The Adaptive Feedback Compensation Algorithm, as a category of block cipher, employs a 128-bit block processing mechanism. This cryptographic technique demonstrates superior dynamic equilibrium capabilities, effectively preserving original sequence integrity while optimizing 0/1 balance. The algorithm proves particularly suitable for implementation, testing, and application in random number products, fulfilling the compound requirements of modern cryptographic application scenarios.
The encryption process implements a two-phase dynamic control strategy: During the initialization phase, the system generates dynamic parameters through analysis of plaintext characteristics, which subsequently guide encryption path selection in real-time. In the core processing phase, a substitution layer comprising four S-boxes collaborates with a linear transformation layer based on 8/16-bit inversion operations to achieve data confusion. Through its operational logic and architectural design, AFCA enhances randomness while retaining critical features of the original sequence, thereby ensuring high integrity preservation during cryptographic transformation. This mechanism provides an encryption solution that balances randomness enhancement with data characteristic preservation for random number applications.
2.1. Key Parameters and Transformations
This section elaborates on the critical parameters and transformation operations within the Adaptive Feedback Compensation Algorithm, which constitute the core components of the algorithm. Specifically, it details: (1) the sequence representations of input plaintext and output ciphertext; (2) computational methods for adaptive parameters; (3) architecture of the nonlinear transformation τ with its S-box design; and (4) implementation mechanisms of linear transformation L. These parameters and transformations are engineered to dynamically adjust encryption strategies, ensuring effective enhancement of data balance while preserving partial features of raw data. The complete encryption workflow will be systematically explained in
Section 2.2, with all relevant nomenclature and definitions provided in
Table 1.
- 1.
Sequence Representation:
The input plaintext with a bit-length of 128 is represented as , where each . The output ciphertext with a bit-length of 128 is denoted as , where each . Here, are defined as 16-bit words. The adaptive parameters are utilized for frequency-adaptive compensation.
- 2.
Adaptive Parameters α and β:
Given an input
, the adaptive parameters
and
are computed as follows, where
sum(
A) denotes the sum of all bit elements in
A:
Example: For input = 0010 1110 0000 1101 and = DFEF, Equations (1)–(3) yield: = 1, = 1; = −6, = −4.
- 3.
Nonlinear Transformation τ:
The S-box functions as a nonlinear substitution table within cryptographic algorithms, mapping input data to output data to enhance randomness and resistance against attacks. It operates as a fixed 8-bit input to 8-bit output permutation. The nonlinear transformation τ is composed of four S-boxes. For different parameter values (
= ±1, ±2, ±3, ±4), the S-boxes adopt differentiated configurations to achieve dynamic nonlinear intensity regulation. Specific configuration data for these S-boxes are provided in
Appendix A Table A1,
Table A2,
Table A3 and
Table A4. For an input vector
, the output vector
is defined by Equation (4):
Example: When = ±2, for an input value 07, the S-box output is determined by indexing the 0th row and 7th column in the corresponding table, yielding Sbox (07) = F8.
- 4.
Linear Transformation L.
The linear transformation
L represents a 16-bit bitwise negation operation, while
l denotes an 8-bit bitwise negation operation. For an input
is defined by Equations (5) and (6):
Example: For the input 1011 1110 0000 1000, applying Equations (5) and (6) yields the negated output 0100 0001 1111 0111.
2.2. Encryption Process
The AFCA comprises up to 16 adaptive parameter operations, 8 decision operations, 8 nonlinear transformations τ, and 16 linear transformations L. Its encryption workflow achieves a balance between enhanced randomness and data integrity. The core logic can be summarized as a three-phase iterative process: Dynamic parameter computation, Encryption strategy selection, and Linear-nonlinear transformations.
- 1.
Dynamic Parameter Computation:
The algorithm first computes the adaptive parameters αi and βi based on the bitwise characteristics of the input plaintext group Xi, using Equations (1)–(3). The recursive calculation mechanism for βi propagates the statistical characteristics of the preceding group to subsequent groups, establishing a feedback compensation mechanism. The parameter αi is piecewise constrained according to the value range of βi, providing a quantitative basis for selecting subsequent encryption strategies.
- 2.
Encryption Strategy Selection:
Let the plaintext input be , and the ciphertext output be , where i = 0, 1, …, 7. Based on the value range of αi, the algorithm employs three distinct encryption strategies (Equations (7)–(9)):
Directly outputs the original group = . This strategy is applied when the input sequence already exhibits high randomness, avoiding redundant computations.
Strategy B (
):
Applies S-box substitution to the latter half-word to enhance local randomness via nonlinear transformation, while preserving the features of the former half-word.
Strategy C (
):
First performs a linear negation transformation on the former half-word, applies S-box substitution to the negated latter half-word, and finally executes a global negation. This strategy shares S-box tables with Strategy B through dual negation, optimizing storage requirements and computational efficiency.
- 3.
Linear and Nonlinear Transformations:
In Strategies B/C, the algorithm utilizes 4 S-boxes (
Table A1,
Table A2,
Table A3 and
Table A4) to achieve 8-bit nonlinear substitution. The S-box design employs a mapping mechanism to strengthen resistance against differential attacks. The linear transformation L implements negation solely via XOR operations, maximizing logical resource utilization.
To systematically describe the complete execution flow of the Adaptive Feedback Compensation Algorithm, Algorithm 1 outlines the iterative logic of dynamic parameter computation (
β and
α), strategy selection branches (Strategies A/B/C), and linear/nonlinear transformations. The workflow proceeds as follows:
| Algorithm 1: Adaptive Feedback Compensation Algorithm (AFCA)
|
| Input: 128-bit plaintext X = (X0, X1, …, X7), where Xi ∈ (Z216)8 |
| Output: 128-bit ciphertext Y = (Y0, Y1, …, Y7) |
| 1. Initialize β_prev = 0, α_prev = 0 |
| 2. Split X into eight 16-bit words: [X0, X1, …, X7] |
| 3. For i = 0 to 7 do: |
| a. Compute βi: |
| if i = 0: βi = 8 − bit_count (x0(i)) − bit_count (x1(i)) |
| else: βi = 8 − bit_count (x0(i)) − bit_count (x1(i)) + β_prev − α_prev |
| b. Compute αi: |
| αi is assigned a value based on which range βi falls into. |
| c. Select encryption strategy: |
| case αi: |
| 0 (Strategy A): |
| Yi = Xi |
| [1, 4] (Strategy B): |
| y0 = x0(i) |
| y1 = Sbox[αi](x1(i)) |
| Yi = (y0, y1) |
| [−4, −1] (Strategy C): |
| Flip the elements of x0(i). |
| y1 = Sbox[|αi|](temp_x1) |
| Yi = −(temp_x0, y1) |
| d. Update parameters: β_prev = βi, α_prev = αi |
| 4. Return Y = (Y0, Y1, …, Y7) |
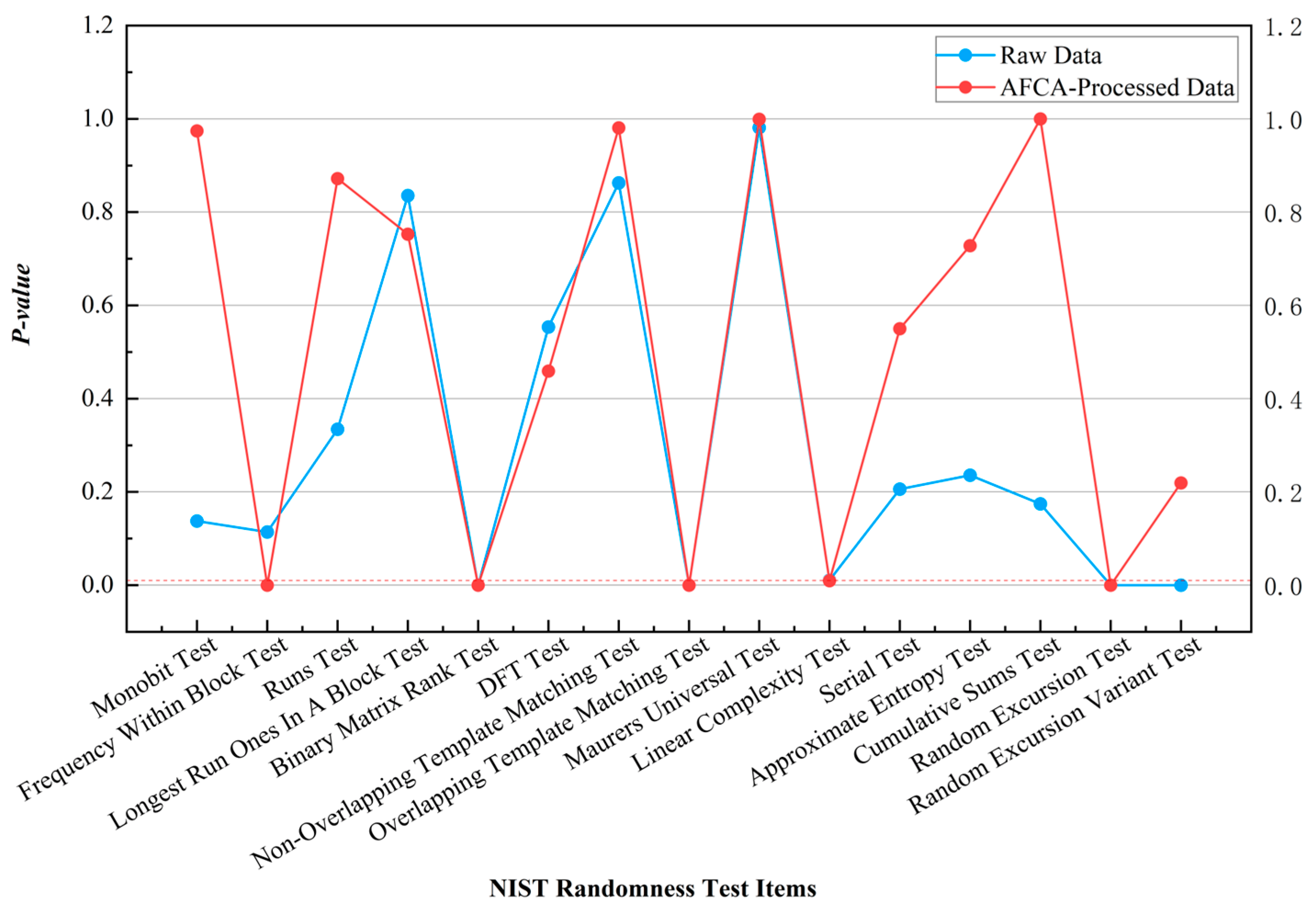
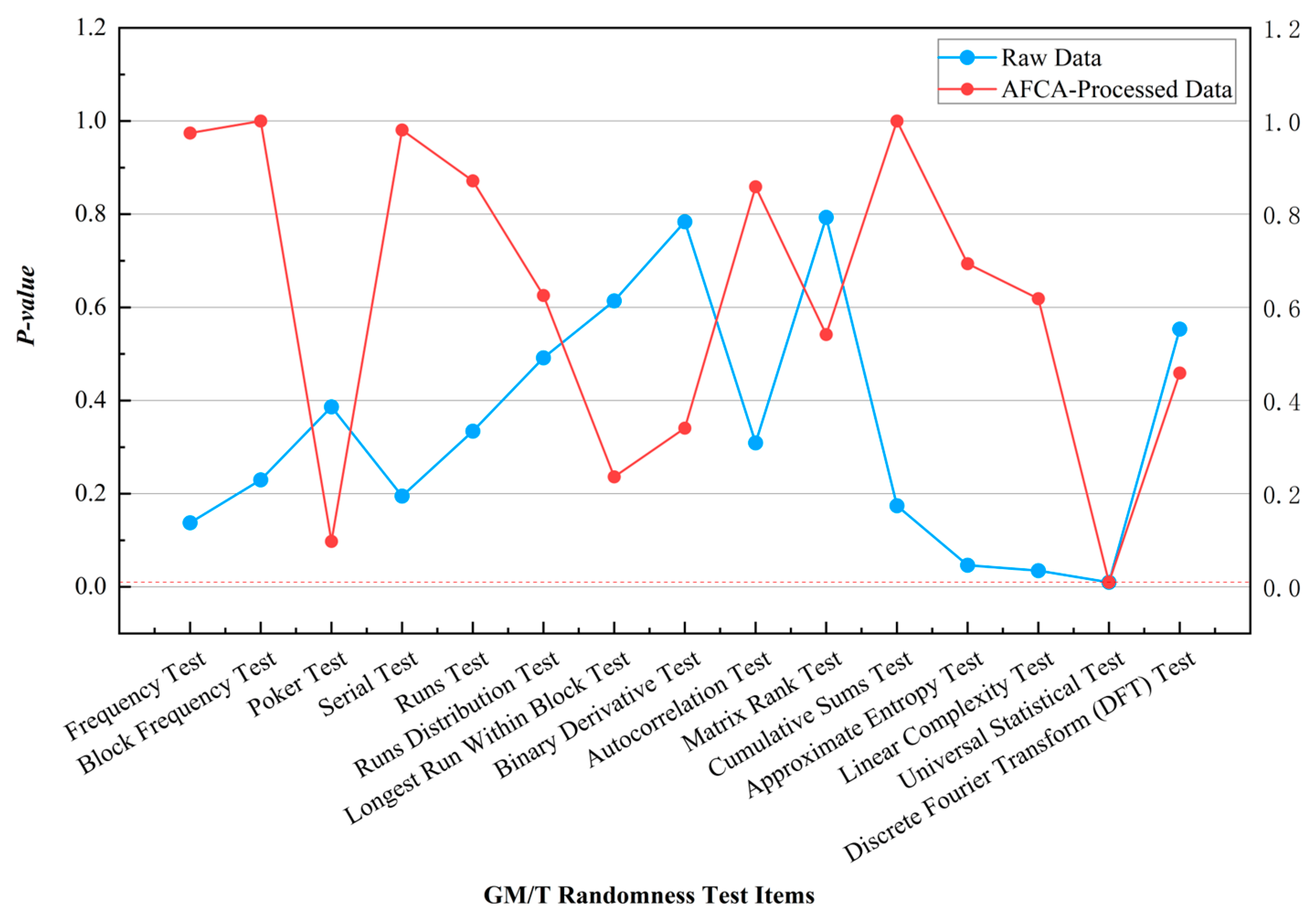
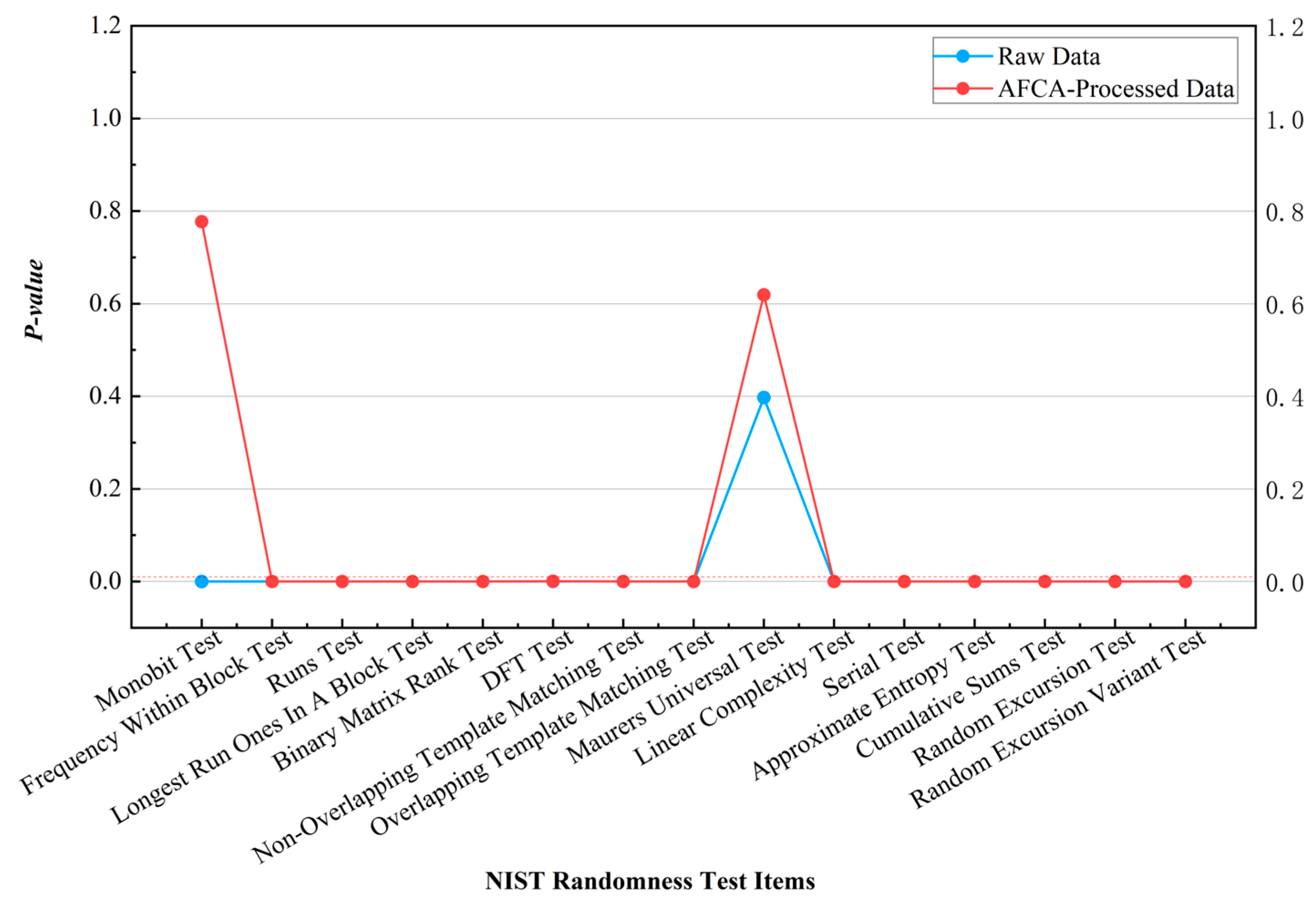
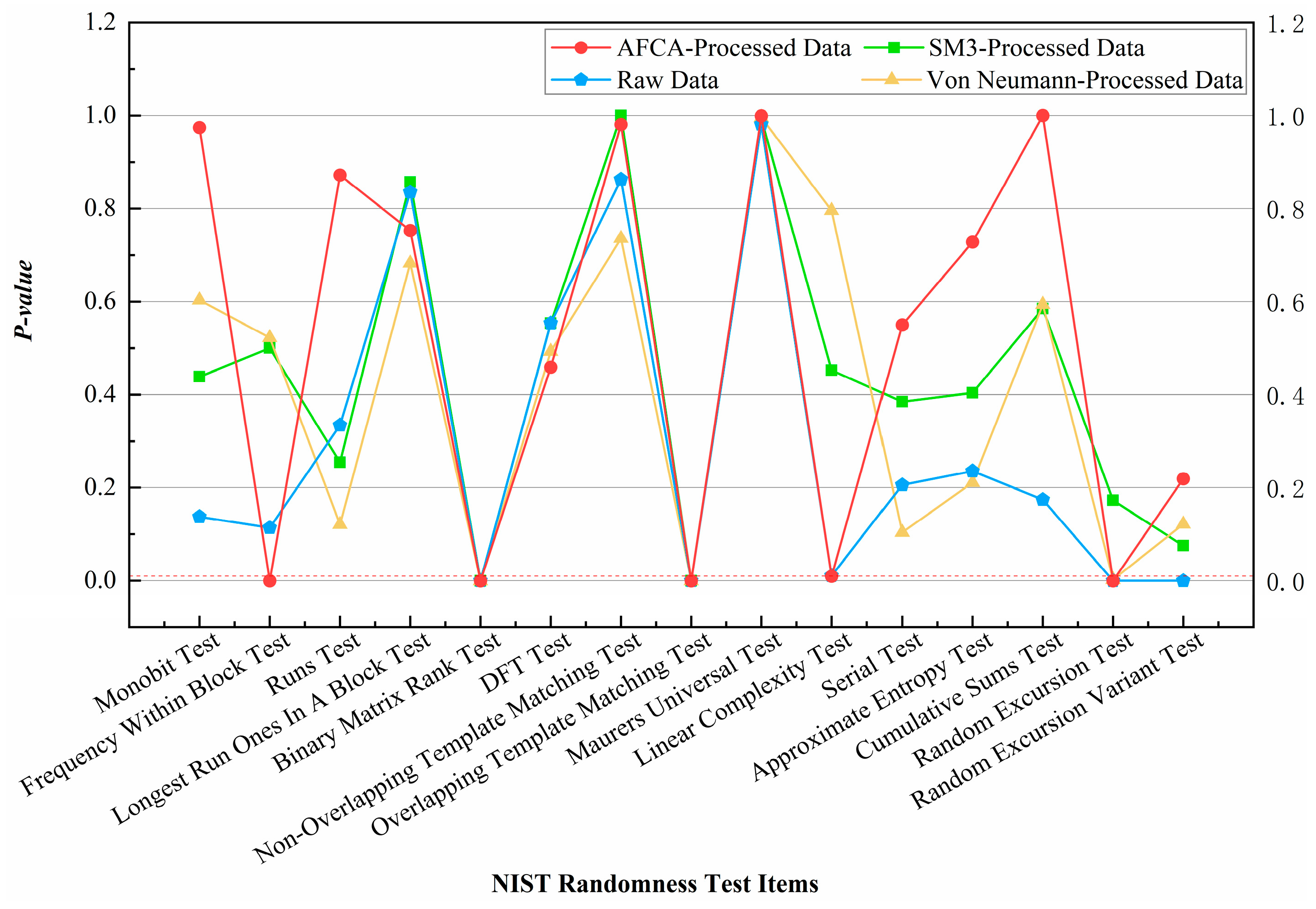
Appendix B validates the algorithm’s characteristics: it optimizes data balance and randomness across both simple and complex environments, preserves partial original data features, and demonstrates strong compatibility in joint encryption with other algorithms. The modular design of AFCA ensures compatibility with multi-stage cryptographic frameworks, which is essential for complex applications like multi-user MDI-QKD systems [
17], where both randomness quality and processing flexibility are critical. However, in specific scenarios (e.g., specialized environments or decryption-oriented applications), the algorithm’s improvement effects may fall below expectations.