Abstract
Cognitive radio can significantly improve the spectrum efficiency, and spectrum handoff is considered as an important functionality to guarantee the quality of service (QoS) of primary users (PUs) and the continuity of data transmission of secondary users (SUs). In this paper, we propose an analytical framework based on a preemptive repeat identical (PRI) M/G/1 queuing network model to characterize spectrum handoff behaviors with general service time distribution of both primary and secondary connections, multiple interruptions and transmission delay resulting from the appearance of primary connections. Then, we derive the close-expression of the extended data delivery and the system sojourn time in both staying and changing scenarios. In addition, based on analysis of spectrum handoff behaviors resulting from multiple interruptions caused by the appearance of the primary connections, we investigate the traffic-adaptive policy, by which the considered SU will optimally adjust its handoff spectrum policy. Moreover, we investigate the admissible region and provide the reference for designing the admission control rule for the arriving secondary connection requests. Finally, simulation results verify that our proposed analytical framework is reasonable and can provide the reference for executing the optimal spectrum handoff strategy and designing the admission control rule for the SU in cognitive radio networks.
1. Introduction
Cognitive radio (CR) has been put forward for more than ten years for its promising future, which could significantly improve the spectrum efficiency by allowing the secondary users (SUs) to access the spare licensed spectrum of the primary users (PUs) or the unlicensed spectrum opportunistically [1,2]. However, the SU will impose challenges for preserving the desired quality of service (QoS) of the PU, mainly including four aspects: spectrum sensing, spectrum decision, spectrum sharing, and spectrum mobility [3,4,5]. For the high fluctuation in dynamic CR networks, the SU may be interrupted by the appearance of the PU or the awful channel condition. Therefore, spectrum mobility is an important feature that will guarantee continuous SU data transmission [6,7]. Considered as the main issue in spectrum mobility, spectrum handoff is the process that a SU stays or changes its operating channel upon the appearance of a PU and then re-builds a new communication connection to resume or repeat its data transmission.
Generally, in cognitive radio networks, there are mainly two spectrum handoff types: the reactive approach and the proactive approach depending on the handoff decision time instant [8,9,10]. In the reactive approach, the SU will execute spectrum sensing and resume or repeat its data transmission on a sensed idle channel after handoff triggering factor occurs. The SU will make the handoff decision when interrupted. Although this process can make sure that the SU can find an available channel to continue its data transmission, it will cause a large delay for sensing different channels [11,12]. In the proactive approach, the SU will make the handoff decision before being interrupted. This means that the SU will switch to the prior determined target channel when the handoff triggering factor happens. This approach extremely decreases the delay without spectrum sensing, but it may cause an obsolescence problem that the prior decided target channel is no longer available [13,14]. In other words, these two approaches have their own advantages and disadvantages.
According to different triggering factors, the spectrum handoff modeling techniques are categorized into connection-based and slot-based [15]. In the context of the connection-based spectrum handoffs, the effects of multiple interruptions resulting from PUs are considered in an event-driven manner. By contract, the slot-based modeling technique characterizes multiple interruptions to the SUs in a time-driven manner. That is, the appearance of the PU will trigger the spectrum handoff process in the connection-based scheme, whereas for the slot-based scheme every time slot can be a triggering factor to start to perform a spectrum handoff.
In [15], the preemptive resume priority (PRP) M/G/1 queuing network model was proposed to characterize the connection-based spectrum handoff behaviors with multiple interruptions in multiple-channel CR networks, where the SU can significantly reduce the extended data delivery time by applying the traffic-adaptive target channel sequence selection method. In [16,17,18,19,20,21,22,23], multiple interruptions and the extended data delivery time were also studied in the PRP M/G/1 queuing network model. However, the authors only considered a single-channel CR network. In [24,25,26,27,28], an optimal proactive target channel sequence selection algorithm was proposed to minimize the cumulative spectrum handoff delay in multiple-channel CR networks. A low-complexity greedy algorithm was also investigated based on the trellis diagram. However, it supposed that the newly arriving secondary connection was capable of calculating its optimal target channel sequence while the existing secondary connections did not change their predetermined target channel sequences. Obviously, this assumption neglected the effects to the existing secondary connections, which were caused by the newly arriving traffic loads. In [29], a probabilistic selection algorithm was proposed to predetermine the initial and target channel sequence for a considered secondary connection, which applied the convex optimization theory to minimize the secondary connection extended service and sojourn time. To characterize the multiple-channel CR networks, a queuing analytical framework was built based on the PRP Geom/Geom/1 queuing system model and two policies, which were “stay” and “change”, respectively. In order to reduce the complexity of the algorithm, it proposed the equiprobable target channel selection and the primary traffic-based target channel selection, which were not optimal selection schemes for the considered secondary connection. In general, in [11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29], all the CR networks were established based on the preemptive resume priority queuing system model. That is, when the secondary connection was interrupted due to the appearance of the primary connection, the interrupted secondary connection would reactively or proactively determine a best available channel to resume its unfinished data transmission. However, in some other scenarios, the interrupted secondary connection may adopt the preemptive repeat scheduling discipline rather than the preemptive resume one. The preemptive repeat priority queue is divided into the preemptive repeat identical (PRI) and the preemptive repeat different (PRD) priority queue. Since the PRD could be viewed as a “simplified” version of the PRI priority queue [30], we focus on the PRI priority queue in this paper.
The PRI priority scheduling discipline was used in the carrier sense multiple access collision detection (CSMA-CD) protocols to describe a fiber optical bus network, which connected a general finite number of stations [31]. Each station with an infinite queuing capacity had different priorities to access the bus network and possibly overwrite information of the downstream stations. By using the randomization solution form and lattice path combinatorics, the transient probability was analyzed for a PRI M/M/1 queuing mode in [32]. The PRI priority queue also was applied to establish an un-slotted optical metropolitan area network (MAN) ring operating with asynchronous variable length optical packets [33,34]. In a ring-based local area network (LAN), a preemptive repeat protocol was proposed to characterize voice-data integration [35], where voice stations had the priority of accessing the ring network. That is, voice stations could overwrite the information of the data stations. Similarly, in some scenarios, the PRI priority scheduling discipline is also worthy of investigating in CR networks. To the best of our knowledge, the preemptive repeat scheduling discipline for characterizing spectrum handoff behaviors in CR networks with multiple interruptions has rarely been studied.
In this paper, unlike [11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29], we propose an analytical framework based on the preemptive repeat identical (PRI) M/G/1 queuing network model to characterize spectrum handoff behaviors with general service time distribution of both primary and secondary connections, multiple interruptions and transmission time delay resulting from the appearance of primary connections. Under the preemptive repeat policy, when interruptions happen, the secondary connection will start from the beginning. In other words, the data that have been transmitted prior to the interruption are abandoned. The contributions of this paper can be summarized in the following:
- (1)
- We propose an analytical framework based on the PRI M/G/1 queuing network model to analyze spectrum handoff behaviors, and derive the close-expression of extended data delivery and sojourn time in both staying and changing scenarios, respectively.
- (2)
- Based on analysis of spectrum handoff behaviors resulting from multiple interruptions caused by the appearance of the primary connections, we investigate the traffic-adaptive policy, by which the considered SU will optimally adjust its handoff spectrum policy (i.e., the staying policy and the changing policy) to reduce the delay resulting from the appearance of primary connections.
- (3)
- Finally, we investigate the admissible region and provide a reference for designing the admission control rule for the arriving secondary connection requests.
The rest of this paper is organized as follows. Section 2 describes the system model and assumptions. Section 3 analyzes the transmission delay caused by spectrum handoff behaviors in both staying and changing scenarios, and derives the corresponding expressions. Section 4 presents simulation results. Section 5 finally draws a conclusion.
2. System Model Description
In this paper, we consider a time-slotted CR network with independent primary channels, based on the PRI M/G/1 queuing network model. Each channel has two kinds of queues: high-priority and the low-priority queue. The PUs and SUs enter the high-priority queue and the low-priority queue, respectively, and build corresponding primary and secondary connections. The arrival processes of the primary and secondary connections at channel are assumed to be Poisson processes with rates and , respectively. Furthermore, let random valuables and denote the general service time distribution, respectively, with the corresponding probability density function (PDF) and . In the same priority queue, the user accesses to the channel based on the first-come-first-served (FCFS) discipline and will transmit data after the initial handshaking at its default initial channel. Since the PU has the preemptive priority, the SU in low-priority queue can access the channel to transmit data only when the high-priority queue is empty. In the case that the secondary connection is interrupted, the SU will stay on the current operating channel or switch to the target channel to repeat its data transmission.
In addition, each SU is equipped with two kinds of antennas: the directional antenna and the omnidirectional antenna. The directional antenna is used for transmitting or receiving data, whereas the omnidirectional antenna is capable of sensing whether the operating channel is busy or not. To avoid causing harmful interference to the PUs, the listen-before-talk access scheme in the IEEE 802.22 standard [36] is adopted. In this scheme, the SU must perform spectrum sensing at the beginning of each time slot and then transmits its data transmission in the rest of the slot only when the operating channel is detected to be idle. For simplicity, the spectrum sensing is supposed to be perfect without missed detections or false alarms as in [11,12,13,14,15,16,17,18,19,20,21,22,23,24,25,26,27,28,29]. Note that a channel can only be occupied by one user at any time.
2.1. Staying Policy
Firstly, we analyze the behaviors of a considered SU under the staying policy. As shown in Figure 1, at time instant , the SU has to enter the low-priority queue of its default initial channel , which is predetermined by the loading balancing spectrum decision [37] or the optimal probabilistic initial channel selection method [29]. In the staying policy, the SU will always stay in this channel until its data transmission is completed. Let denote the duration from the instant when the SU enters the low-priority queue of channel to the instant when it transmits data for the first time, and denote the duration that elapses from the instant when the SU starts to transmit its data until it is interrupted by the PU for the ith time. In the PRI M/G/1 queuing network model, the effective service time is lost in the repeat scheduling discipline. Note that the SU completes its data transmission after experiencing interruptions. Denote as the service time for the newly arriving PU at the ith interruption. Thus, we have:
where represents the extended data delivery time in the staying policy, and:
where denotes the system sojourn time in the staying policy from the instant when the SU enters the low-priority queue to the instant when its data transmission is completed.
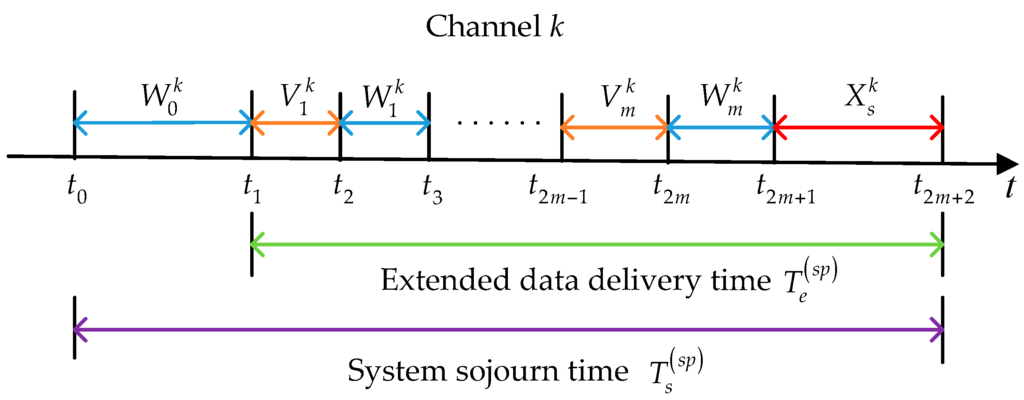
Figure 1.
The behaviors of a secondary user (SU) under the staying policy in the preemptive repeat identical (PRI) M/G/1 queuing network model.
2.2. Changing Policy
Then, we analyze the behaviors of the considered SU under the changing policy. In this scenario, we assume that the target channel sequence with initial channel is denoted as , , , where is the target channel at the ith interruption and is defined as the maximum allowable interruption times. In the proactive spectrum handoff process, the target channel sequence is determined before data transmission. Note that in the changing policy as in [15,29]. In other words, the SU will switch to the target channel as long as the interruption happens. If the target channel is idle, the SU can execute data transmission immediately. Otherwise, according to the proactive spectrum handoff discipline, the SU has to wait until the channel is idle.
The whole proactive spectrum handoff process is illustrated in Figure 2. The considered SU enters the pre-assigned initial channel , and has to wait until the initial channel is idle. The waiting time on initial channel can be represented as . From the instant when the considered SU transmits its data to the instant when the SU completes its data transmission, it will encounter multiple interruptions caused by the appearance of the primary connections. As shown in Figure 2, let denote the waiting time of the SU before starting data transmission at target channel and denote the switching time. Suppose that the SU finishes its data transmission at target channel . Then, we have:
where represents the delay caused by the ith interruption.
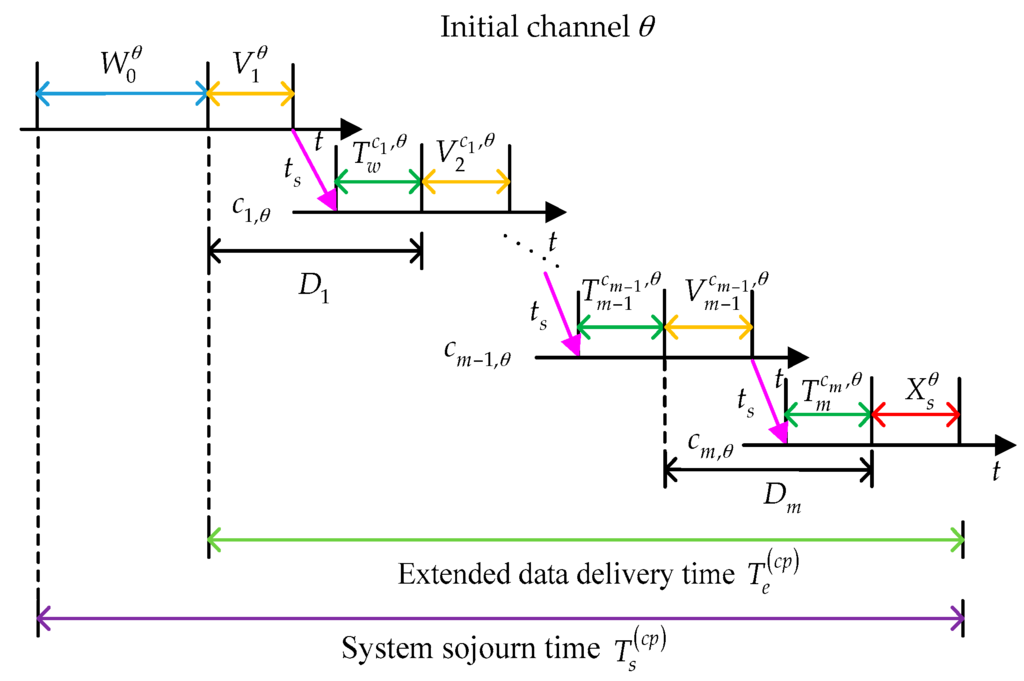
Figure 2.
The behaviors of a secondary user (SU) under the changing policy in the preemptive repeat identical (PRI) M/G/1 queuing network model.
Based on the analysis above, the extended data delivery time under the changing policy can be given by:
and the system sojourn time can be expressed as:
3. Analysis and Derivation for Parameters
In this section, we derive the average extended data delivery time and the system sojourn time of the SU based on both staying and changing policies, in the PRI M/G/1 queuing network.
3.1. Derivation under Staying Policy
Suppose that is a random variable, which denotes the number of times that the SU has been interrupted until its data transmission is completed. Let represent the probability that the SU enters a channel for service and completes its data transmission without being interrupted. Obviously, can be seen as a geometrical distribution with the probability mass function:
Thus, the average number of times can be derived as the following:
For further derivation, we give two propositions first.
Proposition 1: Given the arrival rate of PUs and the PDF of the SU service time distribution on channel , we have .
Proof: According to the assumptions above, the arrivals of PUs occur in a Poisson process. Thus, within time interval , the probability that PUs arrive on channel can be given by:
Obviously, the probability that no PU appears on channel is . In addition, represents the PDF of the service time distribution of the SU on channel . Therefore, the average probability that the SU can enter for service and complete the service without being interrupted can be expressed as:
As a result, the conclusion in proposition 1 is obtained.
Proposition 2: Given the general service time distribution and the corresponding PDF on channel , we have for .
Proof: We prove this conclusion by the renewal theory. Suppose that denotes the length of the inter-arrival gap that the PU arrives by random incidence, whose PDF is . Then, we have:
where denotes the effective service time for the SU before interrupted and represents the residual time of the inter-arrival gap, whose PDF is .
Firstly, we derive the expression of . The probability that a PU arrival occurs in a gap is given by , which can be supposed to be directly proportional to the length of the gap and relative occurrence of such gap. Thus, we have:
where is the proportionality coefficient. Thus,
In addition,
Comparing Equations (12) and (13), we have:
Then, we need to derive the express of . For the given gap length , the PU can arrive at anywhere within the gap. Thus, the conditional PDF of is given by:
Therefore, we have the marginal PDF of :
Then, we have:
Finally, substituting Equation (17) into Equation (10), we can obtain:
Based on Equations (1), (7) and (18), the lost effective service time under the staying policy can be expressed as:
In addition, represents the mean time to serve the PU who arrives within the average extended data delivery time duration. Thus,
where the average extended data delivery time is given by:
Substituting Equations (19) and (20) into Equation (21), we have:
Similarly,
where denotes the mean time to serve the PUs and SUs that are ahead of the considered SU and can be given by [38]:
and denotes the number of PUs those arrive in the average time . Thus, is the mean time to serve the newly arriving PUs. Based on Equations (2) and (22)–(24), the average system sojourn time in the staying policy can be finally given by:
where and can be interpreted as the primary and secondary traffic intensity resulting from primary and secondary connections of channel , respectively. For a stable queuing system, we have . In other words, the utilization factor in each channel must be less than 1.
3.2. Derivation under Changing Policy
In this part, the considered SU will adopt the changing policy as shown in Figure 2 when interruption happens. Firstly, we consider two important system parameters: and . is defined as the arrival rate, at channel , of the secondary connections those has experienced i interruptions and is defined as the transmission duration of a secondary connection between the ith and the (i + 1)th interruption. Thus, referring to [15], we have:
Note that the average waiting time is influenced by the arrival rate of the interrupted secondary connections and their corresponding effective service time duration, except for the arrival rate and service time distribution of the primary and secondary connections at target channel . In addition, for a stable queuing system, we have:
Based on proposition 2, we have . Thus, the average delay caused by the ith interruption can be given by:
Recall the defined random variable , which denotes the number of times that the SU is interrupted until its data transmission is completed. The average total delay can be expressed as:
where denotes the probability that the considered SU has been interrupted times until its data transmission is completed. Thus, we have:
Finally, according to Equation (4), we have:
Thus, the average extended data delivery time based on the changing policy is given by:
Note that selecting different target channel sequences will result in different average extended data delivery times, and an optimal target channel sequence selection can be realized by the dynamic programming algorithm in [35]. Substituting Equation (24) into Equation (5), the average system sojourn time is:
3.3. Traffic-Adaptive Policy
Generally, the considered SU prefers adopting the spectrum handoff policy that can reduce the average extended data delivery time. That is:
In other words, if , the SU will adopt the changing policy. If , the SU will adopt the staying policy. This process is called the traffic-adaptive policy. Similarly, for the average system sojourn time, we have:
For both spectrum handoff polices, the initial channel is pre-assigned. Thus, the minimum average extended data delivery time will result in the minimum average system sojourn time.
4. Numerical Results and Discussion
In this paper, the MATLAB simulation platform is used. In order to validate the proposed analytical network model, we consider a three-channel (i.e., ) continuous-time cognitive radio system, where a waiting connection (primary or secondary connection) is put into service as soon as the server becomes available. In other words, the average extended data delivery and system sojourn time are non-integer time slots in the continuous-time system. Furthermore, assume that these three channels are identical and the primary and secondary connections have the same traffic parameters, i.e., , , and . Because our analytical framework is established on the PRI M/G/1 queuing network model, the arrival rates of the primary and secondary connections are Poisson arrival rates for the high-priority and low-priority connections, respectively. The primary connection service time follows the general distribution. In addition, suppose that the secondary connection service time follows the exponential distribution. According to this assumption, we have . Hence, the average service time for the secondary connection is . We also have , which is given by:
4.1. Effects of Channel Busy Probability and Average Service Time on
Figure 3 shows the effects of channel busy probability and the average service time of secondary connection on the probability when the average service time of primary connections is given. Firstly, we find that the obtained results in Figure 3 match the derivation results. With the increase of channel busy probability , the probability that the secondary connection enters the target channel for service and completes its data transmission without being interrupted decreases. For example, given that (slots/arrival), when , . However, when , the probability dramatically decreases to 0.56. That is because higher channel busy probability will result in larger arrival rates of newly arriving primary connections. Hence, the probability that the secondary connection is interrupted by the newly arriving primary connections becomes larger. In addition, for given channel busy probability, with the increase of average service time of secondary connections, also decreases. That is because longer average service time raises the risk that the secondary connection is interrupted by the newly arriving primary connections. For instance, given that , decreases from 0.83 to 0.71 when the average service time of secondary connections changes from 10 (slots/arrival) to 20 (slots/arrival). Thus, the behaviors of the SU depend on the average service time of the SU and the channel busy probability resulting from the primary connections.
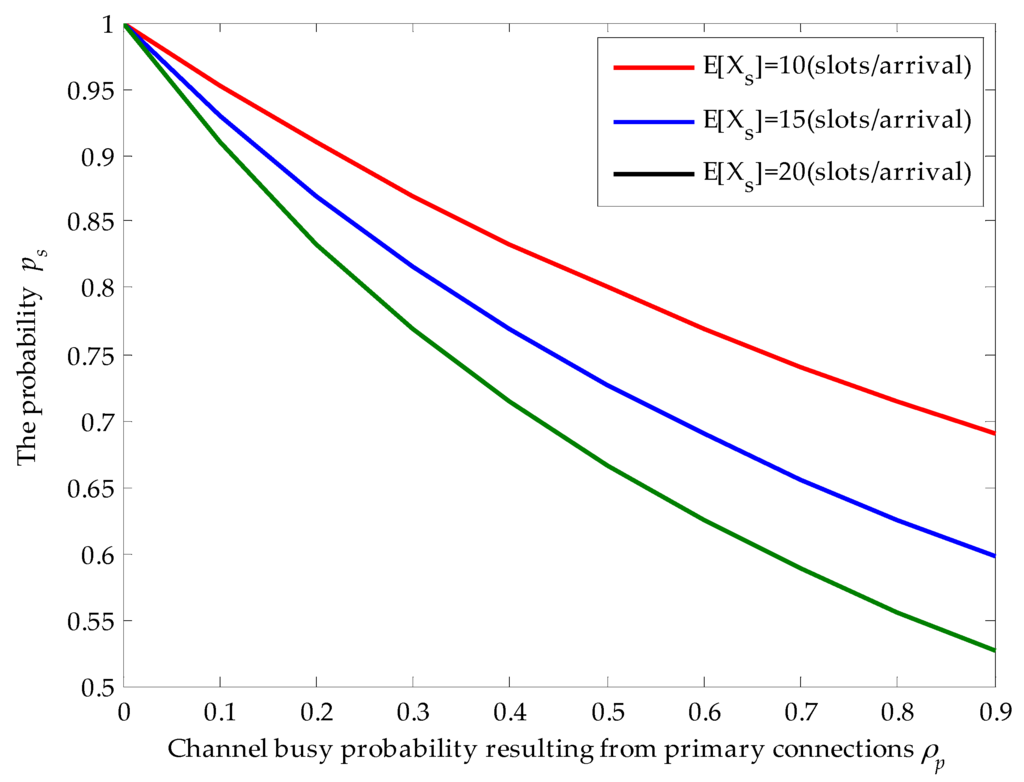
Figure 3.
Effects of the channel busy probability resulting from primary connections and the average service time of secondary connections on the probability , where (slots/arrival), (arrivals/slot), (arrivals/slot) and .
4.2. Effects of Various Service Time Distributions for Primary Connections
Since the initial channel is pre-assigned by methods in [29,37], the waiting time duration from the instant when the SU enters the low-priority queue to the instant when the SU transmits its data for the first time is determined. Thus, we focus on discussing the effects of various service time distributions for primary connections on the average extended data delivery time. Referring to [39], we consider two kinds of service time distributions for primary connections: the exponential distribution and the upper-truncated Pareto distribution, matching the actual voice and data traffic measurements quite well, respectively. According to [40], the formula for the gth moment of the upper-truncated Pareto distribution is given by:
where is the shape parameter; and and denotes the scale parameter and the truncated upper bound, respectively. We set the shape parameter , the scale parameter , and the truncated upper bound bytes. Thus, the average connection length of the primary connection is calculated to be 20 (slots/arrival), i.e., (slots/arrival) when the slot duration is considered to be 10 millisecond as adopted in the IEEE 802.22 standard and the data rate is set to be 19.2 kbps. In addition, the formula for the gth moment of the exponential distribution is expressed as:
For fair comparison, the average connection length of the primary connection for the exponential distribution is also assumed to be 20 (slots/arrival), i.e., (slots/arrival). Furthermore, we suppose that (arrivals/slot), and (slots /arrival). Note that for a stable queuing system, we have .
Figure 4 compares the effects of the upper-truncated Pareto distribution and the exponential distribution for primary connections in the PRI M/G/1 and the PRP M/G/1 analytical frameworks when the staying policy is adopted. Firstly, we can see that the extended data delivery times in both analytical frameworks are the same. Because the extended data delivery time in the staying policy in Equation (22) is determined by the average service time of primary connections and the average service times are the same for the upper-truncated Pareto distribution and the exponential distribution, i.e., . Secondly, in the PRI M/G/1 analytical framework, the extended data delivery time is longer than that in the PRP M/G/1 analytical framework for the reason that the SU has to repeat its data transmission when an interruption happens in the PRI M/G/1 queuing network model. In other words, in the PRI M/G/1 queuing network model, the effective service time is lost in the repeat scheduling discipline. Moreover, with the increase of the channel busy probability, the difference value of the average service time in these two analytical frameworks becomes larger for the reason that a larger channel busy probability will result in more interruptions. For example, when , the difference value equals to 1.25 slots. When , the difference value equals to 7.5 slots.
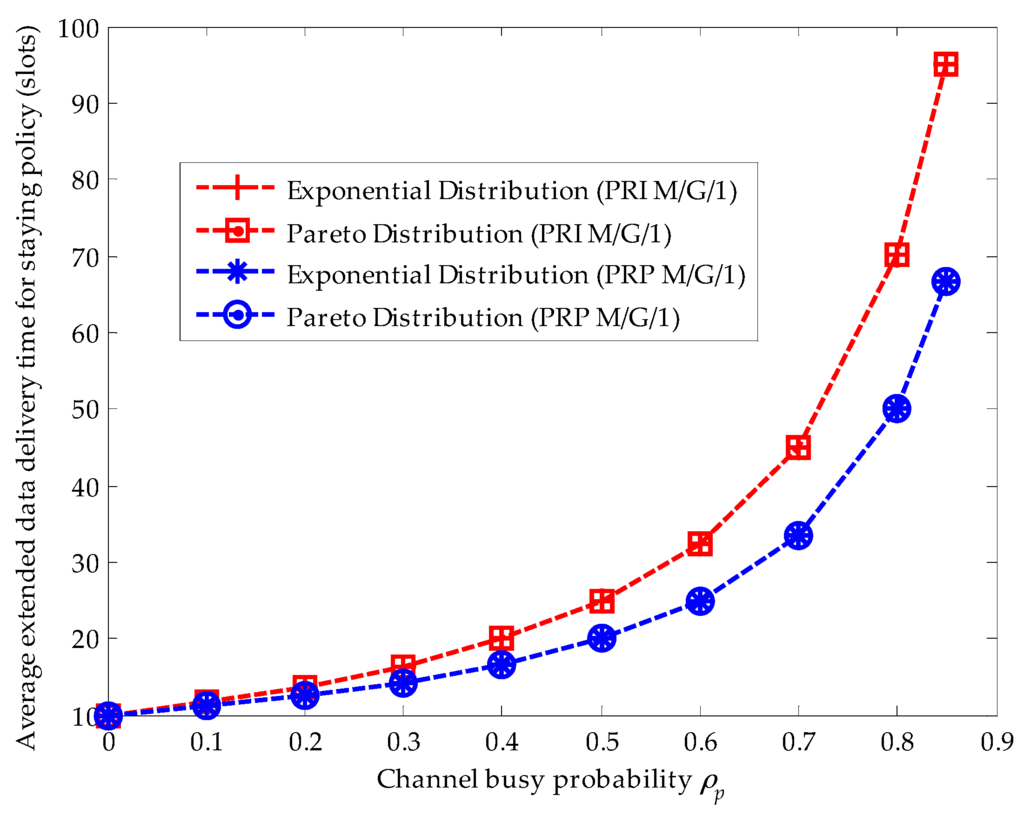
Figure 4.
Effects of the upper-truncated Pareto distribution and the exponential distribution for primary connections when the staying policy is adopted in the preemptive repeat identical (PRI) M/G/1 and the preemptive resume priority (PRP) M/G/1 queuing network models.
Figure 5 compares the effects of the upper-truncated Pareto distribution and the exponential distribution for primary connections in the PRI M/G/1 and the PRP M/G/1 analytical frameworks when the changing policy is adopted. In both analytical frameworks, the upper-truncated Pareto distribution for primary connections results in a larger extended data delivery time than the exponential distribution for primary connections. This is because the second moment of the upper-truncated Pareto distribution is larger than that of the exponential distribution . Furthermore, in the changing policy, the delay in a secondary connection caused by the repeat scheduling discipline can be omitted for the reason that the second moment of the upper-truncated Pareto distribution and exponential distribution results in a huge delay.
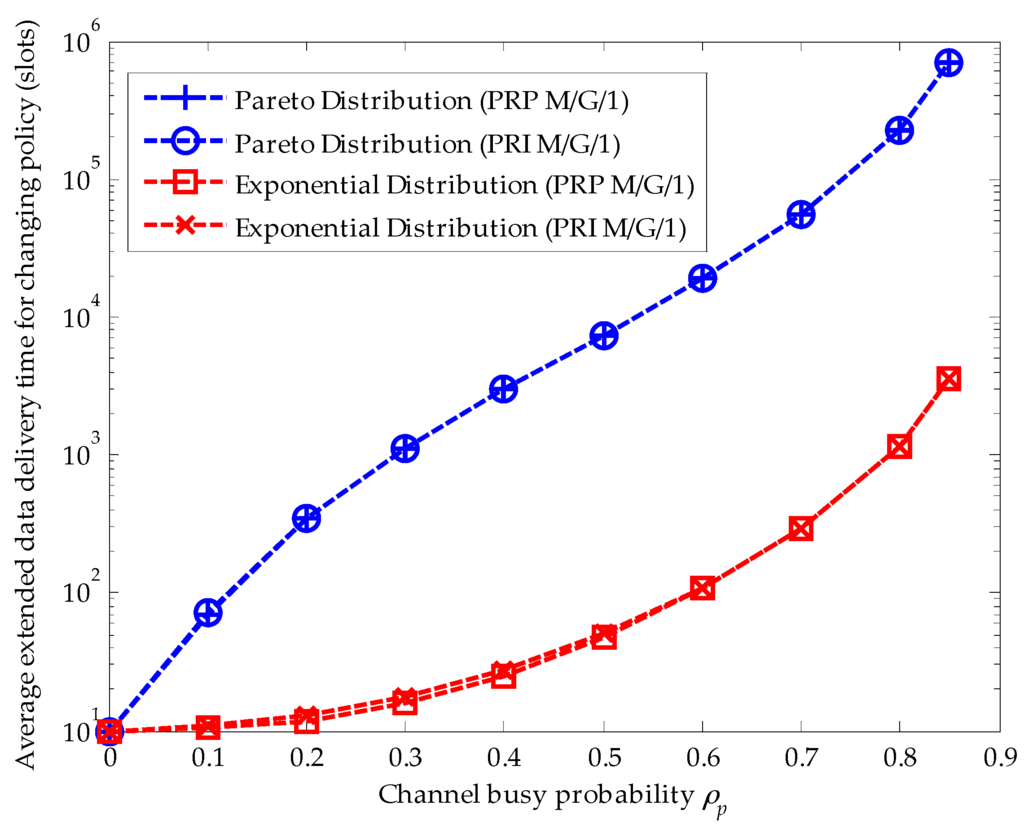
Figure 5.
Effects of the upper-truncated Pareto distribution and the exponential distribution for primary connections when the changing policy is adopted in the preemptive repeat identical (PRI) M/G/1 and the preemptive resume priority (PRP) M/G/1 queuing network models, where (arrivals/slot), (slots/arrival), and (slot).
In addition, we also need to discuss two service time distributions for secondary connections: the upper-truncated Pareto distribution and the exponential distribution. However, from the derivation results, we can see that the extended data delivery time is determined by the averge service time, not related to the gth (g ≥ 2) moment of the service time distribution. Therefore, when the service time distribution of the secondary connection follows the upper-truncated Pareto distribution with , we will obtain the same results as Figure 4 and Figure 5. Thus, for simpicity, we omit discussion about the upper-truncated Pareto distribution for secondary connections.
4.3. Traffic-Adaptive Policy for the Secondary Connection
Comparing Figure 4 with Figure 5, we clearly know that when the service time distribution of the primary connection follows the upper-truncated Pareto distribution, the average extended data delivery time of the secondary connection in the changing policy becomes so large that there is no cross point between the average extended data delivery time curve for the staying policy and that for the changing policy. That is, when the service time distribution of the primary connection follows the upper-truncated Pareto distribution, there is no traffic-adaptive policy for the secondary connection. However, as the service time distribution of the primary connection follows the exponential distribution, the cross point between the staying policy and the changing policy exits, as shown in Figure 6.
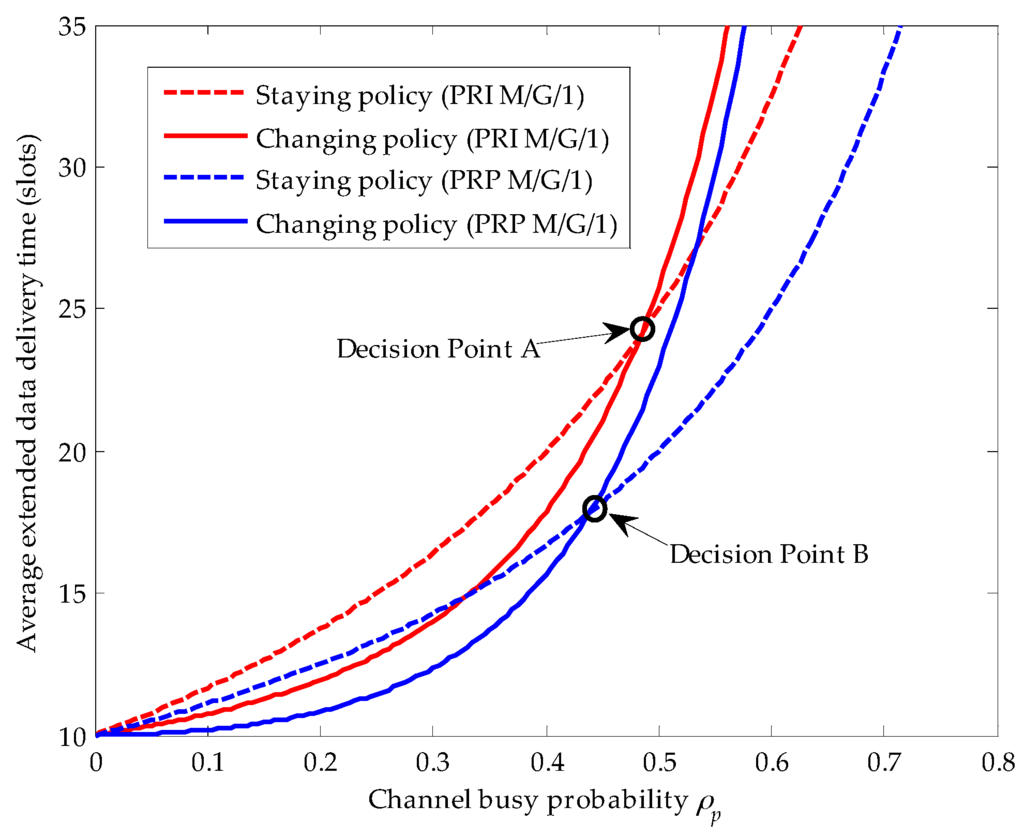
Figure 6.
Compares the traffic-adaptive policy of the considered secondary user (SU) in the preemptive repeat identical (PRI) M/G/1 and the preemptive resume priority (PRP) M/G/1 queuing network models, where the primary connection follows the exponential distribution, (arrivals/slot), (slots/arrival), , (slot) and .
In this figure, we define the cross point as the decision point, and let A and B denote the decision point in the PRI M/G/1 and the PRP M/G/1 queuing networks, respectively. In other words, if the channel busy probability resulting from the arrival of the primary connection lies on the left side of decision point A (i.e., ), the secondary connection will execute the changing policy for shorter average extended data delivery time in the PRI M/G/1 queuing network. On the contrary, if , the secondary connection will adaptively choose the staying policy. Similarly, in the PRP M/G/1 queuing network, when lies on the left side of decision point B (i.e., ), the secondary connection will adopt the changing policy. On the contrary, when lies on the right side of decision point B (i.e., ), the secondary connection will adaptively adopt the staying policy. In addition, the decision point A lies on the right side of the decision point B for the reason that the repeat scheduling discipline results in larger delay in the PRI M/G/1 queuing network than the resume scheduling discipline does in the PRP M/G/1 queuing network.
Figure 7 shows the effects of the secondary connection average service time on the average extended data delivery time and the position of the decision point in the PRI M/G/1 queuing network. Firstly, we can obviously see that with the increase of the secondary connection average service time, the average extended data delivery time becomes larger in both the staying and the changing policy. Because, the longer secondary connection average service time raises the risk that the ongoing secondary connection is interrupted by the newly arriving primary connections. Secondly, when the secondary connection average service time becomes larger, the corresponding decision point moves slightly towards left. For example, for (slots), the horizontal coordinate of the corresponding decision point is 0.495, whereas for (slots), the horizontal coordinate of the corresponding decision point moves to 0.475.
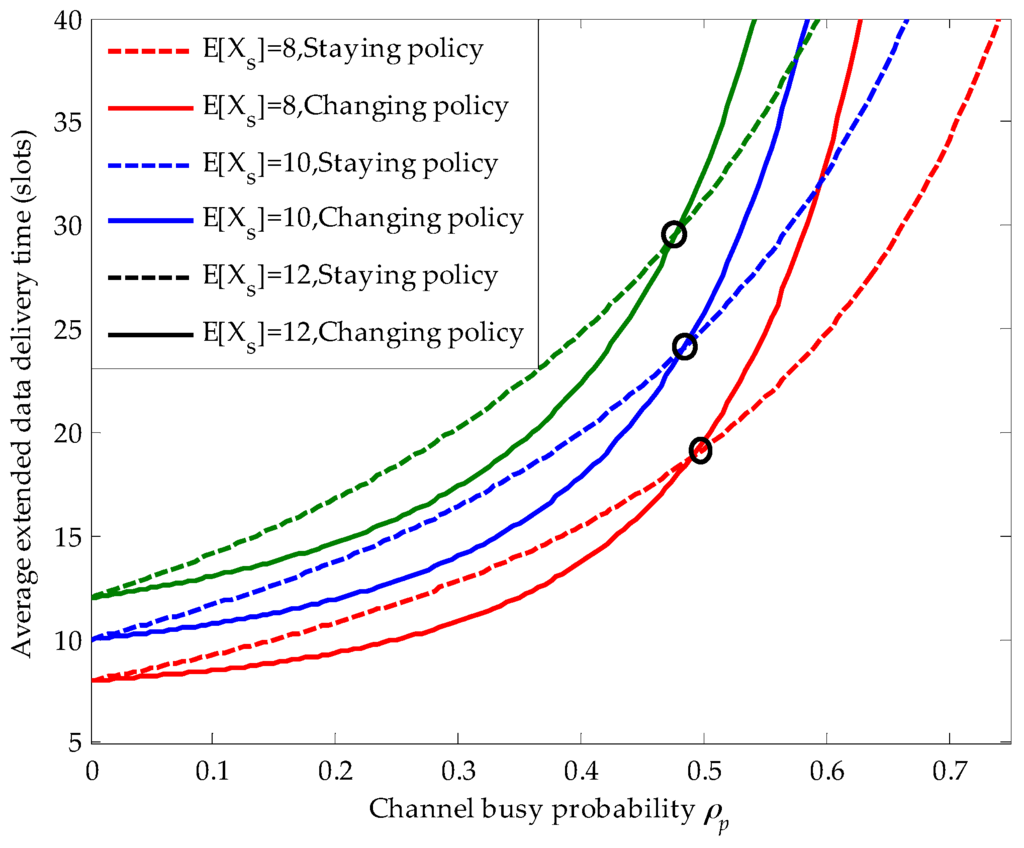
Figure 7.
The effects of the secondary connection average service time on the average extended data delivery time in the preemptive repeat identical (PRI) M/G/1 queuing network, where the primary connection follows the exponential distribution, (arrivals/slot), (arrivals /slot), , (slot), (slots /arrival) and .
4.4. Admission Control Rule
By using the derived results in Section 3, we can design the admission control rule for the SU subject to its maximum cumulative delay requirement. The cumulative delay is referred to as the difference between the average extended data delivery time and the average service time of the secondary connection. Let s (slots) denote the maximum allowable delay for the SU. When the service time distribution of the primary connection follows the upper-truncated Pareto distribution, the optimal policy for the SU is to execute the staying policy based on above-mentioned analysis results. For a stable queuing system, we have:
Figure 8 shows the admissible region of a CR network when the service time of the primary connection follows the upper-truncated Pareto distribution and the admission control policy can be designed based on these results. From Figure 8a, we can find that when , the CR can accept all secondary connection requests as long as they satisfy the queue stable condition, i.e., . In the case that , the CR network will reject any secondary connection request, because the delay is only related to channel busy probability for given (slots) and (slots) and exceeds the maximum allowable delay according to Equation (39). In addition, by comparing Figure 8a,b, we can obviously see that the horizontal coordinate of the admissible region extends from 0.2 to 0.345. That is because the maximum allowable delay is set to be eight slots, which is two times as large as before. Therefore, the secondary connection request can be accepted as long as the channel busy probability is no larger than 0.345.
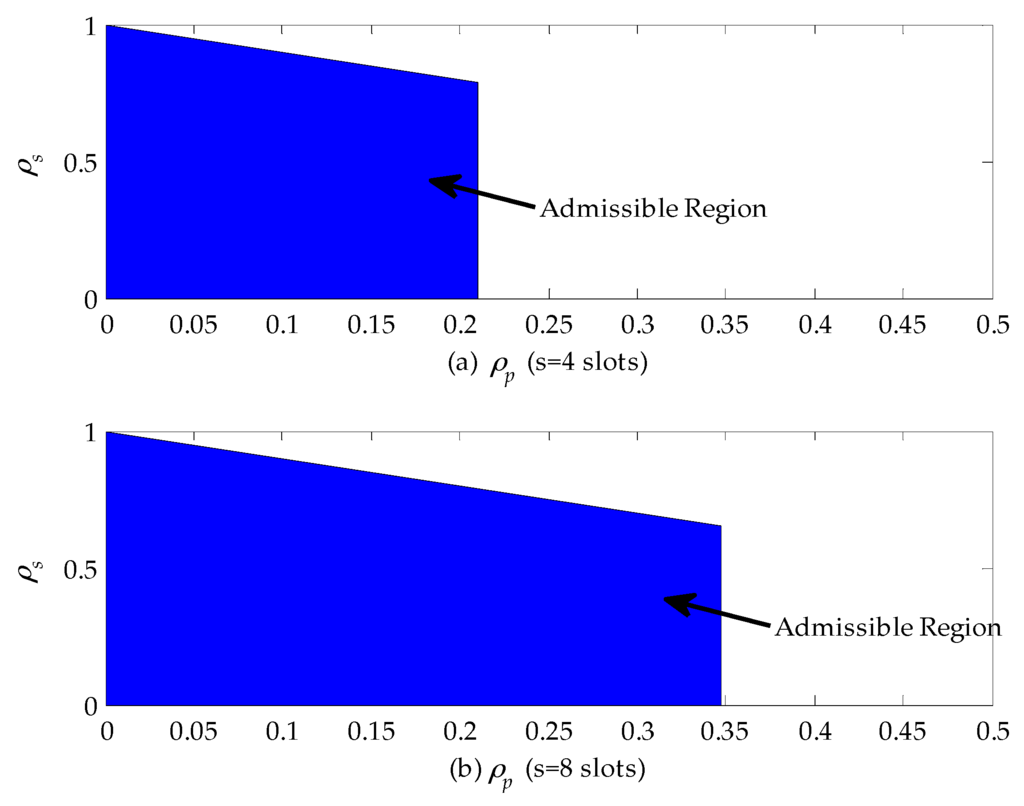
Figure 8.
The admissible region of a cognitive radio (CR) network when the service time of the primary connection follows the upper-truncated Pareto distribution: (a) the maximum allowable delay is set to be four slots; and (b) the maximum allowable delay is set to be eight slots.
When the service time distribution of the primary connection follows the exponential distribution, the optimal policy for the SU is to adopt the traffic-adaptive policy. Thus, for a stable queuing system, we have:
Figure 9 shows the admissible region of a CR network when the service time of the primary connection follows the exponential distribution. From Figure 9a, we can find that if , the CR network can accept all secondary connection requests as long as they satisfy the queuing stable condition, i.e., . If , the secondary connection requests can be accepted only when . Otherwise, they will be rejected to guarantee the maximum allowable delay of SUs. In addition, if , no secondary connection can be built. That is because the delay of SUs exceeds the maximum allowable delay. Furthermore, comparing Figure 9a,b, we can find that a longer maximum allowable delay extends the admissible region. For instance, the horizontal coordinate of the admissible region extends from 0.32 to 0.43. When , no SU is allowed to access to the CR network.
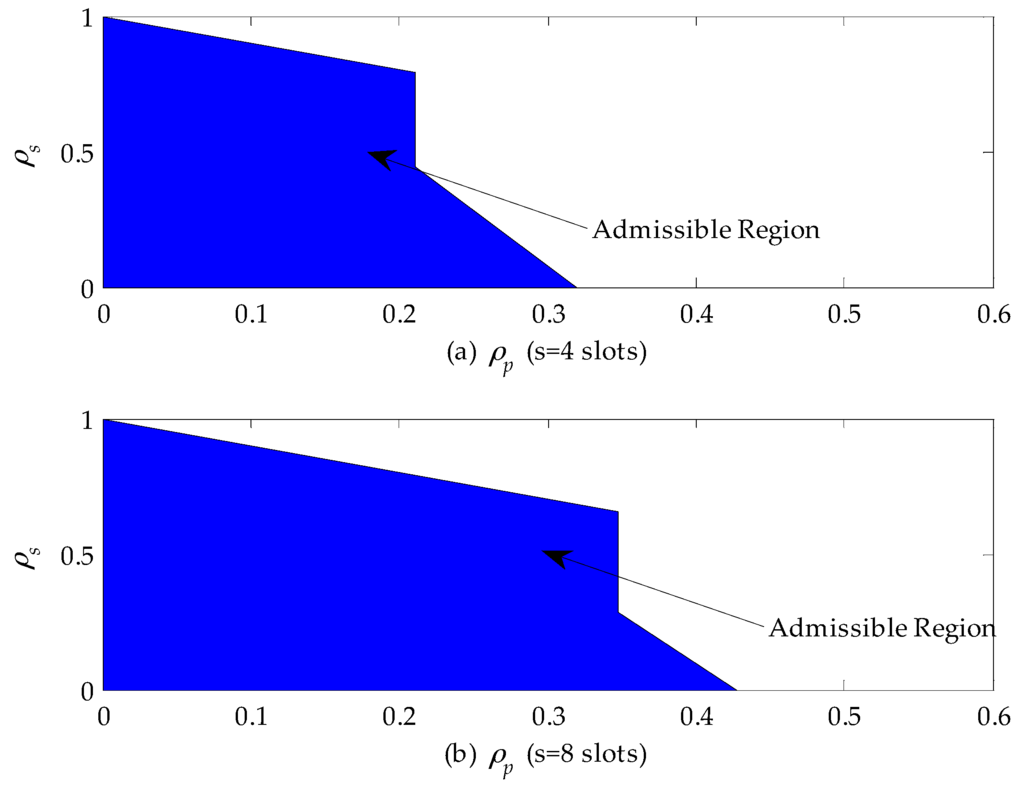
Figure 9.
The admissible region of a cognitive radio (CR) network when the service time of the primary connection follows the exponential distribution: (a) the maximum allowable delay is set to be four slots; and (b) the maximum allowable delay is set to be eight slots.
5. Conclusions
In this paper, an analytical framework model is proposed to describe spectrum handoff behaviors of the SU based on the PRI M/G/1 queuing network. Then, we introduce the staying and the changing scenarios and derive the close-expression of extended data delivery and sojourn time in both scenarios. Based on the derivation results, we propose the traffic-adaptive policy. That is, when the service time distribution of the primary connection follows the upper-truncated Pareto distribution, the best policy for the SU is to execute the staying policy. When the service time distribution of the primary connection follows the exponential distribution, the best policy for the SU is to choose a policy according to the channel probability . In the case that , the SU will choose to execute the changing policy. Otherwise, the staying policy will be the better policy for the SU. In addition, when the service time distribution of the secondary connection follows different distributions (i.e., the upper-truncated Pareto distribution and the exponential distribution), the simulation results are the same, because the average service times of these two distributions are set to be identical for fair comparison. Finally, we investigate the admissible region for a CR network and provide a reference for the arriving SU. Although the repeat scheduling discipline will result in larger delay in the PRI M/G/1 queuing network than the resume scheduling discipline does in the PRP M/G/1 queuing network, the repeat scheduling discipline is usually applied in some special scenarios. Thus, our work makes the research on spectrum handoff behaviors much more complete in CR network. Moreover, our work can provide the reference for executing the optimal spectrum handoff strategy and designing the admission control rule for the SU in the PRI M/G/1 queuing network.
Some important issues can also be considered in the future. For example, the energy efficiency problem in the PRI M/G/1 and the PRP M/G/1 queuing network is worth investigating. That is, the interrupted SU should execute the optimal spectrum handoff strategy to maximize the energy efficiency during the whole data transmission process.
Acknowledgments
This paper is supported by National Natural Science Foundation of China (61571162), Science and Technology Project of Ministry of Public Security Foundation (2015GABJC38), and Major National Science and Technology Project (2015ZX03004002-004).
Author Contributions
Xuezhi Tan proposed the model and conceived the rough idea; Xiaolong Yang derived the close-expression of the extended data delivery and the sojourn time in the staying and changing scenarios and wrote the manuscript; and Liang Ye and Lin Ma reviewed the manuscript.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Kaabouch, N.; Hu, W.C. Handbook of Research on Software-Defined and Cognitive Radio Technologies for Dynamic Spectrum Management, 1st ed.; IGI Global: Hershey, PA, USA, 2014; pp. 300–344. [Google Scholar]
- Hossain, E.; Dusit, N.; Dong, I.K. Evolution and future trends of research in cognitive radio: A contemporary survey. Wirel. Commun. Mobile Comput. 2015, 15, 1530–1564. [Google Scholar] [CrossRef]
- Salahdine, F.; Kaabouch, N.; Ghazi, H.E. A survey on compressive sensing techniques for cognitive radio networks. Phys. Commun. 2016, 20, 61–73. [Google Scholar] [CrossRef]
- Althunibat, S.; Renzo, M.D.; Granelli, F. Towards energy-efficient cooperative spectrum sensing for cognitive radio networks: An overview. Telecommun. Syst. 2015, 59, 77–91. [Google Scholar] [CrossRef]
- Usman, M.; Khan, M.S.; Vu-Van, H.; Insoo, K. Energy-Efficient Channel Handoff for Sensor Network-Assisted Cognitive Radio Network. Sensors 2015, 15, 18012–18039. [Google Scholar] [CrossRef] [PubMed]
- Christian, I.; Moh, S.; Ilyong, C.; Lee, J.Y. Spectrum mobility in cognitive radio networks. IEEE Commun. Mag. 2012, 50, 114–121. [Google Scholar] [CrossRef]
- Sun, N.; Wu, J.X. Maximizing spectral efficiency for high mobility systems with imperfect channel state information. IEEE Trans. Wirel. Commun. 2014, 13, 1462–1470. [Google Scholar] [CrossRef]
- Zubair, S.; Yusoff, S.K.S.; Fisal, N. Mobility-enhanced reliable geographical forwarding in cognitive radio sensor networks. Sensors 2016, 16, 172–201. [Google Scholar] [CrossRef] [PubMed]
- Tayel, A.F.; Rabia, S.I. Load balancing probabilistic spectrum handoff for cognitive radio networks. In Proceedings of the 2015 International Symposium on Performance Evaluation of Computer and Telecommunication Systems (SPECTS), Chicago, IL, USA, 26–29 July 2015; pp. 1–8.
- Southwell, R.; Huang, J.; Liu, X. Spectrum mobility games. In Proceedings of the IEEE International Conference on Computer Communications (INFOCOM), Orlando, FL, USA, 25–30 March 2012; pp. 37–45.
- Wang, C.W.; Wang, L.C.; Adachi, F. Modeling and analysis for reactive-decision spectrum handoff in cognitive radio networks. In Proceedings of the IEEE International Conference on Communications (GLOBECOM), Miami, FL, USA, 14–18 June 2010; pp. 1–6.
- Wang, C.W.; Wang, L.C. Analysis of reactive spectrum handoff in cognitive radio networks. IEEE J. Sel. Areas Commun. 2012, 30, 2016–2028. [Google Scholar] [CrossRef]
- Chakraborty, T.; Misra, I.S. Designing a real-time spectrum handoff algorithm for VoIP based Cognitive Radio Networks. In Proceedings of the Radio and Antenna Days of the Indian Ocean (RADIO), Belle Mare, Mauritius, 21–24 September 2015; pp. 1–2.
- Zheng, S.; Yang, X.; Chen, S.; Lou, C. Target channel sequence selection scheme for proactive-decision spectrum handoff. IEEE Commun. Lett. 2011, 15, 1332–1334. [Google Scholar] [CrossRef]
- Wang, L.C.; Wang, C.W.; Chang, C.J. Modeling and analysis for spectrum handoffs in cognitive radio networks. IEEE Trans. Mobile Comput. 2012, 11, 1499–1513. [Google Scholar] [CrossRef]
- Ashour, M.; El-Sherif, A.A.; ElBatt, T.; Mohamed, A. Cooperative access in cognitive radio networks: Stable throughput and delay tradeoffs. In Proceedings of the 12th International Symposium on Modeling and Optimization in Mobile, Ad Hoc, and Wireless Networks (WiOpt), Hammamet, Tunisia, 12–16 May 2014; pp. 263–270.
- Shafie, A.E.; Sultan, A.; Khattab, T. Probabilistic band-splitting for a buffered cooperative cognitive terminal. In Proceedings of the IEEE 25th Annual International Symposium on Personal, Indoor, and Mobile Radio Communication (PIMRC), Washington, DC, USA, 2–5 September 2014; pp. 1030–1035.
- Das, D.; Abouzeid, A.A. Cooperative caching in dynamic shared spectrum networks. IEEE Trans. Wirel. Commun. 2016, 15, 5060–5075. [Google Scholar] [CrossRef]
- Das, D.; Abouzeid, A.A. Cooperative caching for shared spectrum networks. In Proceedings of the IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 5740–5746.
- Kompella, S.; Nguyen, G.D.; Kam, C.; Wieselthier, J.E.; Ephremides, A. Cooperation in cognitive underlay networks: Stable throughput tradeoffs. IEEE/ACM Trans. Netw. 2014, 22, 1756–1768. [Google Scholar] [CrossRef]
- Darabi, M.; Maham, B.; Saad, W.; Mehbodniya, A.; Adachi, F. Context aware medium access control for buffer-aided multichannel cognitive networks. In Proceedings of the IEEE International Conference on Communications Workshops (GC Wkshps), San Diego, CA, USA, 6–10 December 2015; pp. 1–6.
- Das, D.; Abouzeid, A.A. Spatial–temporal queuing theoretic modeling of opportunistic multi-hop wireless networks with and without Cooperation. IEEE Trans. Wirel. Commun. 2015, 14, 5209–5224. [Google Scholar] [CrossRef]
- Li, H. Queuing analysis of dynamic spectrum access subject to interruptions from primary users. In Proceedings of the Fifth International Conference on Cognitive Radio Oriented Wireless Networks and Communications (CrownCom), Cannes, France, 9–11 June 2010; pp. 1–5.
- Wang, L.C.; Wang, C.W.; Chang, C.J. Optimal target channel sequence design for multiple spectrum handoffs in cognitive radio networks. IEEE Trans. Commun. 2012, 60, 2444–2455. [Google Scholar] [CrossRef]
- Wang, K.; Liu, Q.; Lau, F.C.M. Multichannel opportunistic access by overhearing primary ARQ messages. IEEE Trans. Veh. Technol. 2013, 62, 3486–3492. [Google Scholar] [CrossRef]
- Zhang, Y.; Jiang, T.; Zhang, L.; Qu, D.M.; Peng, W. Analysis on the transmission delay of priority-based secondary users in cognitive radio networks. In Proceedings of the International Conference on Wireless Communications & Signal Processing (WCSP), Hangzhou, China, 24–26 October 2013; pp. 1–6.
- Do, C.T.; Tran, N.H.; Han, Z.; Le, L.B.; Lee, S.; Hong, C.S. Optimal pricing for duopoly in cognitive radio networks: Cooperate or not cooperate. IEEE Trans. Wirel. Commun. 2014, 13, 2574–2587. [Google Scholar]
- Tadayon, N.; Aissa, S. Modeling and analysis framework for multi-interface multi-channel cognitive radio networks. IEEE Trans. Wirel. Commun. 2015, 14, 935–947. [Google Scholar] [CrossRef]
- Sheikholeslami, F.; Nasiri-Kenari, M.; Ashtiani, F. Optimal probabilistic initial and target channel selection for spectrum handoff in cognitive radio networks. IEEE Trans. Wirel. Commun. 2015, 14, 570–584. [Google Scholar] [CrossRef]
- Walraevens, J.; Fiems, D.; Bruneel, H. The discrete-time preemptive repeat identical priority queue. Queueing Syst. 2006, 53, 231–243. [Google Scholar] [CrossRef]
- Chen, J.; Wang, J.P.; Yu, H.; Zheng, S.Q. Opportunistic optical hyper-channel and its distributed QoS assuring access control. IEEE Trans. Parallel Distrib. Syst. 2009, 20, 1626–1640. [Google Scholar] [CrossRef]
- Jin, X.; Min, G. Modelling and analysis of an integrated scheduling scheme with heterogeneous LRD and SRD traffic. IEEE Trans. Wirel. Commun. 2013, 12, 2598–2607. [Google Scholar] [CrossRef]
- Yang, S.; Stol, N. Multiple input single output optical buffers for asynchronous optical packet switched networks. In Proceedings of the IEEE Global Communications Conference (GLOBECOM), Austin, TX, USA, 8–12 December 2014; pp. 2054–2059.
- Baziana, P.A.; Pountourakis, I.E. An asynchronous WDMA protocol without collisions for ring MANs: Study for internet traffic packet size variation. In Proceedings of the 18th European Conference on Network and Optical Communications (NOC), Graz, Austria, 10–12 July 2013; pp. 137–144.
- Nada, F.A. A case study of multi-server ATM buffers routing multimedia traffics with geometric service time. In Proceedings of the Second International Conference on Computer and Electrical Engineering (ICCEE), Dubai, UAE, 28–30 December 2009; pp. 551–555.
- Popescu, V.; Fadda, M.; Murroni, M. Performance analysis of IEEE 802.22 wireless regional area network in the presence of digital video broadcasting-second generation terrestrial broadcasting services. IET Commun. 2016, 10, 922–928. [Google Scholar]
- Wang, L.C.; Wang, C.W.; Adachi, F. Load-Balancing spectrum decision for cognitive radio networks. IEEE J. Sel. Areas Commun. 2011, 29, 757–769. [Google Scholar] [CrossRef]
- Ibe, O.C. Markov Process for Stochastic Modeling, 2nd ed.; Elsevier: Lowell, MA, USA, 2013; pp. 189–193. [Google Scholar]
- Ng, C.H.; Soong, B.H. Queuing Modelling Fundamentals with Applications in Communication Networks, 2nd ed.; John Wiley & Sons, Inc.: New York, NY, USA, 2008; pp. 135–140. [Google Scholar]
- ETSI. Universal Mobile Telecommunications System (UMTS): Selection Procedures for the Choice of Radio Transmission Technologies of the UMTS; Technical Report UMTS 30.03, Version 3.2.0; ETSI: Sophia Antipolis, France, 1998. [Google Scholar]
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).