1. Introduction
Recent advances in wireless communications and electronic device technology make it possible to realize low-power and low-cost wireless sensor networks (WSNs). The low cost of deployment of low-power WSNs can make various IoT services quite feasible [
1]. However, low-power WSNs operating in unlicensed spectrum bands may seriously suffer from unavoidable co-channel interference generated by other radio systems (e.g., IEEE 802.11b/g/n wireless local area networks (WLANs)) [
2,
3,
4,
5]. It is of great concern to deploy low-power WSNs that can provide stable transmission performance in the presence of co-channel interference.
A number of techniques has been proposed for the coexistence of various radio systems operating in unlicensed spectrum bands. It is well recognized that WLAN is one of major interference sources that seriously hamper the operation of low-power WSNs [
6,
7]. A simple technique is to allocate WSN and WLAN devices spectrum resource orthogonal to each other or to exploit the utilization of white space with channel switching [
8,
9,
10,
11,
12]. Recently, channel hopping mechanisms have been applied to low-power WSNs to mitigate the interference. For example, IEEE 802.15.4e deterministic synchronous multi-channel extension (DSME) employs a channel hopping and channel adaptation scheme for channel diversity [
13]. Bluetooth low energy (BLE) employs an adaptive frequency hopping (AFH) mechanism [
14]. However, these approaches may not be effective as the available spectrum is getting sparse due to the increase of active WLAN devices [
15,
16]. The performance of the AFH mechanism may considerably be degraded in the presence of multiple WLAN interference mainly due to its slow adaptation process [
17]. Although WLAN devices employ a carrier sense multiple access with collision avoidance (CSMA/CA) scheme, they may not detect the presence of WSN signals whose transmission power is much lower than theirs [
18]. As a consequence, they may continue the signal transmission even in the presence of low-power WSN signals, significantly deteriorating the operation of low-power WSNs. Some works have considered placing a special device to help low-power WSNs share a channel with WLANs. A special device, referred to as a signaler, may help other ZigBee devices to access the channel by sending a busy tone, forcing WLAN devices to defer their transmissions [
18]. However, the coordination between the signaler and other ZigBee devices may be too complex, making it impractical in WLAN operation environments. Another special device, referred to as the arbitrator, can schedule the activity of ZigBee and WLAN devices through communication among them [
19]. However, the scheduling may not be easy in dynamic interference environments, since it may require the arbitrator to re-initiate a spectrum scanning and re-allocate the parameters.
Some previous works have also considered performance improvement of low-power WSNs in the presence of co-channel interference. Two approaches, the collision-recovery and collision-avoidance approach, have mainly been considered. The collision-recovery approach mainly considers the use of forward error correction (FEC) techniques to mitigate the co-channel interference. For example, BuzzBuzz employs a Hamming(12,8) code-based FECscheme for ZigBee devices [
20]. However, it may not be effective in dynamic interference environments. A real-time adaptive transmission (RAT) scheme makes WSN devices choose an appropriate FEC coding scheme to maximize the throughput [
21]. However, these collision recovery schemes may not be effective unless the signal-to-interference-plus-noise ratio (SINR) is sufficiently high.
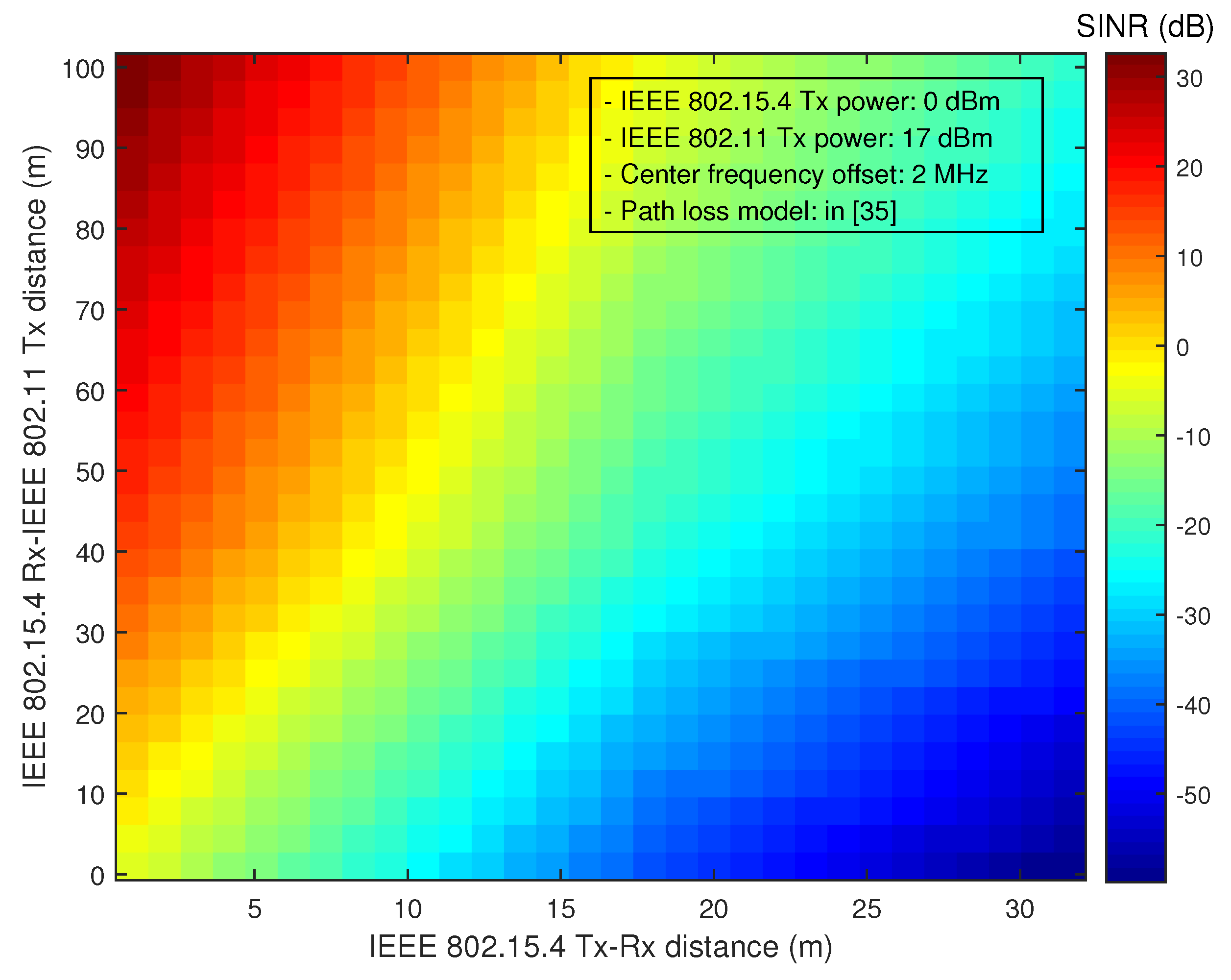
Figure 1 illustrates the SINR of IEEE 802.15.4 in the presence of co-channel interference. Note that IEEE 802.15.4 requires a minimum SINR of 0.4 dB for the transmission of a 20-byte packet (refer to
Appendix A). However, the SINR may not be high in practical operating environments, making the collision-recovery approach ineffective for reliable signal transmission.
The collision-avoidance approach mainly exploits white space to avoid co-channel interference. A dynamic rate adaptation and control for energy reduction (DRACER) scheme adjusts the transmission rate in response to the change of operating condition [
22]. DRACER may reduce the probability of collision with the interference signal by transmitting packets at the highest rate. However, it does not consider the effect of the packet size in the presence of interference, yielding inefficient use of white space. A white space-aware frame adaptation (WISE) scheme considers the packet size control [
15]. Modeling the idle period of interference as a Pareto-distributed random variable, WISE determines the packet size to maximize the throughput efficiency, while providing desired packet collision probability. However, it may need to periodically adjust the Pareto model through channel sensing, which may be a considerable overhead to low-power WSN devices. Another packet size control scheme, referred to as dynamic packet length control (DPLC), simply adjusts the packet size based on a transmission efficiency metric [
23]. DPLC empirically determines the packet size after a number of packet transmissions. However, it may not properly work in the presence of time-varying interference. Moreover, these collision-avoidance schemes only consider the signal transmission at a fixed rate, which may not be efficient when the signal-to-noise ratio (SNR) is higher than that required for the rate. A payload size and transmission rate adjustment scheme was proposed for WLANs in slow fading channel environments [
24]. However, it does not consider the presence of co-channel interference, making it impractical for application to low-power WSNs.
As a collision-avoidance approach, partial packet recovery (PPR) techniques were proposed to reduce the transmission of acknowledgment (ACK) packets. They partition a data packet into a number of smaller blocks and acknowledge the transmission of multiple data packets by a single recovery frame including a block map, which describes the status of all blocks [
25,
26,
27,
28]. The transmitter should retransmit all of the packets when the recovery frame is not received [
25] or wait until it receives the recovery frame, while the receiver retransmits the recovery frame until it receives data packets [
26,
27,
28]. The PPR techniques may severely suffer from frequent loss of recovery frames in practical operation environments. Moreover, they do not consider the waiting time when they evaluate the throughput and the energy consumption. The power consumption during the idle listening of WLAN and ZigBee devices is comparable to the power consumption during signal reception [
29]. Moreover, these schemes only consider the transmission at a fixed rate.
In this paper, we consider the adjustment of the transmission rate and payload size to improve the transmission performance in the presence of co-channel interference. We consider the operation of low-power WSNs that can support the bulk transfer of large data (e.g., e-price tags [
30], surveillance applications involving imaging/acoustics [
31,
32] and structural health monitoring [
33,
34]). Based on the probability of transmission failure and the data throughput, we determine the payload size to maximize the data throughput in the presence of interference. It is shown that the transmission time maximizing the normalized throughput is little affected by the transmission rate, rather mostly by the interference condition. We independently adjust the transmission time and the transmission rate to maximize the data throughput in response to the change of operation environments. Finally, we evaluate the performance of the proposed scheme by computer simulation.
The rest of this paper is organized as follows.
Section 2 describes the WSN model in consideration.
Section 3 analyzes the performance of WSN in the presence of co-channel interference.
Section 4 describes the proposed scheme to improve the throughput performance in the presence of co-channel interference.
Section 5 evaluates the performance of the proposed scheme by computer simulation. Finally,
Section 6 concludes this paper.
2. System Model
As illustrated in
Figure 2, we consider a star-topology WSN comprising a network coordinator and its child nodes located in an operation range of WLANs. The WSN employs a periodic frame structure for synchronous network operation and data communications, where the period of the frame and the length of the data communication interval are
and
, respectively. The network coordinator transmits a beacon at the beginning of each frame for synchronized network operation. It allocates communication resources to a target node using a handshaking protocol during the network operation interval [
35]. Non-target nodes may stay in sleep mode to minimize power consumption.
We assume that a transmitter node generates
-bit data at each transaction. The
-bit data is fragmented by a number of data packets each of which comprises a
L-bit data payload (
) and signaling bits (e.g., packet header). The receiver confirms the packet reception by sending an ACK packet. The transmitter retransmits the data packet if it does not receive an ACK packet. We also assume that the transmission rate is adjustable according to the channel condition. Then, the packet transmission time with transmission mode
m can be represented as:
where
,
and
are respectively the bit size of the synchronization header (SHR), the physical layer packet header (PHR) and the medium access control (MAC) layer packet header (MHR),
(
) denotes the transmission rate of MHR and data payload of transmission mode
m and
is the transmission rate of SHR and PHR (
). We assume that
, and the ACK packet has no payload (i.e.,
).
A node with transmission mode
m may experience packet loss when the received SNR, denoted by
, is lower than a threshold
and/or when the packet has collision with the interference signal. We assume that the SNR is unchanged during each packet transmission and randomly varies between the packet transmissions [
36]. Then, the probability of transmission failure can be represented as:
where
and
denote the probability of transmission failure due to the packet collision and low SNR, respectively. The probability of transmission failure due to SNR can be represented as:
where
denotes the probability of synchronization failure at an SNR of
γ when the SHR length is
(e.g.,
for IEEE 802.15.4 communications is referred to in [
37]) and
denotes the bit error rate (BER) of transmission mode
m at an SNR of
. Note that
is an upper bound of the packet error rate (refer to
Appendix B).
The probability of transmission failure due to the packet collision can be calculated in terms of the channel occupancy of the interference signal. The channel occupancy of the WLAN signal can be characterized using a semi-Markov model [
38,
39]. The channel has two simple operation states, the busy and idle state, whose duration is described by the probability density function (PDF)
and
, respectively. The channel occupancy of the interference signal can be defined by:
where
and
denote the mean duration of the busy and the idle state, respectively. It can be shown that
can be represented as:
where
and
denote the probability of transmission failure due to the packet collision when the packet transmission is initiated in the presence and the absence of the interference signal, respectively. For a given probability of transmission failure, denoted by
, the data throughput can be represented as:
where
denotes the data transaction time (i.e., the round trip time).
Define the bulk transfer delay
by the sum of the access delay
and the transmission delay
. The access delay is the time difference between the start of an access attempt and the successful access. Then, it can be shown that:
where
and
denote the failure probability of the frame synchronization and the scheduling, respectively. Note that a low-power WSN can maintain the frame synchronization robustly in the presence of co-channel interference [
40]. The transmission delay is the time difference between the beginning of data transmissions and the end of all
-bit data transmissions. Then, it can be shown that:
where
denotes the average data throughput. We maximize the average data throughput of low-power WSNs in the presence of co-channel interference by adjusting the transmission rate and the payload size, minimizing the transmission delay.
3. Transmission in the Presence of Interference
We estimate the probability of transmission failure and data throughput in the presence of interference and then determine the payload size maximizing the data throughput. We assume that a node transmits data packets without consideration of the channel condition and confirm the transmission by receiving an ACK packet. The data transaction time can be represented as:
where
,
and
δ denotes the time from the transmission to the reception state and vice versa. The probability of transmission failure due to the packet collision can be represented as:
where
and
denote the collision probability of data and ACK packets, respectively.
When a data packet is transmitted in the presence of interference, it may experience the collision with a probability of one (i.e.,
). Even when it is transmitted in the absence of interference, it may probabilistically experience the collision. Although a WLAN device transmits the signal after carrier sensing-based clear channel assessment (CCA) or energy-based CCA, it may not detect the presence of the signal transmitted by low-power WSN devices. The probability of packet collision can be represented as:
where
can be derived in what follows.
For given idle state length
and data packet transmission time
, a packet collision may occur if a data packet is transmitted (
) seconds after the beginning of the idle state. Let
be the time difference between the beginning of the idle state and the presence of a new data packet (i.e.,
). Assuming that the duration of the idle state is Pareto or exponentially distributed, it can be shown that:
where
σ denotes the shape parameter of Pareto distribution. It can be seen that the probability depends on
when the idle state is Pareto-distributed. When the idle state is exponentially distributed, Equation (
11) can be rewritten as:
Similarly, it can be shown that the collision probability of an ACK packet after successful data packet transmission can be represented as:
The probability of transmission failure due to the packet collision can be represented as:
where
is a constant indifferent from the payload size
L and can be determined as:
Here, , and respectively denote the MHR bit size of the data and the ACK packet.
It can be shown that the data throughput can be represented as:
where
and
denotes the BER of PHR transmission. Assuming that
and
are very low with the use of an appropriate transmission rate in the absence of interference, Equation (
17) can be approximated as:
Taking the derivative of Equation (
18) with respect to
L, i.e.,
we can see that there exists a payload size that maximizes the data throughput. This implies a tradeoff between the packet transmission efficiency and the probability of transmission failure. The use of a smaller payload size may improve the robustness to interference, but it may also increase the signaling overhead, deteriorating the overall transmission efficiency.
The payload size maximizing the data throughput can be determined as:
It can be seen that the payload size depends on the average idle period of interference,
, and the transmission rate
, as well. With
, Equation (
20) can be rewritten as:
where
denotes the payload transmission time that maximizes the data throughput. It can be shown that:
Since
is typically large, Equation (
22) implies that the sensitivity of the payload transmission time with respect to the transmission rate is much smaller than that of the payload size. Moreover,
depends on
. The sensitivity of
with respect to the transmission rate is much smaller than that of
. The transmission time can approximately be represented as:
It can be seen that depends on and not on the transmission rate. Note that the payload size depends on the transmission rate.
4. Proposed Transmission Scheme
Exploiting the above investigation, we consider the performance improvement of low-power WSNs in the presence of interference. We determine the initial payload size based on the interference characteristics estimated by Equation (
20). Exploiting Equation (
23), we adjust the transmission rate
R and the transmission time
T in response to the change of channel and interference condition, respectively. Algorithm 1 summarizes the proposed scheme.
| Algorithm 1: Overall process of the proposed scheme |
- 1:
Initialize using - 2:
Initialize using and R - 3:
- 4:
- 5:
Initialize and - 6:
while -bit data are not delivered do - 7:
for i = 1:W do - 8:
Transmit a data packet with R and L - 9:
if an ACK packet is received then - 10:
- 11:
- 11:
Update R using - 13:
- 14:
- 15:
else - 16:
- 17:
if then - 18:
- 19:
- 20:
- 21:
end if - 22:
end if - 23:
end for - 24:
Update T by Algorithm 2 - 25:
- 26:
- 27:
end while
|
We initially determine the payload size by estimating the average idle period of interference. We define the interference estimation interval by the dedicated interval within the first data communication interval of a pair of scheduled nodes. With the use of an energy-type detector for the channel sensing, the transmitter node can estimate the channel occupancy of interference signal as:
where
is an indicator function,
is the energy of the
j-th received sample,
λ is a threshold level and
is the total number of samples for the measurement. It can be shown that the average busy period of interference can be estimated as:
where
is the number of busy periods,
is the length of the
j-th busy period and
is the channel sensing interval. Finally, the average idle period of interference can be estimated as:
As an example, when
and
, assume that the result of channel sensing is {O,O,X,X,X,O,X,X,X,X}, where “O” and “X” denote the presence and the absence of interference, respectively. Then, it is estimated that the channel occupancy of interference signal is 0.3; the average busy period of interference is 480 usand the average idle period of interference is 1.12 ms, since
,
and
. The initial payload size can be determined as:
where the initial transmission rate can independently be determined in what follows.
The transmitter node determines the transmission rate based on the estimated SNR. It determines the transmission rate of the next data packet based on the received signal strength (RSS) of the ACK packet received most recently. It can determine the initial transmission rate from the RSS of received packets. For an estimated SNR
, it determines the transmission rate by the highest transmission rate
that satisfies
, where
is the minimum SNR for transmission mode
m, which can provide the desired packet error rate of
with the use of maximum payload size in the absence of interference and can be represented by:
Here,
denotes the inverse function of
. As described in
Section 2, the packet loss can occur due to low SNR and/or packet collision. If the packet loss is mainly due to the low SNR, it may be desirable to decrease the transmission rate
R. If it is mainly due to the packet collision, it may be desirable to decrease the transmission time
T to reduce the collision probability.
Consider the case that the transmission failure consecutively occurs due to the packet collision, and the transmitter node decreases the transmission rate. Then, the transmission time will be increased, and thus, the packet collision problem may rather be exacerbated. This problem can be alleviated by adjusting the transmission rate and the transmission time together. If the number of consecutive transmission failures reaches a threshold
, the transmitter node reduces the transmission rate, while keeping the transmission time
T unchanged. If the transmission rate is adjusted from
to
, it may be desirable to adjust the payload size from
to
as:
It may be feasible for the transmitter node to adjust the transmission time
T according to the interference condition, while adjusting the transmission rate according to the channel condition. The normalized throughput, defined by
, can be estimated by:
after performance measurement of
W-packet transmission. Note that this metric is not affected by the adjustment of the transmission rate since it is normalized with respect to the transmission rate. After each
W-packet transmission, the transmitter node updates the normalized throughput, say
. Comparing
with a previous one, say
, it can adjust the transmission time
T to increase the normalized throughput. Let Δ be the step size for the adjustment of transmission time and
be a parameter indicating whether the transmission time was increased or decreased previously. If
, where
, it implies that the transmission time was effectively adjusted. In this case, it may be desirable to keep the adjustment. The transmitter node increases or decreases the transmission time by Δ according to
. If
, it implies that the previous adjustment was not effective, requiring the change of the sign of
(i.e.,
). Then, the transmitter node adjusts the transmission time by
. Otherwise, the transmitter node does not adjust the transmission time. It may also be desirable to change the step size in consideration of the difference between
and
. If the difference is large, it may be desirable to use a larger step size to quickly adjust the transmission time. Algorithm 2 summarizes the adjustment of the transmission time.
| Algorithm 2: Adjustment of transmission time |
- 1:
if then - 2:
if then - 3:
- 4:
else if then - 5:
- 6:
end if - 7:
else - 8:
if then - 9:
- 10:
else if then - 11:
- 12:
end if - 13:
- 14:
end if - 15:
and
|
5. Performance Evaluation
We evaluate the performance of the proposed scheme by computer simulation using a lab-developed WSN simulator written in C++.
Figure 3 depicts the simulator structure, which considers data transmission from the network coordinator to its child nodes in the presence of IEEE 802.11g WLAN interference signals [
38,
39] in a Ricean fading channel with a maximum Doppler frequency of
[
36]. For the performance evaluation, we use Monte Carlo simulation of 300 iterations, each of which runs
simulation time slots.
The simulation environment is summarized in
Table 1, which is mainly based on the specification of the IEEE 802.15.4 PHY layer. For comparison, we also consider the performance of seven schemes; an IEEE 802.15.4 baseline scheme at a transmission rate of 250 Kbps with a fixed payload size, DRACER, which adjusts a transmission rate with a fixed payload size [
22], DPLC, which adjusts a payload size at a fixed transmission rate of 250 Kbps [
23], DRACER with DPLC that adjusts the transmission rate and the payload size by using DRACER and DPLC, respectively, a streaming data link layer scheme, which is a static PPR scheme referred to as Seda [
25], a hybrid frame fragmentation scheme, which is a dynamic PPR scheme referred to as HiFrag [
27], and a green frame fragmentation scheme, which is a combination of HiFrag and transmit power adaptation, referred to as GreenFrag [
28]. The proposed scheme and DRACER use one of four transmission rates, 250, 500, 1000 and 2000 Kbps, by adjusting the spreading factor with an appropriate coding set, while using the same spectrum bandwidth as conventional IEEE 802.15.4 [
22,
41,
42]. The transmission rate can be informed to the receiver using a start frame delimiter (SFD) without additional signaling overhead [
22]. Considering application areas of WSNs, we assume that the maximum payload size is 1024 bytes, which is larger than that of the conventional IEEE 802.15.4 PHY layer (i.e., 127 bytes). Note that IEEE 802.15.4g, a recent amendment of IEEE 802.15.4, supports a maximum payload size of up to 2047 bytes with using almost the same PHY layer techniques as IEEE 802.15.4 [
43].
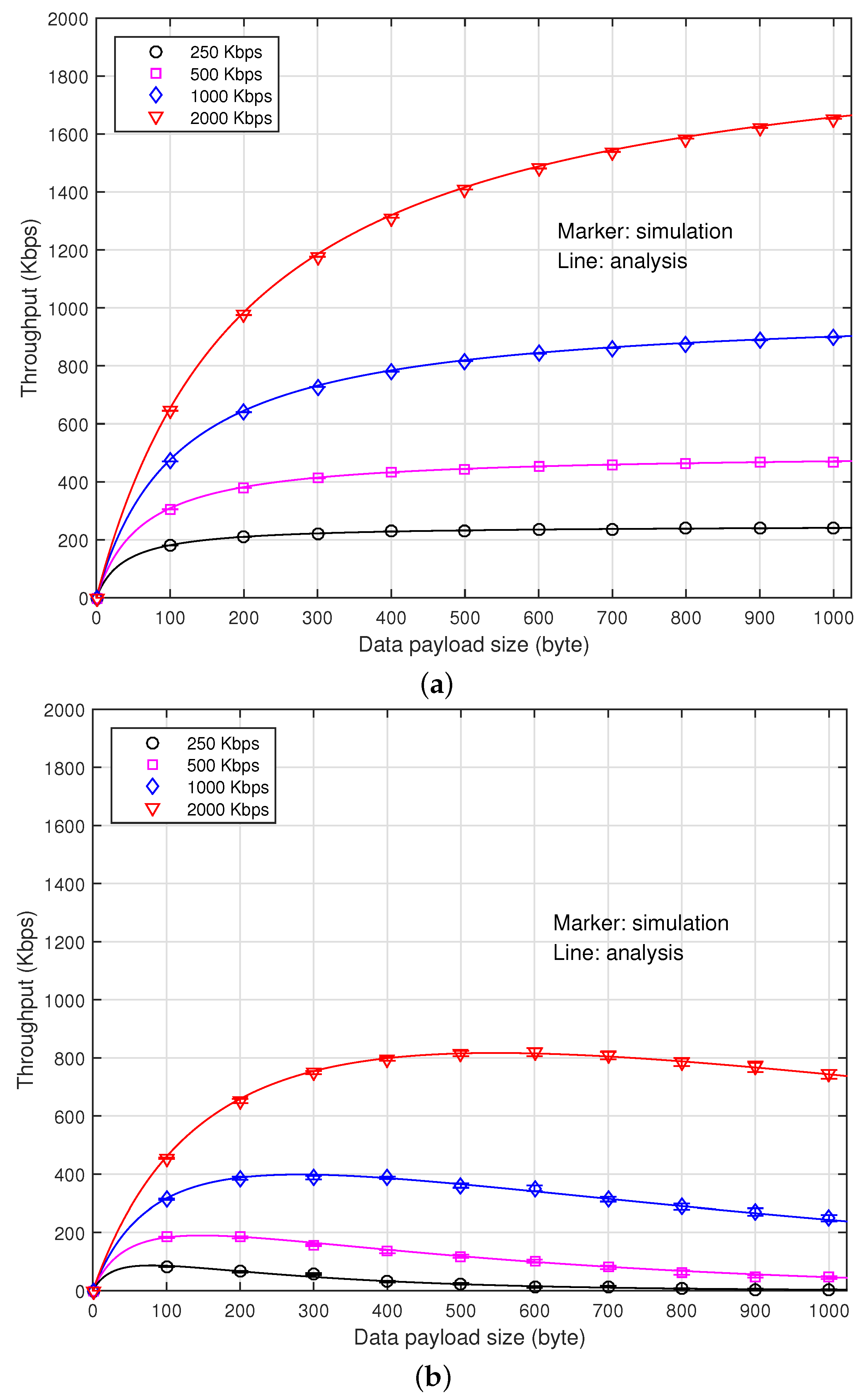
Figure 4 depicts the data throughput according to data payload size when the channel occupancy of the interference signal,
ρ, is zero and 0.2. The error bar represents the standard deviation of the simulation result. To observe the impact of the channel occupancy of interference signal on the performance, we assume that
. We also assume that the SNR is high enough so that the transmitter can employ all of the transmission rates. It can be seen that when
, the data throughput increases indifferently from the transmission rate as the payload size increases, which is mainly due to the decrease of the header signaling overhead. When
, however, there exists a payload size maximizing the data throughput at each transmission rate. It is mainly due to the fact that the use of a larger payload size may become more susceptible to the collision. It can also be seen that the analytical results agree very well with the simulation results.
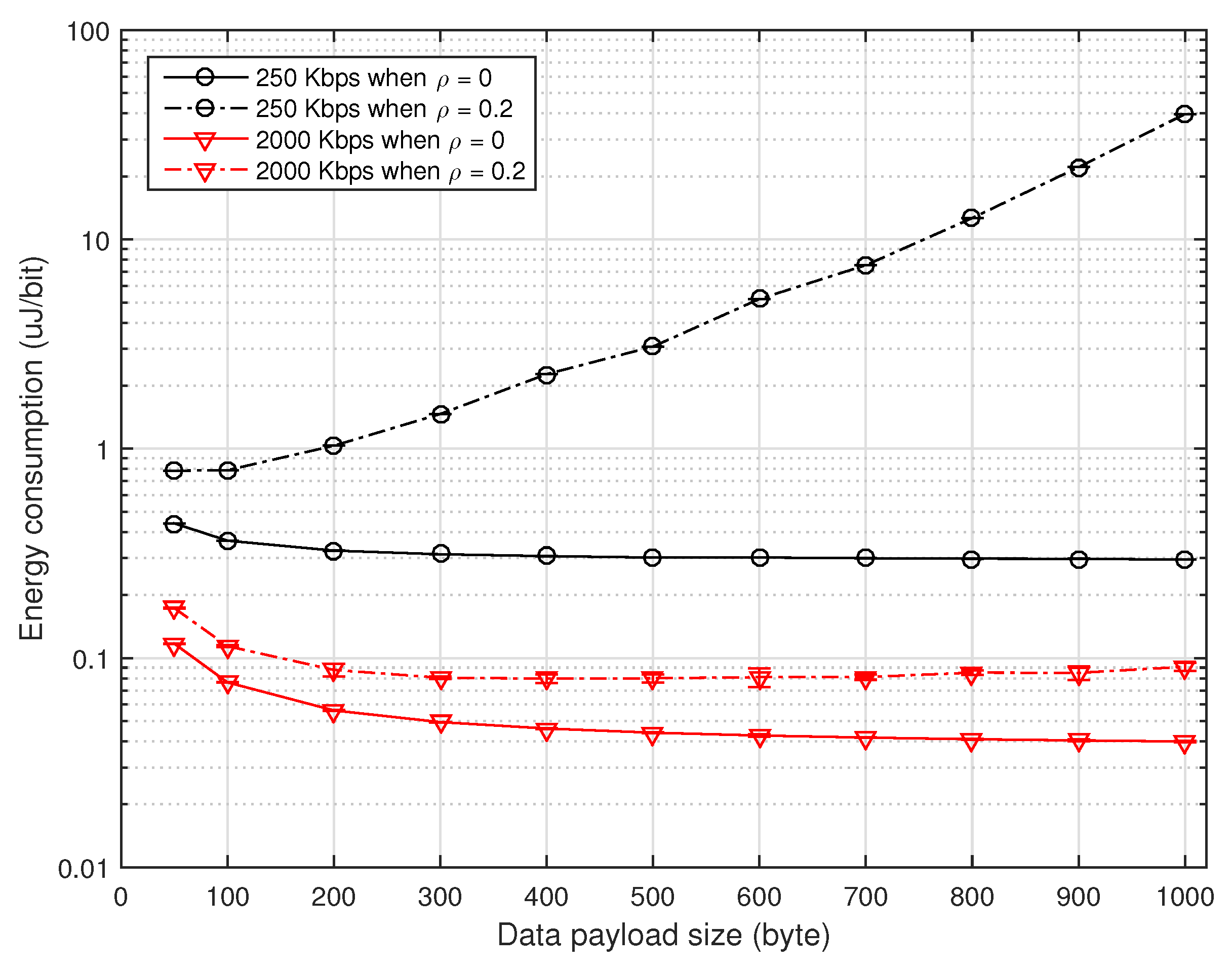
Figure 5 depicts the energy consumption (in uJoule/bit) of the WSN transmitter and receiver according to the data payload size when
and 0.2, which is measured from the power consumption for the transmission and reception of all packets and the power consumption during idle listening (i.e., waiting a packet), as well. It can be seen that when
, the energy consumption somewhat decreases as the payload size increases mainly due to the increase of the throughput. Note that the energy consumption
may increase as the payload size increases, where
denotes the average power consumption. When
, however, there exists a payload size that minimizes the energy consumption, which is slightly different from the one that maximizes the throughput. This is mainly due to the fact that
varies with the payload size. It can also be seen that the use of a higher transmission rate considerably reduces the power consumption, implying that the transmission rate should be adjusted according to the channel condition.
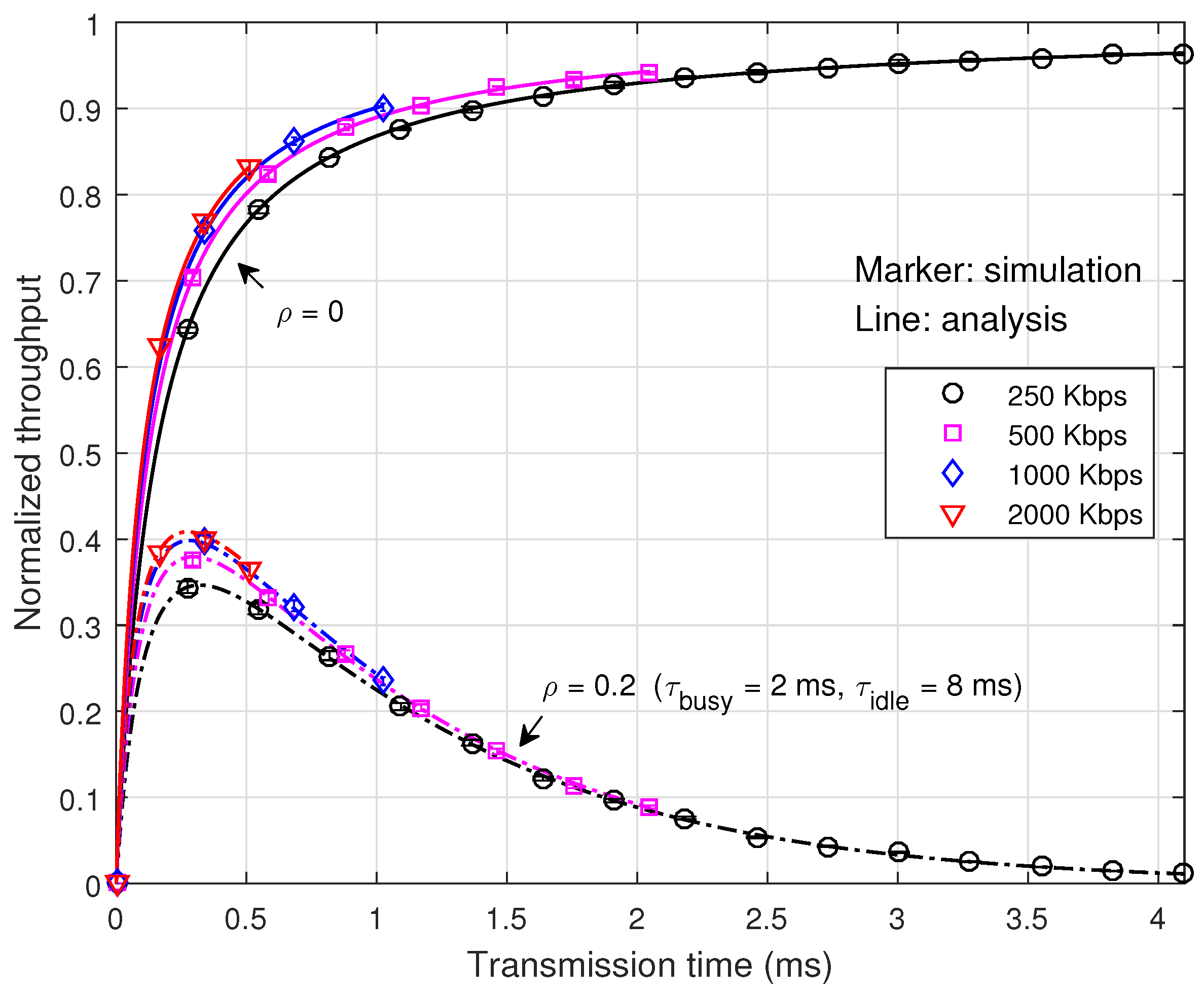
Figure 6 depicts the normalized throughput according to the transmission time. It can be seen that the normalized throughput and the optimum transmission time are quite affected by the channel occupancy of the interference signal, but little by the transmission rate. Note that the data throughput and the optimum payload size depend on the transmission rate. This property makes it desirable to adjust the transmission time according to the interference condition and the transmission rate according to the channel condition.
Figure 7 depicts the data throughput according to the channel occupancy of the interference signal when the SNR is 8 dB and the maximum Doppler frequency is 0.1 Hz, where the IEEE 802.15.4 baseline and DRACER use a fixed payload size of 300 or 1000 bytes, DPLC uses an initial payload size of 300 or 1000 bytes and adjusts it according to the performance and Seda, HiFrag and GreenFrag use their own frame structure proposed in their works, whereas the proposed scheme determines the initial payload size by estimating the average idle period of interference and then adjusts it according to the throughput performance. It can be seen that the IEEE 802.15.4 baseline provides very poor throughput performance even with the use of a large payload size (i.e., 300 or 1000 bytes) mainly due to the use of a low fixed transmission rate. It can also be seen that DRACER can improve the throughput performance by adjusting the transmission rate, but it may suffer from performance degradation with the use of a small fixed payload size in the absence of interference, which is mainly due to the transmission inefficiency, or with the use of a large fixed payload size in the presence of interference, which is mainly due to the increase of packet collision. We consider two DRACER schemes; DRACER I, which transmits packets at the highest rate regardless of transmission failure, and DRACER II, which adjusts the transmission rate in response to transmission failure. It was reported that these schemes are effective in an interference and a channel fading environment, respectively [
22]. However, it can be seen that DRACER I and II make little difference on the transmission performance. This is mainly because they do not consider the effect of the payload size in the presence of interference, yielding inefficient use of white space. It can also be seen that DPLC can little improve the throughput performance even with the use of DRACER. This is mainly because it does not consider the effect of the transmission rate adjustment with a fixed step size of 10 bytes regardless of the transmission rate [
23], yielding inefficient use of white space and slow adaptation of the payload size. It can also be seen that the proposed scheme significantly outperforms the other schemes by adjusting both the transmission rate and the transmission time in response to the change of interference and channel condition. It can also be seen that the PPR schemes (i.e., Seda, HiFrag and GreenFrag) may provide throughput improvement over the IEEE 802.15.4 baseline in the presence of co-channel interference. This is mainly because they partition the data packet into a number of small blocks and adapt the block size based on the transmission performance, which may provide robustness to co-channel interference. It can also be seen that they may outperform DPLC, which is mainly due to fast adaptation of the block size. However, PPR schemes may severely suffer from the presence of co-channel interference, mainly due to the frequent loss of recovery frames. It can also be seen that their performances are limited mainly due to the use of a low fixed transmission rate, fixed frame structure and small maximum payload size. It may not be easy for the PPR schemes to increase the maximum payload size and the transmission rate since the computational complexity may considerably increase as the number of blocks for the packet partitioning increases.
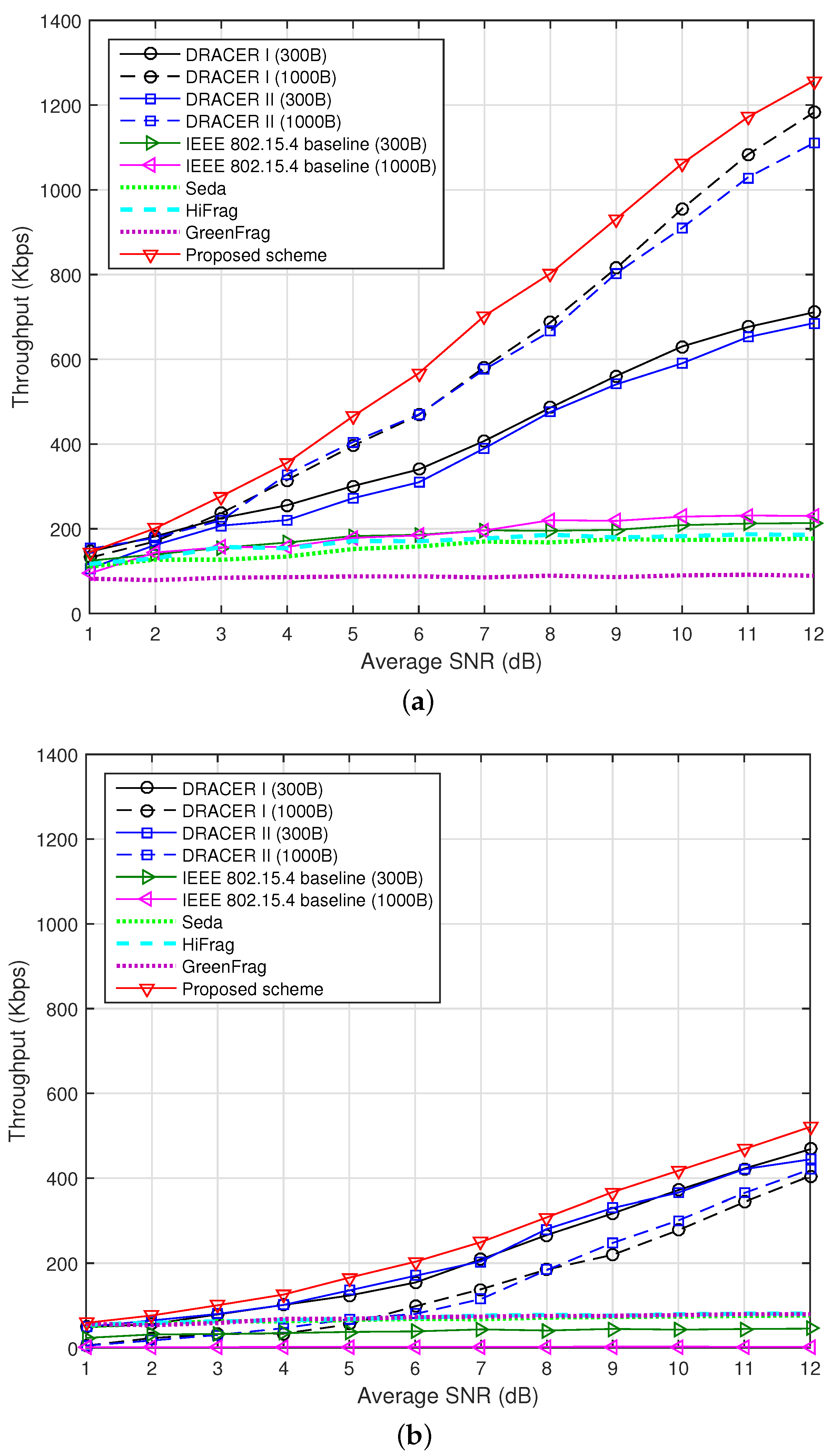
Figure 8 depicts the throughput according to the SNR when
and 0.2. Since DPLC does not provide noticeable performance improvement over the IEEE 802.15.4 baseline and DRACER, we hereafter consider the performances of the IEEE 802.15.4 baseline and DRACER for the clarity of description. It can be seen that DRACER can improve the performance of the IEEE 802.15.4 baseline by using a large payload size in the absence of interference and a small payload size in the presence of interference. However, there is no proposed strategy when to employ DRACER I and II and how to adjust the payload size together in the presence of interference and channel fading. It can also be seen that the proposed scheme can significantly improve the throughput performance by independently adjusting the transmission rate and the transmission time according to the interference characteristics and channel condition, respectively. It can be seen that GreenFrag provides poorer throughput performance than HiFrag, although GreenFrag is a combination of HiFrag and transmit power adaptation, where it uses a transmit power level of 0, −3, −7, −15 or −25 dBm. When GreenFrag confirms good transmission performance, it reduces the transmit power without consideration of the channel condition. This may cause a ping-pong effect, seriously deteriorating the throughput performance. In fact, GreenFrag may not work well unless the SNR is sufficiently high (e.g., >30 dB).
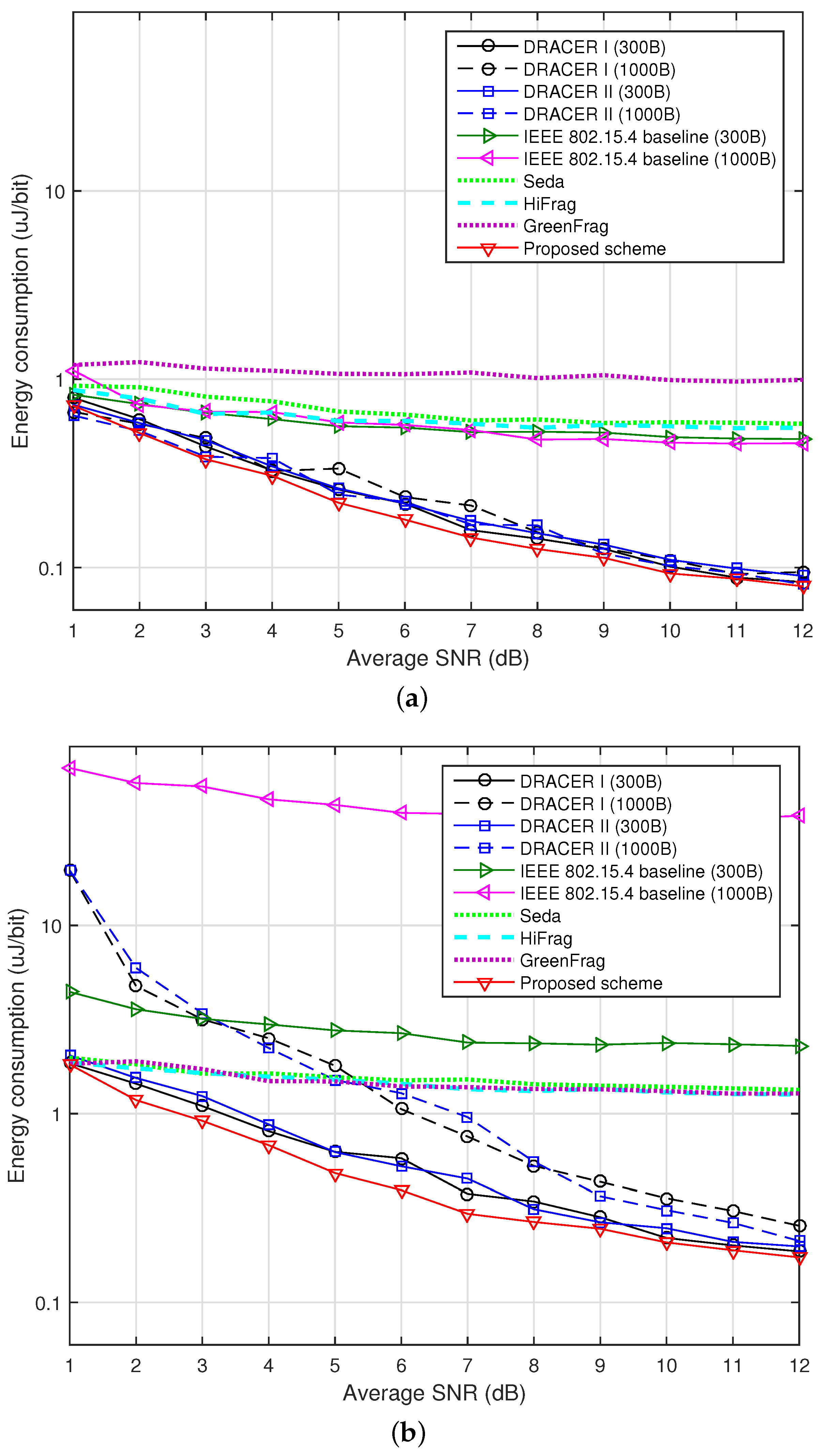
Figure 9 depicts the energy consumption (in uJoule/bit) according to the SNR when
and 0.2. The power consumption of GreenFrag is measured at various power levels [
28]. It can be seen that the power consumption increases when the SNR decreases or the channel occupancy of the interference signal increases, which is mainly due to the increase of transmission failure. It can also be seen that the proposed scheme reduces the power consumption by adjusting the transmission rate and the transmission time. However, the gain in power consumption is somewhat marginal. It is mainly because the use of a larger payload size in the absence of interference may increase the data throughput and the average power consumption, as well.
Table 2 summarizes the transmission delay according to the SNR when
and 0.2, where
,
and
. It can be seen that the transmission delay decreases when the SNR increases or the channel occupancy of the interference signal decreases, which is mainly due to the increase of the data throughput. It can also be seen that the proposed scheme and DRACER significantly outperform the other schemes, which is mainly due to the transmission rate adjustment. It can also be seen that the proposed scheme can reduce the transmission delay further than DRACER both in the absence and the presence of interference. This is mainly because the proposed scheme can adjust both the transmission rate and the payload size to maximize the data throughput in response to the change of operation environments.
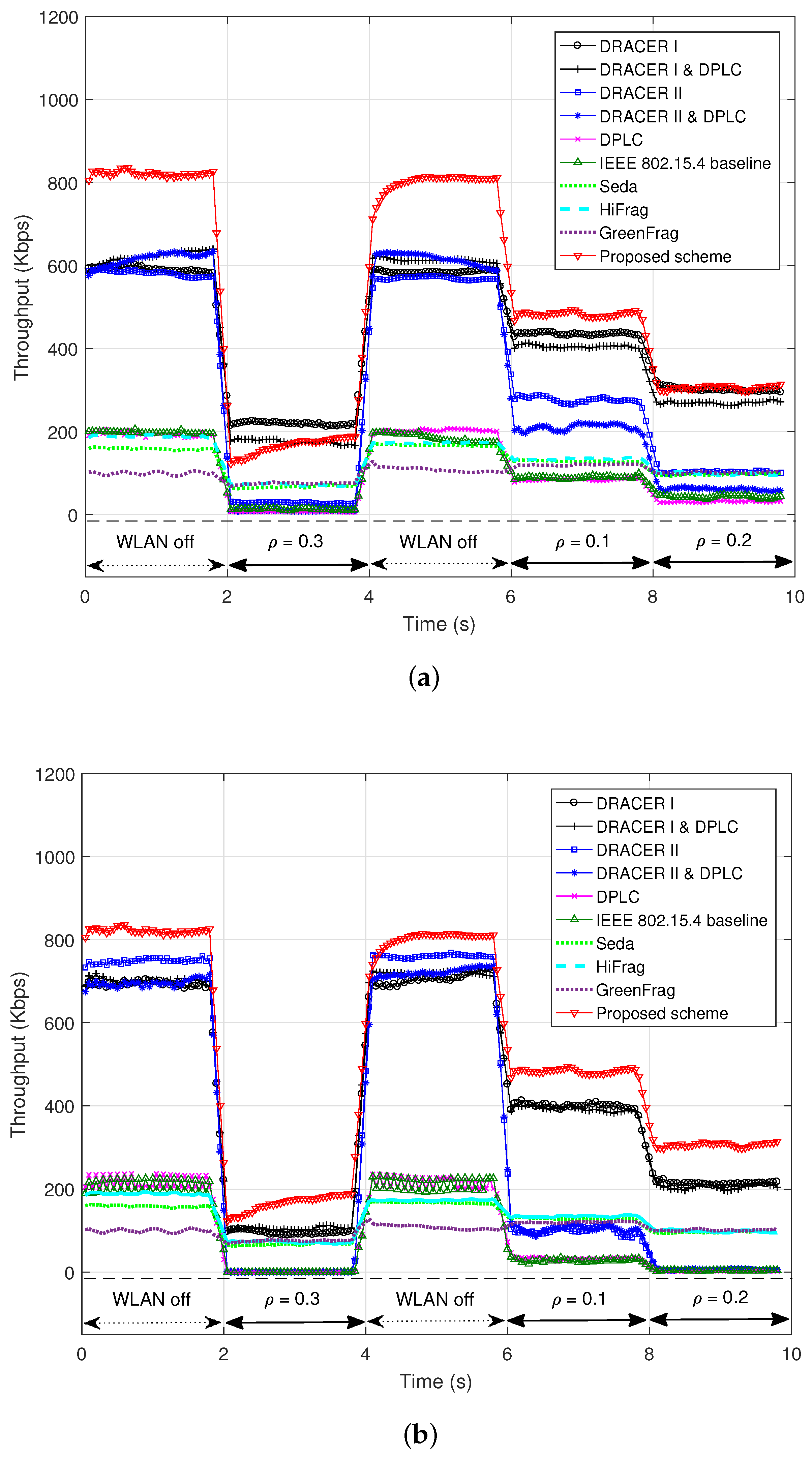
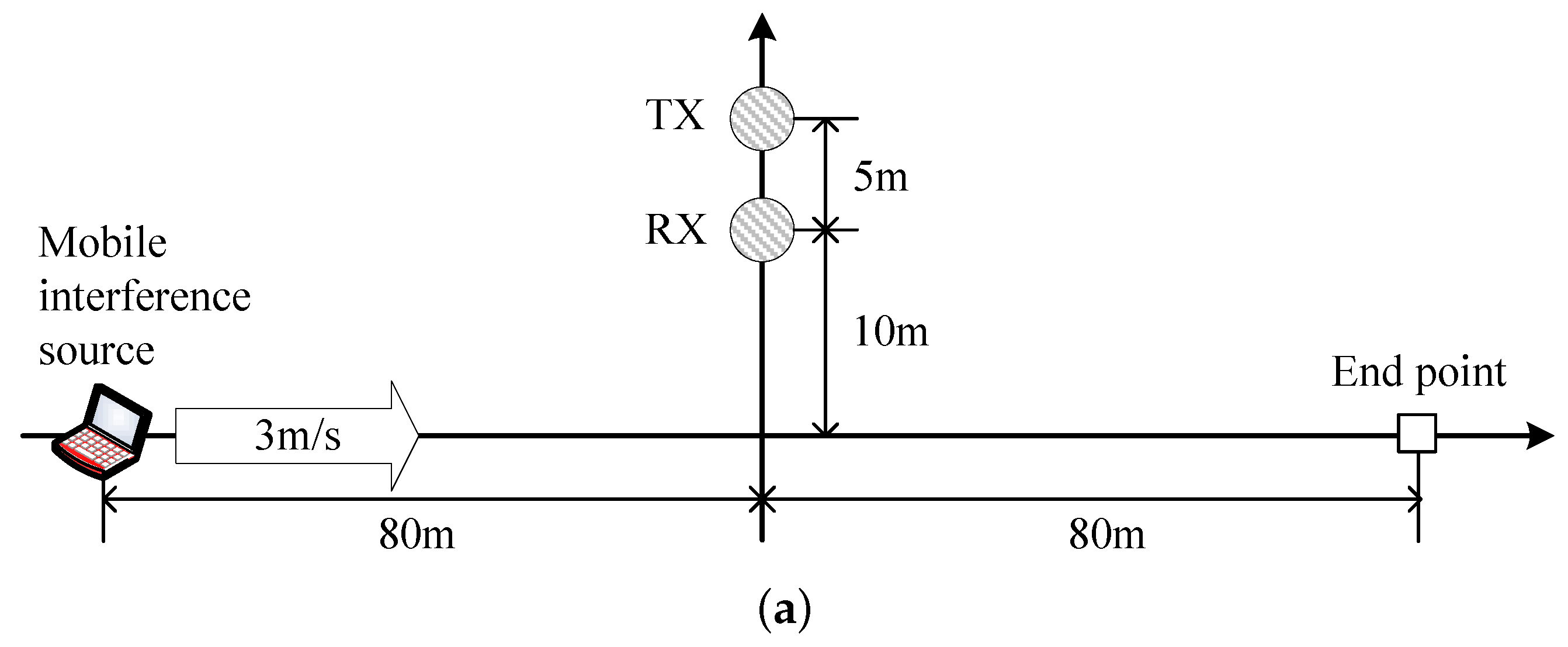
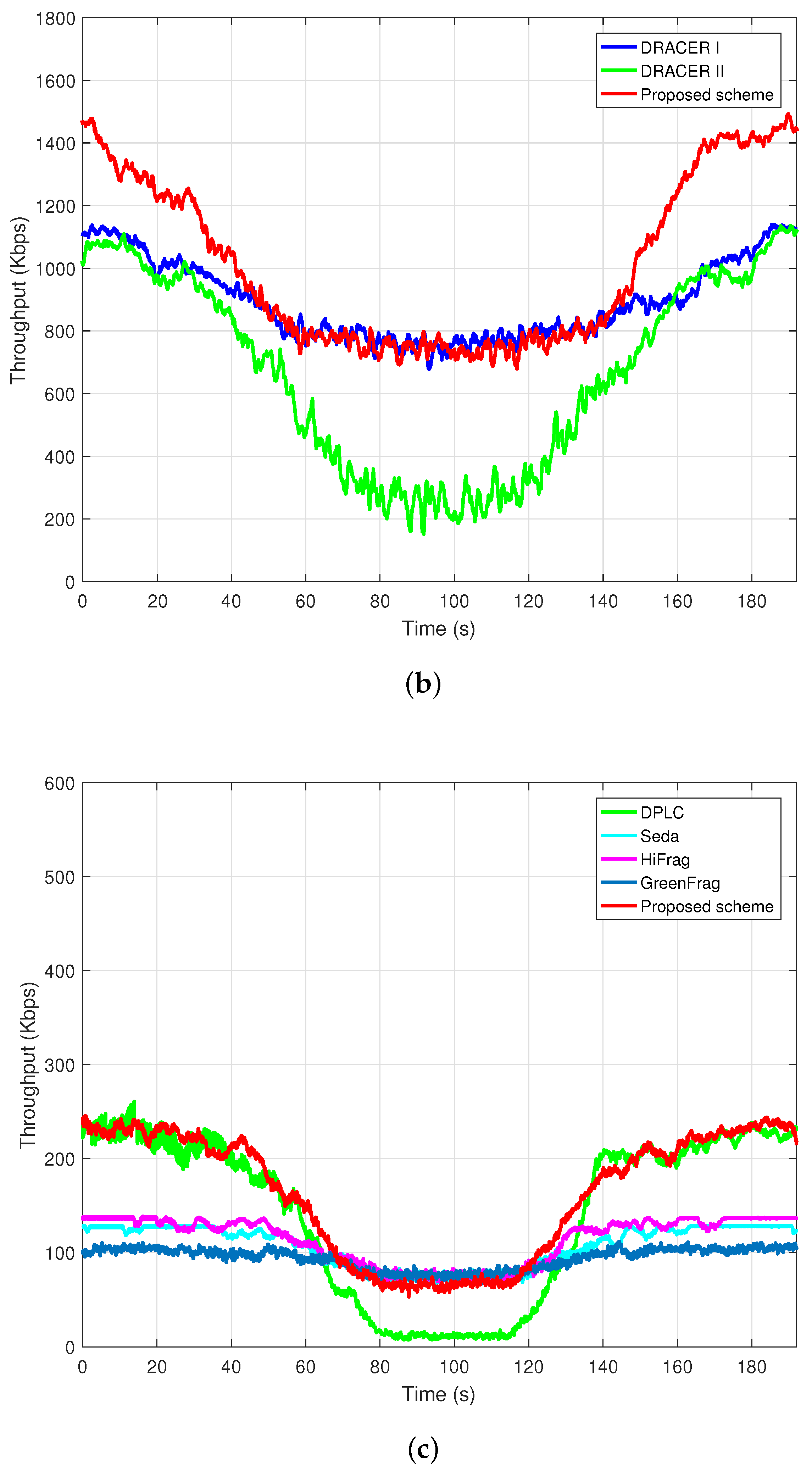
Figure 10b,c depicts the throughput in the presence of the interference signal with
and a mobility of 3 km/h, as illustrated in
Figure 10a, where the SNR slowly changes with a value of 35∼40 dB, but the SINR changes from −20 to 20 dB when the maximum transmission rate is limited to 2 Mbps and 250 Kbps, respectively.
Figure 10b depicts the performance of the proposed scheme and DRACER since they outperform the other schemes. It can be seen that DRACER I outperforms DRACER II, which is mainly because it keeps the highest rate indifferently from the transmission failure. When the SNR is not high enough to employ the highest rate, however, DRACER I may not outperform DRACER II (as shown in
Figure 7). It can also be seen that the proposed scheme outperforms DRACER I and II by adjusting both the transmission rate and the payload size, maximally exploiting the white space of the interference signal. The performance gap between the proposed scheme and DRACER I increases as the SNR decreases.
Figure 10c depicts the performance of the proposed scheme without adjustment of the transmission rate, DPLC and the PPR schemes. It can be seen from
Figure 10c that DPLC provides poor throughput performance, which is mainly due to the slow adaptation of the payload size. It can also be seen that the performance of PPR schemes is limited mainly due to the use of a fixed frame structure and small maximum payload size. It can also be seen that the proposed scheme outperforms the other schemes, which is mainly due to the fast adaptation of the payload size with a large maximum payload size. Note that it may not be easy for the PPR schemes to increase the maximum payload size since the computational complexity may considerably increase as the number of blocks for the packet partitioning increases.