Bulk Data Dissemination in Low Power Sensor Networks: Present and Future Directions
Abstract
:1. Introduction
- Reliability. Since it is often used for distribute commands and code updates to all network nodes, 100% reliability is typically required (i.e., all nodes should receive all the transmitted data).
- Scalability. For maintaining a WSN, there are typically multiple parameters to maintain, e.g., sensing data type, neighbor table, etc. Hence the framework should be scalable to support multi-object and large scale dissemination.
- Efficiency. Due to the resource-constrained nature of WSN nodes, dissemination should be done in a transmission/energy efficient way.
- Cross-technology interference/communications. As many IoT applications of sensor networks are deployed in an indoor environment (e.g., smart home [6], body sensor network [16], etc.), other wireless devices such as WiFi and BlueTooth may cause fierce cross-technology interference (CTI) to WSNs. The recent advances in reducing CTI and enabling cross-technology communication can potentially support further optimization on dissemination in low power WSNs.
- Coding techniques. Network coding is an important means to improve the transmission efficiency in dissemination. However, the complexity and the corresponding coding delay have always been an obstacle for the utilization in dissemination. Some novel coding designs such as [17] achieves considerable improvement in the coding delay, which is a promising alternative to improve the dissemination performance.
2. Bulk Data Dissemination
2.1. Application Scenarios
2.2. Key Requirements for Bulk Data Dissemination
2.2.1. Reliability
2.2.2. Scalability
2.2.3. Transmission & Time Efficiency
2.2.4. Energy Efficiency
2.3. System Overview and Taxonomy
2.4. Reliability
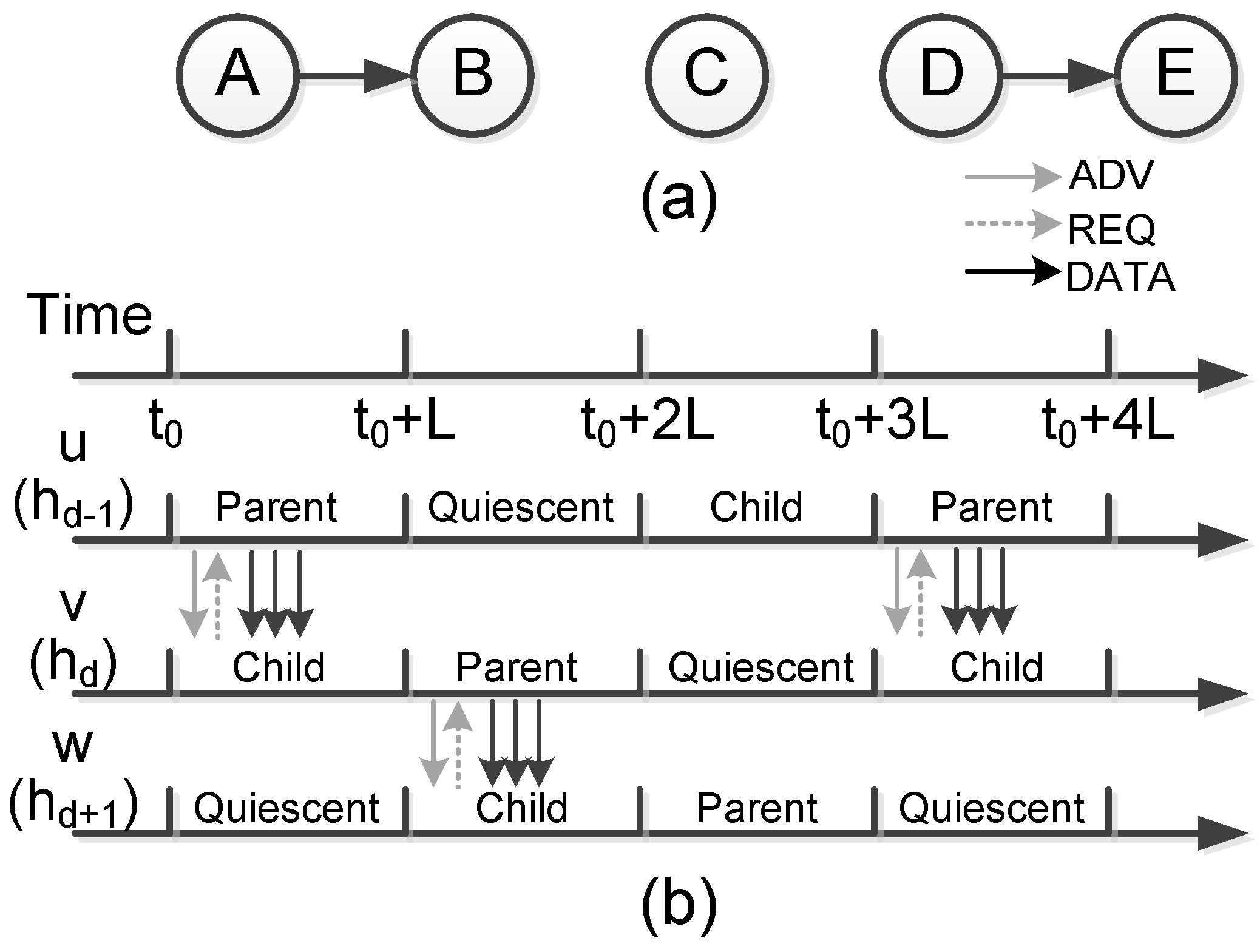
2.4.1. NACK Based Mechanisms
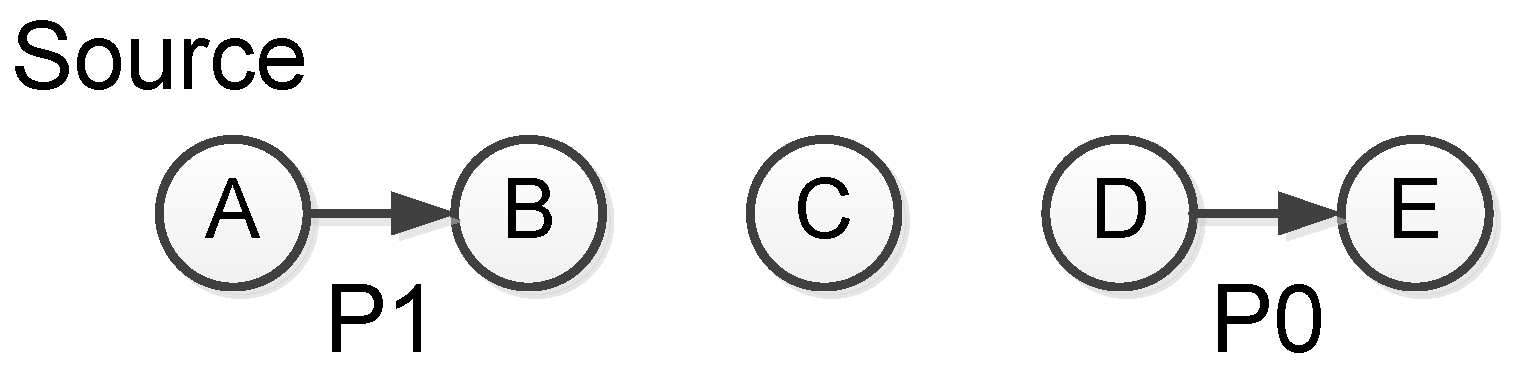
- ADV—new data advertisement. When a node has new data to distribute, it can advertise this fact by broadcasting an ADV message containing the meta-data.
- REQ—request for data. A SPIN node sends a REQ message when it wishes to receive some actual data.
- DATA—data message. DATA messages contain actual sensor data with a meta-data header, indicating the source node id, sequence number, etc.
2.4.2. ACK Based Mechanism
2.4.3. Short Summary
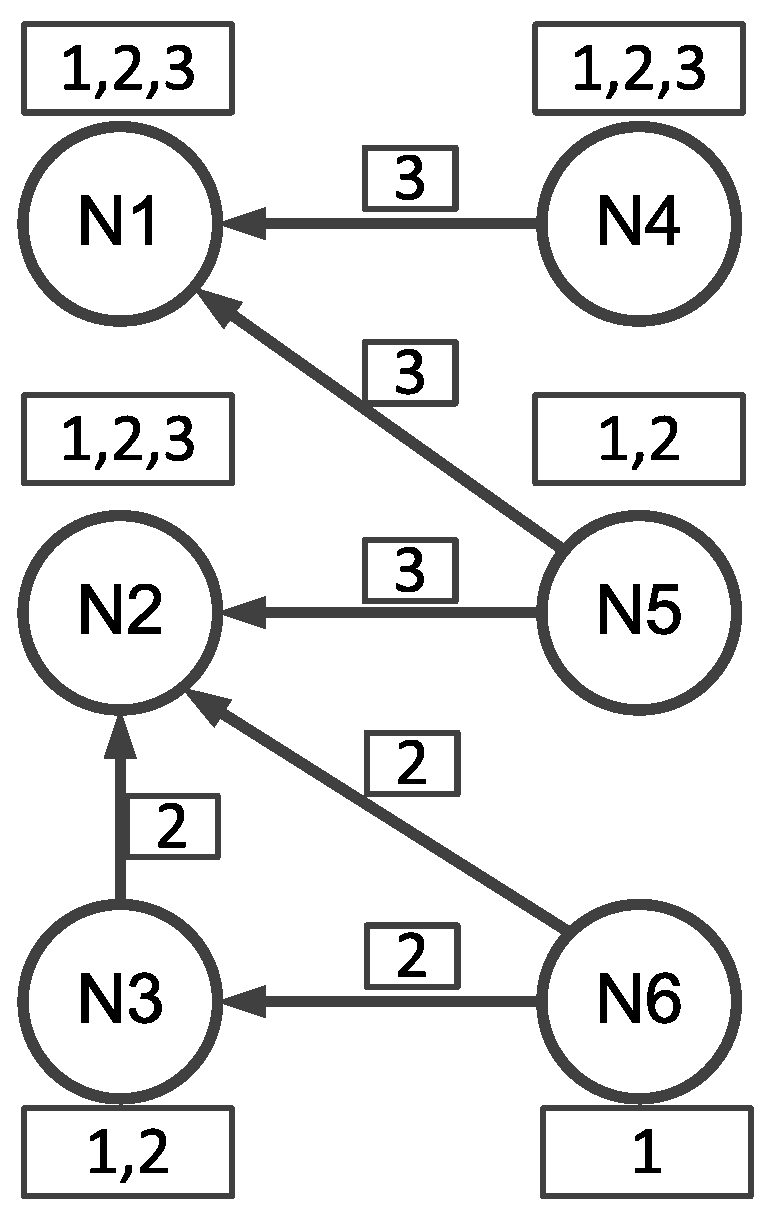
2.5. Scalability
2.5.1. Single-Hop vs. Multi-Hop
2.5.2. Structured vs. Structureless
2.6. Transmission Efficiency
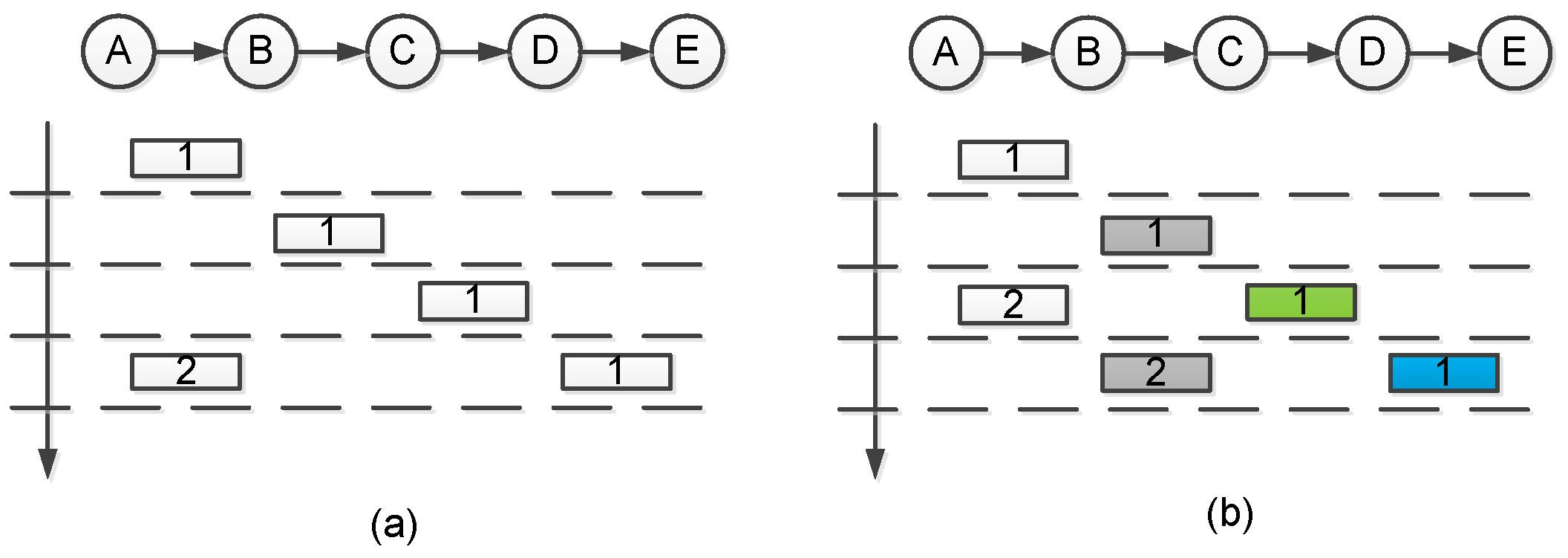
2.6.1. Multi-Hop Pipelining
2.6.2. Sender Selection
Exploiting Topology Information
Exploiting Link Quality
Exploiting Link Correlation
2.6.3. Network Coding
2.6.4. Exploring the Synergy among Link Correlation and Rateless Codes
2.6.5. Channel Diversities
Multi-Channel
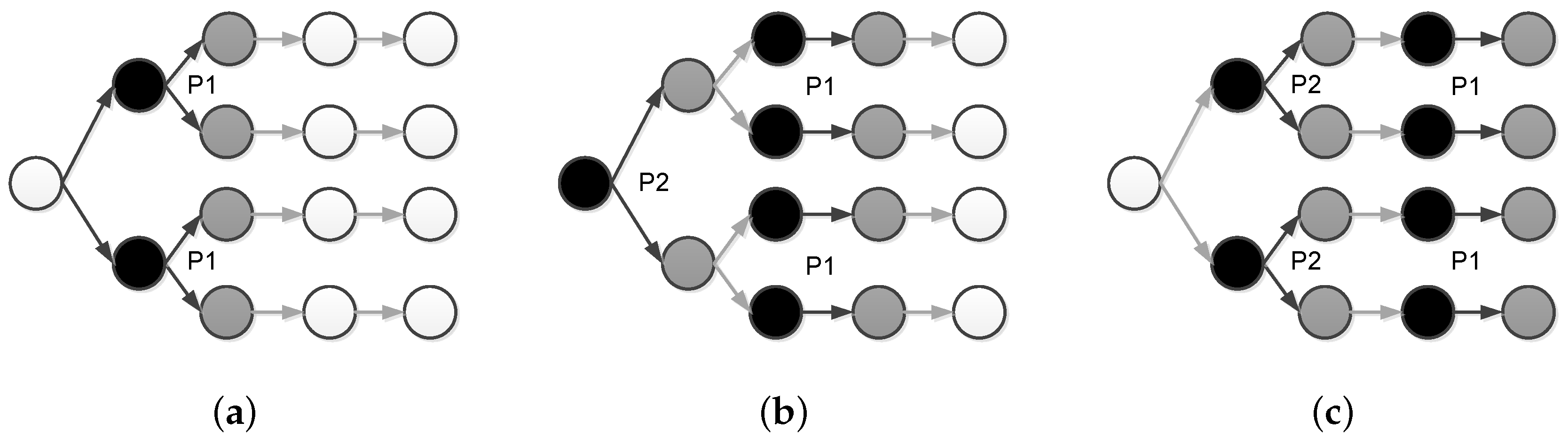
Constructive Interference
2.6.6. Sender Selection vs. Constructive Interference
2.7. Energy Efficiency
Short Summary
3. Open Issues
3.1. Summary of the Literature
- Towards exploiting the spatial wireless diversity. For example, the sender selection schemes try to exploit the best sender for each round of transmissions in the dissemination process. Besides, constructive interference is also based on the appropriate relative positions between the concurrent senders, which also tries to exploit the spatial opportunities for dissemination.
- Towards exploiting the temporal wireless diversity. For example the protocols [50] detects the time varying link quality and choose the time with the best link quality for transmission.
- Towards exploiting the wireless channel diversity. The works that uses multichannel techniques try to find the best strategy for wireless channel reuse to achieve high-efficiency bulk data dissemination.
3.2. Modeling of Dissemination Performance
3.3. Cross-Technology Interference and Communications
- Appropriate negotiation mechanism for CTI aware dissemination is required. The existing works apply FEC codes for error recovery, which do not support reliable broadcast since each link has a different error rate and the coding is likely to be inefficient.
- Hardware support. The existing works on CTI require high-granularity measurement of in-packet byte-level samples, which requires a >32 KHz timer. Another alternative is to use data-driven analysis to infer the in-packet error patterns [95,96] and then apply the recovery codes tailored for dissemination.
- Coding schemes that support batch transmissions. The existing works recover errors packet-by-packet. However in dissemination, the data packets are often transmitted in unit of pages. Therefore, if page-level recovery code can be implemented, dissemination can benefit from the advances in CTI.
3.4. Error Estimating Codes
3.5. Constructive Interference
3.6. Co-Existence with Other Network-Layer Protocols
3.7. Transparency over MAC Layer
3.8. Specific Applications
4. Conclusions
Acknowledgments
Author Contributions
References
- Mo, L.; He, Y.; Liu, Y.; Zhao, J.; Tang, S.; Li, X.; Dai, G. Canopy closure estimates with greenorbs: Sustainable sensing in the forest. In Proceedings of the 7th ACM Conference on Embedded Networked Sensor Systems, Berkeley, CA, USA, 4–6 November 2009.
- Du, W.; Xing, Z.; Li, M.; He, B.; Chua, L.H.C.; Miao, H. Optimal sensor placement and measurement of wind for water quality studies in urban reservoirs. In Proceedings of the 13th International Symposium on Information Processing in Sensor Networks (IPSN-14), Berlin, Germany, 15–17 April 2014; pp. 167–178.
- Du, W.; Li, Z.; Liando, J.C.; Li, M. From rateless to distanceless: Enabling sparse sensor network deployment in large areas. In Proceedings of the 12th ACM Conference on Embedded Network Sensor Systems, Memphis, TN, USA, 3–6 November 2014; pp. 134–147.
- Fadel, E.; Gungor, V.; Nassef, L.; Akkari, N.; Maik, M.A.; Almasri, S.; Akyildiz, I.F. A survey on wireless sensor networks for smart grid. Comput. Commun. 2015, 71, 22–33. [Google Scholar] [CrossRef]
- Chen, Y.; Shen, W.; Huo, H.; Xu, Y. A smart gateway for health care system using wireless sensor network. In Proceedings of the 2010 Fourth International Conference on Sensor Technologies and Applications (SENSORCOMM), Venice, Italy, 18–25 July 2010.
- Li, M.; Lin, H.J. Design and implementation of smart home control systems based on wireless sensor networks and power line communications. IEEE Trans. Ind. Electron. 2015, 62, 4430–4442. [Google Scholar] [CrossRef]
- Magno, M.; Polonelli, T.; Benini, L.; Popovici, E. A low-cost, highly scalable wireless sensor network solution to achieve smart LED light control for green buildings. IEEE Sens. J. 2015, 51, 2963–2973. [Google Scholar] [CrossRef]
- Zhao, Z.; Dong, W.; Bu, J.; Gu, T.; Chen, C.; Xu, X.; Pu, S. Exploiting link correlation for core-based dissemination in wireless sensor networks. In Proceedings of the 2014 Eleventh Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), Singapore, 30 June–3 July 2014.
- Wang, J.; Dong, W.; Cao, Z.; Liu, Y. On the delay performance in a large-scale wireless sensor network: Measurement, analysis, and implications. IEEE/ACM Trans. Netw. (TON) 2015, 23, 186–197. [Google Scholar] [CrossRef]
- Du, W.; Liando, J.C.; Zhang, H.; Li, M. Pando: Fountain-enabled fast data dissemination with constructive interference. IEEE/ACM Trans. Netw. 2016, PP, 1–14. [Google Scholar] [CrossRef]
- Zhao, Z.; Dong, W.; Bu, J.; Gu, T.; Min, G. Accurate and generic sender selection for bulk data dissemination in low-power wireless networks. IEEE/ACM Trans. Netw. 2016, PP, 1–12. [Google Scholar] [CrossRef]
- Ahmed, D.; Qureshi, J. Cooperative coded data dissemination for wireless sensor networks. In Proceedings of the 2016 13th Annual IEEE International Conference on Sensing, Communication, and Networking (SECON), London, UK, 27–30 June 2016; pp. 1–3.
- Srinivasan, K.; Jain, M.; Choi, J.I.; Azim, T.; Kim, E.S.; Levis, P.; Krishnamachari, B. The κ factor: Inferring protocol performance using inter-link reception correlation. In Proceedings of the Sixteenth Annual International Conference on Mobile Computing and Networking, Chicago, IL, USA, 20–24 September 2010; pp. 317–328.
- Suzuki, M.; Yamashita, Y.; Morikawa, H. Low-power, end-to-end reliable collection using glossy for wireless sensor networks. In Proceedings of the 2013 IEEE 77th Vehicular Technology Conference (VTC Spring), Dresden, Germany, 2–5 June 2013; pp. 1–5.
- Hou, I.H.; Tsai, Y.E.; Abdelzaher, T.F.; Gupta, I. Adapcode: Adaptive network coding for code updates in wireless sensor networks. In Proceedings of the 27th Conference on Computer Communications (INFOCOM 2008), Phoenix, AZ, USA, 15–17 April 2008.
- Yoo, J.; Yan, L.; Lee, S.; Kim, Y.; Yoo, H.J. A 5.2 mw self-configured wearable body sensor network controller and a 12 w wirelessly powered sensor for a continuous health monitoring system. IEEE J. Solid-State Circuits 2010, 45, 178–188. [Google Scholar] [CrossRef]
- Chen, B.; Zhou, Z.; Zhao, Y.; Yu, H. Efficient error estimating coding: Feasibility and applications. ACM SIGCOMM Comput. Commun. Rev. 2010, 40, 3–14. [Google Scholar] [CrossRef]
- Ferrari, F.; Zimmerling, M.; Thiele, L.; Saukh, O. Efficient network flooding and time synchronization with Glossy. In Proceedings of the 2011 IEEE 10th International Conference on Information Processing in Sensor Networks (IPSN), Chicago, IL, USA, 12–14 April 2011; pp. 73–84.
- Liu, Y.; He, Y.; Li, M.; Wang, J.; Liu, K.; Li, X. Does wireless sensor network scale? A measurement study on GreenOrbs. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 1983–1993. [Google Scholar] [CrossRef]
- Dong, W.; Chen, C.; Bu, J.; Liu, W. Optimizing relocatable code for efficient software update in networked embedded systems. ACM Trans. Sens. Netw. (TOSN) 2015, 11, 22. [Google Scholar] [CrossRef]
- Stathopoulos, T.; Heidemann, J.; Estrin, D. A Remote Code Update Mechanism for Wireless Sensor Networks; Technical Report; University of California: Berkeley, CA, USA, 2003. [Google Scholar]
- Ganesan, D.; Woo, A.; Culler, D.; Wicker, S. Complex Behavior at Scale: An Experimental Study of Low-Power Wireless Sensor Networks; Technical Report; Citeseer: Princeton, NJ, USA, 2002. [Google Scholar]
- Mainwaring, A.; Culler, D.; Polastre, J.; Szewczyk, R.; Anderson, J. Wireless sensor networks for habitat monitoring. In Proceedings of the 1st ACM International Workshop on Wireless Sensor Networks and Applications, Atlanta, GA, USA, 28 September 2002; pp. 88–97.
- Mao, X.; Miao, X.; He, Y.; Li, X.Y.; Liu, Y. CitySee: Urban CO2 monitoring with sensors. In Proceedings of the 31st Annual IEEE International Conference on Computer Communications (2012 IEEE INFOCOM), Orlando, FL, USA, 25–30 March 2012; pp. 1611–1619.
- Sugihara, R.; Gupta, R.K. Programming models for sensor networks: A survey. ACM Trans. Sens. Netw. (TOSN) 2008, 4, 8. [Google Scholar] [CrossRef]
- Crossbow, T. TelosB Data Sheet. Available online: www.willow.co.ukTelosB_Datasheet.pdf (accessed on 12 December 2016).
- Dandelski, C.; Wenning, B.L.; Kuhn, M.; Pesch, D. Broadcast storm problem in dense wireless lighting control networks. In Proceedings of the 2015 International Symposium on Wireless Communication Systems (ISWCS), Brussels, Belgium, 25–28 August 2015; pp. 91–95.
- Yu, J.; Wang, N.; Wang, G.; Yu, D. Connected dominating sets in wireless ad hoc and sensor networks—A comprehensive survey. Comput. Commun. 2013, 36, 121–134. [Google Scholar] [CrossRef]
- Romer, K.; Mattern, F. The design space of wireless sensor networks. IEEE Wirel. Commun. 2004, 11, 54–61. [Google Scholar] [CrossRef]
- Padhye, J.; Agarwal, S.; Padmanabhan, V.N.; Qiu, L.; Rao, A.; Zill, B. Estimation of link interference in static multi-hop wireless networks. In Proceedings of the 5th ACM SIGCOMM Conference on Internet Measurement, Berkeley, CA, USA, 19–21 October 2005; p. 28.
- Gummadi, R.; Wetherall, D.; Greenstein, B.; Seshan, S. Understanding and mitigating the impact of RF interference on 802.11 networks. ACM SIGCOMM Comput. Commun. Rev. 2007, 37, 385–396. [Google Scholar] [CrossRef]
- Hull, B.; Jamieson, K.; Balakrishnan, H. Mitigating congestion in wireless sensor networks. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA, 3–5 November 2004; pp. 134–147.
- Kulkarni, S.S.; Arumugam, M. Infuse: A TDMA based data dissemination protocol for sensor networks. Int. J. Distrib. Sens. Netw. 2006, 2, 55–78. [Google Scholar] [CrossRef]
- Levis, P.A.; Patel, N.; Culler, D.; Shenker, S. Trickle: A Self Regulating Algorithm for Code Propagation and Maintenance in Wireless Sensor Networks; Computer Science Division, University of California: Oakland, CA, USA, 2003. [Google Scholar]
- Levis, P.; Madden, S.; Polastre, J.; Szewczyk, R.; Whitehouse, K.; Woo, A.; Gay, D.; Hill, J.; Welsh, M.; Brewer, E.; et al. TinyOS: An operating system for sensor networks. In Ambient Intelligence; Springer: Berlin/Heidelberg, Germany, 2005; pp. 115–148. [Google Scholar]
- Liang, C.J.M.; Musăloiu-e, R.; Terzis, A. Typhoon: A reliable data dissemination protocol for wireless sensor networks. In Wireless Sensor Networks; Springer: Berlin, Germany, 2008; pp. 268–285. [Google Scholar]
- Hill, J.L.; Culler, D.E. Mica: A wireless platform for deeply embedded networks. IEEE Micro 2002, 22, 12–24. [Google Scholar] [CrossRef]
- Dutta, P.; Grimmer, M.; Arora, A.; Bibyk, S.; Culler, D. Design of a wireless sensor network platform for detecting rare, random, and ephemeral events. In Proceedings of the 4th International Symposium on Information Processing in Sensor Networks, Los Angeles, CA, USA, 25–27 April 2005; p. 70.
- Hui, J.W.; Culler, D. The dynamic behavior of a data dissemination protocol for network programming at scale. In Proceedings of the 2nd International Conference on Embedded Networked Sensor Systems, Baltimore, MD, USA, 3–5 November 2004; pp. 81–94.
- Jeong, J.; Kim, S.; Broad, A. Network Reprogramming; Technical Report; University of California: Berkeley, CA, USA, 2003. [Google Scholar]
- Naik, V.; Arora, A.; Sinha, P.; Zhang, H. Sprinkler: A reliable and energy efficient data dissemination service for wireless embedded devices. In Proceedings of the 26th IEEE International Real-Time Systems Symposium (RTSS 2005), Miami, FL, USA, 5–8 December 2005.
- Huang, L.; Setia, S. CORD: Energy-efficient reliable bulk data dissemination in sensor networks. In Proceedings of the 27th Conference on Computer Communications (INFOCOM 2008), Phoenix, AZ, USA, 13–18 April 2008.
- Zhao, Z.; Wang, Z.; Min, G.; Cao, Y. Highly-efficient bulk data transfer for structured dissemination in wireless embedded network systems. J. Syst. Archit. 2016. [Google Scholar] [CrossRef]
- Zhao, Z.; Bu, J.; Dong, W.; Gu, T.; Xu, X. CoCo+: Exploiting correlated core for energy efficient dissemination in wireless sensor networks. Ad Hoc Netw. 2016, 37, 404–417. [Google Scholar] [CrossRef]
- Sivakumar, R.; Akyildiz, I.F. GARUDA: Achieving effective reliability for downstream communication in wireless sensor networks. IEEE Trans. Mob. Comput. 2008, 7, 214–230. [Google Scholar]
- Dong, W.; Chen, C.; Liu, X.; Bu, J.; Liu, Y. Performance of bulk data dissemination in wireless sensor networks. In Distributed Computing in Sensor Systems; Springer: Berlin, Germany, 2009; pp. 356–369. [Google Scholar]
- Doddavenkatappa, M.; Chan, M.C.; Leong, B. Splash: Fast data dissemination with constructive interference in wireless sensor networks. In Proceedings of the USENIX Symposium on Networked Systems Design and Implementation (NSDI), Lombard, IL, USA, 2–5 April 2013.
- Kulkarni, S.S.; Wang, L. MNP: Multihop network reprogramming service for sensor networks. In Proceedings of the 25th IEEE International Conference on Distributed Computing Systems (CDCS 2005), Columbus, OH, USA, 6–10 June 2005; pp. 7–16.
- De, P.; Liu, Y.; Das, S.K. ReMo: An energy efficient reprogramming protocol for mobile sensor networks. In Proceedings of the Sixth Annual IEEE International Conference on Pervasive Computing and Communications (PerCom 2008), Hong Kong, China, 17–21 March 2008; pp. 60–69.
- Dong, W.; Liu, Y.; Wang, C.; Liu, X.; Chen, C.; Bu, J. Link quality aware code dissemination in wireless sensor networks. In Proceedings of the 2011 19th IEEE International Conference on Network Protocols (ICNP), Vancouver, BC, Canada, 17–20 October 2011; pp. 89–98.
- Zhu, T.; Zhong, Z.; He, T.; Zhang, Z.L. Exploring link correlation for efficient flooding in wireless sensor networks. In Proceedings of the 7th USENIX Conference on Networked Systems Design and Implementation (NSDI 2010), San Jose, CA, USA, 28–30 April 2010; pp. 49–64.
- Guo, S.; Kim, S.M.; Zhu, T.; Gu, Y.; He, T. Correlated flooding in low-duty-cycle wireless sensor networks. In Proceedings of the 2011 19th IEEE International Conference on Network Protocols (ICNP), Vancouver, BC, Canada, 17–20 October 2011; pp. 383–392.
- Alam, S.I.; Sultana, S.; Hu, Y.C.; Fahmy, S. SYREN: Synergistic link correlation-aware and network coding-based dissemination in wireless sensor networks. In Proceedings of the 2013 IEEE 21st International Symposium on Modelling, Analysis & Simulation of Computer and Telecommunication Systems, San Francisco, CA, USA, 14–16 August 2013; pp. 485–494.
- Subramanian, J.; Morris, R.; Balakrishnan, H. UFlood: High-throughput flooding over wireless mesh networks. In Proceedings of the 31st Annual IEEE International Conference on Computer Communications (2012 IEEE INFOCOM), Orlando, FL, USA, 25–30 March 2012.
- Hagedorn, A.; Starobinski, D.; Trachtenberg, A. Rateless deluge: Over-the-air programming of wireless sensor networks using random linear codes. In Proceedings of the 7th International Conference on Information Processing in Sensor Networks, St. Louis, MO, USA, 22–24 April 2008; pp. 457–466.
- Rossi, M.; Zanca, G.; Stabellini, L.; Crepaldi, R.; Harris, A.; Zorzi, M. Synapse: A network reprogramming protocol for wireless sensor networks using fountain codes. In Proceedings of the 5th Annual IEEE Communications Society Conference on Sensor, Mesh and Ad Hoc Communications and Networks (SECON’08), San Francisco, CA, USA, 16–20 June 2008; pp. 188–196.
- Dong, W.; Chen, C.; Liu, X.; Bu, J.; Gao, Y. A lightweight and density-aware reprogramming protocol for wireless sensor networks. IEEE Trans. Mob. Comput. 2011, 10, 1403–1415. [Google Scholar] [CrossRef]
- Gao, Y.; Bu, J.; Dong, W.; Chen, C.; Rao, L.; Liu, X. Exploiting concurrency for efficient dissemination in wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2013, 24, 691–700. [Google Scholar] [CrossRef]
- Wang, L.; Kulkarni, S.S. Gappa: Gossip based multi-channel reprogramming for sensor networks. In Distributed Computing in Sensor Systems; Springer: Berlin/Heidelberg, Germany, 2006; pp. 119–134. [Google Scholar]
- Dong, W.; Chen, C.; Liu, X.; Teng, G.; Bu, J.; Liu, Y. Bulk data dissemination in wireless sensor networks: Modeling and analysis. Comput. Netw. 2012, 56, 2664–2676. [Google Scholar] [CrossRef]
- Aguayo, D.; Bicket, J.; Biswas, S.; Judd, G.; Morris, R. Link-level measurements from an 802.11 b mesh network. ACM SIGCOMM Comput. Commun. Rev. 2004, 34, 121–132. [Google Scholar] [CrossRef]
- Cerpa, A.; Wong, J.L.; Potkonjak, M.; Estrin, D. Temporal properties of low power wireless links: Modeling and implications on multi-hop routing. In Proceedings of the 6th ACM International Symposium on Mobile Ad Hoc Networking and Computing, Urbana, IL, USA, 25–27 May 2005; pp. 414–425.
- Kumaran, K.; Golowich, S.E.; Borst, S. Correlated shadow-fading in wireless networks and its effect on call dropping. Wirel. Netw. 2002, 8, 61–71. [Google Scholar] [CrossRef]
- Agrawal, P.; Patwari, N. Correlated link shadow fading in multi-hop wireless networks. IEEE Trans. Wirel. Commun. 2009, 8, 4024–4036. [Google Scholar] [CrossRef]
- Gungor, V.C.; Hancke, G.P. Industrial wireless sensor networks: Challenges, design principles, and technical approaches. IEEE Trans. Ind. Electron. 2009, 56, 4258–4265. [Google Scholar] [CrossRef]
- Biswas, S.; Morris, R. ExOR: Opportunistic multi-hop routing for wireless networks. ACM SIGCOMM Comput. Commun. Rev. 2005, 35, 133–144. [Google Scholar] [CrossRef]
- Tian, S.; Li, Y.; Shirvanimoghaddam, M.; Vucetic, B. A physical-layer rateless code for wireless channels. IEEE Trans. Commun. 2013, 61, 2117–2127. [Google Scholar] [CrossRef]
- Rossi, M.; Bui, N.; Zanca, G.; Stabellini, L.; Crepaldi, R.; Zorzi, M. SYNAPSE++: Code dissemination in wireless sensor networks using fountain codes. IEEE Trans. Mob. Comput. 2010, 9, 1749–1765. [Google Scholar] [CrossRef]
- Chipcon, A.S. CC2420 Datasheet-2.4 GHz IEEE 802.15. 4/ZigBee-Ready RF Transceiver (Rev. B); Texas Instruments: Dallas, TX, USA, 2007. [Google Scholar]
- Tobagi, F.A.; Kleinrock, L. Packet switching in radio channels: Part II—The hidden terminal problem in carrier sense multiple-access and the busy-tone solution. IEEE Trans. Commun. 1975, 23, 1417–1433. [Google Scholar] [CrossRef]
- Huang, P.; Xiao, L.; Soltani, S.; Mutka, M.W.; Xi, N. The evolution of MAC protocols in wireless sensor networks: A survey. IEEE Commun. Surv. Tutor. 2013, 15, 101–120. [Google Scholar] [CrossRef]
- Raman, B.; Chebrolu, K.; Bijwe, S.; Gabale, V. PIP: A connection-oriented, multi-hop, multi-channel TDMA-based MAC for high throughput bulk transfer. In Proceedings of the 8th ACM Conference on Embedded Networked Sensor Systems, Zurich, Switzerland, 3–5 November 2010; pp. 15–28.
- Duquennoy, S.; Landsiedel, O.; Voigt, T. Let the tree Bloom: Scalable opportunistic routing with ORPL. In Proceedings of the 11th ACM Conference on Embedded Networked Sensor Systems, Roma, Italy, 11–15 November 2013; p. 2.
- Wang, Y.; He, Y.; Mao, X.; Liu, Y.; Huang, Z.; Li, X. Exploiting constructive interference for scalable flooding in wireless networks. In Proceedings of the 31st Annual IEEE International Conference on Computer Communications (2012 IEEE INFOCOM), Orlando, FL, USA, 25–30 March 2012; pp. 2104–2112.
- Doddavenkatappa, M.; Chan, M.C.; Ananda, A.L. Indriya: A low-cost, 3D wireless sensor network testbed. In Testbeds and Research Infrastructure. Development of Networks and Communities; Springer: Berlin/Heidelberg, Germany, 2012; pp. 302–316. [Google Scholar]
- Handziski, V.; Köpke, A.; Willig, A.; Wolisz, A. TWIST: A scalable and reconfigurable testbed for wireless indoor experiments with sensor networks. In Proceedings of the 2nd International Workshop on Multi-Hop Ad Hoc Networks: From Theory to Reality, Florence, Italy, 26 May 2006; pp. 63–70.
- Gnawali, O.; Fonseca, R.; Jamieson, K.; Moss, D.; Levis, P. Collection tree protocol. In Proceedings of the ACM Conference on Embedded Network Sensor Systems, Berkeley, CA, USA, 4–6 November 2009.
- Han, C.C.; Kumar, R.; Shea, R.; Srivastava, M. Sensor network software update management: A survey. Int. J. Netw. Manag. 2005, 15, 283–294. [Google Scholar] [CrossRef]
- Rault, T.; Bouabdallah, A.; Challal, Y. Energy efficiency in wireless sensor networks: A top-down survey. Comput. Netw. 2014, 67, 104–122. [Google Scholar] [CrossRef]
- Moss, D.; Hui, J.; Klues, K. Low Power Listening; Technical Report; University of California: Berkeley, CA, USA, 2007. [Google Scholar]
- Fonseca, R.; Dutta, P.; Levis, P.; Stoica, I. Quanto: Tracking energy in networked embedded systems. In Proceedings of the 8th USENIX Conference on Operating Systems Design and Implementation (OSDI), San Diego, CA, USA, 8–10 December 2008; Volume 8, pp. 323–338.
- Dutta, P.; Dawson-Haggerty, S.; Chen, Y.; Liang, C.J.M.; Terzis, A. Design and evaluation of a versatile and efficient receiver-initiated link layer for low-power wireless. In Proceedings of the 8th ACM Conference on Embedded Networked Sensor Systems, Zurich, Switzerland, 3–5 November 2010; pp. 1–14.
- Gu, Y.; He, T. Data forwarding in extremely low duty-cycle sensor networks with unreliable communication links. In Proceedings of the 5th International Conference on Embedded Networked Sensor Systems, Sydney, Australia, 5–9 November 2007; pp. 321–334.
- Lu, G.; Krishnamachari, B.; Raghavendra, C.S. An adaptive energy-efficient and low-latency MAC for data gathering in wireless sensor networks. In Proceedings of the IEEE 18th International Parallel and Distributed Processing Symposium, Santa Fe, NM, USA, 26–30 April 2004; p. 224.
- Gao, Y.; Chen, C.; Liu, X.; Bu, J.; Dong, W.; Xu, X. Reprogramming over Low Power Link Layer in Wireless Sensor Networks. In Proceedings of the 2013 IEEE 10th International Conference on Mobile Ad-Hoc and Sensor Systems (MASS), Hangzhou, China, 14–16 October 2013; pp. 461–469.
- Yang, P.; Yan, Y.; Li, X.Y.; Zhang, Y.; Tao, Y.; You, L. Taming cross-technology interference for Wi-Fi and ZigBee coexistence networks. IEEE Trans. Mob. Comput. 2016, 15, 1009–1021. [Google Scholar] [CrossRef]
- Hithnawi, A.; Shafagh, H.; Duquennoy, S. TIIM: Technology-independent interference mitigation for low-power wireless networks. In Proceedings of the 14th International Conference on Information Processing in Sensor Networks, Seattle, WA, USA, 14–16 April 2015; pp. 1–12.
- Dong, W.; Yu, J.; Zhang, P. Exploiting error estimating codes for packet length adaptation in low-power wireless networks. IEEE Trans. Mob. Comput. 2015, 14, 1601–1614. [Google Scholar] [CrossRef]
- Noda, C.; Pérez-Penichet, C.M.; Seeber, B.; Zennaro, M.; Alves, M.; Moreira, A. On the scalability of constructive interference in Low-Power wireless networks. In Proceedings of the European Conference on Wireless Sensor Networks, Porto, Portugal, 9–11 February 2015; Springer: Cham, Switzerland, 2015; pp. 250–257. [Google Scholar]
- Li, J.W.; Li, S.N.; Zhang, Y.; Gu, T.; Law, Y.W.; Yang, Z.; Zhou, X.; Palaniswami, M. An analytical model for coding-based reprogramming protocols in lossy wireless sensor networks. IEEE Trans. Comput. 2017, 66, 24–37. [Google Scholar] [CrossRef]
- Son, D.; Lee, J.; Qiao, S.; Ghaffari, R.; Kim, J.; Lee, J.E.; Song, C.; Kim, S.J.; Lee, D.J.; Jun, S.W.; et al. Multifunctional wearable devices for diagnosis and therapy of movement disorders. Nat. Nanotechnol. 2014, 9, 397–404. [Google Scholar] [CrossRef] [PubMed]
- Pyattaev, A.; Johnsson, K.; Andreev, S.; Koucheryavy, Y. Communication challenges in high-density deployments of wearable wireless devices. IEEE Wirel. Commun. 2015, 22, 12–18. [Google Scholar] [CrossRef]
- Hauer, J.H.; Willig, A.; Wolisz, A. Mitigating the effects of RF interference through RSSI-based error recovery. In Proceedings of the 7th European Conference on Wireless Sensor Networks, Coimbra, Portugal, 17–19 February 2010; Springer: Berlin/Heidelberg, Germany, 2010; pp. 224–239. [Google Scholar]
- Dong, W.; Yu, J.; Liu, X. CARE: Corruption-aware retransmission with adaptive coding for the low-power wireless. In Proceedings of the 2015 IEEE 23rd International Conference on Network Protocols (ICNP), San Francisco, CA, USA, 10–13 November 2015; pp. 235–244.
- Hermans, F.; Rensfelt, O.; Voigt, T.; Ngai, E.; Norden, L.Å.; Gunningberg, P. SoNIC: Classifying interference in 802.15. 4 sensor networks. In Proceedings of the 12th International Conference on Information Processing in Sensor Networks, Philadelphia, PA, USA, 8–11 April 2013; pp. 55–66.
- Zheng, X.; Cao, Z.; Wang, J.; He, Y.; Liu, Y. ZiSense: Towards interference resilient duty cycling in wireless sensor networks. In Proceedings of the 12th ACM Conference on Embedded Network Sensor Systems, Memphis, TN, USA, 3–6 November 2014; pp. 119–133.
- Baccour, N.; Koubâa, A.; Mottola, L.; Zúñiga, M.A.; Youssef, H.; Boano, C.A.; Alves, M. Radio link quality estimation in wireless sensor networks: A survey. ACM Trans. Sens. Netw. (TOSN) 2012, 8, 34. [Google Scholar] [CrossRef]
- Dezfouli, B.; Radi, M.; Whitehouse, K.; Razak, S.A.; Tan, H.P. CAMA: Efficient modeling of the capture effect for low-power wireless networks. ACM Trans. Sens. Netw. (TOSN) 2014, 11, 20. [Google Scholar] [CrossRef]
- Kim, B.; Lavrova, O. Optimal power flow and energy-sharing among multi-agent smart buildings in the smart grid. In Proceedings of the 2013 IEEE Energytech, Cleveland, OH, USA, 21–23 May 2013; pp. 1–5.
- Tsakalakis, M.; Bourbakis, N. Health care sensor—Based systems for point of care monitoring and diagnostic applications: A brief survey. In Proceedings of the 2014 36th Annual International Conference of the IEEE Engineering in Medicine and Biology Society (EMBC), Chicago, IL, USA, 26–30 August 2014; pp. 6266–6269.
- Teymorian, A.; Cheng, W.; Ma, L.; Cheng, X.; Lu, X.; Lu, Z. 3D underwater sensor network localization. IEEE Trans. Mob. Comput. 2009, 8, 1610–1621. [Google Scholar] [CrossRef]
- Lee, S.C.; Chung, W.Y. Ad-hoc and query-based indoor air-conditioning system using low power wireless sensor network. In Proceedings of the International Conference on Convergence Information Technology, Gyeongju, Korea, 21–23 November 2007; pp. 481–486.




| Operation | nAh |
|---|---|
| Receive a Packet | 8.000 |
| Transmit a Packet | 20.000 |
| Idle-Listen for 1 ms | 1.250 |
| EEPROM Read data (per byte) | 1.111 |
| EEPROM Write/Erase data (per byte) | 83.333 |
| Protocols | Platform | DataObj Aware | MAC Layer | Negotiation Messages | Control Mess- Age Transmission | Other Aspects |
|---|---|---|---|---|---|---|
| Infuse [33] | MICA2 [37] TelosB [26] XSM [38] | No | TDMA | Implicit ACK | Broadcast | Out-of-order transmission |
| Typhoon [36] | Unknown | No | TDMA | Active ACK Periodic REQ (page level) | Unicast ACK Broadcast REQ | CDS structure |
| SPIN [28] | None | Yes | CSMA | Periodic ADV Active REQ (page level) | Broadcast ADV Unicast REQ | Negotiation suppression |
| Trickle [34] | MICA2 | Yes | CSMA | Periodic ADV Active NACK | Broadcast | ADV suppression |
| Deluge [39] | MICA2 TelosB | Yes | CSMA | Periodic ADV Active NACK | Broadcast ADV Unicast NACK | NACK suppression |
| Protocols | Fineness | Recovery Mechanism | Pipeline Spacing | Transmission Sequence | Strucure |
|---|---|---|---|---|---|
| Deluge [39] | Page level | NACK | 3 hops | In-sequence | None |
| Modeling [46] | Page level (with optimal page size) | NACK | 3 hops | In-sequence | None |
| Sprinkler [41] | Packet level | Piggybacked ACK | 3 hops | In-sequence | CDS |
| GARUDA [45] | Packet level | Piggybacked ACK | 3 hops | Out-of-sequence | CDS |
| Typhoon [36] | Page level | NACK | 2 hops | In sequence | None |
| Splash [47] | Packet level | NACK (in recovery phase) | 2 hops | Out-of-sequence | Tree |
| Protocols | Platform | Information Used | Contention Mechanism | Topology | Initiation |
|---|---|---|---|---|---|
| Deluge [39] | MICA2 TelosB | None | REQ suppression | Dynamic | Receiver |
| Sprinkler [41] | Mesh nodes | Location | Not addressed | Fixed | Pre-selected |
| MNP [48] | MICA2 | one-hop topology | Message exchange | Dynamic | Sender |
| CORD [42] | MICA2 TelosB | one-hop topology, PRR | Pre-scheduled | Fixed | Pre-selected |
| Remo [49] | MICA2 | RSSI, LQI | REQ suppression | Mobile dynamic | Receiver |
| ECD [50] | TelosB | one-hop topology, PRR | Back-off | Dynamic | Sender |
| Collective Flooding [51] | MICAz | one-hop topology, PRR link correlation | Back-off | Dynamic | Sender |
| Correlated Flooding [52] | MICAz | one-hop topology, PRR link correlation | Message exchange | Fixed | Pre-selected |
| SYREN [53] | TelosB | one-hop topology, PRR link correlation | Back-off | Dynamic | Sender |
| UFlood [54] | Mesh nodes | one-hop topology, PRR link correlation, bit rates | Message exchange | Dynamic | Sender |
| Protocols | Coding Strategy | Decoding Delay | Memory Overhead | Other Focus |
|---|---|---|---|---|
| Rateless Deluge | Random linear code | 6.96 s | 2.44 KB | Up to 20 pkts per page on TelosB motes for acceptable decoding delay |
| Synapse | Fountain code | 462 ms | 1.5 KB | Employing ARG optimization |
| ReXOR | XOR | 184 ms | 1.59 KB | |
| AdapCode | Linear Combination | 430 ms | 1.4 KB | |
| UFlood | Random network coding | >7 s | >5 KB | The overhead is acceptable for Mesh networks |
| MT-Deluge | Random linear coding | 2.08 s | 2.44 KB | Using Multi-thread to improvethe concurrency of decoding and receiving |
| Splash | XOR | 184 ms | 1.76 KB |
© 2017 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Xu, Z.; Hu, T.; Song, Q. Bulk Data Dissemination in Low Power Sensor Networks: Present and Future Directions. Sensors 2017, 17, 156. https://doi.org/10.3390/s17010156
Xu Z, Hu T, Song Q. Bulk Data Dissemination in Low Power Sensor Networks: Present and Future Directions. Sensors. 2017; 17(1):156. https://doi.org/10.3390/s17010156
Chicago/Turabian StyleXu, Zhirong, Tianlei Hu, and Qianshu Song. 2017. "Bulk Data Dissemination in Low Power Sensor Networks: Present and Future Directions" Sensors 17, no. 1: 156. https://doi.org/10.3390/s17010156
APA StyleXu, Z., Hu, T., & Song, Q. (2017). Bulk Data Dissemination in Low Power Sensor Networks: Present and Future Directions. Sensors, 17(1), 156. https://doi.org/10.3390/s17010156





