Routing Protocols for Mobile Internet of Things (IoT): A Survey on Challenges and Solutions
Abstract
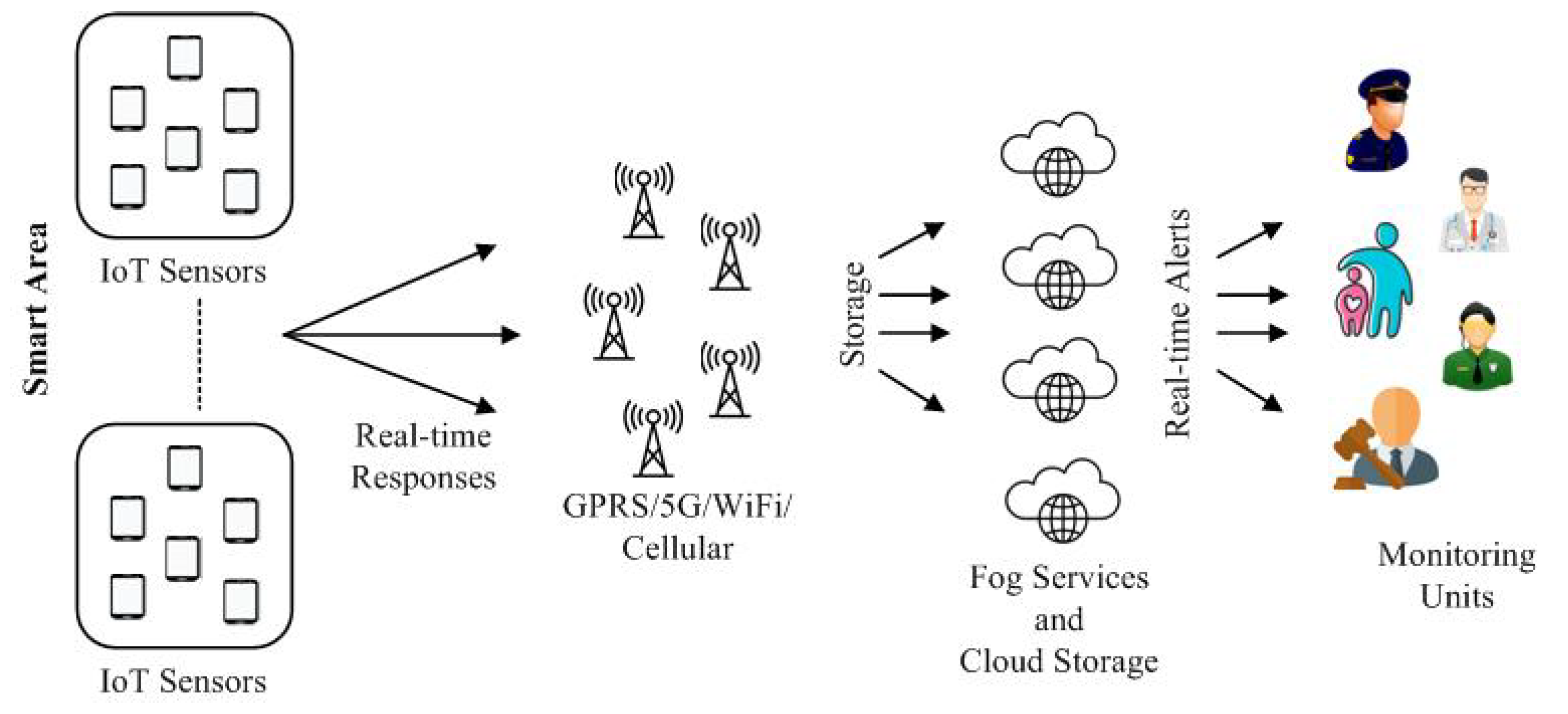
:1. Introduction
- To analyze the issues faced by RPL when IoT devices are non-stationary;
- To critically evaluate the solutions that are proposed in the current literature to mitigate the issues faced by RPL during mobility of IoT devices;
- To categorize various solutions into different types and illustrate the working principle, strengths, and weaknesses of each solution; and
- To propose future research directions that can be explored to propose better solutions to the issues faced by RPL during the mobility of IoT devices.
2. Background and Literature Review
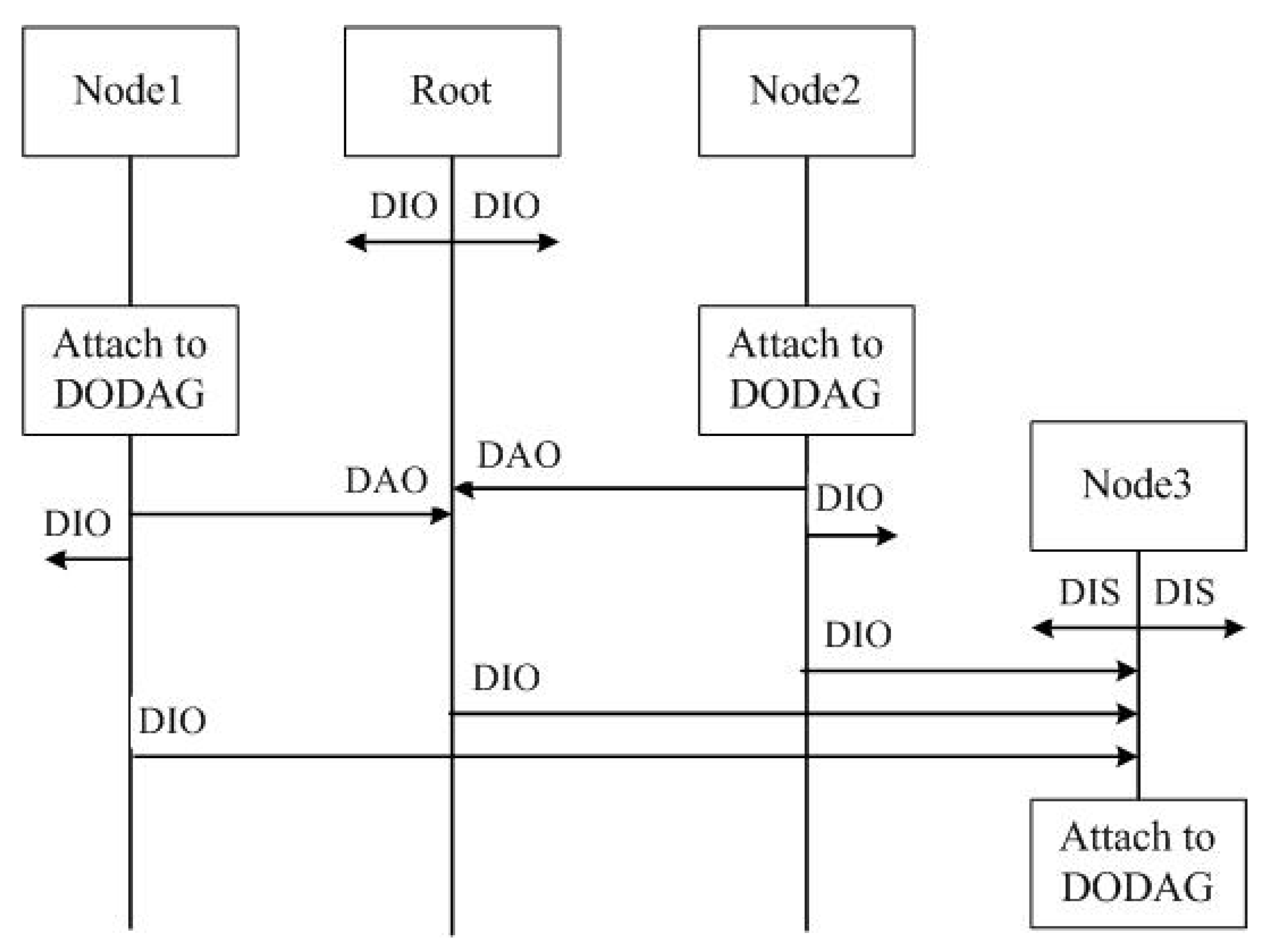
2.1. Background
2.2. Literature Review
3. Issues Faced by RPL during Mobility
3.1. Lack of Identification of Mobile IoT Nodes
3.2. Issues with Trickle Algorithm
3.3. Loops in the Network
3.4. Delay Caused by ETX Probing
3.5. Lack of Positioning Information
3.6. Increase in Hand-off Delays
3.7. Issues with the Rank of Detached Mobile Nodes
3.8. Lack of Sink-to-Sink Cooperation
4. Solutions to the Issues Faced by RPL during Mobility
4.1. Trickle Timer-Based Solutions
4.1.1. Co-RPL
4.1.2. Enhanced Trickle Algorithm
4.1.3. Mobility Enhanced RPL
4.1.4. Elastic Trickle Timer Algorithm
4.2. ETX-Based Solutions
4.2.1. Fuzzy Logic Based Energy-Aware Routing Protocol (FLEA-RPL)
4.2.2. Multi-Fuzzy Model (MI-FL)
4.2.3. A Congestion Avoidance Multipath Routing Protocol (CA-RPL)
4.2.4. Modified RPL
4.2.5. Multiple Sinks
4.3. RSSI Based Solutions
4.3.1. Mobility and Energy-Aware Routing Protocol (ME-RPL)
4.3.2. Game-Theoretic Optimization of RPL (GTM-RPL)
4.3.3. MoMoRo
4.3.4. Enhanced Hand-Off Mechanism
4.3.5. mRPL
4.3.6. Energy and Mobility Aware Routing (EMA-RPL)
4.3.7. DAG-Based Multipath Routing (DMR)
4.4. Position-Based Solutions
4.4.1. Kalman Positioning RPL (KP-RPL)
4.4.2. Mobility Prediction Based RPL (MP-RPL)
4.5. Miscellaneous Solutions
4.5.1. Sink-to-Sink Coordination Framework (SSCF)
4.5.2. Downward Path Construction Mechanism
5. Future Work
5.1. Efficient Routing Protocol Supporting Various Traffic Patterns
5.2. Mobility Support
5.3. Energy-Efficient Routing
5.4. Privacy-Aware Routing
5.5. Exhaustive List of Experimental Parameters
6. Conclusions
Author Contributions
Funding
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Madakam, S.; Ramaswamy, R.; Tripathi, S. Internet of Things (IoT): A Literature Review. J. Comput. Commun. 2015, 3, 164–173. [Google Scholar] [CrossRef] [Green Version]
- IoT Growth Demands Rethink of Long-Term Storage Strategies, Says IDC. Available online: https://www.idc.com/getdoc.jsp?containerId=prAP46737220 (accessed on 28 December 2020).
- Raza, S. Medium Access Control Protocols for Reliable Communication in Low-Power Industrial Applications. Ph.D. Thesis, Otto-von-Guericke-Universität Magdeburg, Magdeburg, Germany, 2020. [Google Scholar]
- Farag, H. Enabling Industrial IoT Applications: Supporting Reliable and Real-Time Data Delivery. Ph.D. Thesis, Mid Sweden University, Östersund, Sweden, 2020. [Google Scholar]
- Kim, S.; Kim, C.; Cho, H.; Jung, K. A Hierarchical Routing Graph for Supporting Mobile Devices in Industrial Wireless Sensor Networks. Sensors 2021, 21, 458. [Google Scholar] [CrossRef] [PubMed]
- Bharat, B.; Gadadhar, S. Requirements, protocols, and security challenges in wireless sensor networks: An industrial perspective. In Handbook of Computer Networks and Cyber Security; Springer: Berlin/Heidelberg, Germany, 2020; pp. 683–713. [Google Scholar]
- Azadeh, Z. Remote Patient Monitoring: Health Status Detection and Prediction in IoT-Based Health Care. In IoT in Healthcare and Ambient Assisted Living; Springer: Berlin/Heidelberg, Germany, 2021; pp. 89–102. [Google Scholar]
- Wu, T.-Y.; Wang, T.; Lee, Y.-Q.; Zheng, W.; Kumari, S.; Kumar, S. Improved Authenticated Key Agreement Scheme for Fog-Driven IoT Healthcare System. Secur. Commun. Netw. 2021, 2021, 1–16. [Google Scholar]
- Kavita, J.; Veena, A. A Survey on IoT-Based Healthcare System: Potential Applications, Issues, and Challenges. In Advances in Biomedical Engineering and Technology; Springer: Berlin/Heidelberg, Germany, 2021; pp. 459–471. [Google Scholar]
- Doshi, H.; Shankar, A. Wireless Sensor Network Application for IoT-Based Healthcare System. In Data Driven Approach towards Disruptive Technologies: Proceedings of MIDAS; Springer: Singapore, 2020; pp. 287–307. [Google Scholar]
- Haque, H.M.U.; Zulfiqar, H.; Ahmed, A.; Ali, Y. A context-aware framework for modelling and verification of smart parking systems in urban cities. Concurr. Comput. Pract. Exp. 2019, 33, 5401. [Google Scholar]
- Ma, X.; Hu, X.; Weber, T.; Schramm, D. Experiences with Establishing a Simulation Scenario of the City of Duisburg with Real Traffic Volume. Appl. Sci. 2021, 11, 1193. [Google Scholar] [CrossRef]
- Frenken, M.; Flessner, J.; Hurka, J. Building Automation and Control Systems for Healthcare in Smart Homes. In Handbook of Large-Scale Distributed Computing in Smart Healthcare; Springer: Berlin/Heidelberg, Germany, 2017; pp. 87–119. [Google Scholar]
- Wibhada, N.; Ridnarong, P.; Aimaschana, N. Remote air conditioning control system based on ZigBee Wireless Sensor Network for building. In Proceedings of the IEEE 2015 International Computer Science and Engineering Conference (ICSEC), Chiang Mai, Thailand, 23–26 November 2015; pp. 1–6. [Google Scholar]
- Admire, M.; Muthoni, M. Implementation of middleware for internet of things in asset tracking applications: In-lining approach. In Proceedings of the 2015 IEEE 13th international conference on industrial informatics (INDIN), Cambridge, UK, 22–24 July 2015; pp. 460–469. [Google Scholar]
- Mhlaba, A.M.; Masinde, M. An Integrated Internet of Things Based System for Tracking and Monitoring Assets–the case of the Central University of Technology. In Proceedings of the IST-Africa 2015 Conference Proceedings, Lilongwe, Malawi, 6–8 May 2015. [Google Scholar]
- Choudhary, P.; Bhargava, L.; Suhag, A.K.; Choudhary, M.; Singh, S. An Era of Internet of Things Leads to Smart Cities Initiatives Towards Urbanization. In Digital Cities Roadmap: IoT-Based Architecture and Sustainable Buildings; Wiley: Hoboken, NJ, USA, 2021; pp. 319–350. [Google Scholar]
- Huang, X.; Yi, J.; Zhu, X.; Chen, S. A Semantic Approach with Decision Support for Safety Service in Smart Home Management. Sensors 2016, 16, 1224. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Ghabar, O. An Investigation into Context-Aware Automated Service in Smart Home Facilities: Search Engine and Machine Learning with Smartphone. Ph.D. Thesis, University of Huddersfield, Huddersfield, UK, 2018. [Google Scholar]
- Sanaboina, C.S.; Sanaboina, P. Impact of mobility on power consumption in RPL. i-Managers J. Wirel. Commun. Netw. 2018, 6, 23. [Google Scholar]
- Winter, T.; (Ed.) RPL: IPv6 Routing Protocol for Low-Power and Lossy Networks. Internet Engineering Task Force (IETF), ISSN: 2070-1721, RFC: 6550. March 2012. Available online: https://datatracker.ietf.org/doc/html/rfc6550 (accessed on 1 September 2021).
- Ghaleb, B.; Al-Dubai, A.Y.; Ekonomou, E.; Alsarhan, A.; Nasser, Y.; Mackenzie, L.M.; Boukerche, A. A survey of limitations and enhancements of the IPv6 routing protocol for low-power and lossy networks: A focus on core operations. IEEE Commun. Surv. Tutor. 2018, 21, 1607–1635. [Google Scholar] [CrossRef] [Green Version]
- Kim, H.-S.; Ko, J.; Culler, D.E.; Paek, J. Challenging the IPv6 routing protocol for low-power and lossy networks (RPL): A survey. IEEE Commun. Surv. Tutor. 2017, 19, 2502–2525. [Google Scholar] [CrossRef]
- Kharrufa, H.; Al-Kashoash, H.A.; Kemp, A.H. RPL-based routing protocols in IoT applications: A review. IEEE Sens. 2019, 19, 5952–5967. [Google Scholar] [CrossRef] [Green Version]
- Lamaazi, H.; Benamar, N. A comprehensive survey on enhancements and limitations of the RPL protocol: A focus on the objective function. Ad Hoc Netw. 2020, 96, 102001. [Google Scholar] [CrossRef]
- Sebastian, A.; Sivagurunathan, S. A survey on load balancing schemes in RPL based internet of things. Int. J. Sci. Res. Netw. Secur. Commun. 2018, 6, 43–49. [Google Scholar]
- Pancaroglu, D.; Sen, S. Load balancing for RPL-based Internet of Things: A review. Ad Hoc Netw. 2021, 116, 102491. [Google Scholar] [CrossRef]
- Oliveira, A.; Vazão, T. Low-power and lossy networks under mobility: A survey. Comput. Netw. 2016, 107, 339–352. [Google Scholar] [CrossRef]
- Zhao, M.; Kumar, A.; Chong, P.H.J.; Lu, R. A comprehensive study of RPL and P2P-RPL routing protocols: Implementation, challenges and opportunities. Appl. Peer-to-Peer Netw. 2017, 10, 1232–1256. [Google Scholar] [CrossRef]
- Kamgueu, P.O.; Nataf, E.; Ndie, T.D. Survey on RPL enhancements: A focus on topology, security and mobility. Comput. Commun. 2018, 120, 10–21. Available online: http://www.sciencedirect.com/science/article/pii/S0140366417308241 (accessed on 1 September 2021). [CrossRef]
- Rodrigues, J.; Neves, P.A.C.S. A survey on IP-based wireless sensor network solutions. Int. J. Commun. Syst. 2010, 23, 963–981. [Google Scholar] [CrossRef]
- Latif, K.; Javaid, N.; Ullah, I.; Kaleem, Z.; Malik, Z.A.; Nguyen, L.D.; Abbas, Z. DIEER: Delay-Intolerant Energy-Efficient Routing with Sink Mobility in Underwater Wireless Sensor Networks. Sensors 2020, 20, 3467. [Google Scholar] [CrossRef]
- Ko, J.; Terzis, A.; Dawson-Haggerty, S.; Culler, D.E.; Hui, J.W.; Levis, P. Connecting low-power and lossy networks to the internet. IEEE Commun. Mag. 2011, 49, 96–101. [Google Scholar]
- Dohler, M.; Watteyne, T.; Winter, T.; Barthel, D. Routing Requirements for Urban Low-Power and Lossy Networks. RFC 5548. 2009. Available online: https://datatracker.ietf.org/doc/html/rfc5548 (accessed on 1 September 2021).
- Pister, K.; Thubert, P.; Dwars, S.; Phinney, T. Industrial Routing Requirements in Low-Power and Lossy Networks. Citeseer. 2009. Available online: https://datatracker.ietf.org/doc/rfc5673/ (accessed on 1 September 2021).
- Porcu, G.; Buron, J.; Brandt, A. Home Automation Routing Requirements in Low-Power and Lossy Networks; RFC 5826; IETF Secretariat: Fremont, CA, USA, 2010. [Google Scholar]
- Martocci, J.; Mil, P.; Riou, N.; Vermeylen, W. Building Automation Routing Requirements in Low-Power and Lossy Networks; RFC 5867; IETF Secretariat: Fremont, CA, USA, 2010. [Google Scholar]
- Kharrufa, H.; Al-Kashoash, H.; Kemp, A.H. A Game Theoretic Optimization of RPL for Mobile Internet of Things Applications. IEEE Sens. J. 2018, 18, 2520–2530. [Google Scholar] [CrossRef]
- Gnawali, O.; Levis, P. The Minimum Rank with Hysteresis Objective Function. Internet Engineering Task Force (IETF) RFC: 6719. 2012. Available online: https://datatracker.ietf.org/doc/html/rfc6719 (accessed on 1 September 2021).
- Cobarzan, C.; Montavont, J.; Noel, T. Analysis and performance evaluation of RPL under mobility. In Proceedings of the 2014 IEEE Symposium on Computers and Communications (ISCC), Madeira, Portugal, 23–26 June 2014; pp. 1–6. [Google Scholar]
- Hong, K.; Choi, L. DAG-based multipath routing for mobile sensor networks. In Proceedings of the ICTC 2011, Seoul, Korea, 28–30 September 2011; pp. 261–266. [Google Scholar] [CrossRef]
- Sankar, S.; Srinivasan, P. Mobility and Energy Aware Routing Protocol for Healthcare IoT Application. Res. J. Pharm. Technol. 2018, 11, 3139. [Google Scholar] [CrossRef]
- Gaddour, O.; Koubäa, A.; Rangarajan, R.; Cheikhrouhou, O.; Tovar, E.; Abid, M. Co-RPL: RPL routing for mobile low power wireless sensor networks using corona mechanism. In Proceedings of the 9th IEEE International Symposium on Industrial Embedded Systems (SIES 2014), Pisa, Italy, 18–20 June 2014; pp. 200–209. [Google Scholar]
- El Korbi, I.; Brahim, M.B.; Adjih, C.; Saidane, L.A. Mobility enhanced RPL for wireless sensor networks. In Proceedings of the 2012 Third International Conference on the Network of the Future (NOF), Gammarth, Tunisie, 21–23 November 2012; pp. 1–8. [Google Scholar]
- Lee, K.C.; Sudhaakar, R.; Ning, J.; Dai, L.; Addepalli, S.; Vasseur, J.; Gerla, M. A Comprehensive Evaluation of RPL under Mobility. Int. J. Veh. Technol. 2012, 2012, 1–10. [Google Scholar] [CrossRef] [Green Version]
- Fotouhi, H.; Moreira, D.; Alves, M. mRPL: Boosting mobility in the Internet of Things. Ad Hoc Netw. 2015, 26, 17–35. [Google Scholar] [CrossRef]
- Pongle, P.; Chavan, G. A survey: Attacks on RPL and 6lowpan in IoT. In Proceedings of the 2015 International Conference on Pervasive Computing (ICPC), Pune, India, 8–10 January 2015; pp. 1–6. [Google Scholar]
- Kamble, A.; Malemath, V.S.; Patil, D. Security attacks and secure routing protocols in RPL-based internet of things: Survey. In Proceedings of the 2017 International Conference on Emerging Trends & Innovation in ICT (ICEI), Pune, India, 3–5 February 2017; pp. 33–39. [Google Scholar]
- Gaddour, O.; Koubâa, A. RPL in a nutshell: A survey. Comput. Netw. 2012, 56, 3163–3178. Available online: http://www.sciencedirect.com/science/article/pii/S1389128612002423 (accessed on 1 September 2021). [CrossRef]
- Zikria, Y.B.; Afzal, M.K.; Ishmanov, F.; Kim, S.W.; Yu, H. A survey on routing protocols supported by the Contiki Internet of things operating system. Futur. Gener. Comput. Syst. 2018, 82, 200–219. Available online: http://www.sciencedirect.com/science/article/pii/S0167739X17324299 (accessed on 1 September 2021). [CrossRef]
- Lamaazi, H.; Benamar, N.; Jara, A.J. RPL-based networks in static and mobile environment: A performance assessment analysis. J. King Saud Univ.—Comput. Inf. Sci. 2018, 30, 320–333. [Google Scholar] [CrossRef]
- Kharrufa, H.; Al-Kashoash, H.; Al-Nidawi, Y.; Mosquera, M.Q.; Kemp, A.H. Dynamic RPL for multi-hop routing in IoT applications. In Proceedings of the 2017 13th Annual Conference on Wireless On-Demand Network Systems and Services (WONS), Jackson Hole, WY, USA, 21–24 February 2017; pp. 100–103. [Google Scholar]
- Falk, J.; Kucherawy, M. Creation and Use of Email Feedback Reports: An Applicability Statement for the Abuse Reporting Format (ARF). RFC 6650. June 2012. Available online: https://datatracker.ietf.org/doc/html/rfc6650 (accessed on 1 September 2021).
- Barcelo, M.; Correa, A.; Vicario, J.L.; Morell, A.; Vilajosana, X. Addressing Mobility in RPL with Position Assisted Metrics. IEEE Sens. J. 2015, 16, 2151–2161. [Google Scholar] [CrossRef]
- Carels, D.; Derdaele, N.; de Poorter, E.; Vandenberghe, W.; Moerman, I.; Demeester, P. Support of multiple sinks via a virtual root for the RPL routing protocol. EURASIP J. Wirel. Commun. Netw. 2014, 2014, 91. [Google Scholar] [CrossRef]
- Khan, M.; Lodhi, M.; Rehman, A.; Khan, A.; Hussain, F. Sink-to-Sink Coordination Framework Using RPL: Routing Protocol for Low Power and Lossy Networks. J. Sens. 2016, 2016, 1–11. [Google Scholar] [CrossRef]
- Park, J.; Kim, K.-H.; Kim, K. An algorithm for timely transmission of solicitation messages in RPL for energy-efficient node mobility. Sensors 2017, 17, 899. [Google Scholar] [CrossRef] [Green Version]
- Ghaleb, B.; Al-Dubai, A.; Ekonomou, E. E-Trickle: Enhanced Trickle Algorithm for Low-Power and Lossy Networks. In Proceedings of the IEEE International Conference on Computer and Information Technology; Ubiquitous Computing and Communications; Dependable, Autonomic and Secure Computing; Pervasive Intelligence and Computing, Liverpool, UK,, 26–28 October 2015; pp. 1123–1129. [Google Scholar]
- Yassein, M.B.; Aljawarneh, S.; Masa’deh, E. A new elastic trickle timer algorithm for internet of things. J. Netw. Comput. Appl. 2017, 89, 38–47. [Google Scholar] [CrossRef]
- Sankar, S.; Srinivasan, P. Fuzzy Logic Based Energy Aware Routing Protocol for Internet of Things. Int. J. Intell. Syst. Appl. 2018, 10, 11–19. [Google Scholar] [CrossRef]
- Aljarrah, E. Deployment of multi-fuzzy model based routing in RPL to support efficient IoT. Int. J. Commun. Netw. Inf. Secur. 2017, 9, 457–465. [Google Scholar]
- Lorente, G.G.; Lemmens, B.; Carlier, M.; Braeken, A.; Steenhaut, K. BMRF: Bidirectional Multicast RPL Forwarding. Ad Hoc Netw. 2017, 54, 69–84. [Google Scholar] [CrossRef] [Green Version]
- Tang, W.; Ma, X.; Huang, J.; Wei, J. Toward Improved RPL: A Congestion Avoidance Multipath Routing Protocol with Time Factor for Wireless Sensor Networks. J. Sens. 2016, 2016, 8128651. [Google Scholar] [CrossRef] [Green Version]
- Ko, J.; Chang, M. MoMoRo: Providing Mobility Support for Low-Power Wireless Applications. IEEE Syst. J. 2014, 9, 585–594. [Google Scholar] [CrossRef]
- Sneha, K.; Prasad, B.G. An efficient hand-off optimization based RPL routing protocol for optimal route selection in mobility enabledllns. In Proceedings of the 2016 International Conference on Global Trends in Signal Processing, Information Computing and Communication (ICGTSPICC), Jalgaon, India, 22–24 December 2016; pp. 130–137. [Google Scholar]
- Bouaziz, M.; Rachedi, A.; Belghith, A.; Berbineau, M.; Al-Ahmadi, S. EMA-RPL: Energy and mobility aware routing for the Internet of Mobile Things. Future Gener. Comput. Syst. 2019, 97, 247–258. [Google Scholar] [CrossRef]
- Somaa, F.; el Korbi, I.; Saidane, L.A. Mobility support over RPL using sensor nodes speed classification. In Proceedings of the 2016 IEEE/ACS 13th International Conference of Computer Systems and Applications (AICCSA), Agadir, Morocco, 29 November–2 December 2016; pp. 1–6. [Google Scholar]
- Carels, D.; de Poorter, E.; Moerman, I.; Demeester, P. RPL Mobility Support for Point-to-Point Traffic Flows towards Mobile Nodes. Int. J. Distrib. Sens. Netw. 2015, 11, 470349. [Google Scholar] [CrossRef] [Green Version]
- Levis, P.; Tavakoli, A.; Dawson-Haggerty, S. Overview of Existing Routing Protocols for Low Power and Lossy Networks. Internet Engineering Task Force, Internet-Draft Draftietf-Roll-Protocols-Survey-07. 2009. Available online: https://datatracker.ietf.org/doc/html/draft-ietf-roll-protocols-survey (accessed on 1 September 2021).
- Misra, P.; Ahmed, N.; Ostry, D.; Jha, S. Characterization of Asymmetry in Low-Power Wireless Links: An Empirical Study; Springer: Berlin/Heidelberg, Germany, 2011; pp. 340–351. [Google Scholar]
- Dong, M.; Ota, K.; Yang, L.T.; Chang, S.; Zhu, H.; Zhou, Z. Mobile agent-based energy-aware and user-centric data collection in wireless sensor networks. Comput. Netw. 2014, 74, 58–70. [Google Scholar] [CrossRef]
- Safdar, V.; Bashir, F.; Hamid, Z.; Afzal, H.; Pyun, J.Y. A hybrid routing protocol for wireless sensor networks with mobile sinks. In Proceedings of the 7th IEEE International Symposium on Wireless and Pervasive Computing (ISWPC), Dalian, China, 3–4 July 2012; pp. 1–5. [Google Scholar]
- Tunca, C.; Isik, S.; Donmez, M.Y.; Ersoy, C. Distributed Mobile Sink Routing for Wireless Sensor Networks: A Survey. IEEE Commun. Surv. Tutor. 2012, 16, 877–897. [Google Scholar] [CrossRef]
- Gormus, S.; Tosato, F.; Fan, Z.; Bocus, Z.; Kulkarni, P. Opportunistic RPL for reliable AMI mesh networks. Wirel. Netw. 2014, 20, 2147–2164. [Google Scholar] [CrossRef]
- Dong, M.; Ota, K.; Liu, A.; Guo, M. Joint optimization of lifetime and transport delay under reliability constraint wireless sensor networks. IEEE Trans. Parallel Distrib. Syst. 2016, 27, 225–236. [Google Scholar] [CrossRef] [Green Version]
- Pavkovic, B.; Theoleyre, F.; Duda, A. IEEE 802.15. 4 and RPL crossoptimization for reliable opportunistic routing in wsn. In Proceedings of the ACM International Conference on Modeling, Analysis and Simulation ofWireless and Mobile Systems (MSWiM), Miami, FL, USA, 31 October–4 November 2011. [Google Scholar]
- Biswas, S.; Morris, R. Exor: Opportunistic multi-hop routing for wireless networks. ACM SIGCOMM Comput. Commun. Rev. 2005, 35, 133–144. [Google Scholar] [CrossRef]
- Chachulski, S.; Jennings, M.; Katti, S.; Katabi, D. Trading structure for randomness in wireless opportunistic routing. ACM SIGCOMM Comput. Commun. Rev. 2007, 37, 169–180. [Google Scholar] [CrossRef] [Green Version]
- Chen, Y.B.; Hou, K.M.; Chanet, J.P.; El Gholami, K. A RPL based Adaptive and Scalable Data-collection Protocol module for NS-3 simulation platform. In Proceedings of the NICST 2013 New Information Communication Science and Technology for Sustainable Development: France-China International Workshop, Clermont-Ferrand, France, 17 September 2013. [Google Scholar]
- Pfletschinger, S.; Navarro, M.; Ibars, C. Energy-efficient data collection in wsn with network coding. In Proceedings of the 2011 IEEE GLOBECOM Workshops (GC Wkshps), Houston, TX, USA, 5–9 December 2011; pp. 394–398. [Google Scholar]
- Razali, M.F.; Rusli, M.E.; Jamil, N.; Ismail, R.; Yussof, S. The authentication techniques for enhancing the RPL security mode: A survey. In Proceedings of the 6th International Conference on Computing &, Informatics, Kuala Lumpur, Malaysia, 25–27 April 2017; pp. 735–743. [Google Scholar]
- Airehrour, D.; Gutierrez, J.; Ray, S.K. Securing RPL routing protocol from blackhole attacks using a trust-based mechanism. In Proceedings of the 2016 26th International Telecommunication Networks and Applications Conference (ITNAC), Dunedin, New Zealand, 7–9 December 2016; pp. 7–9. [Google Scholar]
- Mardini, W.; Ebrahim, M.; Al-Rudaini, M. Comprehensive performance analysis of RPL objective functions in IoT networks. Int. J. Commun. Netw. Inf. Secur. 2017, 9, 323–332. [Google Scholar]
- Mayzaud, A.; Badonnel, R.; Chrisment, I. A taxonomy of attacks in RPL-based internet of thing. Int. J. Netw. Secur. 2016, 18, 459–473. [Google Scholar]
- Sharma, D.; Mishra, I.; Jain, S. A detailed classification of routing attacks against RPL in internet of things. Int. J. Adv. Res. Ideas Innov. Technol. 2017, 3, 692–703. [Google Scholar]
- Karthik, V.K.; Pushpalatha, M. Addressing attacks and security mechanism in the RPL based IoT. Int. J. Comput. Sci. Eng. Commination 2017, 5, 1715–1721. [Google Scholar]
- Staudemeyer, R.C.; Pöhls, H.C.; Wójcik, M. The Road to Privacy in IoT: Beyond Encryption and Signatures, Towards Unobservable Communication. In Proceedings of the IEEE 19th International Symposium on A World ofWireless, Mobile and Multimedia Networks (WoWMoM), Chania, Greece, 12–15 June 2018; pp. 14–20. [Google Scholar]

| Category | Working Principle | Issues Addressed | Advantages | Disadvantages |
|---|---|---|---|---|
| Co-RPL [43] | Reduces frequent node failures by improving localization of mobile nodes. | Issues with the Trickle timer. | Compared to basic RPL, Co-RPL has a lower loss rate of 20%, 50% less energy consumption, and 2.5 sec avg delay. | The effect of sink mobility on network performance is not discussed for Co-RPL. |
| Enhanced Trickle Algorithm [57] | Supports nodes mobility by dynamically adjusting DIS message broadcasts based on Doppler frequency. | Issues with the Trickle timer. | Helps in lowering DIS message count to 52.7%, packet loss rate of 0.3%, and energy consumption of 72.5 mJ. | Solutions to high PLR due to mobile nodes not matching time intervals for selecting parent nodes are not discussed. |
| ME-RPL [44] | Mobility information is added in the DIO message of mobile IoT to differentiate static and mobile nodes. | Lack of facility of identifying mobile nodes. | ME-RPL shows lower PLR and higher stable routes as compared to RPL. | No discussion provided for mobile nodes selected as Preferred Parent and its effect on network performance. |
| Elastic Trickle Timer Algorithm [59] | The `listen-only’ period is dynamically selected based on the number of neighboring nodes. | Issues with the Trickle timer. | 76% convergence time, power consumption of 1.5MJ is obtained with value of 20% and average PDR of 87%. | The effects of diverse and intervals over its performance evaluation have not been discussed. |
| Category | Working Principle | Issues Addressed | Advantages | Disadvantages |
|---|---|---|---|---|
| FLEA-RPL [60] | Applies fuzzy logic over metrics such as ETX and RER to select the best route for data transmission. | Delay caused by ETX probing. | Shows maximum delay of 2.9 s for 10 hops as compared to RPL, which has 3.8 s. | To perform efficient unicast routing, fuzzy logic is not suitable as it considers only a few metrics. |
| MI-FL [61] | Used for unicast transmission from a child node to root node in order to minimize delay and suppresses duplicate packets. | Delay caused by ETX probing. | It consumes 8% less power and provides a 90% packet delivery ratio with a packet loss rate of 4%. | Simulations are done just for the static nodes (mobility of nodes is not introduced). |
| CA-RPL [63] | Dynamically adjusts the path selection scheme and balances the network load. | Increase in hand-off delay. | Minimizes the average delay towards DAG root and the packet loss rate reduces to 25% as compared to RPL. | As the devices are battery-operated, network lifetime measurements are not evaluated. |
| Modified RPL [45] | Performs immediate ETX probing and avoids loops by introducing parent ID in the DIO messages. | Delay caused by ETX probing and loops in the network. | Shows a high PDR of 90%, high throughput of 19 kbps, and average delay of 1.3 ms. | It causes longer delays as compared to RPL, solutions to overcome these longer delays are not discussed. |
| Multiple Sinks [55] | Packets are delivered by the sensor node to the nearest sink reducing average hop count. | Increase in hand-off delay. | Less packet loss, reduced energy consumption, and increased packet reception ratio. | Simulations are done in a wired network, so it is difficult to examine how multiple sinks would work in a wireless network. |
| Category | Working Principle | Issues Addressed | Advantages | Disadvantages |
|---|---|---|---|---|
| ME-RPL [42] | Parent node from DODAG is selected when it is within the RSSI range. | Lack of identification of mobile nodes. | Improved PDR to 92% and energy consumption to 1.2 MJ/min. | Details over nodes variations to obtain the desired results are missing. |
| GTM-RPL [38] | Uses mobility and density metric parameters. | Lack of identification of mobile nodes. | GTM-RPL achieves better QoS compared to mRPL. | Only few protocol comparison is done. |
| MoMoRo [64] | Detects and notifies route disconnectivity for the reconstruction process. | Increase in hand-off delay. | PRR for downward traffic to and from mobile nodes by MoMoRo is 90%. | An adequate information on achieving low PRR is not discussed given. |
| Enhanced Hand-off Mechanism [65] | Average RSSI level of each neighboring node is used for selecting the best route. | Increase in hand-off delay, Loop in the network. | Achieves better performance when traffic burst interval is increased. | Solution to overhead by control messages during DODAG formation is not discussed. |
| mRPL [46] | Uses RSSI; neighboring nodes within the child set are ignored to avoid loops. | Increase in hand-off delay, Loop in the network. | 100% PDR is provided by mRPL because of the fast hand-off process. | Solution to the overhead caused due to high traffic is not discussed. |
| EMA-RPL [66] | RSSI of a mobile node is used for connectivity of a mobile node in a network. | Issue with the rank of detached mobile nodes. | EMA-RPL reduces signaling cost, energy, and handover delay compared to RPL. | None of the scenarios are discussed in which mobile node can be chosen as preferred parent. |
| DMR [41] | Uses rank information and LQI. | Loops in-network, issue with the rank of detached mobile nodes. | DMR reduces average per node energy consumption by 25%. | To reconstruct a DODAG using DMR broadcasts is not thoroughly discussed. |
| Category | Working Principle | Issues Addressed | Advantages | Disadvantages |
|---|---|---|---|---|
| KP-RPL [54] | Kalman filter takes into account the velocity estimates by enhancing mobile node position accuracies resulting in better routing decisions. | Lack of positioning information. | Robust to channel conditions, and reliable routing, which increases the network reliability by 25% as compared to KP-RPL without Kalman filtering. | Routing among the mobile nodes alone and how it will affect the positioning information is not discussed. |
| MP-RPL [67] | MP-RPL uses the SNSC model to detect node movements and constructs DODAG by selecting the least mobile nodes as Preferred Parents to ensure route stability. | Lack of positioning information. | This approach provides scalability as the gap between MP-RPL and RPL PDD remains unchanged even if the node number increases. | The effect of parameters such as energy consumption, throughput, and PDR are not discussed. |
| Category | Working Principle | Issues Addressed | Advantages | Disadvantages |
|---|---|---|---|---|
| SSCF [56] | Sink coordination is used to exchange network-defined parameters such as network size and sink mobility. | Lack of sink-to-sink coordination. | Achieved higher PDR of 22% and 26% in random and grid topologies. | Latency of RPL and SSCF is high. |
| Downward path construction mechanism [68] | The downward routes allow ancestors of old and new routes to send no-path DAO messages upon receiving updated DAO messages. | Issues with a rank of detached mobile nodes. | Improves PDR from 20–80%, and also reduces overall overhead without using location information. | Packet losses may occur if the mobile node is no longer reachable to the old parent; we note that the cancellation of the old route is still not done by the new DAO. |
| Categorized Solutions | Node | DIO Intervals | Simulation Parameters | |||||
|---|---|---|---|---|---|---|---|---|
| Categories | Proposal | Node Type | Nodes | Speed | Min Interval | Interval Doubling | Duration | Area |
| Trickle-Timer Based | Co-RPL [43] | Tmote sky | 10–100 | 1–3 m/s | X | X | 3600 s | X |
| Enhanced Trickle Algorithm [57] | X | 6–72 | 1.25–2.5 m/s | X | X | X | X | |
| Mobility Enhanced RPL [44] | X | 9 | X | X | X | X | X | |
| Elastic Trickle Timer [59] | X | 20–80 | X | X | X | 900 a | 1000 m2 | |
| ETX Based | FLEA-RPL [60] | Tmote sky | 100 | X | 12 s | 10 s | 48 h | 600 m2 |
| MI-FL [61] | X | 40 | X | X | X | 100 s | 500 m2 | |
| CA-RPL [63] | Tmote sky | 20 | 1–5 m/s | X | X | 360 s | 100 m2 | |
| Modified RPL [45] | Car | 10 | 25–65 mph | X | X | X | X | |
| Multiple Sinks [55] | Tmote sky | 30 | X | X | X | 3600 s | 20 m2 | |
| RSSI Based | ME-RPL [42] | CC2420 | 25 | 0–2 m/s | X | X | 24 h | 150 m2 |
| GTM-RPL [38] | Tmote sky | 12 | X | 8 | 6 | 3600 s | 1600 m2 | |
| MoMoRo [64] | Tmote sky | 30 | X | X | X | X | X | |
| Enhanced Hand-Off [65] | Tmote sky | X | X | X | X | X | X | |
| mRPL [46] | Tmote sky | X | 2 m/s | X | 0.256 s | X | X | |
| EMA-RPL [66] | X | X | 2 m/s | 180 ms | X | 900 s | X | |
| DMR [41] | X | 100 | 2–10 m/s | X | X | 200 s | 500 m2 | |
| Position Based | KP-RPL [54] | IRIS motes | 100 | 2 m/s | X | X | X | 150 m2 |
| MP-RPL [67] | Cooja Tmote | 50 | 1–10 m/s | X | X | 900 s | 600 m2 | |
| Miscellaneous | SSCF [56] | Sky mote | 2–8 | X | 4 s | 17.5 min | 600 s | X |
| Downward Path | Tmote sky | 37 | 5–20 km/h | X | X | 1800 s | 375 m2 | |
| Construction Mechanism [68] | ||||||||
| Categorized Solutions | Characteristics | System Parameters | ||||||
| Categories | Proposal | Power Comsumption | Packet Loss | PDR | Latency | Operating System | Tx | |
| Trickle-Timer Based | Co-RPL [43] | X | 20% | X | 2.5 s | Contiki | 50 m | |
| Enhanced Trickle Algorithm [57] | 7.10% | X | X | X | MATLAB | 20 m | ||
| Mobility Enhanced RPL [44] | X | 10% | X | X | Contiki | X | ||
| Elastic Trickle Timer [59] | 1.5 mJ | X | 87% | X | Cooja 2.7 | 30 m | ||
| ETX Based | FLEA-RPL [60] | X | 1–7% | X | X | Contiki 2.7 | X | |
| MI-FL [61] | 8% | 4% | 90% | X | Windows 7 | 200 m | ||
| CA-RPL [63] | X | 20% | X | 5 s | Contiki 2.6 | 40 m | ||
| Modified RPL [45] | X | X | 90% | 1.3 ms | Quainet 4.5 | 250 m | ||
| Multiple Sinks [55] | X | X | X | X | Office Testbed | 25 m | ||
| RSSI Based | ME-RPL [42] | 1.2 MJ | X | 92% | X | Contiki | 50 m | |
| GTM-RPL [38] | 55 mJ/pkt | X | 88% | 5 s | Contiki | 20 m | ||
| MoMoRo [64] | X | X | 84.65% | X | Indoor Testbed | X | ||
| Enhanced Hand-Off [65] | X | X | 85% | 60 ms | Instant Contiki 2.6 | X | ||
| mRPL [46] | X | X | 99.77% | 92.7 ms | Contiki 2.6 | 10 m | ||
| EMA-RPL [66] | 1 mW | X | 100% | 156.25 ms | Contiki IPv6 | 50 m | ||
| DMR [41] | X | X | 97% | X | NS 2.34 | X | ||
| Position Based | KP-RPL [54] | 0.056 W | X | 65% | X | MATLAB | X | |
| MP-RPL [67] | X | 28.7% | X | 750 ms | Contiki 2.6 | 50 m | ||
| SSCF [56] | 20% | X | X | 600 s | Contiki | X | ||
| Miscellaneous | Downward Path | X | X | 60–78% | 50–100 ms | Contiki 2.7 | 100 m | |
| Construction Mechanism [68] | ||||||||
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2021 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Shah, Z.; Levula, A.; Khurshid, K.; Ahmed, J.; Ullah, I.; Singh, S. Routing Protocols for Mobile Internet of Things (IoT): A Survey on Challenges and Solutions. Electronics 2021, 10, 2320. https://doi.org/10.3390/electronics10192320
Shah Z, Levula A, Khurshid K, Ahmed J, Ullah I, Singh S. Routing Protocols for Mobile Internet of Things (IoT): A Survey on Challenges and Solutions. Electronics. 2021; 10(19):2320. https://doi.org/10.3390/electronics10192320
Chicago/Turabian StyleShah, Zawar, Andrew Levula, Khawar Khurshid, Jawad Ahmed, Imdad Ullah, and Sushmita Singh. 2021. "Routing Protocols for Mobile Internet of Things (IoT): A Survey on Challenges and Solutions" Electronics 10, no. 19: 2320. https://doi.org/10.3390/electronics10192320
APA StyleShah, Z., Levula, A., Khurshid, K., Ahmed, J., Ullah, I., & Singh, S. (2021). Routing Protocols for Mobile Internet of Things (IoT): A Survey on Challenges and Solutions. Electronics, 10(19), 2320. https://doi.org/10.3390/electronics10192320







