4.1. Problem Formulation
Each sensor node has a limited communication ability; therefore, without pre-installed relay nodes, data acquired by sensor nodes may not be able to be piggybacked to the base station. In this section, we try to give the optimal scheme for relay nodes’ placement with respect to minimum overall power usage. Without losing the rigorous nature of mathematics, we resort to the Lagrange dual problem and KKT conditions in order to figure out the closed-form solution.
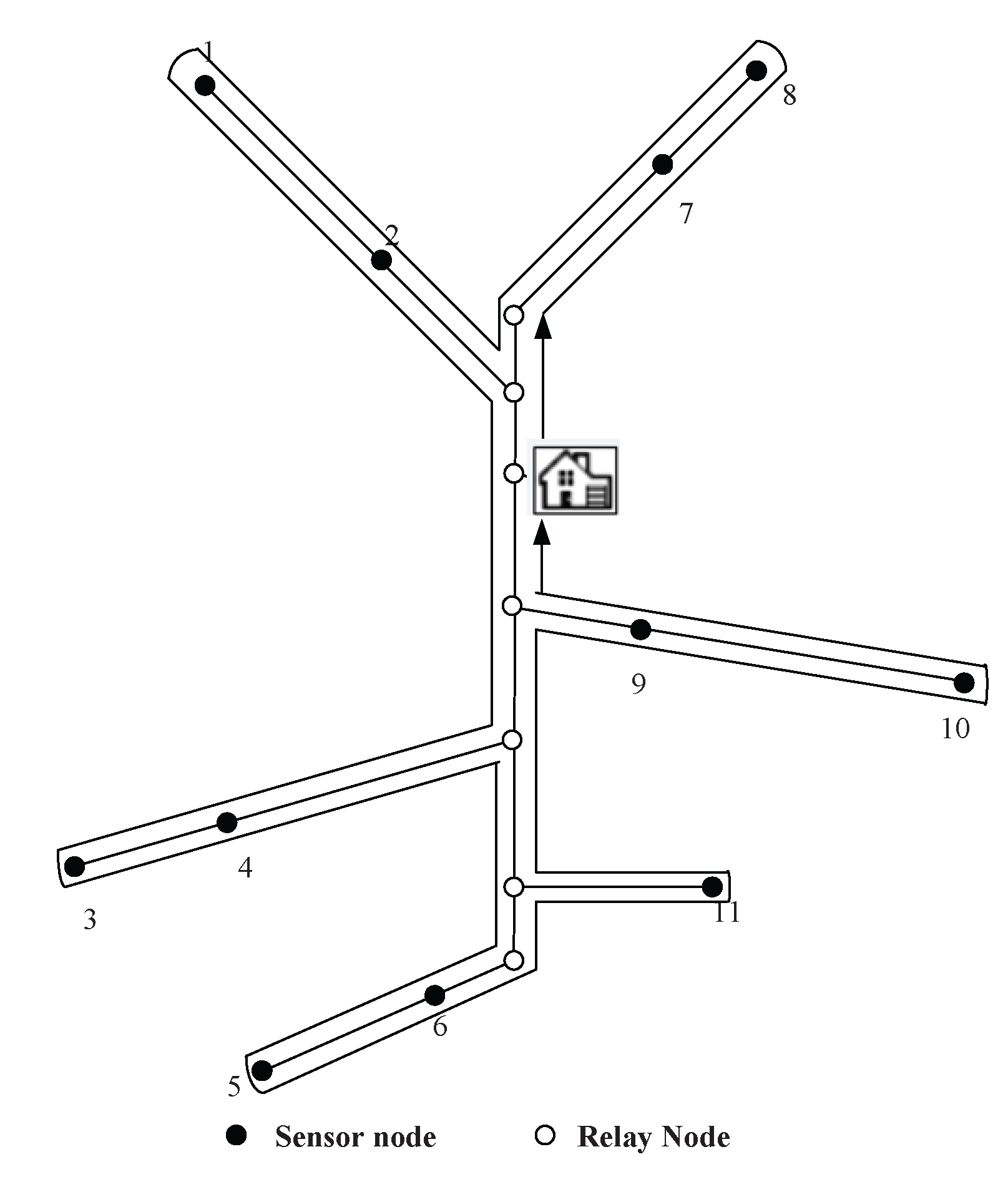
Before we step forward into the problem formulation, please allow us to introduce some notations used here. Since the networking issues among all layers are similar to each other, without any loss of generality, we take one layer of the mine for example. Since most coal mines are composed of tunnels, the topological structure of sensor networks of coal mines is somewhat linear. The optimization problem we formulated in this section is aimed to minimize the energy consumption of sensor and relay nodes along a linear structure. Assume that the distance between two sensor nodes is
L meters. The communication range of each sensor node is
R meters, and
R <
L. For the successful communication between these two sensor nodes, a certain amount of relay sensor nodes should be placed between them. As shown in
Figure 2, there are
n relay nodes placed successively at
, and each of these sensor nodes has a communication range of
R meters. The positions of the two sensor nodes are denoted as
and
. We assume that the relay nodes are only reliable for receiving and forwarding data in the following discussion.
Figure 2.
A sketch map for sensor nodes and relay nodes.
Figure 2.
A sketch map for sensor nodes and relay nodes.
The power usage of each node is composed of transmitting, receiving, processing and sensing data. Since the last two parts are relatively smaller compared to the first two factors and are independent of the optimization problem we discuss below, therefore, we omit the last two factors in the formulation of our optimization problem. The power usage of a node when transmitting data can be modeled as:
where
is the transmitting power used by node
i at time instance
t,
is the transmitting distance,
k is often chosen between two and four and
is the transmitting data rate of node
i at time instance
t. The symbols
and
are power-related constants.
The receiving power used by node
i can be modeled as:
where
is the power used for receiving data at time instance
t,
is the receiving data rate and
ρ is the power-related constant.
As shown in
Figure 2, there are two sensor nodes and
n relay nodes. By the definition of
given in the previous section, we have the following equation,
where
is the distance between two successive sensor nodes.
Then, we formulate the following optimization problem, OPT-1:
In this optimization problem, our objective is to minimize the energy used for transmitting data among sensor nodes and the corresponding relay nodes. The optimization variables are the number of relaying nodes n, which is an integer value, and the distance between two nodes . The optimization constants are the power-related constants, i.e., , and ρ, the transmitting data rate of the first sensor node, .
Since all nodes should communicate properly, we have . After solving this problem, we are able to obtain the optimal number and placement for relay nodes.
4.2. Solution to OPT-1
To solve this optimization problem, we might use the method of the Lagrange multiplier. However, the mathematical correctness and completeness of this method can only be ensured when finding extreme points for problems with equality constraints. The optimization problem formulated in
Section 4.1 obviously has inequality constraints and an integer optimization variable. Therefore, the method of the Lagrange multiplier may not be applied easily without any criticism. In order to solve this problem, alternatively, we firstly divide OPT-1 into two sub-optimization problems. Secondly, we form the Lagrange dual problem of the first one and prove the strong duality of the prime and dual problems. Eventually, we combine these two optimization problems together to get the optimal number and placement for relay nodes.
By substituting the objective function with Equations (1) and (2), we have:
The objective function can be further reshaped as:
where
and
are the data that the i-th node transmits and receives during the time period
τ. For the data integrity, during the time period
τ, we have the following chain equation,
This chain equation indicates that during time period τ, the data transmitted by the i-th node are equal to the data received by it (in this article, we do not take into consideration the data aggregation and data compression at each node).
After expanding the objective function, we have:
The Constraints (1) and (2) are omitted here in that they have been already plugged into the objective function. The optimization variables are the number of relay nodes n and the distance between two successive nodes . To solve this optimization problem, we firstly divide it into two sub-optimization problems.
For a given number
n, we can firstly solve the following optimization problem OPT-2,
It is not difficult to verify that this optimization problem is a convex problem since the objective function and all of the constraints are convex.
Then, the Lagrangian of this prime optimization problem is:
The Lagrangian dual function is defined as:
where the
stands for the infimum over all
.
The Lagrange dual problem of the prime problem is:
In general cases, the optimal value of the dual problem always provides a loose lower bound of the optimal value of the prime one. However, in this case, we can prove that the strong duality holds for the prime and dual problems, that is the optimal values of the prime and dual problem are identical.
Theorem 1. The strong duality of the prime optimization problem OPT-2 and its Lagrange dual problem holds, i.e., the optimal values of these two problem are identical.
The proof of this theorem is not trivial, and we leave it to the Appendix section for a better intelligibility. The next theorem will show a necessary condition for achieving the optimality of OPT-1.
Theorem 2. The optimality of OPT-1 can be achieved only if relay nodes are placed at the equal partition points between two sensor nodes.
Proof. Since the prime optimization problem OPT-2 is a convex problem and the strong duality holds, we can use the KKT conditions to figure out the optimal value of both the prime and dual optimization problems.
The KKT conditions for OPT-2 for a given n are listed below:
After solving this set of equations, we can draw the conclusion that,
which means that relay nodes must be put at the equal partition points between two sensor nodes to get the minimum overall energy consumption, since the first term of the objective function of OPT-1 is constant given the value of
n.
The next step is to decide how many relay nodes should be installed. Since relay nodes should be placed at the equal partition points, the optimization problem OPT-1 can be rewritten as the following optimization problem, denoted as OPT-3,
The variable
n of this optimization problem must have an integer value. However, we can first take the unconstrained problem into consideration,
i.e.,
By calculating the second derivative of the objective function, we could find out that this function is strict convex when
is greater than zero. Therefore, this problem can be solved by calculating the stationary points of the objective function,
i.e., if any stationary point exists when
n is greater than zero, it also must be the minimum point. In order to calculate the stationary point, we first calculate the first derivative of the objective function. We have:
From the property of convex functions, we have the following conclusions:
If is an integer and , then ;
If , but is not endowed with an integer value, then the value of n is chosen from and ;
If , then the value of n is .
Next, the correctness of solving OPT-1 via the given procedure can be validated by contradiction.
Assume that the value n and the relay nodes’ placement is not optimal, i.e., there exist another value and a relay nodes’ placement method that lead to a smaller objective value of OPT-1. However, for a given , due to the result of OPT-2, the objective function can only be minimized by placing relay nodes at the equal partition points. Then, OPT-1 is transformed into OPT-3. Since the value of n is obtained by solving OPT-3, the objective function value must be smaller than that acquired by , which causes the contradiction. Therefore, the optimality of OPT-1 can be ensured when following the given solution procedure. ☐