A Trust-Based Adaptive Probability Marking and Storage Traceback Scheme for WSNs
Abstract
:1. Introduction
- (1)
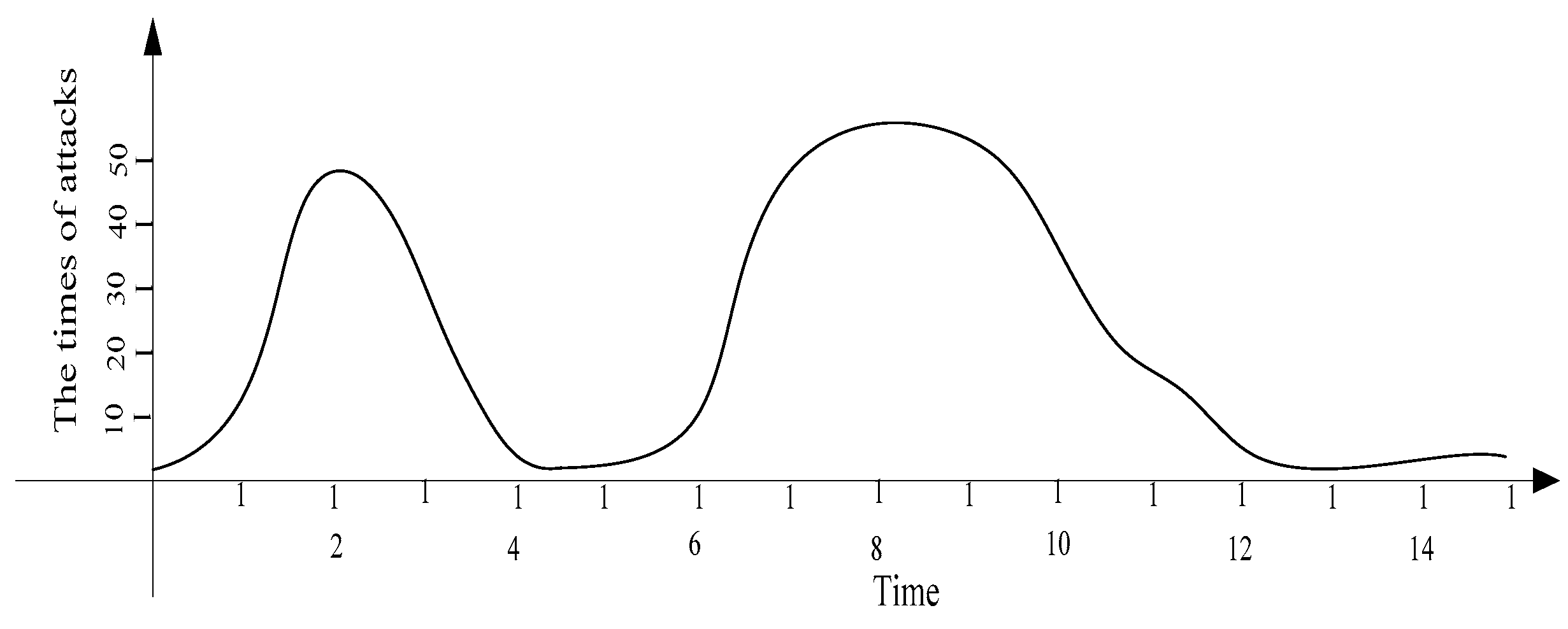
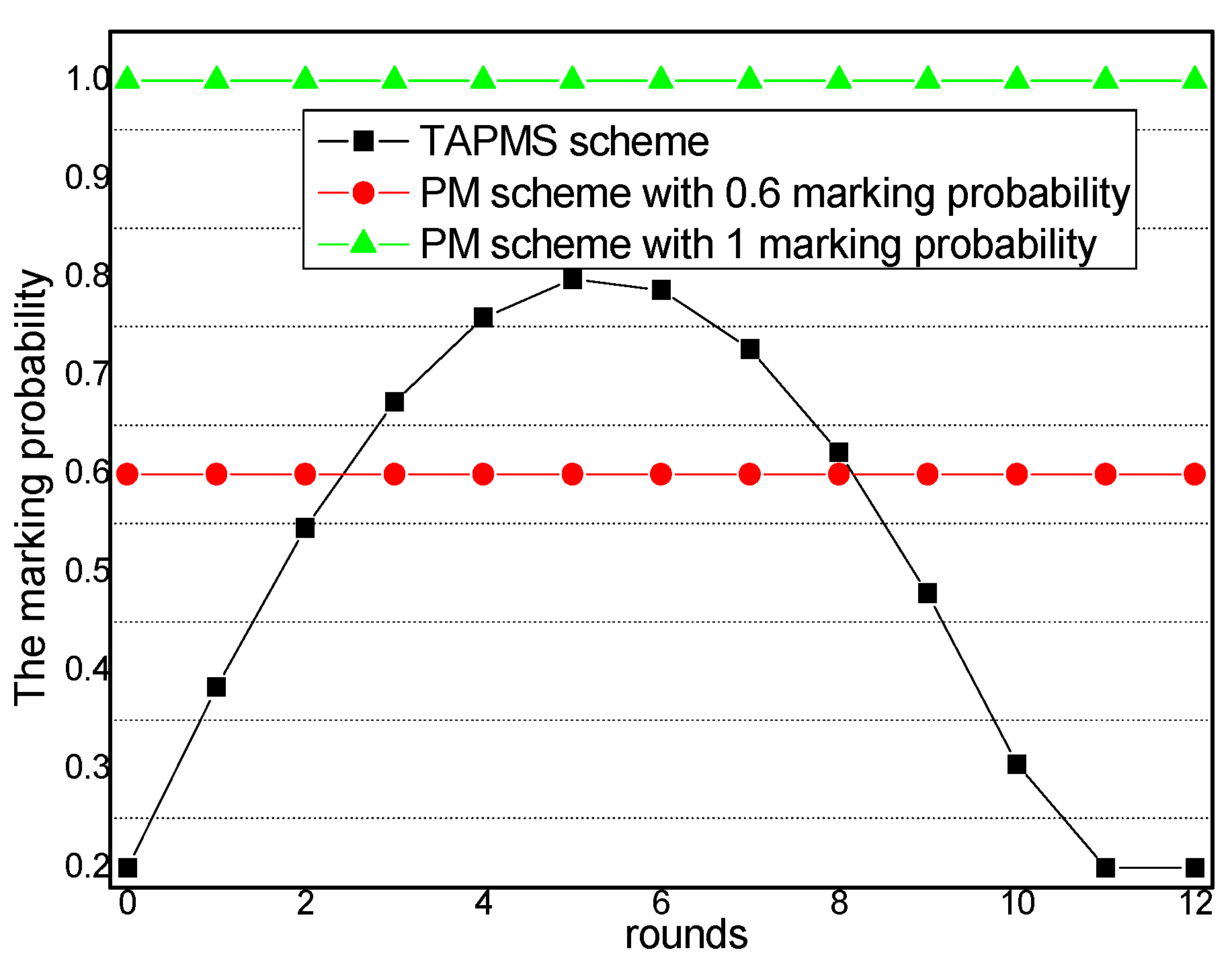
- In the TAPMS scheme, the marking probability of nodes is adaptively adjusted according to their trust. First, in data transmissions, the times a network is attacked can be detected by the sink; thus, the security level in the network can be evaluated by the sink. The process for evaluating the security level is that before beginning data transmission, the sink provides predetermined attack times. At the time of data transmission, if the attack time of the network is greater than the predetermined value, the security level in the network has not improved. Therefore, the security level in the network requires adjustment. After time slots τ, the security level in the network can be evaluated by the sink according to the difference between two consecutive time slots. If the attack time in this time slot is less than the attack times in the last time slot, the security level has become good, therefore, the security level of the network will be better in the next time slot τ. It is reasonable to set a low marking probability in a secure network to save energy, but to set a high marking probability in an insecure network to locate the source(s) of malicious nodes. Therefore, the marking probability can be set in the TAPMS scheme as follows: if the network is in a “safe” state, the baseline of the marking probability can be set low to reduce the number of marking tuples. In contrast, the baseline of the marking probability can be set high when the security level of the network is low. Second, if node trust is high, the marking probability of nodes can be reduced. Conversely, the marking probability of nodes with low trust should be high. Because most nodes are marked with low probability, it will be easy to determine that the average marking probability of nodes in TAPMS is lower, the traceback time is shorter, and network lifetime is longer.
- (2)
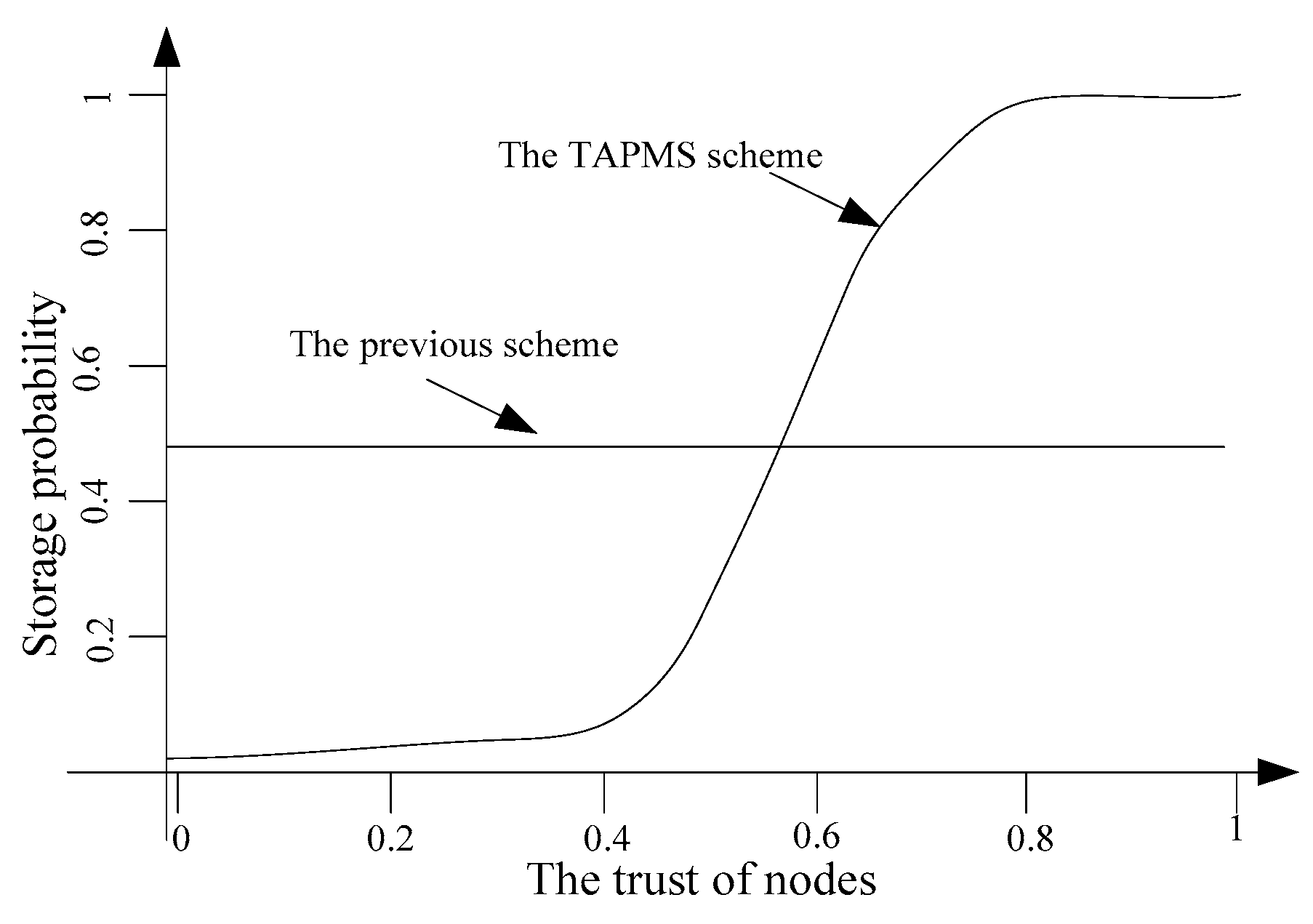
- In the TAPMS scheme, marking tuples are stored in high trust nodes to ensure stored marking tuples with high reliability. In previous schemes, nodes are randomly selected to store marking tuples. If marking tuples are stored in low trust nodes, those marking tuples can be dropped easily, which leads to a loss of marking tuples that are used to reconstruct the path from the sink to source nodes; therefore, the performance of the scheme is poor. In the TAPMS scheme, marking tuples are stored in high trust nodes, thus, the performance of this scheme has been improved.
- (3)
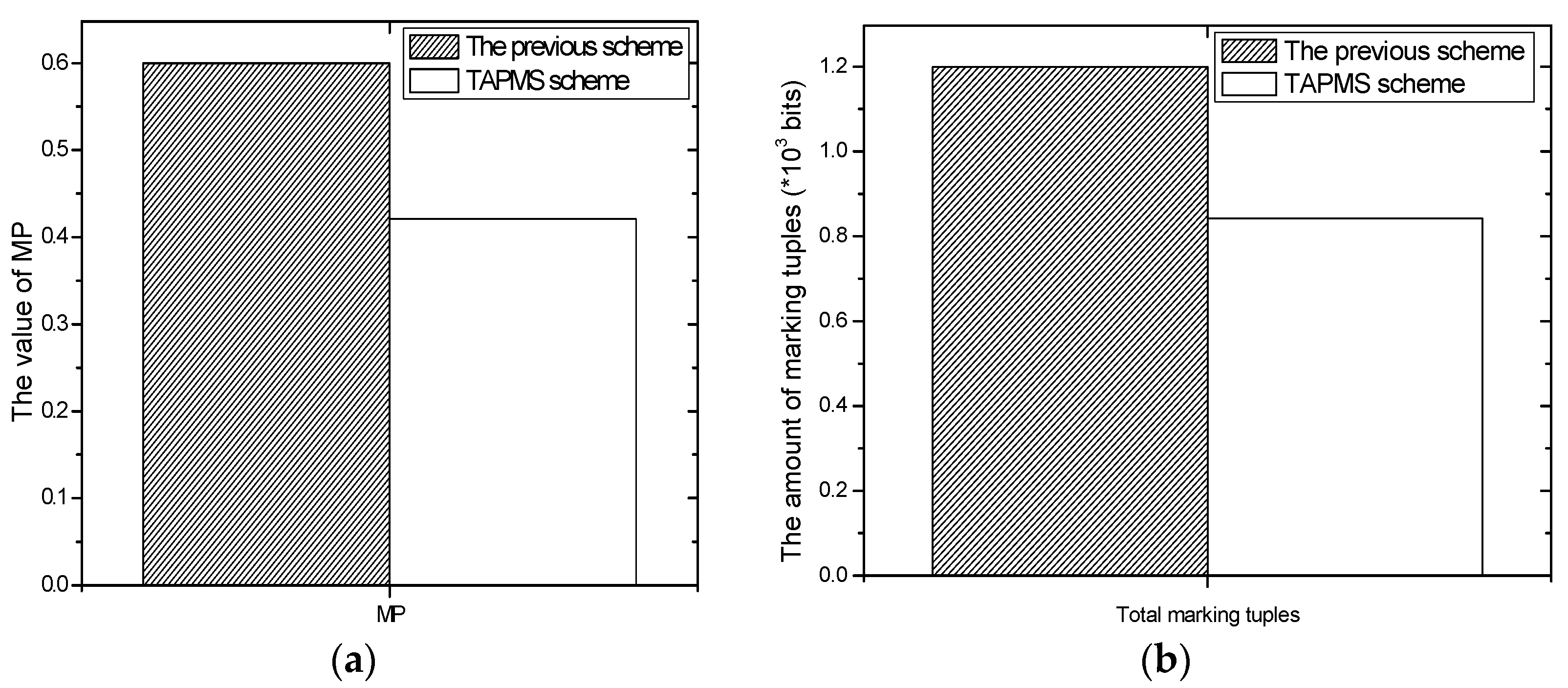
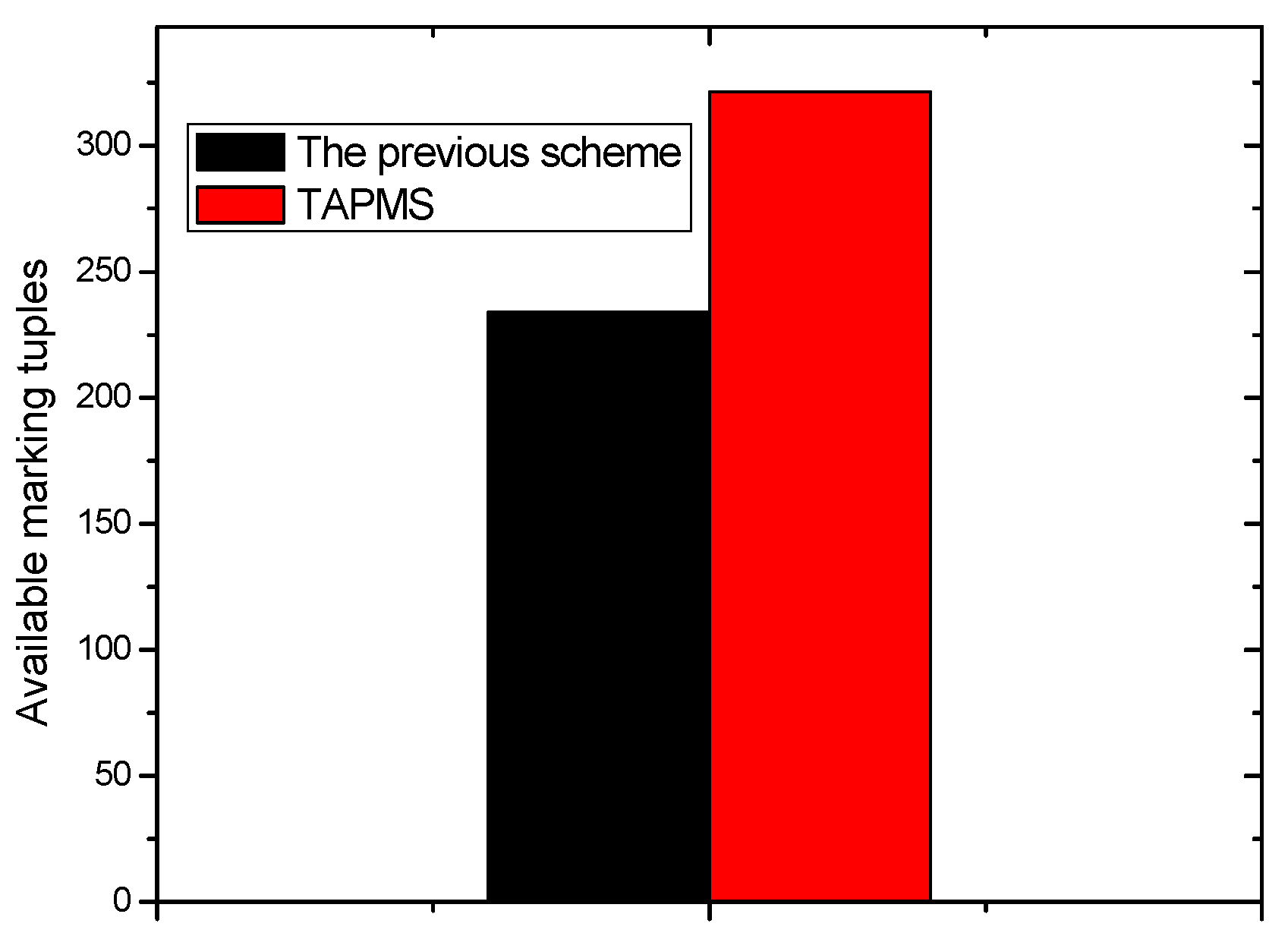
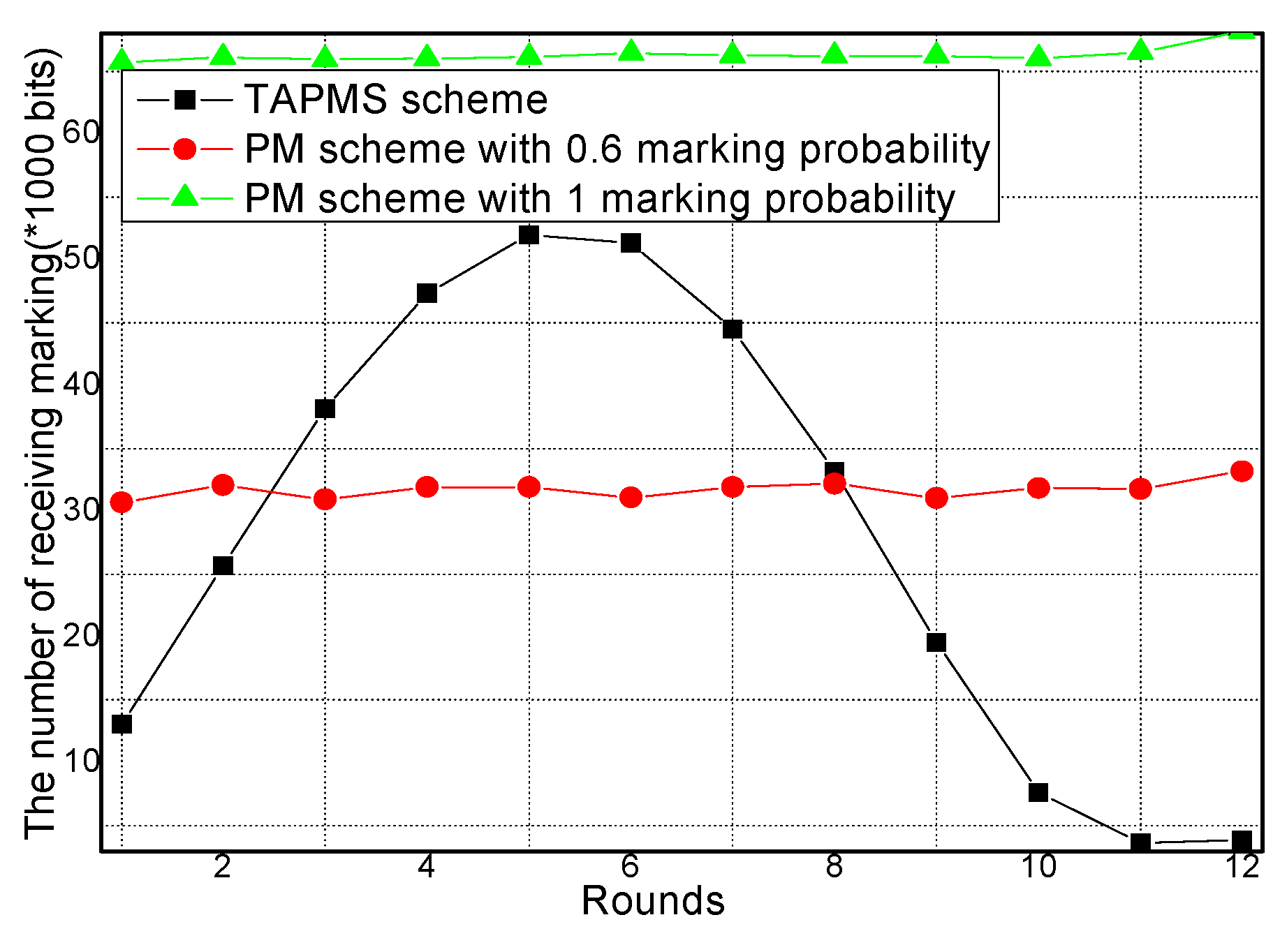
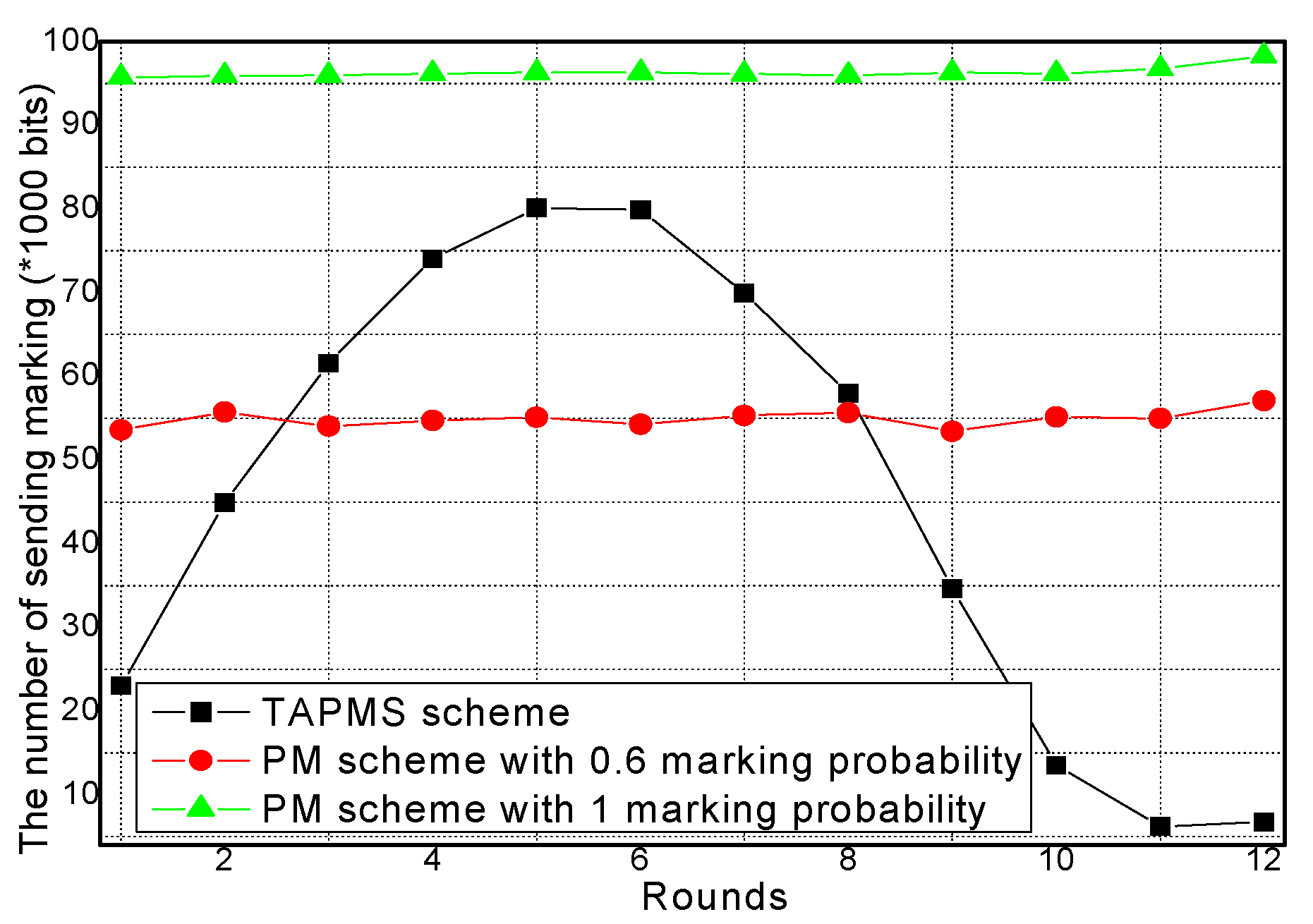
- The theoretical analysis and experimental analysis demonstrate that traceback time and lifetime in TAPMS are both improved. The results show that the number of total marking tuples can be reduced by 13.20%–73.70% in the TAPMS scheme compared with that in the probability marking (PM) scheme with marking probability equal to 1 to improve network lifetime, and the traceback time can be reduced by more than 80%.
2. Related Work
3. System Model
3.1. Network Model
- (1)
- We consider a WSN consisting of homogeneous static sensor nodes and Sink node , nodes deployed over a 2-D circular surveillance field, and a network radius of . Sink node is the center of the network. The communication radius of each sensor node is . The network model is shown in Figure 1. The nodes have different trust levels, where most nodes are high trust nodes and a few nodes are low trust nodes. The node and node are compromised nodes with low trust in Figure 1. If the marking tuples are stored in those nodes, the marking tuples would be dropped with high probability. The marking tuples are dropped with low probability if the node trust level is high. The energy of each sensor node is limited, and the energy of the sink is infinite. Sensor nodes monitor their surroundings, and once an event is generated, nodes report to the base station through multi-hop transmissions [12,13].
- (2)
- We consider the following attack scenario: a compromised node used to launch a false data injection attack to exhaust network resources is designated as the attack or source node [20,23,24,28]. Nodes mark packets with a certain probability ; in the event of an attack, the system can locate a malicious sources through those information marks, which is similar to cyber-forensics technologies [20,21,22,23,24,28].
- (3)
- The sink can assess the trust of each node based on the marking tuples.
3.2. Energy Consumption Model and Related Definitions
3.3. Problem Statement
- (1)
- Network lifetime is to be maximized.The basic goal of this application requirement is to maximize network lifetime. Network lifetime can be defined as the elapsed time until the first node dies [7,14,33,34]. The death of the first node can affect the connectivity and coverage of the network severely, preventing the network from playing a proper role. The end-to-end connectivity refers to the correct transmission from one node to the final destination, which characterizes the ability of every node to report to the fusion center, thus it is important to ensure a high probability of connectivity [35]. Hence, the definition of network lifetime in this paper is consistent with references [7,14] and is defined as the time elapsed until the first sensor node in the network depletes its energy. We denote as the energy consumption of node in one round. is the total energy of node . The formula of maximizing network lifetime can be expressed as follows:
- (2)
- The scheme can locate attack sources quickly while defending against attacks.The spent time for determining a malicious source is evaluated by the amount of marking information stored in attack paths. Obviously, in the process of reconstructing the attack paths, if the traceback scheme marks many data packets in the attack path, the system can collect much marking information quickly; then, the malicious node can be rapidly determined. Therefore, means to maximize marking information. denotes the amount of marking information of node in a unit time; thus:
- (3)
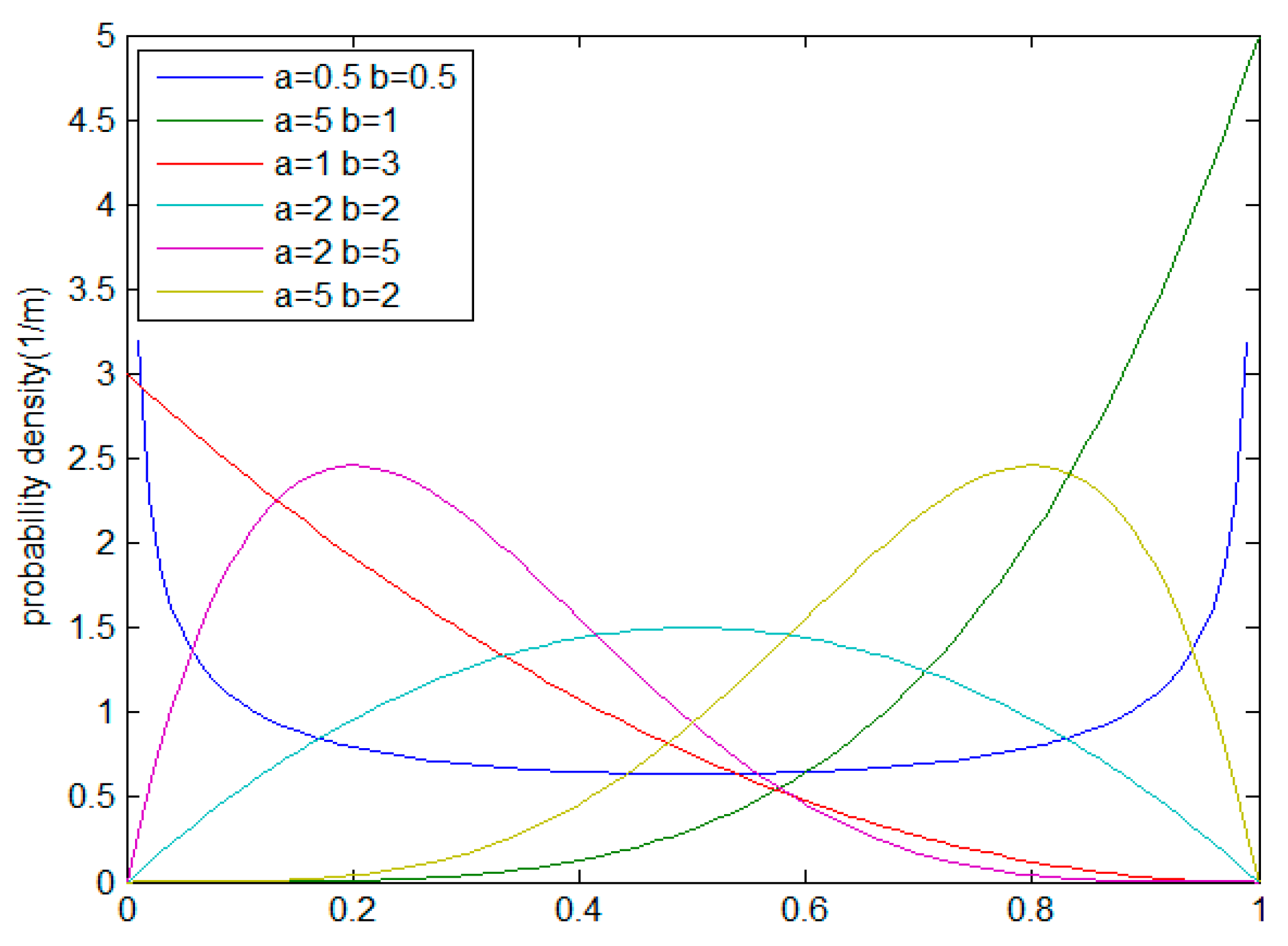
- The average credibility of nodes, which is used to store marking tuples, is to be maximized.When the produced data packet is sent to the sink, the marking information of nodes can be added to the data packet. However, when the length of marking information reaches a certain value, the marking information can be stored in nodes. If marking tuples are stored in a malicious node, those marking tuples can be dropped or tampered with. Therefore, one goal of the TAPMS scheme is to maximize the average trust of nodes that store marking tuples. Consider that the trust of node is . The number of marking tuples stored in node is , as shown in Equation (5):In summary, the optimization purpose of the scheme in this paper is:
4. Trust-Based Adaptive Probability Marking and Storage Traceback Scheme
4.1. Research on Motivation
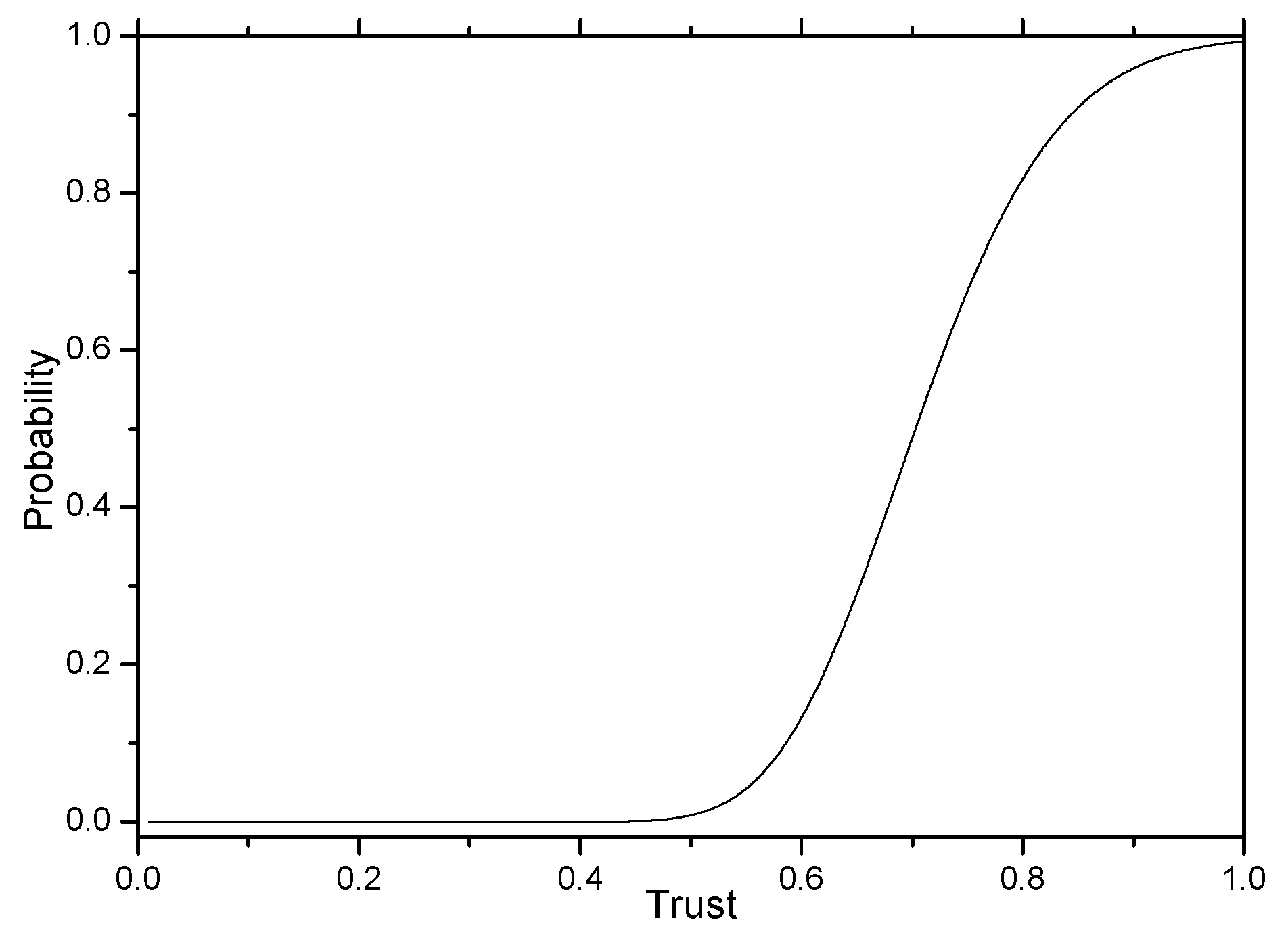
4.2. Trust-Based Adaptive Marking Probability Approach
| Algorithm 1: The adaptive probability marking traceback approach |
Initialize: Let the network’s trust be 0.5;
|
4.3. Trusted Storage Approach
| Algorithm 2: The adaptive logging approach |
|
5. Performance Analysis and Optimization
5.1. Energy Consumption and Network Lifetime
5.2. Detection Probability Analysis
5.3. Average Trust of Storage
6. Experimental Results
6.1. Marking Probability and the Number of Receiving and Sending Marking Tuples
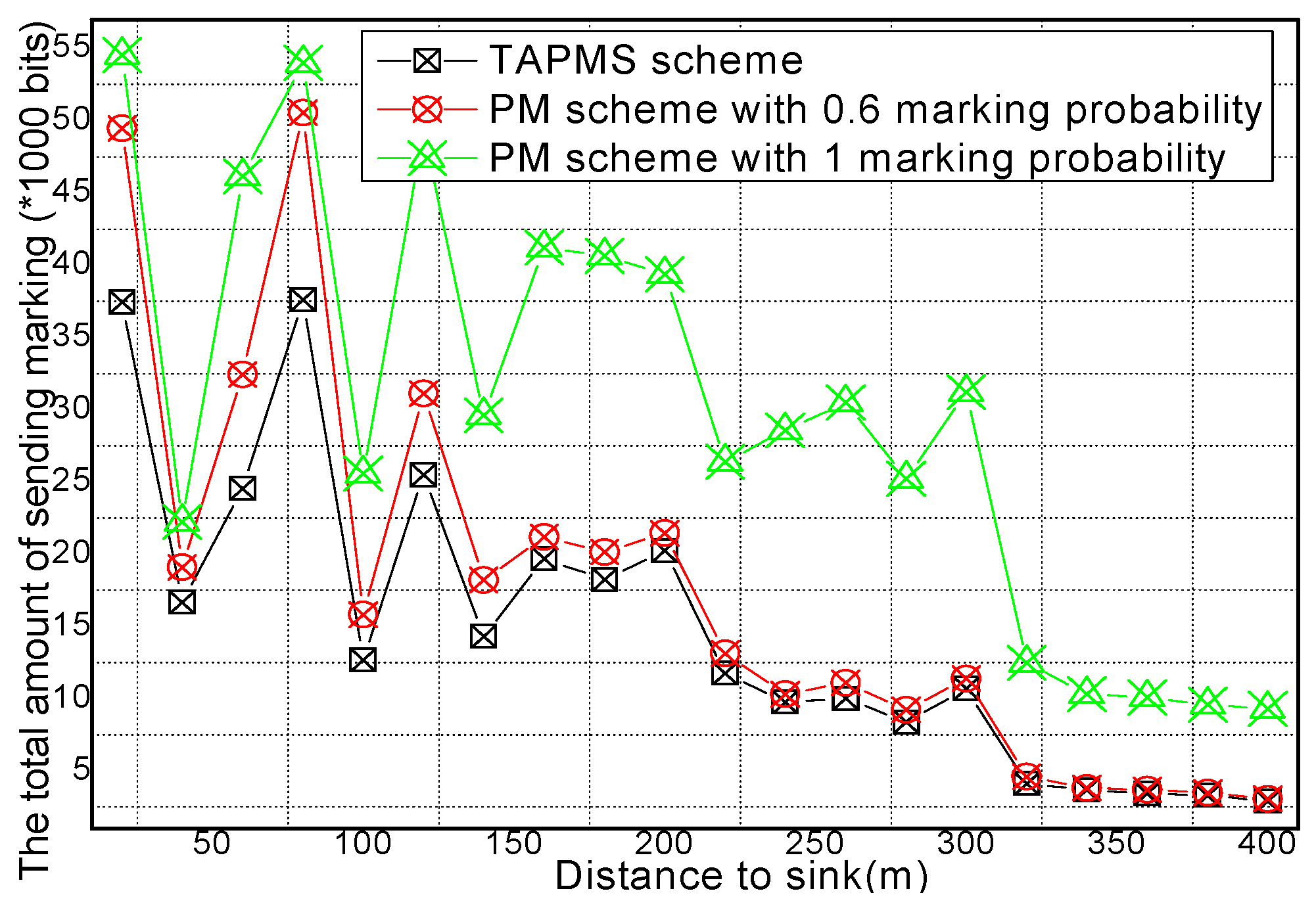
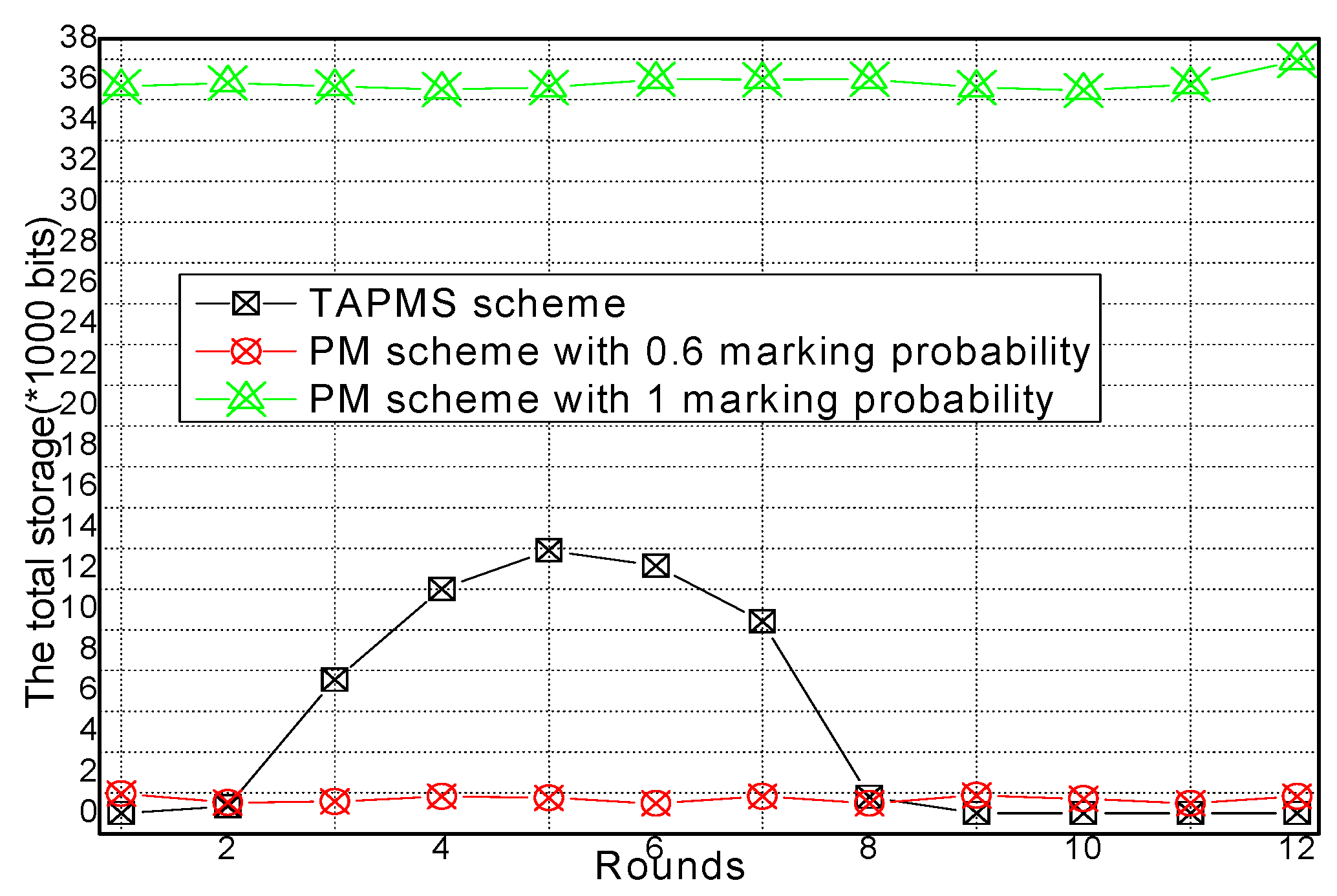
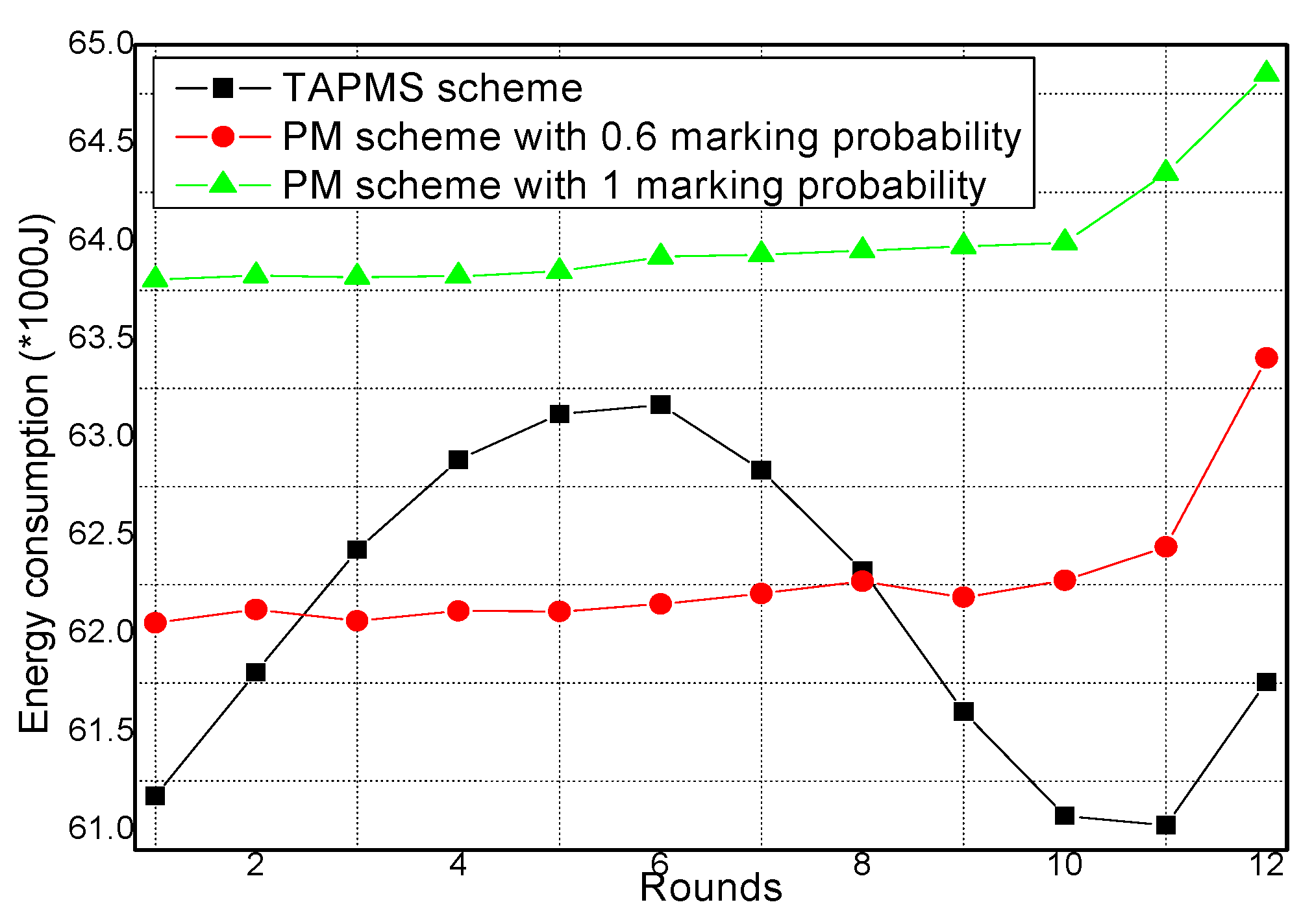
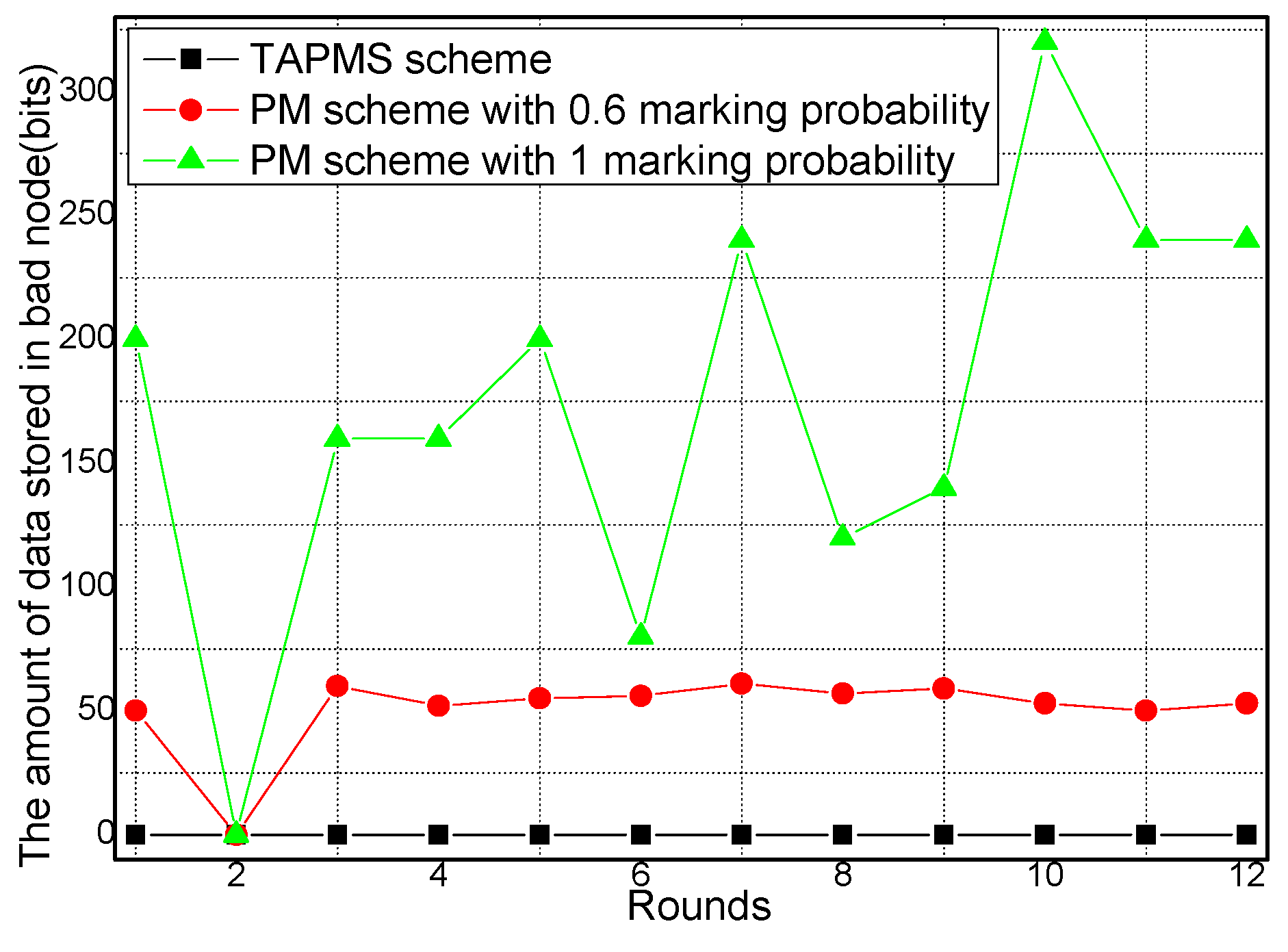
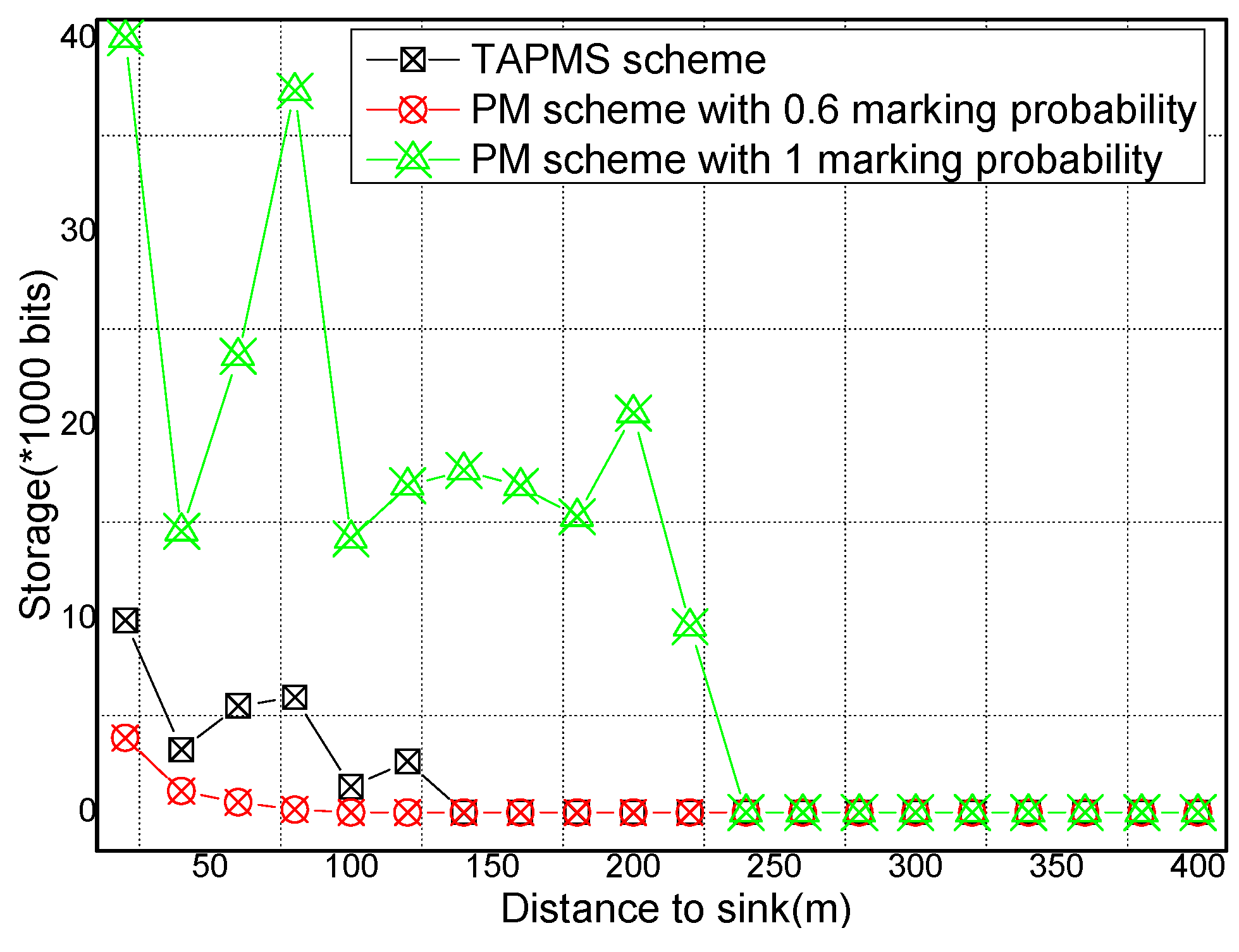
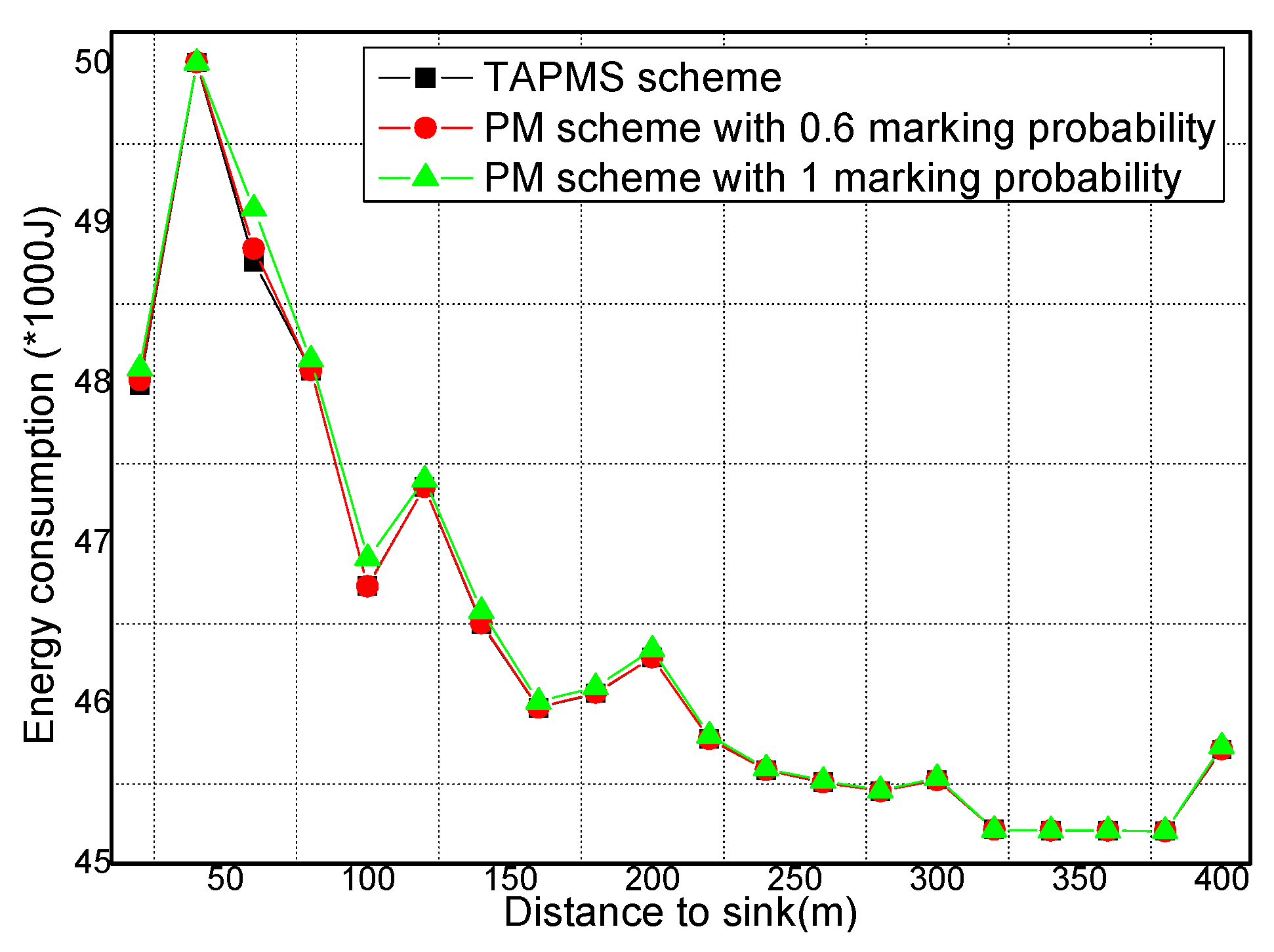
6.2. Number of Stored Marking Tuples and Energy Consumption
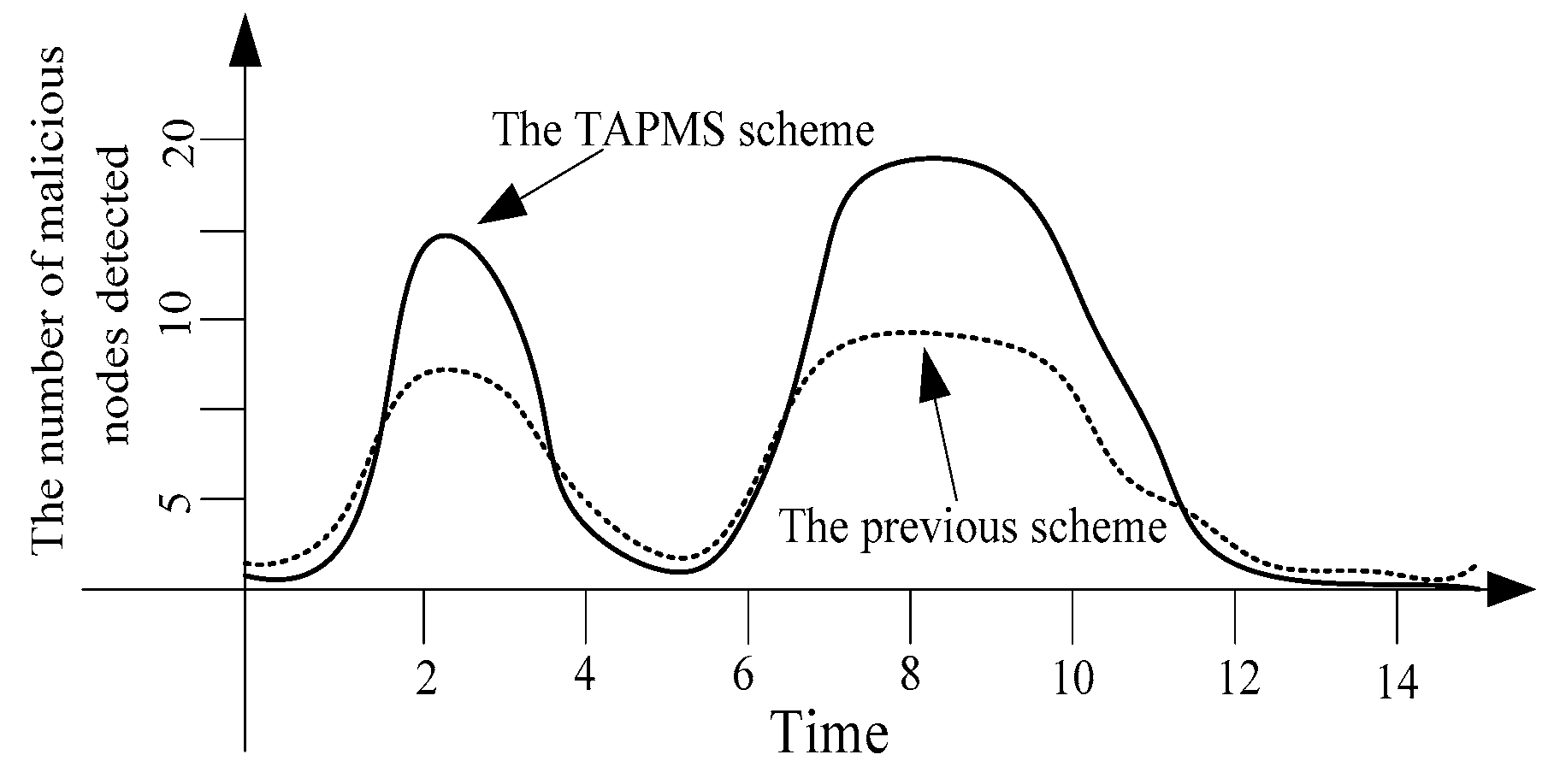
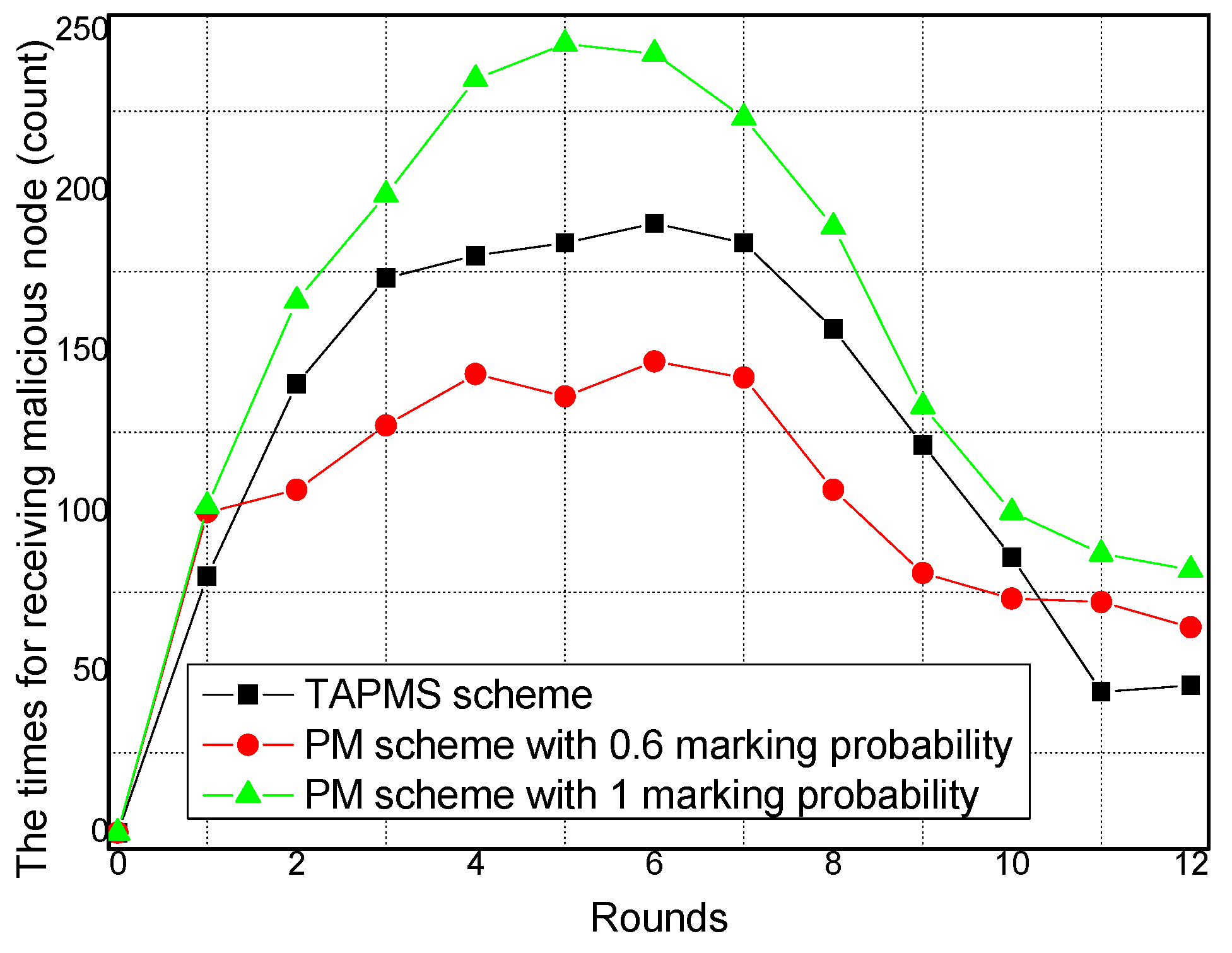
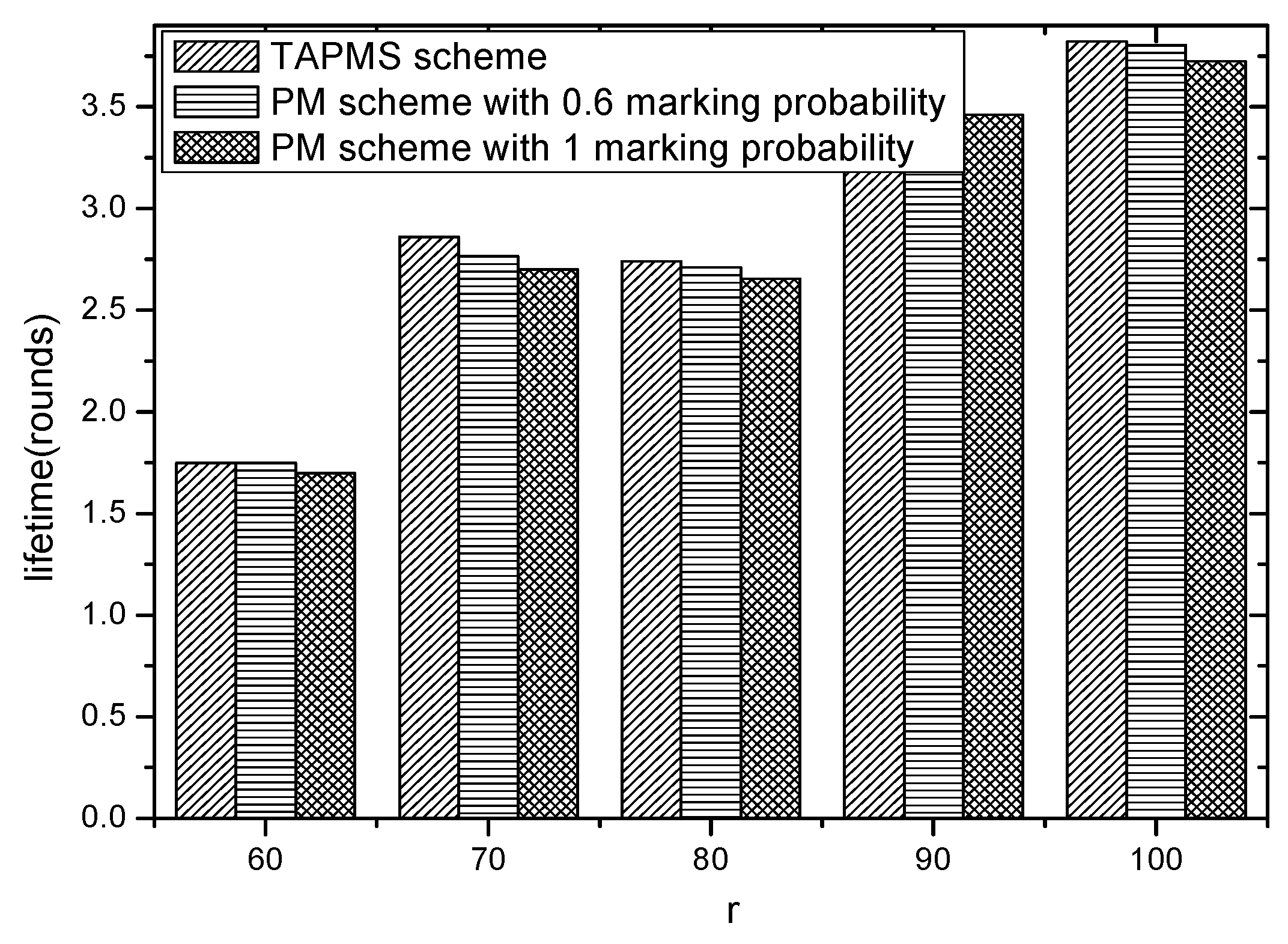
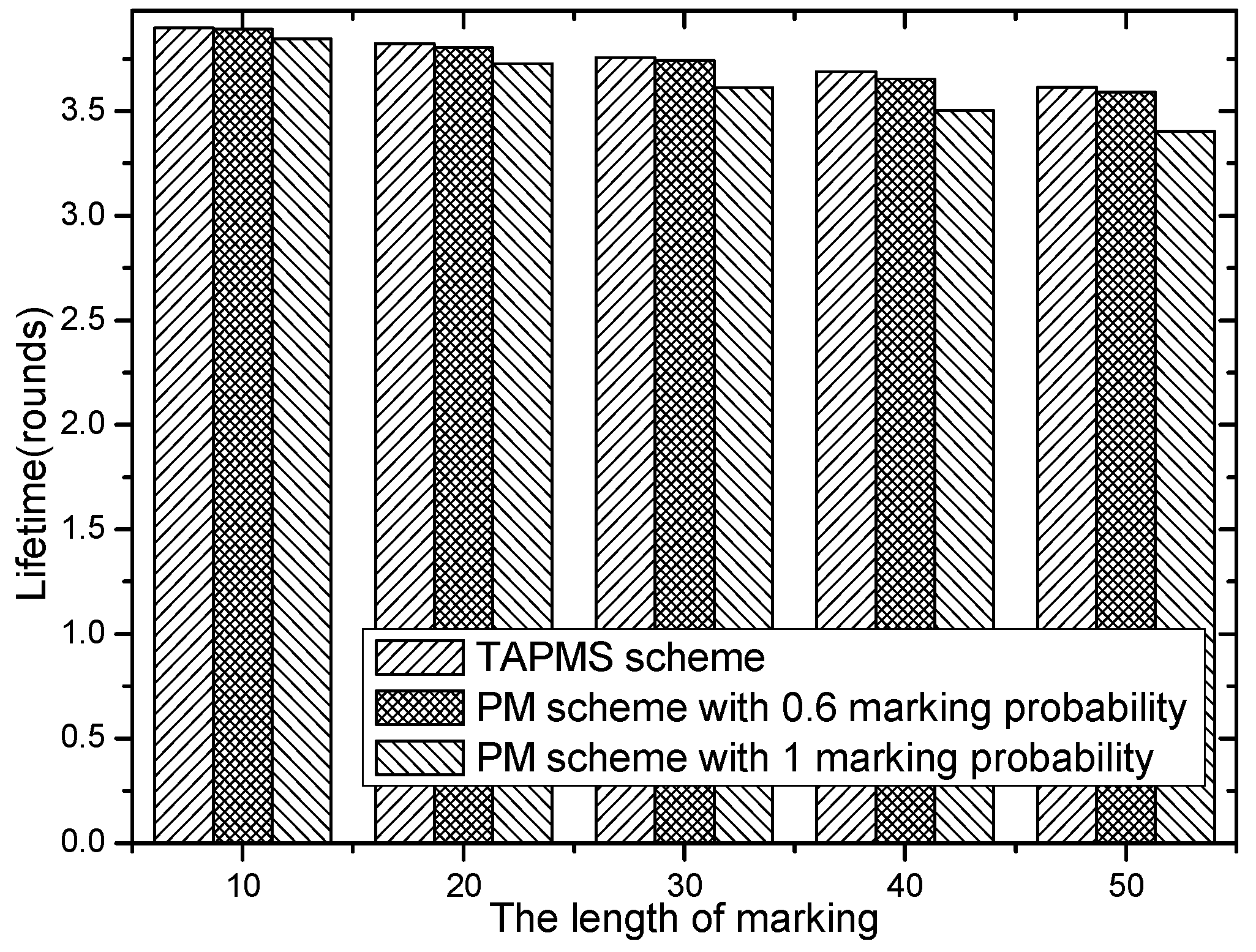
6.3. Security and Lifetime Performance
7. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Dai, H.; Chen, G.; Wang, C.; Wang, S.; Wu, X.; Wu, F. Quality of energy provisioning for wireless power transfer. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 527–537. [Google Scholar] [CrossRef]
- Yang, L.; Cao, J.; Zhu, W.; Tang, S. Accurate and Efficient Object Tracking based on Passive RFID. IEEE Trans. Mob. Comput. 2015, 14, 2188–2200. [Google Scholar] [CrossRef]
- Yang, L.; Cao, J.; Cheng, H.; Ji, Y. Multi-User Computation Partitioning for Latency Sensitive Mobile Cloud Applications. IEEE Trans. Comput. 2015, 64, 2253–2266. [Google Scholar] [CrossRef]
- Verma, V.K.; Singh, S.; Pathak, N.P. Impact of malicious servers over trust and reputation models in wireless sensor networks. Int. J. Electron. 2016, 103, 530–540. [Google Scholar] [CrossRef]
- Dai, H.; Wu, X.; Xu, L.; Wu, F.; He, S.; Chen, G. Practical scheduling for stochastic event capture in energy harvesting sensor networks. Int. J. Sens. Netw. 2015, 18, 85–100. [Google Scholar] [CrossRef]
- Liu, X.; Dong, M.; Ota, K.; Hung, P.; Liu, A. Service Pricing Decision in Cyber-Physical Systems: Insights from Game Theory. IEEE Trans. Serv. Comput. 2015. [Google Scholar] [CrossRef]
- Chen, L.; Lu, R.; Cao, Z.; AlHarbi, K.; Lin, X. MuDA: Multifunctional data aggregation in privacy-preserving smart grid communications. Peer-to-Peer Netw. Appl. 2015, 8, 777–792. [Google Scholar] [CrossRef]
- Huang, G.; Chen, D.; Liu, X. A Node Deployment Strategy for Blindness Avoiding in Wireless Sensor Networks. IEEE Commun. Lett. 2015, 19, 1005–1008. [Google Scholar] [CrossRef]
- Liu, X. A Deployment Strategy for Multiple Types of Requirements in Wireless Sensor Networks. IEEE Trans. Cybernet. 2015, 45, 2364–2376. [Google Scholar] [CrossRef] [PubMed]
- Hu, Y.; Liu, A. An efficient heuristic subtraction deployment strategy to guarantee quality of event detection for WSNs. Comput. J. 2015, 58, 1747–1762. [Google Scholar] [CrossRef]
- Xiao, B.; Zhang, S.; Bu, K. Unknown Tag Identification in Large RFID Systems: An Efficient and Complete Solution. IEEE Trans. Parallel Distrib. Syst. 2015, 26, 1775–1788. [Google Scholar]
- Liang, J.; Li, T. A Maximum Lifetime Algorithm for Data Gathering Without Aggregation in Wireless Sensor Networks. Appl. Math. 2013, 7, 1705–1719. [Google Scholar] [CrossRef]
- Liu, X.; Ota, K.; Liu, A.; Chen, Z. An incentive game based evolutionary model for crowd sensing networks. Peer-to-Peer Netw. Appl. 2015. [Google Scholar] [CrossRef]
- Dong, M.; Liu, X.; Qian, Z.; Liu, A. QoE-ensured price competition model for emerging mobile networks. IEEE Wirel. Commun. 2015, 22, 50–57. [Google Scholar] [CrossRef]
- Jiang, L.; Liu, A.; Hu, Y.; Chen, Z. Lifetime maximization through dynamic ring-based routing scheme for correlated data collecting in WSNs. Comput. Electr. Eng. 2015, 41, 191–215. [Google Scholar] [CrossRef]
- Liu, A.; Dong, M.; Ota, K.; Long, J. PHACK: An Efficient Scheme for Selective Forwarding Attack Detection in WSNs. Sensors 2015, 15, 30942–30963. [Google Scholar] [CrossRef] [PubMed]
- Bysani, L.K.; Turuk, A.K. A Survey on Selective Forwarding Attack in Wireless Sensor. In Proceedings of the International Conference on Networks, Devices and Communications (ICDeCom), Ranchi, India, 24–25 February 2011; pp. 1–5.
- Lu, R.; Lin, X.; Zhu, H.; Liang, X.; Shen, X. BECAN: A bandwidth-efficient cooperative authentication scheme for filtering injected false data in wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2012, 23, 32–43. [Google Scholar]
- Zheng, Z.; Liu, A.; Cai, L.; Chen, Z.; Shen, X. Energy and memory efficient clone detection in wireless sensor networks. IEEE Trans. Mob. Comput. 2015. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, A.; He, S. A novel joint logging and migrating traceback scheme for achieving low storage requirement and long lifetime in WSNs. AEU Int. J. Electron. Commun. 2015, 69, 1464–1482. [Google Scholar] [CrossRef]
- Gui, J.; Zhou, K. Flexible Adjustments Between Energy and Capacity for Topology Control in Heterogeneous Wireless Multi-Hop Networks. J. Netw. Syst. Manag. 2016. [Google Scholar] [CrossRef]
- Alam, S.M.; Fahmy, S. A practical approach for provenance transmission in wireless sensor networks. Ad Hoc Netw. 2014, 16, 28–45. [Google Scholar] [CrossRef]
- Cheng, B.C.; Chen, H.; Li, Y.J.; Tseng, R.Y. A packet marking with fair probability distribution function for minimizing the convergence time in wireless sensor networks. Comput. Commun. 2008, 31, 4352–4359. [Google Scholar] [CrossRef]
- Siddiqui, M.S.; Obaid Amin, S.; Hong, C.S. Hop-by-hop traceback in wireless sensor networks. IEEE Commun. Lett. 2012, 16, 242–245. [Google Scholar] [CrossRef]
- Mekikis, P.V.; Lalos, A.; Antonopoulos, A.; Alonso, L.; Verikoukis, C. Wireless Energy Harvesting in Two-Way Network Coded Cooperative Communications: A Stochastic Approach for Large Scale Networks. IEEE Commun. Lett. 2014, 18, 1011–1014. [Google Scholar] [CrossRef]
- Mekikis, P.V.; Antonopoulos, A.; Kartsakli, E.; Lalos, A.S.; Alonso, L.; Verikoukis, C. Information Exchange in Randomly Deployed Dense WSNs with Wireless Energy Harvesting Capabilities. IEEE Trans. Wirel. Commun. 2016. [Google Scholar] [CrossRef]
- Serra, J.; Serra, J.; Pubill, D.; Antonopoulos, A.; Verikoukis, C. Smart HVAC Control in IoT: Energy Consumption Minimization with User Comfort Constraints. Sci. World J. 2014. [Google Scholar] [CrossRef] [PubMed]
- Xu, J.; Zhou, X.; Yang, F. Traceback in wireless sensor networks with packet marking and logging. Front. Comput. Sci. China 2011, 5, 308–315. [Google Scholar] [CrossRef]
- Zhang, Y.; He, S.; Chen, J. Data Gathering Optimization by Dynamic Sensing and Routing in Rechargeable Sensor Networks. IEEE/ACM Trans. Netw. 2015. [Google Scholar] [CrossRef]
- He, S.; Chen, J.; Jiang, F.; Yau, D.K.; Xing, G.; Sun, Y. Energy provisioning in wireless rechargeable sensor networks. IEEE Trans. Mob. Comput. 2013, 12, 1931–1942. [Google Scholar] [CrossRef]
- Hu, Y.; Dong, M.; Ota, K.; Liu, A. Mobile Target Detection in Wireless Sensor Networks with Adjustable Sensing Frequency. IEEE Syst. J. 2014. [Google Scholar] [CrossRef]
- Yang, Q.; He, S.; Li, J.; Chen, J.; Sun, Y. Energy-efficient probabilistic area coverage in wireless sensor networks. IEEE Trans. Veh. Technol. 2015, 64, 367–377. [Google Scholar] [CrossRef]
- Long, J.; Liu, A.; Dong, M.; Li, Z. An energy-efficient and sink-location privacy enhanced scheme for WSNs through ring based routing. J. Parallel Distrib. Comput. 2015, 81, 47–65. [Google Scholar] [CrossRef]
- Dong, M.; Ota, K.; Liu, A.; Guo, M. Joint Optimization of Lifetime and Transport Delay under Reliability Constraint Wireless Sensor Networks. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 225–236. [Google Scholar] [CrossRef]
- Mekikis, P.V.; Kartsakli, E.; Lalos, A.S.; Antonopoulos, A.; Alonso, L.; Verikoukis, C. Connectivity of large-scale WSNs in fading environments under different routing mechanisms. In Proceedings of the 2015 IEEE International Conference on Communications (ICC), London, UK, 8–12 June 2015; pp. 6553–6558.
- Linhart, J.M. Algorithm 885: Computing the logarithm of the normal distribution. ACM Trans. Math. Softw. (TOMS) 2008, 35. [Google Scholar] [CrossRef]
- Liu, Y.; Liu, A.; Chen, Z. Analysis and Improvement of Send-and-Wait Automatic Repeat-Request protocols for Wireless Sensor Networks. Wirel. Person. Commun. 2015, 81, 923–959. [Google Scholar] [CrossRef]
- Nigmatullin, R.R.; Osokin, S.I.; Awrejcewicz, J.; Wasilewski, G.; Kudra, G. The fluctuation spectroscopy based on the scaling properties of beta-distribution: Analysis of triple pendulum data. Mech. Syst. Signal Process. 2015, 52, 278–292. [Google Scholar] [CrossRef]
- Varga, A. The OMNET++ Discrete Event Simulation System, Version 4.1. Available online: http://www.omnetpp.org (accessed on 24 March 2016).






| Parameter | Value |
|---|---|
| Threshold distance (d0) (m) | 87 |
| Sensing range rs (m) | 15 |
| Eelec (nJ/bit) | 50 |
| εfs (pJ/bit/m2) | 10 |
| εamp (pJ/bit/m4) | 0.0013 |
| Initial energy (J) | 0.5 |
| Parameter | State |
|---|---|
| Baseline marking probability (BMP) | |
| Trust of node in time slot | |
| Average trust of network in the last time | |
| Baseline trust | |
| Max trust | |
| Average marking probability of the entire network | |
| Number of marking tuples | |
| Optimal value of to maximize its payoff | |
| Trust threshold | |
| Reliability of node | |
| Trust of node | |
| Constant |
© 2016 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons by Attribution (CC-BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, A.; Liu, X.; Long, J. A Trust-Based Adaptive Probability Marking and Storage Traceback Scheme for WSNs. Sensors 2016, 16, 451. https://doi.org/10.3390/s16040451
Liu A, Liu X, Long J. A Trust-Based Adaptive Probability Marking and Storage Traceback Scheme for WSNs. Sensors. 2016; 16(4):451. https://doi.org/10.3390/s16040451
Chicago/Turabian StyleLiu, Anfeng, Xiao Liu, and Jun Long. 2016. "A Trust-Based Adaptive Probability Marking and Storage Traceback Scheme for WSNs" Sensors 16, no. 4: 451. https://doi.org/10.3390/s16040451
APA StyleLiu, A., Liu, X., & Long, J. (2016). A Trust-Based Adaptive Probability Marking and Storage Traceback Scheme for WSNs. Sensors, 16(4), 451. https://doi.org/10.3390/s16040451







