Securing Health Sensing Using Integrated Circuit Metric
Abstract
:1. Introduction
- In this system the ICMetric technology is utilized to generate keys based on the hardware/software characteristics and specification of the device, thereby enabling device verification. This provides an effective means to address the issues related to storage of key, thereby safeguarding against the major threat of key compromise. In our work we highlight how such a device identification can be generated for a health sensor using its physical characteristics, e.g., from the Micro Electro Mechanical Systems (MEMS) accelerometer. In addition to the accelerometer credentials, we identify a range of other features that also form part of the device identification.
- In this system we propose a secure admission control process as a core component. This part of the design is aimed at recognizing each entity, which is part of the application. It recognizes each patient based on its allocated sensors, and the health professionals based on their end point device. So this part authenticates, authorizes and evaluates each entity prior to secure communication of the health data. However, at no point is the ICMetric value sent over the channel or even communicated to others.
- A challenge with the generated ICMetric is the entropy and length of the generated secret value. The proposed design generates a strong symmetric key based on the communicating parties’ device ICMetric. This generates symmetric key facilitates in secure end-to-end communications.
1.1. Related Work
2. Integrated Circuit Metric (ICMetric)
2.1. Calibration Phase
2.2. Operation Phase
2.3. Generating the Device ICMetric
3. Types of Health Sensing Devices
- Environment—sensors designed to detect temperature, humidity, pressure, light, noise etc.
- Device—some sensors are designed to sense physiological data directly from the human body, while other sensors use images like facial features, eye movement to measure data.
- User—sensors designed to detect user specific data like location, acceleration, heart rates, EMI, body temperature, etc.
- Interaction—sensors designed to interact with multiple device through diverse mediums like RFID, Bluetooth, Ethernet etc. Pervasive sensors allow multiple sensors to interact with each other.
3.1. MEMS Accelerometer
| Sensor | Bias |
|---|---|
| Accelerometer | Linear acceleration bias |
| Gyroscope | Linear gyroscopic bias |
| Touchscreen | Screen misalignment |
| Camera | Camera noise pattern |
| GPS | Clock skew |
3.2. Accelerometer Offset Measurement and Device Feature Establishment

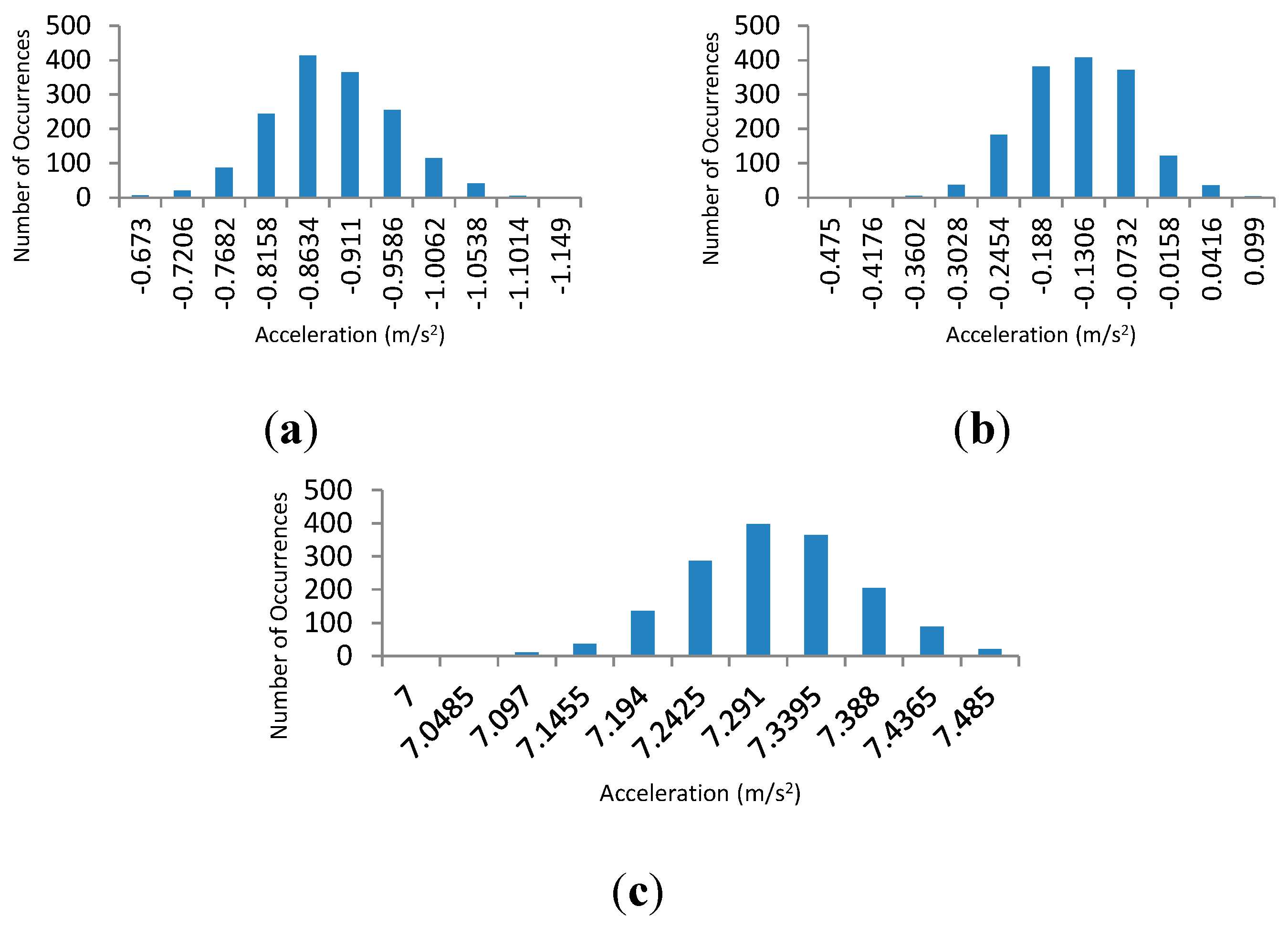
| Device A | Device B | ||
|---|---|---|---|
| x-axis | Confidence Interval | (−0.919,−0.912) | (−0.281,−0.298) |
| Standard Deviation | 0.071 | 0.0693 | |
| Inter Quartile Range | −0.285 | −0.473 | |
| Mean | −0.916 | −0.292 | |
| Skewness | −1.190 | 0.0229 | |
| y-axis | Confidence Interval | (−0.160,−0.167) | (−9.248,−9.271) |
| Standard Deviation | 0.074 | 0.0678 | |
| Inter Quartile Range | 0.344 | 0.411 | |
| Mean | −0.163 | −9.266 | |
| Skewness | 0.072 | 0.0685 | |
| z-axis | Confidence Interval | (7.284,7.276) | (−0.598,−0.621) |
| Standard Deviation | 0.075 | 0.053 | |
| Inter Quartile Range | 0.291 | 0.0728 | |
| Mean | 7.280 | −0.615 | |
| Skewness | −31.341 | −1.371 | |
| Resulting ICMetric | −13.286 | −31.5687 |
- Sensor Bluetooth MAC address—a 48 bit MAC address that uniquely identifies each sensor.
- Dongle Bluetooth MAC address—a 48 bit MAC address that uniquely identifies the dongle to which the sensor is connecting.
- Bluetooth radio identification—a 16 bit hexadecimal number that is associated with a device. This identification can be modified which makes it a strong ICMetric candidate.
- Factory lasered 64 bit registration—Every sensor is equipped with a DS-2411 chip [28] which provides the device with a unique identification. This is a single line chip which is factory coded with a serial that can be read for the purpose of identification. The serial number is composed of a CRC, serialization and a family code. The serialization structure is given in the Figure 3:

- Calibration Matrices—it is the role of every sensor to generate readings that are accurate. The calibration is defined by three individual matrices namely the offset vector, sensitivity matrix and alignment matrix. Figure 4 shows a sample set of calibration matrices which can be used to identify a sensor. Here it must be pointed out that the smallest change in the calibration matrices causes a chain of events which results in the wrong ICMetric being generated. When an attacker attempts to guess the calibration matrices, the resulting accelerometer readings will not reflect what was expected from the sensor. This will ultimately result in the wrong ICMetric being generated. The readings are generated following a specific algorithm [29] targeting accelerometer readings and calibrations.
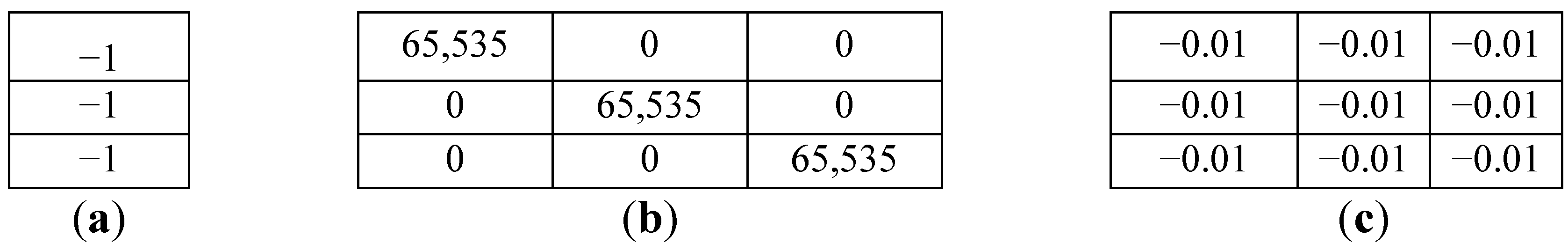
4. Framework Assumptions
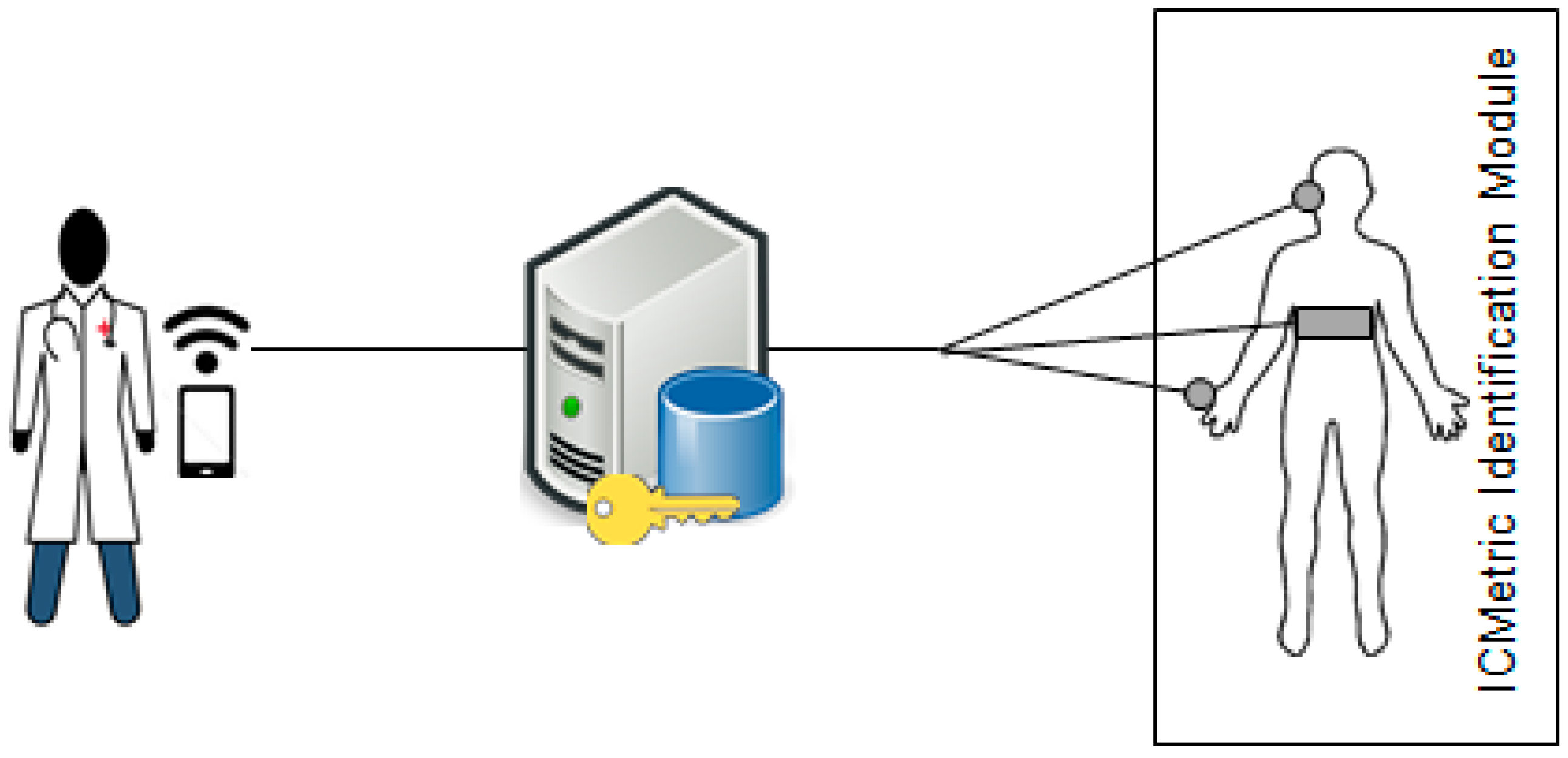
5. The Security Framework
5.1. Secure Admission Control
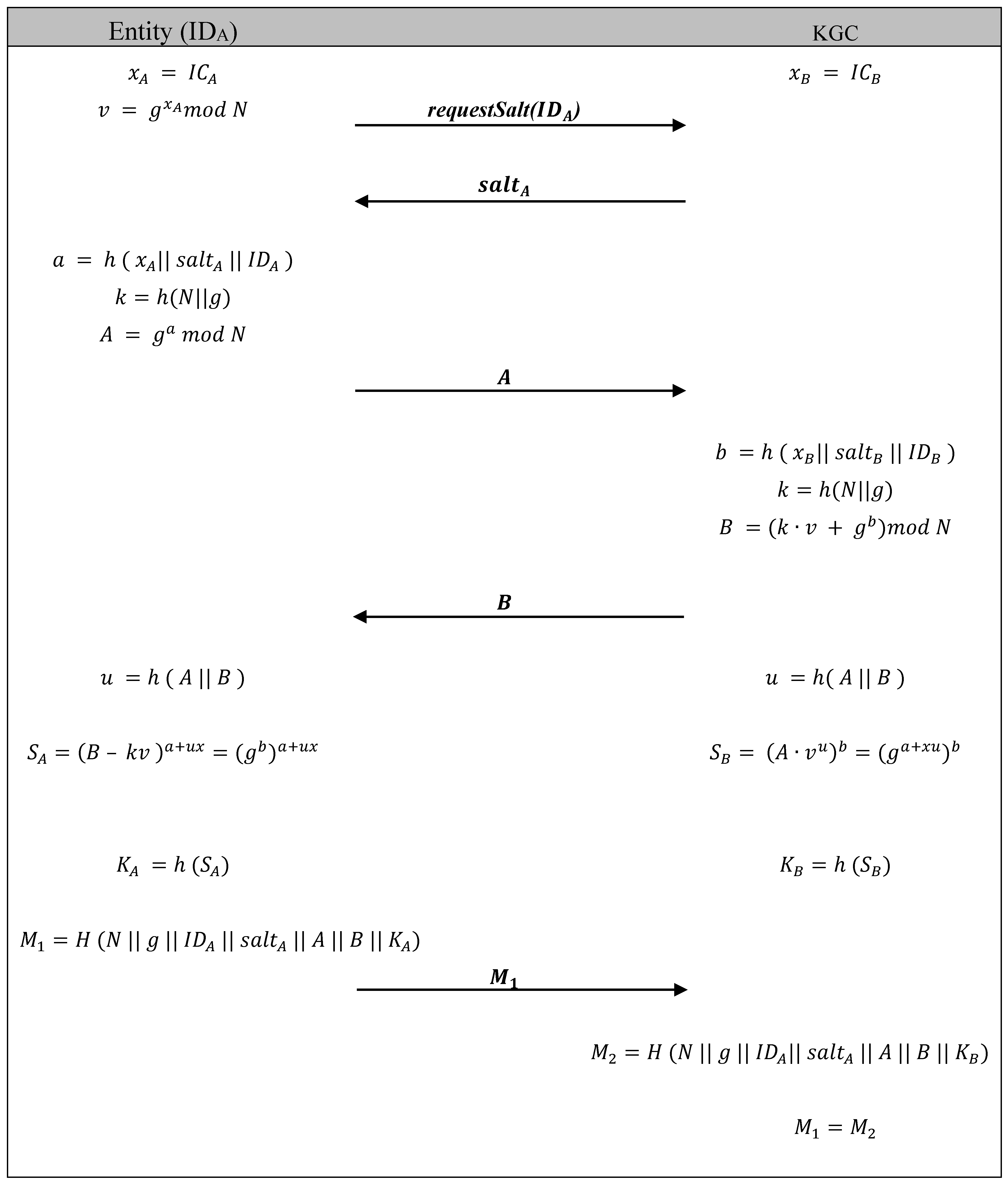
- When an entity wishes to register with the KGC, its necessary credentials are forwarded to a KGC where the registration is digitized.
- Once the entity is registered, the KGC is updated with a unique identification and a 128 bit random per-entity value (so called “salt”).
- A copy of the identification and salt is also provided to the entity for storage.
5.2. Symmetric Cryptographic Module
5.2.1. Strong Symmetric Key Generation
| Symbol | Meaning |
|---|---|
| || | The concatenation operator |
| A large prime number. All computations are performed modulo n | |
| A primitive root modulo (often called a generator) | |
| A random string used as the entity’s and KGC’s salt | |
| The verifier of the entity | |
| ICMetric of entity and KGC respectively | |
| ID of entity and KGC respectively | |
| ICMetric number of entity and KGC respectively | |
| Ephemeral private keys, generated randomly and not publicly revealed | |
| One-way hash function e.g., SHA-256 | |
| Scrambling parameter- and concatenated and hashed | |
| Session keys |
5.2.2. Symmetric Key Authentication
5.2.3. Symmetric Key Encryption/Decryption
6. Implementation
7. Results and Discussion
- Useful heap—heap used by the program over time.
- Extra heap—heap blocks allocated for administration data over the program’s lifetime.
- Total heap—total of the useful heap and extra heap allocated for the program over its lifetime.
- Stack—stacks used by the program over time.
7.1. Performance Evaluation of ICMetric Key Generation and Authentication Module
7.1.1. Execution Time
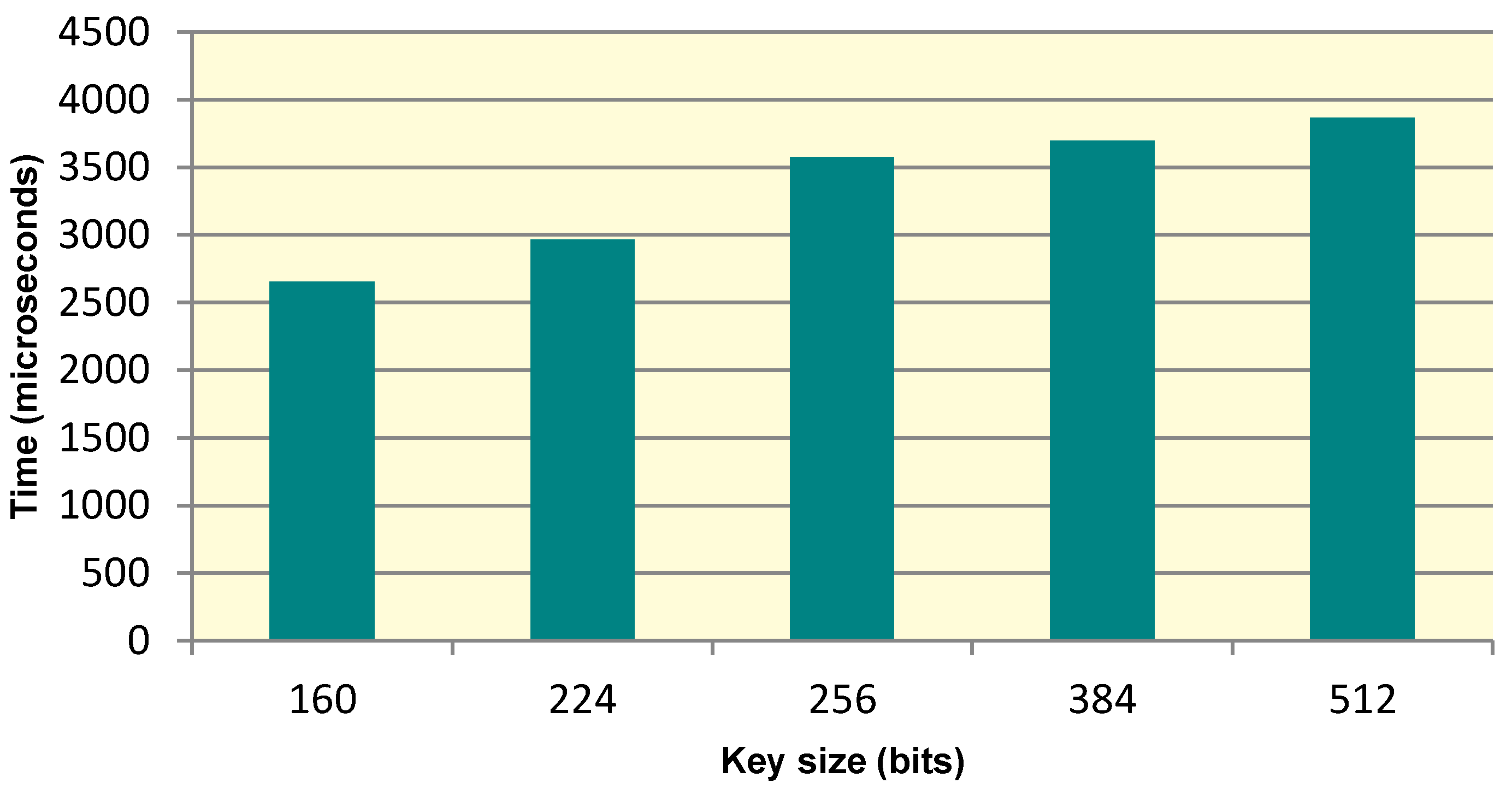
7.1.2. RAM Consumption
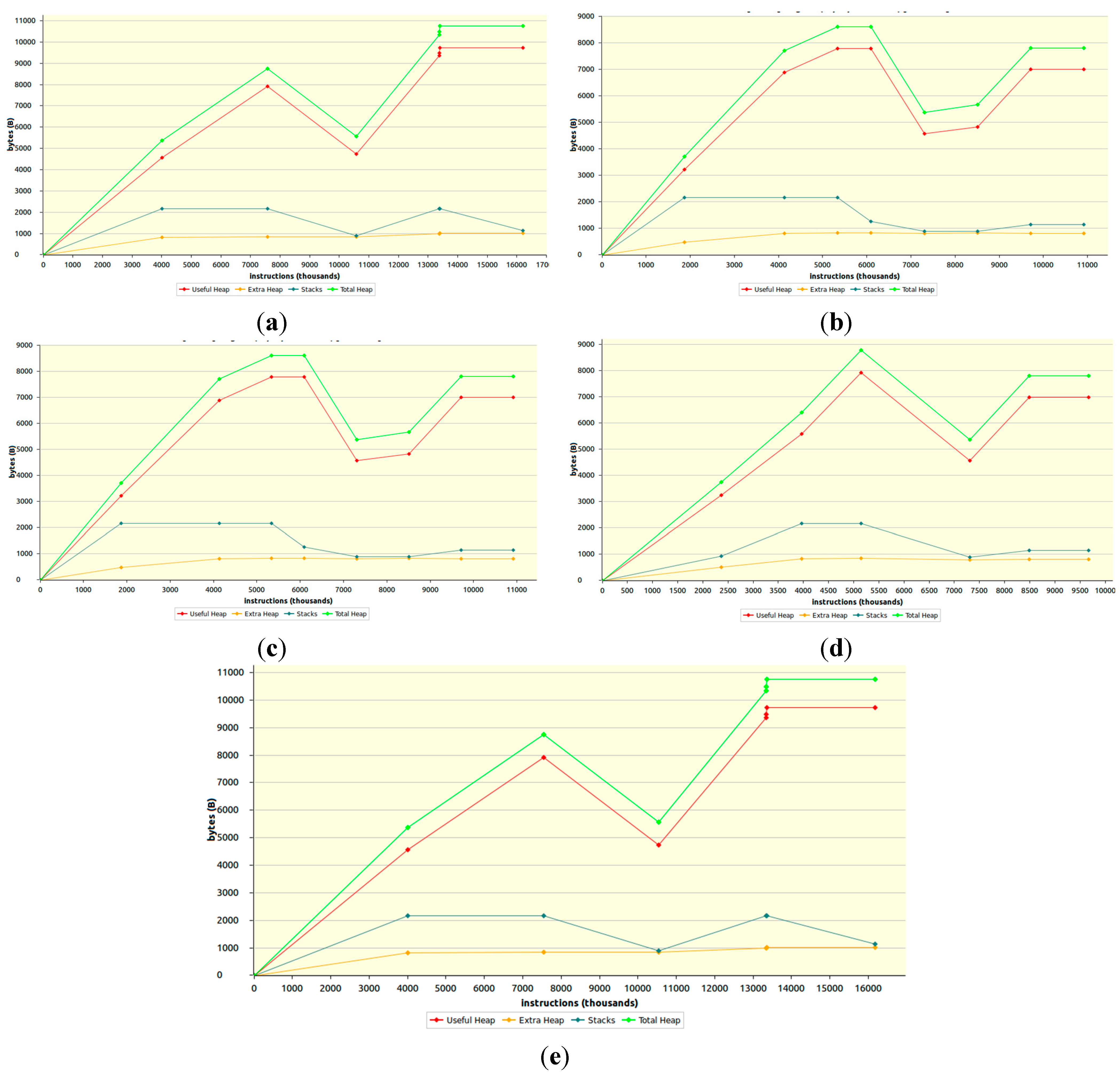
7.2. Performance Evaluation of ICMetric Based AES Encryption/Decryption Module
7.2.1. Execution Time

7.2.2. RAM Consumption
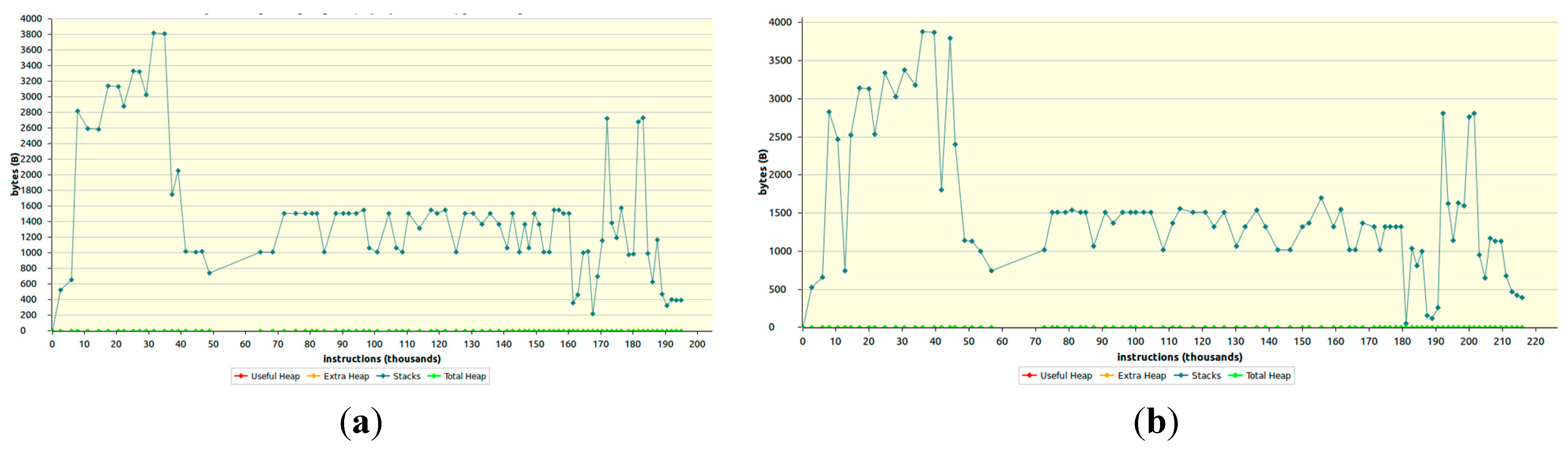
7.3. Discussion
| System Goals | |||||||
|---|---|---|---|---|---|---|---|
| Authentication | Confidentiality | Access Control | Non Repudiation | Precomputed Attacks | Integrity | ||
| Modules | MEMS Accelerometer | √ | |||||
| ICMetric | √ | √ | |||||
| Strong Key Generation | √ | ||||||
| Symmetric Module | √ | ✓ | √ | √ | |||
| AES | √ | √ | |||||
8. Conclusions
Acknowledgments
Author Contributions
Conflicts of Interest
References
- Vandrico Inc. (2008) Wearable Technology Database. Available online: http://vandrico.com/database (accessed on 13 October 2015).
- Zheng, Y.L.; Ding, X.R.; Poon, C.C.Y.; Lo, B.P.L.; Zhang, H.; Zhou, X.-L.; Yang, G.Z.; Zhao, N.; Zhang, Y.-T. Unobtrusive sensing and wearable devices for health informatics. IEEE Trans. Biomed. Eng. 2014, 26, 1538–1554. [Google Scholar] [CrossRef] [PubMed]
- Kovalchuk, Y.; Howells, G.; McDonald-Maier, K. Overview of ICMetrics technology—Security infrastructure for autonomous and intelligent healthcare system. Intern. J. Serv. Sci. and Technol. 2014, 4, 49–60. [Google Scholar]
- Tahir, R.; Hu, H.; Gu, D.; McDonald-Maier, K.; Howells, G. A Scheme for the Generation of Strong ICMetric Based Session Key Pairs For Secure Embedded System Applications. In Proceeding of the International Conference on Advanced Information Networking and Applications, Barcelona, Spain, 25–28 March 2013; pp. 689–696.
- Alam, M.M.; Hamida, E.B. Surveying wearable human assistive technology for life and safety applications: standards, challenges and opportunities. Sensors 2014, 14, 9153–9209. [Google Scholar] [CrossRef] [PubMed]
- Bourbakis, N.; Pantelopoulos, A.; Kannavara, R.; Nikita, K. Security and Privacy in Biomedical Telemetry: Mobile Health Platform for Secure Information Exchange; Handbook of Biomedical Telemetry Wiley IEEE: Hoboken, NJ, USA, 2014; pp. 382–418. [Google Scholar]
- Ragesh, G.K.; Baskaran, K. CRYP: Towards Cryptographically Enforced and Privacy Enhanced WBANs. In Proceeding of the First International Conference on Security of Internet of Things, Kollam, India, 17–19 August 2012; pp. 204–209.
- Yi, X.; Willemson, J.; Nait-Abdesselam, F. Privacy-Preserving Wireless Medical Sensor Network. In Proceeding of the 12th IEEE International Conference on Trust, Security and Privacy in Computing and Communications, Melbourne, Australia, 16–18 July 2013; pp. 118–125.
- Barua, M.; Liang, X.; Lu, R.; Shen, X. PEACE: An Efficient and Secure Patient-Centric Access Control Scheme for eHealth Care System. In Proceedings of the IEEE Conference on Computer Communications Workshops, Shanghai, China, 10–15 April 2011; pp. 970–975.
- Rostami, M.; Juels, A.; Koushanfar, F. Heart-to-Heart (H2H): Authentication for Implanted Medical Devices. In Proceeding of the 20th ACM Conference on Computer and Communications Security, Berlin, Germany, 4–8 November 2013; pp. 1099–1112.
- Kannavara, R.; Mertoguno, S.; Bourbakis, N. SCAN secure processor and its biometric capabilities. J. Electron. Imaging 2011, 20. [Google Scholar] [CrossRef]
- Venkatasubramanian, K.K.; Banerjee, A.; Gupta, S.K.S. PSKA: Usable and secure key agreement scheme for body area networks. IEEE Trans. Inf. Technol. Biomed. 2010, 1, 60–68. [Google Scholar] [CrossRef] [PubMed]
- Jurik, D.; Weaver, A.C. Securing Mobile Devices with Biotelemetry. In Proceeding of the 20th International Conference on Computer Communications and Networks, Maui, Hawai, 31 July–4 August 2011; pp. 1–6.
- Venkatasubramanian, K.K.; Banerjee, A.; Gupta, S.K.S. EKG—Based Key Agreement in Body Sensor Networks. In Proceeding of the 2nd Workshop on Mission Critical Networks, Phoenix, AZ, USA, 13–18 April 2008; pp. 1–6.
- Strydis, C.; Seepers, R.M.; Peris-Lopez, P.; Siskos, D.; Sourdis, I. A System Architecture, Processor and Communication Protocol for Secure Implants. ACM Trans. 2013, 10, 1–23. [Google Scholar] [CrossRef]
- Hu, C.; Xiuzhen, C.; Zhang, F.; Wu, D.; Liao, X.; Chen, D. OPFKA: Secure and Efficient Ordered Physiological Feature Based Key Agreement for Wireless Body Area Networks. In Proceedings of the 32nd IEEE International Conference on Computer Communications, Turin, Italy, 14–19 April 2013; pp. 2274–2282.
- Papoutsis, E. Investigation of The Potential of Generating Encryption Keys For ICMetrics. Ph.D. Thesis, The University of Kent, Canterbury, UK, June 2009. [Google Scholar]
- Kokosy, A.; Floquet, T.; Howells, G.; Hu, H.; Pepper, M.; Sakel, M.; Donze, C. SYSIASS—An Intelligent Powered Wheelchair. In Proceedings of the 1st International Conference on Systems and Computer Science, Lille, France, 29–31 August 2012.
- Defence Advanced Research Project Agency; Micro Electro-Mechanical Systems (MEMS). Annu. Rev. Fluid Mechan. 1998, 30, 579–612.
- Castoldi, L. The MEMS Revolution (2012, September). Available online: http://www.semi.org/eu/sites/semi.org/files/docs/STM.pdf (assessed on 15 October 2015).
- Kuc, R. Electrical Engineering in Context: Smart Devices, Robots & Communications; Cengage Learning: Boston, MA, USA, 2014. [Google Scholar]
- Feng, M.; Fukuda, Y.; Mizuta, M.; Ozer, E. Citizen sensors for SHM: Use of accelerometer data from smartphones. Sensors 2015, 15, 2980–2998. [Google Scholar] [CrossRef] [PubMed]
- Dey, S.; Roy, N.; Xu, W.; Choudhury, R.R.; Nelakuditi, S. AccelPrint: Imperfections of Accelerometers Make Smartphones Trackable. In Proceedings of the 21st Annual Network and Distributed System Security Symposium NDSS, San Diego, CA, USA, 23–26 February 2014.
- Mobile Device Identification via Sensor Fingerprinting. National Research & Simulation Center, Rafael, Internal Report 2014. Available online: https://crypto.stanford.edu/gyrophone/sensor_id.pdf (assessed on 15 October 2015).
- Aysu, A.; Ghalaty, N.F.; Franklin, Z.; Yali, M.P.; Schaumont, P. Digital Fingerprints for Low-Cost Platforms Using MEMS Sensors. In Proceedings of the Workshop on Embedded Systems Security, Montreal, Canada, 29 September 2013.
- Burns, A.; Greene, B.R.; McGrath, M.J.; O’Shea, T.J.; Kuris, B.; Ayer, S.M.; Stroiescu, F.; Cionca, V. SHIMMER™—A wireless sensor platform for noninvasive biomedical research. IEEE Sens. J. 2010, 9, 1527–1534. [Google Scholar] [CrossRef]
- Freescale Semiconductor. (2008, April) ±1.5g, ±6g Three Axis Low-g Micromachined Accelerometer. Technical Data. Available online: http://www.freescale.com/files/sensors/doc/data_sheet/MMA7361L.pdf (assessed on 10 October 2015).
- Maxim Integrated. DS2411 Silicon Serial Number with VCC Input (2003, May). Data Sheet. Available online: http://datasheets.maximintegrated.com/en/ds/DS2411.pdf (assessed on 10 October 2015).
- Ferraris, F.; Grimaldi, U.; Parvis, M. Procedure for effortless in-field calibration of three-axial rate gyro and accelerometers. Sens. Mater. 1995, 7, 311–330. [Google Scholar]
- Tahir, H.; Tahir, R.; McDonald-Maier, K. Securing MEMS Based Sensor Nodes in the Internet of Things. In Proceedings of the Sixth International Conference on Emerging Security Technologies, Braunschweig, Germany, 3–15 September 2015.
- Almulhem, A. Threat modeling for electronic health record systems. J. Med. Syst. 2012, 36, 2921–2926. [Google Scholar] [CrossRef] [PubMed]
- Wu, T. The Secure Remote Password Protocol. In Proceedings of the 1998 Internet Society Network and Distributed System Security Symposium, San Diego, CA, USA, 11–13 March 1998; pp. 97–111.
- RFC 5054, Using the Secure Remote Password (SRP) Protocol for TLS Authentication. November 2007. Available online: http://www.rfc-editor.org/info/rfc5054 (accessed on 10 October 2015).
- CyaSSL User Manual. User Manual (2013, September). Available online: http://www.yassl.com/documentation/CyaSSL-Manual.pdf (accessed on 10 October 2015).
- Gueron, S. Intel Advanced Encryption Standard (AES) New Instructions Set. Intel. Corp. White Pap. 2012, 3, 1–95. [Google Scholar]
- The Valgrind Quick Start Guide. User Manual (2014, September). Available online: http://valgrind.org/docs/manual/valgrind_manual.pdf (accessed on 10 October 2015).
- Wolff, M. (2011, August) Massif-Visualizer Memory Profiling UI. Presentation. Available online: https://desktopsummit.org/sites/www.desktopsummit.org/files/massif-visualizer.pdf (assessed on 15 October 2015).
- Electronic Authentication Guideline—Recommendations of the National Institute of Standards and Technology (2006, April). Available online: http://csrc.nist.gov/publications/nistpubs/800-63/SP800–63V1_0_2.pdf (accessed on 10 October 2015).
© 2015 by the authors; licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Tahir, R.; Tahir, H.; McDonald-Maier, K. Securing Health Sensing Using Integrated Circuit Metric. Sensors 2015, 15, 26621-26642. https://doi.org/10.3390/s151026621
Tahir R, Tahir H, McDonald-Maier K. Securing Health Sensing Using Integrated Circuit Metric. Sensors. 2015; 15(10):26621-26642. https://doi.org/10.3390/s151026621
Chicago/Turabian StyleTahir, Ruhma, Hasan Tahir, and Klaus McDonald-Maier. 2015. "Securing Health Sensing Using Integrated Circuit Metric" Sensors 15, no. 10: 26621-26642. https://doi.org/10.3390/s151026621
APA StyleTahir, R., Tahir, H., & McDonald-Maier, K. (2015). Securing Health Sensing Using Integrated Circuit Metric. Sensors, 15(10), 26621-26642. https://doi.org/10.3390/s151026621






