A.; Guo, A.; Li, Z.; Choi, Y.; Sekiy, H. Context-aware collect data with energy efficient in Cyber-physical cloud systems. Future Gener. Comput. Syst. 2017. [Google Scholar] [CrossRef]
- Varga, A. The OMNET++ Discrete Event Simulation System, Version 4.1. Available online: http://www.omnetpp.org (accessed on 24 March 2016).





| Parameter | Value |
|---|---|
| Threshold distance (d0) (m) | 87 |
| Sensing range rs (m) | 15 |
| Eelec (nJ/bit) | 50 |
| efs (pJ/bit/m2) | 10 |
| eamp (pJ/bit/m4) | 0.0013 |
| Initial energy (J) | 0.5 |
© 2017 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Huang, C.; Ma, M.; Liu, X.; Liu, A.; Zuo, Z. Unequal Probability Marking Approach to Enhance Security of Traceback Scheme in Tree-Based WSNs. Sensors 2017, 17, 1418. https://doi.org/10.3390/s17061418
Huang C, Ma M, Liu X, Liu A, Zuo Z. Unequal Probability Marking Approach to Enhance Security of Traceback Scheme in Tree-Based WSNs. Sensors. 2017; 17(6):1418. https://doi.org/10.3390/s17061418
Chicago/Turabian StyleHuang, Changqin, Ming Ma, Xiao Liu, Anfeng Liu, and Zhengbang Zuo. 2017. "Unequal Probability Marking Approach to Enhance Security of Traceback Scheme in Tree-Based WSNs" Sensors 17, no. 6: 1418. https://doi.org/10.3390/s17061418
APA StyleHuang, C., Ma, M., Liu, X., Liu, A., & Zuo, Z. (2017). Unequal Probability Marking Approach to Enhance Security of Traceback Scheme in Tree-Based WSNs. Sensors, 17(6), 1418. https://doi.org/10.3390/s17061418






