Reputation and Reward: Two Sides of the Same Bitcoin
Abstract
:1. Introduction
2. State of the Art
2.1. User Participation
2.2. Data Sensing Quality
Data Quality vs. Incentive Mechanisms
2.3. User Anonymity
2.3.1. Anonymity vs. Incentive Mechanisms
2.3.2. Anonymity vs. Reputation Systems
3. Bitcoins: The Integration Tool
3.1. Bitcoins as a Rewarding Mechanism
3.2. Bitcoins as a Reputation Annotation Mechanism
4. The PaySense System
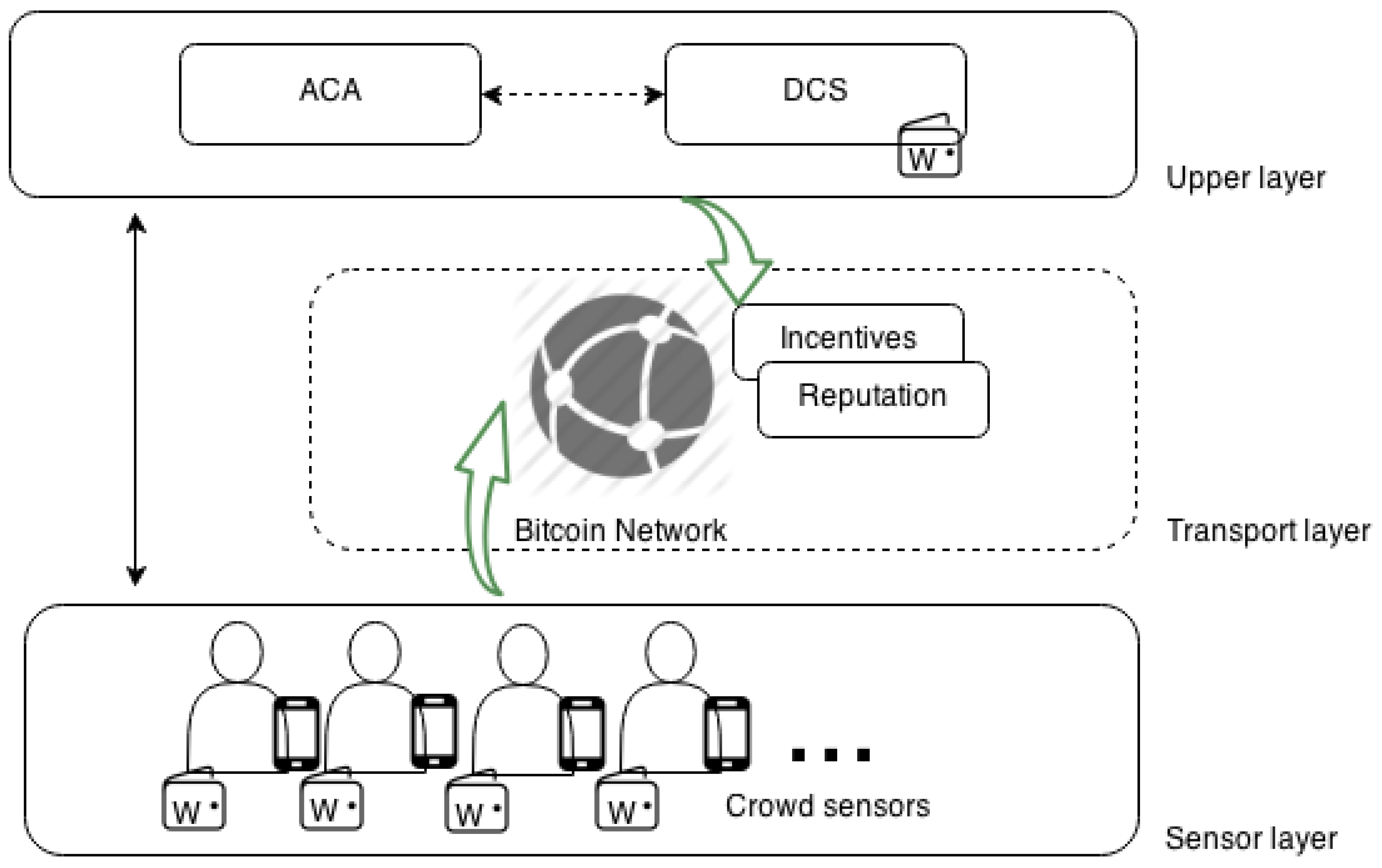
4.1. PaySense Architecture Overview
4.2. PaySense Entities
4.3. PaySense Interaction Model
4.3.1. Crowd Sensor Enrollment
- generates n different Bitcoin addresses () and for each one computes the certificate request, , and obtains its hash value, .
- blinds each of the n hash values obtained in Step 1, for , and sends the n hashed values to the ACA together with ’s real identity. The blinding factor depends on the selected digital signature. Although it has been represented as a function for clarity, the blinding factor is a specific unrelated value for each different to blind.
- The ACA randomly selects one of the received blinded hash values, namely , and requests from both the unblind factor and the for the rest of the values . Then, the ACA extracts the Bitcoin addresses contained in the received and verifies that all of them have a zero balance. Then, the ACA uses the unblinding factors to unblind each for and checks that the unblinded values match with the hash values of the received .
- If all verifications performed by the ACA in Step 3 hold, the ACA signs the blinded value and sends the result to .
- Upon reception, unblinds the digital signature performed by the ACA and uses the unblinded result together with the original value to create the certificate: .
4.3.2. Micropayment Channel Setup
4.3.3. Sensing and Reporting Data
4.3.4. Verification and Validation of Sensed Data
- Decrypts the report using his or her private key:
- Verifies that the data were sent by a registered crowd sensor. For that purpose, the DCS verifies the correctness of .
- Validates the source authenticity of the data by verifying the digital signature included in the report, that is .
- Applies a validation process on the data themselves to assess their quality.
4.3.5. Crowd Sensor Reputation Query
4.3.6. Job Rewarding and Reputation Update
4.3.7. Withdrawal of Rewarded Coins
4.3.8. Transferring Reputation to a New Address
- The ACA should not learn about the CS identity.
- The ACA should not link the old and the new address of a particular CS.
- The CS should not be able to increase his or her reputation.
4.4. Transfer Reputation Protocol
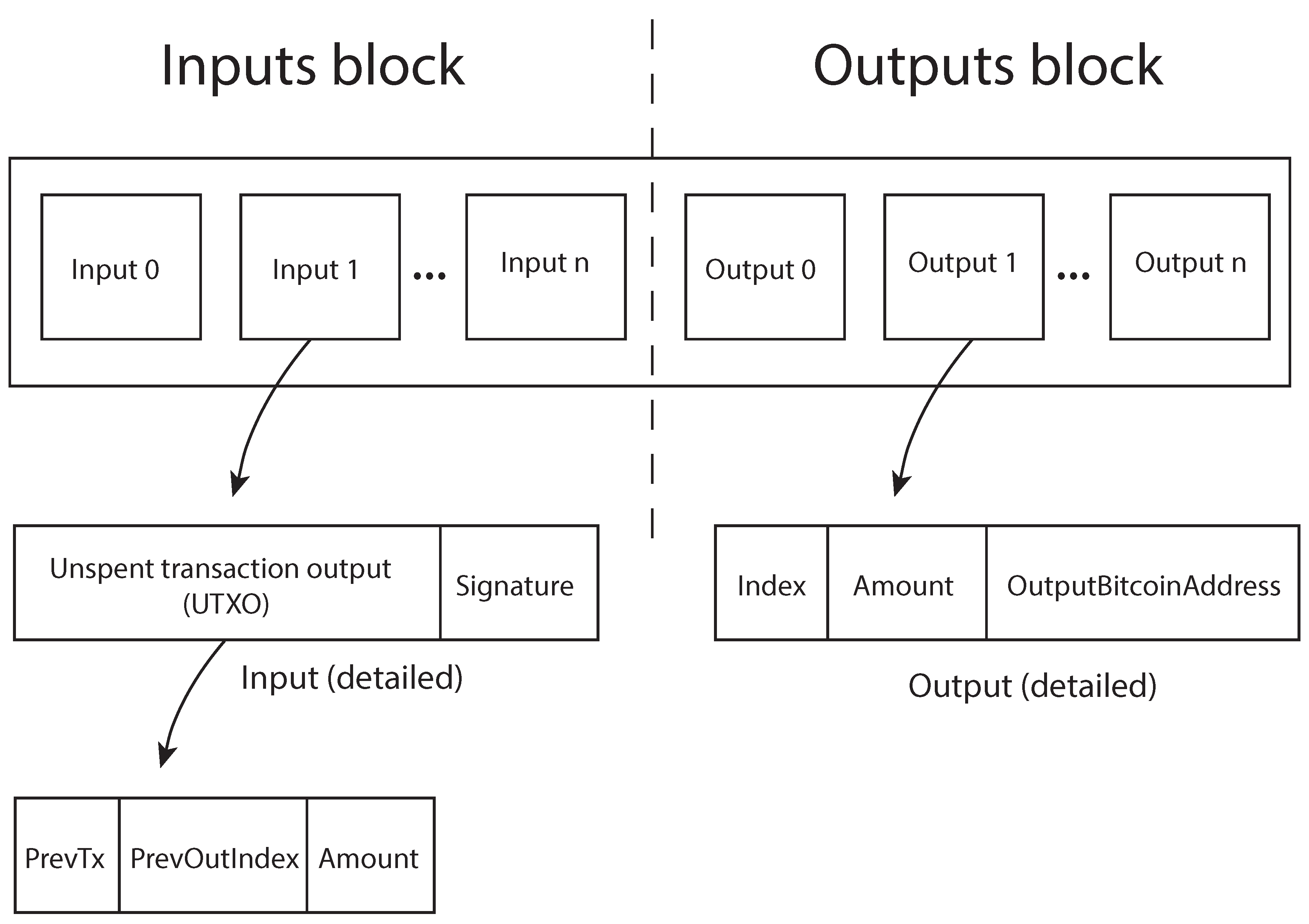
4.4.1. Bitcoin Transaction Structure
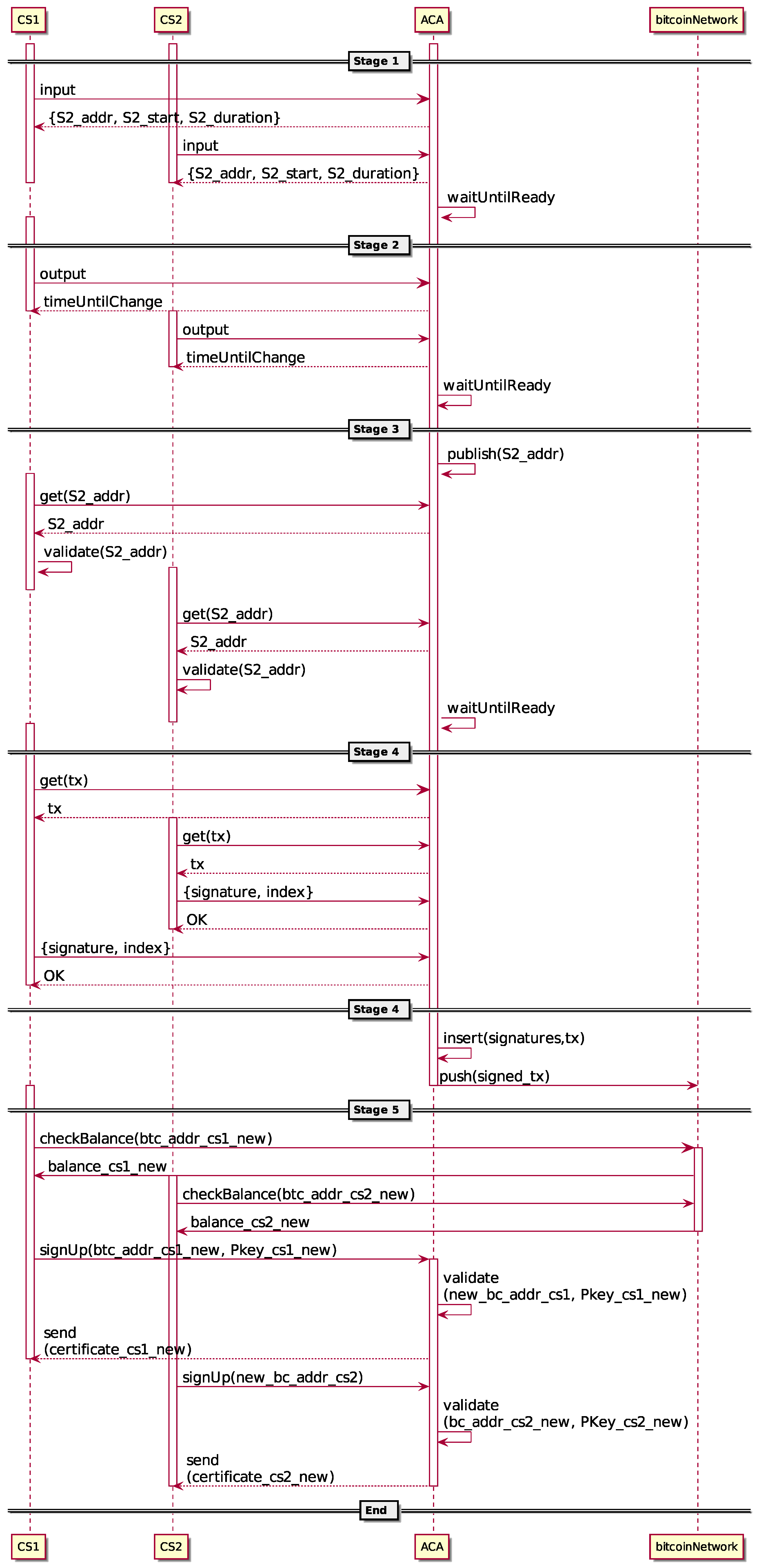
4.4.2. Transfer Reputation Protocol Description
- The ACA advertises a hidden service for transferring a predetermined and fixed reputation value R between certified Bitcoin addresses and new ones.
- The ACA randomly generates, for later use, an output stage hidden service address, duration and starting time.
- Crowd sensors with a certified Bitcoin address with reputation equal to or greater than the fixed R may join the protocol by sending a utxo with the exact value R. Notice that only one input per crowd sensor is allowed.
- In case any CS does not have a single utxo of value R to send to the mixing service, he or she could perform an reputation unifying transaction to create it (described in the next subsection). The new generated utxo will be sent as the input.
- The ACA verifies that each crowd sensor trying to participate in the protocol has at least a reputation score of R, including possible reputation reduction punishment for misbehaving.
- The ACA verifies that each received input comes from a valid source. There are only three valid sources: the DCS, a previously-certified Bitcoin address and the same address itself. Transactions from the DCS are bound to the earned reputation that have been paid by the system to the user. Transactions from a previous certified Bitcoin address are bound to transferred reputation and are limited to just one per address (the very first one actually). Finally, transactions from the same address are bound to a reputation unifying transaction (see the next subsection for details).
- The ACA sends the output stage hidden service address, duration and starting time to each CS whose inputs have been accepted.
- The ACA ends such an input recollection stage after a predefined time discarding any input with a value different from R.
- Crowd sensors that have already sent the input in the previous stage now send the output. Again, only a single output for each crowd sensor is allowed.
- The ACA validates that all of the outputs have an exact value of R.
- The ACA, using the inputs and outputs received in the first and second stages, constructs the base non-signed reputation transfer transaction.
- The ACA ends the output recollection stage after a predefined time.
- The ACA publishes the output stage hidden service address he or she has sent to the participating CS in Stage 1.
- Each CS could now check that the previously-provided output stage hidden service address matches with that openly published.
- The ACA ends the stage after a predefined time.
- Crowd sensors request the base non-signed reputation transfer transaction from the ACA.
- Crowd sensors sign the obtained value and send the result to the ACA.
- The ACA checks the correctness of every provided signature.
- The ACA composes the reputation transfer transaction with the base non-signed transaction that he or she built in the second stage and each of the signatures received from each crow sensor.
- Finally, the ACA pushes the resulting reputation transfer transaction to the Bitcoin P2P network to be included in the blockchain.
- Crowd sensors validate that the reputation transfer transaction has been published in the blockchain and that his or her reputation has effectively been transferred to the new Bitcoin address.
- Crowd sensors send to the ACA the public key corresponding to the Bitcoin address where the reputation has been transferred.
- The ACA verifies that the received public key matches one of the Bitcoin addresses included as output in the reputation transfer transaction and that the address has only one payment related to it. If the validation is correct, he or she sends the new certificate to the crowd sensor.
4.4.3. Reputation Unifying Transaction
4.5. PaySense Integration with Existing MCS Systems
5. Security Analysis
5.1. Adversary Model
- CS identity disclosure aims to discover the identity of a certain user. It could be divided into two degrees depending on the level of disclosure: full disclosure, where the pseudonym is linked with the user’s identity, and pseudonym linkability, where two or more pseudonyms are known to belong to the same user.
- Certificate tampering consists of the inclusion of fake data inside a certificate to get some additional gain during the registration.
- The CS data sensing tampering objective is to generate fake data and to try to pass it off as correct or to modify some data originally created by some user in such a way that it becomes false.
- The Sybil attack provides a single attacker with more than one pseudonym in the system, that is multiple identities.
- The DoS attack consists of interrupting the normal system behavior. Traditionally, general DoS attacks are usually related to low level implementation details or integration specificities. We do not intend to address this kind of attack, but those DoS attacks related to high level protocol dysfunctions.
- A fraudulent reputation increase is a group of attacks where an attacker tampers with the information provided to the system in order to obtain more reputation than the supposed one. Four attacks fit inside this group: fake reward attack, target reputation attack, stale address attack and reputation injection attack.
- Steal rewards consist of changing the reported data in such a way that it looks like the attacker is the original issuer, and therefore, the reward is assigned to him or her.
- Data sensing poisoning aims to send fake information to the DCS in order to spread this information over the network taking some advantage with it.
- A fraudulent reward increase occurs when a certain reward is paid more than once to the same user for the same provided data.
- 5.
- CS data sensing tampering.
- 6.
- Sybil attack.
- 7.
- DoS attack.
5.2. Security Measures
6. Conclusions and Further Research
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Eisenman, S.B.; Miluzzo, E.; Lane, N.D.; Peterson, R.A.; Ahn, G.S.; Campbell, A.T. BikeNet: A Mobile Sensing System for Cyclist Experience Mapping. ACM Trans. Sen. Netw. 2010, 6, 6:1–6:39. [Google Scholar] [CrossRef]
- Dutta, P.; Aoki, P.M.; Kumar, N.; Mainwaring, A.; Myers, C.; Willett, W.; Woodruff, A. Common Sense: Participatory urban sensing using a network of handheld air quality monitors. In Proceedings of the 7th ACM Conference on Embedded Networked Sensor Systems, SenSys ’09, Berkeley, CA, USA, 4–6 November 2009.
- Mohan, P.; Padmanabhan, V.N.; Ramjee, R. Nericell: Rich monitoring of road and traffic conditions using mobile smartphones. In Proceedings of the 6th ACM Conference on Embedded Network Sensor Systems, SenSys ’08, Raleigh, NC, USA, 5–7 November 2008.
- Xu, C.; Li, S.; Zhang, Y.; Miluzzo, E.; Chen, Y.F. Crowdsensing the speaker count in the wild: Implications and applications. IEEE Commun. Mag. 2014, 52, 92–99. [Google Scholar] [CrossRef]
- Rosen, S.; j. Lee, S.; Lee, J.; Congdon, P.; Mao, Z.M.; Burden, K. MCNet: Crowdsourcing wireless performance measurements through the eyes of mobile devices. IEEE Communications Magazine 2014, 52, 86–91. [Google Scholar] [CrossRef]
- Sergi Delgado-Segura. PaySense Python Implementation. Available online: https://github.com/sr-gi/paysense (accessed on 24 May 2016).
- Lane, N.D.; Eisenman, S.B.; Musolesi, M.; Miluzzo, E.; Campbell, A.T. Urban Sensing Systems: Opportunistic or Participatory? In Proceedings of the 9th Workshop on Mobile Computing Systems and Applications, HotMobile ’08, Napa, CA, USA, 25–26 February 2008.
- Yang, D.; Xue, G.; Fang, X.; Tang, J. Crowdsourcing to Smartphones: Incentive Mechanism Design for Mobile Phone Sensing. In Proceedings of the 18th Annual International Conference on Mobile Computing and Networking, Mobicom ’12, Istanbul, Turkey, 22–26 Auguest 2012.
- Zhong, S.; Li, L.E.; Liu, Y.G.; Yang, Y.R. On designing incentive-compatible routing and forwarding protocols in wireless ad-hoc networks. Wirel. Netw. 2006, 13, 799–816. [Google Scholar] [CrossRef]
- Jaimes, L.G.; Vergara-Laurens, I.J.; Raij, A. A Survey of Incentive Techniques for Mobile Crowd Sensing. IEEE Internet Things J. 2015, 2, 370–380. [Google Scholar] [CrossRef]
- Gao, H.; Liu, C.H.; Wang, W.; Zhao, J.; Song, Z.; Su, X.; Crowcroft, J.; Leung, K.K. A Survey of Incentive Mechanisms for Participatory Sensing. IEEE Commun. Surv. Tutor. 2015, 17, 918–943. [Google Scholar] [CrossRef]
- Koutsopoulos, I. Optimal incentive-driven design of participatory sensing systems. In Proceedings of the 2013 IEEE INFOCOM, Turin, Italy, 14–19 April 2013; pp. 1402–1410.
- Brereton, M.; Roe, P.; Foth, M.; Bunker, J.M.; Buys, L. Designing Participation in Agile Ridesharing with Mobile Social Software. In Proceedings of the 21st Annual Conference of the Australian Computer-Human Interaction Special Interest Group: Design, Melbourne, Australia, 23–27 November 2009; pp. 257–260.
- Bellavista, P.; Corradi, A.; Foschini, L.; Ianniello, R. Scalable and Cost-Effective Assignment of Mobile Crowdsensing Tasks Based on Profiling Trends and Prediction: The ParticipAct Living Lab Experience. Sensors 2015, 15, 18613–18640. [Google Scholar] [CrossRef] [PubMed]
- Marczewski, A. Chapter User Types. In Even Ninja Monkeys Like to Play: Gamification, Game Thinking and Motivational Design; CreateSpace Independent Publishing Platform: North Charleston, SC, USA, 2015; pp. 65–80. [Google Scholar]
- Resnick, P.; Kuwabara, K.; Zeckhauser, R.; Friedman, E. Reputation Systems. Commun. ACM 2000, 43, 45–48. [Google Scholar] [CrossRef]
- Jø sang, A.; Ismail, R.; Boyd, C. A survey of trust and reputation systems for online service provision. Decis. Support Syst. 2007, 43, 618–644. [Google Scholar] [CrossRef]
- Amintoosi, H.; Kanhere, S.S. A Reputation Framework for Social Participatory Sensing Systems. Mob. Netw. Appl. 2014, 19, 88–100. [Google Scholar] [CrossRef]
- Tanas, C.; Herrera-Joancomartí, J. When users become sensors: Can we trust their readings? Int. J. Commun. Syst. 2015, 28, 601–614. [Google Scholar] [CrossRef]
- Christin, D.; Reinhardt, A.; Kanhere, S.S.; Hollick, M. A Survey on Privacy in Mobile Participatory Sensing Applications. J. Syst. Softw. 2011, 84, 1928–1946. [Google Scholar] [CrossRef]
- Foremski, P.; Gorawski, M.; Grochla, K.; Polys, K. Energy-Efficient Crowdsensing of Human Mobility and Signal Levels in Cellular Networks. Sensors 2015, 15, 22060–22088. [Google Scholar] [CrossRef] [PubMed]
- De Montjoye, Y.A.; Radaelli, L.; Singh, V.K.; Pentland, A. Unique in the shopping mall: On the reidentifiability of credit card metadata. Science 2015, 347, 536–539. [Google Scholar] [CrossRef] [PubMed]
- Shin, M.; Cornelius, C.; Kapadia, A.; Triandopoulos, N.; Kotz, D. Location Privacy for Mobile Crowd Sensing through Population Mapping. Sensors 2015, 15, 15285–15310. [Google Scholar] [CrossRef] [PubMed]
- Vergara-Laurens, I.J.; Mendez-Chaves, D.; Labrador, M.A. Network and System Security. In Proceedings of the 7th International Conference, NSS 2013, Madrid, Spain, 3–4 June 2013; pp. 614–620.
- Jaimes, L.G.; Vergara-Laurens, I.; Labrador, M.A. A location-based incentive mechanism for participatory sensing systems with budget constraints. In Proceedings of the 2012 IEEE International Conference on Pervasive Computing and Communications (PerCom), Lugano, Switzerland, 19–23 March 2012; pp. 103–108.
- Li, Q.; Cao, G. Providing privacy-aware incentives for mobile sensing. In Proceedings of the IEEE International Conference on Pervasive Computing and Communications (PerCom), San Diego, CA, USA, 18–22 March 2013; pp. 76–84.
- Krontiris, I.; Maisonneuve, N. Participatory Sensing: The Tension Between Social Translucence and Privacy. In Trustworthy Internet; Springer: Milan, Italy, 2011; pp. 159–170. [Google Scholar]
- Androulaki, E.; Choi, S.; Bellovin, S.; Malkin, T. Reputation Systems for Anonymous Networks. In Privacy Enhancing Technologies; Borisov, N., Goldberg, I., Eds.; Springer: Berlin, Germany, 2008; Volume 5134, pp. 202–218. [Google Scholar]
- Miranda, H.; Rodrigues, L. A Framework to Provide Anonymity in Reputation Systems. In Proceedings of the 2006 3rd Annual International Conference on Mobile and Ubiquitous Systems—Workshops, San Jose, CA, USA, 17–21 July 2006; pp. 1–4.
- Christin, D.; Roß kopf, C.; Hollick, M.; Martucci, L.A.; Kanhere, S.S. IncogniSense: An anonymity-preserving reputation framework for participatory sensing applications. Pervasive Mob. Comput. 2013, 9, 353–371. [Google Scholar] [CrossRef]
- Nakamoto, S.; Andresen, G.E.A. Bitcoin Standard Client. Available online: https://github.com/bitcoin/bitcoin/ (accessed on 24 May 2016).
- Tschorsch, F.; Scheuermann, B. Bitcoin and Beyond: A Technical Survey on Decentralized Digital Currencies. Cryptology ePrint Archive, Report 2015/464. 2015. Available online: http://eprint.iacr.org/ (accessed on 24 May 2016).
- Reid, F.; Harrigan, M. An Analysis of Anonymity in the Bitcoin System. In Security and Privacy in Social Networks; Altshuler, Y., Elovici, Y., Cremers, A.B., Aharony, N., Pentland, A., Eds.; Springer: New York, NY, USA, 2013; pp. 197–223. [Google Scholar]
- Ober, M.; Katzenbeisser, S.; Hamacher, K. Structure and Anonymity of the Bitcoin Transaction Graph. Future Internet 2013, 5, 237–250. [Google Scholar] [CrossRef]
- Ganti, R.K.; Ye, F.; Lei, H. Mobile crowdsensing: Current state and future challenges. IEEE Commun. Mag. 2011, 49, 32–39. [Google Scholar] [CrossRef]
- The Bitcoin Wiki. Contract. 2014. Available online: https://en.bitcoin.it/wiki/Contract (accessed on 24 May 2016).
- Bitcoin Project. Micropayment Channel. Available online: https://bitcoin.org/en/developer-guide#micropayment-channel (accessed on 24 May 2016).
- Vergara-Laurens, I.J.; Mendez, D.; Labrador, M.A. Privacy, quality of information, and energy consumption in Participatory Sensing systems. In Proceedings of the 2014 IEEE International Conference on Pervasive Computing and Communications (PerCom), Budapest, Hungary, 24–28 March 2014; pp. 199–207.
- Rifà-Pous, H.; Herrera-Joancomartí, J. Computational and Energy Costs of Cryptographic Algorithms on Handheld Devices. Future Internet 2011, 3, 31–48. [Google Scholar] [CrossRef]
- Maxwell, G. CoinJoin: Bitcoin Privacy for the Real World. Post on Bitcoin Forum. Available online: https://bitcointalk.org/index.php?topic=279249 (accessed on 24 May 2016).
- Bonneau, J.; Narayanan, A.; Miller, A.; Clark, J.; Kroll, J.A.; Felten, E.W. Mixcoin: Anonymity for Bitcoin with accountable mixes. In Financial Cryptography and Data Security; Christin, N., Safavi-Naini, R., Eds.; Springer: New York, NY, USA, 2014; Volume 8437, pp. 486–504. [Google Scholar]
- Bissias, G.; Ozisik, A.P.; Levine, B.N.; Liberatore, M. Sybil-Resistant Mixing for Bitcoin. In Proceedings of the 13th ACM Workshop on Workshop on Privacy in the Electronic Society, WPES ’14, Scottsdale, AZ, USA, 3–7 November 2014.
- Torproject. Tor. Available online: https://www.torproject.org/about/overview.html.en (accessed on 24 May 2016).
- Bitcoin Project. Bitcoin Core. Available online: https://bitcoin.org/en/download (accessed on 24 May 2016).
- Bitcoinj. Bitcoin Protocol Java Implementation. Available online: https://bitcoinj.github.io (accessed on 24 May 2016).
- Electrum. Electrum Bitcoin Wallet. Available online: https://electrum.org/ (accessed on 24 May 2016).
- Sergi Delgado-Segura. PaySense utils package API. Available online: http://deic-projectes.uab.cat/paysense (accessed on 24 May 2016).
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Delgado-Segura, S.; Tanas, C.; Herrera-Joancomartí, J. Reputation and Reward: Two Sides of the Same Bitcoin. Sensors 2016, 16, 776. https://doi.org/10.3390/s16060776
Delgado-Segura S, Tanas C, Herrera-Joancomartí J. Reputation and Reward: Two Sides of the Same Bitcoin. Sensors. 2016; 16(6):776. https://doi.org/10.3390/s16060776
Chicago/Turabian StyleDelgado-Segura, Sergi, Cristian Tanas, and Jordi Herrera-Joancomartí. 2016. "Reputation and Reward: Two Sides of the Same Bitcoin" Sensors 16, no. 6: 776. https://doi.org/10.3390/s16060776
APA StyleDelgado-Segura, S., Tanas, C., & Herrera-Joancomartí, J. (2016). Reputation and Reward: Two Sides of the Same Bitcoin. Sensors, 16(6), 776. https://doi.org/10.3390/s16060776




