Security Analysis of DDoS Attacks Using Machine Learning Algorithms in Networks Traffic
Abstract
1. Introduction
1.1. Motivation
1.2. Main Contribution
- This research covers a review of ML- and DL-based IDSs, involving their pros, cons and detections methods.
- Covering and comparing different datasets available for network- and IoT-security-related research. This is done by presenting which ML was used and the resulting accuracy found.
- Presentation of the current research challenges and their future directions for research in this field.
2. Related Work
2.1. Signature-Based Detection Techniques
2.2. Anomaly-Based Detection Techniques
2.3. Hybrid-Based Detection Techniques
3. Evaluation of Performance
3.1. CICDDoS2019 Dataset
3.2. The Characteristics Utilized in the Implementation
3.3. Multibel Categorization Utilized in the Implementation
4. Measurement of Evaluation
5. Challenges and Future Work
- There are no publicly available IoT network traffic datasets. Because assessing and validating anomaly prevention strategies on a real network will be difficult, efforts to create an IoT dataset are essential. This will make evaluating and validating suggested anomaly mitigation techniques in the IoT much easier.
- There are not any standard authentication apps for IoT. The validation of implemented structures is critical since it guarantees that they are developed acceptably. The implemented structures are put to the test in a variety of ways, including simulations and tests. However, because of a lack of standard authentication applications, most of implemented IDS structures in the IoT are not evaluated in contrast to other IDS structures in the IoT. As a result, efforts must be made to produce standard authentication, which will assure duplication, reproducibility, and research continuity.
- RNN and CNN are examples of supervised and unsupervised ML techniques, and both can be discovered using the CICDDoS2019 dataset.
- It is possible to gather and examine real-time packets against the classified training dataset. It is possible to use a technique for splitting the data and comparing it with the performance of the classifiers utilized fold cross authentication.
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Acknowledgments
Conflicts of Interest
References
- Covington, M.J.; Carskadden, R. Threat implications of the Internet of Things. In Proceedings of the 2013 5th International Conference on Cyber Conflict, Tallinn, Estonia, 4–7 June 2013; pp. 1–12. [Google Scholar]
- Conner, B. Worldwide security. Netw. Secur. 2003, 2003, 16. [Google Scholar] [CrossRef]
- Sharafaldin, I.; Lashkari, A.H.; Hakak, S.; Ghorbani, A.A. Developing realistic distributed denial of service (DDoS) attack dataset and taxonomy. In Proceedings of the International Carnahan Conference on Security Technology, Chennai, India, 1–3 October 2019. [Google Scholar] [CrossRef]
- Anstee, D.; Escobar, J.; Sockrider, C. 10th Annual Worldwide Infrastructure Security Report. 2015. Available online: https://www.netscout.com/blog/cloud-crosshairs (accessed on 14 March 2021).
- Mouli, V.R.; Jevitha, K. Web Services Attacks and Security- A Systematic Literature Review. Procedia Comput. Sci. 2016, 93, 870–877. [Google Scholar] [CrossRef]
- Oliveira, R.A.; Laranjeiro, N.; Vieira, M. Assessing the security of web service frameworks against Denial of Service attacks. J. Syst. Softw. 2015, 109, 18–31. Available online: https://www.sciencedirect.com/science/article/pii/S0164121215001454 (accessed on 26 October 2021). [CrossRef]
- Abhishta; Joosten, R.; Nieuwenhuis, L.J.M. Analysing the Impact of a DDoS Attack Announcement on Victim Stock Prices. In Proceedings of the 2017 25th Euromicro International Conference on Parallel, Distributed and Network-Based Processing (PDP 2017), St. Petersburg, Russia, 6–8 March 2017; pp. 354–362. [Google Scholar] [CrossRef]
- Subbulakshmi, T.; Balakrishnan, K.; Shalinie, S.M.; Anandkumar, D.; Ganapathisubramanian, V.; Kannathal, K. Detection of DDoS attacks using Enhanced Support Vector Machines with real time generated dataset. In Proceedings of the 3rd International Conference on Advanced Computing, ICoAC 2011, Chennai, India, 14–16 December 2011; pp. 17–22. [Google Scholar] [CrossRef]
- Gupta, B.; Joshi, R.C.; Misra, M. Defending against Distributed Denial of Service Attacks: Issues and Challenges. Inf. Secur. J. A Glob. Perspect. 2009, 18, 224–247. [Google Scholar] [CrossRef]
- Samtani, S.; Kantarcioglu, M.; Chen, H. Trailblazing the Artificial Intelligence for Cybersecurity Discipline. ACM Trans. Manag. Inf. Syst. 2020, 11, 1–19. [Google Scholar] [CrossRef]
- Zarpelão, B.B.; Miani, R.S.; Kawakani, C.T.; de Alvarenga, S.C. A survey of intrusion detection in Internet of Things. J. Netw. Comput. Appl. 2017, 84, 25–37. [Google Scholar] [CrossRef]
- Kumar, R.; Kumar, P.; Tripathi, R.; Gupta, G.P.; Kumar, N.; Hassan, M.M. A Privacy-Preserving-Based Secure Framework Using Blockchain-Enabled Deep-Learning in Cooperative Intelligent Transport System. IEEE Trans. Intell. Transp. Syst. 2021. [Google Scholar] [CrossRef]
- Liu, C.; Yang, J.; Chen, R.; Zhang, Y.; Zeng, J. Research on immunity-based intrusion detection technology for the Internet of Things. In Proceedings of the 2011 7th International Conference on Natural Computation, ICNC 2011, Shanghai, China, 26–28 July 2011; Volume 1, pp. 212–216. [Google Scholar] [CrossRef]
- Kasinathan, P.; Pastrone, C.; Spirito, M.A.; Vinkovits, M. Denial-of-Service detection in 6LoWPAN based Internet of Things. In Proceedings of the International Conference on Wireless and Mobile Computing, Networking and Communications, Lyon, France, 7–9 October 2013; pp. 600–607. [Google Scholar] [CrossRef]
- Kasinathan, P.; Costamagna, G.; Khaleel, H.; Pastrone, C.; Spirito, M.A. Demo: An IDS framework for internet of things empowered by 6LoWPAN. In Proceedings of the ACM Conference on Computer and Communications Security, Berlin, Germany, 4–8 November 2013; pp. 1337–1339. [Google Scholar] [CrossRef]
- Oh, D.; Kim, D.; Ro, W.W. A Malicious Pattern Detection Engine for Embedded Security Systems in the Internet of Things. Sensors 2014, 14, 24188–24211. [Google Scholar] [CrossRef]
- Ioulianou, P.; Vasilakis, V.; Moscholios, I.; Logothetis, M. A Signature-based Intrusion Detection System for the Internet of Things. Jun 2018. Available online: https://eprints.whiterose.ac.uk/133312/ (accessed on 28 March 2021).
- Keshk, M.; Turnbull, B.; Moustafa, N.; Vatsalan, D.; Choo, K.-K.R. A Privacy-Preserving-Framework-Based Blockchain and Deep Learning for Protecting Smart Power Networks. IEEE Trans. Ind. Inform. 2019, 16, 5110–5118. [Google Scholar] [CrossRef]
- Mitchell, R.; Chen, I.-R. A survey of intrusion detection techniques for cyber-physical systems. ACM Comput. Surv. 2014, 46, 1–29. [Google Scholar] [CrossRef]
- Jan, S.U.; Ahmed, S.; Shakhov, V.; Koo, I. Toward a Lightweight Intrusion Detection System for the Internet of Things. IEEE Access 2019, 7, 42450–42471. [Google Scholar] [CrossRef]
- Deshmukh-Bhosale, S.; Sonavane, S.S. A Real-Time Intrusion Detection System for Wormhole Attack in the RPL based Internet of Things. Procedia Manuf. 2019, 32, 840–847. [Google Scholar] [CrossRef]
- Raza, S.; Wallgren, L.; Voigt, T. SVELTE: Real-time intrusion detection in the Internet of Things. Ad Hoc Netw. 2013, 11, 2661–2674. [Google Scholar] [CrossRef]
- Hamza, A.; Gharakheili, H.H.; Benson, T.A.; Sivaraman, V. Detecting Volumetric Attacks on IoT Devices via SDN-Based Monitoring of MUD Activity. In Proceedings of the 2019 ACM Symposium on SDN Research, SOSR 2019, San Jose, CA, USA, 3–4 April 2019; pp. 36–48. [Google Scholar] [CrossRef]
- Cvitić, I.; Peraković, D.; Periša, M.; Botica, M. Novel approach for detection of IoT generated DDoS traffic. Wirel. Netw. 2019, 27, 1573–1586. [Google Scholar] [CrossRef]
- Cvitić, I.; Peraković, D.; Periša, M.; Gupta, B. Ensemble machine learning approach for classification of IoT devices in smart home. Int. J. Mach. Learn. Cybern. 2021, 12, 3179–3202. [Google Scholar] [CrossRef]
- Cvitic, I.; Perakovic, D.; Gupta, B.; Choo, K.-K.R. Boosting-based DDoS Detection in Internet of Things Systems. IEEE Internet Things J. 2021, 1. [Google Scholar] [CrossRef]
- Srinivas, T.A.S.; Manivannan, S. Prevention of Hello Flood Attack in IoT using combination of Deep Learning with Improved Rider Optimization Algorithm. Comput. Commun. 2020, 163, 162–175. [Google Scholar] [CrossRef]
- Ujjan, R.M.A.; Pervez, Z.; Dahal, K.; Bashir, A.K.; Mumtaz, R.; González, J. Towards sFlow and adaptive polling sampling for deep learning based DDoS detection in SDN. Future Gener. Comput. Syst. 2019, 111, 763–779. [Google Scholar] [CrossRef]
- Priyadarshini, R.; Barik, R.K. A deep learning based intelligent framework to mitigate DDoS attack in fog environment. J. King Saud Univ.-Comput. Inf. Sci. 2019. [Google Scholar] [CrossRef]
- Hasan, Z.; Hasan, K.Z.; Sattar, A. Burst Header Packet Flood Detection in Optical Burst Switching Network Using Deep Learning Model. Procedia Comput. Sci. 2018, 143, 970–977. [Google Scholar] [CrossRef]
- Krishnan, P.; Duttagupta, S.; Achuthan, K. VARMAN: Multi-plane security framework for software defined networks. Comput. Commun. 2019, 148, 215–239. [Google Scholar] [CrossRef]
- Zhu, M.; Ye, K.; Xu, C.Z. Network Anomaly Detection and Identification Based on Deep Learning Methods. In International Conference on Cloud Computing; Springer: Cham, Switzerland, 2018; Volume 10967 LNCS, pp. 219–234. [Google Scholar] [CrossRef]
- Alzahrani, S.; Hong, L. Detection of distributed denial of service (ddos) attacks using artificial intelligence on cloud. In Proceedings of the 2018 IEEE World Congress on Services, SERVICES 2018, San Francisco, CA, USA, 2–7 July 2018; pp. 37–38. [Google Scholar] [CrossRef]
- Alzahrani, R.J.; Alzahrani, A. Survey of Traffic Classification Solution in IoT Networks. Int. J. Comput. Appl. 2021, 183, 37–45. [Google Scholar] [CrossRef]
- Rudman, L.; Irwin, B. Characterization and analysis of NTP amplification based DDoS attacks. In Proceedings of the 2015 Information Security for South Africa, Johannesburg, South Africa, 12–13 August 2015. [Google Scholar] [CrossRef]
- Liu, Q.; Zhang, Y. TFTP vulnerability finding technique based on fuzzing. Comput. Commun. 2008, 31, 3420–3426. [Google Scholar] [CrossRef]
- Rehman, S.U.; Khaliq, M.; Imtiaz, S.I.; Rasool, A.; Shafiq, M.; Javed, A.R.; Jalil, Z.; Bashir, A.K. DIDDOS: An approach for detection and identification of Distributed Denial of Service (DDoS) cyberattacks using Gated Recurrent Units (GRU). Future Gener. Comput. Syst. 2021, 118, 453–466. [Google Scholar] [CrossRef]
- Wang, X.; Sun, Y.; Nanda, S.; Wang, X. Looking from the Mirror: Evaluating IoT Device Security through Mobile Companion Apps. 2019. Available online: https://www.usenix.org/conference/usenixsecurity19/presentation/wang-xueqiang (accessed on 26 October 2021).
- Hudaib, A.A.Z.; Hudaib, E.A.Z. DNS advanced attacks and analysis. Int. J. Comput. Sci. Secur. 2014, 8, 63–74. Available online: http://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.736.2315&rep=rep1&type=pdf (accessed on 26 October 2021).
- Alonso, J.M.; Bordon, R.; Beltrán, M.; Guzmán, A. LDAP injection techniques. In Proceedings of the 2008 11th IEEE Singapore International Conference on Communication Systems, ICCS 2008, Guangzhou, China, 19–21 November 2008; pp. 980–986. [Google Scholar] [CrossRef]
- Sarıkoz, B.G. An Information Security Framework for Web Services in Enterprise Networks. 2015. Available online: https://open.metu.edu.tr/handle/11511/24441 (accessed on 26 October 2021).
- Gondim, J.J.; Albuquerque, R.D.O.; Orozco, A.L.S. Mirror saturation in amplified reflection Distributed Denial of Service: A case of study using SNMP, SSDP, NTP and DNS protocols. Future Gener. Comput. Syst. 2020, 108, 68–81. [Google Scholar] [CrossRef]
- Yaacoub, J.-P.A.; Noura, H.N.; Salman, O.; Chehab, A. Robotics cyber security: Vulnerabilities, attacks, countermeasures, and recommendations. Int. J. Inf. Secur. 2021, 1–44. [Google Scholar] [CrossRef]
- Lau, F.; Rubin, S.H.; Smith, M.H.; Trajković, L. Distributed denial of service attacks. In Proceedings of the IEEE International Conference on Systems, Man and Cybernetics, Nashville, TN, USA, 8–11 October 2000; Volume 3, pp. 2275–2280. [Google Scholar] [CrossRef]
- Chica, J.C.C.; Imbachi, J.C.; Vega, J.F.B. Security in SDN: A comprehensive survey. J. Netw. Comput. Appl. 2020, 159, 102595. [Google Scholar] [CrossRef]
- Yusof, M.A.M.; Ali, F.H.M.; Darus, M.Y. Detection and Defense Algorithms of Different Types of DDoS Attacks. Int. J. Eng. Technol. 2018, 9, 410–444. [Google Scholar] [CrossRef][Green Version]
- Perez-Diaz, J.A.; Valdovinos, I.A.; Choo, K.-K.R.; Zhu, D. A Flexible SDN-Based Architecture for Identifying and Mitigating Low-Rate DDoS Attacks Using Machine Learning. IEEE Access 2020, 8, 155859–155872. [Google Scholar] [CrossRef]
- Karan, B.v.; Narayan, D.G.; Hiremath, P.S. Detection of DDoS Attacks in Software Defined Networks. In Proceedings of the 2018 3rd International Conference on Computational Systems and Information Technology for Sustainable Solutions, CSITSS, Bengaluru, India, 20–22 December 2018; pp. 265–270. [Google Scholar] [CrossRef]
- Ravi, N.; Shalinie, S.M. Learning-Driven Detection and Mitigation of DDoS Attack in IoT via SDN-Cloud Architecture. IEEE Internet Things J. 2020, 7, 3559–3570. [Google Scholar] [CrossRef]
- Asharf, J.; Moustafa, N.; Khurshid, H.; Debie, E.; Haider, W.; Wahab, A. A Review of Intrusion Detection Systems Using Machine and Deep Learning in Internet of Things: Challenges, Solutions and Future Directions. Electronics 2020, 9, 1177. [Google Scholar] [CrossRef]


| Study | Model | Dataset | Application Area | Feature | Result |
|---|---|---|---|---|---|
| [27] | DBN | Generated dataset | IoT Network | BAU-ROA optimization | Produces a better outcome than other optimization methods |
| [28] | SAE | Generated dataset | SDN of IoT | sFlow-based and adaptive polling | sFlow 91% accuracy and Adaptive polling 89% accuracy |
| [29] | LSTM | ISCX 2012 and IDS CTU-13 | Fog and cloud | LSTM has 128 units and three hidden layers | The accuracy rate was 98.88% |
| [30] | DCNN | Generated dataset | Traffic classification | To analyse few number samples in the dataset | The accuracy of the model was 99% and better than shallow ML algorithms in terms of performance |
| [31] | NDAE and RF | NSL-KDD and CICIDS2017 | SDN | DL and shallow learning algorithms are combined in a hybrid model. | Accuracy was 98%. As a consequence, it has higher accuracy than others because it has a lower false-positive rate (FPR) less than 5% |
| [32] | FNN and CNN | NSL-KDD | Traffic categorization | An efficient feature modelling ability | Higher accuracy than shallow machine learning algorithms |
| [33] | ANN | Generated dataset | IDS | An integration of signature-based detection and ANN | The accuracy value was 99.98% |
| [34] | DT, K-NN, NB and GRB | BoT-IoT dataset | IoT Network | Analysis normal and attack traffic | Better accuracy in DT and GRB with 99.96% and 99.88%, respectively. |
| DDoS Attribute (Class Label) | Number of Instances |
|---|---|
| DNS | 5,071,011 |
| LDAP | 2,179,930 |
| MSSQL | 4,522,492 |
| NetBIOS | 4,093,279 |
| NTP | 1,202,642 |
| SNMP | 5,159,870 |
| SSDP | 2,610,611 |
| SYN | 1,582,289 |
| TFTP | 20,082,580 |
| UDP | 3,134,645 |
| UDP_Lag | 366,461 |
| Feature | Description |
|---|---|
| Fwd Packet Length Max | Maximum packet size in the forward (outgoing) direction |
| Fwd Packet Length Min | Smallest packet size in the forward route |
| Min Packet Length | Minimum of a packet’s length |
| Max Packet Length | Maximum of a packet’s length |
| Average Packet Size | A packet’s average size |
| FWD Packets/s | Number of forward packets (p/s) |
| Fwd Header Length | The extent of a forwarded packet’s header |
| Fwd Header Length 1 | Number of bytes in a header in the forward direction |
| Min_Seg_Size_Forward | Minimum segment size in the forward direction |
| Total Length of Fwd Packet | Packet size in the forward direction |
| Fwd Packet Length Std | The standard deviation of a packet in the forward direction |
| Flow IAT Min | The minimum amount of time passes between two packets in a flow |
| Subflow Fwd Bytes | The average number of bytes in a sub-flow in the forward direction |
| Destination Port | Address to accept the sent TCP or UDP packets |
| Protocol | TCP or UDP for data transference |
| Packet Length Std | The packet extent standard variation |
| Flow Duration | The flow’s duration in μs |
| Fwd IAT Total | In the forward route, the total time among two packets |
| ACK Flag Count | The number of packets with ACK |
| Init_Win_Bytes_Forward | In the forward route, the number of bytes in the early window |
| Flow IAT Mean | Mean time amongst two packets in the flow |
| Flow IAT Max | Maximum time amongst two packets in the flow |
| Fwd IAT Mean | Mean time amongst two packets in the forward route |
| Fwd IAT Max | Maximum time amongst two packets in the forward route |
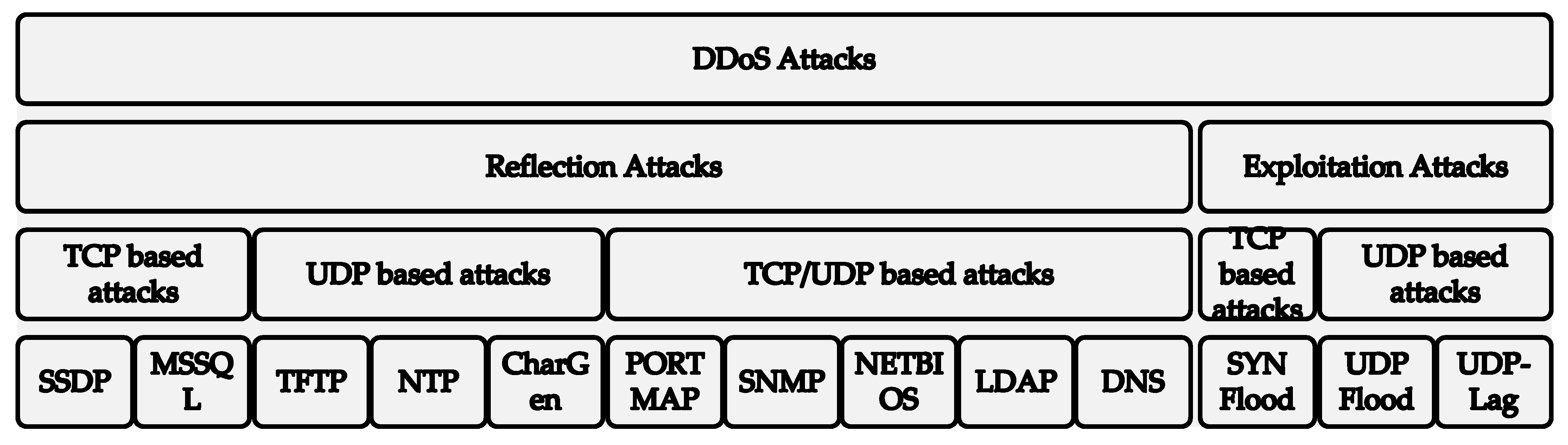
| Type | Class | Description | |
|---|---|---|---|
| Reflection based attack | UDP Attacks | NTP | The attacker uses publicly available NTP servers to overload the aim with UDP traffic in an expansion attack known as NTP [35]. |
| TFTP | The buffer excess defenselessness in TFTP and server is taking advantage of TFTP attack [36]. | ||
| TCP Attacks | MSSQL | An injection of the MSSQL allows malicious SQL declarations to be executed [37]. | |
| SSDP | An SSDP attack uses universal plug and play (UPnP) networking protocols to direct a massive volume of traffic to a victim, causing their computational properties to be overwhelmed [38]. | ||
| TCP/UDP Attacks | DNS | A DNS attack takes use of DNS flaws [39]. | |
| LDAP | LDAP injection is an attack utilized to achieve web-based applications that structure LDAP declarations based on client information [40]. | ||
| NETBIOS | A security flaw in NetBIOS permits an attacker to read data [41]. | ||
| SNMP | An SNMP attack produces a huge amount of traffic that is pointed towards numerous networks’ victims [42]. | ||
| Exploitation based attack | TCP Attack | SYN Flood | SYN flood is a type of DoS attack in which an attacker forwards a series of SYN requests to a target system in order to exhaust server resources and render the system unusable to real traffic [43]. |
| UDP Attacks | UDP | Flooding with UDP packets is an attack that sends a high amount of UDP packets to a victim to overload their capability to proceed and reply. As a result, the firewall that protects the victim server is overburdened [44]. | |
| UDP-Lag | UDP-Lag is a type of attack that deactivate the client-server relationship [3]. | ||
| Symbol | Meaning |
|---|---|
| True Positive (tp) | It is the amount of DDoS attacks that have been recognized as attacks. |
| True Negative () | It is the amount of legitimate network traffic instances benign recognized as legitimate. |
| False Positive () | It is the amount of legitimate network traffic examples benign misidentified as attacks. |
| False Negative () | It is the amount of DDoS attacks that cannot be defined as legitimate. |
| TPR | The amount of DDoS attacks exposed as attacks is split by the total amount of DDoS attacks in the dataset and is calculated as shown in Equation (1). |
| FPR | Calculated by dividing the amount number of benign instances imperfectly distributed as DDoS attacks by the whole amount number of benign instances in a dataset, and it is calculated as shown in Equation (2). |
| Precision () | Defined as the amount number of among all instances that are forecast to be positive, and it is calculated as shown in Equation (3). |
| Recall () | The percentage of from all instances that are essentially positive and is calculated as shown in Equation (4). |
| f-measure | The weighted harmonic means of precision and recall and is calculated as shown in Equation (5). |
| Accuracy | It is obtained by the equation below, and it displays the model’s exact forecast rate, and it is calculated as shown in Equation (6). |
| Selected Algorithm | Accuracy | Precision | Recall | F-Measure | Computation Time |
|---|---|---|---|---|---|
| K_Nearest_Neighbors (K-NN) | 0.98 | 0.99 | 0.99 | 0.99 | 3.5 s |
| Super Vector Machine (SVM) | 0.86 | 0.86 | 0.87 | 0.85 | 7.29 s |
| Naïve Bayes (NB) | 0.45 | 0.66 | 0.54 | 0.38 | 1.3 s |
| Decision Tree (DT) | 0.99 | 0.99 | 0.99 | 0.99 | 4.53 s |
| Random Forest (RF) | 0.99 | 0.99 | 0.99 | 0.99 | 84.2 s |
| Logistic Regression (LR) | 0.98 | 0.99 | 0.98 | 0.99 | 5.53 s |
| Datasets | Feature Selection | ML Algorithms | Accuracy |
|---|---|---|---|
| CIC DoS dataset [47] | No feature selection | RT, J48, REP Tree, SVM, RF, MLP | 95% |
| KDD Cup’99 [48] | No feature selection | SVM and DNN | 92.30% |
| UNB-ISCX [49] | No feature selection | Semi-supervised ML algorithm | 96.28% |
| CICDDoS2019 (Our approach) | Feature selection RFR | SVM, K-NN, DT, NB, RF and LR | 99% |
| ML Method | Pros | Cons |
|---|---|---|
| KNN |
|
|
| SVM |
|
|
| NB |
|
|
| DT |
|
|
| RF |
|
|
| LR |
|
|
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Alzahrani, R.J.; Alzahrani, A. Security Analysis of DDoS Attacks Using Machine Learning Algorithms in Networks Traffic. Electronics 2021, 10, 2919. https://doi.org/10.3390/electronics10232919
Alzahrani RJ, Alzahrani A. Security Analysis of DDoS Attacks Using Machine Learning Algorithms in Networks Traffic. Electronics. 2021; 10(23):2919. https://doi.org/10.3390/electronics10232919
Chicago/Turabian StyleAlzahrani, Rami J., and Ahmed Alzahrani. 2021. "Security Analysis of DDoS Attacks Using Machine Learning Algorithms in Networks Traffic" Electronics 10, no. 23: 2919. https://doi.org/10.3390/electronics10232919
APA StyleAlzahrani, R. J., & Alzahrani, A. (2021). Security Analysis of DDoS Attacks Using Machine Learning Algorithms in Networks Traffic. Electronics, 10(23), 2919. https://doi.org/10.3390/electronics10232919






