1. Introduction
Supporting Internet of Things (IoT) services is emerging as one of the most important problems facing communication systems [
1,
2]. There are many applications, such as public safety, e-health, fleet management, and smart metering [
1], that will use machine-to-machine (M2M) communication technology, which ensures connectivity to the devices without human interaction
Cellular networks are expected to play a major role in enabling M2M communications because they can provide seamless coverage over a large area, support mobility, and offer security. However, there are several problems with enabling M2M communications over cellular networks because these networks are optimized for human-to-human (H2H) communications and the characteristics of M2M communications are different from those of conventional H2H communications. For example, M2M communications are triggered by events, time-controlled, involve the transmission of small amounts of data, and are energy-limited [
3]. The 3rd Generation Partnership Project (3GPP) has studied the issues facing M2M services in cellular networks. In [
1], the 3GPP studied potential system improvements for M2M communications, the authors organized the architectural considerations and defined the expected problems for M2M communications. One of the most critical problems is congestion due to the massive access by M2M devices. The control plane at the radio-access-network (RAN) level suffers during massive access by M2M devices due to their characteristics. M2M devices try to establish a connection with an evolved node B (eNB) when they have data to transmit, causing a severe random access channel (RACH) congestion problem. The 3GPP suggested some solutions [
1], including an access class barring (ACB) scheme, a separate RACH resource-allocation scheme, a dynamic RACH resource-allocation scheme, and an M2M-specific back-off scheme.
Because RACH congestion due to massive access causes the degradation of RA throughput, increasing the RA throughput has become a major research target. The ACB method efficiently solves the RA throughput problem by controlling the access probabilities of separate access classes. In [
4], the authors suggested dynamic-ACB (D-ACB) to not only overcome the RACH congestion problem due to bursts of M2M traffic but also to reduce the total service time. The D-ACB determines the accurate ACB factor without backlog information. In [
5], a cooperative ACB (C-ACB) scheme was proposed to reduce the congestion in multi-cell cases. In this study, the ACB factors of each eNB were used for the eNB selection by M2M devices. Furthermore, the ACB factors were jointly determined among the neighboring eNBs. The access load could be distributed using the cooperative method. In [
6], timing-advance (TA) information was used to reduce the RA collision probability because the propagation delay between a stationary M2M device and the eNB is a constant. Hence, the authors assumed that the TA values in a random access response (Msg2) could be used as an identifier; therefore, some preamble collisions could be solved. Based on this, they proposed a TA-based ACB scheme for increasing RA throughput. In [
7], an ACB scheme for delay-sensitive devices is proposed. The authors consider the scenario where delay-sensitive and delay-tolerant services coexist. In addition, a priority-based ACB scheme adjusts dynamically the access probability and the number of preambles to satisfy the requirements of delay-sensitive services. In addition, delay-tolerant services can also be highly utilized based-on preamble allocation.
A preamble-separation method has also been proposed to increase the RA throughput. In [
8], two preamble-allocation methods for M2M/H2H services were studied. One method split the preambles into disjointed sets for M2M and H2H separately, while the other split them into an H2H-only set and an H2H/M2M-hybrid set. The authors modeled these methods and analyzed them in terms of throughput. In [
9], the authors analyzed the non-overlapping preamble separation, proposing the use of a load-adaptive throughput-maximizing preamble-allocation procedure, which automatically adjusted the preamble allocation to the priority classes, based on the access load. Both studies showed that the preamble–separation scheme increased the RA throughput, especially when the access load was heavy.
The energy consumption of M2M devices is also a very important issue because most M2M devices are vulnerable to energy consumption. Therefore, many studies have been conducted on the energy consumption of the RA process. In [
10], further improvement of traffic scattering for the group paging (FI-TSFGP) scheme was proposed to achieve high channel-access probability for M2M services. They also provided analysis of the scheme in terms of access latency and power consumption. Consequently, they argued that the FI-TSFGP scheme led to the reduction of both the channel access latency and the power consumption. In [
11], group-based access control was studied in terms of the energy consumption of M2M devices. The authors introduced a coordinator to reduce massive access. In addition, they proposed a joint massive access control and resource allocation scheme that minimized total energy consumption.
Analyzing the RA procedure is fundamental to understanding the RACH congestion problem and to providing the proper solutions. Various studies have analyzed an RA procedure to solve the RACH problem. These studies have mostly focused on the well-known multi-slotted Advocates of Linux Open-source Hawaii Association (ALOHA) model. The RA throughput, access delay, efficiency, and energy consumption of the RA procedure have been well analyzed using the multi-slotted ALOHA model [
4,
5,
6,
12,
13,
14]. However, these studies used the classical collision model to interpret RA nature, which assumes that no signal is decoded when multiple nodes transmit simultaneously. This model allows for simple analysis but does not yield accurate results due to the characteristics of wireless communications. Other studies have used the slotted-ALOHA system in a capture model [
15,
16]. This model assumed that a certain signal could be decoded when the received power of a specific signal was larger than a predefined threshold. Studies exploiting this model have provided more realistic results.
In this paper, we provide novel solution to resolve the RACH congestion problem due to massive access of M2M devices by exploiting the capture effect: Msg3 power ramping (PR) scheme. The main contributions of this paper are summarized as follows:
We formulated analysis models of the RA procedure considering the capture effect. Previous studies [
4,
5,
6,
12,
13,
14] adopted the collision model to analyze the RA procedure and assumed that the RA performance degradation due to the collisions of the preambles (Msg1) could not be prevented. However, we provide an RA analysis model that considers the capture effect. Therefore, we consider RA performance improvements due to the capture effect of the physical layer, even if the collision occurs. We provide an RA performance analysis model, in terms of the RA throughput, the connection failure probability, and the average energy consumption of the devices.
Exploiting the capture effect to improve the RA performances, we propose the Msg3 PR scheme. This scheme causes a difference in the received power of messages at the eNB, so that the capture effect occurs frequently. In addition, it is easy to apply because the proposed scheme adopts the power ramping scheme that has already been used in the cellular system. Moreover, by applying this new technique, a device that has performed many retransmissions would have a higher RA success probability; thus, the connection failure probability could be reduced.
In the simulation, we demonstrate the accuracy of proposed analysis and the advantages of the Msg3 PR scheme. In addition, the effects of various network parameters on the performance of the technology are demonstrated. Moreover, we discuss the beneficial points of the proposed scheme when used with other RA-related schemes.
The rest of the paper is organized as follows. In
Section 2, we introduce our system model. The motivation of this study and an introduction to the Msg3 PR scheme are presented in
Section 3. In
Section 4, we derive the analysis models for the RA procedure, considering the capture effect, and provide the performance of the proposed scheme, in terms of several performance metrics. In
Section 5, the simulation results demonstrate the performance of the Msg3 PR scheme and the accuracy of the proposed analysis. Finally,
Section 6 presents the conclusions.
3. Motivation and Proposed Scheme
The RACH congestion problem can be fatal for a network system and devices. As described in the RA procedure in
Section 2.1, a collision occurs when multiple devices select the same preamble and send their Msg1s. Because this Msg1 collision cannot be detected by the eNB during the Msg1 reception, these devices suffer from an Msg3 collision that also wastes the PUSCH resources. Moreover, the congestion problem gets worse due to the retransmission by the RA-failed devices and can even cause a connection failure. In summary, the RACH congestion problem causes (1) degradation of the RACH throughput, (2) increased probability of connection failures, and (3) wasting of the uplink resources (PUSCH). Exploiting the capture effect positively affects the network system [
15,
16]. Intuitively, the RACH congestion problem can also benefit from exploiting the capture effect. Even though collisions occur, if an Msg3 of a specific device is captured, the eNB can send an Msg4 to the device, and, therefore, the device would successfully connect. The received signal powers at the eNB are differentiated to exploit the capture effect. However, as seen in Equation (
4), there is no difference between the target powers of the received signals when perfect power control for M2M devices is performed. Hence, we propose adopting a power ramping scheme for Msg3 transmission to exploit the capture effect. The proposed scheme leads the device to transmit at higher power as more retransmissions occur. There are some advantages using the power ramping scheme: first, it is easy to implement because it has been adopted for Msg1 transmission; and, second, the more retransmitted devices there are, the higher the probability of being captured, reducing the probability of connection failure. Because the proposed scheme uses a power-ramping scheme, the Msg3 transmission power can be reformulated as follows:
As a result, the received power can be differentiated based on the ramping number (r) of the device.
4. Analysis Model
Intuitively, the Msg3 PR will have a positive effect on the probability of RA success because it helps the eNB capture the Msg3, even in a collision situation. However, it is necessary to analyze how the proposed scheme is affected by the network parameters and to analyze negative aspects of the scheme, such as the increased energy consumption of the devices. In this section, we propose an RA procedure analysis model that considers the capture effect in the Msg3 reception. For mathematical tractability, we assume that network is in a steady-state (in [
4,
10,
14], a heavily congested network reaches a steady-state. In other words, the number of arrivals of retransmitted devices is much greater than the number of new arrivals. When the network is in a steady state, the network states (ex. the number of RA arrivals, the distribution of the trial numbers in the network, the number of RA successes at each RA procedure, etc.) are merely constant). We provide an analytic model for three performance metrics: RA throughput, connection failure probability, and average energy consumption. The RA throughput and connection failure probability demonstrate the positive effect of the proposed Msg3 PR scheme, while the average energy consumption is a potential negative effect of the proposed scheme.
Table 1 summarizes the notations used in this analysis.
4.1. System Model
We consider a single cell with radius
. Let
and
N denote the set of devices sending Msg1 to participate in RA at the same RA slot, and the size of
, respectively. Devices in
are uniformly distributed in a cell, hence,
which denotes the distance between the eNB and
u, follows a uniform distribution. A device
, which failed the RA procedure
times and participates in the
RA at this RA slot has a trial number
. Similarly,
denotes the ramping number of a device defined by Equation (
5) at the current RA slot. As seen in Equation (
5), the Msg3 transmission power of
u is upper-bounded by
as
. Note that
is related to
x. For simplicity,
can be defined using the log-distance path loss model without fading as
where
and
are the reference-path loss and distance, respectively. From the upper-bound condition and the path-loss model, the upper-bound of the ramping number of the device located at a distance
x from the eNB is as follows:
Definition 1. is the maximum allowable ramping number of a device located at a distance x from the eNB. Then, the ramping number of u, , can be defined as follows: However, Equation (
7) is hard to deal with. Hence, we introduce the concept of
zones for tractability as shown in
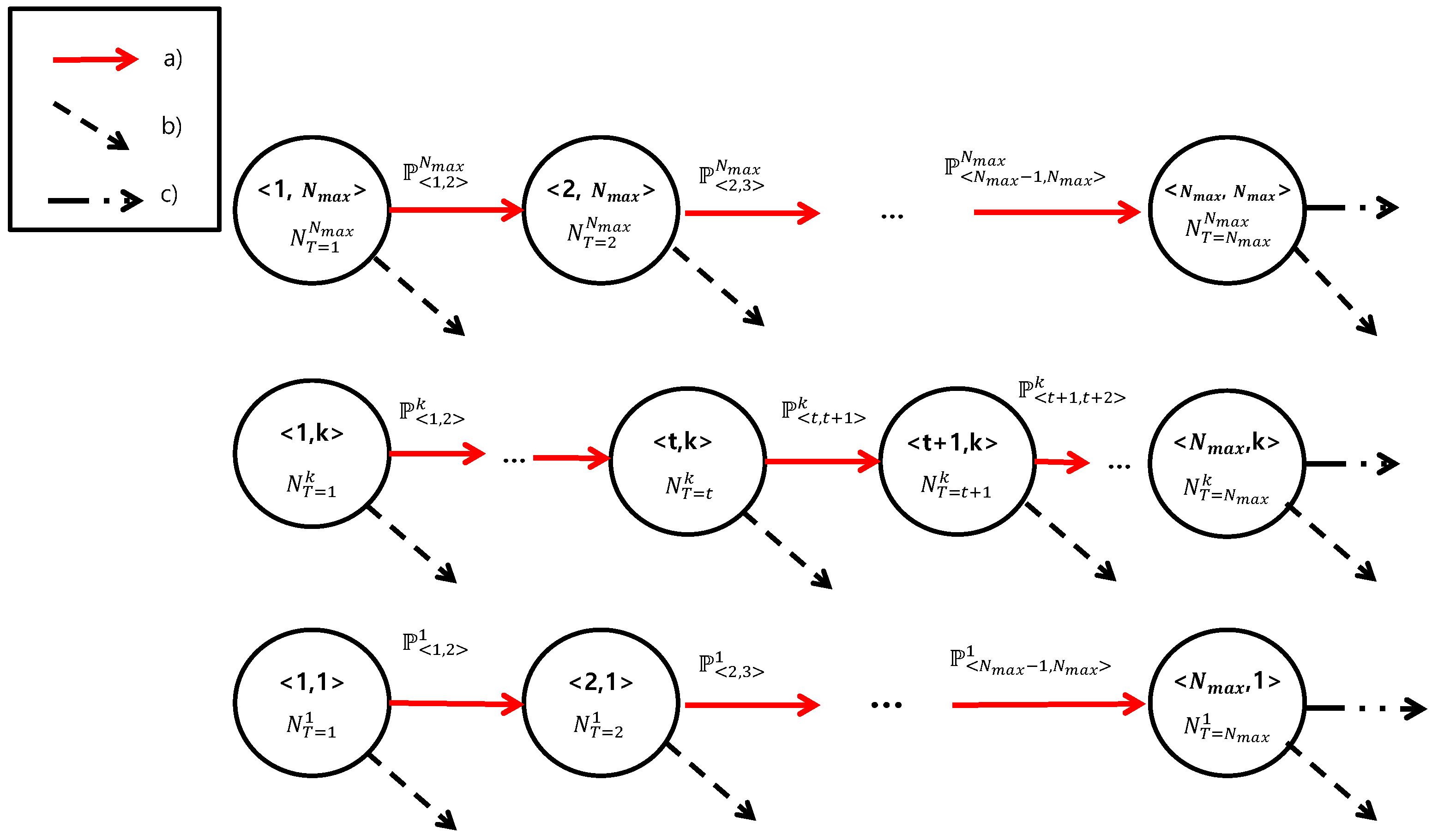
Figure 1.
Definition 2. Zone k is the area in which devices with are located. In addition, is the zone in which device u belongs. Thus, means that a device u is in zone k (also, u can only increase its ramping number up to k). Therefore, is the closet to the eNB, whereas 1 is the farthest from the eNB.
If the distribution of
is known (i.e., the distribution of devices in a cell), the probability that device
u belongs to
zone k,
, is (see
Figure 1)
Note that is a decreasing function for x. Therefore, there exists a boundary distance where .
Definition 3. is the expected number of devices having a trial number t that are located in zone k for and . Then, holds.
If for are given, we can define the distribution of the ramping number.
Definition 4. is the probability that a device has a ramping number r and is located in zone k; is the expected number of devices that have a trial number r and are located in zone k when N devices participate in the RA for and .
can be derived from
. Because the devices belonging to
zone k can only increase their ramping numbers to
k,
for
. Hence,
can be defined using
as follows:
Finally, the following two equations are derived.
where
is the distribution of the ramping number when the number of accesses is
N.
4.2. RA Throughput
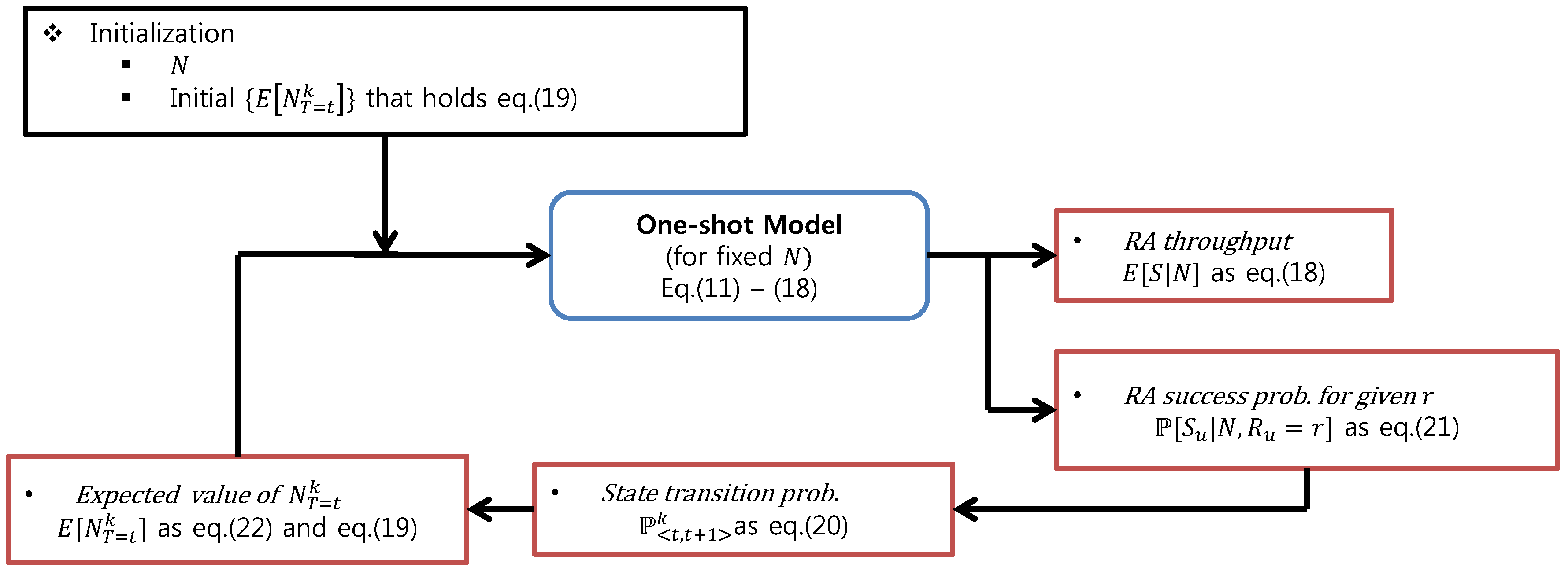
In this sub-section, we provide an analysis model for the RA throughput. First, we provide a one-shot model when N and for are given. Then, we demonstrate a steady-state RA throughput using the one-shot model because is affected by the RA success probability, as determined by the RA throughput.
4.2.1. One-Shot RA Throughput Analysis
Devices in
send an Msg1 that is randomly selected from
V preambles. Focusing on a certain device,
with
and
, and, therefore,
. Let
denote the preamble selected by device
u, and
denote the number of devices that select preamble
v among
excluding device
u. Then, the probability that device
u and
m devices in set
select preamble
v can be expressed as follows:
Next, we derive the probability that device
u succeeds in a RA (i.e., the Msg3 from
u is successfully decoded by the eNB), which we denote as the event
. Let the random variable
denote the received signal power from device
i at the eNB. Then, the event
occurs, even if
u collides with
m devices, when
meets the capture condition defined in Equation (
1). Hence, the conditional probability of (
) is
Since we assume that power control with full compensation of path loss is performed perfectly,
is a function of the ramping number as in Equation (
5). Therefore, the probability density function (PDF) of
follows the distribution of the ramping number
of the RA-participating devices as Equation (
10). In other words, the PDF of
is
Hence, the conditional probability in Equation (
12) is redefined as
:
where
is the Msg3 capture probability, which means the probability that device
u whose ramping number is
r is captured by the eNB when
m devices among
N devices collide with
u. Note that
is the capture probability when
u selects the singleton preamble, and therefore,
for any
N and
r. Because the PDF of
is defined, and is independent and identically distributed,
i.i.d., Equation (
14) can be solved using
the m-fold convolution of the PDF of
for given values of
and
r [
16].
Then, the following conditional probability can be obtained from Equations (
8), (
10) and (
14), and
the chain rule:
Note that (a)
is dependent of
, not
, (b)
is independent of
and
, and (c)
is independent of
, and
, so Equation (
15) holds.
From Equations (
11) and (
15), we have
Thus, the probability that an arbitrary device succeeds in RA when
N devices participate in the RA is
where
which denotes the capture probability of a device when it collides with
m devices among
N devices.
Consequently, we can obtain the one-shot RA throughput when
N devices participate in RA as
4.2.2. Steady-State RA Throughput Analysis Model
As seen in Equation (
14), the capture probability,
, is affected by the distribution of the ramping number
, which is determined by
as in Equation (
9). Therefore,
must first be obtained. Let us assume that the network is in a steady-state with a stable number of RA accesses
N at each RA slot; then, with a slight abuse of notation, we can still represent
N and
as steady-state values. Then, the following condition holds.
Note that
denotes the number of new arrivals. Now, we introduce a Markov chain model to determine the state of the devices, where state
presents those devices with a trial number
t and are located in
. If we assume that the M2M devices have no mobility, a state transition only occurs when a device (a) fails in RA and retries (from
to
), (b) succeeds in RA, or (c) fails in its connection set up.
Figure 2 presents this Markov chanin model. Then,
can be derived as follows:
where
Finally, we can obtain the steady-state value
using balance equation property.
Here, the first line of Equation (
21) holds because the locations of devices are uniformly distributed. From Equations (
21) and (
22),
can be obtained. In summary, the steady-state RA throughput for fixed the number of accesses,
N, can be obtained by the iterative procedure as in
Figure 3.
4.3. Connection Failure Probability
Connection failure probability is defined as the probability that a device fails to acquire connectivity by failing the RA process
times. Let
and
denote the conditional connection success and connection failure probabilities, respectively, of a device with a trial number
t for given
and total arrival
N, respectively. Therefore,
is equal to the probability that the device fails at RA
times, and finally succeeds in the
RA trial. Then,
where
is the simple notation of
, as defined in Equation (
20). Then, the connection failure event is same as the complementary event of the connection success cases. Thus,
can be derived as follows:
Finally, the connection failure probability,
, can be derived using Equation (
8) as follows:
4.4. Average Energy Consumption
4.4.1. Energy Consumption Model
An average energy consumption model for the devices needs to be defined to analyze the energy consumption of the proposed scheme. For the energy-consumption parameters, we have partially referenced the model used in [
10]. In [
10], the authors assumed that an RA collision is detected by the eNB during the Msg1 reception, whereas we assumed that a collision is detected when the eNB cannot decode Msg3. Therefore, we refer to and modify the energy consumption model defined in [
10]. In this study, the description of how parameters are defined is omitted. See [
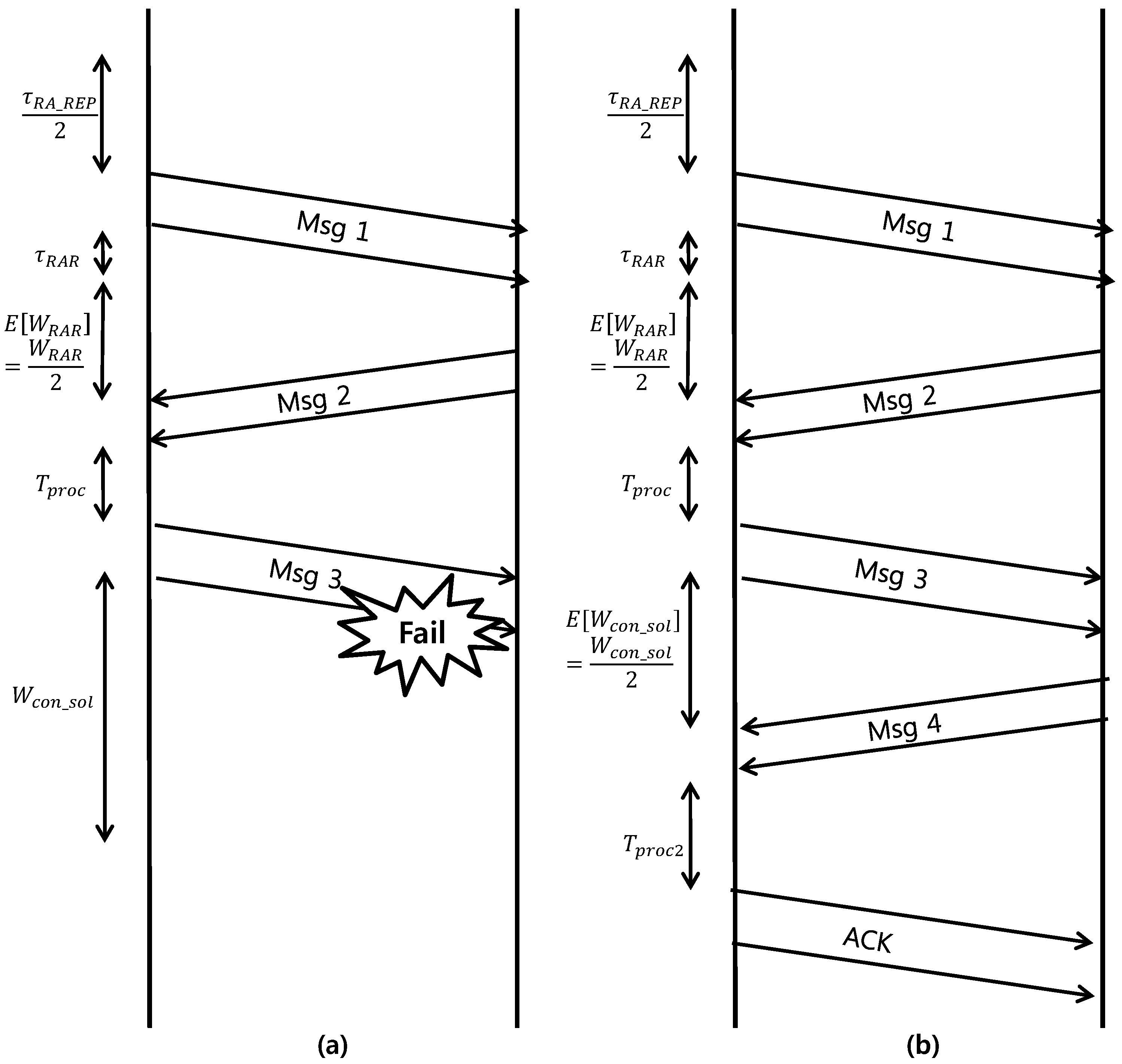
10] for a detailed description of the parameters. Instead, we provide simplified description in
Figure 4. Let
, and
denote the power consumption for waiting RA slot and performing back-off, receiving messages from the eNB, and transmission, respectively. Here, for analytic convenience, we assume that all transmission powers are equal, i.e.,
as in Equation (
5). Then, the average energy consumption for failed RA and successful RA events can be modeled as follows.
The energy consumed during a failed RA event is equal to that consumed in the following steps: waiting for the first RA slots(), transmitting Msg1 (), waiting for the RAR window (), wating for the Msg2 (), receiving the Msg2 (), processing time for Msg3 (), transmitting Msg3 (), and expiring the contention-resolution timer ().
The energy consumed during a successful RA event is equal to that consumed during the following steps. From transmitting Msg1 to receiving Msg2, the power consumed by the successful RA follows that consumed by the failed RA procedure and equals . In addition, the following steps are: for waiting Msg4 (), the power consumed when receiving Msg4 (), processing time for acknowledgement (ACK) (), and the power consumed by transmitting the ACK of Msg4 ().
Note that
terms denote the average time values. Parameter values in the above model are described in
Table 2.
4.4.2. Average Energy Consumption
and
denote the energy consumption for single failed and successful RA event, respectively. Note that
and
are random variables because
is the random variable that is determined by the trial number and the path-loss of device as in Equations (
5) and (
7). Therefore,
can be expressed as
, where
is the ramping component;
,
is the path-loss component, and
is the target power, which is a constant value. From the previously-described power consumption model,
and
can be simply expressed as follows:
where
, and
are constants defined by the consumption model. In the previous section, because the analysis was performed based on
rather than
, Equation (
26) can be reformulated as follows:
where
and
denote the average energy consumption of device, which is located within
with the trial number
t, having single failed and successful RA events, respectively. Here,
can be calculated using the average path-loss of the devices within
. Therefore,
where
is the ramping component where
,
is the average path-loss of devices in
.
The energy consumption of a device located within
that succeeds in acquiring a connection after a number
t of RA trials is denoted by
. Moreover,
denotes the energy consumption of a device located within
that fails to acquire a connection. Then,
and
can be derived as follows:
where
, which denotes the maximum ramping number of the device with
and
as defined in Equation (
7). Then, the average energy consumption of a device located within
when the total arrival is
N, i.e.,
, is calculated using Equations (
23) and (
24) as follows:
Finally,
is
5. Simulation Results
In this section, the simulation results are provided to show the performance of the proposed Msg3 PR scheme. A discrete event simulator is built to analyze the performance of the RA procedure and the effect of the capture. The simulator implements the RA procedure defined in
Section 2.1, and also implements the capture effects by adjusting the capture condition as Equation (
1).
Table 2 summarizes the commonly used simulation parameters in
Section 5.1 and
Section 5.2.
Through the analysis results defined in
Section 4 and the simulation results, the steady-state performances in terms of the RA throughput, the connection failure probability and the average energy consumption are presented in
Section 5.1. In
Section 5.2, the possibility of coexistence of the Msg3 PR scheme with other typical RA-related schemes is presented by showing simulation results.
5.1. Performance of the Msg3 PR Scheme
In this subsection, we present the analysis (Anal.) and simulation (Sim.) results of the Msg3 PR scheme when the network is in a steady-state. Because the steady-state analysis model defined in
Section 4 can be obtained when
N is determined, the simulations also performed with fixed
N. Therefore, we generate static new arrival at each RACH to converge the total arrival to
N. Moreover, the locations of newly arrived devices are determined by the uniform distribution.
The simulation model assumes a steady-state condition. In other words, the number of arrivals and the distribution of the trial and the ramping number of devices converge.
We show RA throughput performance in terms of , , and the number of preambles in an RACH, V. Furthermore, the connection failure probability analysis and the average energy consumption analysis according to change are additionally performed to further analyze the performance of Msg3 PR scheme. The performance metrics used in the study are defined as follows.
The RA throughput performance is evaluated in terms of
,
, and the number of preambles in a RACH,
V. Furthermore, analyses of the connection failure probability and the average energy consumption according to
change are additionally performed to further analyze the performance of the Msg3 PR scheme. Note that we use the same parameters relative to energy consumption model as in
Table 2 in the simulation. The performance metrics used in the study are defined as follows:
In each figure, the analysis results are displayed as lines, and the simulation results are displayed as markings if we performed both an analysis and a simulation.
5.1.1. The Consequences of the Capture Effect and Its Properties
Before discussing the performance metrics of the Msg3 PR scheme, we describe the consequences of the capture effect and its properties.
Table 3 shows the RA success probability for given ramping numbers defined as in Equation (
20), when the number of accesses is high, i.e.,
. As seen in
Table 3,
increases as
r increases. For example,
, whereas
when
dB. In addition,
, whereas
when
dB. In other words, the probability of RA success for a device with
is 5.7 times that of a device with
when
dB. Furthermore, in the case of
dB, the difference in the success probability is further increased to approximately 20.4 times. From
Table 3, the RA success probability increases as the Msg3 PR scheme uses higher
values.
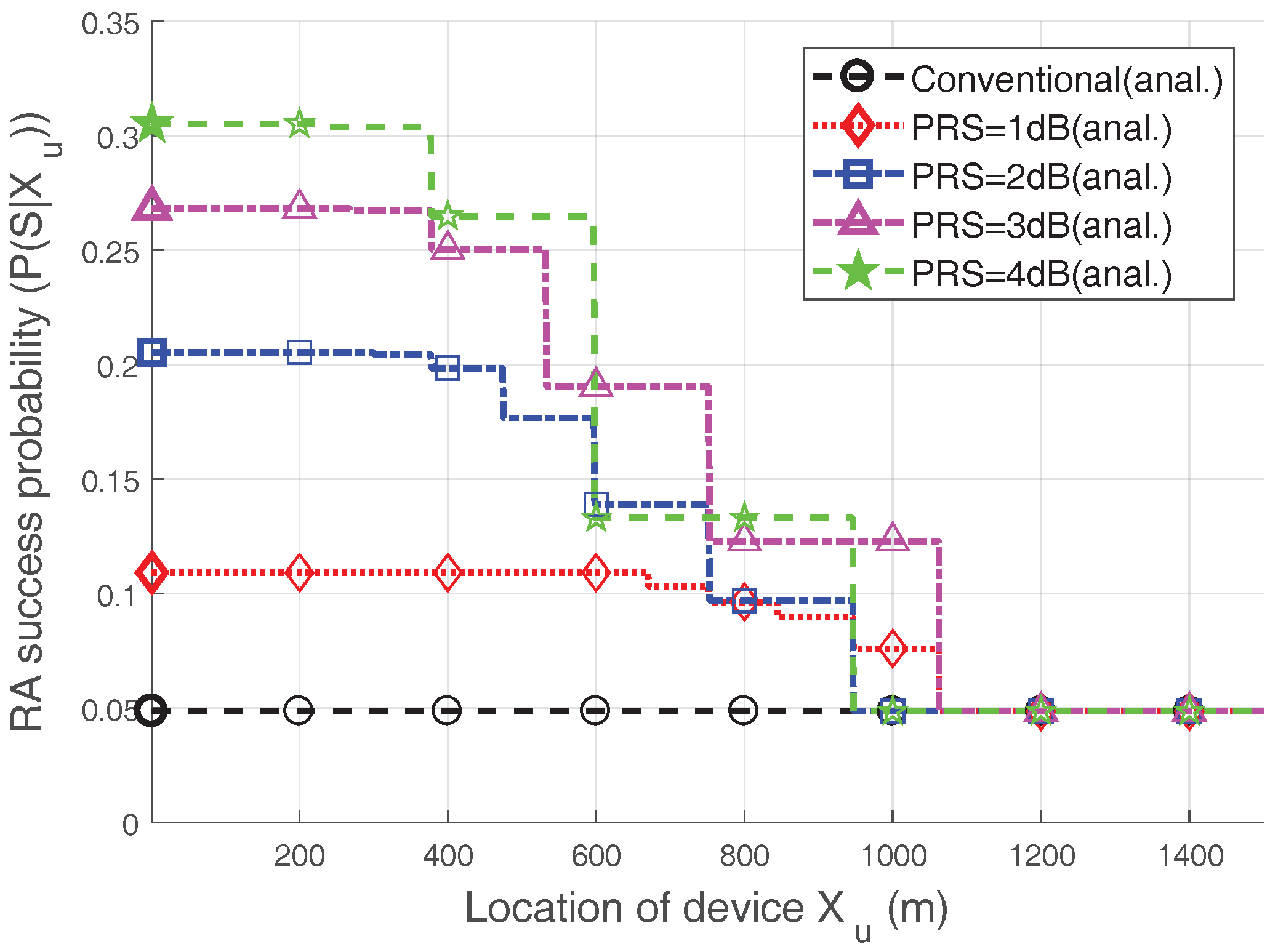
However, this is not always true, as seen in
Figure 5, which shows the RA success probability according to the location of the device. Note that the heavy-access load (
) case is considered, i.e.,
which can be derived from
. We observe that the RA success probability decreases as the device moves away from the eNB. This is because
defined in Equation (
6), decreases as
x increases, and thus, the capture probability declines. One interesting point in
Figure 5 is that the RA success probability is not necessarily high when the
is high; in other words, the trend noted in
Table 3 is not always true. Based on the distance, the RA success probability when
dB is often less than the RA success probability with
dB. Moreover, even when
x is between approximately 600 m and 700 m, the RA success probability for a
dB is lower than that with a
dB. The reason is that having too large of a
value in certain areas lowers the maximum ramping number, as seen in Equation (
6), and, therefore, the RA success probability can be decreased. As a result, as the
increases, the devices close to the eNB have a higher probability of being captured, while the devices further from the eNB cannot perform power ramping well due to their lower
. Hence, we can make an inference about performance: an increase in
does not necessarily lead to an increase in RA performance.
5.1.2. The RA Throughput
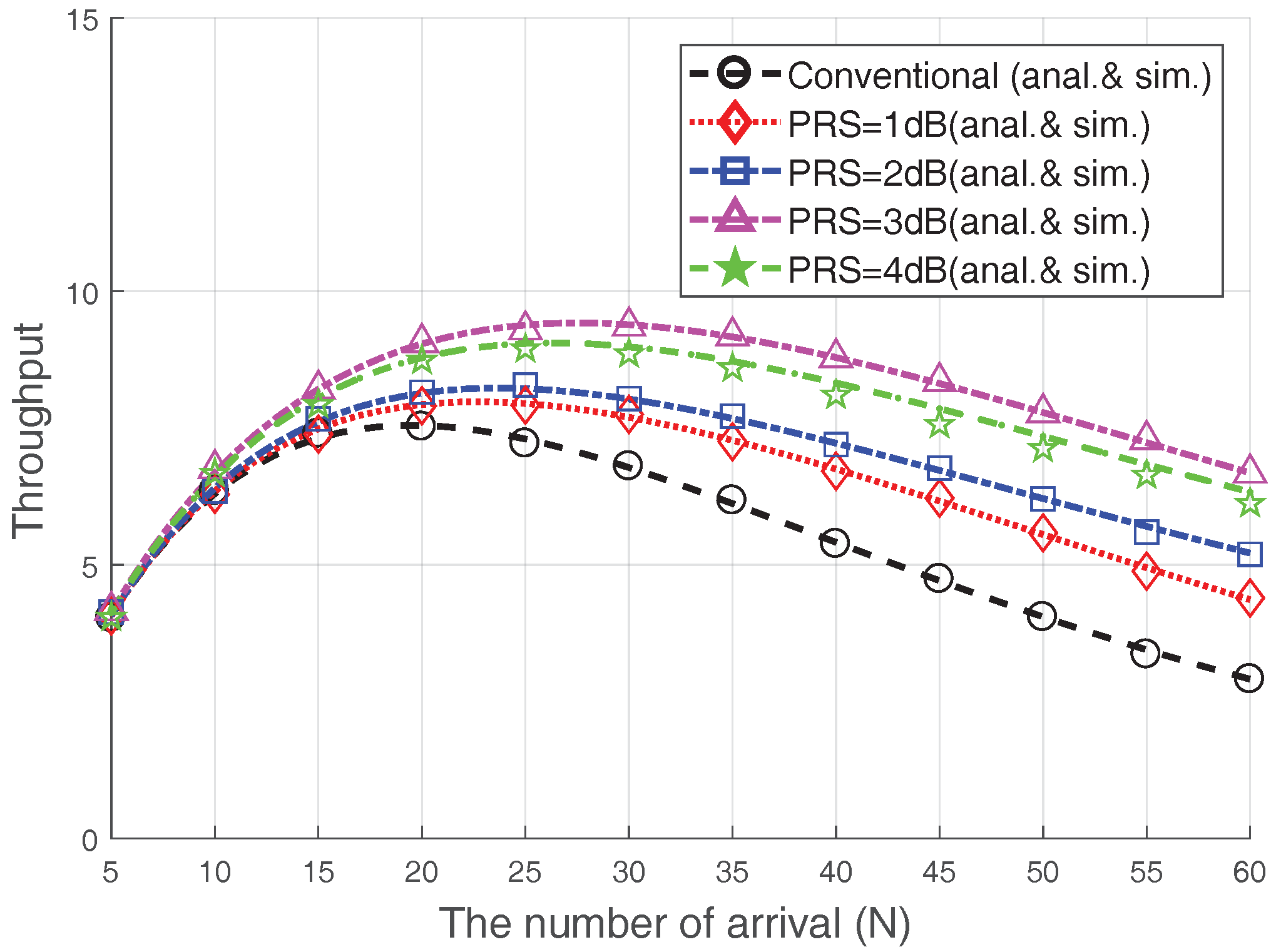
Figure 6 illustrates the RA throughput when the
is changed with
and
. In addition, we compare the performance of the conventional case, which does not consider the capture effect of Msg3 (i.e.,
) [
4,
5,
9,
14]. The RA throughput is clearly improved using the Msg3 PR scheme; particularly when heavy congestion occurs (i.e.,
), the RA throughput for
dB, 2 dB, 3 dB, and 4 dB is improved by approximately
, and
, respectively, as compared to the conventional case. This is due to the fact that the capture effect may occur among the devices that suffer from collisions that reduce the RA throughput, and the Msg3 PR can increase the capture probability. Note that the increase in
does not necessarily lead to an increase in RA throughput, as previously mentioned. In particular, the RA throughput in the case of 4 dB is lower than that in the case of
because the RA success probability of 4 dB-case is lower, as seen in
Figure 5. Therefore, it is important to choose a proper
value. For example, choosing
dB would be preferred in terms of the RA throughput.
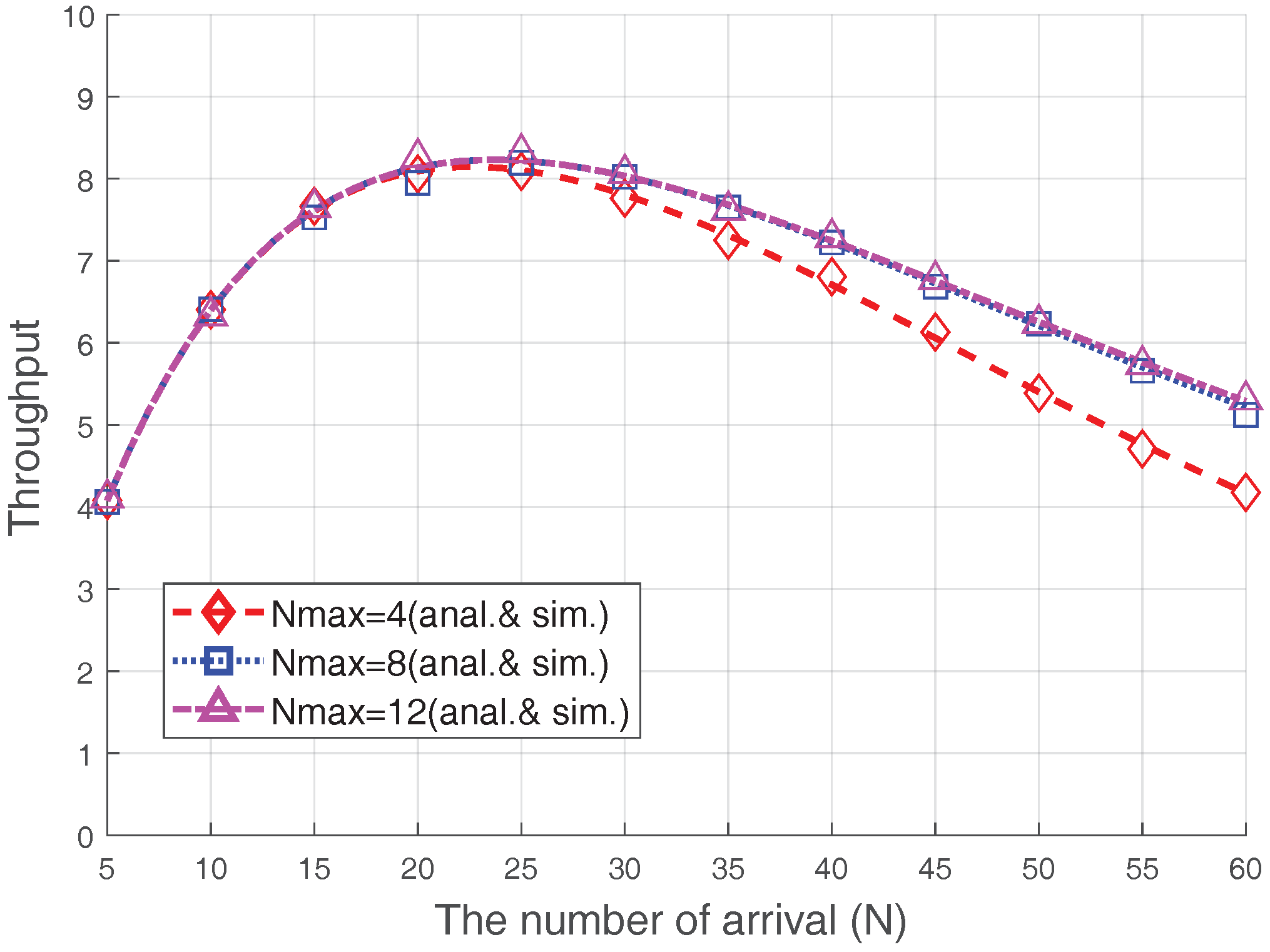
Figure 7 illustrates the effect of changes in
on the RA throughput when
dB and
. Comparing the RA throughputs in the cases when
and
, a throughput difference is observed when the number of accesses is large because, if the congestion level is not severe (
), retransmissions are not likely to occur more than four times. Hence, there is no throughput difference between these two cases. However, if the congestion level becomes severe, the trial number of most devices will reach to
due to severe collisions. Therefore, in this case, the probability of capture increases
is larger. However, this observation does not apply to the
case; the performance difference between the cases with
and 12 is negligible. This is due to the following reasons: (1) most devices (except the devices near the eNB) could not increase their ramping number enough due to the ramping number limitation,
, and (2) the devices near the eNB are often captured before the ramping number is significantly increased. As a result, if
becomes sufficiently large, the overall throughput is no longer affected.
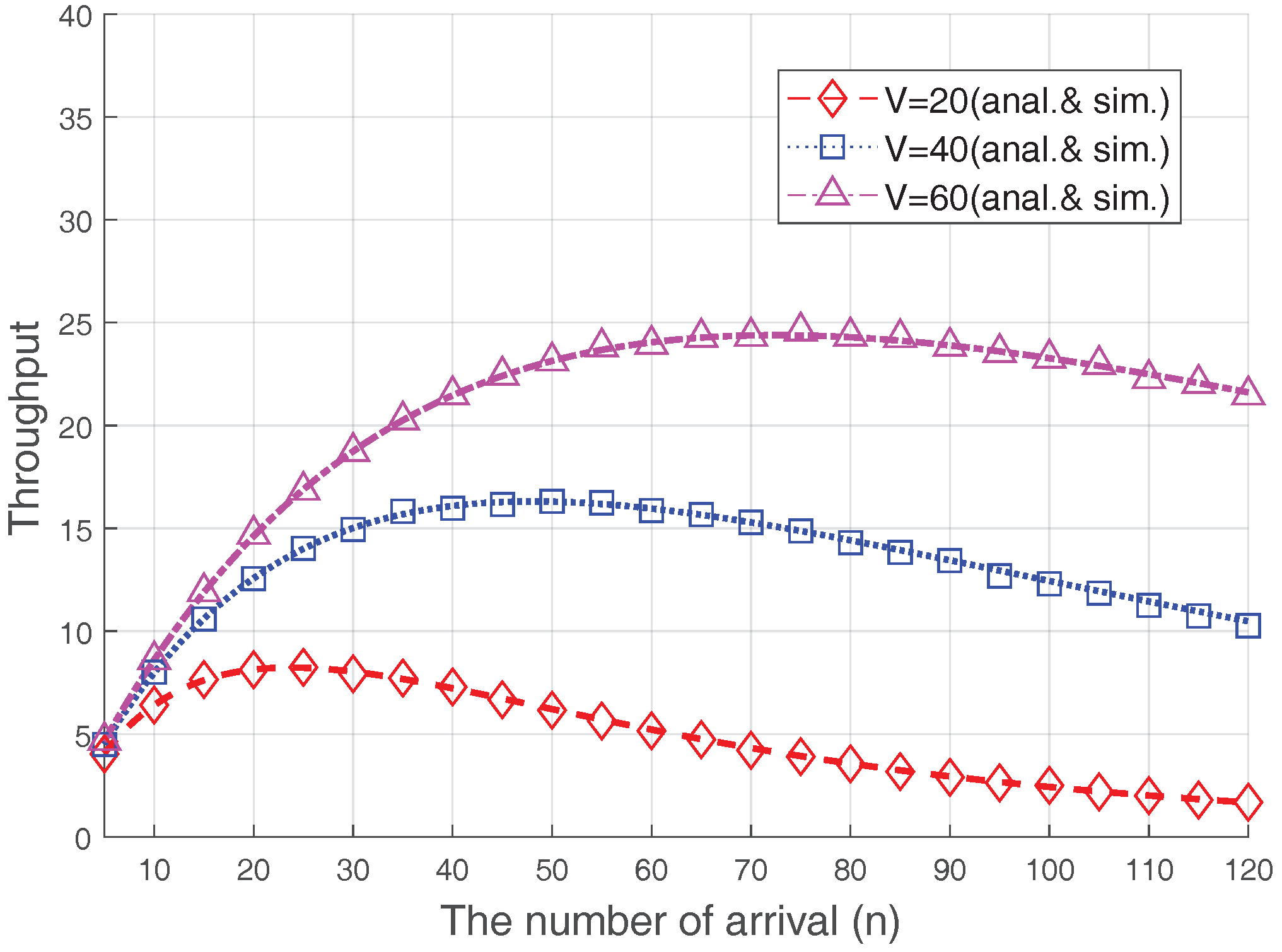
In
Figure 8, we also show the RA throughput varying with the size of the preamble set,
V, where
dB and
. As analyzed in other studies [
5,
6,
8,
12] (or, the conventional case in shown
Figure 6), the RA throughput is maximized when the number of accesses is the same as the preamble size, i.e.,
. However, if the Msg3 PR is used, the number of throughput-maximizing arrivals increases significantly. This result further demonstrates that, because of the capture effect on the RA procedure, optimization is needed if diverse RACH congestion-control schemes, such as ACB or M2M-specific back-off, are used.
5.1.3. The Connection Failure Probability
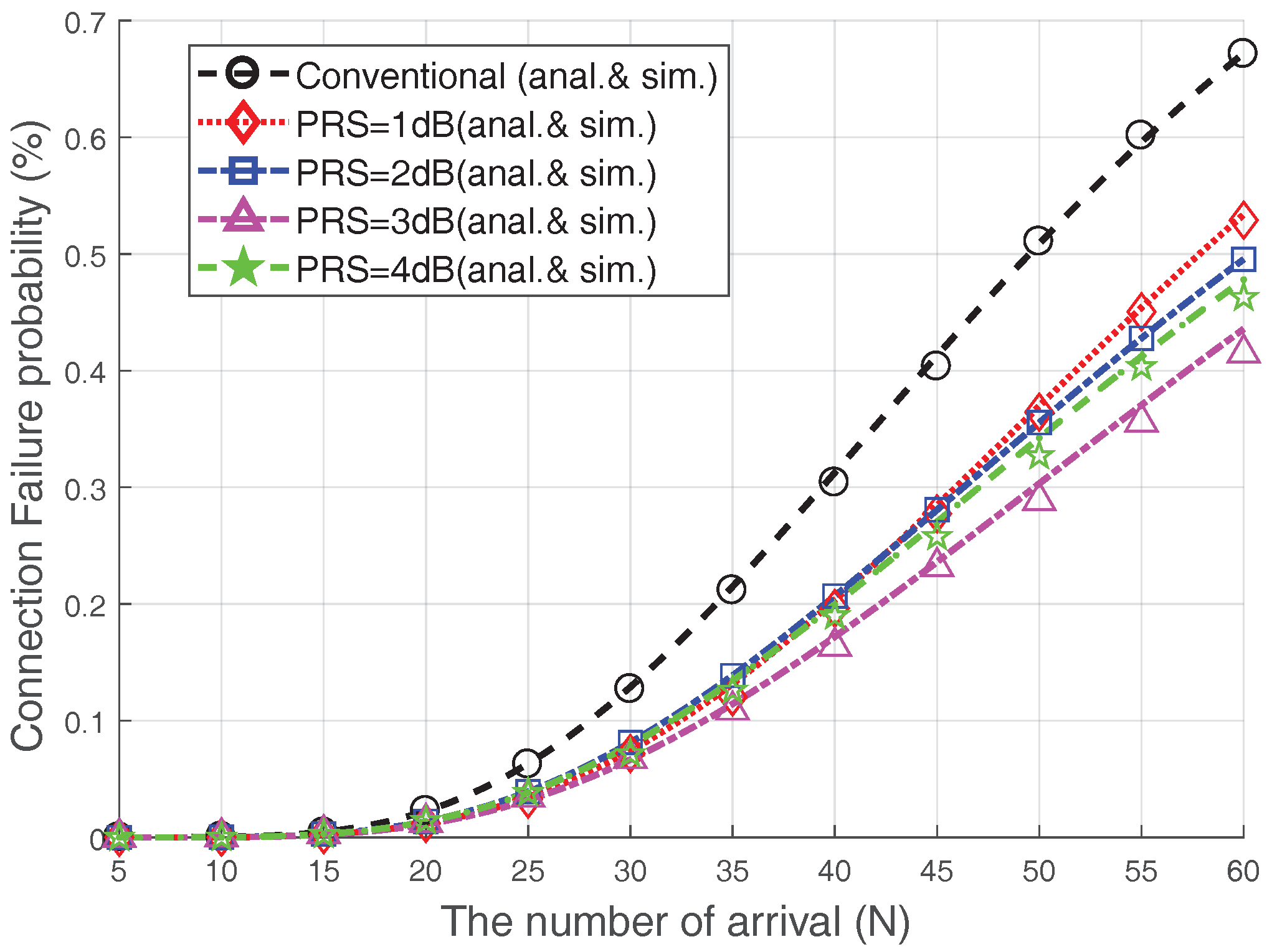
Figure 9 presents the relationship between the
and the connection failure probability when
and
. From
Figure 9, we can see that, by increasing the number of accesses, the connection failure probability increases due to severe collisions. In the conventional case, almost
of devices experience a connection failure when the number of arrivals surges (
). The Msg3 PR scheme reduces the connection failure probability significantly. For example, under heavy access load (
), the connection failure probability could be reduced by approximately
when Msg3 PR with
dB is used, as compared with the conventional case. In addition, the connection failure probability of the 3 dB-case is lower than that of the 4 dB-case.
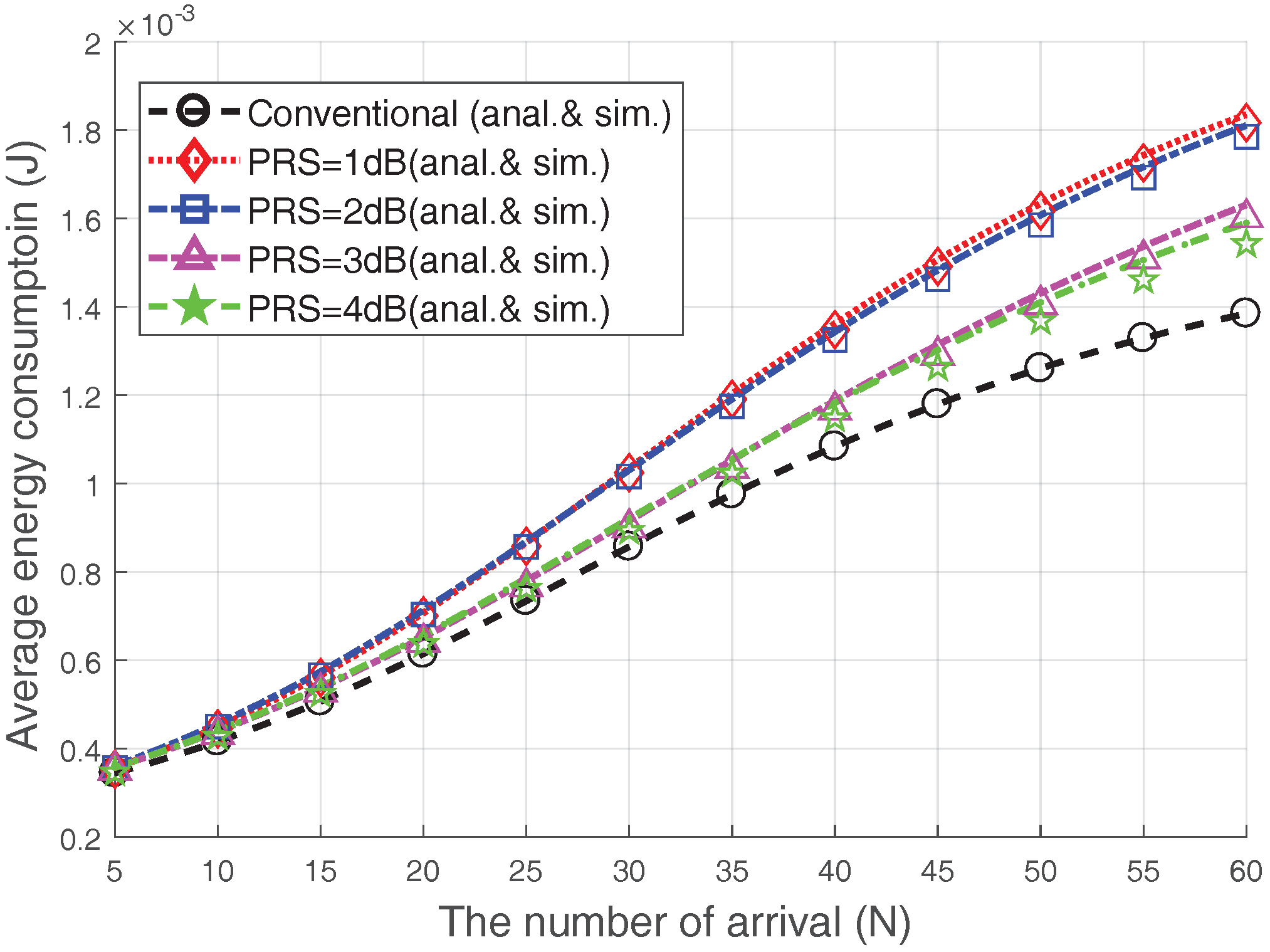
5.1.4. The Average Energy Consumption
Figure 10 presents the average energy consumption of the devices that completed the RA. We plot the performance when
and
. The average energy consumption of the devices increases with increasing the number of accesses; this is because the RA success probability decreases due to the congestion. Since most energy consumption occurs during transmission, the Msg3 PR scheme consumes more energy than the conventioal case. However, increasing the
does not necessarily increase the energy consumption. Surprisingly, the Msg3 PR with
dB or 4 dB consumes less energy than the Msg3 PR with
dB or 2 dB. For example, the Msg3 PR consumes approximately
more energy than the conventional case when
dB or 4 dB, while it consumes approximately
more energy than the conventional case when
dB or
dB. From this observation, we can argue that the energy consumption reductions due to the increase in the RA success probability are greater than the increased energy consumption due to increased transmission power results from
increment. In conclusion, choosing proper values of
and
for the Msg3 PR scheme can improve the RA throughput and lower the connection failure probability with relatively little additional energy consumption.
5.2. Coexistence with Other Schemes
Because the Msg3 PR scheme only controls the Msg3 transmission power, it can easily coexist with other RA-related schemes. In this sub-section, we discuss the possibility of coexistence of the Msg3 PR scheme with other typical RA-related schemes through simulation results.
The simulations assume bursts of M2M traffic. In [
20], the M2M traffic arrival is modeled as a beta-distribution to express the burstiness of M2M traffic. Let
denote the probability that each device is activated at time
. Then,
where
is the beta-function,
is the activation time which denotes the period during which all devices are activated, and
for bursty-M2M traffic. In this simulation, 10,000 devices are uniformly distributed in a cell, and each device generates traffic only once. That is, when a device experiences connection failure/success, it does not participate in the RA again. The activation time,
, is 10 s. Optimal ACB is assumed in this simulation, and the barring time and back-off window size are 200 ms and 20 ms, respectively.
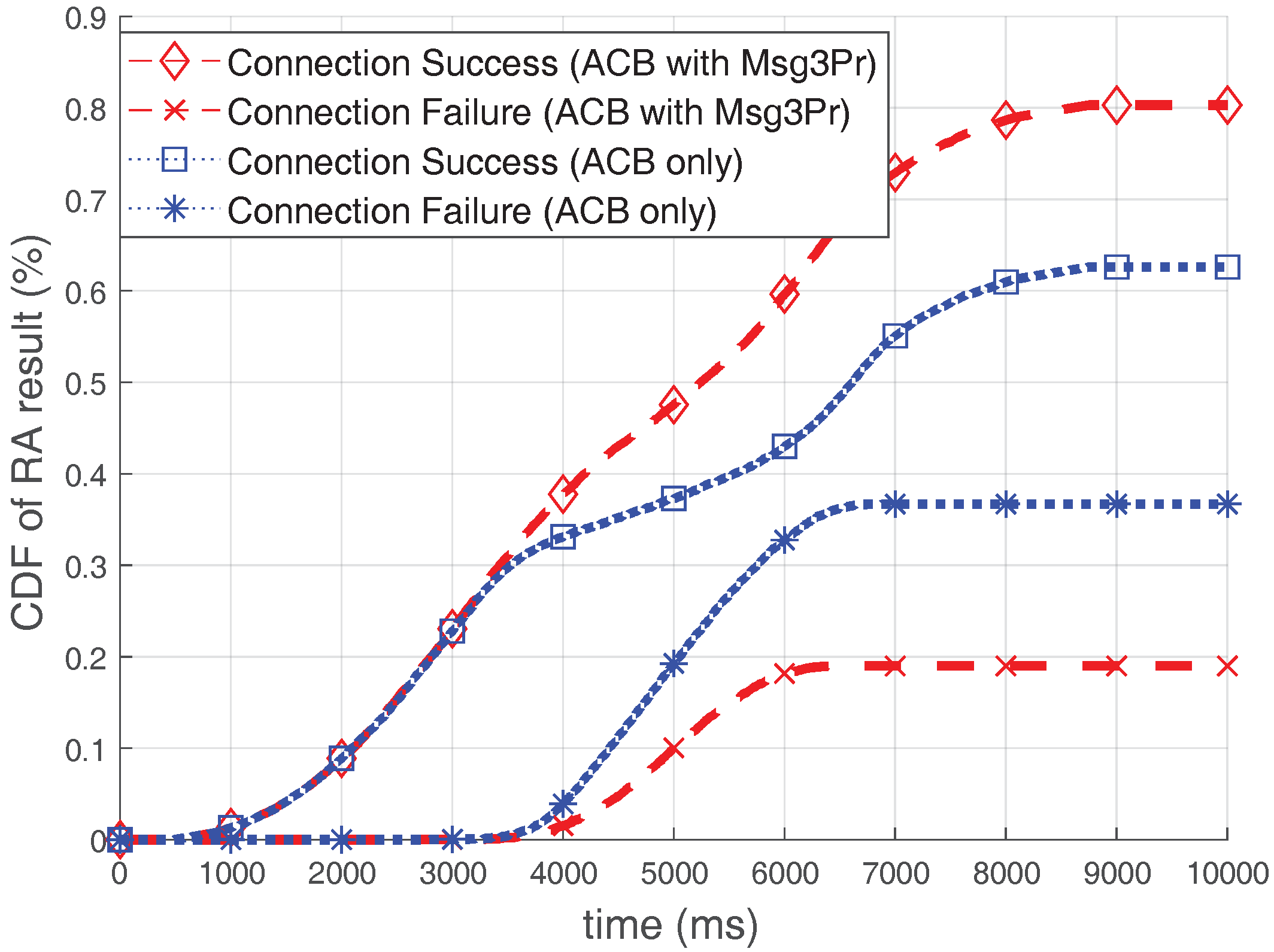
Figure 11 illustrates the cumulative distribution function (CDF) of the RA results over time when the optimal ACB is used. The ACB scheme controls the number of participants, so that the efficiency of the RACH could be maximized. Therefore, if severe congestion is predicted, it protects the RACH efficiency by blocking accesses of devices, but it does not improve RA throughput itself. As seen in
Figure 11, the number of connection failed-devices is increased due to bursty arrivals if only the ACB is used. However, when using the ACB with the Msg3 PR, the number of devices experiencing connection failure is much smaller than in the case of using the ACB only. Because the Msg3 PR scheme improves the RA throughput, approximately
of devices (almost 2000 devices) are more successful in acquiring connections by using the Msg3 PR together. Furthermore, this performance is the result when the ACB is performed without considering the RA efficiency improvement due to the Msg3 PR scheme. Therefore, although it is not the scope of this study, a larger performance improvement can be expected if ACB optimization is performed considering Msg3 PR.
6. Conclusions
RACH congestion problems resulting from massive access by the M2M devices cause severe performance degradation on both the eNB and M2M devices—for example, wasting the uplink resources such as RACH and PUSCH, and increasing the connection failure probability hindering the M2M communications.
We conducted a study of the influence of the capture effect on the RA performance. It was observed that the RA performance could be improved when the Msg3 was captured by the eNB even if collision occurred. Because the capture effect could occur when the received signal powers were differentiated by the eNB, we proposed the Msg3 PR scheme that exploited the power ramping scheme to increase the capture probability.
A steady-state analysis model was provided to show the performance of the proposed scheme in terms of the RA throughput, the connection failure probability, and the average energy consumption. Numerical results of analysis and simulation results showed that the Msg3 PR scheme with proper parameters increases the RA throughput (and also increased the PUSCH efficiency), even under heavy access loads. Moreover, the proposed scheme reduced the connection failure probability, which disturbs the M2M communications, by slightly increasing the average energy consumption.
Moreover, by conducting additional simulation, we discussed the benefits of using the proposed scheme and the effects of coexistence with other RA-related technologies. The simulation results show that the proposed algorithm can be combined with other technologies to achieve a larger performance improvement. In future work, further optimization could be performed for RA-related technologies using the Msg3 PR scheme.