Value-Based Caching in Information-Centric Wireless Body Area Networks
Abstract
:1. Introduction
2. Related Work
2.1. Location Based Caching
2.2. Content Based Caching
2.3. Node Functionality Based Caching
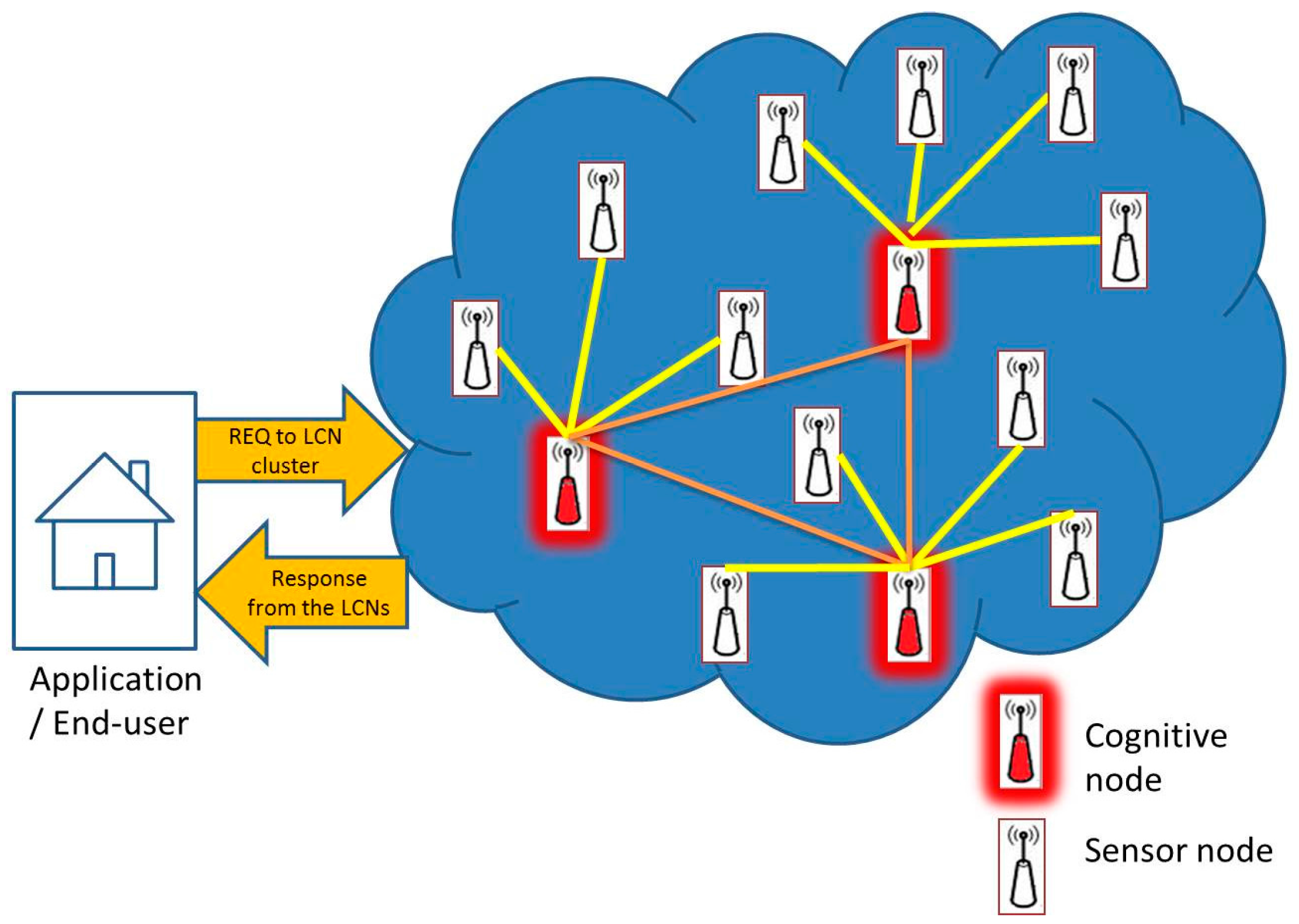
3. System Models
3.1. ICN-Based WBAN Model
3.2. Delay Model
3.3. Age Model
3.4. Popularity of On-Demand Requests
3.5. Channel Communication Model
4. VoI Cache Replacement
- Delay-based content: The delay sensitivity of the cached data content is a measure specified by the requesting user to indicate how long the consumer is willing to wait for it. Examples of delay-sensitive data can be found in applications serving areas of emergencies (e.g., disaster or health emergency).
- Age-based content: Some contents are more sensitive to aging. For instance, if a user requests information about the traffic updates for the coming 30 min, then any related content that does not cover this time interval is useless.
- Demand-based content: This is a measure of the data popularity which is specified by the frequency of requesting specific data.
| Algorithm 1: Drop least . |
| 1. Function VoI (content) |
| 2. Input |
| 3. content: A content item within the ICN. |
| 4. Begin |
| 5. for each node, do |
| 6. for each duty round, do |
| 7. Set value of each in the cache based on Equation (8) |
| 8. if cache_full |
| 9. Check history of the data requests |
| 10. Drop the data content of the least |
| 11. End if |
| 12. End for |
| 13. End for |
| 14. End |
Theoretical Delay Analysis
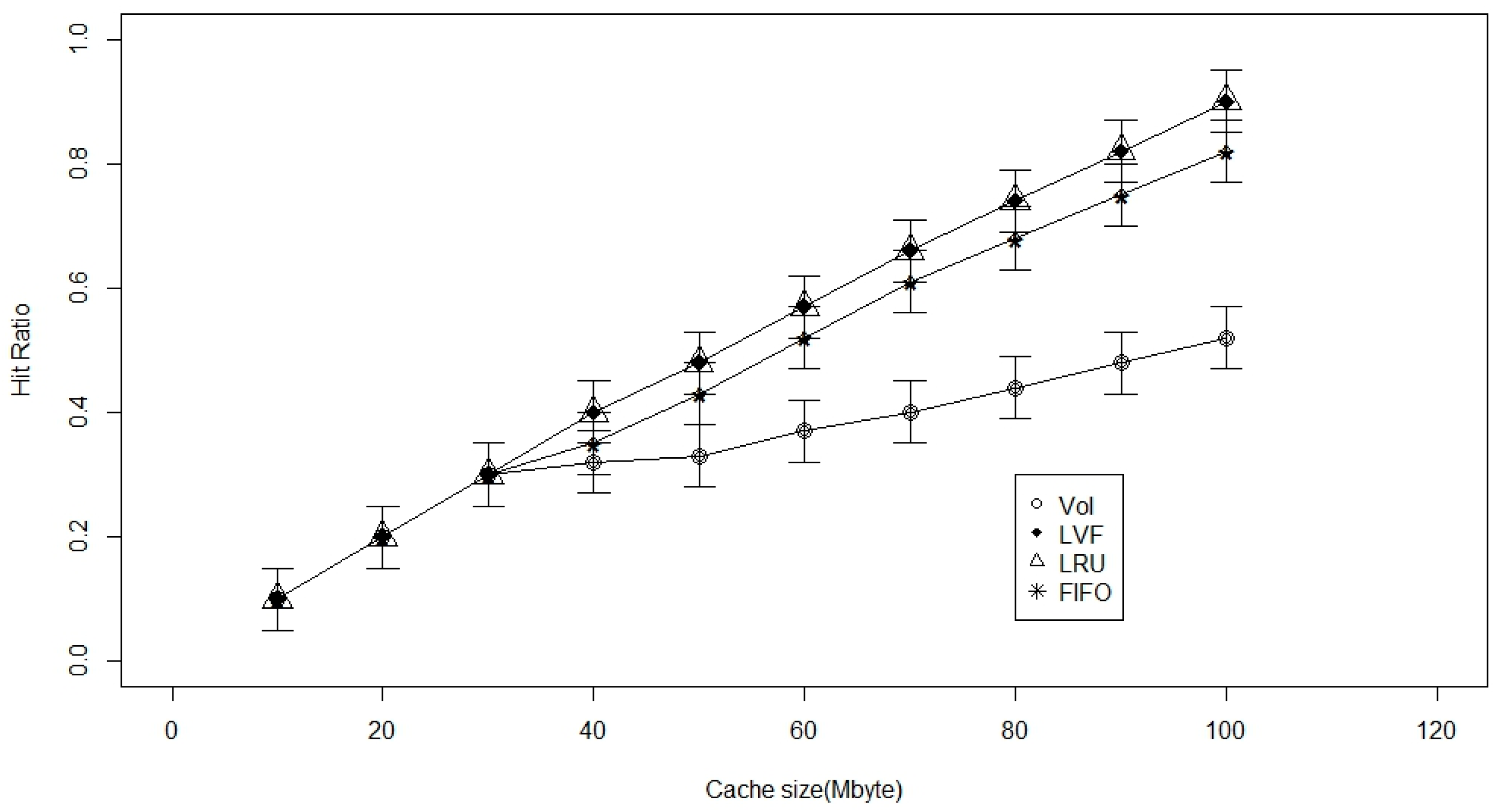
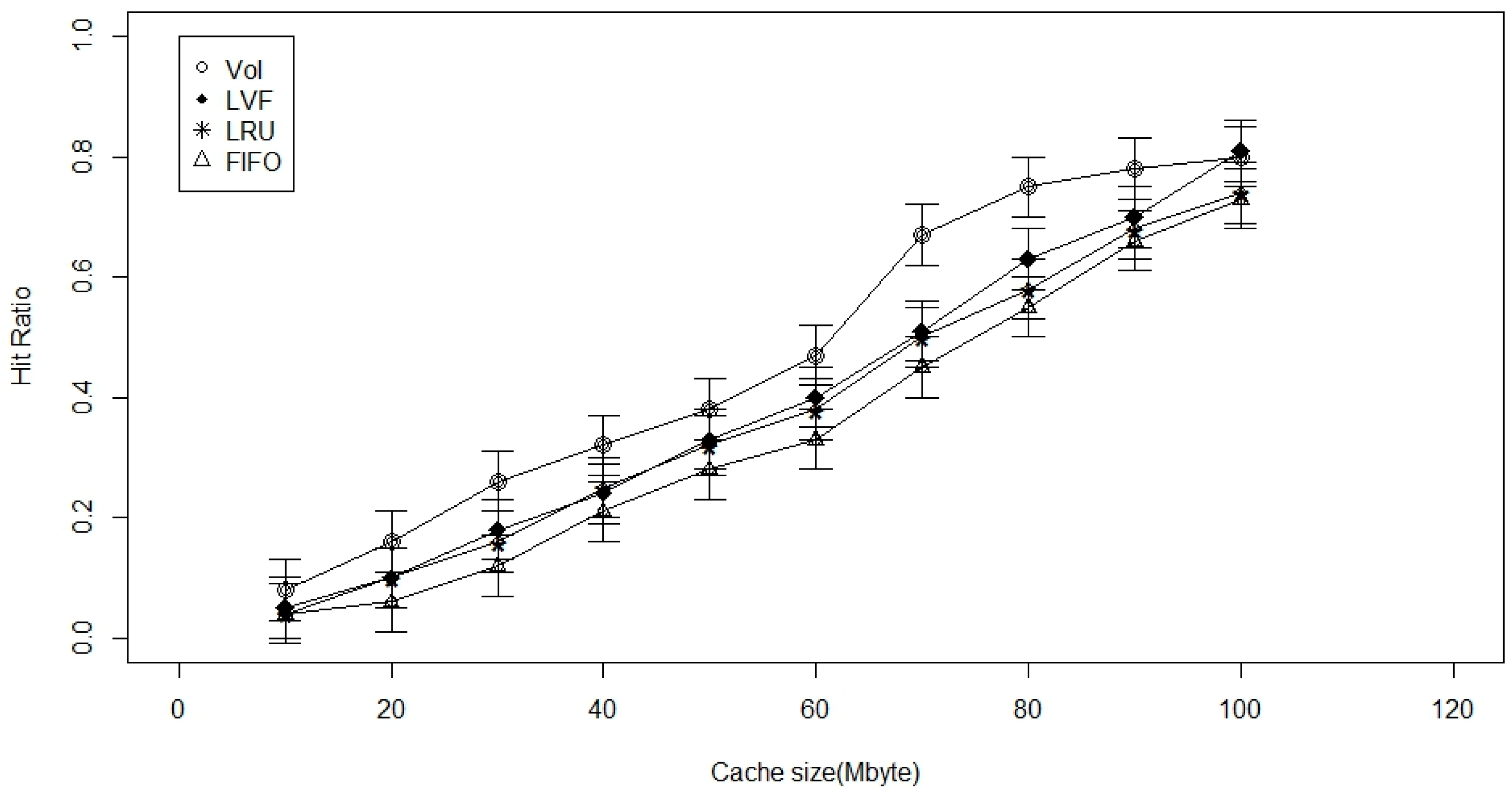
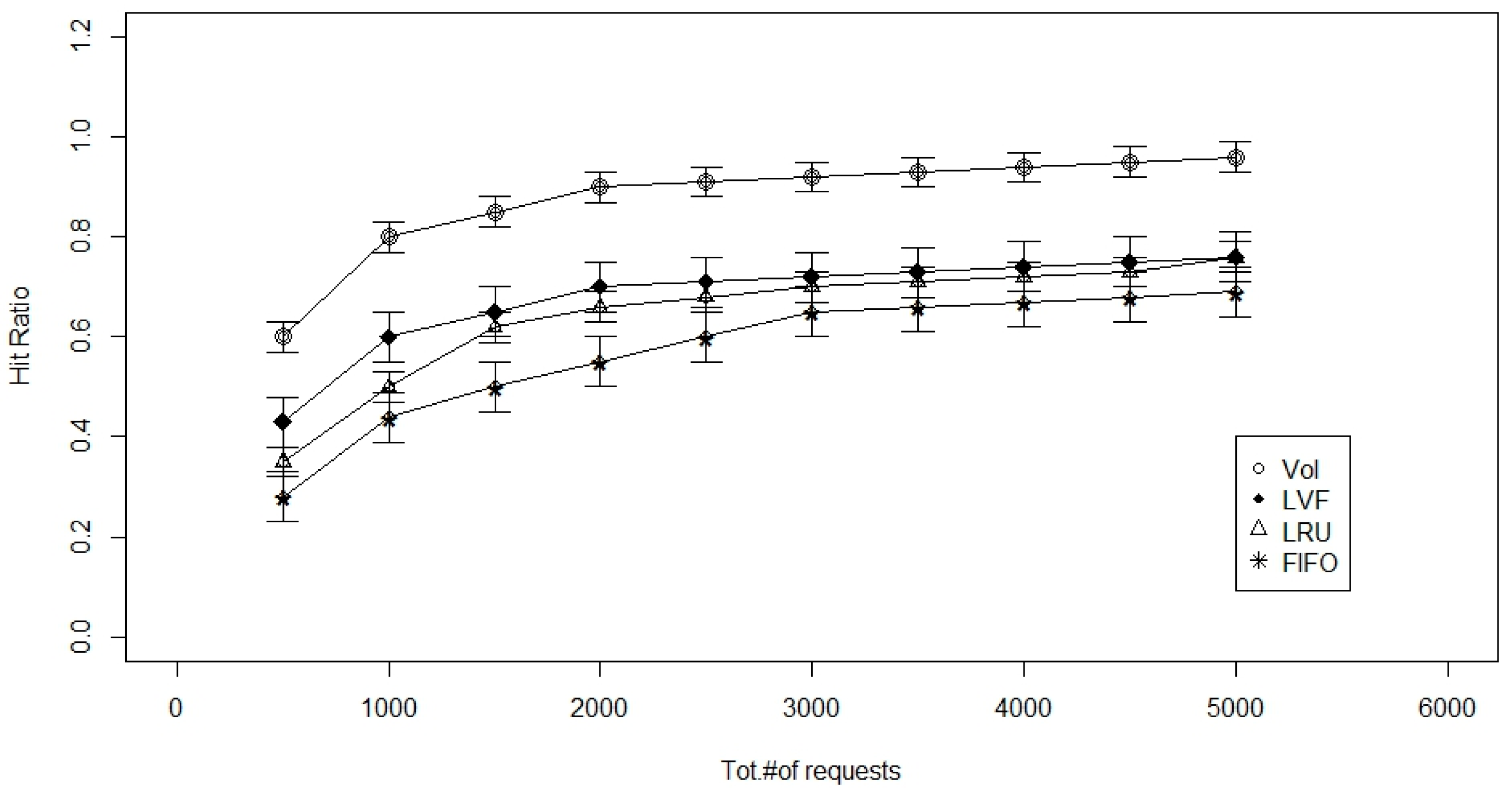
5. Performance Evaluation
5.1. Performance Metrics
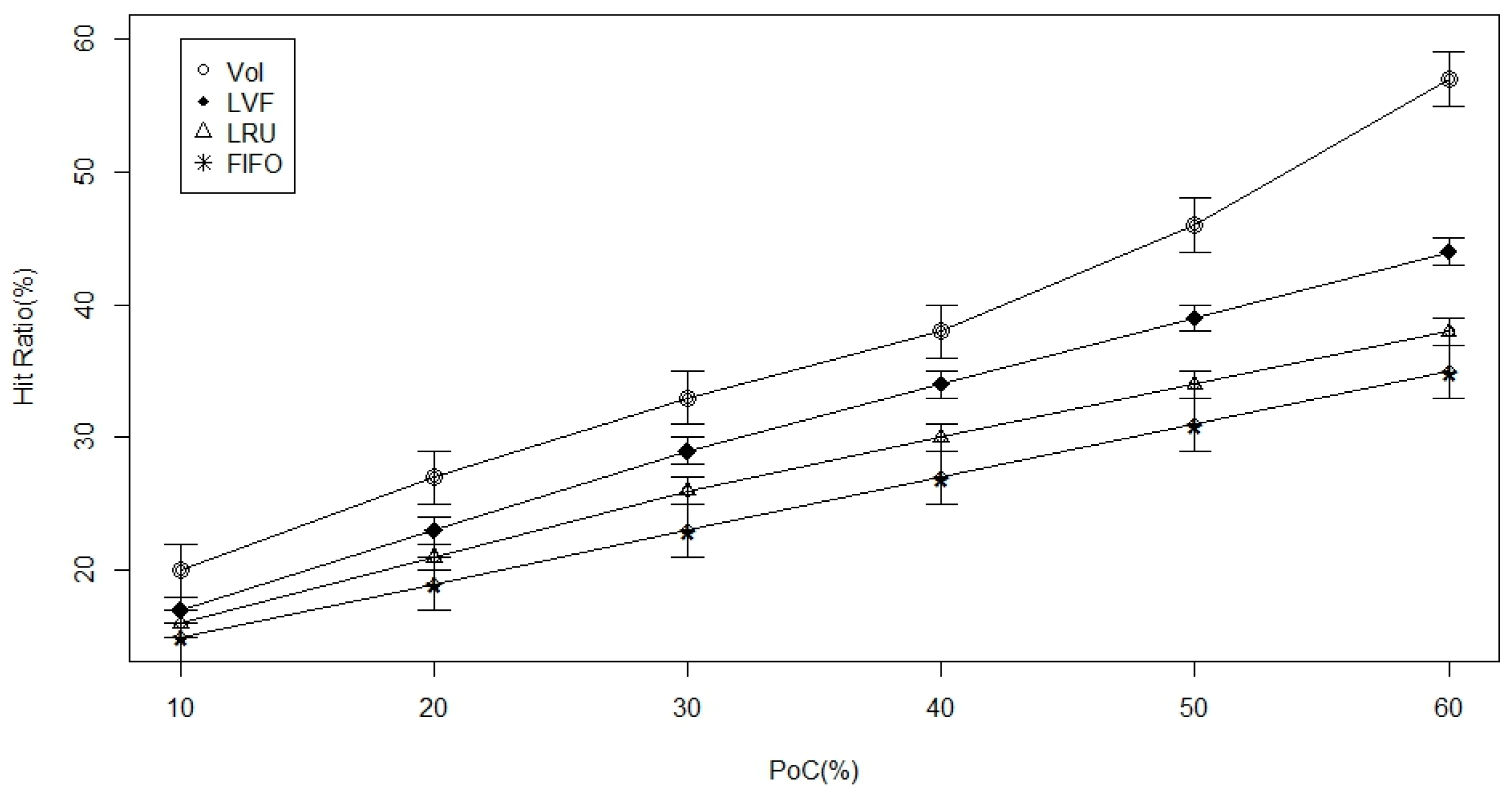
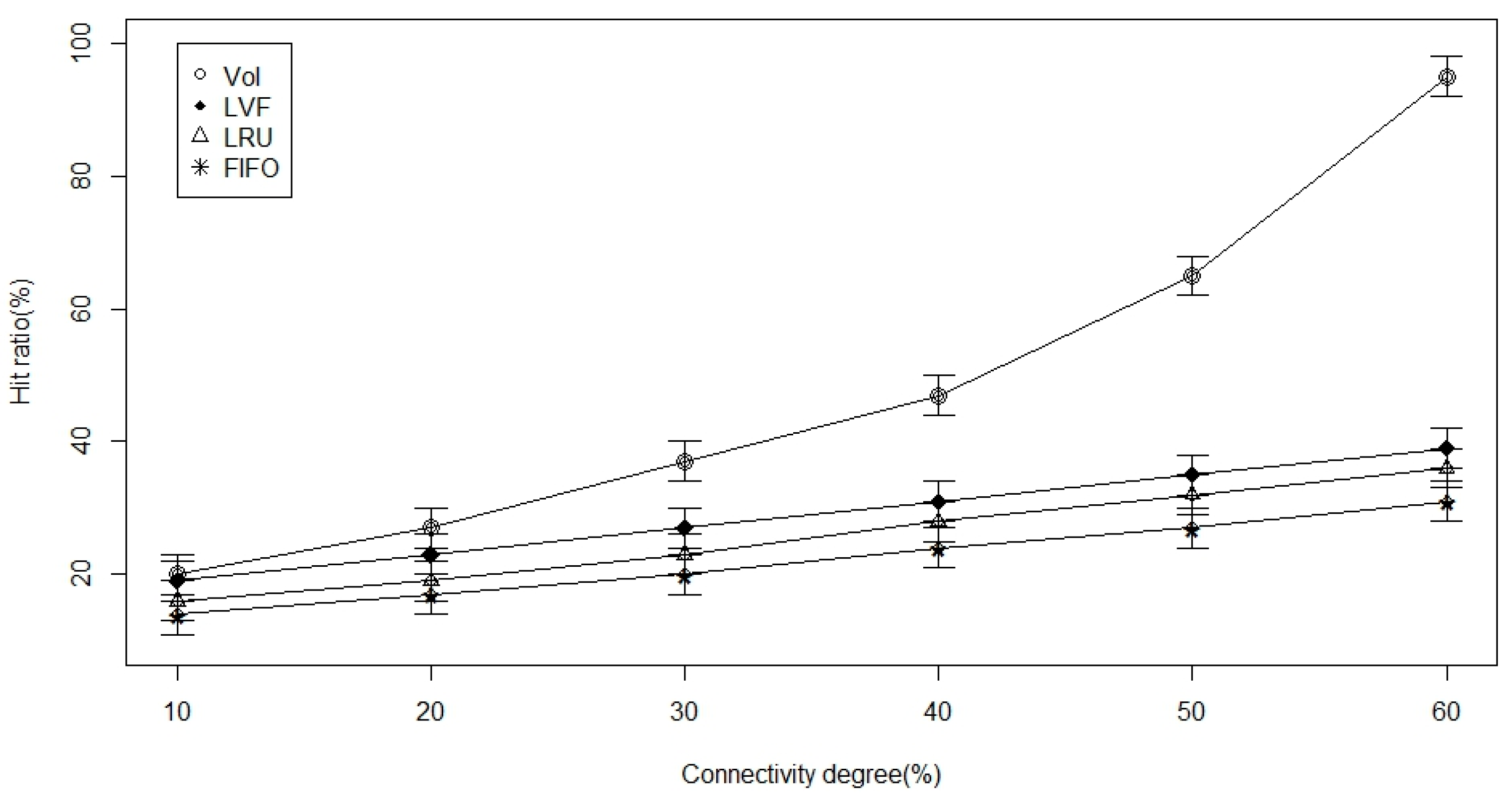
- Cache-hit ratio: is simply the fraction of time a request arrives at a node to which that cache is attached but does not contain the requested data item. It is the average hitting ratio over all the in-network caches. We preferred to look at average time to hit data and hitting ratio more than publisher load, but we generally expect publisher load to improve as the other metrics improve as well.
- Time-To-Hit-data (TTH): is found by simply logging all the total costs of the request and response paths incurred by every sensor node. Ideally, ICN-based WBAN is supposed to minimize the total average time-to-hit data per request
- In-network latency (delay): this metric represents the end-to-end delay as described above. Note that we differentiate between latency to hit data and in-network latency since the two metrics may differ because of mobility or disruption conditions
- Average Request per Publisher (ARP): this metric is measured in number of data requests per hour (req/h) and it represents the average load per publisher in an ICN paradigm. We track publisher load by monitoring the total fraction of data requests that had to be satisfied by a data publisher.
5.2. Simulation Parameters
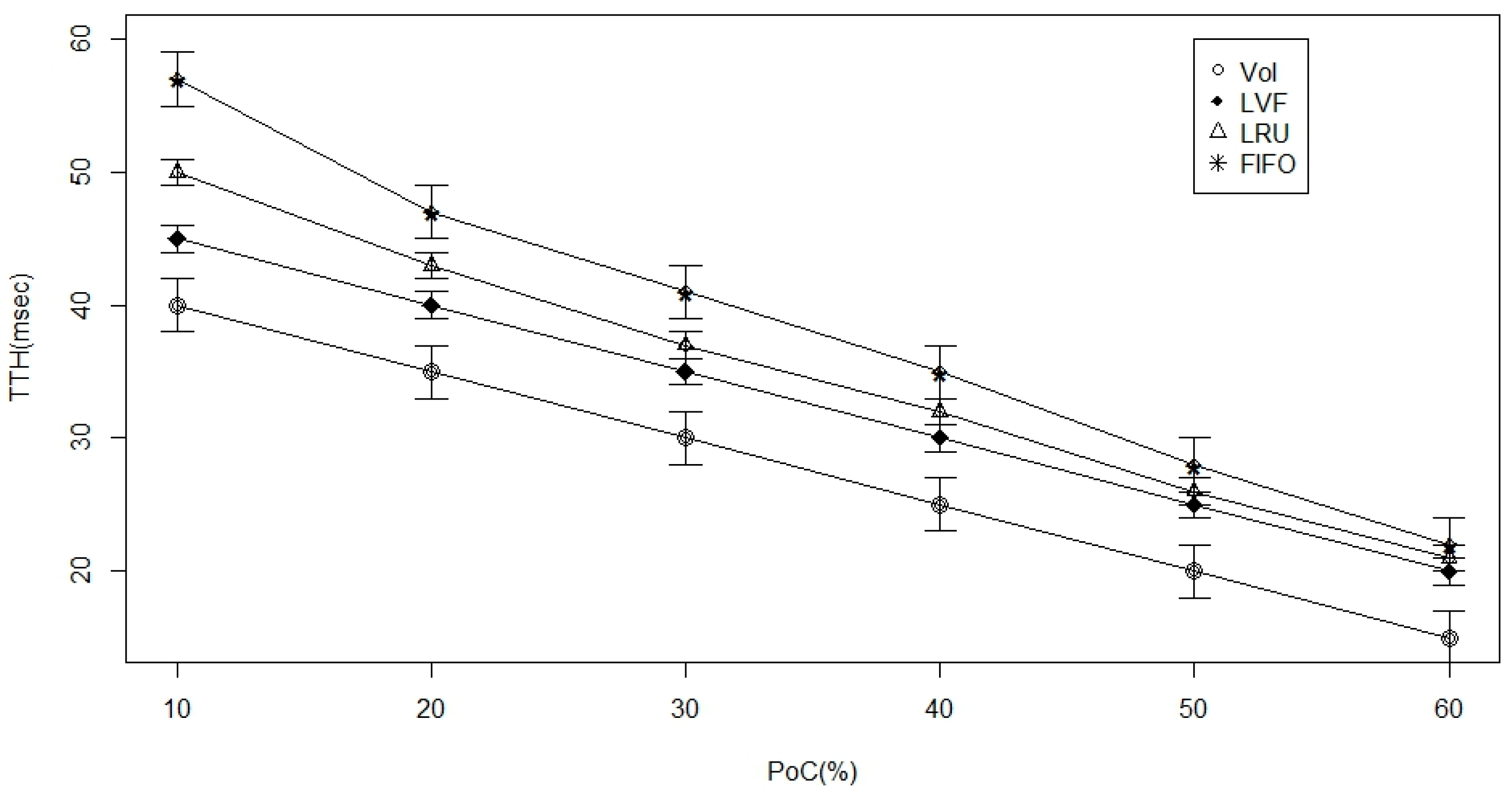
- Percentage of nodes with caches (PoC): This parameter is our primary method for controlling the extent of caching in our ICN. By varying this parameter, we can study the sensitivity of metrics like time-to-hit-data to the caching extent.
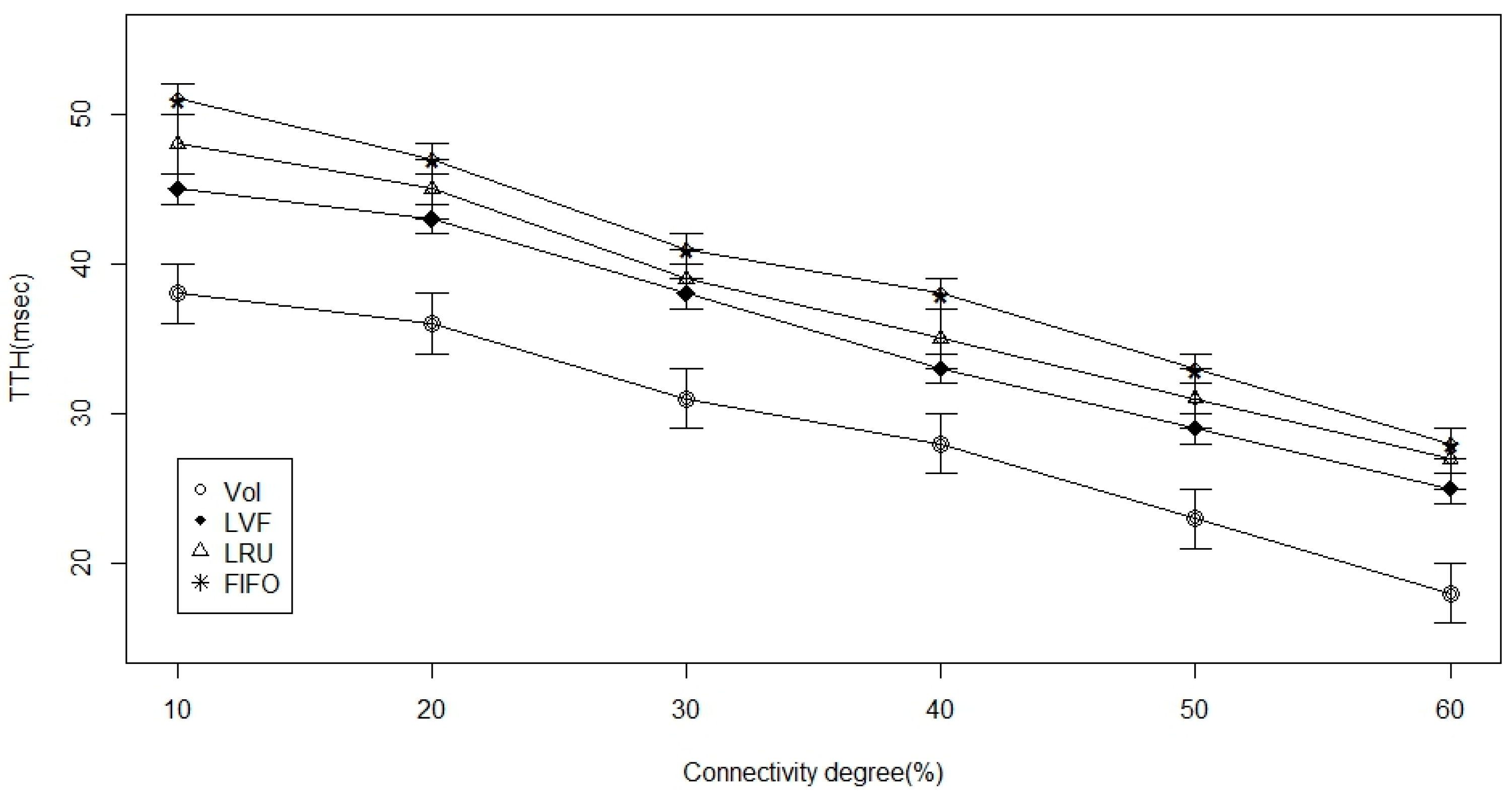
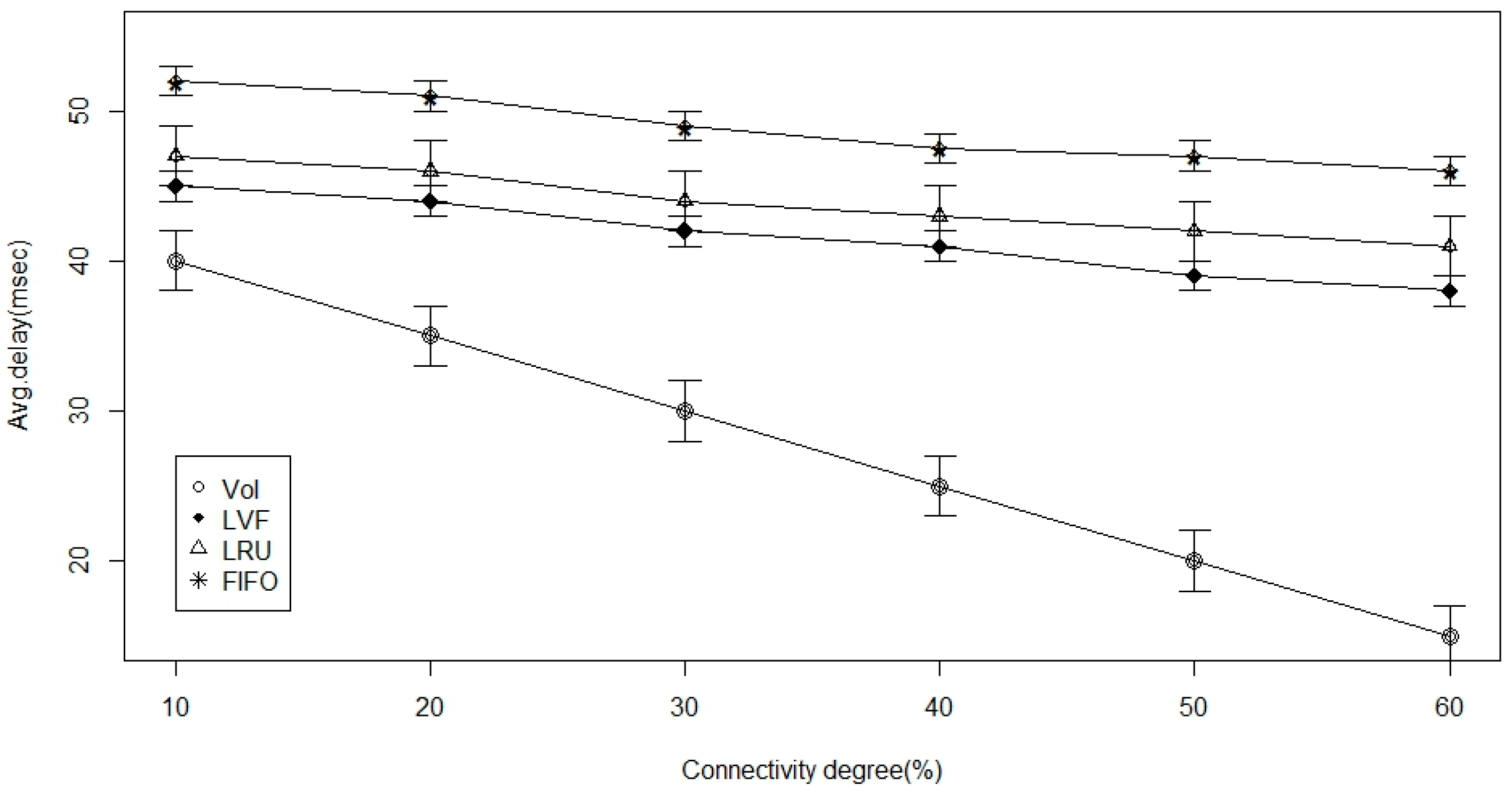
- Connectivity level (degree): It represents how tightly connected is the ICN-based WBAN. We use the connectivity matrix, based on our described communication model in Section 3.
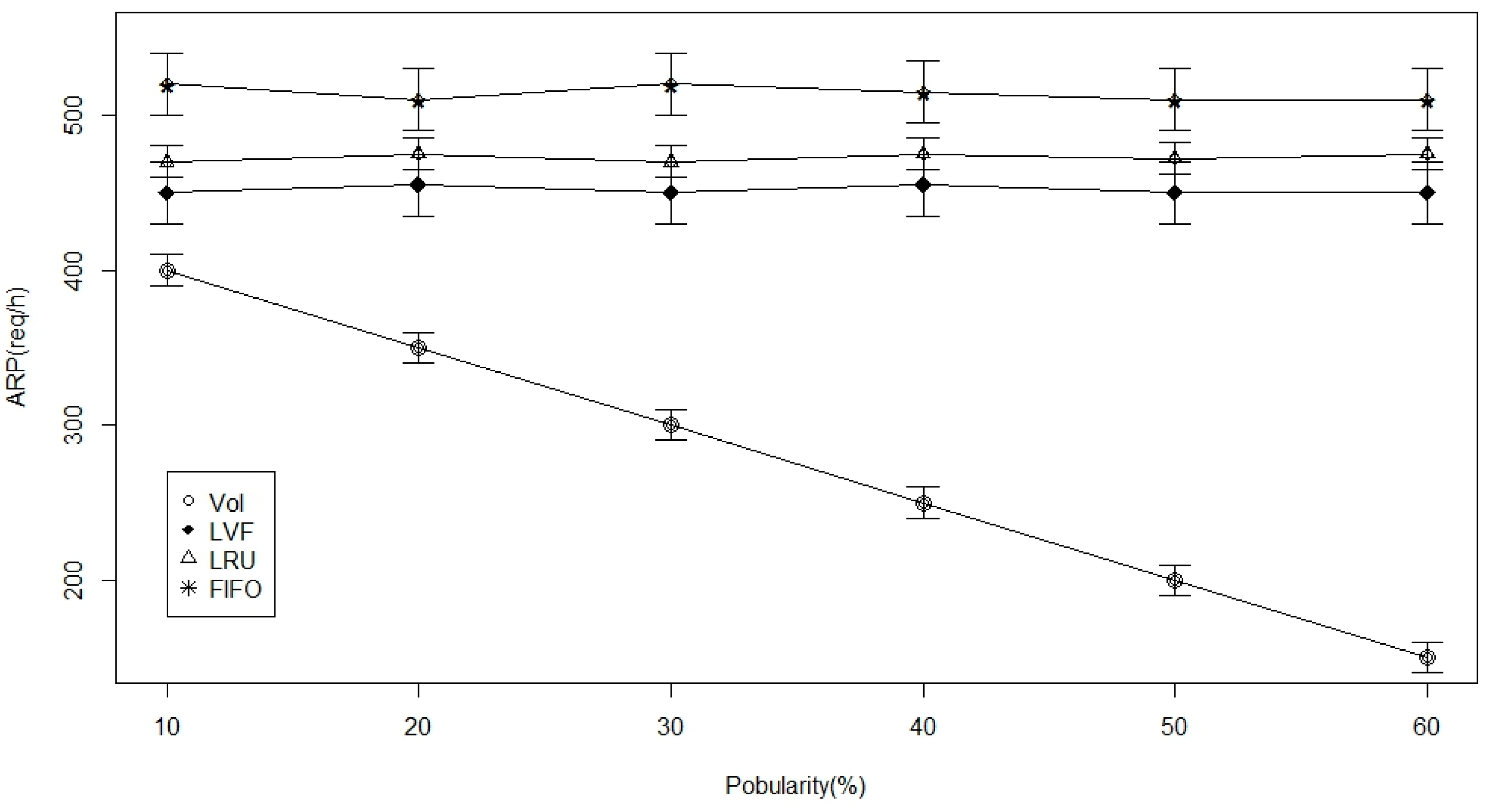
- Data Popularity: It indicates how frequent a specific data content is requested. This metric is measured in percentage with respect to other requested data contents. This parameter is represented by a single Poisson process parameter in order to give the content replacements per time unit.
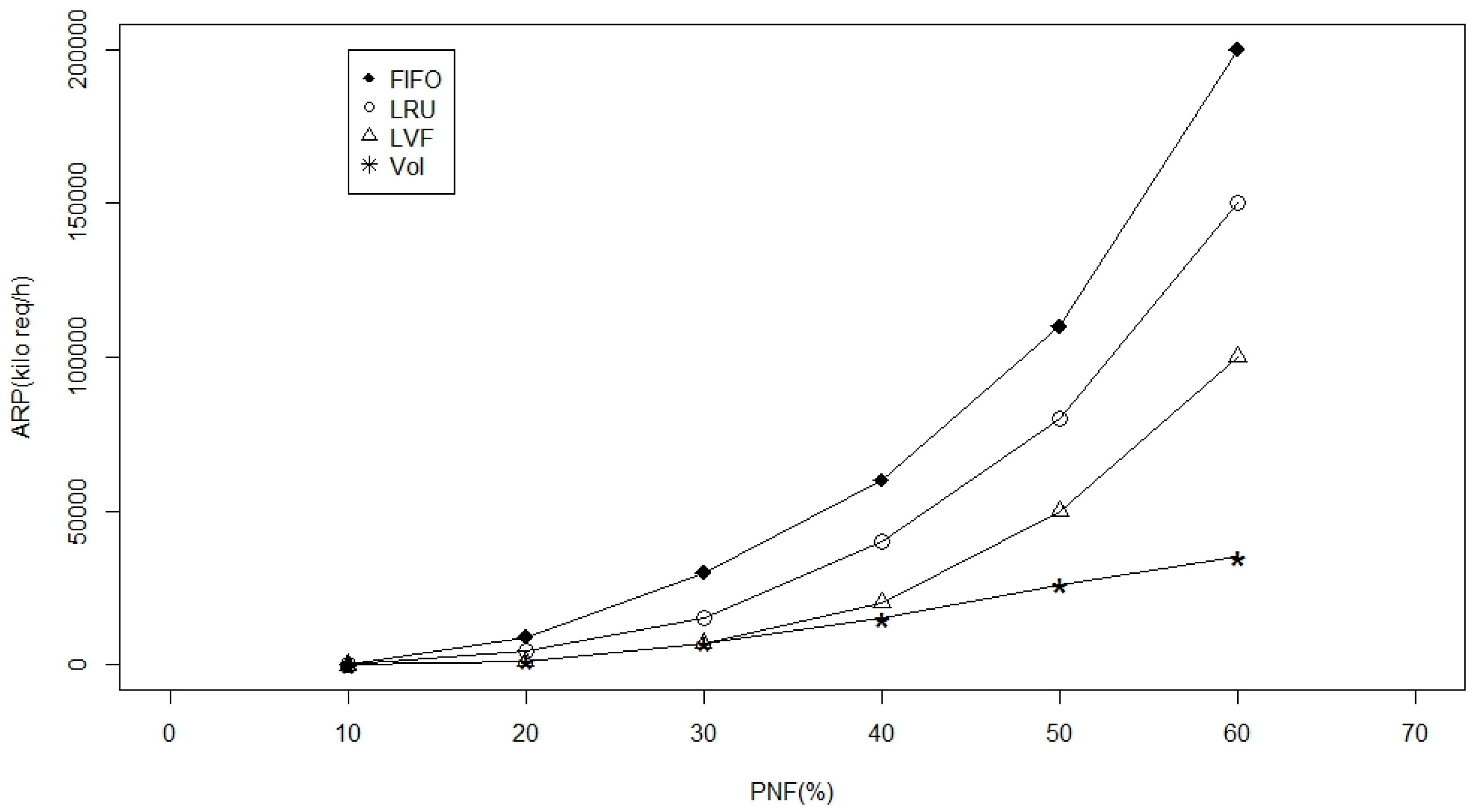
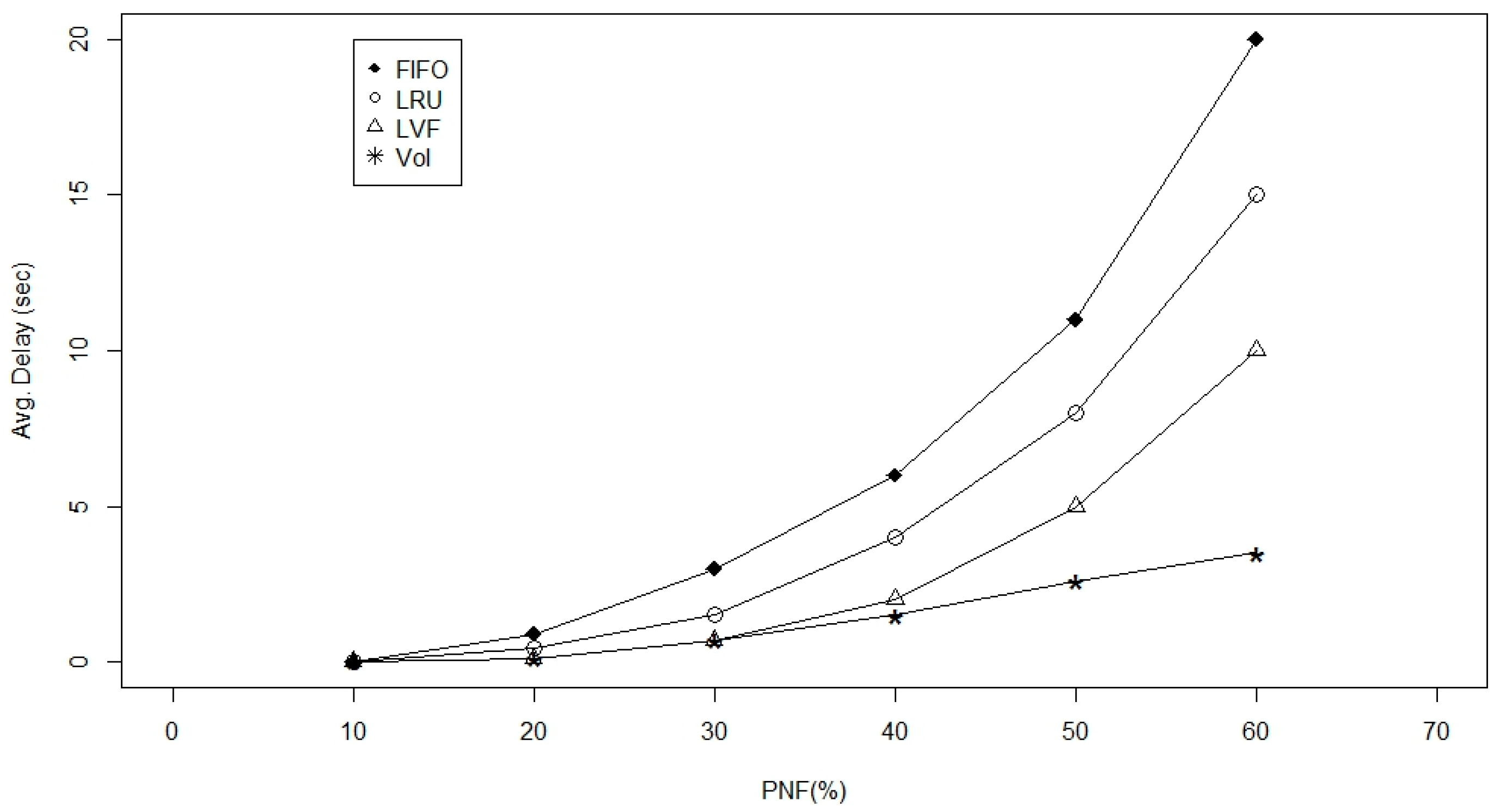
- PNF (%): It is the probability of a physical damage and/or a battery depletion for the deployed WBAN node due to harsh operational conditions. This parameter is chosen to reflect the impact in case of disaster scenarios or fragmented WBAN.
5.3. Simulation and Results
6. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Fortino, G.; Galzarano, S.; Gravina, R.; Li, W. A framework for collaborative computing and multi-sensor data fusion in body sensor networks. Inf. Fusion 2015, 22, 50–70. [Google Scholar] [CrossRef]
- Fortino, G.; Giannantonio, R.; Gravina, R.; Kuryloski, P.; Jafari, R. Enabling effective programming and flexible management of efficient body sensor network applications. IEEE Trans. Hum. Mach. Syst. 2013, 43, 115–133. [Google Scholar] [CrossRef]
- Al-Turjman, F. Impact of user’s habits on smartphones’ sensors: An overview. In Proceedings of the HONET-ICT International IEEE Symposium, Kyrenia, Cyprus, 13–14 October 2016; pp. 70–74.
- Singh, G.; Al-Turjman, F. Learning data delivery paths in QoI-Aware information-centric sensor networks. IEEE Internet Things J. 2016, 3, 572–580. [Google Scholar] [CrossRef]
- SmartSantander. Future Internet Research and Experimentation. Available online: http://www.smartsantander.eu/ (accessed on 13 January 2017).
- IBM|A Smarter Planet|Smarter Cities. Available online: http://www.ibm.com/smarterplanet/us/en/smarter_cities (accessed on 13 December 2016).
- Al-Turjman, F. Cognition in Information-Centric Sensor Networks for IoT applications: An overview. Ann. Telecommun. 2016, 1–16. [Google Scholar] [CrossRef]
- Singh, G.T.; Al-Turjman, F.M. A data delivery framework for Cognitive Information-Centric Sensor Networks in smart outdoor monitoring. Elsevier Comput. Commun. 2016, 74, 38–51. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Alfagih, A.; Alsalih, W.; Hassanein, H. A delay-tolerant framework for integrated RSNs in IoT. Elsevier Comput. Commun. 2013, 36, 998–1010. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Hassanein, H.; Ibnkahla, M. Efficient deployment of wireless sensor networks targeting environment monitoring applications. Elsevier Comput. Commun. 2013, 36, 135–148. [Google Scholar] [CrossRef]
- Gravina, R.; Alinia, P.; Ghasemzadeh, H.; Fortino, G. Multi-sensor fusion in body sensor networks: State-of-the-art and research challenges. Inf. Fusion 2017, 35, 68–80. [Google Scholar] [CrossRef]
- Chankhunthod, A.; Danzig, P.; Neerdaels, C.; Schwartz, M.; Worrell, K. A hierarchical internet object cache. In Proceedings of the 1996 Annual Conference on USENIX Annual Technical Conference, San Diego, CA, USA, 22–26 January 1996.
- Gritter, M.; Cheriton, D.R. TRIAD: A New Next-Generation Internet Architecture; Stanford University: Stanford, CA, USA, 2000. [Google Scholar]
- Al-Turjman, F.; Hassanein, H. Enhanced data delivery framework for dynamic Information-Centric Networks (ICNs). In Proceedings of the IEEE Local Computer Networks (LCN), Sydney, Australia, 21–24 October 2013; pp. 831–838.
- Chai, W.K.; He, D.; Psaras, I.; Pavlou, G. Cache “Less for More” in Information-Centric Networks (extended version). Elsevier Comput. Commun. 2013, 36, 758–770. [Google Scholar] [CrossRef]
- Eum, S.; Nakauchi, K.; Shoji, Y.; Nishinaga, N.; Murata, M. CATT: Cache aware target identification for ICN. IEEE Commun. Mag. 2012, 50, 60–67. [Google Scholar] [CrossRef]
- Radoslavov, P.; Govindan, R.; Estrin, D. Topology-informed internet replica placement. In Proceedings of WCW’01: Web Caching and Content Distribution Workshop, Boston, MA, USA, 20–22 June 2001.
- Bhattacharjee, S.; Calvert, K.L.; Zegura, E.W. Self-organizing wide-area network caches. In Proceedings of the Seventeenth Annual Joint Conference of the IEEE Computer and Communications Societies, San Francisco, CA, USA, 29 March–2 April 1998; pp. 752–757.
- Vasilakos, X.; Siris, V.; Polyzos, G.; Pomonis, M. Proactive selective neighbor caching for enhancing mobility support in Information-Centric Networks. In Proceedings of the ICN Workshop on Information-Centric Networking, Helsinki, Finland, 17 August 2012; ACM: New York, NY, USA, 2012; pp. 61–66. [Google Scholar]
- Li, J.; Wu, H.; Liu, B.; Wang, X.; Zhang, Y.; Dong, L. Popularity-driven coordinated caching in named data networking. In Proceedings of the Eighth ACM/IEEE Symposium on Architectures for Networking and Communications Systems, Austin, TX, USA, 29–30 October 2012; pp. 200–211.
- Cho, K.; Lee, M.; Park, K.; Kwon, T.T.; Choi, Y.; Pack, S. WAVE: Popularity-based and collaborative in-network caching for Content-oriented networks. In Proceedings of the 2012 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Orlando, FL, USA, 25–30 March 2012; pp. 316–321.
- Ming, Z.; Xu, M.; Wang, D. Age-based cooperative caching in information-centric networks. In Proceedings of the 2014 23rd International Conference on Computer Communication and Networks (ICCCN), Shanghai, China, 4–7 August 2014.
- Wang, Y.; Lee, K.; Venkataraman, B.; Shamanna, R.L.; Rhee, I.; Yang, S. Advertising cached contents in the control plane: Necessity and feasibility. In Proceedings of the 2012 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Orlando, FL, USA, 25–30 March 2012.
- Fricker, C.; Robert, P.; Roberts, J.; Sbihi, N. Impact of traffic mix on caching performance in a Content-Centric Network. In Proceedings of the 2012 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS), Orlando, FL, USA, 25–30 March 2012; pp. 310–315.
- Al-Turjman, F.; Al-Fagih, A.; Hassanein, H. A value-based cache replacement approach for Information-Centric Networks. In Proceedings of the 38th Annual IEEE Conference on Local Computer Networks Workshops, Sydney, Australia, 21–24 October 2013.
- Vasilakos, A.V.; Li, Z.; Simon, G.; You, W. Information centric network: Research challenges and opportunities. J. Netw. Comput. Appl. 2015, 52, 1–10. [Google Scholar] [CrossRef]
- Amadeo, M.; Campolo, C.; Quevedo, J.; Corujo, D.; Molinaro, A.; Iera, A.; Aguiar, R.L.; Vasilakos, A.V. Information-Centric Networking for the internet of things: Challenges and opportunities. IEEE Netw. 2016, 30, 92–100. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Hassanein, H.; Ibnkahla, M. Towards prolonged lifetime for deployed WSNs in outdoor environment monitoring. Elsevier Ad Hoc Netw. J. 2015, 24, 172–185. [Google Scholar] [CrossRef]
- Al-Turjman, F.; Hassanein, H.; Ibnkahla, M. Quantifying connectivity in wireless sensor networks with grid-based deployments. Elsevier J. Netw. Comput. Appl. 2013, 36, 368–377. [Google Scholar] [CrossRef]
- Alnuem, M.A.; Zafar, N.A.; Imran, M.; Fayed, M.; Ullah, S. Formal specification and validation of a localized algorithm for segregation of Critical/Non-critical nodes in MAHSNs. Int. J. Distrib. Sens. Netw. 2014, 2014, 140973. [Google Scholar] [CrossRef]

| Quality of Information (QoI)—Attributes | ||||
|---|---|---|---|---|
| Request Type | Latency (L) | Energy (E) | Reliability (R) | Throughput (T) |
| Type I: On-Demand | x | 3 | 1 | 2 |
| Type II: Periodic | 1 | 2 | 4 | 3 |
| Type III: Emergency | 1 | 1 | x | 2 |
| L1 Caching Policy | L1 Hit Ratio | L2 Caching Policy | L2 Hit Ratio | Tot. Hit Ratio |
|---|---|---|---|---|
| VoI | 0.811542 | LRU | 0.81743 | 0.81542 |
| VoI | 0.547 | FIFO | 0.7792 | 0.6194 |
| VoI | 0.899 | VoI | 0.0099 | 0.81743 |
| LRU | 0.754 | VoI | 0.398 | 0.6837 |
| LRU | 0.9 | FIFO | 0 | 0.71818 |
| LRU | 0.802 | LRU | 0.49 | 0.75125 |
| FIFO | 0.9 | LRU | 0 | 0.71818 |
| FIFO | 0.9 | VoI | 0 | 0.61818 |
| FIFO | 0.9 | FIFO | 0 | 0.65125 |
© 2017 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Al-Turjman, F.M.; Imran, M.; Vasilakos, A.V. Value-Based Caching in Information-Centric Wireless Body Area Networks. Sensors 2017, 17, 181. https://doi.org/10.3390/s17010181
Al-Turjman FM, Imran M, Vasilakos AV. Value-Based Caching in Information-Centric Wireless Body Area Networks. Sensors. 2017; 17(1):181. https://doi.org/10.3390/s17010181
Chicago/Turabian StyleAl-Turjman, Fadi M., Muhammad Imran, and Athanasios V. Vasilakos. 2017. "Value-Based Caching in Information-Centric Wireless Body Area Networks" Sensors 17, no. 1: 181. https://doi.org/10.3390/s17010181
APA StyleAl-Turjman, F. M., Imran, M., & Vasilakos, A. V. (2017). Value-Based Caching in Information-Centric Wireless Body Area Networks. Sensors, 17(1), 181. https://doi.org/10.3390/s17010181







