Wrapping Trust for Interoperability: A Preliminary Study of Wrapped Tokens
Abstract
:1. Introduction
2. Materials and Methods
- A.
- Within this group are whitepapers and official blogs written by the developers of the related platforms. Articles from renowned experts, such as Vitalik Buterin, also belong to this group. The reason for considering those resources as the most reliable is that details on technology are certain and accurate since they directly come from the developers. On the other hand, expert opinion is inserted, as it is thought to directly impact technology development.
- B.
- To this group belongs guides and study material, provided by famous blogs, such as Binance Academy, The Cryptonomist, or opinion posts written by academics/developers.
- C.
- This category includes opinion posts and blogs written by bloggers with a verifiable bio and a traceable history of blog activity. Therefore, bloggers’ first articles or articles without an identifiable source do not belong to this group.
- D.
- Finally, articles that are not on a reliable source and not written by an identifiable author are inserted in this group. They are not discarded as they provide information that is not available in other sources.
Data Extraction
3. Why Wrapped Tokens?
3.1. Wrapped Assets and Stablecoins
3.2. The Emergence of Wrapped Tokens
3.3. Wrapped Tokens Issuing Mechanisms
4. Active, Wrapped Tokens Projects
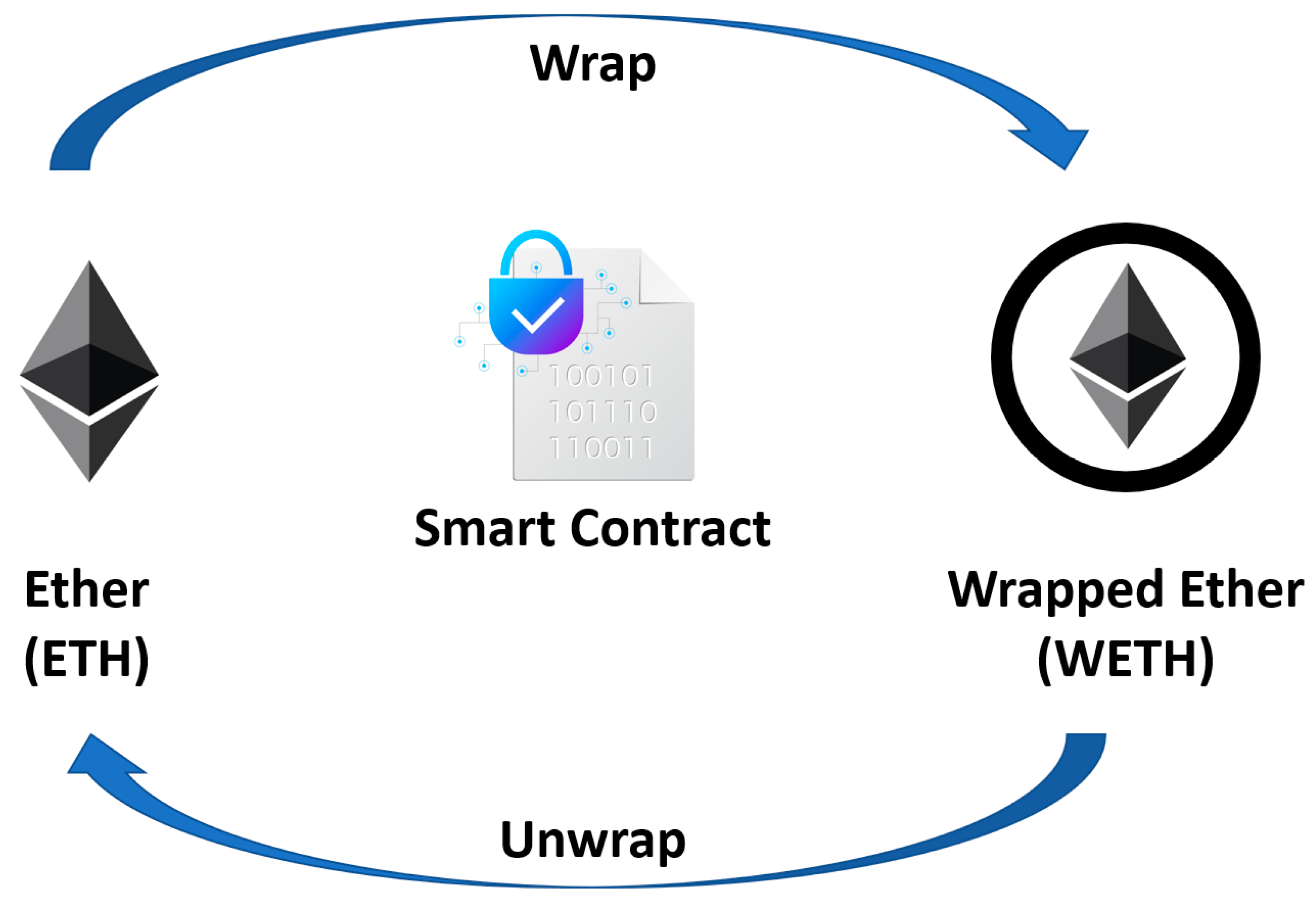
4.1. Wrapped Ether (WETH)
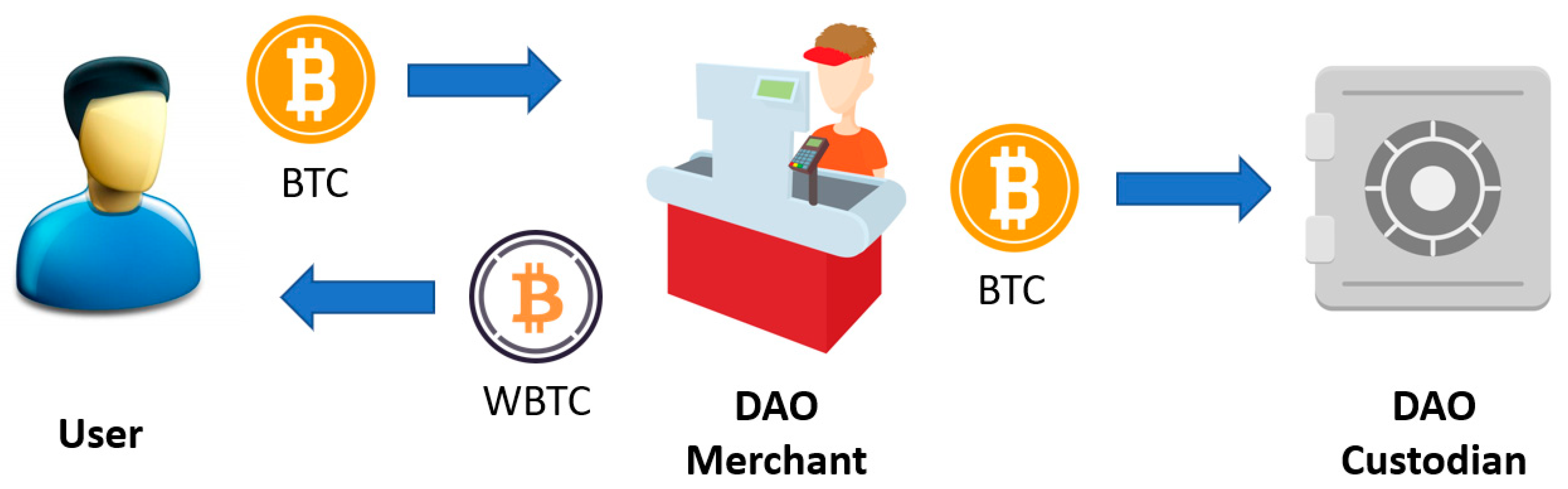
4.2. Wrapped Bitcoin (WBTC)
4.3. Ren Project
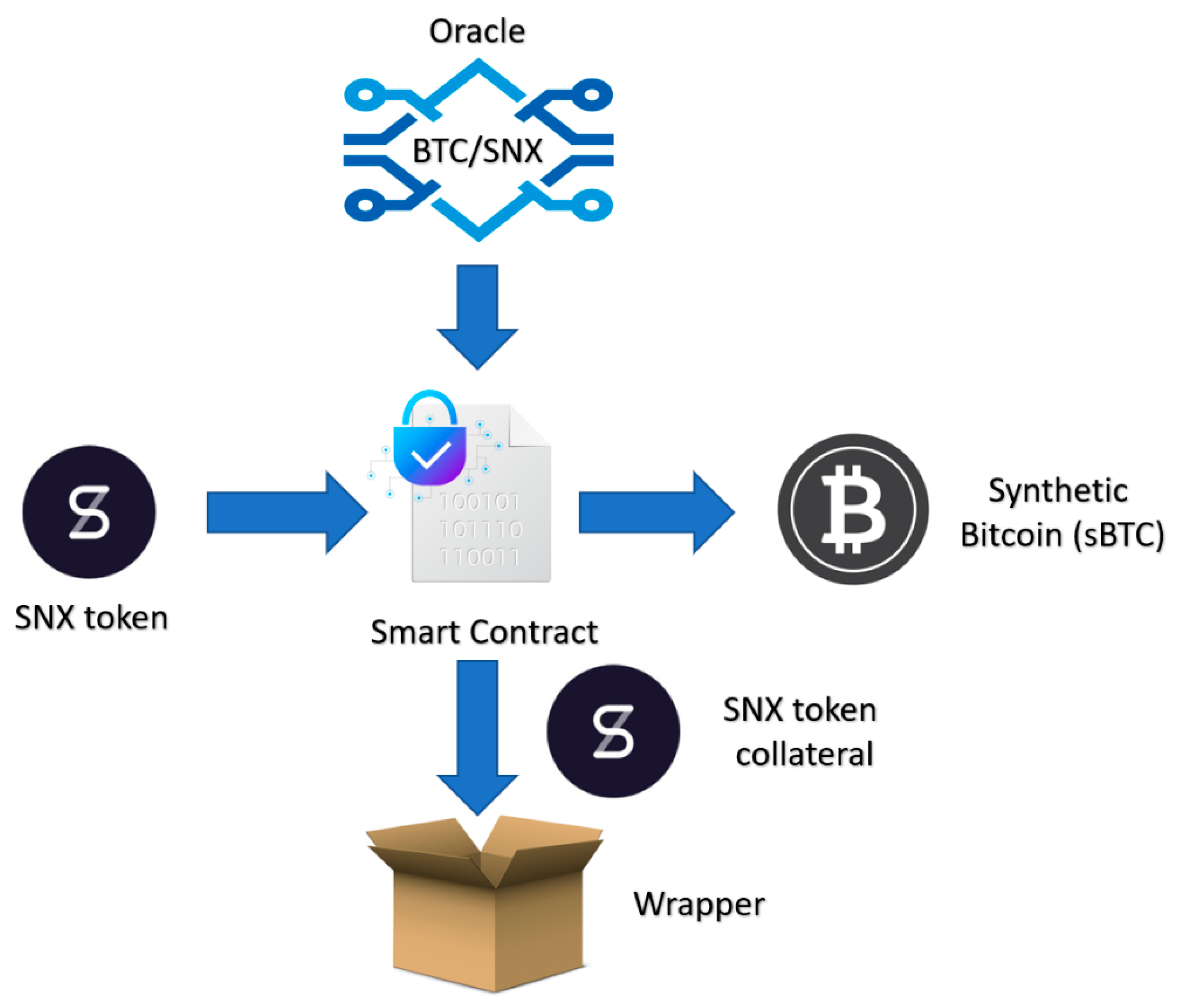
4.4. Synthetic Tokens and sBTC
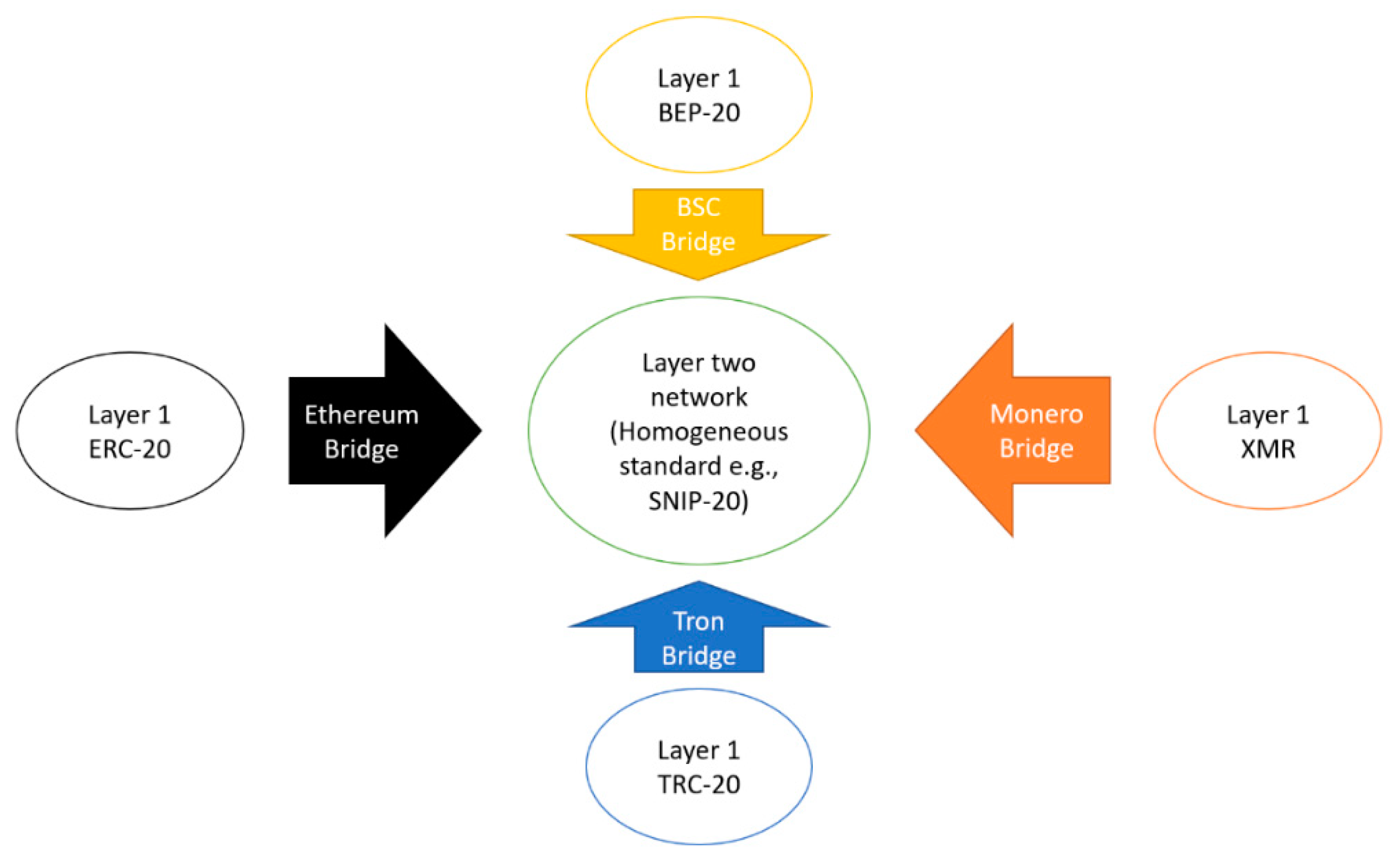
4.5. Secret Network
5. Discussion
5.1. Ease of Use, Costs, and Acceptance
5.2. Risks and Concerns of Wrapping Tokens
5.3. Evaluation of Interoperability Features
6. Conclusions
Funding
Data Availability Statement
Conflicts of Interest
Appendix A
| Reliability | Source Name | Author/s | Title | Reference |
|---|---|---|---|---|
| A | wbtc.network | Kyber Network BitGo Inc. Republic Protocol | Wrapped Tokens A multi-institutional framework for tokenizing any asset | [57] |
| A | Weth.io | Radar Relay Inc. 2021 | WTF IS WETH? | [17] |
| A | Renproject.io | Zhang, T. Wang, L. | Republic Protocol A decentralized dark pool exchange providing atomic swaps for Ethereum-based assets and Bitcoin | [77] |
| A | U.Today | Dovbnya, A | Vitalik Buterin Worried About ‘Trust Models’ of Some Bitcoin-Backed Ethereum Tokens | [100] |
| B | Bitrates | Banov, M. | Wrapped Tokens, Crypto-Derivatives and Candidate Ethereum Standards (ERCs). | [101] |
| B | The Cryptonomist | Cavicchioli, M. | What are the so-called wrapped bitcoin? | [98] |
| B | Cointelegraph.com | Kuznetsov, N. | Wrapped Crypto Tokens, Explained | [76] |
| B | Shrimpy Academy | The Shrimpy Team | What Are Wrapped Tokens? | [72] |
| C | NiceHash | Tarman, M. | What is Wrapped Bitcoin? | [67] |
| C | BSC NEWS | Wilfred, V. | cryptonomics-wrapped-tokens-explained | [12] |
| C | The Chain Bulletin | Andreychev, A. | Binance Introduces Wrapped Tokens For Ethereum | [80] |
| C | CoinsCapture | Ghag, S. | Wrapped Tokens-Explained | [69] |
| D | Publish0x | Gongo | Wrapped Tokens Explained | [75] |
| D | Phemex | Tang, N. | Wrapped Tokens: Wrap Your Head Around These New Crypto Tokens | [34] |
| D | The Motley Fool | Sun, Z. | What Are Wrapped Tokens? | [88] |
| D | Cryptopedia | Cryptopedia Staff | wBTC: What Can You Do with Wrapped Bitcoin? | [43] |
Appendix B
| Wrapped Token | Gas Price * (Gwei) | Total Cost (Ether) | Transaction Description | Platform |
|---|---|---|---|---|
| WETH (ERC-20) | 96 | 0.004 | Wrapping Ether into WETH | SushiSwap |
| sWBTC | 89 | 0.005 | Bridge WBTC to secret network | Secret Bridge |
| WBTC | 75 | 0.01 | Bridge BTC to Ethereum (centralized) | Coinlist.co |
| WBTC | 107 | 0.076 | Bridge BTC to Ethereum (Hybrid) | BadgerDao |
| RenBTC | 89 | 0.019 | Mint RenBTC (erc-20) once received by RenVM | Renproject Bridge |
| sUSD ** | 90 | 0.05 | Mint sUSD, depositing SNX as collateral | Synthetix |
References
- Larsen, A. A Primer on Blockchain Interoperability. Available online: https://medium.com/blockchain-capital-blog/a-primer-on-blockchain-interoperability-e132bab805b (accessed on 9 December 2019).
- Tasca, P.; Tessone, C.J. A Taxonomy of Blockchain Technologies: Principles of Identification and Classification. Ledger 2019, 4, 140. [Google Scholar] [CrossRef]
- Hardjono, T.; Lipton, A.; Pentland, A. Towards a Design Philosophy for Interoperable Blockchain Systems. arXiv 2018, arXiv:1805.05934. [Google Scholar]
- The European Union Blockchain Observatory and Forum. Central Bank Digital Currencies and a Euro for the Future; The European Union Blockchain Observatory and Forum: Brussels, Belgium, 2021. [Google Scholar]
- Pang, Y. A New Consensus Protocol for Blockchain Interoperability Architecture. IEEE Access 2020, 8, 153719–153730. [Google Scholar] [CrossRef]
- Hardjono, T.; Lipton, A.; Pentland, A. Toward an Interoperability Architecture for Blockchain Autonomous Systems. IEEE Trans. Eng. Manag. 2020, 67, 1298–1309. [Google Scholar] [CrossRef]
- Imsicoinexc. What Is a Wrapped Token? What Does WBTC Do? Available online: https://coinexc.com/2021/05/26/what-is-a-wrapped-token-what-does-wbtc-do/ (accessed on 21 August 2021).
- Borkowski, M.; Sigwart, M.; Frauenthaler, P.; Hukkinen, T.; Schulte, S. Dextt: Deterministic Cross-Blockchain Token Transfers. IEEE Access 2019, 7, 111030–111042. [Google Scholar] [CrossRef]
- Lafourcade, P.; Lombard-Platet, M. About blockchain interoperability. Inf. Process. Lett. 2020, 161, 105976. [Google Scholar] [CrossRef]
- Beck, J. How Wrapped Tokens Bring More Liquidity to DeFi. Available online: https://consensys.net/blog/codefi/put-your-bitcoin-to-work-on-ethereum/ (accessed on 12 August 2021).
- LEDU. What Is a Wrapped Token? Available online: https://ledu.education-ecosystem.com/what-is-a-wrapped-token/ (accessed on 31 August 2021).
- Wilfred, V. Wrapped Tokens Explained. Available online: https://www.bsc.news/post/cryptonomics-wrapped-tokens-explained (accessed on 30 August 2021).
- DefiPulse. Bitcoin At Work. Available online: https://defipulse.com/btc (accessed on 10 September 2021).
- Tron BitTorrent-Chain Whitepaper 1 Introduction. Available online: https://tron.network/static/doc/BitTorrent-ChainWhitepaper_EN.pdf (accessed on 13 September 2021).
- Behrens, A. Wrapped ETH Comes to Tezos as It Takes on Ethereum DeFi Market. Available online: https://decrypt.co/51860/wrapped-eth-comes-to-tezos-as-it-takes-on-ethereum-defi-market (accessed on 4 September 2021).
- Santiago, S. Wrapped Tokens: A Tool to Jump across Blockchains. Available online: https://thecrypto.app/blog/wrapped-tokens-blockchain-btc-wbtc/?cookie-state-change=1630431206305 (accessed on 31 August 2021).
- RADAR. WTF IS WETH? Available online: https://weth.io/ (accessed on 19 August 2021).
- Loong How RenVM Actually Works. Available online: https://medium.com/renproject/how-renvm-actually-works-c2f76a2630c4 (accessed on 12 August 2021).
- Carpenter, A. What is Wrapped Bitcoin (WBTC) and How Can DeFi Investors Use It? Available online: https://www.bitcoinmarketjournal.com/what-is-wrapped-bitcoin/ (accessed on 19 August 2021).
- Baker, P. Synthetic Bitcoin Product Launches on Ethereum. Available online: https://cryptobriefing.com/synthetic-bitcoin-synthetix/ (accessed on 7 September 2021).
- SecretNetwork. Introducing Secret Network. Available online: https://scrt.network/blog/introducing-secret-network (accessed on 19 August 2020).
- Frankenreiter, J. The Limits of Smart Contracts. J. Inst. Theor. Econ. JITE 2019, 175, 149–162. [Google Scholar] [CrossRef]
- Soldani, J. Grey Literature. ACM SIGSOFT Softw. Eng. Notes 2019, 44, 11–12. [Google Scholar] [CrossRef]
- Ogawa, R.T.; Malen, B. Towards Rigor in Reviews of Multivocal Literatures: Applying the Exploratory Case Study Method. Rev. Educ. Res. 2016, 61, 265–286. [Google Scholar] [CrossRef]
- Pupyshev, A.; Sapranidi, I.; Dzhafarov, E.; Khalilov, S.; Teterin, I. Graviton: Interchain swaps and wrapped tokens liquidity incentivisation solution. arXiv 2020, arXiv:2009.05540. [Google Scholar]
- Darisi, M.; Savla, J.; Shirole, M.; Bhirud, S. STEM: Secure Token Exchange Mechanisms. Commun. Comput. Inf. Sci. 2019, 1132, 206–219. [Google Scholar] [CrossRef]
- Moncada, R.; Ferro, E.; Favenza, A.; Freni, P. Next Generation Blockchain-Based Financial Services. In Euro-Par 2020: Parallel Processing Workshops; Springer: Cham, Switzerland, 2021; Volume 12480, pp. 30–41. [Google Scholar]
- Fedorova, E.P.; Skobleva, E.I. Application of blockchain technology in higher education. Eur. J. Contemp. Educ. 2020, 9, 552–571. [Google Scholar] [CrossRef]
- Caldarelli, G.; Ellul, J. The Blockchain Oracle Problem in Decentralized Finance—A Multivocal Approach. Appl. Sci. 2021, 11, 7572. [Google Scholar] [CrossRef]
- Pasdar, A.; Dong, Z.; Lee, Y.C. Blockchain Oracle Design Patterns. arXiv 2021, arXiv:2106.09349. [Google Scholar]
- Garousi, V.; Felderer, M.; Mäntylä, M.V. Guidelines for including grey literature and conducting multivocal literature reviews in software engineering. Inf. Softw. Technol. 2019, 106, 101–121. [Google Scholar] [CrossRef] [Green Version]
- EnergiDefi. What Is a Wrapped Asset? Available online: https://defi.support.energi.world/hc/en-us/articles/360055624532-What-is-a-wrapped-asset- (accessed on 10 September 2021).
- Klages-Mundt, A.; Harz, D.; Gudgeon, L.; Liu, J.-Y.; Minca, A. Stablecoins 2.0: Economic Foundations and Risk-based Models. SSRN Electron. J. 2020, 59–79. [Google Scholar] [CrossRef]
- Tang, N. Wrapped Tokens: Why Are Wrapped Tokens so Important?—Phemex Academy. Available online: https://phemex.com/academy/what-are-wrapped-tokens (accessed on 3 December 2021).
- Gu, W.C.; Raghuvanshi, A.; Boneh, D. Empirical Measurements on Pricing Oracles and Decentralized Governance for Stablecoins. Cryptoecon. Syst. 2021, 1. [Google Scholar] [CrossRef]
- Tether Holdings Limited Tether: Fiat currencies on the Bitcoin blockchain. Northwest. Univ. Law Rev. 2018, 113, i–viii.
- Centre USDC Centre Whitepaper. Self-Publ. White Pap. 2018. Available online: https://f.hubspotusercontent30.net/hubfs/9304636/PDF/centre-whitepaper.pdf (accessed on 10 September 2021).
- Werner, S.M.; Perez, D.; Gudgeon, L.; Klages-Mundt, A.; Harz, D.; Knottenbelt, W.J. SoK: Decentralized Finance (DeFi). SSRN Electron. J. 2021, 1–19. [Google Scholar] [CrossRef]
- DR, T. An Introduction to Binance Bridge. Available online: https://academy.binance.com/en/articles/an-introduction-to-binance-bridge (accessed on 6 September 2021).
- Moore, C. Independent Accountant’s Report. 2021. Available online: https://tether.to/wp-content/uploads/2021/08/tether_assuranceconsolidated_reserves_report_2021-06-30.pdf (accessed on 10 September 2021).
- Maker Team. The Dai Stablecoin System. Whitepaper 2017, 21. Available online: https://makerdao.com/whitepaper/White%20Paper%20-The%20Maker%20Protocol_%20MakerDAO%E2%80%99s%20Multi-Collateral%20Dai%20(MCD)%20System-FINAL-%20021720.pdf (accessed on 11 September 2021).
- Brooks, S.; Jurisevic, A.; Spain, M.; Warwick, K. Synthetix: A Decentralised Payment Network and Stablecoin v0.8. Available online: https://www.synthetix.io/uploads/synthetix_litepaper.pdf (accessed on 9 January 2021).
- Cryptopedia Staff. Wrapped Bitcoin: What Can You Do With A wBTC Token? | Gemini. Available online: https://www.gemini.com/cryptopedia/wrapped-bitcoin-what-can-you-do (accessed on 3 December 2021).
- Amler, H.; Eckey, L.; Faust, S.; Kaiser, M.; Sandner, P.; Schlosser, B. DeFi-ning DeFi: Challenges & Pathway. arXiv 2021, arXiv:2101.05589. [Google Scholar]
- Liu, B.; Szalachowski, P.; Zhou, J. A First Look into DeFi Oracles. In Proceedings of the 2021 IEEE International Conference on Decentralized Applications and Infrastructures (DAPPS), Oxford, UK, 23–26 August 2020. [Google Scholar]
- Udeji, C. What Are Wrapped Tokens?—Everything You Need To Know. Available online: https://www.nigeriabitcoincommunity.com/wrapped-tokens/ (accessed on 12 August 2021).
- Qasse, I.A.; Talib, M.A.; Nasir, Q. Inter blockchain communication: A survey. In Proceedings of the ArabWIC 6th Annual International Conference Research Track, Rabat, Morocco, 7–9 March 2019; pp. 1–6. [Google Scholar] [CrossRef]
- Frincu, I.A. Wrapped Tokens, Long-Story-Short. Available online: https://www.linkedin.com/pulse/wrapped-tokens-long-story-short-ioana-alexandra-frincu/ (accessed on 23 August 2021).
- Hancock, B. What Is a Wrapped Token? Available online: https://blog.uphold.com/what-is-a-wrapped-token (accessed on 6 September 2021).
- Antonopoulos, A.M.; Woods, G. Mastering Ethereum—Building Smart Contracts and DAPPS; O’Reilly: Newton, MA, USA, 2018. [Google Scholar]
- Schär, F. Decentralized Finance: On Blockchain- and Smart Contract-based Financial Markets. SSRN Electron. J. 2020, 1–24. [Google Scholar] [CrossRef]
- DefiPulse. DexGuru—Real-time Data, Analytics and Trading for AMMs in One Place. Available online: https://defipulse.com/blog/dexguru/ (accessed on 19 April 2021).
- CoinMarketCap. Today’s Cryptocurrency Prices by Market Cap. Available online: https://coinmarketcap.com/ (accessed on 13 September 2021).
- Easley, D.; O’Hara, M.; Basu, S. From mining to markets: The evolution of bitcoin transaction fees. J. Financ. Econ. 2019, 134, 91–109. [Google Scholar] [CrossRef]
- Nakamoto, S. Bitcoin: A Peer-to-Peer Electronic Cash System. Available online: https://bitcoin.org/bitcoin.pdf (accessed on 11 June 2019).
- Elena, R. A 3 Minute Guide to Wrapped Bitcoin—WBTC. Available online: https://coinpedia.org/information/guide-to-wrapped-bitcoin/ (accessed on 23 August 2021).
- Network, K.; Protocol, R. Wrapped Tokens—A Multi-Institutional Framework for Tokenizing Any Asset. Available online: https://wbtc.network/assets/wrapped-tokens-whitepaper.pdf (accessed on 1 September 2021).
- Antonopoulos, A.M. Mastering Bitcoin: Programming the Open Blockchain, 2nd ed.; O’Reilly: Newton, MA, USA, 2017. [Google Scholar]
- U/qqwe22 People Who Own Wrapped Btc and Similair Tokens, Why? Available online: https://www.reddit.com/r/CryptoCurrency/comments/ozrodk/people_who_own_wrapped_btc_and_similair_tokens_why/ (accessed on 26 August 2021).
- Zhang, T. Republic Protocol: An Introduction. Available online: https://medium.com/renproject/republic-protocol-an-introduction-3d04e74c8f04 (accessed on 4 September 2021).
- BinanceAcademy. What Are Wrapped Tokens? Available online: https://academy.binance.com/en/articles/what-are-wrapped-tokens?ref=JLI1VBLA&utm_source=BinanceTwitter&utm_medium=GlobalSocial&utm_campaign=GlobalSocial (accessed on 30 August 2021).
- Gudgeon, L.; Moreno-Sanchez, P.; Roos, S.; McCorry, P.; Gervais, A. SoK: Layer-Two Blockchain Protocols. In Financial Cryptography and Data Security, Proceedings of the 24th International Conference on Financial Cryptography and Data Security, Kota Kinabalu, Malaysia, 10–14 February 2020; Springer: Cham, Switzerland, 2020; Volume 12059, pp. 201–226. [Google Scholar] [CrossRef]
- Li, C.; Zhang, J.; Yang, X. Scalable blockchain storage mechanism based on two-layer structure and improved distributed consensus. J. Supercomput. 2021, 1–32. [Google Scholar] [CrossRef]
- Johnson, S.; Robinson, P.; Brainard, J. Sidechains and interoperability. arXiv 2019, arXiv:1903.04077. [Google Scholar]
- Egberts, A. The Oracle Problem—An Analysis of how Blockchain Oracles Undermine the Advantages of Decentralized Ledger Systems. SSRN Electron. J. 2017. [Google Scholar] [CrossRef]
- Madine, M.; Salah, K.; Jayaraman, R.; Al-Hammadi, Y.; Arshad, J.; Yaqoob, I. appXchain: Application-Level Interoperability for Blockchain Networks. IEEE Access 2021, 9, 87777–87791. [Google Scholar] [CrossRef]
- Tarman, M. What is Wrapped Bitcoin? | NiceHash. Available online: https://www.nicehash.com/blog/post/what-is-wrapped-bitcoin#! (accessed on 3 December 2021).
- Thomson, C. The DAO of ETHEREUM: Analyzing the DAO Hack, the Blockchain, Smart Contracts, and the Law. Available online: https://medium.com/blockchain-review/the-dao-of-ethereum-e228b93afc79 (accessed on 3 April 2020).
- Ghag, S. Wrapped Tokens—Explained | CoinsCapture. Available online: https://coinscapture.com/blog/wrapped-tokens-explained (accessed on 3 December 2021).
- Scheid, E.J.; Hegnauer, T.; Rodrigues, B.; Stiller, B. Bifröst: A Modular Blockchain Interoperability API. In Proceedings of the 2019 IEEE 44th Conference on Local Computer Networks (LCN), Osnabrueck, Germany, 14–17 October 2019; pp. 332–339. [Google Scholar] [CrossRef] [Green Version]
- Yos Smart Contract Extensibility with Wrapped Tokens. Available online: https://yos.io/2019/07/13/smart-contract-extensibility-wrapped-tokens/ (accessed on 21 August 2021).
- TheShrimpyTeam. What Are Wrapped Tokens? Available online: https://academy.shrimpy.io/lesson/what-are-wrapped-tokens (accessed on 24 August 2021).
- CryptopediaStaff. What Is Kyber Network and How Does It Work? Available online: https://www.gemini.com/cryptopedia/what-is-kyber-network (accessed on 28 August 2021).
- Rothrie, S. What Is BitGo? Enterprise Cryptocurrency Solutions. Available online: https://coincentral.com/what-is-bitgo/ (accessed on 28 August 2021).
- Gongo Wrapped Tokens Explained. Available online: https://www.publish0x.com/decentralization-why-is-it-important/wrapped-tokens-explained-xzwkzpn (accessed on 3 December 2021).
- Kuznetsov, N. Wrapped Crypto Tokens, Explained. Available online: https://cointelegraph.com/explained/wrapped-crypto-tokens-explained (accessed on 2 December 2021).
- Zhang, T.; Wang, L. Republic Protocol A Decentralized Dark Pool Exchange Providing Atomic Swaps for Ethereum-Based Assets and Bitcoin. Available online: https://renproject.io/whitepaper_1.0.0.pdf (accessed on 5 June 2021).
- We Are DigiByte. renDGB—It’s Here and Here’s What You Can Do with It. | By We Are DigiByte | Medium. Available online: https://wearedgb.medium.com/rendgb-its-here-and-here-s-what-you-can-do-with-it-a092f567a563 (accessed on 18 November 2021).
- Project, R. Ren Whitepaper. Available online: https://medium.com/renproject (accessed on 13 September 2021).
- Andreychev, A. Binance Introduces Wrapped Tokens For Ethereum—The Chain Bulletin. Available online: https://chainbulletin.com/binance-introduces-wrapped-tokens-for-ethereum/ (accessed on 2 December 2021).
- Sriram, S. Binance Launches BTokens—Wrapped Tokens on Ethereum. Available online: https://eng.ambcrypto.com/binance-btokens-ethereum/ (accessed on 30 August 2021).
- Binance.org. Proof of Assets. Available online: https://www.binance.org/en/assets-proof (accessed on 18 November 2021).
- TheShrympyTeam. What Are Crypto Synths? Synthetic Assets Explained. Available online: https://academy.shrimpy.io/post/what-are-crypto-synths-synthetic-assets-explained (accessed on 7 September 2021).
- The Synthetix Team. The Vega Release. Available online: https://blog.synthetix.io/the-vega-release/ (accessed on 15 November 2021).
- Al-Breiki, H.; Rehman, M.H.U.; Salah, K.; Svetinovic, D. Trustworthy Blockchain Oracles: Review, Comparison, and Open Research Challenges. IEEE Access 2020, 8, 85675–85685. [Google Scholar] [CrossRef]
- Krupka, D. Secret Network (SCRT) Review: Privacy Meets Compliance. Available online: https://www.coinbureau.com/review/secret-network-scrt/ (accessed on 8 September 2021).
- Hayward, A. What Is Secret Network (SCRT)? Available online: https://decrypt.co/resources/what-is-secret-network-scrt-formerly-enigma (accessed on 8 September 2021).
- Sun, Z. What Are Wrapped Tokens? | The Motley Fool. Available online: https://www.fool.com/investing/2021/10/05/what-are-wrapped-tokens/ (accessed on 3 December 2021).
- ByBitLearn. What are Wrapped Tokens—And How do They Work? Available online: https://learn.bybit.com/crypto/what-are-wrapped-tokens-and-how-do-they-work/ (accessed on 1 September 2021).
- Jin, H.; Dai, X.; Xiao, J. Towards a novel architecture for enabling interoperability amongst multiple blockchains. In Proceedings of the 2018 IEEE 38th International Conference on Distributed Computing Systems (ICDCS), Vienna, Austria, 2–6 July 2018; pp. 1203–1211. [Google Scholar] [CrossRef]
- Gas Tracker—Etherscan. Available online: https://docs.etherscan.io/api-endpoints/gas-tracker (accessed on 18 November 2021).
- Ren RenBridge Terms of Service. Available online: https://documentcloud.adobe.com/link/track?uri=urn:aaid:scds:US:33d77e75-ba96-4db3-85d1-5ffb6fd34a8f#pageNum=1 (accessed on 24 August 2021).
- Caldarelli, G. Understanding the Blockchain Oracle Problem: A Call for Action. Information 2020, 11, 509. [Google Scholar] [CrossRef]
- Monika; Bhatia, R. Interoperability solutions for blockchain. In Proceedings of the 2020 International Conference on Smart Technologies in Computing, Electrical and Electronics (ICSTCEE), Bengaluru, India, 9–10 October 2020; pp. 381–385. [Google Scholar] [CrossRef]
- SecretFinance. Secret Finance F.A.Q. Available online: https://bridge.scrt.network/faq (accessed on 14 September 2021).
- Sztorc, P. The Oracle Problem. Available online: https://www.infoq.com/presentations/blockchain-oracle-problems (accessed on 3 March 2020).
- Pillai, B.; Biswas, K.; Muthukkumarasamy, V. Cross-chain interoperability among blockchain-based systems using transactions. Knowl. Eng. Rev. 2020, 35, e23. [Google Scholar] [CrossRef]
- Cavicchioli, M. What Are the So-Called Wrapped Bitcoin?—The Cryptonomist. Available online: https://en.cryptonomist.ch/2020/09/19/what-are-wrapped-bitcoin/ (accessed on 3 December 2021).
- Reike, F. Advantages and Disadvantages of Wrapped Assets. Available online: https://medium.com/nakamo-to/advantages-and-disadvantages-of-wrapped-assets-ffe35fa2f566 (accessed on 17 August 2021).
- Dovbnya, A. Vitalik Buterin Worried About “Trust Models” of Some Bitcoin-Backed Ethereum Tokens. Available online: https://u.today/vitalik-buterin-worried-about-trust-models-of-some-bitcoin-backed-ethereum-tokens (accessed on 22 November 2021).
- Banov, M. Ethereum Instruments and Standard Specifications. Wrapped Tokens and ERCs. Available online: https://www.bitrates.com/news/p/wrapped-tokens-crypto-derivatives-and-candidate-ethereum-standards-ercs (accessed on 3 December 2021).
- Ren Community Ren, October Development Update. Available online: https://medium.com/renproject/october-development-update-3b68ea6d2dea (accessed on 19 November 2021).
- Arasa, D. What Are Wrapped Tokens? How Wrapped Tokens Bring the Gift of Blockchain in Many Ways. Available online: https://usa.inquirer.net/79580/what-are-wrapped-tokens (accessed on 30 August 2021).
- Liu, Z.; Xiang, Y.; Shi, J.; Gao, P.; Wang, H.; Xiao, X.; Wen, B.; Hu, Y.C. Hyperservice: Interoperability and programmability across heterogeneous blockchains. In Proceedings of the 2019 ACM SIGSAC Conference on Computer and Communications Security, London, UK, 11–15 November 2019; pp. 549–566. [Google Scholar] [CrossRef]
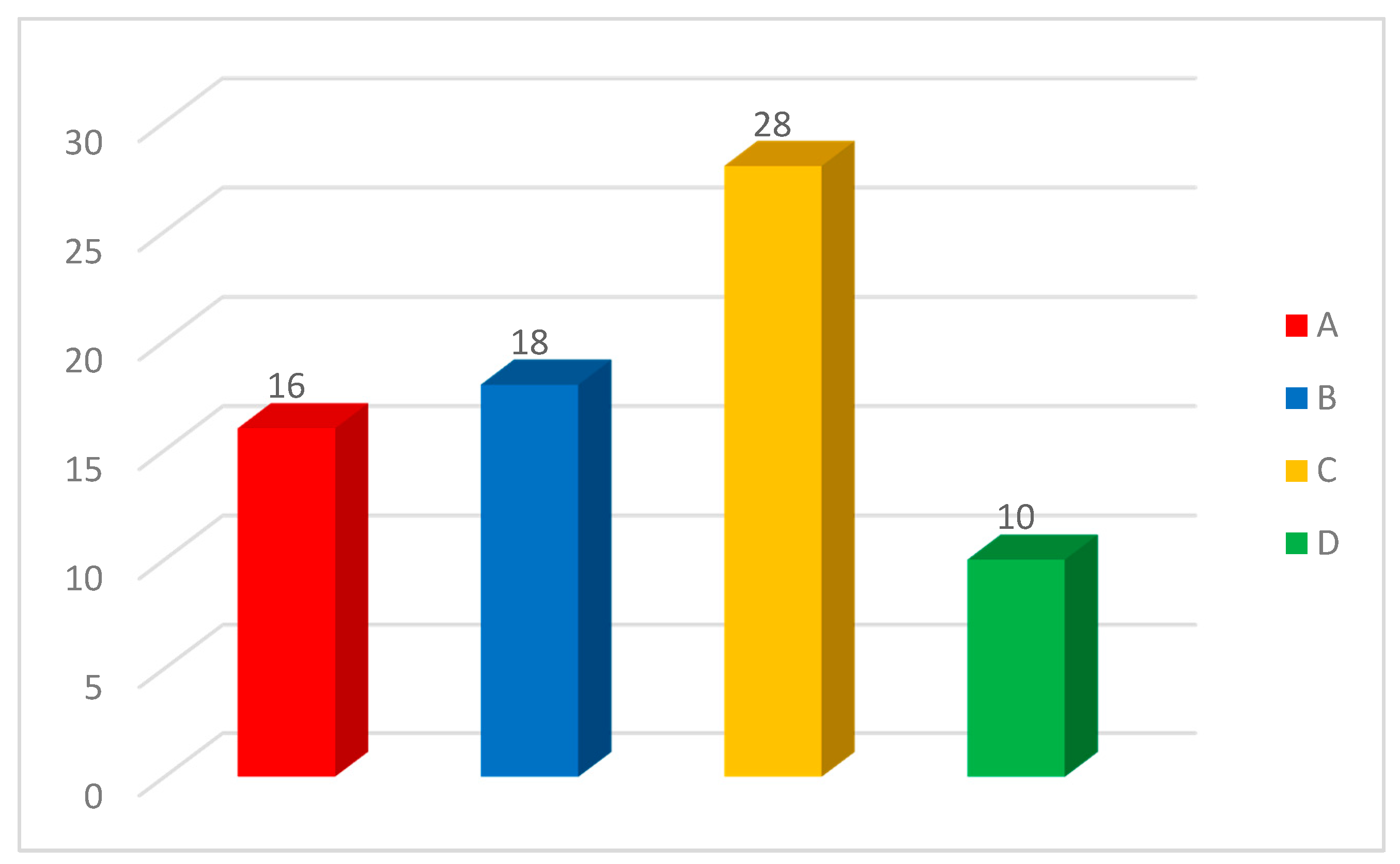
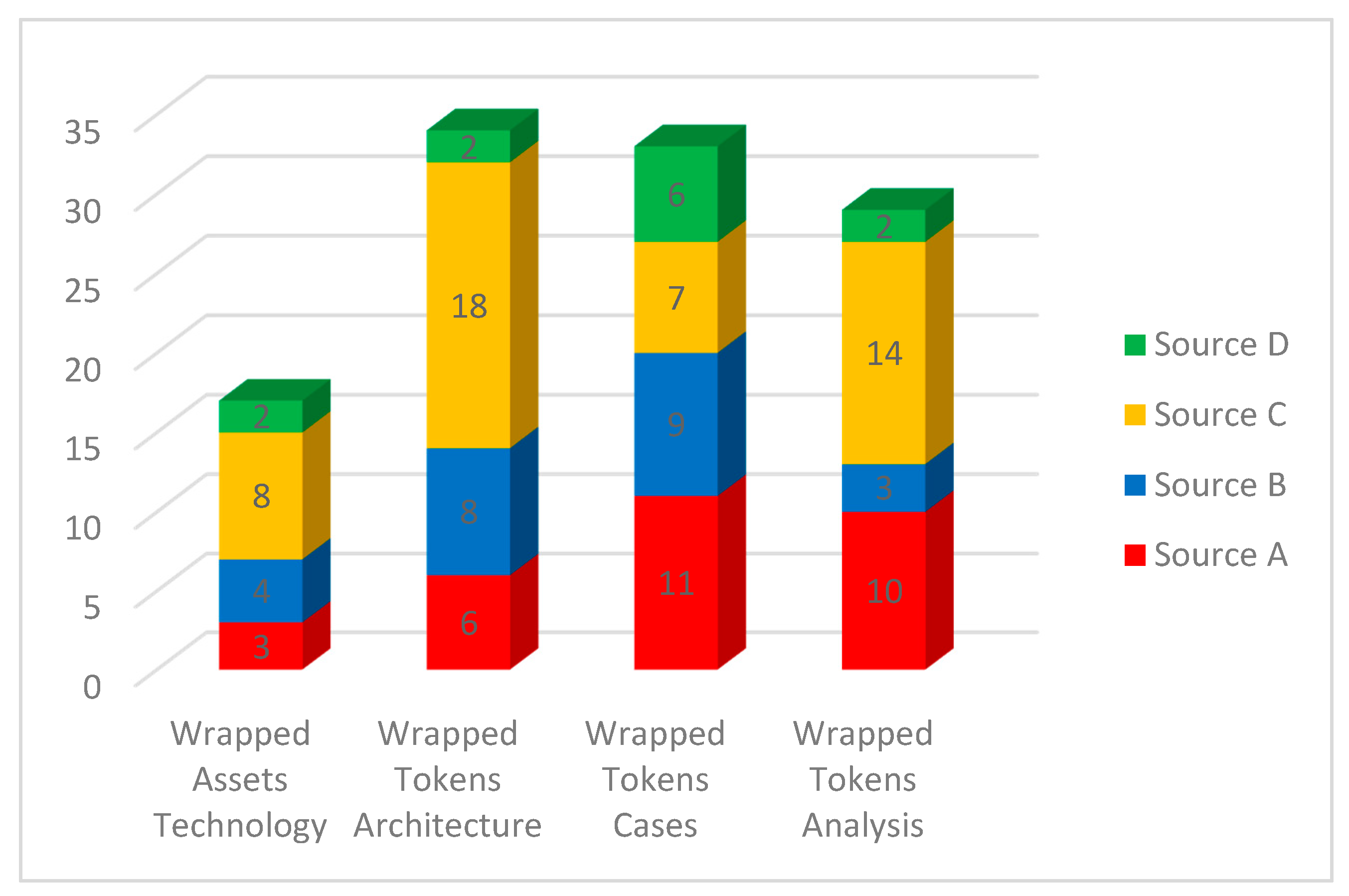
| Data Extraction Type | Description |
|---|---|
| Wrapped Assets Technology | Explanation of what a wrapped asset is and the technologies involved. |
| Wrapped Tokens Architecture | Description of how a wrapped token works. |
| Wrapped Tokens Cases | Overview of operating protocols offering wrapped tokens. |
| Wrapped Tokens Analysis | Discussion over wrapped tokens’ functionalities, advantages, and drawbacks |
| STEP 1 | Fund non-custodial wallet with ether. |
| STEP 2 | Connect the wallet to a protocol that supports WETH minting. |
| STEP 3 | Approve ETH spending (paying gas fees). |
| STEP 4 | Initiate the wrap smart contract and pay gas fees. |
| STEP 5 | Add WETH token contract address to view them in the wallet. |
| STEP 1 | Choose a trusted merchant from the WBTC.network official webpage. |
| STEP 2 | Perform KYC verification procedures. |
| STEP 3 | Fund the BTC wallet. |
| STEP 4 | Request WBTC minting (pay fees). |
| STEP 5 | Withdraw WBTC to a non-custodial address. |
| STEP 1 | Connect a non-custodial wallet to the RenVM. |
| STEP 2 | Select the BTC amount and destination network (e.g., Ethereum, BSC, Polygon). |
| STEP 3 | Send the required BTC to the unique gateway address. |
| STEP 4 | Wait for the required confirmation on the BTC network. |
| STEP 5 | Trigger the smart contract to mint RenBTC and receive them on the selected non-custodial address. |
| STEP 1 | Connect a non-custodial wallet to the Synthetix/Mintr service. |
| STEP 2 | Select the required synth and the SNX amount to be locked. |
| STEP 3 | Wait for the SNX/BTC price update. |
| STEP 4 | Approve the provider fees and collateralization ratio. |
| STEP 5 | Sign the smart contract and wait for sBTC to be minted. |
| STEP 1 | Mint or acquire WBTC from Centralized/Decentralized exchange. |
| STEP 2 | Put WBTC in a non-custodial wallet supported by the secret protocol. |
| STEP 3 | Connect both Metamask and Keplr to the protocol. |
| STEP 4 | Select token quantity to bridge and approve the transaction. |
| STEP 5 | Wait for the smart contract to execute the bridging process. |
| STEP 6 | Generate a viewing key to visualize secret token balance in the secret wallet. |
 |  |  |  |  | |
| Name | WETH (ERC-20) | WBTC | RenBTC | sBTC | sWBTC |
| Wrapping Procedure | Decentralized | Centralized | Hybrid | Synthetic | Layer two |
| Minting Costs (gas) | Ether transfer | ERC20 transfer | Uniswap swap | Uniswap Add/remove LP | ERC20 transfer |
| Acceptance | All Ethereum dApps | -Swap -Liquidity pools -Lending -Collateral | -Swap -Liquidity pools | None, except for dedicated applications | None, except for dedicated applications |
| Minting Process requirements. | -Non-custodial wallet -Swap functionalities knowledge | -KYC, -Deposits -Approval -Withdrawal | -Non-custodial wallet -Gateway functionalities knowledge | -Non-custodial wallet -Derivatives knowledge -Collateral | -Non-custodial wallet -Bridging technology knowledge |
| Available platforms. | Ethereum | Ethereum | Ethereum L1, L2 Solana Avalanche Polygon BSC | Dedicated Ethereum platforms (e.g., Kwenta) | Dedicated L2 network, with ad-hoc standard |
| Concern | Possible Negative Outcome | Affected Wrapping Procedure | Possible Solution |
|---|---|---|---|
| Merchant interaction | Loss of privacy due to KYC requirements | Centralized | Opt for decentralized/hybrid solutions |
| Third-party centralized custodian | Loss of token | Centralized, hybrid, layer two | Implement decentralized custodian service |
| Centralized protocol development | Deletion, censorship, or change in critical features | All, except for decentralized | Opt for a protocol managed by a DAO |
| Reliance on third-party oracle | Oracle manipulation | Synthetic | Reduce or remove needs for oracle calls |
| Heterogeneous asset deposit (e.g., SNX to mint sBTC) | Alteration of the represented asset total supply | Synthetic | Keep the derivative as a separate platform |
| Reliance on a dedicated network | Lower security standard | Layer two | Provide yield for moving assets to a different network |
| Non-audited smart contracts | Bug in the smart contract code | Decentralized, hybrid, layer two, synthetic | Perform specialized contract auditing |
| Restricted custodian number | Collusion of custodians for stealing the deposited assets | Centralized, hybrid, layer two | Utilize a dynamic incentive mechanism to reward custodians appropriately |
| Scarcity of users or applications | Lower utility of a wrapped token with respect to its original form | Layer two, synthetic | Incentivize competition between protocols |
| Massive increase in asset locks | Network Centralization. Reduction in the incentives of miners/stakers | All, except for synthetic | Limit to the issuance of wrapped tokens |
| Company/Provider | Interoperability Attained | Interoperability Limitations | Expectation |
|---|---|---|---|
| Weth.io | Eth interoperable with ERC-20 tokens | No other supported networks | Early obsolescence if an update makes ether compatible with ERC-20 tokens |
| WBTC Network | Bitcoin fully interoperable with the Ethereum network | No other supported networks | Turn to a hybrid/decentralized protocol or be replaced by more trustless alternatives |
| Synthetix | Interoperability among derivatives | Not usable outside their protocol | Remain a solution for derivatives only |
| RenVM | Interoperability among multiple chains | Limited assets and supported networks | Broadly integrated into cross-chains protocols if h2h upgrade proves to be successful |
| Secret Network | Interoperability on a dedicated network | Not usable outside their network | A valid alternative to layer one lack of interoperability |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the author. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Caldarelli, G. Wrapping Trust for Interoperability: A Preliminary Study of Wrapped Tokens. Information 2022, 13, 6. https://doi.org/10.3390/info13010006
Caldarelli G. Wrapping Trust for Interoperability: A Preliminary Study of Wrapped Tokens. Information. 2022; 13(1):6. https://doi.org/10.3390/info13010006
Chicago/Turabian StyleCaldarelli, Giulio. 2022. "Wrapping Trust for Interoperability: A Preliminary Study of Wrapped Tokens" Information 13, no. 1: 6. https://doi.org/10.3390/info13010006
APA StyleCaldarelli, G. (2022). Wrapping Trust for Interoperability: A Preliminary Study of Wrapped Tokens. Information, 13(1), 6. https://doi.org/10.3390/info13010006






