1. Introduction
With the emergence of the Internet-of-Things (IoT), the sustainable energy supply of electronic equipment has become an important issue. However, the lifetime of wireless devices with fixed sources (e.g., batteries) is limited, as periodically replacing or recharging batteries may be inconvenient or infeasible. Recently, radio frequency (RF) signals—which can charge devices by energy harvesting (EH) techniques—have become a potential energy source [
1].
RF signals based on EH techniques have been extensively exploited in simultaneous wireless information and power transfer (SWIPT) systems [
2,
3] and wireless-powered communication networks (WPCNs) [
4,
5,
6,
7]. However, in either SWIPT systems or WPCNs, devices require oscillators for carrier signal generation and analog-to-digital converters (ADCs) for signal modulation, which causes high energy consumption. To solve this problem, backscatter communication (BackCom) techniques [
8] that do not require oscillators and ADCs have received significant attention in recent years, and can be extensively used in wireless sensor networks [
9,
10,
11,
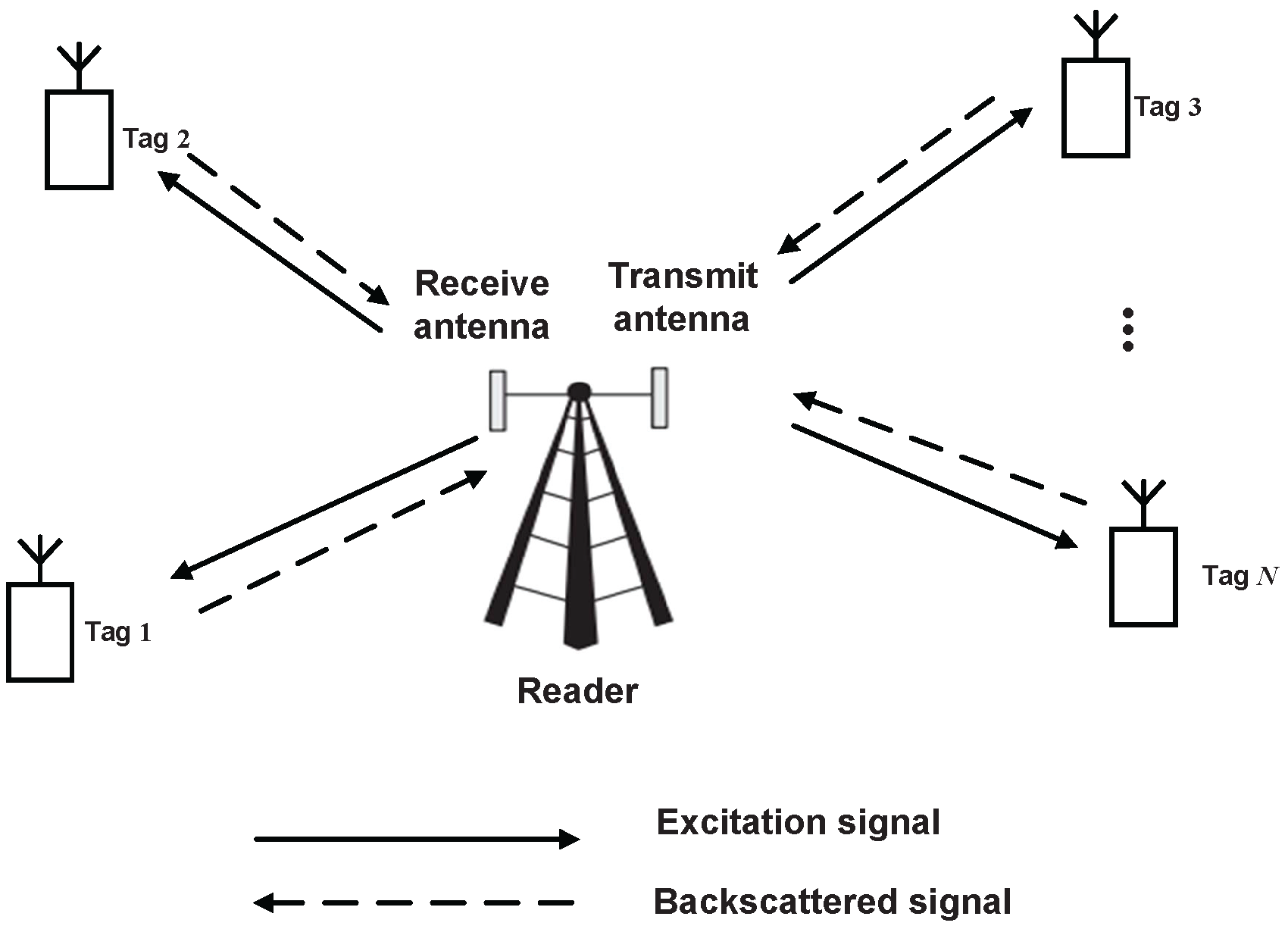
12]. BackCom systems normally include a transceiver, often known as a reader, and multiple nodes, known as tags. The reader transmits excitation signals to activate the tags in forward channels and receives backscattered signals from the tags in backward channels. Tags can be classified as three types: active, passive, and semi-passive. Active tags can radiate signals, while the latter two types communicate with readers based on reflection [
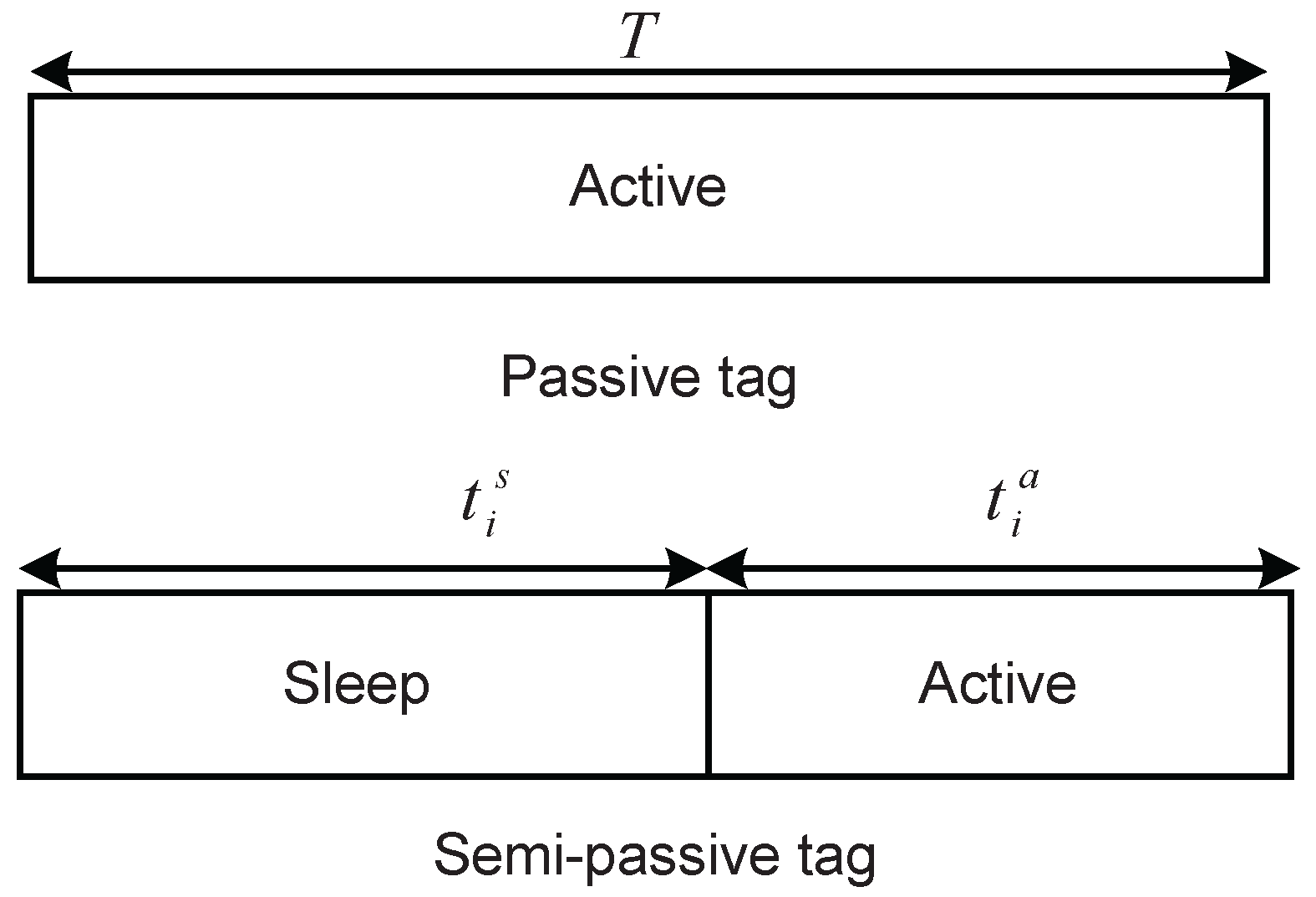
8]. Throughout this paper, tags refer to passive or semi-passive tags without specific declaration. For an activated tag, there are typically two states—i.e., sleep and active states. In the sleep state, each tag’s antenna input impedance is matched, and all input energy will be harvested. In the active state, a portion of excitation signals is backscattered to the reader, and the remainder is harvested for circuit operation. However, only semi-passive tags can store energy during the sleep state, due to the availability of batteries.
In [
13], ambient backscatter was introduced to enable ubiquitous communication where devices communicate by backscattering environment signals (e.g., TV broadcast signals). However, communication based on environmental power sources may not be stable. To fix this problem, fixed energy sources were introduced in [
14]. In [
15], a novel network architecture—i.e., a wirelessly powered BackCom network—was modeled using stochastic geometry, and the network coverage probability and transmission capacity were analyzed. In [
16] and [
17], the authors investigated the security problems of signal-input single-output (SISO) and multiple-input multiple output (MIMO) BackCom systems, respectively. To improve the transmission rate of the secondary user, the BackCom was introduced in cognitive radio networks [
18]. To boost the deployment of BackCom systems, the reader collision problem was studied in [
19].
The resource allocation problem is usually an important issue in wireless networks. In [
20], the authors investigated the resource allocation schemes for two-tier networks, including spectrum-sharing femtocells and macrocells. In [
21], the authors used cooperative Hash bargaining game theory to study the joint uplink subchannel and power allocation problem in cognitive small cells. Note that the time resource allocation of both the sleep and active states has an important effect on the performance of BackCom systems. However, this key factor was not investigated in the works [
13,
14,
15,
16,
17]. Although this time allocation was considered in [
18], the transmission rate was fixed such that the significant link reliability was not investigated. To account for the link reliability, the time allocation control for maximizing the system goodput with fixed reader transmission power in a single-user BackCom system including a semi-passive tag was studied in our previous work [
22]. In practical deployment of a BackCom system, a reader usually serves multiple tags. Hence, this paper considers a practical multi-user BackCom system where each tag communicates with the reader in time-division-multiple-access (TDMA) mode. In this paper, both the passive and semi-passive tags are considered. Moreover, a dynamic reader transmission power allocation scheme is proposed to further improve the system performance. The key contributions of this paper are summarized as follows.
We consider a multi-user BackCom system including a reader and N tags for both cases of passive and semi-passive tags. To account for the link reliability of each case, an optimization problem is formulated to maximize the total goodput by jointly optimizing reader transmission power, time allocation, and reflection ratio.
For the case of passive tags, by exploiting the priority of allocated reader transmission power, the corresponding non-convex optimization problem is decomposed into N convex sub-problems. By solving the feasible sub-problems sequentially and comparing their maximum total goodput, we derive the optimal resource allocation policy. In this policy, a part of tags cannot be activated due to the low priorities. The “activate or not” decision is discussed.
For the case of semi-passive tags, the corresponding problems are also decomposed into
N sub-problems. Each sub-problem is reformulated as a biconvex optimization problem, for which a local optimum point can be found by the proposed block coordinate descent (BCD) [
23] based optimization algorithm. Finally, the close-to-optimal resource allocation policy is derived. Note that throughout this paper, “close-to-optimal” corresponds to “locally optimal”.
The simulation results are given to confirm the superiority of the proposed resource allocation policies. Moreover, the equal power allocation policy is given as the benchmark.
The rest of this paper is organized as follows. In
Section 2, we introduce the system model. In
Section 3 and
Section 4, the problem formulation of the passive tags case is formulated, and the optimal solution for this problem is derived, respectively. In
Section 5 and
Section 6, for the case of semi-passive tags, the problem formulation and a close-to-optimal resource allocation policy are given, respectively. Simulation results are presented in
Section 7. Finally,
Section 8 concludes this paper.
3. Problem Formulation of Passive Tags
In this section, the total goodput maximization problem of a BackCom system with
N passive tags is considered. As stated before, the
i-th passive tag can be activated, only when the corresponding reader transmission power is not smaller than a threshold. The threshold is given as
To avoid the waste of power, if the reader transmission power for the
i-th passive tag is smaller than its threshold, let
to allocate more power to other tags with better channel conditions. Therefore, the reader transmission power for the
i-th tag satisfies
Based on the above analysis, the goodput formulation is rewritten as
Once the
i-th passive tag is activated, the circuit energy constraint
should be satisfied, from which
is rewritten as
. Considering the QoS constraint, the minimum reflection ratio for the
i-th tag is given as
. Therefore, the reflection ratio for the
i-th tag satisfies
. The reader transmission power for each tag is also constrained by the average and peak power, which are denoted by
and
, respectively. The constraints are given as
and
, respectively. Therefore, the optimization problem is formulated as follows to maximize the total goodput.
where
and
,
is the indicator function, having the Value 1 if the condition
is satisfied, or the value 0 if the condition is not satisfied.
Problem P1 is a non-convex problem because the constraints include the indicator function. Hence, it is difficult to find the optimal solution by solving Problem P1 directly. In the following section, the optimal solution for Problem P1 is investigated by exploiting the priority of allocated reader transmission power.
4. Optimal Resource Allocation of Passive Tags
In this section, the optimal solution for Problem P1 is derived. First, Problem P1 is decomposed into N convex sub-problems. Then, the optimal solutions for these feasible sub-problems are derived by convex optimization techniques. Last, the solution for the sub-problem with the maximum total goodput also solves Problem P1.
is an increasing function with respect to
. To maximize the total goodput, these tags with better channel conditions will be allocated power (or be activated) with priority. Hence, there are at most
N permutations for activated passive tags. Without loss of generality, assuming the channel gains of
N passive tags satisfy
, these
N permutations for the indices of activated passive tags are given as
,
,
,
. Based on the above permutations, Problem P1 can be decomposed into
N sub-problems. That is to say, each permutation corresponds to a sub-problem. For the
i-th sub-problem, the number of activated passive tags is
M, where
.
is also an increasing function with respect to
, so that
can keep as
over the whole duration in order to maximize the power of backscattered signals. The
i-th sub-problem is given by
where
,
, and
. It can prove that
is a concave function by deriving its second derivative with respect to
. It follows that
is also a concave function, since it is the summation of
. Hence, Problem P2 is a convex problem [
26]. Before solving the
i-th sub-problem, we first check its feasibility. The feasibility of Problem P2 is given as
and
. If Problem P2 is feasible, the optimal solution for Problem P2 can be derived by considering two sub-cases. First, check whether
. If so, the optimal solution for Problem P2 can be easily derived below.
Theorem 1. The optimal power allocation of Problem P2 under the condition is given by In order to derive the optimal solution for Problem P1, all feasible sub-problems need to be solved sequentially. To reduce the complexity, a useful conclusion is given in the following lemma.
Lemma 1. If for the i-th sub-problem, then the optimal solutions for -th, ..., N-th sub-problem are not the optimal solution for Problem P1.
Based on Lemma 1, it is not necessary to solve the -th, ..., N-th sub-problem if , since the optimal solution for Problem P1 can be found from the first i sub-problems.
If , Problem P2 is solved by Lagrange method. The optimal power allocation is given in the following theorem.
Theorem 2. If , then the optimal power allocation for Problem P2 is given as followswhere is the unique solution for the equation with respect to ,
,
,
is the optimal Lagrange multiplier, and . The optimal Lagrange multiplier can be obtained by the bisection method. Based on above discussions, the optimal power allocation policy can be derived using Algorithm 1. The asymptotic complexity of Algorithm 1 is analyzed as follows. The main complexity of Problem P2 comes from deriving Theorem 2. Suppose Δ iterations are needed for the bisection method used in Theorem 2 to guarantee the converge. The complexity of deriving Theorem 2 is given as . We assume that if and only if () and consider the worst-case; i.e., the first K sub-problems are all feasible, the total complexity of Algorithm 1 is thus .
| Algorithm 1 Algorithm for Problem P1 |
Step 1: Decompose Problem P1 into N sub-problems given as Problem P2, and let ; Step 2: If , check the feasibility of the i-th sub-problem. Then, if the i-th sub-problem is feasible, turn to Step 3; else, let and turn to Step 2. If , turn to Step 4. Step 3: If , the optimal power allocation of the i-th sub-problem is given in Theorem 1 and turn to Step 4; If not, the optimal power allocation of i-th sub-problem is given in Theorem 2, let , and turn to Step 2. Step 4: Compare the total goodput of all feasible sub-problems. The solution corresponding to the maximum total goodput also solves Problem P1.
|
Remark 1 (Activate or Not)
. It can be derived that the decision on whether a tag can be activated is determined by the allocated reader transmission power (or the receive power at the tag). If the allocated power is not smaller than the threshold , the i-th tag is activated; otherwise, this tag stays in the non-activated state. From Algorithm 1, if the i-th sub-problem corresponds to the maximum total goodput, only the first tags can be activated.
Generally, for a BackCom system with passive tags, the tags corresponding to worse channel conditions cannot be activated because the average and peak of reader transmission power are limited. To make the system work in lower reader transmission power, a BackCom system with semi-passive tags is considered in the following sections.
5. Problem Formulation of Semi-Passive Tags
In this section, the total goodput maximization problem of a BackCom system with
N semi-passive tags is studied. Since each semi-passive tag has a battery, it can first enter the sleep state to store energy and then operate in the active state. Therefore, the activation threshold for the
i-th semi-passive tag can be reduced compared to the case of passive tags. This threshold is given as follows:
Following the case of passive tags, Equation (1) is also suitable here, while
needs to further optimized. Hence, Equation (2) is rewritten as
If the
i-th semi-passive tag can be activated, the reflection ratio satisfies
. To power up the
i-th semi-passive tag, the energy harvested during both the sleep and active states should be sufficient to cover the circuit energy consumption, resulting in the following circuit power constraint:
Based on the above discussions, the optimization problem of maximizing the total goodput is given as follows
where
.
Problem P3 is also a non-convex problem. Different from the case of passive tags, Problem P3 is more complicated. In the following section, both the priority of the allocated reader transmission power and the biconvex property are used to solve Problem P3.
6. The Optimal Resource Allocation of Semi-Passive Tags
Like the case of passive tags, the allocated reader transmission power controls the decision to “activate or not”. Hence, there are also at most
N permutations for activated semi-passive tags. Based on the analysis in
Section 4, Problem P3 is also decomposed into
N sub-problems. The formulation of the
i-th sub-problem is given by
where
and
. The feasible condition of Problem P4 is also given as
and
. Assume Problem P4 is feasible. Before solving Problem P4, a useful structure for the optimal solution is given in the following lemma.
Lemma 2. The optimal , , and for solving Problem P4 satisfy: To solve Problem P4, two sub-cases mentioned in
Section 4 are considered. If
, let
. Lemma 2 indicates that extending the active time by full use of harvested power leads to the maximum total goodput. With Lemma 2 and
,
is rewritten as
. Combining with the constraints
and
leads to the new constraint
, where
. Based on the above analysis, Problem P4 can be reduced to Problem P5 as follows.
where
. It is easy to prove that Problem P5 is a convex problem. Exploiting the Lagrange method and KKT conditions, the optimal active time and reflection ratio with
are given in the following theorem.
Theorem 3. Given the reader transmission power of each activated semi-passive tag as , the optimal and have the following structure.where is the solution for with respect to , . Theorem 3 reveals that the optimal control policy of an activated tag has a threshold-based structure. The thresholds are with respect to the reader transmission power. Normally, an activated semi-passive tag has two working strategies; i.e.,
directly active or
sleep-then-active. The decision on whether the activated semi-passive tag first enters the sleep state is characterized in [
22].
If
, the method used for Problem P5 cannot solve Problem P4, due to the coupling of
,
and
in the objective function and constraints. However, Problem P4 can be reformulated as Problem P6 based on Lemma 2,
where
. Note that Problem P6 is still non-convex due to the coupling
and
in the constraint. However, an important property can be used to solve Problem P6, which is given in the following lemma, and for which the proof is omitted for simplification.
Lemma 3. Problem P6 can be reformulated as a biconvex optimization problem.
For a biconvex optimization problem, multiple local maxima can be found—some of which may be the global optimum [
27]. In order to find a potentially point solving Problem P6, Problem P6 is decomposed into two convex optimization problems with given part of the variables according to Lemma 3. First, given
, Problem P6 is reduced to a convex problem as follows:
where
. Using the method for Problem P5, the solution for Problem P7 is given as:
, where
is the solution for
.
Given
, Problem P6 is reduced to the other convex problem as follows
Using the method for Problem P2, the solution for Problem P8 can be obtained, and is given as: , where and , is the solution for equation with respect to , is the optimal Lagrange multiplier.
In the state-of-the-art literature, the BCD method is extensively used to solve biconvex problems due to its superior performance. Therefore, an algorithm-based BCD is proposed to solve Problem P6, which is summarized in Algorithm 2. After deriving the optimal and , the optimal reflection ratio is given as . The asymptotic complexity of Algorithm 2 is analyzed as follows. The complexity of solving Problem P7 is , where Θ is the number of iterations for the bisection method used for Problem P7. The complexity of solving Problem P8 is , as analyzed for Algorithm 1. We assume that Ξ iterations is needed for Algorithm 2 to converge. The total complexity of Algorithm 2 is thus .
Combining Algorithms 1 and 2, Problem P3 can be solved, and the close-to-optimal solution is finally derived. Following the assumptions for Algorithm 1, the asymptotic complexity for solving Problem P3 is .
| Algorithm 2 Algorithm for Problem P6 |
- 1:
Initialize: Set , choose , satisfying the constraints of Problem P6, and compute , set the threshold and . - 2:
while do - 3:
Keep fixed, solve Problem P7 to derive the optimal time allocation . - 4:
Keep fixed, solve Problem P8 to derive the optimal power allocation . - 5:
j=j+1. - 6:
Update with , . - 7:
end while - 8:
return , and .
|
7. Simulation Results
In this section, simulation results are given to corroborate the superiority of the proposed resource allocation policies. The simulation environment is set as follows. For convenience, we assume that the duration of each tag is
s. The forward and backward channel gains are set as
, where
is the distance between the reader and
i-th tag.
is randomly generated from 4 m to 6 m. The energy harvesting efficiency and maximum BER are set as
and
, respectively. Moreover, we set the circuit and noise power as
dBm and
dBm, respectively. In addition, all of the experimental parameters are listed in
Table 1. For performance comparison, the equal power allocation policy is considered. All of simulation curves are adopted 1000 Monte Carlo runs.
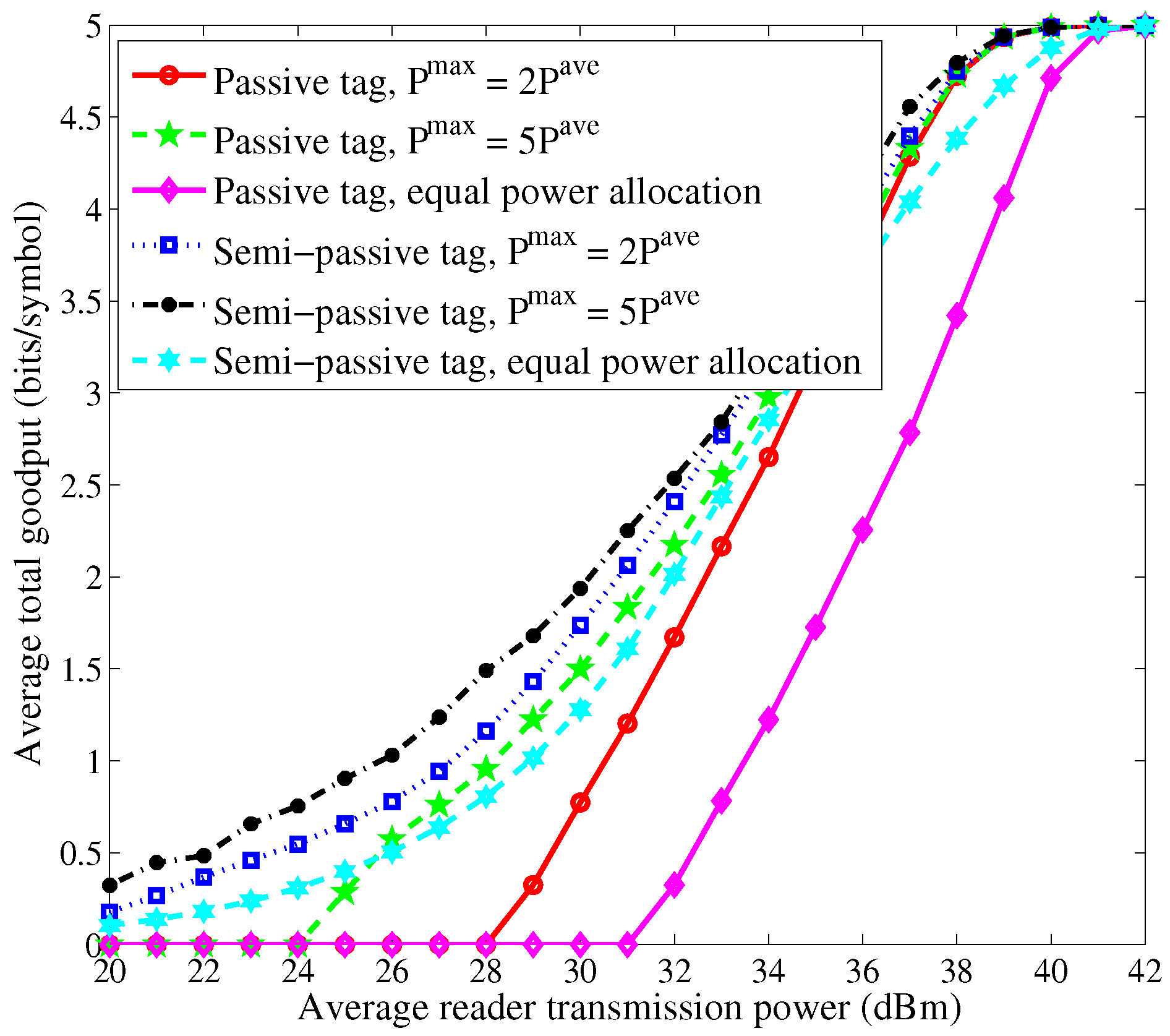
Figure 3 and
Figure 4 show the curves of average total goodput versus the average reader transmission power. We can observe that as the average reader transmission power increases, the average total goodput first increases and then becomes invariant after the average reader transmission power exceeds some threshold. This is because the BER of each tag is close to 0 for high signal-to-noise ratio (SNR) when high allocated power is available. For low average reader transmission power, the passive tags cannot work. The performance of the case of semi-passive tags is superior to the case of passive tags due to the adoption of
sleep-then-active strategy. Moreover, the proposed schemes yield much larger goodput than the scheme of equal power allocation.