1. Introduction
Underwater wireless sensor networks (U-WSN) are a promising technology to deal with applications that require offshore monitoring, e.g., environmental quality control, seismic analysis, oilfield monitoring and sea robotics [
1]. The wireless underwater communication presents, however, a challenging task that needs to be approached depending on the application under consideration. In these two-part papers, we focus on the use of U-WSN in shallow waters.
There are three main technologies that can be considered for underwater wireless communications, namely acoustic, optical and radio. Each of them presents its own benefits and drawbacks and can be used in different scenarios [
2,
3].
For instance, acoustic communications are valid for medium range distances (several km [
4]), but have limited bandwidth and provide poor performance in shallow waters. Acoustic systems near ports or the coastline are affected by multiple sources of noise, such as industries or nearby boats. Furthermore, multi-path associated with different transmission speeds, reverberation and ambient noise also degrade the communication performance.
Optical communications present ultra-high bandwidth over short distances, but are susceptible to turbidity, particles or marine fouling. Ambient light is another adverse effect that can degrade the performance of this technology in shallow waters [
5]. Furthermore, this technology currently requires directional communication, as omni-directional wireless transmissions are under research [
6].
Electromagnetic (EM) communications in the low frequency range (i.e., kHz) are not affected by ambient noise nor light and can be used in omni-directional or directional deployments. Thus, it becomes a worth-studying option to establish communication between nodes in shallow waters, such as in lakes, bays, harbors and areas close to the sea shores.
In shallow waters, the medium presents two alternative propagation mechanisms for EM waves: the water-to-air and water-to-seafloor interfaces, e.g., [
7,
8]. Since these interfaces present less conductivity than seawater, depending on the relative position of the transceivers and receivers with regards to the surface and seafloor, the communication range of the EM communication in shallow water is usually larger than over a homogeneous medium.
In the first part of this paper [
9], we performed measurements and characterized the underwater channel for shallow waters in a real setup, described the measurement testbed, provided channel measurements at different frequencies and distances and verified the validity of the results using an EM model of the channel and simulations. In this second part, we focus on analyzing the viability of U-WSN using the mentioned EM propagation mechanisms for localization applications. Although the water medium still has a strong attenuation in the low frequency range, we show that reliable communications are possible in the range of tens of meters, making U-WSN viable for deployment. The research described in this paper is part of a national research project named UnderWorld [
10], in which all authors are involved.
Our main contribution in this publication is to use the channel characterization from [
9,
11,
12] to show that it is possible to use EM-based U-WSN for localization and monitoring applications. First, we introduce some application requirements for the deployment of a U-WSN, which include low connectivity, low data rate and robustness against packet loss; Then, we consider two localization problems: self-localization for the nodes that have been randomly located during the network deployment and localization of an underwater unmanned vehicle (UUV) for aiding navigation. We propose new and existing localization algorithms that solve these problems and study them under the specific restrictions of underwater radio networks, which include low connectivity, a low data rate and considerable packet loss. Once we understand the requirements of the proposed algorithms, we simulate a complete U-WSN on a prototypical scenario and study the influence of different parameters. In particular, we consider alternative MAC protocols (unicast with ACK and synchronous and asynchronous broadcast) for node-to-node communications (as required for the proposed localization algorithms) and a standard routing protocol for external monitoring. The network simulations are realistic, in the sense that they include multiple effects that affect the overall performance of the network, including propagation impairments (e.g., noise, interference), radio parameters (e.g., modulation scheme, bandwidth, transmit power) and hardware limitations (e.g., clock drift, transmission buffer).
We perform the network simulations in Castalia [
13]. Castalia is a simulator for wireless sensor networks based on the OMNeT++ platform [
14] that offers realistic wireless channel and radio models and realistic node behavior. The main reasons for choosing Castalia are its level of realism, speed and flexibility. The speed is achieved because all of the modules are written in C++. The flexibility is at the cost of having no graphical user interface. Indeed, Castalia is a command line simulator, where scenarios and settings are defined through external configuration files. The results are also given in text files, but they can be accessed with convenient parser scripts.
The paper is structured as follows. In
Section 2, we propose a parametric model of the underwater channel characterized in Part I of this paper [
9], so that it can be efficiently simulated. In
Section 3, we introduce two algorithms for localization applications and discuss the communication requirements for the network in these scenarios. In particular, in
Section 3.1, a self-positioning algorithm is proposed; while
Section 3.2 presents a target localization method for navigation aid. In
Section 4, we describe the simulations of a complete U-WSN and obtain some guidelines on the communication schemes for the deployment of a network that addresses the proposed applications.
2. Parametrization of the Communication Channel
We consider a U-WSN consisting of
N nodes, and we refer to the set of nodes as
. We performed real measurements in the underwater medium to characterize the channel, where the specific procedure is described in Part I of this paper, presented in [
9].
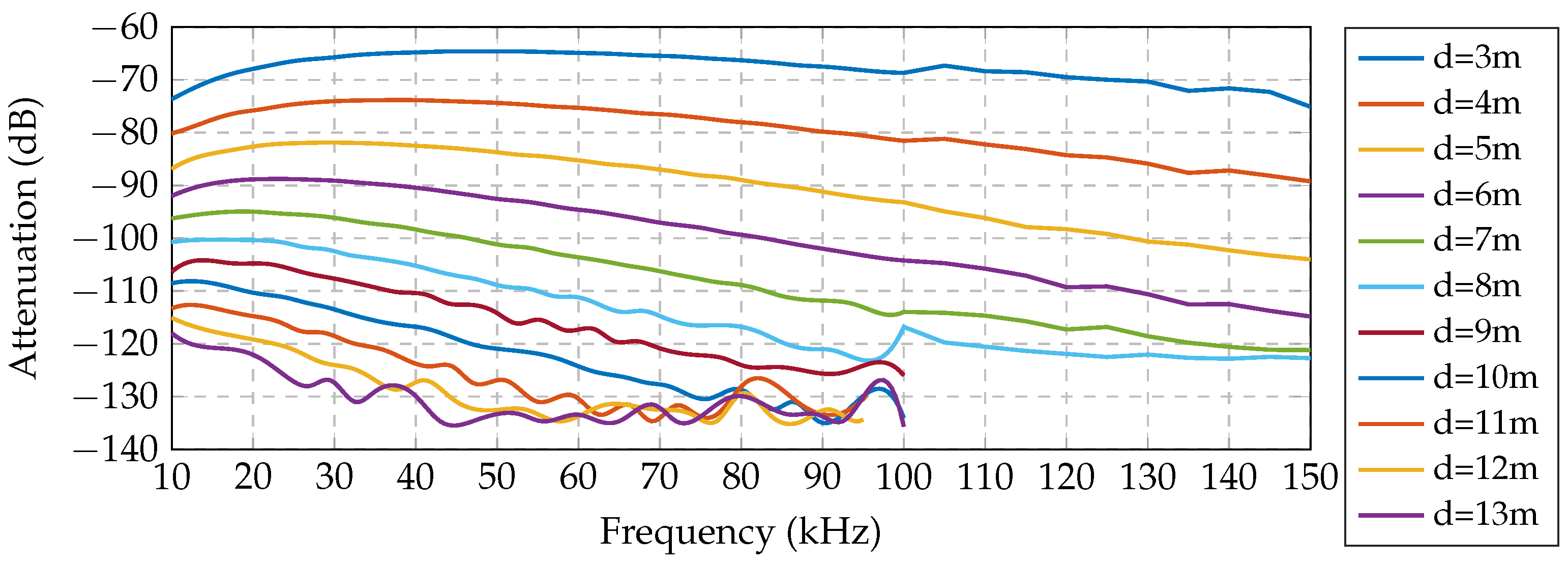
Figure 1 shows the specific signal strengths measured between receiver and transmitter with loop antennas of an 80
radius at the seabed. We only show the lowest frequency range (from 10 to 150
), since it offers the lowest attenuation.
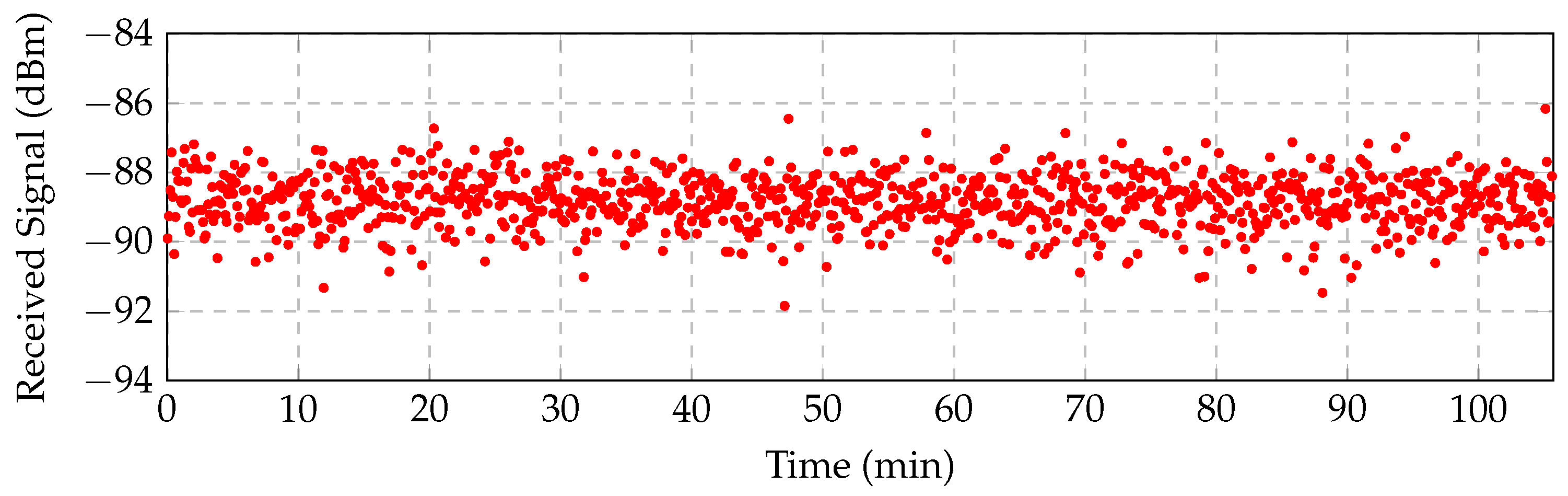
Figure 2 illustrates the temporal variation and reception noise at 40
along almost two hours. Note also that since the attenuation increases in higher frequencies, the overall bandwidth must be narrow. For the previous reasons, the communication frequencies should be established at a low frequency (∼10 kHz) and present a narrow bandwidth (≤3 kHz).
In Part I of this paper (see [
9]), we considered a sophisticated simulator of EM fields to validate the measurement procedure. For the purpose of this paper, we use the EM field simulator to extrapolate the attenuation levels at distances greater than those considered during the measurement campaign. The simulation results appear in
Table 1, which require a high computation time. In order to simulate a complete U-WSN with multiple nodes transmitting multiple packets each, we need to express the channel model in a manner that can be simulated with low computational cost. In this section, we propose to approximate the EM model with a parametric path loss model, which basically extends the log-distance path loss model by including a linear term. Let
denote the path loss (dB) at
d meters from the transmitter. Let
denote the reference distance (in meters), and let
X be a random variable that considers random variations in the channel. Then, the proposed model with parameter
,
has the following form:
We remark that in general, the path loss model should be frequency dependent, but we have assumed the simpler narrow band case. As we will see below, this parametric form provides an efficient characterization of the underwater wireless channel for our network requirements.
In order to find parameters , and for the model, we have considered carrier frequency 10 and . Let be the vector of unknown parameters. Now, for the parametric model, we introduce the matrix of size , where is a vector of ones. Thus, we have a system of equations, , which, using the mean square error (MSE) criterion, can be solved as follows: , obtaining path loss terms , and offset . The MSE results in 0.3225 .
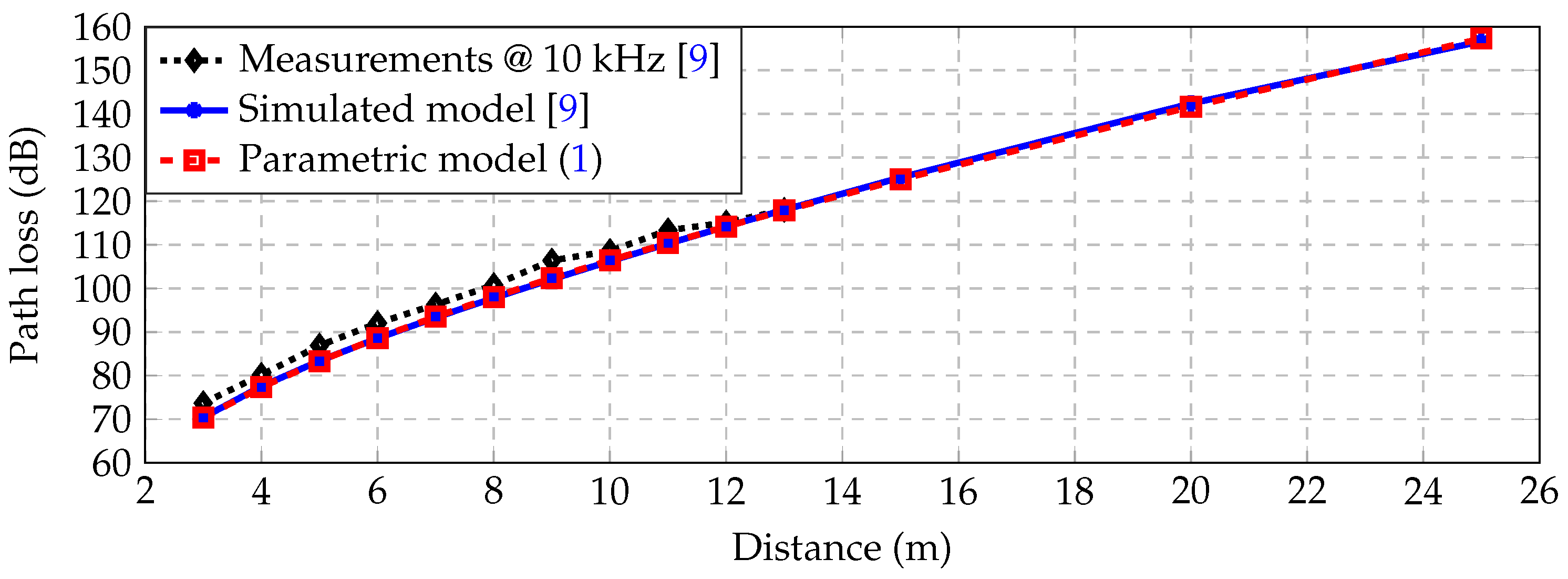
Figure 3 shows the real measurements at 10
(black dots) as presented in [
9], the simulated EM channel (solid blue) also presented in [
9] and the proposed parametric model (dashed red) described by Equation (
1).
Table 1 presents the measuring distances and the corresponding losses. It is apparent that the parametric model (
1) fits the measurements accurately in the given distances.
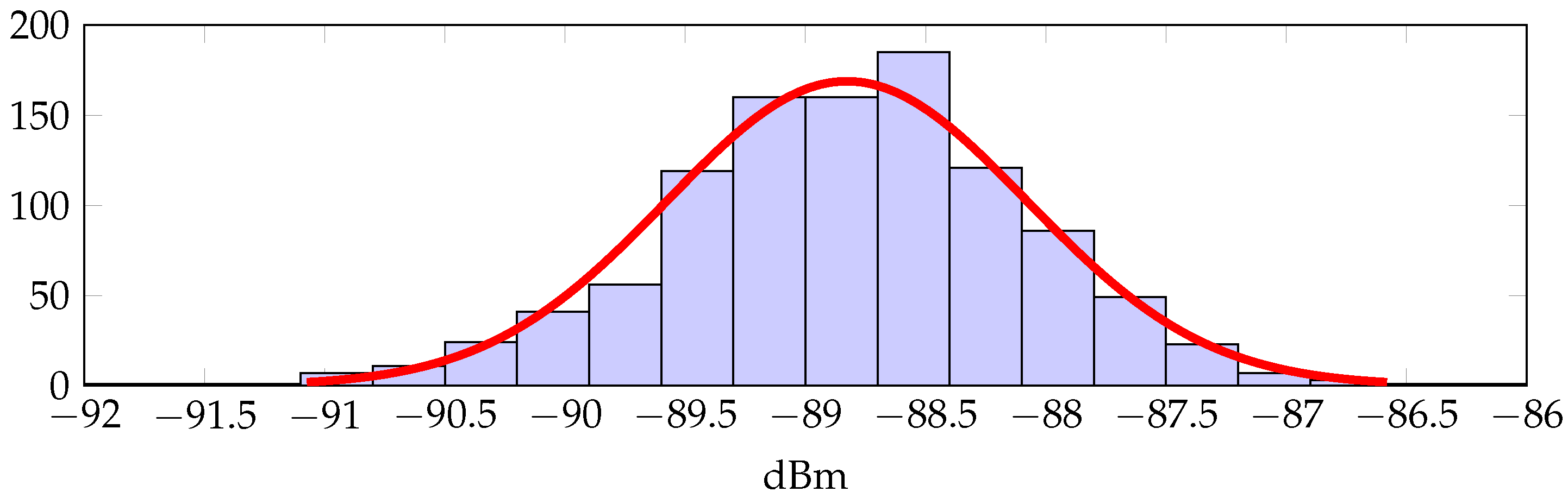
The additive noise
X can be also estimated from the trace of measurements displayed in
Figure 2.
Figure 4 shows the histogram for such a trace together with a normal distribution fit. We conclude that the normal distribution is a reasonable approximation, so that we can assume
, with
.
A final observation from
Figure 2 relevant to the wireless channel simulation is that we can dismiss slow fading.
Once we have fit all of the parameters, we can use the parametric model for estimating the distance between nodes and develop localization algorithms, as explained in the following section.
4. Simulation of a Complete U-WSN
In this section, we simulate a complete U-WSN in the Castalia simulator [
13]. The results of this section should be considered realistic, in the sense that our simulations include propagation impairments (e.g., noise, interference between nodes), radio parameters (e.g., modulation scheme, bandwidth, transmit power) and hardware limitations (e.g., clock drift, transmission buffer), and complete MAC and routing protocols have been implemented.
We start discussing the simulation of the parametric channel presented in
Section 2. Then, we explain the radio parameters used for the simulations. Finally, we simulate a number of scenarios to obtain relevant figures of merit, like received packet rate or latency. We also explain how to extend Castalia for these simulations.
4.1. Simulation of the Parametric Channel
Castalia offers only one parametric channel out of the box, which is the log-distance model. Hence, we had to extend Castalia by including the parametric model (
1) into the class
WirelessChannel. We have set the parameters found in
Section 2:
,
,
,
and noise variance
.
Another detail to consider when using Castalia is that it assumes 0 of transmit power by default. Thus, we had to slightly modify the class WirelessChannel to allow for 40 transmit power. In addition, Castalia only sends to each node those radio signals that are above some threshold, so that we had to set the parameter signalDeliveryThreshold = −130 (i.e., smaller than the receiver sensitivity).
4.2. Radio Parameters
Modulations are typically classified as bandwidth efficient or power efficient [
26]. Bandwidth-efficient modulations, such as high density QAM schemes, are able to accommodate data within a limited bandwidth. Power-efficient schemes, such as BPSK and FSK, are able to reliably send information at the lowest practical power level. In
Section 2, we have seen that the underwater medium exhibits high attenuation. Thus, in order to increase the communication range, we require transmitting at high power levels and establishing reliable communication at a low signal to noise ratio (SNR). We chose 2-FSK, since it is power efficient and allows us to use efficient power amplifiers (i.e., FSK provides a constant envelope signal, so that we can use amplifiers that work in saturation mode).
Castalia only offered FSK with a noncoherent receiver and no channel coding. Therefore, we have added the coherent receiver and channel coding to the class
Radio (in particular, to the method
Radio::SNR2BER). We have chosen a convolutional code
, whose non-systematic feedforward encoder is represented by
, with free distance
and
(this is the total number of nonzero information bits on all weight-
paths, divided by the number of information bits per unit time). Let
p be the bit error rate (BER) obtained from the SNR curve for our FSK modulation. We have characterized the system by including the coding gain as the BER upper bound given by ([
27] Equation 12.1):
The radio parameters common to all simulations are: data rate 1 , 1 bit per symbol, signal bandwidth 3 , noise bandwidth 3 , receiver sensitivity −115 , clear channel assessment −112 and noise floor −127 . We assumed carrier frequency separation of 1 .
The required transmit power depends on the scenario under study and influences critically the communication range.
Section 4.3.1 shows simulation results for 10
, 25
and 40
, while
Section 4.3.2,
Section 4.3.3 and
Section 4.3.4 only consider 40
. We remark that a transmit power level of 40
is used in commercial products [
24]. Castalia has a prefixed value of 0
as the maximum power allowed by the simulator, which must be updated for our setting. In particular, it is needed to increase the value of variable
maxTxPower in the
WirelessChannel class.
The maximum packet size depends on the application under study. For instance, the localization algorithm considered in
Section 3.1 requires small packets of a size of eight bytes (i.e., typically two float numbers per iteration in single precision) before encoding. Recall that the larger the packet, the higher the probability that it suffers some impairment.
Section 4.3.1 shows simulation results for random packets of 30 bytes, while the rest of the simulations transmit their neighbor list, which consists of around 15 bytes.
4.3. Scenarios under Test
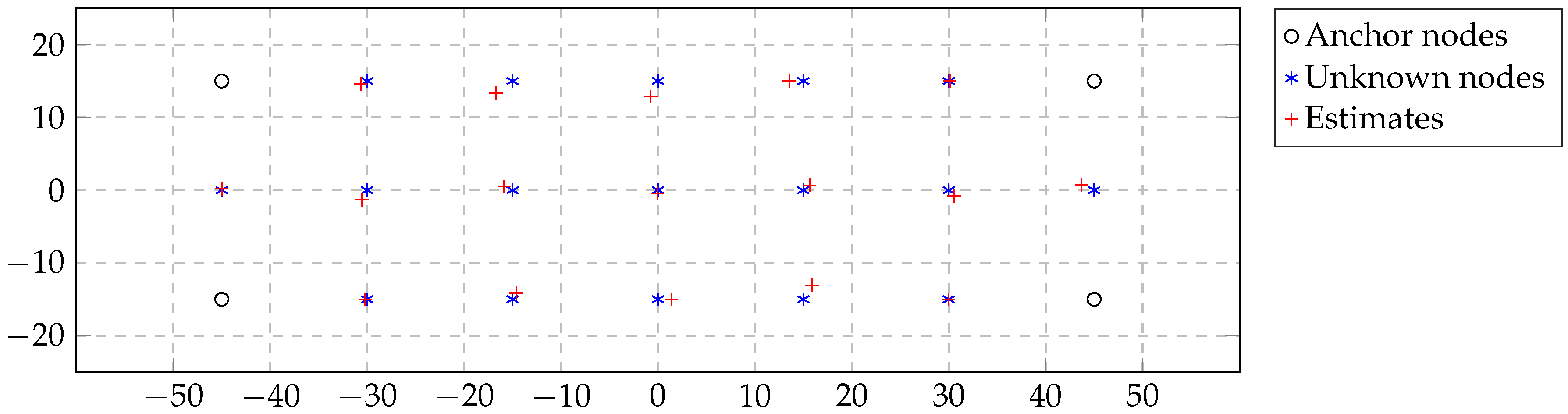
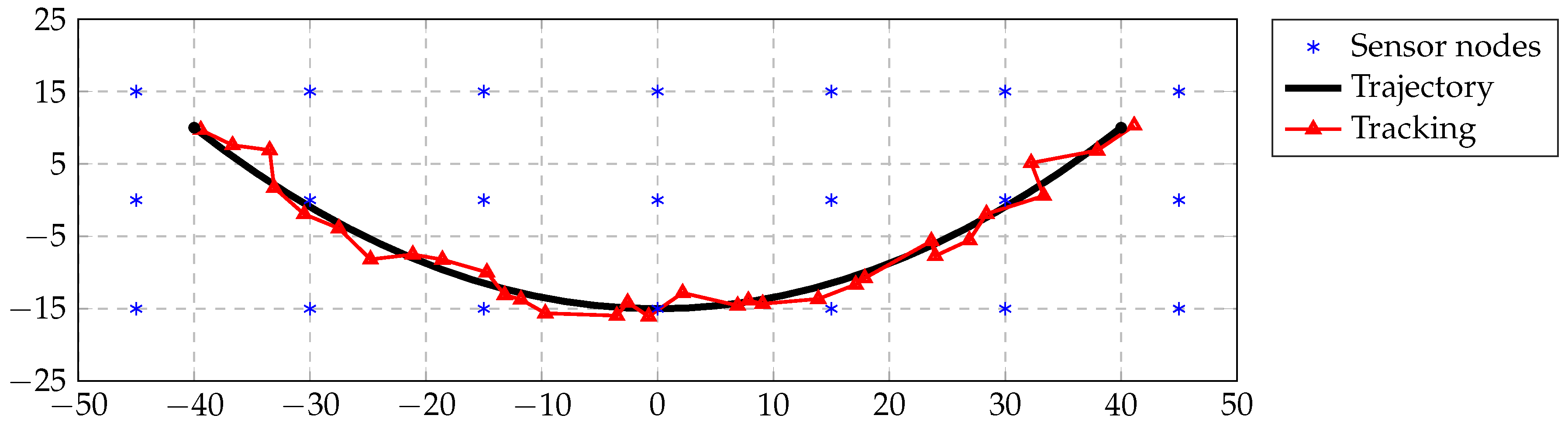
We consider four scenarios: (i) a two-node point-to-point transmission scenario for studying the packet reception rate as a function of the distance; (ii) a network of 21 nodes using diffusion unicast transmissions with acknowledgment (ACK) for studying the ability of an MAC protocol to surmount collisions for different packet periods; since unicast transmissions are costly, in the sense that they require transmitting the same information to every neighbor, we also simulate (iii) diffusion broadcast transmissions (no ACK) in the same network and study the packet rate as a function of a synchronization parameter that ranges from completely asynchronous to a time division multiple access (TDMA) scheme; finally, we consider a (iv) routing in the same 21-node network and study packet rate and latency. For Scenarios (ii)–(iv), all simulations have been performed with a 40 transmit power level and with a coherent receiver with channel coding. All simulation results have been averaged over 50 independent trials.
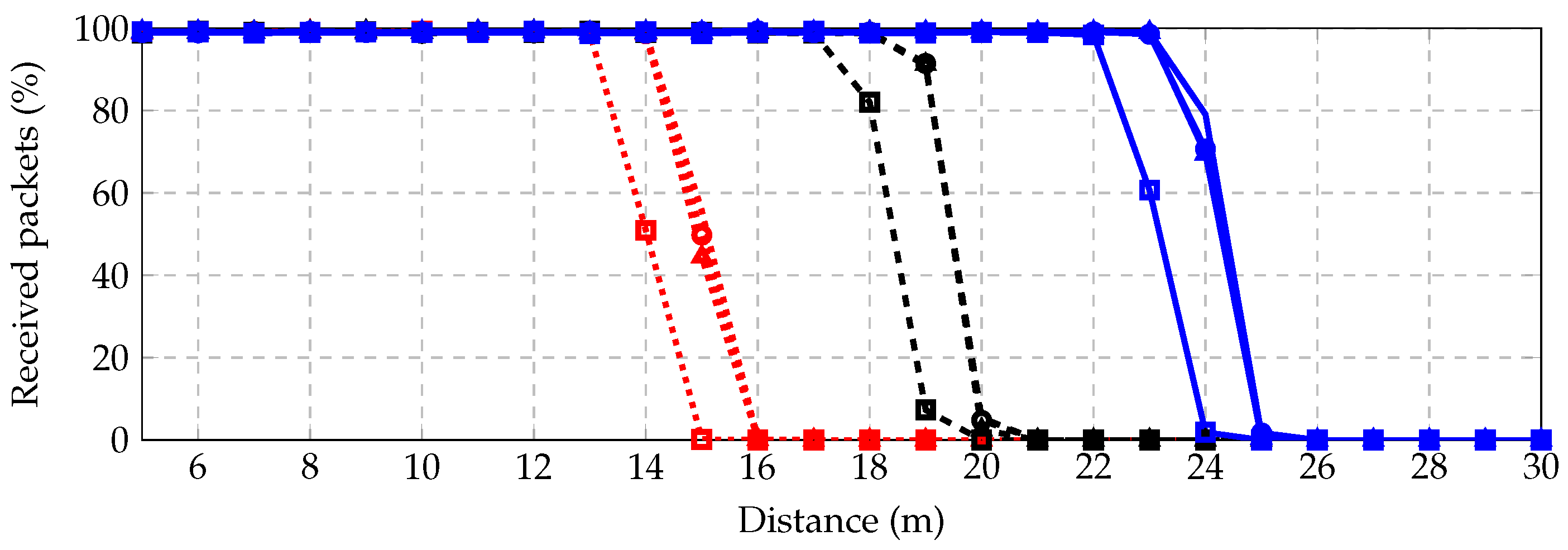
4.3.1. Point to Point
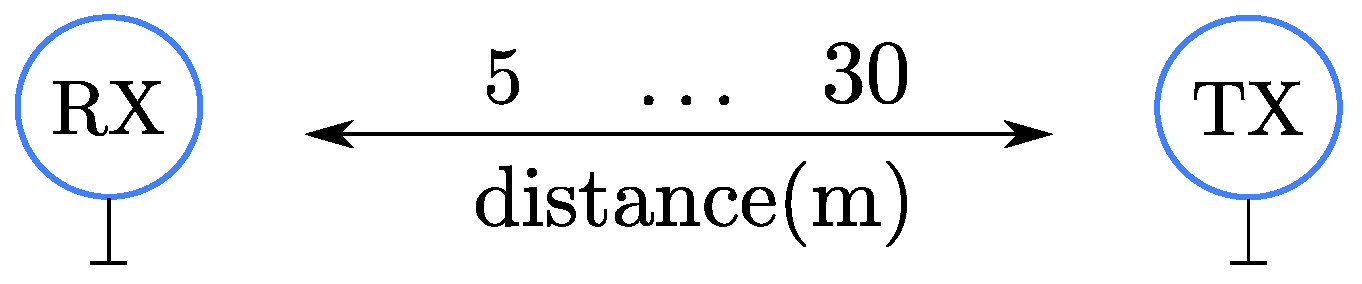
The first scenario under study is a two-node, point-to-point setting, where one node transmits and the other listens (see
Figure 8).
We study the probability of successfully receiving a packet for different distances between five and 30 m.
Figure 9 shows results for three different transmit powers: 10
(red dotted), 25
(black dashed) and 40
(blue solid); and for four different receivers: noncoherent with no channel coding (square), coherent with no channel coding (circle), noncoherent with channel coding (triangle) and coherent with channel coding (no marker). As expected, including a coherent receiver and some channel coding improves the rate. We conclude that with the current radio system, the maximum reliable distance (with
success packet reception rate) is around 14
for 10
, 18
for 25
and 23
for 40
.
4.3.2. Diffusion Unicast Transmission with ACK
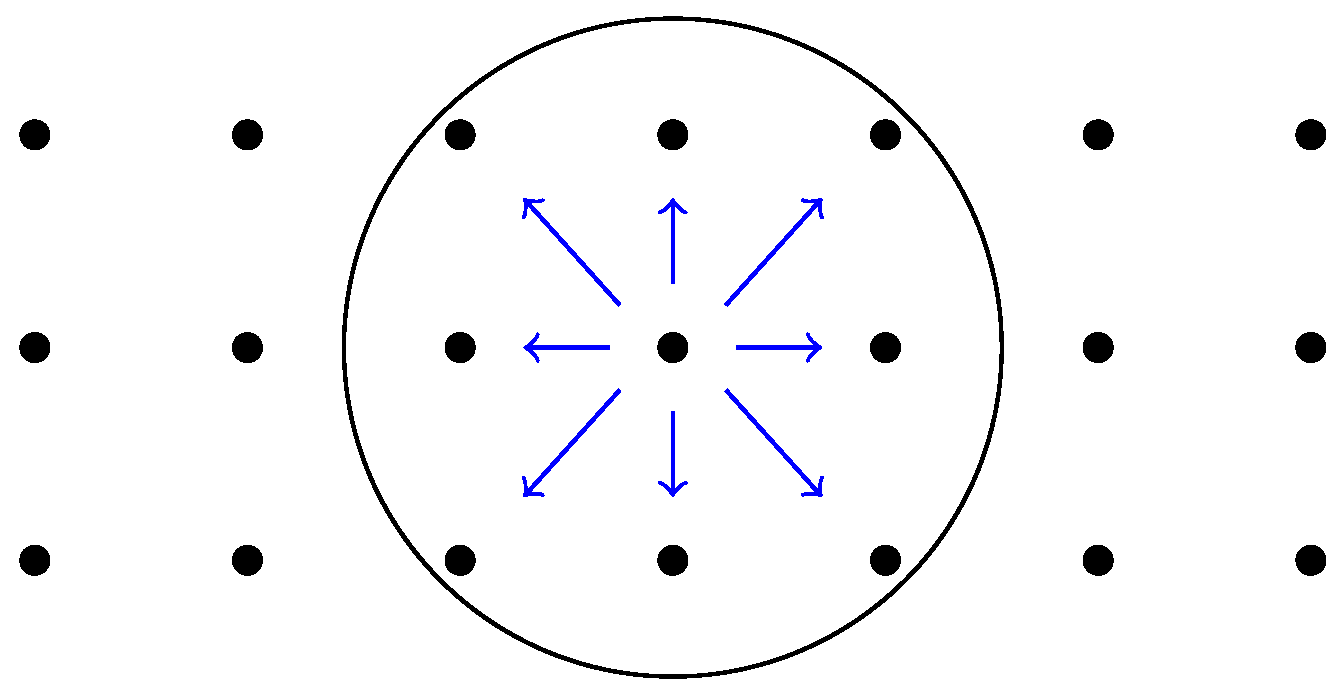
In this scenario, we simulate a complete network of 21 nodes, which are deployed over a field of
in a three-row by seven-column grid, so that contiguous and diagonal nodes in the same row or column are separated 15
and 21.2
, respectively; see
Figure 10. The nodes only communicate with their neighbors (see
Figure 10), as if they were performing an iterative distributed algorithm (like those presented in
Section 3.1).
We use acknowledged unicast transmissions. This means that every node has to discover its neighbor nodes. We use the collection-tree-protocol (CTP) [
28,
29,
30], since it offers an MAC with an ACK layer and an efficient mechanism for neighborhood discovery. CTP has been implemented in several operating systems (e.g., TinyOS, Mantis OS, Contiki OS, Sun SPOTs). It is also offered by Castalia [
31] as a set of routing and MAC modules. We remark that for the Castalia implementation of CTP, the neighborhood discovery mechanism is only available for routing tasks. Therefore, we have extended the current CTP implementation so that this neighborhood discovery mechanism can be used for diffusion, as well. We followed the following steps to extend CTP:
Create an extra field in the routing packet that accounts for the address of the destination neighbor.
Extend CtpForwardingEngine::encapsulatePacket to account for the new field.
Include in CtpForwardingEngine::event_SubReceive_receive the case where the node that receives the packet is the destination neighbor, so that it passes the packet to the application layer instead of forwarding it to its parent.
This extension should be also useful for simulating more complex scenarios, where nodes perform a distributed algorithm and also transmit data to the sink, combining autonomous and external monitoring.
When using unicast transmissions, the nodes have to transmit and receive as many packets as neighbors per iteration. In order to minimize congestion, we have modeled an asynchronous algorithm in which, at every iteration, every node transmits its packet to all of its neighbors, waiting some time (named unicast period) between each unicast transmission (i.e., the waiting time before transmitting the same information to the following node in its neighbors’ table). Then, once the current packet has been transmitted to all of its neighbors, each node waits some extra time (named contention period) before starting another iteration. This contention period allows enough retries so that the packets from the latest iteration can be acknowledged. Thus, the time between consecutive packets for node
i is given by:
where
is the unicast period,
denotes the contention period and
is the number of neighbors of node
i.
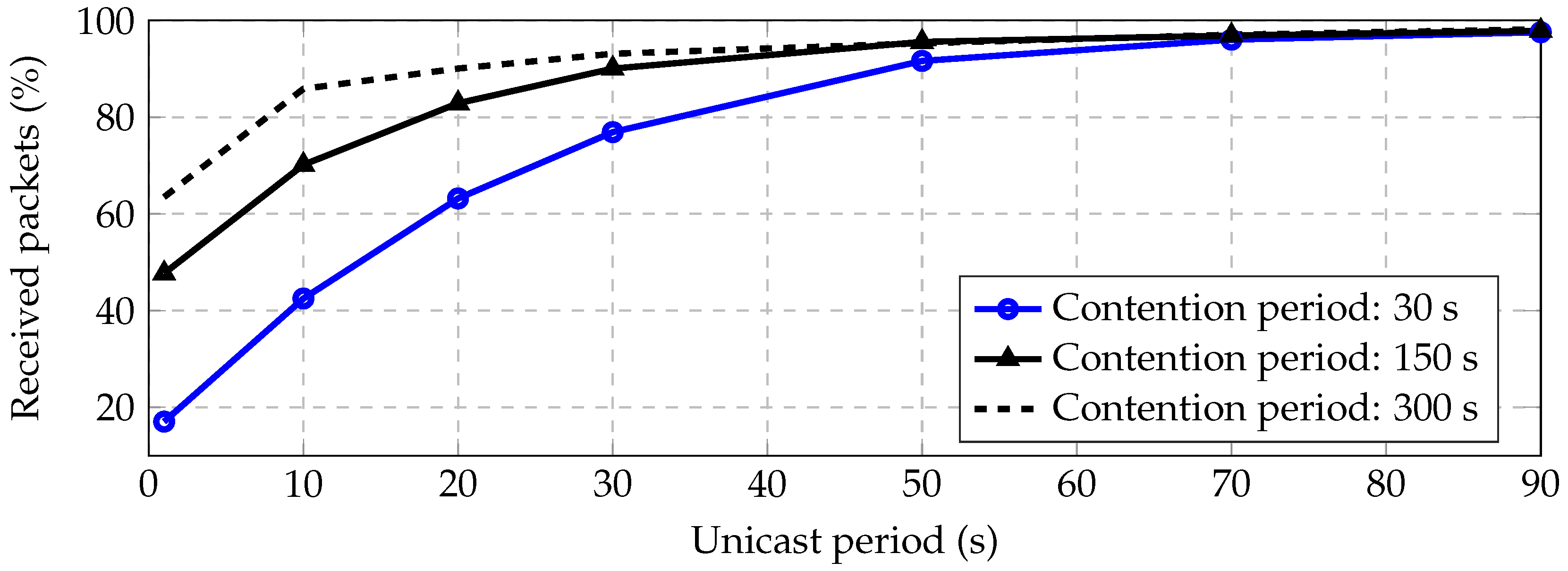
Figure 11 shows the percentage of successfully received packet vs. unicast period for different contention periods. We have observed that for unicast period 50 s and contention period 30 s, the received packet rate is greater than
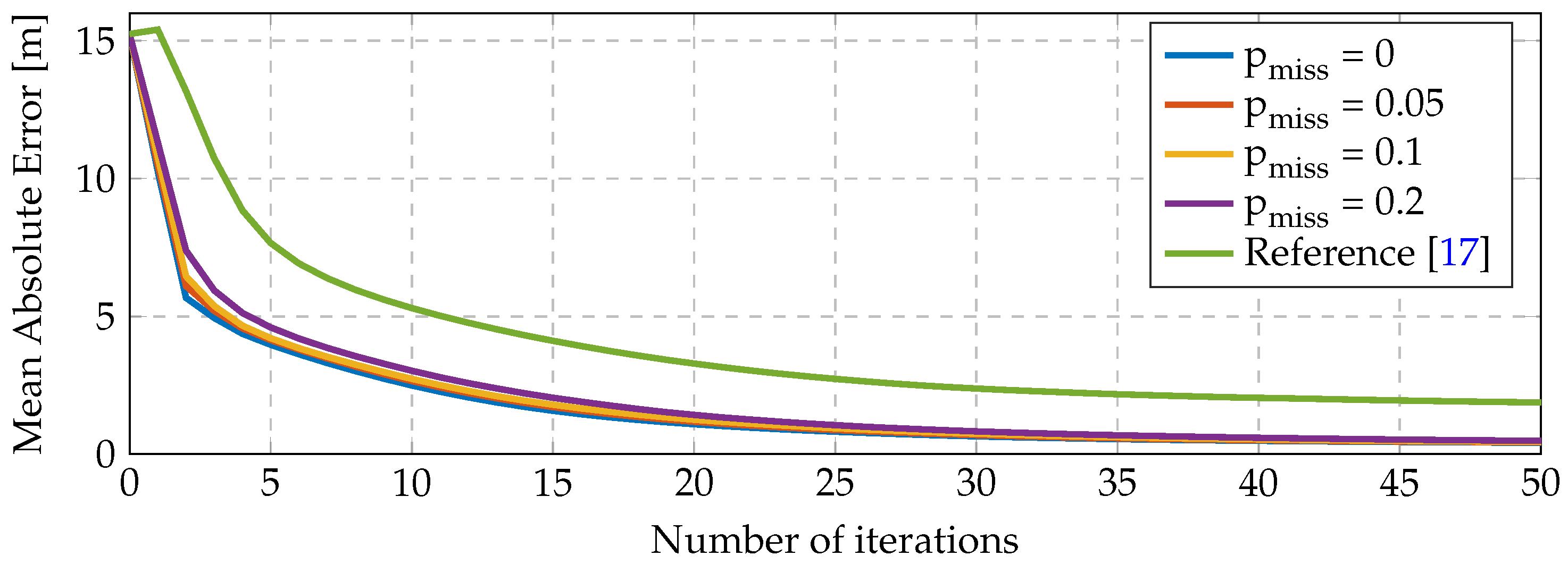
%, achieving 98% for 90 s of the unicast period. These long periods are required for low data rates and dense deployments.
We conclude that, although reliable communications are possible using unicast transmissions, it takes a long time to transmit packets safely. The reason is that, since the data rate is low and each node has to transmit the same information to each of its neighbor, the collision probability is high. In addition, multiple collisions imply multiple retransmissions, which also implies high energy consumption, especially when the transmit power is high.
4.3.3. Diffusion Broadcast Transmission (No ACK)
In this section, we consider nodes transmitting to their neighbors over the same setting displayed by
Figure 10. Nevertheless, here, we suppose that the nodes broadcast only one packet for all of its neighbors, instead of transmitting one packet per neighbor (this is achieved in Castalia by using the macro
BROADCAST_NETWORK_ADDRESS as the destination address).
We study two cases: synchronous and asynchronous transmissions.
Synchronous Transmissions:
Every node transmits during its own time slot in a time-division-multiple-access (TDMA) manner. Hence, only one node is transmitting at a time, meaning that there is neither interference, nor collisions. The packet loss is only due to channel noise. In order to achieve this TDMA scheme, we have extended the Castalia default application
connectivityMap, setting the starting transmission time for node
i as follows:
where
is the time between consecutive packets from the same node,
P is the number of packets (in a real algorithm, this should be one, but here, we set
to average the channel noise when estimating the received packet probability) and
is the node identity. Thus, the time that it takes to transmit all packets of all
N nodes in the network is given by:
Simulations show that we can achieve of successfully-received packets by waiting between consecutive packets. This is a relatively high percentage with a minimum number of transmitted packets (neither ACK, nor retries are necessary), but the cost of achieving accurate TDMA synchronization should be taken into account when considering this option.
Asynchronous Transmissions:
By asynchronous transmission, we mean that there is no coordination among nodes. Hence, the packet loss can be due to noise and collisions (i.e., interference). We have parametrized asynchronous transmissions by adding a term
to (
13), so that the starting time for node
i becomes:
On the one hand, when
, we have
for all
, so that all nodes transmit at the same time (with the exception of very small random clock drifts that can be dismissed for short simulation times). This makes all transmissions collide since no node can receive any packet while it is busy with its own transmission. On the other hand, when
, we have
, i.e., we recover the same result as for the perfect synchronization case studied in
Section 4.3.3 (1. Synchronous Transmissions). The range
aims to model the natural level of asynchrony that happens when the nodes transmit at random intervals or when they are initialized at random times.
Figure 12 shows the average percentage of received packets vs. the overlapping parameter
δ.
Since the probability of all nodes choosing the same slot is low, we can expect that the nodes will tend to spread their starting times uniformly (i.e., ); we conclude that asynchronous broadcast transmission is an efficient scheme that allows both a quick packet rate (e.g., ) and minimum energy consumption (nodes transmit the same packet to all of their neighbors).
4.3.4. Network Routing Using Unicast Transmissions with ACK for Monitoring
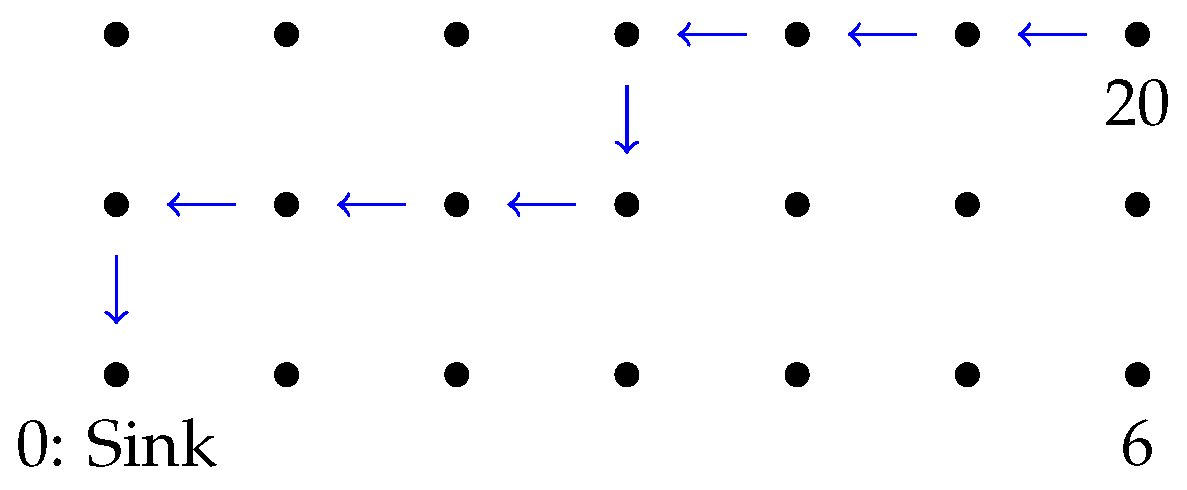
In this scenario, we consider the same network topology displayed in
Figure 10. Nevertheless, instead of diffusing information within their neighborhoods, the nodes forward packets multiple hops until reaching a sink node; see
Figure 13. In this particular experiment, every node sends 50 packets to the sink. Hence, the nodes closer to the sink have to forward multiple packets, apart from transmitting their own packets. The main application for this scenario is to collect data from the network for external monitoring.
We chose the collection tree protocol (CTP) for routing packets to the sink [
28,
29,
30]. CTP uses three techniques to provide efficient and reliable routing: (i) an accurate link estimator that uses feedback from both the data and control planes; (ii) the trickle algorithm [
32] to time the control traffic, sending a few beacons in stable topologies, yet quickly adapting to changes; and (iii) actively probing the topology with data traffic, quickly discovering and fixing routing failures. As already mentioned in
Section 4.3.2, CTP relies on acknowledged unicast transmissions for estimating the quality of the links.
When a node is chosen as the parent from several neighbors or it must perform many retransmissions attempts, its transmission queue can be filled up with unsent packets, and further, incoming packets are dropped. Since the dropped incoming packets are never acknowledged, the link seems down for its neighbors. This kind of congestion becomes worse when nodes operate at low data rates. Although CTP is able to detect and surmount congested nodes, there is some performance limit. We have studied the average number of successfully routed packets from any node to the sink as a function of the packet periodicity. The idea is that the packet period should be long enough for every other node in the network to route its packet to the sink successfully.
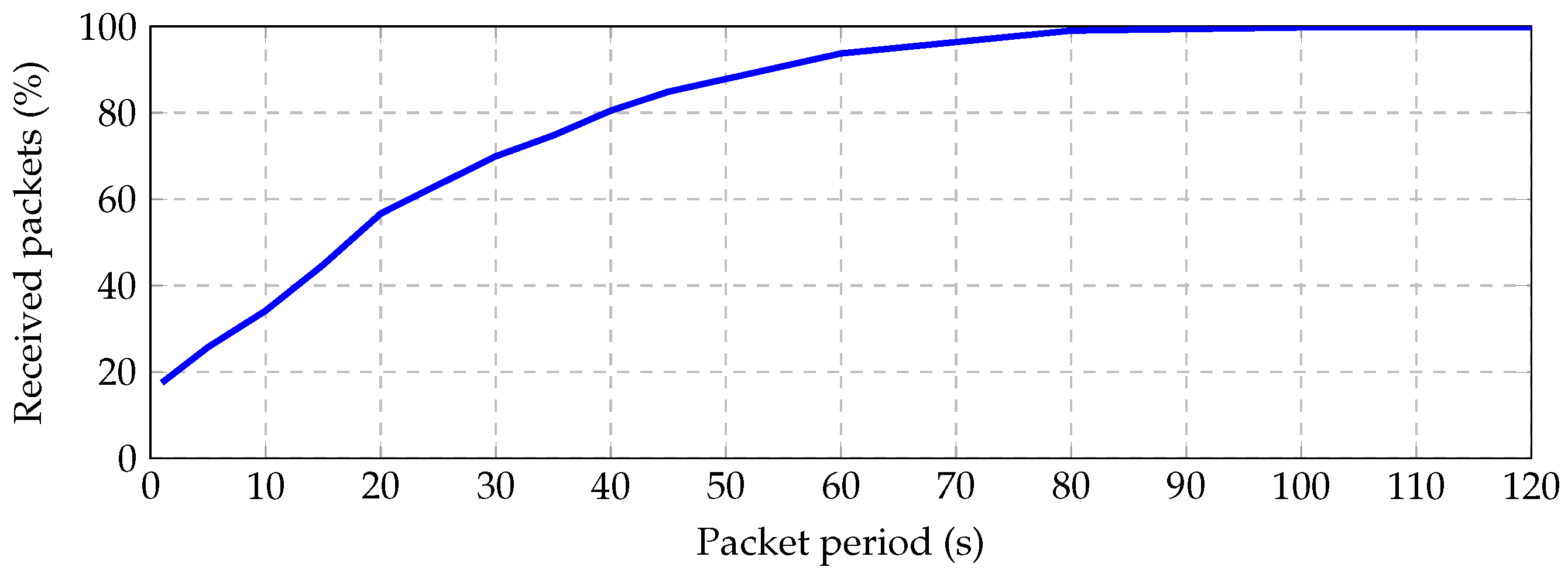
Figure 14 shows that the application layer should wait 60 s between consecutive transmissions in order to successfully route
of the packets to the sink, and it must wait 100 s for routing
of the packets.
Another important metric is the time that it takes a packet from any node to be routed to the sink. This latency depends on several issues, like the number of hops in the route, whether there are congested nodes that behave like bottlenecks, packet loss and retries, etc.
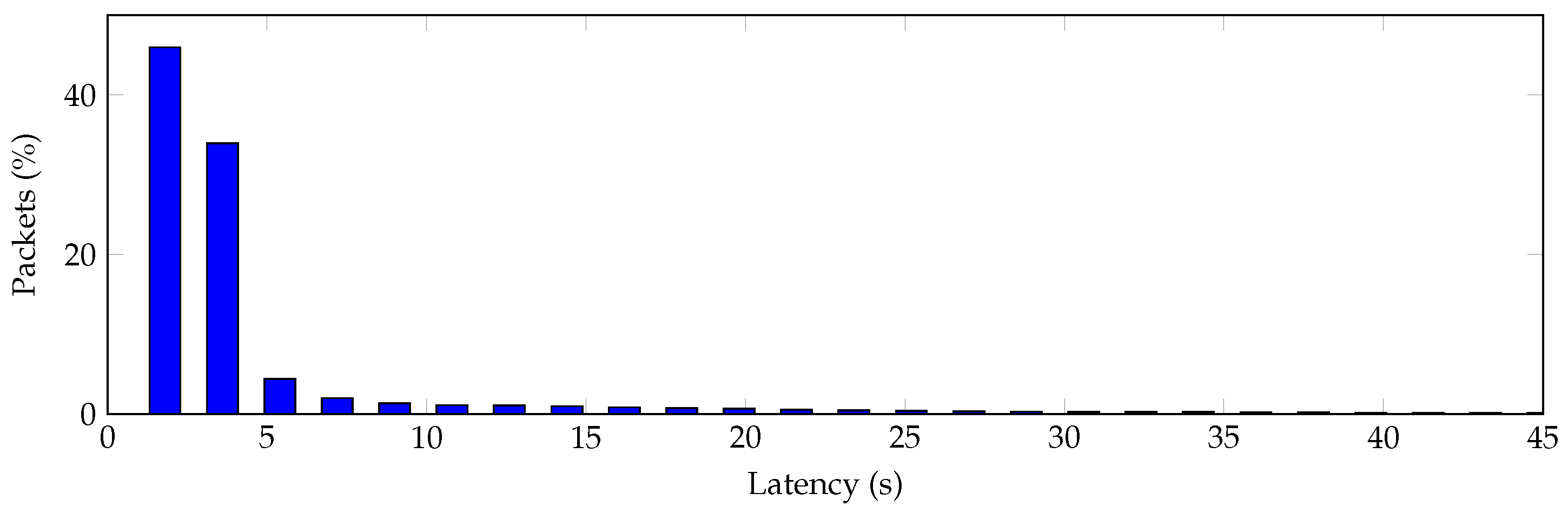
Figure 15 shows a latency histogram. We have observed that, for this particular scenario and packet period equal to 100
,
of the received packets have latency lower than
s,
lower than
s,
lower than
s and
lower than 72 s.
In order to perform these simulations, we extended the default CtpTest application such that the sink could store the packet number and source ID for each received packet. This way, we were able to discharge duplicated packets (due to retransmission) and count only the packets that were successfully routed. In addition, we increased the ACK wait delay constant to 0.469 (by setting the constant CC2420_ACK_WAIT_DELAY = 15360 jiffies) in the CC2420Mac header file to work better with our low bit rate.
Moreover, we set the transmit power to 40 and used coherent receiver and channel coding, so that we achieved good connectivity and every node could find a route to the sink.
5. Conclusions
We intend that this publication serves as proof of concept for a prototype U-WSN deployment in shallow waters with complete communication capabilities. In order to accomplish that, we took real measurements of the underwater channel and characterized an EM channel model in the first part of this paper, i.e., [
9]. From these measurements and channel model, we fitted a parametric path loss model for narrow-band communications and low noise levels.
We studied and proposed algorithms for self-localization techniques with available neighboring communication. We took into account packet loss considerations due to channel changes and also low connectivity between nodes, as well as low data rate packet limits. We proposed Algorithm 1 for self-localization, which can be solved in a distributed manner, and Algorithm 2 for UUV target localization, which is solved optimally.
We also presented preliminary simulation results of U-WSN in Castalia, a realistic, flexible and fast simulator, the precursor of a real deployment. We considered routing, as well as diffusion scenarios and presented some results that are useful for designing centralized and distributed signal processing algorithms, which are motivated by the previous localization proposals. In order to perform the simulations, we extended Castalia, implementing the proposed path loss model, including coherent receiver and channel coding to the radio and adding diffusion capabilities to CTP.