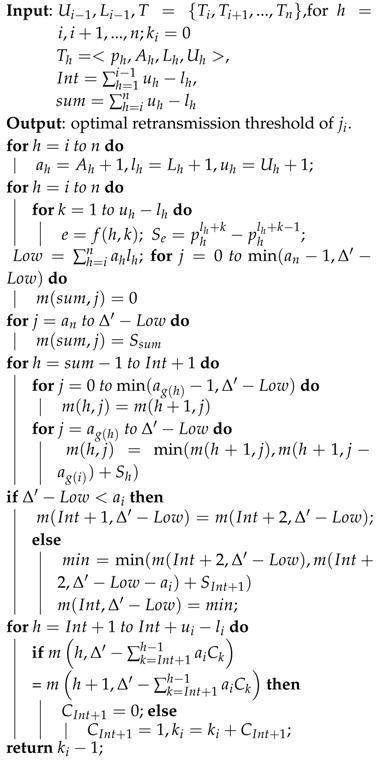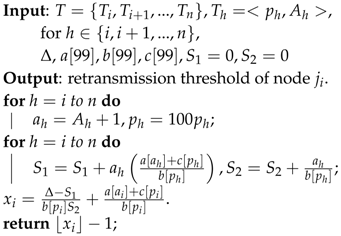1. Introduction
Wireless Sensor Networks (WSNs) have been increasingly deployed for a wide variety of real-time applications, such as industrial Internet-of-Things, emergency response, critical infrastructure monitoring and process measurement and control. In real-time applications, deadline misses in data transmission may bring about irreparable damage [
1,
2,
3,
4]. For mission-critical tasks, not only the packet delivery deadline should be met, but also the transmission reliability is supposed to be guaranteed. Therefore, providing reliable and timely data delivery in WSNs is crucial to the success of the mission.
In supporting mission critical-tasks, data delivery is required to be timely and reliable, but it is challenging for desirable Quality of Service (QoS). Due to the transmission uncertainties, wireless link dynamics and the queueing dynamics, wireless link qualities in sensor networks can vary at a wide range of timescales [
5,
6], which also results in node failures and connectivity varying over time [
7]. In practical sensor networks, the sensor node may need multiple retransmissions for successfully forwarding a packet at each hop. A maximum number of retransmissions,
i.e., retransmission threshold, is usually set for each node to prevent transmitting a packet over a bad link unlimitedly, and the packet will be eventually dropped by the sender after the maximum number of transmission retries. The success of a packet delivery is probabilistic, and thus, the WSNs are rendered unreliable.
QoS supported by the underlying networks aims to meet end users’ satisfaction with the services that the system provides [
8]. The QoS provisioning in data delivery can be measured in the form of performance metrics, such as delay, packet loss rate and throughput. There exists a tradeoff among the QoS requirements, such as transmission reliability and deliver delay. Thus, the soft QoS supported can be accomplished, in which the soft QoS refers to achieving the QoS requirements with probability. Many efforts have been made to improve transmission reliability and deliver delay in WSNs, including quality measurement of forwarding data [
5,
9,
10] and real-time routing protocol designing [
11,
12,
13].
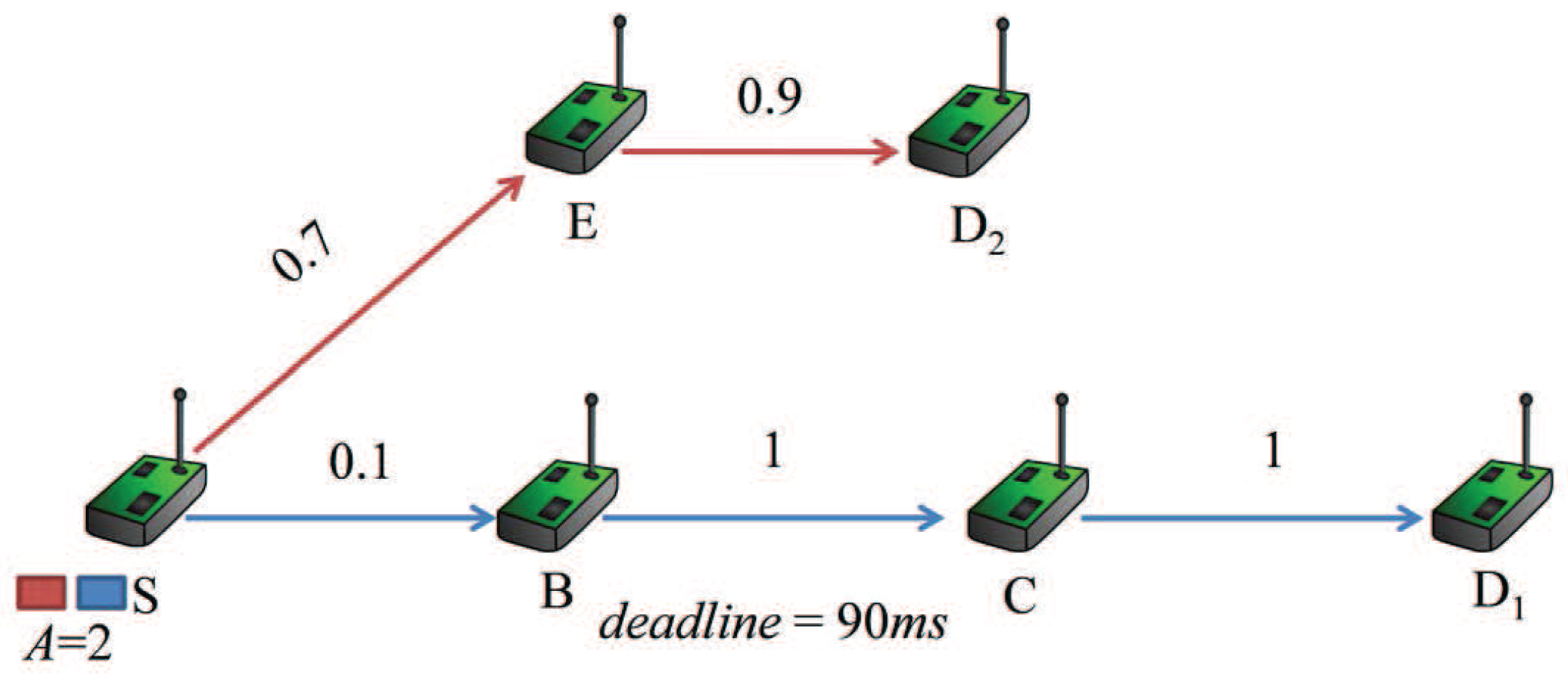
The main methodology applied in the existing works is to exploit a delivery path based on the QoS-aware forwarding quality metrics to improve the performance of packet transmission. However, there exist limited studies on the optimization of the retransmission threshold for each node in a delivery path, which imposes a significant effect on the probability of a packet being successfully transmitted within specified deadline. Most protocols set the same retransmission threshold for all sensor nodes in advance without considering the delay requirement and link quality, so that the delivery performance in terms of latency and reliability is decreased. We use an example inspired by the one in [
14] to show the impact of retransmission threshold on the performance, illustrated in
Figure 1.
The number associated with each link is the probability for a packet being successfully delivered to the next node through the link, denoted by
, which means that on average,
transmission trials are needed to successfully deliver a packet through the link. The integer variable
A denotes the number of packets in the buffer waiting to be served. The delivery path for the first packet is
, and the path for the second packet is
. We assume that one transmission takes 10 ms, and the deadline of delivering the first packet from node
S to node
is 90 ms. For delivering the packet to node
before the deadline, the summation of transmission trials along the path must be no more than nine, that is the result of 90 ms divided by one transmission time of 10 ms. Traditional protocols set the same retransmission threshold for each relay node in advance. If the protocol is set by a high retransmission threshold, such as 29, in the CTPprotocol [
15], without the consideration of delay requirement, thus the probability for successfully transmitting the first packet through the link
can be significantly improved. However, this strategy may make the deadlines of both packets expire and consumes more system resource. If the maximum number of transmission trials is three for each node, in view of the summation of transmission trials, there are no more than nine. Then, the probability of the first packet passing the link
is
. However, if the retransmission thresholds of the three nodes are set to 6, 0 and 0, that is the maximum numbers of transmission trials are 7, 1 and 1, then the probability is
. In terms of latency and reliability, there is a tradeoff in determining the retransmission threshold. Therefore, the retransmission threshold should be carefully chosen to achieve desirable QoS provisioning [
9].
From the example above, it is obvious that the retransmission threshold has significant impact on the delivery performance in terms of delay and reliability. Few studies focus on the optimization of the retransmission threshold [
5,
14], and they have the following two major disadvantages. In the feedback control-based framework [
5], a heuristic method for adjusting the transmission numbers is proposed, which does not provide the reliability guarantee. In our previous work [
14], a greedy-based algorithm for finding optimal retransmission thresholds is proposed, which overlooks the impact of queue length on the forwarding quality. The aforementioned observation motivates us to investigate the problem of finding optimal retransmission thresholds in this paper. The problem is formalized as an integer optimization problem first. Then, a dynamic programming-based distributed algorithm for solving the problem is proposed. It can be run on a sensor node and enables the node to adaptively set the optimal retransmission threshold based on the link quality and the remaining time to deadline. Its time complexity is
, where
is the given upper bound of the retransmission threshold of sensor node
i in a given delivery path and
n is the length of the delivery path. The complexity depends on delivery delay Δ. If Δ is less than or equal to the polynomial, the complexity of the algorithm is polynomial. Otherwise, the algorithm is not efficient. In this case, a
-approximation algorithm is provided based on the linear programming. Furthermore, when the ranges of the upper and lower bounds of the retransmission thresholds are big enough, a Lagrange multiplier-based distributed
-approximation algorithm with time complexity
is developed. The main contributions of the paper are as follows.
The problem of finding optimal retransmission thresholds for each node along a delivery path is defined and is formalized as an integer optimization problem.
A Dynamic Programming-based Distributed Algorithm (DPDA) for solving the problem above is proposed; the correctness of the algorithm is proven; and its time and space complexity are analyzed, i.e., , and .
In case of the delivery delay Δ being greater than the polynomial, a Linear Programming-based -Approximation Algorithm (LPAA) is proposed.
Furthermore, in the case of the ranges of the upper and lower bounds of the retransmission thresholds being big enough, a Lagrange Multiplier-based Distributed Approximation Algorithm (LMDAA) with time complexity is proposed.
Simulation experiments are conducted to evaluate the proposed algorithms. Simulation results show that the proposed algorithms in the paper have better performance for real-time data delivery.
The rest of this paper is organized as follows. The related works on real-time data delivery are surveyed in
Section 2. In
Section 3, the problem is described. In
Section 4, a dynamic programming-based distributed algorithm for finding optimal retransmission thresholds is provided.
Section 5 gives a linear programming-based approximation algorithm, and the ratio bound is analyzed. In
Section 6, a Lagrange multiplier-based distributed
-approximation algorithm with time complexity
is proposed. Experimental results are illustrated in
Section 7, and
Section 8 concludes this paper.
2. Related Works
The real-time performance of packet delivery is a fundamental factor in sensor networks, and many efforts have been made to design efficient real-time routing protocols in WSNs. Most of the existing works addressed the following two challenges. First, it is essential to design the metric, which measures the forwarding quality, such as node forwarding quality [
9], link quality [
10], data aggregation [
2] and energy efficiency [
12]. Approximate aggregation for tracking quantiles and range countings is presented in [
2], where a dynamic binary tree based deterministic tracking algorithm is proposed. Based on the actual number of data transmissions, link-Quality of Forwarding (QoF) and node-QoF metrics are proposed in [
9]. A data-driven-based link quality prediction approach is provided in [
10], which combines the packet reception ratio and the physical-layer information. Considering queuing delay, the Weighted End-to-End Delay (WEED) metric is introduced in [
11]; the work focuses on selecting the path with the minimum expected end-to-end delay. In multi-hop wireless networks, the routing decision takes spatial reusability into account to improve the end-to-end throughput [
16]. The authors in [
17] utilize the expected available bandwidth to capture the logical intra-flow and inter-flow interference, and an isotonic metric of expected delay is proposed. Dependence among links was revealed recently. By exploiting the low correlated forwarding links, link-correlation Opportunistic Routing (OR) is given in [
18]. Facing the uncertainties in wireless communication, the multi-timescale adaptation routing protocol is provided in [
6], which can adapt to
in situ delay conditions in routing delay.
To provide real-time packet delivery, QoS provisioning protocols and transmission scheduling protocols have also been extensively studied. The literature [
13] studies geographic opportunistic routing protocol for multi-constrained QoS provisioning in WSNs, and the problem is formulated as a multi-objective multi-constraint optimization problem. By differentiating the priorities of user-level applications, the author in [
19] develops an optimization tool for balancing the system resources and presents a cluster-based routing protocol. Under the constraints of delay and load balancing requirements, a centralized heuristic algorithm for selecting the path with minimal cost is provided in [
20]. To separate the packet of different QoS requirements, a virtual hybrid potential field is introduced in [
21]. Considering capacitated multicast routing problem, the work [
22] provides the approximation algorithms for multicast k-path routing and multicast k-tree routing. By supporting slot rescheduling, the segmented slot assignment-based method for improving retransmission efficiency is proposed in [
23]. Pan
et al. [
24] formulate joint routing and scheduling into an optimization problem and solve the problem with a column generation method. To route around the dead end relay node, the authors in [
25] propose the cross-layer protocol, which integrates geographic routing with the contention-based MAC protocol. The author in [
26] map the scheduling of data flow to multiprocessor scheduling and prove an upper bound of the end-to-end communication delay.
There exist limited studies on optimizing the retransmission threshold [
5,
14]. A distributed route maintenance framework is proposed in [
5], which enables the link to adjust the retransmission number. However, the proposed heuristic method cannot provide the reliability guarantee theoretically. In our previous work [
14], a greedy-based algorithm for finding optimal retransmission thresholds is proposed, which overlooks the impact of queue length on the forwarding quality. To overcome the shortage of the method, we investigate the problem of finding optimal retransmission thresholds in this paper.
3. Problem Description
In this section, the problem of finding optimal retransmission thresholds for each node along a delivery path is defined and is formalized as a general integer optimization problem. We prove that the problem is NP-hard.
3.1. Problem Definition
Suppose that the end-to-end path is
, where
and
are source and destination nodes and other
’s are relay nodes. There exist the following four attributes for each link
.
transmission time t: This means that once transmission costs time, including encoding and wireless communication. Usually each sensor node takes the same time for once transmission.
transmission failure probability : denotes the transmission failure probability over the link . It means that is the probability of a transmission failure due to either collisions or bad channel quality when node forwards a packet to node .
retransmission threshold : This means that the maximum number of retransmission trials is . It is obvious that the maximum number of transmission retries is , and thus, the packet will be eventually dropped by the sender after the transmission retries. It can be known that is the probability of a packet being successfully delivered to node .
retransmission threshold
: Each hop delay consists of the transmission delay over the wireless link and the queuing delay in the buffer [
9].
denotes the number of the packets queued at node
, which means that there exist
packets to be forwarded [
6].
We define the metric of a given retransmission threshold as the probability of a packet being successfully delivered through the link. Existing works exploit multipath routing to guarantee both reliability and deliver delay in WSNs [
13,
27,
28]. Similarly to [
5,
9], we aggregate the measure over a path based on the metric and aim at maximizing the summation of the probability of the packet delivered to the next relay node along the given path within the deadline. The path-metric estimates the given path forwarding quality, and it considers both transmission reliability and delay constraint.
The end-to-end delay over a path is the summation of the delays of all of the hops along the path. Let
δ denote the delay constraint. Then, the problem of finding the optimal retransmission thresholds for each node can be formulated as the following integer optimization problem, where
and
are the given lower and upper bounds of the retransmission threshold of node
i.
Each hop delay consists of the transmission delay and the queuing delay in the buffer; thus, the maximum delay latency for each hop is . The first inequality constraint means that the deliver delay of the last packet served at source node is no more than the deadline constraint δ. The second inequalities mean that the retransmission thresholds should be bounded in a given interval.
For the convenience of formalization and analysis, let Δ denote
. For any
, let
and
; then, the problem above is equivalent to the following integer optimization problem.
3.2. Computational Complexity Analysis
In this subsection, we construct a
0-1 Knapsack problem [
29], and we prove that integer optimization Equation (2) is equivalent to the proposed
0-1 Knapsack problem. The computational complexity of the
0-1 Knapsack problem is NP-hard [
29]; thus the hardness of the problem for calculating optimal retransmission thresholds is NP-hard.
Let
denote
, where
. It can be known that
. Thus, we can formulate a 0-1 Knapsack problem as follows.
Lemma 1. For ,
the following inequalities hold if and ,
where .
Proof. Let . For any , it is obvious that is a monotone decreasing function; thus, . Obviously, . Since and , we have . In conclusion, . ☐
Lemma 2. If are the optimal solutions to Equation (3), then there exist ,
such that:where .
Proof. The proof is by contradiction. Suppose that are the optimal solutions to Equation (3) and that they enable the objective function value to achieve the minimum. For given m, if there is no integer in such that Equation (5) are true, then there must exist integers such that and . We can construct a solution, whose objective function values are less than that of , by exchanging and . Suppose that are derived by merely exchanging and .
Firstly, we prove that are feasible solutions of Equation (3). For any and , and are variables. It is obvious that . According to the construction of the solution, and are identical correspondingly, except for and . Since , we have . Thus, are feasible solutions.
Let
be the difference between the values of the two objective functions. It is easily derived that
. From Lemma 1, we know
. Then,
are more optimal solutions, and it contradicts the fact that
are the optimal solutions. ☐
Theorem 3. Suppose that are the optimal solutions to Equation (3). For any , let . Then, are the optimal solutions to Equation (2), and the values of the two objective functions are identical.
Proof. Suppose that
are the optimal solutions of Equation (2), then we can construct feasible solutions
to Equation (3) as following, where
.
It can be known that
. Since
,
are the feasible solutions to Equation (3). Based on the definition of
, it can be derived that
. Thus, the following inequality can be derived.
Therefore, the objective function value of Equation (3) is a lower bound of that of Equation (2).
Since
are the optimal solutions of Equation (3), there exist
, such that Equation (5) hold according to Lemma 2. For any
i,
from Equation (5), then
. Since
, we have
. Since
satisfy all of the constraints of Equation (3),
. For any
i, it is obvious that
. Thus,
are the feasible solutions of Equation (2), and hence:
Thus, the objective function value of Equation (2) is a lower bound of that of Equation (3). Based on the analysis above, we can conclude that
are the optimal solutions of Equation (2); the values of the two objective functions are identical. ☐
Corollary 4. The hardness of integer optimization Equation (2) is NP-hard. That is, finding optimal retransmission thresholds for each node in a delivery path is NP-hard.
Proof. Based on Theorem 3, the hardness of Equation (2) is identical to 0-1 programming Equation (3), which is equivalent to the
Knapsack problem. Since the
Knapsack problem is
NP-hard [
29], the hardness of integer optimization Equation (2) is
NP-hard. ☐
4. Dynamic Programming-Based Distributed Algorithm for Optimal Retransmission Thresholds
As analyzed in
Section 3.2, the problem of finding optimal retransmission thresholds is equivalent to the
0-1 Knapsack Problem. Thus, it can be solved by a dynamic programming-based pseudo-polynomial time algorithm [
29]. In this section, we first prove the correctness of the dynamic programming-based algorithm, which can output the optimal resolutions to Equation (3). We design a dynamic programming-based algorithm to solve the proposed
0-1 Knapsack Problem, and then, according to Theorem 3, the optimal retransmission thresholds can be derived based on the resolutions to Equation (3).
Theorem 5. If are the optimal solutions to Equation (3), then are the optimal solutions to the following problem. Proof. The proof is by contradiction. If
are not optimal solutions to Equation (
8), suppose that
are the optimal solutions of Equation (
8). Then,
are batter solutions of Equation (3), which leads to a contradiction. The proof demonstrates the correctness of the dynamic programming-based algorithm. ☐
To briefly describe the recursive procedure, based on Lemma 2, the following mappings are introduced,
where
. Let
and
, then Equation (3) is equivalent to the following knapsack problem.
When the object set is
and the capacity is bounded by
j, we use
to express the minimum cost. Then, we derive the recursive equation of
.
Additionally, the initial conditions are as follows.
Suppose that node
needs to forward a packet with delivery delay
and that the end-to-end path is
. Since the packet is the first one queued at node
,
. Therefore, finding the optimal retransmission threshold
for the packet over link from
to
is equivalent to solving the following integer optimization problem.
According to Theorem 3, the above Equation (
10) is equivalent to the following knapsack Equation (
11).
Based on the above analysis, knapsack Equation (
11) is a special instance of Equation (
9), where the `object’ set is
and the `capacity’ is bounded by
. Suppose
are the optimal solutions of Equation (
11), then
is the optimal retransmission threshold of node
. The message exchanges among network nodes are enhanced to carry necessary information of link quality and queue length [
6,
11], so that each node can independently calculate the optimal retransmission threshold based on the path forwarding quality and the remaining time to deadline. Such a property enables the node to adaptively set the optimal retransmission threshold in a scalable manner. The proposed dynamic-based distributed algorithm for the optimal retransmission threshold is described in Algorithm 1.
We present the analysis for the computational complexity of Algorithm 1. The recurrence process of the algorithm yields the time computation of . Thus, the time complexity of the proposed distributed algorithm is . Space complexity can be similarly analyzed, that is .
5. Linear Programming-Based Approximation Algorithm
The dynamic programming-based algorithm proposed in
Section 4 is not efficient, if Δ is greater than the polynomial function with respect to
n. In this section, we construct a linear programming problem and prove that the solution of the proposed problem can be used to construct the approximate solution of integer optimization Equation (2). Additionally, then, a linear programming-based
-approximation algorithm is provided.
5.1. Mathematical Foundations
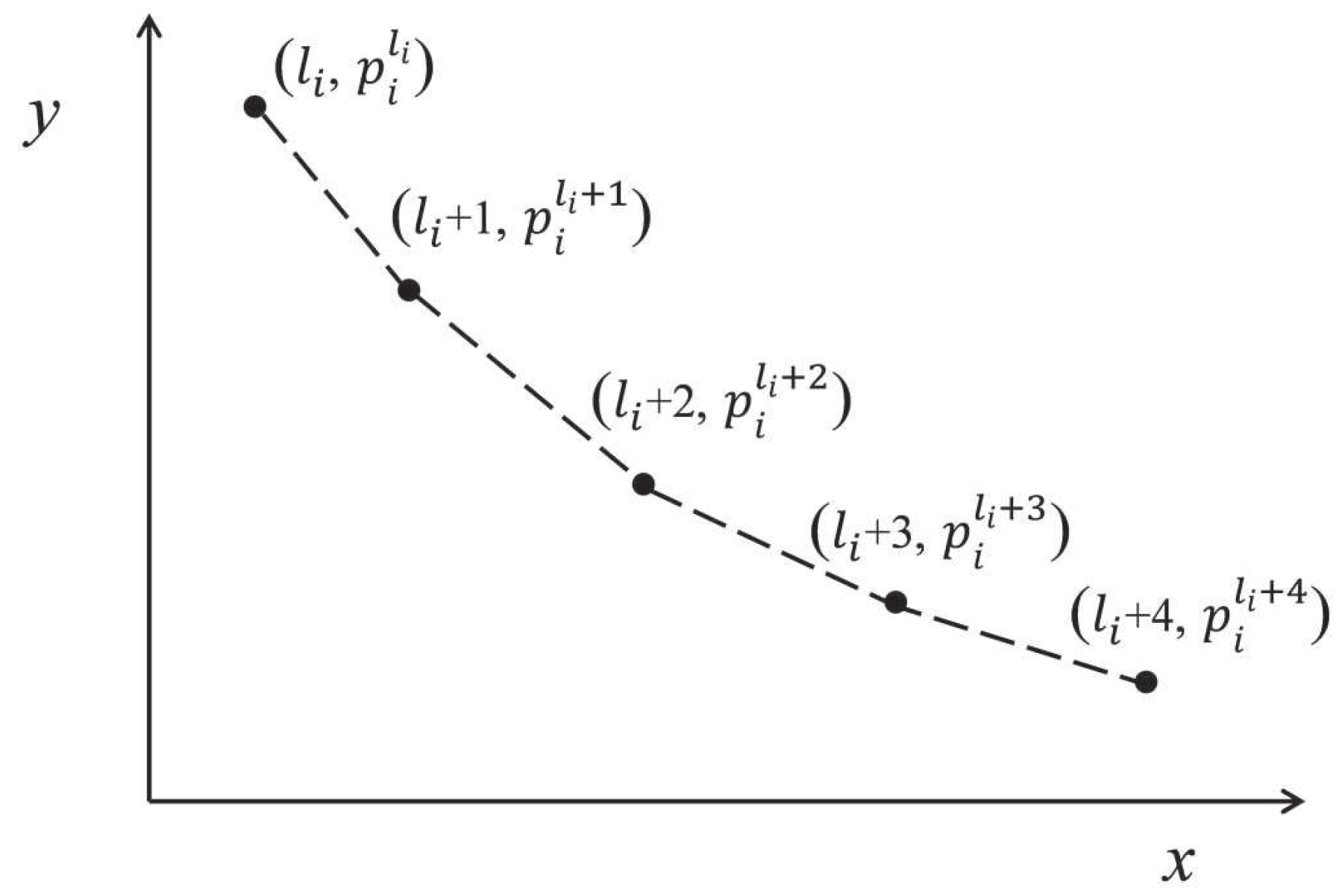
According to
and
, piecewise linear function
is defined as follows, where
. We use an example to illustrate the defined function, as depicted in
Figure 2.
Lemma 6. For any , is a convex function.
| Algorithm 1: Dynamic Programming-based Distributed Algorithm for the optimal retransmission threshold (DPDA). |
![Sensors 16 00665 i001]() |
Proof. For any i, since is a piecewise linear function, , where and . Thus, satisfies the sufficient condition of convexity function if . Now, we prove that is a convex function if .
Suppose that , where and . Since , is a convex function. Thus, . For any , there must exist , such that .
From the definition of , . Let , we have , and . Since , then according to the convexity of . Based on the above analysis, it can be derived that . In conclusion, for any , is a convex function. ☐
According to the constraints of Equation (2), a general optimization problem can be formulated as follows.
Theorem 7. The objective function value of Equation (12) is a lower bound of that of Equation (2), which implies that a feasible solution can be derived based on the optimal resolutions of Equation (12).
Proof. Suppose that
are the optimal solutions to Equation (2). For any
, let
. Thus,
are feasible solutions to Equation (12), and hence:
Therefore, the objective function value of Equation (12) is a lower bound of that of Equation (2). ☐
Theorem 8. The proposed optimization Equation (12) is equivalent to the following linear programming problem, and then, the general optimization Equation (12) can be solved by the linear programming technique. Proof. For any , we have . It is easily known that for any , there exist , such that and . Additionally, similarly for any , if , there must exist , such that .
Suppose that
are feasible solutions of Equation (13). For any
, let
. Thus,
are feasible solutions of Equation (12). According to the convexity of
, we have
, and hence:
Suppose that
are the optimal solutions to Equation (12); there must exist
n integers
, such that
. For any
, let
, and the others
are zero. Obviously,
are feasible solutions of Equation (13). Based on the definition of
,
. Thus, we can have the following formula.
In conclusion, optimization Equation (12) is equivalent to linear programming Equation (13). ☐
5.2. Linear Programming-Based Approximation Algorithm
Suppose that
are the optimal solutions to Equation (13). For any
, let
. Thus,
are the optimal solutions to Equation (12) according to the proof of Theorem 8. To obtain the feasible solutions of integer optimization Equation (2), rounding optimal fractional solutions is a natural idea [
29]. The following theorem guarantees that the ratio bound of the rounding approach is
, where
is the minimum of the probabilities of one transmission failure along the given end-to-end path.
Theorem 9. For any , the ratio bound of the rounding approach is , if , where .
Proof. Suppose that
are the optimal solutions to Equation (12), which are derived from the optimal solutions of linear programming Equation (13). Denote
as the optimal solutions to Equation (1). From Theorem 7, the approximation ratio
r satisfies the following formula.
According to the proof of Theorem 8, for any
, there must exist integer
in
, such that
. Based on the convexity of
, we know that:
Let
; we have:
Additionally, then, the approximation ratio
r satisfies the following formula:
For any , since , and . In conclusion, the ratio bound is . ☐
The link properties vary as a result of environmental conditions changing at a longer timescale [
6,
15], then the difference of failure transmission probability among links is little. Thus, the premises of Theorem 9 are always satisfied in practical sensor networks. Since the objective function value of Equation (12) is decreasing with respect to
, its optimum value can be achieved if and only if
. For a general linear programming problem, finding optimal solutions incurs high computational overhead. However, it can be efficiently solved if the problem is to optimize a linear function subject to linear equality constraints [
30].
The linear programming-based distributed approximation algorithm running at each sensor node is described in Algorithm 2, which is derived from the convex programming algorithm in [
30].
and
are the left and right derivative of
, respectively. The proposed algorithm in [
30] can yield optimal solutions for the piecewise linear convex function. For any
, the derivative of
is discontinuous and constant. According to the proposed algorithm [
30], the termination condition can be satisfied when the optimal retransmission threshold is not
or
. The maximum number for iteration rounds can be assigned in advance. The algorithm can also be stopped if the convergence condition is not achieved. Therefore, figuring out the retransmission threshold of node
can be achieved.
7. Experiment Evaluation
The effectiveness and efficiency of the proposed algorithms are evaluated through simulations in this section. Several experiments are conducted to demonstrate the relationships between the performance of real-time data delivery and the input parameter, such as deadline, the number of hops of the given delivery path and the number of packets queued at the relay node. The first two group of simulations are carried out by MATLAB, and the third group is implemented with NS2.
One hundred sensor nodes and the sink are randomly deployed into a region of size 200 m × 200 m (m for meters), and we assume that the sensors have the same transmission radius. In each simulation, source and destination nodes are randomly selected. Each simulation is repeated 100 times and the simulation result corresponds to the average value over 100 times. To understand the benefits of the proposed algorithms, the comparison with the general method is conducted. The main idea of the general method is that we set the same retransmission threshold for all of the sensor nodes.
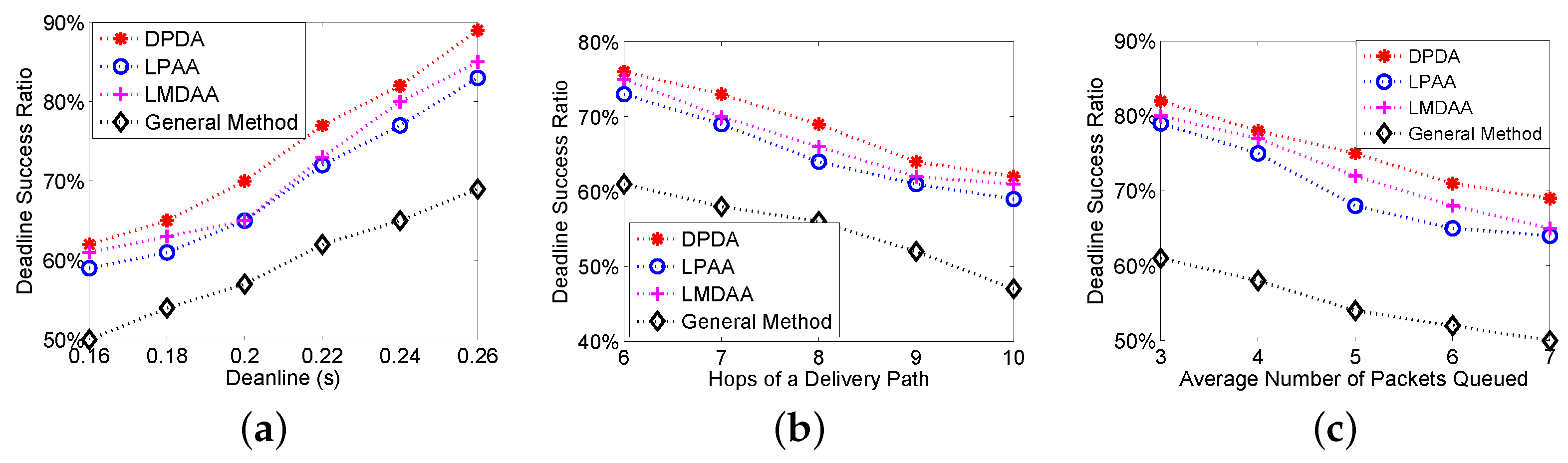
The first group of experiments is to investigate the Deadline Success Ratio (DSR) of the proposed algorithms, where DSR is the ratio of the packets delivered to the destination before their deadlines.
Figure 3a shows the relationship between the deadlines and DSRs. The proposed algorithms have better performance. For example, when the deadline is 0.22 s, the DSRs of LMDAA and general method are 74% and 61%, respectively. Furthermore, we investigate the impact of the number of hops of a delivery path on the DSR. The remaining time to the deadline and link quality have been considered; thus, our algorithms can achieve higher deadline success ratios as shown in
Figure 3b.
Figure 3c depicts the relationship between the average number of packets queued at relay nodes and DSRs. From
Figure 3c, the DSR becomes worse with the increase of the packets queued on the condition that the deadline is a constant. LMDAA is a distributed algorithm and enables the node to adaptively set the optimal retransmission threshold based on the link quality and the remaining time to the deadline. Therefore, LMDAA has better performance in terms of DSR than that of LPAA.
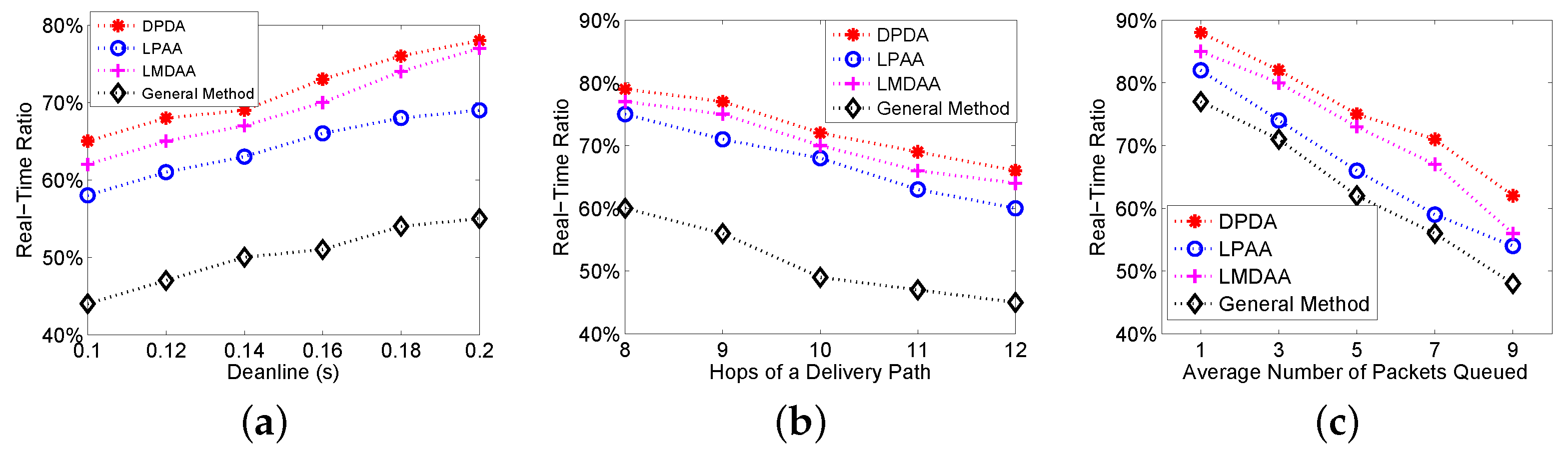
The second group of experiments is to investigate the Real-Time Ratio (RTR) of the proposed algorithms, where RTR is the ratio of the packets delivered to the destination before their deadlines among the packets successfully delivered to the destination node.
Figure 4a shows the relationship between the deadlines and RTRs. As expected, the proposed algorithms can reach higher RTR than that of the general method.
Figure 4b depicts the relationship between the number of hops of a delivery path and RTRs. The figure shows that our algorithms have better performance. For example, the real-time ratio of LPAA is more than 60%. Similarly, we investigate the impact of the average number of packets queued at relay nodes on RTR, with results illustrated in
Figure 4c. Experimental results show that the proposed algorithms can reduce the deliveries of the packets, which cannot meet their deadlines. Therefore, our algorithms can improve the real-time ratio and energy efficiency.
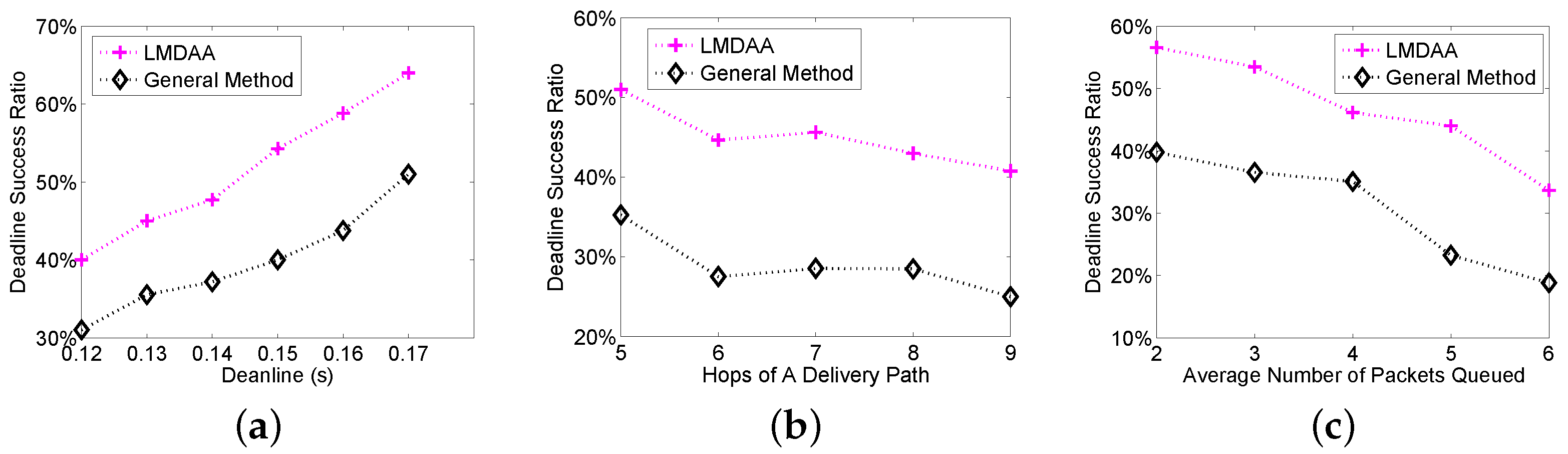
The third group of simulations is implemented with NS2, which is a widely-used simulation tool in wireless sensor networks. From the experimental results of the first two groups of simulations, LMDAA can reveal the effectiveness of the proposed algorithms more neutrally, then we compare the results of LMDAA and the general method. The reasons why DSRs in the simulations implemented by NS2 are lower than those in case of MATLAB are as follows. For identical transmission failure probability, the link quality in NS2 simulation is much worse, which leads to a lower packet delivery ratio. Secondly, we have to set stationary retransmission thresholds in advance in NS2 simulations, and the retransmission thresholds cannot be adaptively set based on the link quality and remaining time during the packet delivery. As shown in
Figure 5a–c, the proposed algorithm has better performance in real-time data delivery, in the case of worse wireless links or a severe delivery delay requirement.
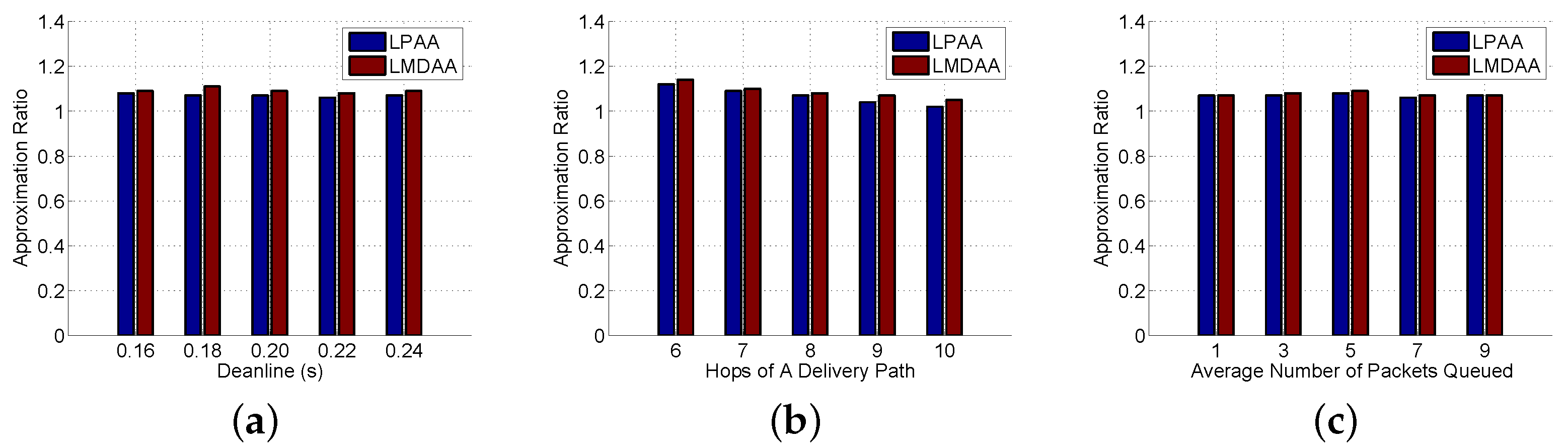
The forth group of experiments is to investigate the computing performance of LPAA and LMDAA, and the correctness of the approximation ratio is verified. We prove that the objective function value of Equation (12) is a lower bound of that of Equation (2), then
generated by the optimal solution of Equation (12) is an upper bound of Equation (1). In the experiments, the Approximation Ratio (AR) is the ratio of
generated by the optimal solutions of linear programming Equation (13) to that of the approximated solutions output by LPAA and LMDAA.
Figure 6a–c demonstrates the relationships between the approximation ratio and the input parameter. Experimental results show that the objective function value of the approximation results returned by LPAA and LMDAA is very close to that of the optimal ones. Additionally, the proposed approximation algorithms can achieve high accuracy in terms of optimal retransmission thresholds.