Opportunistic Mobility Support for Resource Constrained Sensor Devices in Smart Cities
Abstract
:1. Introduction
- We propose, develop, and validate EAP-Swift, an Extensible Authentication Protocol (EAP)-based, lightweight sensor authentication protocol specifically designed to meet the aforementioned requirements on both security and lightweight implementation;
- We propose and validate the use of a tree-based Authentication, Authorization and Accounting (AAA) infrastructure for the authentication of mobile sensors. To the best of our knowledge, we are the first to apply evaluate this AAA infrastructure in the area of sensor mobility;
- We propose, develop, and validate a handoff mechanism that facilitates handoffs between wireless sensor gateways based on signal strength and network latency; and
- We evaluate EAP-Swift and the handoff mechanism through real-life test cases in a smart city environment and in a Long Term Evolution (LTE) radio environment in an anechoic radio test chamber.
2. Background and Problem Definition

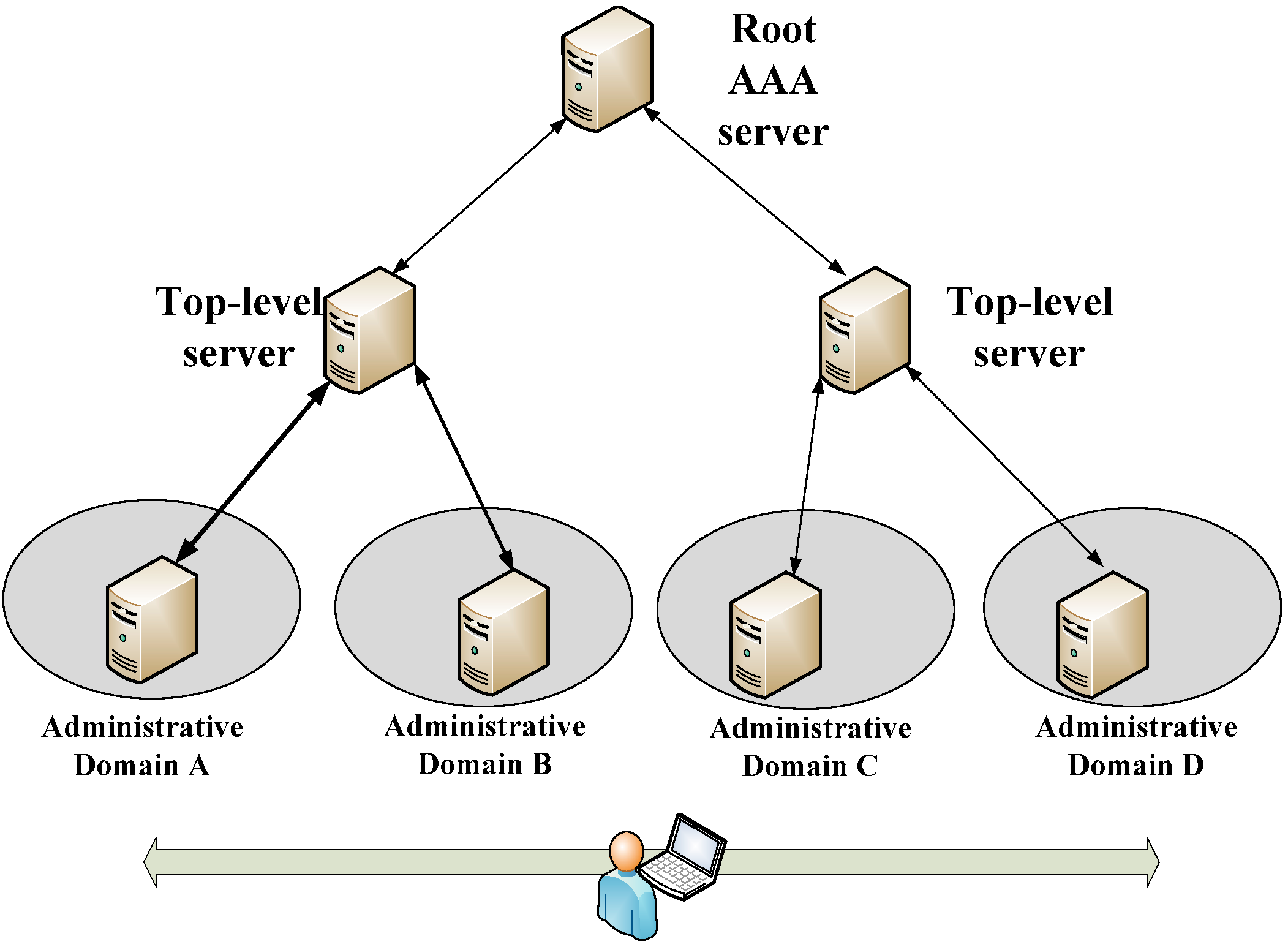
Problem Definition
3. Related Work
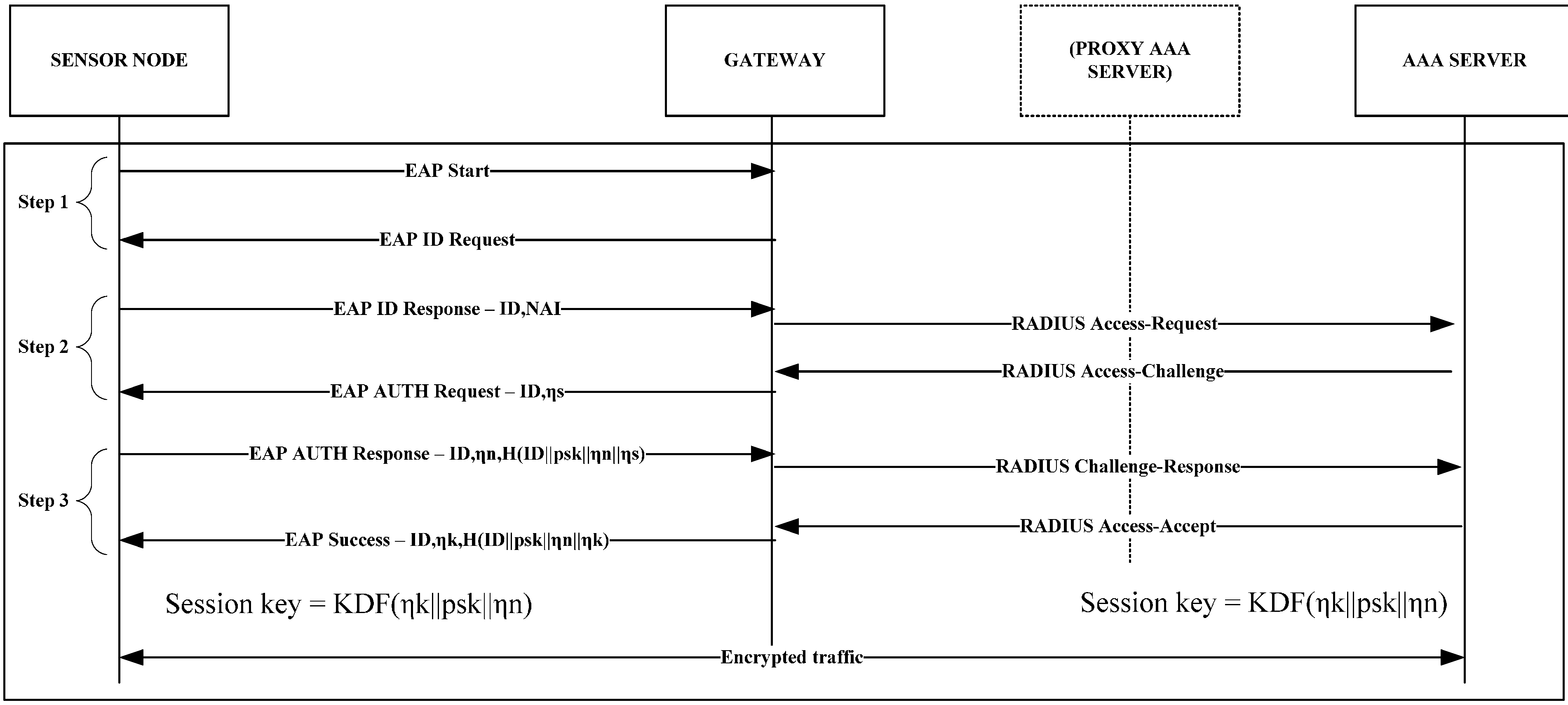
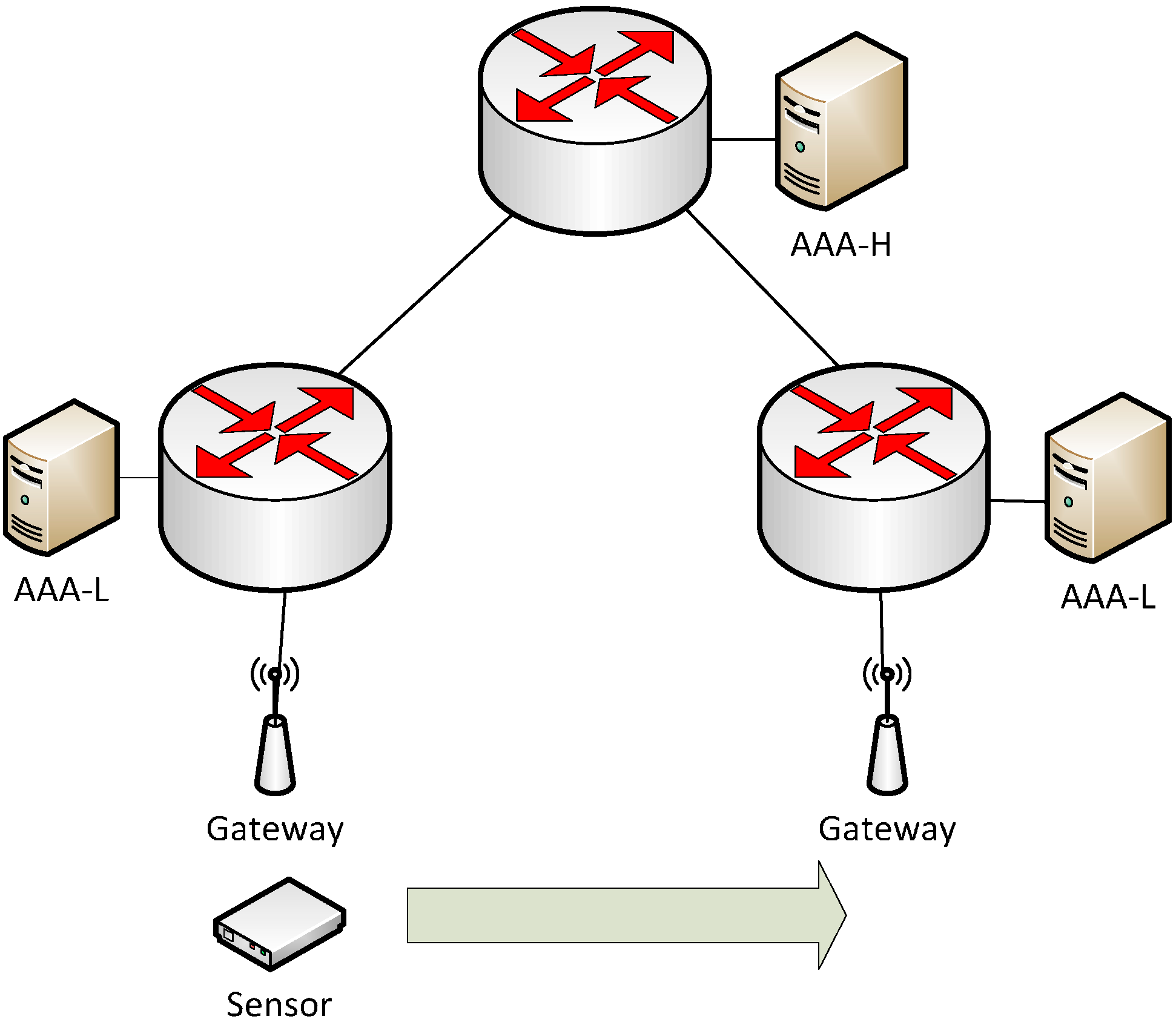
4. Proposed Sensor Authentication and Mobility Protocol
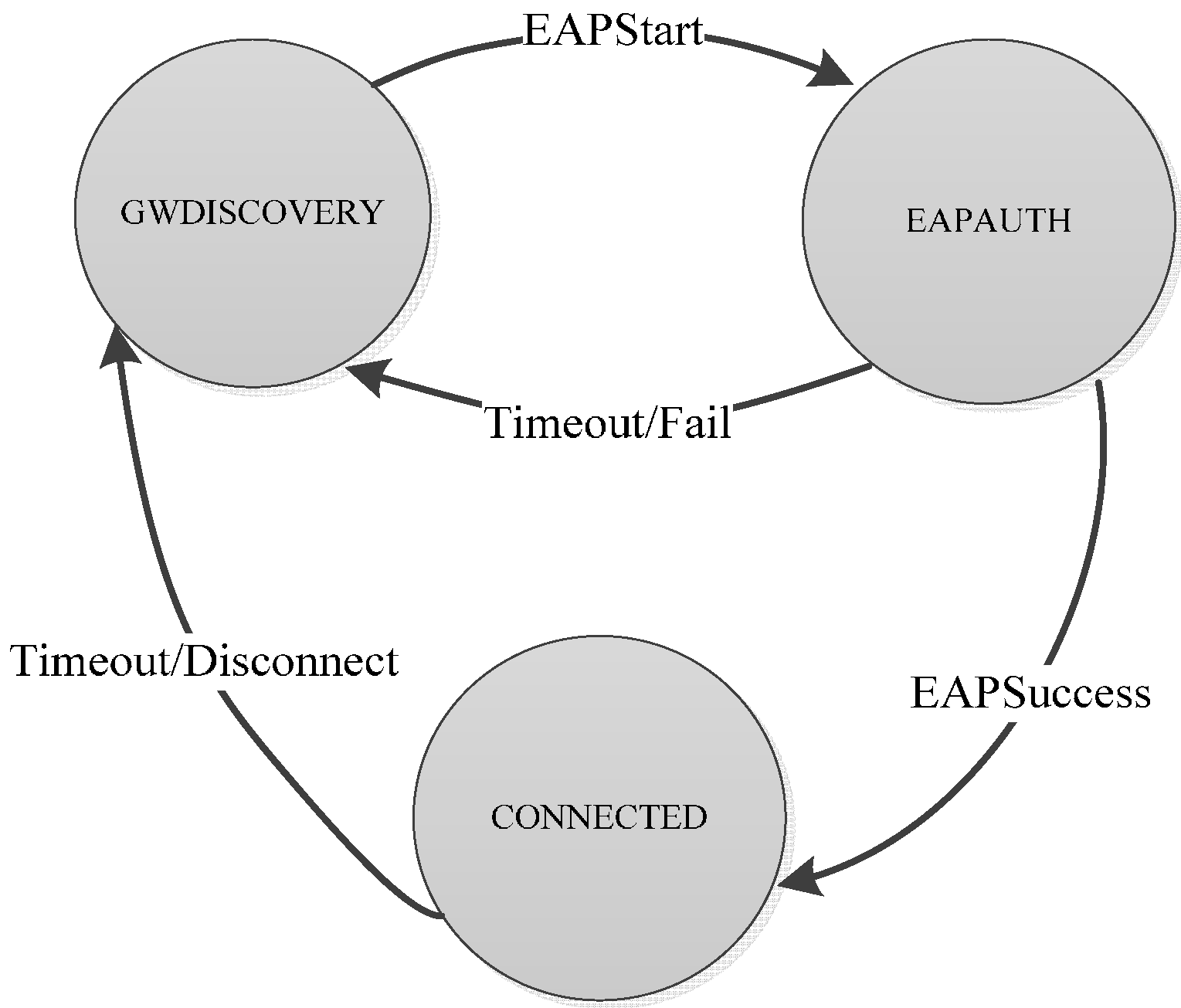
4.1. EAP-Swift
4.2. Handoff Mechanism
| Algorithm 1 Gateway Selection based on RSSI, RTT, and Jitter |
| Input: Candidate gateways, I |
| Initialization: |
| Using RSSI, RTT, and Jitter, discover I; |
| 1 foreach (i ϵ I) do |
| 2 | if RSSIi > Threshold(RSSI) then |
| 3 | | send EAP-Start to i |
| 4 | | measure and update RTT/Jitter for i |
| 5 | end |
| 6 end |
| 7 foreach (i ϵ I) do |
| 8 | compute PVi |
| 9 | if PVi > PVicurr then |
| 10 | handoff to i |
| 11 | zero PVicurr to eliminate ping-pong effect |
| 12 | else |
| 13 | | keep connected to the current gateway icurr |
| 14 end |
4.3. Prototype Implementation
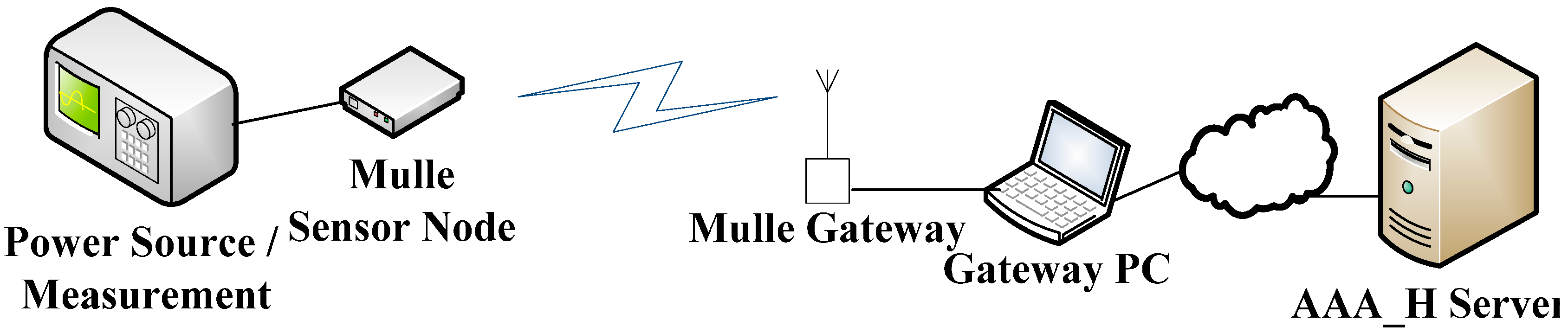
5. Results Analysis
5.1. Evaluation of EAP-Swift
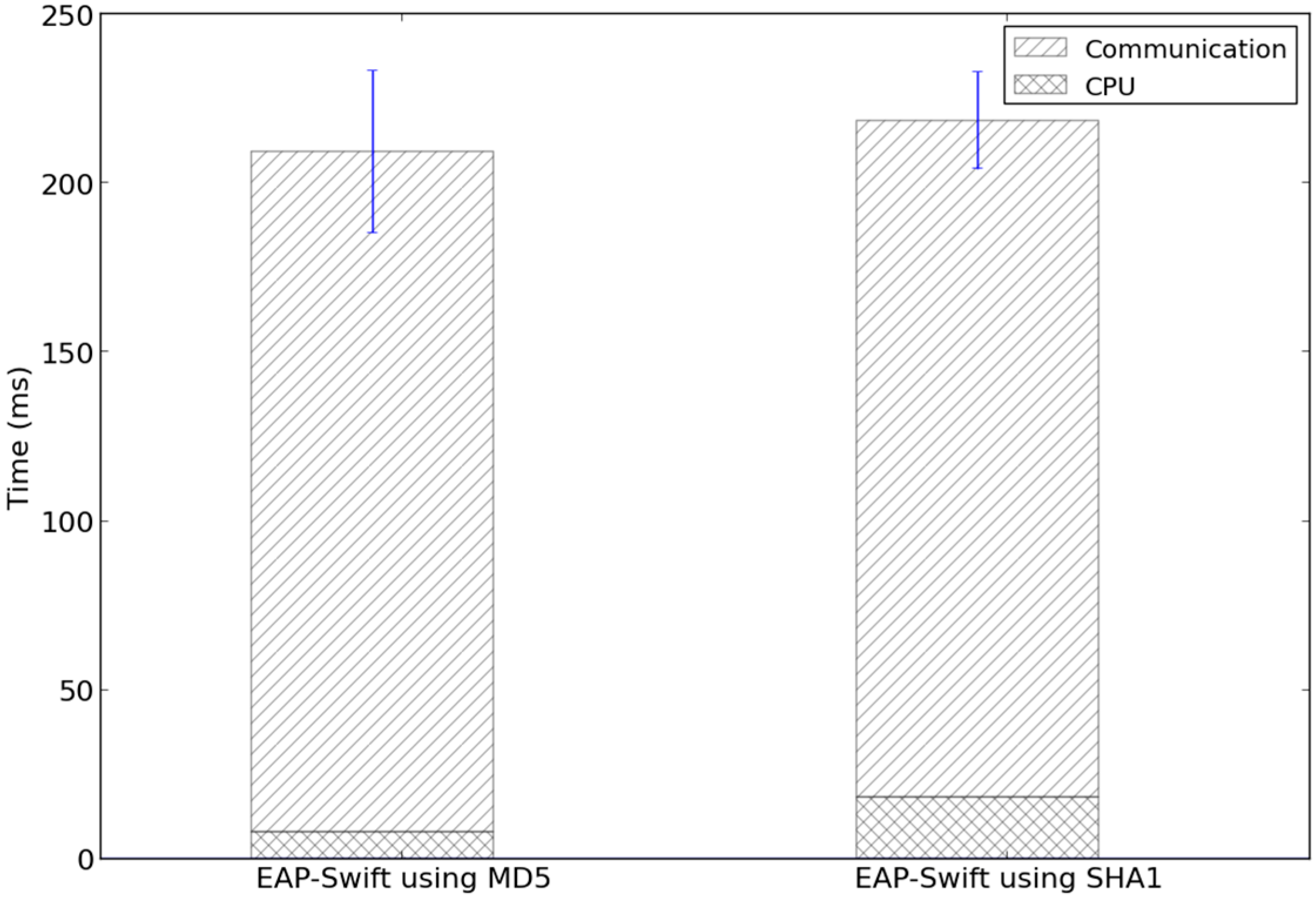
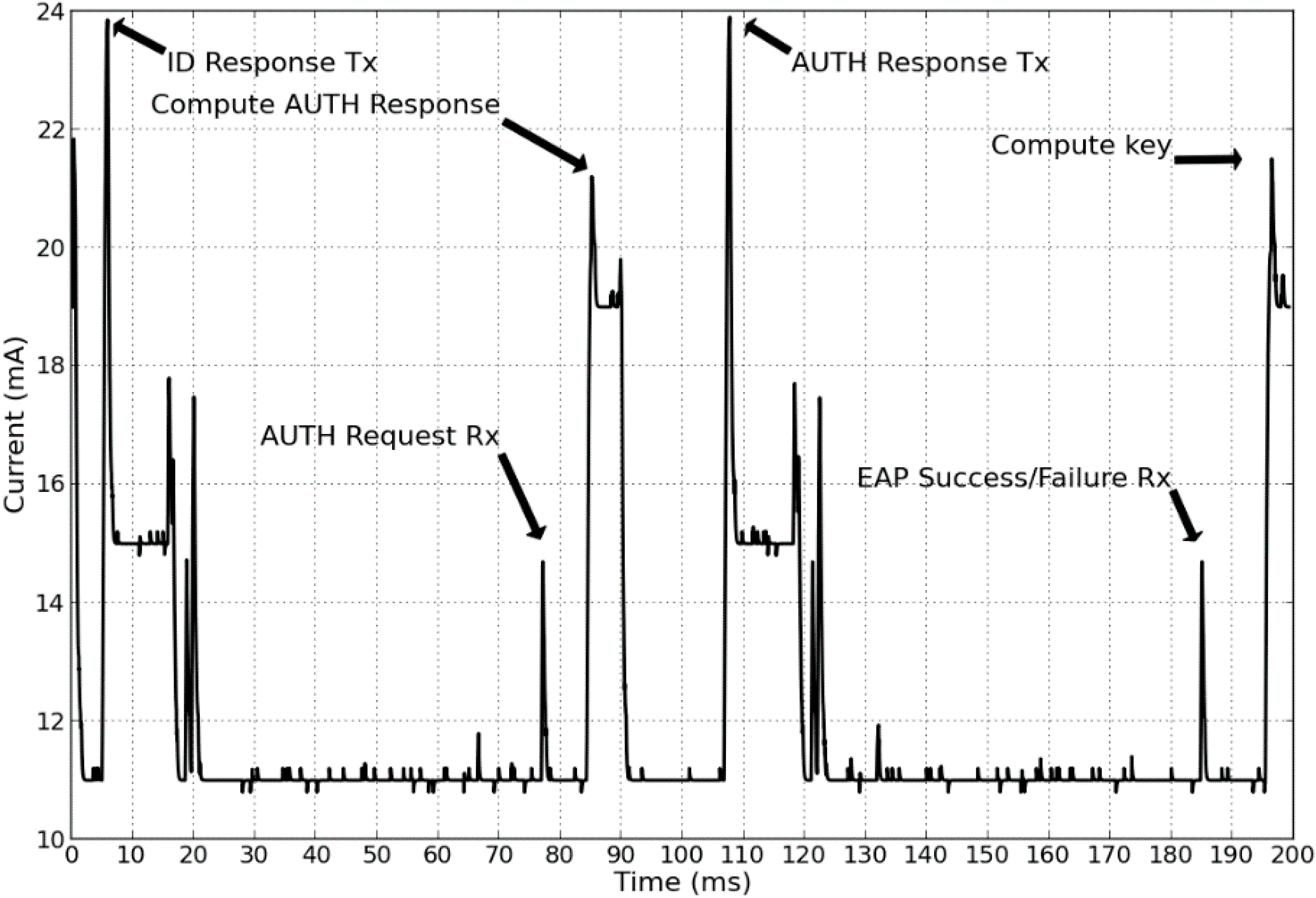
5.2. Evaluation of the Handoff Mechanism
| Forced Handoff | Normal Handoff | |||
|---|---|---|---|---|
| Packet Loss | Application Down Time | Packet Loss | Application Down Time | |
| (packets) | (ms) | (packets) | (ms) | |
| 100 bytes/s | 5 | 5000 | 0 | 0 |
| 1 kbyte/s | 20 | 2000 | 6 | 600 |
5.3. Evaluation in City Environments
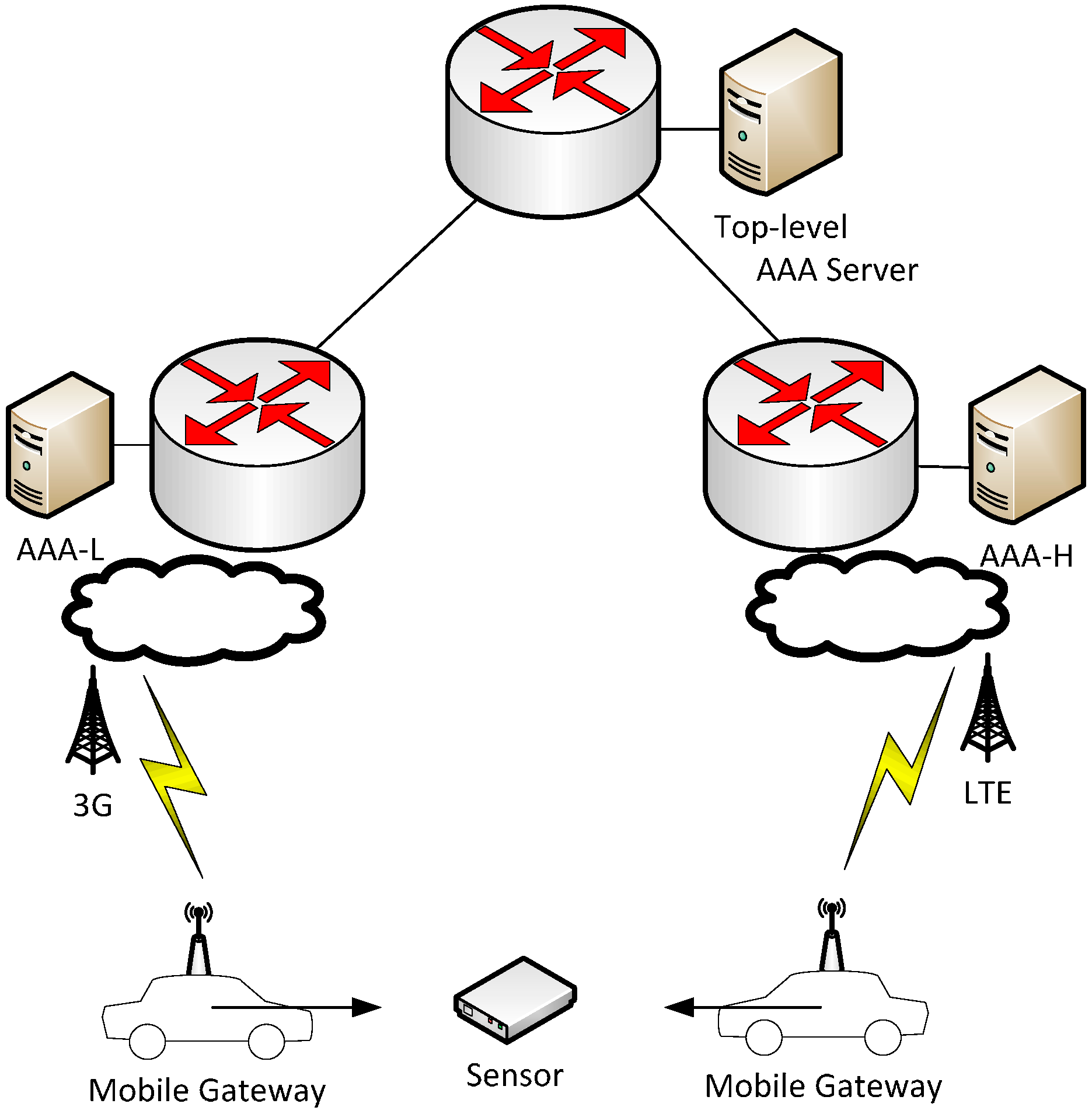
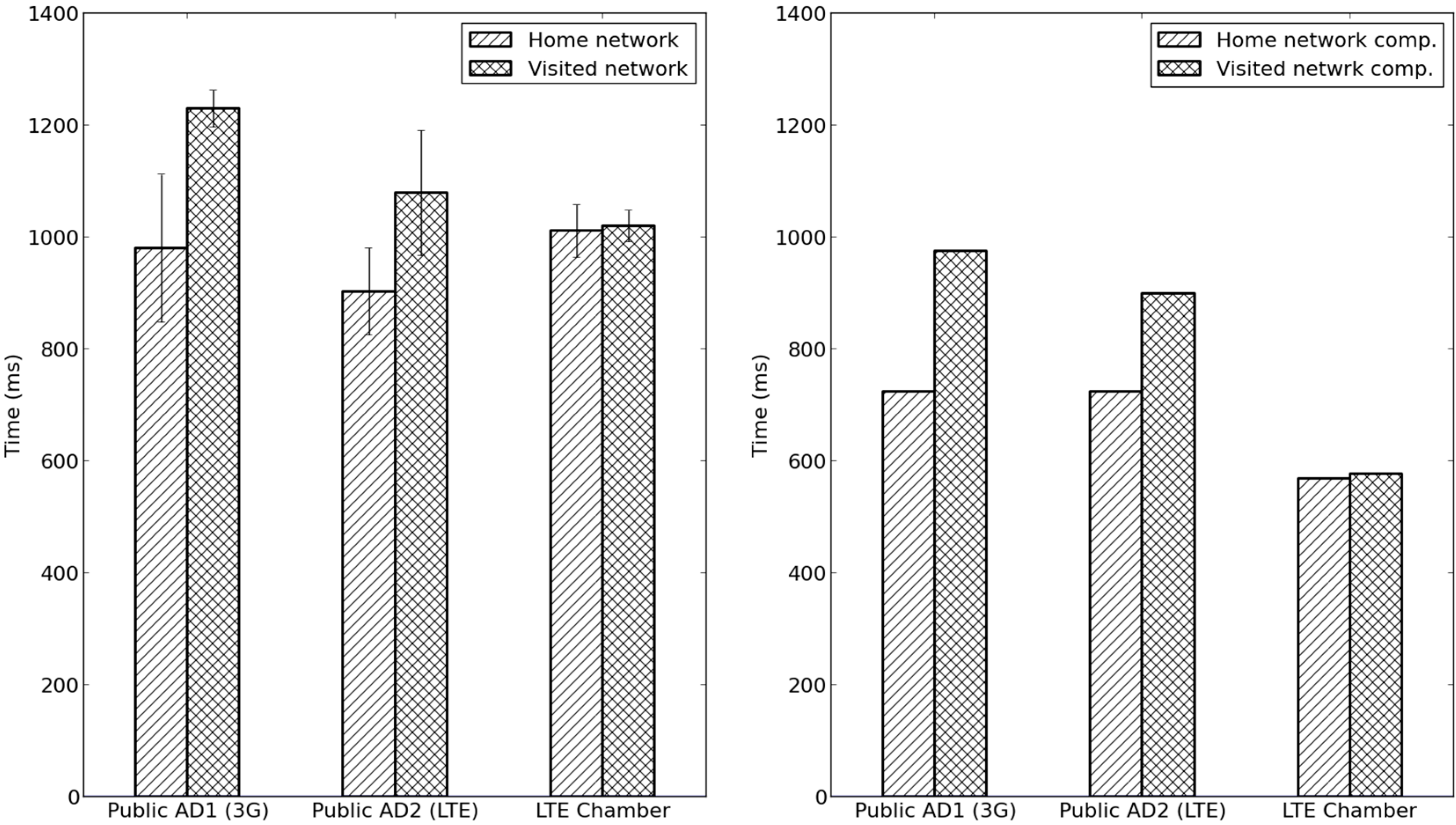
| RTT in Access Network | RTT to AAA Server | |||
|---|---|---|---|---|
| Average RTT | Standard Deviation | Average RTT | Standard Deviation | |
| (ms) | (ms) | (ms) | (ms) | |
| AD1 (3G uplink) | 308.6 | 76.1 | 435.8 | 268.7 |
| AD2 (LTE uplink) | 114.0 | 82.3 | 122.9 | 147.2 |
| LTE Chamber | 50.2 | 19.3 | 72.4 | 2.9 |
5.4. Numerical Analysis
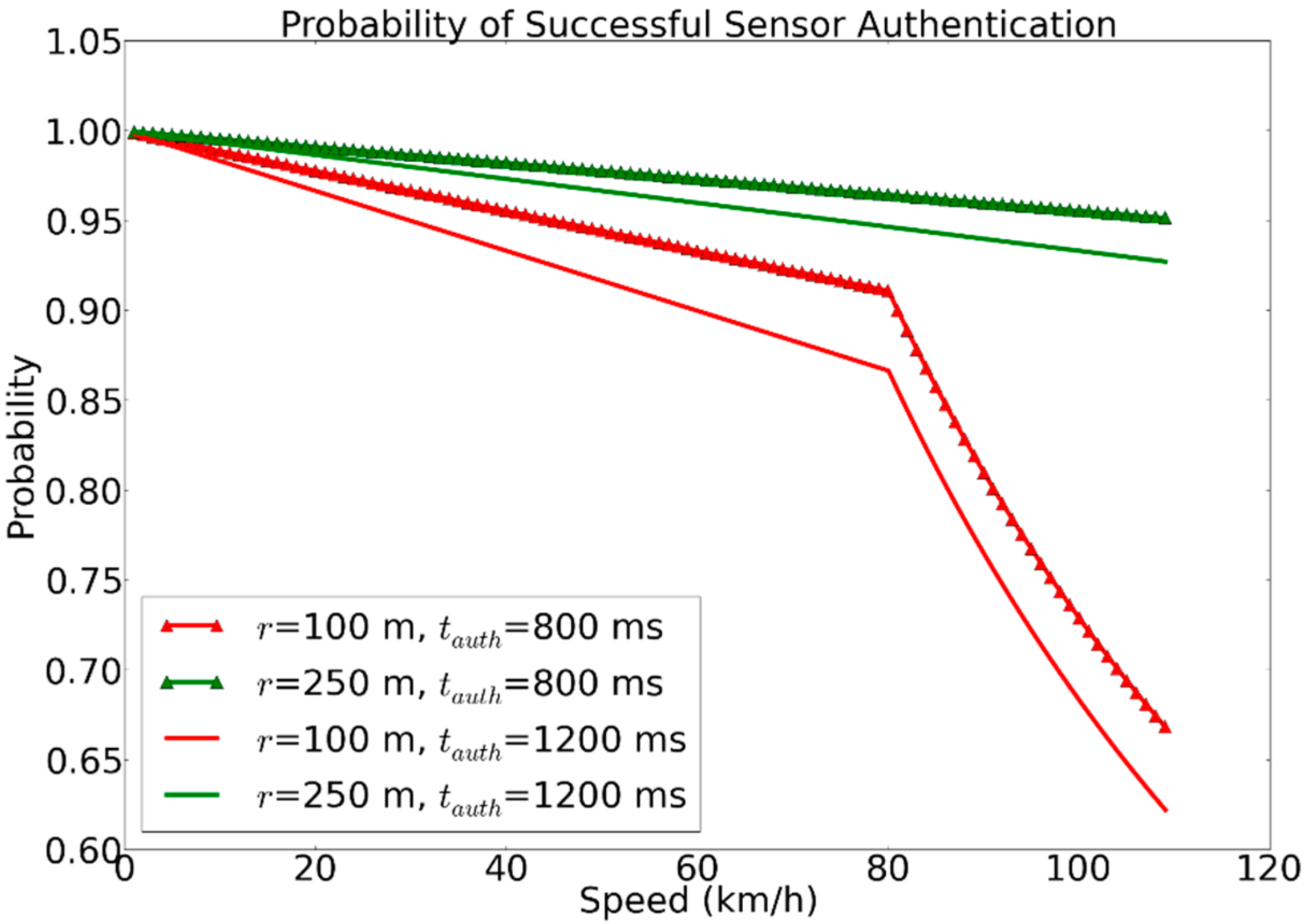
5.5. Scalability Analysis
| Entries in Sensor Database | Authentication Carried Out at AAA_H | Authentication Carried Out via Proxy Server | ||
|---|---|---|---|---|
| Authentications per Second | AAA_H CPU | Authentications per Second | Proxy CPU | |
| 1000 | 1218 | 97% | 791 | 20% |
| 10,000 | 1132 | 95% | 584 | 15% |
| 100,000 | 1080 | 94% | 581 | 15% |
| 1,000,000 | 1073 | 94% | 582 | 14% |
5.6. Discussion
6. Conclusions and Future Work
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Kwon, J.W.; Park, Y.M.; Koo, S.J.; Kim, H. Design of air pollution monitoring system using ZigBee networks for ubiquitous-city. In Proceedings of the International Conference on Convergence Information Technology, Gyeongju, Korea, 21–23 November 2007; pp. 1024–1031.
- Hostettler, R.; Birk, W.; Nordenvaad, M. Surface Mounted Vehicle Property Sensing for Cooperative Vehicle Infrastructure Systems. In Proceedings of the World Congress and Exhibition on Intelligent Transport Systems and Services, Stockholm, Sweden, 21–25 September 2009.
- Hancke, G.P.; de Carvalho e Silva, B.; Hancke, G.P., Jr. The Role of Advanced Sensing in Smart Cities. Sensors 2013, 13, 393–425. [Google Scholar] [CrossRef]
- ZigBee Alliance, ZigBee Specifications, Version 1.0. Available online: http://www3.nd.edu/~mhaenggi/ee67011/zigbee.pdf (accessed on 28 February 2015).
- Zanella, A.; Bui, N.; Castellani, A.P.; Vangelista, L.; Zorzi, M. Internet of Things for smart cities. IEEE Internet Things J. 2014, 1, 22–32. [Google Scholar] [CrossRef]
- Bellavista, P.; Cardone, G.; Corradi, A.; Foschini, L. Convergence of MANET and WSN in IoT Urban Scenarios. IEEE Sens. J. 2013, 13, 3558–3567. [Google Scholar] [CrossRef]
- Zorzi, M.; Gluhak, A.; Lange, S.; Bassi, A. From Today’s Intranet of Things to a Future Internet of Things: A Wireless and Mobility related view. IEEE Wirel. Commun. 2010, 17, 44–51. [Google Scholar] [CrossRef]
- Eisenman, S.; Lane, N.; Campbell, A. Techniques for Improving Opportunistic Sensor Networking Performance. In Proceedings of the International Conference on Distributed Computing in Sensor Systems (DCOSS’08), Santorini, Greece, 11–14 June 2008.
- Oualha, N.; Olivereau, A.; Wehner, M.; Bartzsch, T.; Burggraf, D.; Zeisberg, S.; Gheorghe, L.; Lusanschi, E.; Tudose, D. AAA-based infrastructure for industrial wireless sensor networks. In Proceedings of the Future Network Mobile Summit, Berlin, Germany, 4–6 July 2012; pp. 1–8.
- Kopets, H. Design Principles for Embedded Applications, Chapter 13: Internet of Things, Real-Time Systems; Springer: Berlin, Germany, 2011; pp. 307–323. [Google Scholar]
- Kortuem, G.; Fitton, F.K.D.; Sundramoorthy, V. Smart objects as building blocks for the Internet of things. IEEE Internet Comput. 2009, 14, 44–51. [Google Scholar] [CrossRef]
- Perera, C.; Zaslavsky, A.; Christen, P.; Georgakopoulos, D. Sensing as a service model for smart cities supported by internet of things. Trans. Emerg. Telecommun. Technol. 2014, 25, 81–93. [Google Scholar] [CrossRef]
- Simplicio, M.A., Jr.; Barreto, P.S.L.M.; Margi, C.B. A Survey on Key Management Mechanisms for Distributed Wireless Sensor Networks, Computer Networks; Elsevier: Amsterdam, Holland, 2010; Volume 54, pp. 2591–2612. [Google Scholar]
- Yeh, H.L.; Chen, T.H.; Liu, P.C.; Kim, T.H.; Wei, H.W. A Secured Authentication Protocol for Wireless Sensor Networks Using Elliptic Curves Cryptography. Sensors 2011, 11, 4767–4779. [Google Scholar] [CrossRef] [PubMed]
- Sense Smart City Project. Available online: http://www.sensesmartcity.org (accessed on 9 December 2014).
- EduRoam. Available online: http://www.eduroam.org (accessed on 15 November 2014).
- Rigney, C. (Ed.) Remote Authentication Dial in User Service (RADIUS); IETF, RFC2865: Pleasanton, CA, USA, 2000.
- Z-Wave, Z-Wave Protocol Overview, v. 4. Available online: http://wiki.ase.tut.fi/courseWiki/images/9/94/SDS10243_2_Z_Wave_Protocol_Overview.pdf (accessed on 28 February 2015).
- Bluetooth SIG, Bluetooth Baseband Specification Version I.OB. Available online: http://www.bluetooth.com (accessed on 2 November 2014).
- Hui, J. (Ed.) Compression Format for IPv6 Datagrams over IEEE 802.15.4-Based Networks; IETF, RFC6282: San Francisco, CA, USA, 2011.
- Perkins, C.; Johnson, D.; Arkko, J. Mobility Support in IPv6; IETF, RFC-6275: Naperville, IL, USA, 2011. [Google Scholar]
- Haw, R.; Cho, E.; Hong, C.; Lee, S. A 6LoWPAN sensor node mobility scheme based on proxy mobile IPv6. IEEE Trans. Mob. Comput. 2012, 11, 2060–2072. [Google Scholar] [CrossRef]
- Silva, R.; Silva, J.S.; Boavida, F. A proposal for proxy-based mobility in WSNs. Comput. Commun. 2012, 35, 1200–1216. [Google Scholar] [CrossRef]
- Chatzigiannakis, I.; Fischer, S.; Koninis, C.; Mylonas, G.; Pfisterer, D. WISEBED: An open large-scale wireless sensor network testbed. In Proceedings of the 1st International Conference on Sensor Networks Applications, Experimentation and Logistics, Athens, Greece, 25 September 2009.
- Sanchez, L.; Muñoz, L.; Galache, J.A.; Sotres, P.; Santana, J.R.; Gutierrez, V.; Ramdhany, R.; Gluhak, A.; Krco, S.; Theodoridis, E.; et al. SmartSantander: IoT experimentation over a smart city testbed. Comput. Netw. 2014, 61, 217–238. [Google Scholar] [CrossRef]
- Alim, M.A.; Sarikaya, B. EAP-Sens: A Security Architecture for Wireless Sensor Networks. In Proceedings of the 4th International Wireless Internet Conference (WICON’08), Maui, HI, USA, 17–19 November 2008.
- Clancy, T.; Tschofenig, H. EAP Generalized Pre-Shared Key; IETF, RFC5433: College Park, MD, USA, 2009. [Google Scholar]
- Cheikhrouhou, O.; Laurent, M.; Abdallah, A.B.; Jemaa, M.B. An EAP-EHash authentication method adapted to resource constrained terminals. Ann. Telecommun. 2009, 65, 271–284. [Google Scholar] [CrossRef]
- Jovanov, E.; O’Donnel Lords, A.; Raskovic, D.; Cox, P.G.; Adhami, R.; Andrasik, F. Stress monitoring using a distributed wireless intelligent sensor system. IEEE Eng. Med. Biol. Mag. 2003, 22, 49–55. [Google Scholar] [CrossRef] [PubMed]
- Becker, M.; Wenning, B.L.; Görg, C.; Jedermann, R.; Timm-Giel, A. Logistic applications with wireless sensor networks. In Proceedings of the 6th Workshop on Hot Topics in Embedded Networked Sensors (HotEMNETS’10), Killarney, Ireland, 28–29 June 2010; pp. 1–5.
- Hu, S.C.; Wang, Y.C.; Huang, C.Y.; Tseng, Y.C. Measuring air quality in city areas by vehicular wireless sensor networks. J. Syst. Softw. 2011, 84, 2005–2012. [Google Scholar] [CrossRef]
- Sarma, H.K.D.; Kar, A.; Mall, R. Energy efficient routing protocol for wireless sensor networks with node and sink mobility. In Proceedings of the IEEE Sensors Applications Symposium, San Antonio, TX, USA, 22–24 February 2011; pp. 239–243.
- Benslimane, A.; Taleb, T.; Sivaraj, R. Dynamic clustering-based adaptive mobile gateway management in integrated VANET C 3G Heterogeneous wireless networks. IEEE J. Sel. Areas Commun. 2011, 29, 559–570. [Google Scholar] [CrossRef]
- Granlund, D.; Andersson, K.; Brännström, R. Estimating network performance using low impact probing. In Proceedings of the 1st Workshop on Wireless Broadband Access for Communities and Rural Developing Regions (WIRELESS4D’08, co-located with M4D 2008), Karlstad, Sweden, 11–12 December 2008.
- Rivest, R. The MD5 Message-Digest Algorithm; IETF, RFC1321: Cambridge, MA, USA, 1992. [Google Scholar]
- Eastlake, D.; Jones, P. US Secure Hashing Algorithm 1 (SHA1); IETF, RFC3174: Milford, MA, USA, 2001. [Google Scholar]
- Eistec, A.B. Available online: http://www.eistec.se (accessed on 8 August 2014).
- Renesas Electronics. Available online: http://www.renesas.eu/ (accessed on 9 August 2014).
- Atmel Corp. Available online: http://www.atmel.com/ (accessed on 10 December 2014).
- Levis, P.; Madden, S.; Polastre, J.; Szewczyk, R.; Whitehouse, K.; Woo, A.; Gay, D.; Hill, J.; Welsh, M.; Brewer, E.; et al. Tiny OS: An Operating System for Sensor Networks, Ambient Intelligence; Springer: Berlin, Germany, 2005. [Google Scholar]
- Deutsch, L.P. Independent Implementation of MD5 (RFC1321), Aladdin Enterprises, 2002. Available online: http://fedoraproject.org/w/uploads/2/22/Deutsch-md5.c (accessed on 1 December 2014).
- Jones, P.E. Secure Hashing Algorithm (SHA1), A C and C++ Implementation. Available online: http://www.packetizer.com/security/sha1/ (accessed on 22 November 2014).
- FreeRadius. Available online: http://www.freeradius.org (accessed on 10 August 2014).
- Tiny OS. Available online: http://www.tinyos.net (accessed on 12 August 2014).
- Raspberry Pi. Available online: http://www.raspberrypi.org (accessed on 10 October 2014).
- Ascom Network Testing. Available online: http://www.ascom.com/nt/ (accessed on 9 October 2014).
- Vadeby, A.; Forsman, Å. Evaluation of Speed Limits in Sweden: A Sample Survey; Taylor & Francis: Philadelphia, PA, USA, 2014. [Google Scholar]
- Granlund, D.; Ahlund, C. A Scalability Study of AAA Support in Heterogeneous Networking Environments with Global Roaming Support. In Proceedings of the 10th International Conference on Trust, Security and Privacy in Computing and Communications, Changsha, China, 16–18 November 2011.
- Mitra, K.; Saguna, S.; Åhlund, C.; Granlund, D. M2C2: A Mobility Management System for Mobile Cloud Computing. In Proceedings of the IEEE Wireless Communications and Networking Conference (WCNC2015), New Orleans, LA, USA, 9–12 March 2015.
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Granlund, D.; Holmlund, P.; Åhlund, C. Opportunistic Mobility Support for Resource Constrained Sensor Devices in Smart Cities. Sensors 2015, 15, 5112-5135. https://doi.org/10.3390/s150305112
Granlund D, Holmlund P, Åhlund C. Opportunistic Mobility Support for Resource Constrained Sensor Devices in Smart Cities. Sensors. 2015; 15(3):5112-5135. https://doi.org/10.3390/s150305112
Chicago/Turabian StyleGranlund, Daniel, Patrik Holmlund, and Christer Åhlund. 2015. "Opportunistic Mobility Support for Resource Constrained Sensor Devices in Smart Cities" Sensors 15, no. 3: 5112-5135. https://doi.org/10.3390/s150305112
APA StyleGranlund, D., Holmlund, P., & Åhlund, C. (2015). Opportunistic Mobility Support for Resource Constrained Sensor Devices in Smart Cities. Sensors, 15(3), 5112-5135. https://doi.org/10.3390/s150305112






