Post-Quantum Secure Multi-Factor Authentication Protocol for Multi-Server Architecture
Abstract
1. Introduction
Our Contributions
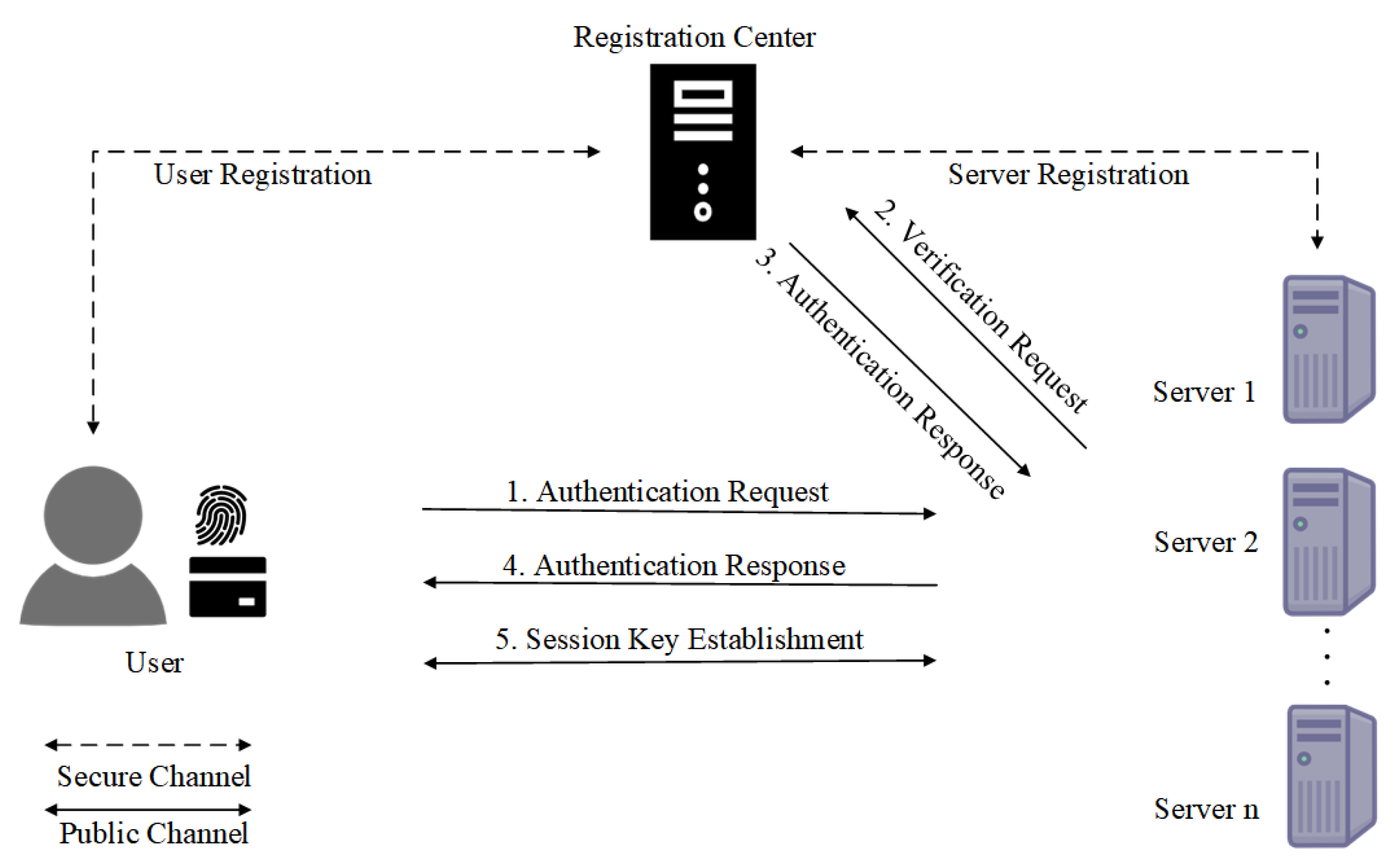
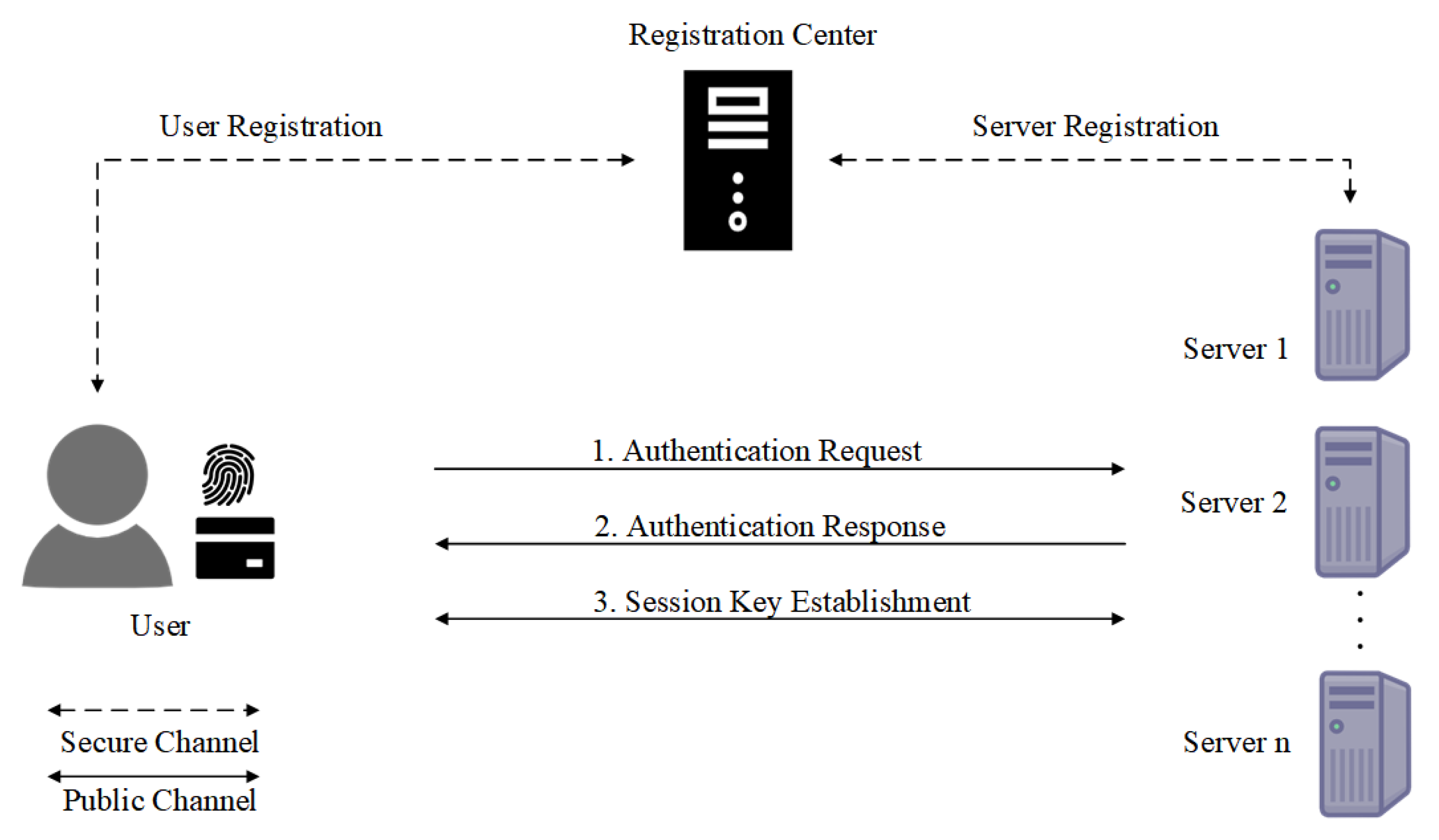
- In our protocol, both users and servers must initially register with the RC via a secure channel. After registration, any user can conduct mutual authentication with registered servers over an insecure channel, effectively negotiating a secure session key even when the RC is offline. Furthermore, our protocol supports users in updating their password and revoking their smart cards as needed.
- To achieve post-quantum security, our MFA protocol incorporates the post-quantum secure Kyber KEM and an information-theoretically secure fuzzy extractor as core components. The fuzzy extractor addresses minor variations in biometric inputs and prevents the storage of raw biometric data on the smart card, thereby reducing the risk of potential information leakage.
- We have proven the semantic security of our MFA protocol under the ROR (real or random) model. Furthermore, we conducted a comparative analysis with related protocols, demonstrating that our protocol achieves higher efficiency while maintaining reasonable communication overhead.
2. Related Work
3. Preliminaries
3.1. Notation
3.2. Module-LWE
3.3. Key Encapsulation Mechanism
- algorithm: upon input the security parameter , outputs a public key and a secret key .
- algorithm: inputs and outputs a ciphertext c and a key .
- algorithm: inputs and c and outputs either a key or a special symbol ⊥, indicating failure.
3.4. Metric Spaces and Min-Entropy
3.5. Fuzzy Extractor
- : on input of an element , it outputs a public helper string P and an extracted string .
- : on input of an element and the public helper string P, it outputs an extracted string R or ⊥.
- Correctness. If , then for all , we have .
- -Security. For any distribution W over such that , for any adversary , it follows thatwhere and .
3.6. Collision-Resistant Hash Function
3.7. Adversary Model
- is familiar with the protocol’s operation and public parameters. Any legitimate user can pretend to be , and vice versa.
- can eavesdrop, replay, modify, and forge messages communicated over the insecure public channel.
- can attempt offline password guessing attacks using information extracted from smart cards or other sources.
- cannot simultaneously compromise a legitimate user’s smart card, biometric and password. However, can compromise any two of three factors and attempt to guess the third factor.
- Through side-channel attacks, such as power analysis, can extract sensitive information stored on a smart card.
4. Proposed Protocol
4.1. Initializaiton Phase
- selects a hash function h: .
- selects the and algorithms for the fuzzy extractor.
- selects security parameters for the Kyber KEM.
- randomly generates a private key K, publishes , Kyber.Decaps, and securely stores K.
4.2. Registration Phase
4.2.1. Server Registration
- first assumes that k initial servers will complete their registration before any user’s registration, and additional servers will complete their registration thereafter. Then, selects unique for servers that may register in the future and computes .
- If a server intends to register, it first chooses its unique ID, denoted as . Then, the server invokes , stores securely, and sends along with to .
- Upon receiving the message from , will do the following:
- If no user has registered, will start to check the . If the has been occupied, will returns a rejection message. Otherwise, computes and publishes as the public information of server and securely stores . Finally, transmits to the server .
- If a user has completed their registration, the will disregard the received from the server. Instead, will use its pre-selected as the server’s ID, setting . Then publishes as the public information of server and securely stores . Finally, sends to server .
- After receiving from , server will use as its own ID and securely store for future authentication purposes.
4.2.2. User Registration
- User selects its own user ID and password . Then, inputs biometric data and invokes the generation algorithm . generates a random nonce a and computes and . Finally, sends to .
- When receives the registration request from the user, it first verifies whether the is unique. If the is already in use, returns a rejection message. Otherwise, stores in its database for future use. For , computes and and stores in a smart card . Finally, it securely delivers to the user.
- After receiving the smart card , user stores , and in the smart card . Ultimately, the smart card contains .
4.3. Login and Authentication Phase
4.3.1. User Login
- User inserts the smart card to a smart card scanner and inputs , and biometric data .
- invokes the algorithm to reproduce and computes , , . Then, verifies whether . If it is true, continues the process. Otherwise, it rejects the login request.
4.3.2. Mutual Authentication
- invokes and . Then, generates a time stamp and computes the following messages:then, it transmits to .
- Upon receiving message , the server first records the current timestamp and checks if . If it does not hold, ends the session. Otherwise, invokes . Then, uses the stored in the registration phase to computeIf holds, invokes the . Then, generates the time stamp and computesFinally, server transmits to user .
- Upon receiving message , generates the current time stamp and then checks if . If , computesIf holds, generates the time stamp , computes and transmits to server .
- Upon receiving the message , server records the current timestamp and checks if . If it does not hold, ends the session. Otherwise, computes . If , acknowledges the correctness of the session key. The session key is established between and for subsequent communication.
4.4. Update Phase
4.4.1. Password Update Phase
- User inserts the smart card to a smart card scanner and inputs , and biometric data .
- invokes the algorithm to reproduce and computes , and . Then, verifies whether . If it is true, continues the process. Otherwise, it rejects the login request.
- provides a new password .
- computesFor , computes
- updates information as .
4.4.2. Smart Card Revocation Phase
- User inserts the old smart card, selects new , , , inputs biometric data and computes . Then, computes , , and , and then transmits to along with a revocation request.
- verifies the legitimacy of by comparing with all the s stored in the database.
- replaces the old with the . Then, computes and for .
- For , stores all the in a smart card and delivers to the user through a secure channel.
- stores , and in .
4.5. Formal Security Analysis
4.5.1. ROR Model
- Participants: and represent the ath instance of user and the bth instance of server , respectively.
- Adversary: denotes a probabilistic polynomial time adversary.
- : This oracle outputs the protocol messages of an honest protocol execution between and . By querying this oracle, the adversary launches passive attacks.
- : This query simulates an active attack by the adversary , where can send message m to the instance or and receive the response message from or .
- : By querying this oracle, the adversary can obtain one or two types of ’s secret information.: compromises ’s and .: compromises all the information stored in ’s smart card.: compromises ’s .
- : If is established, the oracle returns if , and it returns a uniformly random key if , where c is uniformly chosen from .
- Random Oracle: We model the collision-resistant hash function as a random oracle, denoted by H, which is publicly available to all participants, including the adversary .
4.5.2. Security Proof
- : This game corresponds to the real attack. According to the definition of semantic security, we have
- : This game is identical to , except that the simulator modifies the simulation of the query by replacing the key and used in with random strings and of the same length. Recall that in our protocol, , where and . In this game, . Messages that can obtain from a query are , , . By the security of Kyber.KEM, with ciphertext , and public key , , the probability that can distinguish and from and is smaller than . Since can make at most queries, we have
- : In this game, the simulator will stop if a collision exists in hash queries or a collision exists in or . Based on the birthday paradox, the maximum probability of a collision in the output of a hash function is . The probability of finding a collision in or through Execute queries is at most . Thus, we have
- : In this game, the simulator will reject all the queries.
- Upon receiving the query , the simulator will check if . If , the simulator will reject the query; otherwise, the simulator will compute , , , , , and it will verify if . If , the simulator will reject the query.
- -
- Suppose that has already executed and before executing the query. In this case, obtains the smart card , password and user identity and does not know the biometric date . In order to pass the verification, needs to compute where . Note that as long as biometric data has enough entropy, is almost uniform. More precisely, for all adversary , the probability of to distinguish from a random string R is smaller than . As a result, the probability of guessing is smaller than .
- -
- Suppose that has already executed and before executing the query. In this case, obtains the biometric data , password and , but does not obtain the smart card . In order to pass the verification, needs to compute and , and then it computes and . Recall that and K is the secret key of . If can correctly guess the key of and simultaneously, can pass the verification. Since the key of is uniformly random, the probability of guessing the key of and simultaneously is less than .
- -
- Suppose that has already executed and before executing the query. In this case, obtains the smart card and the biometric data , but does not obtain the password and . With the smart card, only needs to compute to pass the verification. If can correctly guess the , would be able to pass the verification. Recall that , and , where a is a random nonce. Since a is random, is masked by a. As a result, cannot launch the offline user ID guessing attack. Therefore, can guess with probability .
- Upon receiving the , the simulator checks if . Then, the simulator computes , , , and verifies if . If wants to pass the verification, needs to compute . Since the adversary does not know the secret key and , it is hard for to compute and . As a result, can guess with a probability no larger than .
- Upon receiving , the simulator checks if . Then, the simulator computes and verifies if . Since does not know , it cannot decapsulate the ciphertext to obtain . As a result, can guess the with a probability no larger than .
4.6. Informal Security Analysis
- user anonymity: To preserve user anonymity, in the registration phase, the user computes masked identity , where is generated by . In the authentication phase, sends to the server ; the masked identity is involved in . Note that the message related to transmitted to the and server is the masked identity . This ensures that the actual user identity remains protected. More precisely, due to the security of fuzzy extractor, as long as the biometric data have enough entropy, is almost uniformly distributed. Given the security properties of the hash function, it is infeasible for the , server , or adversary to guess . This ensures user anonymity with respect to , server and adversary .
- user untraceability: The user untraceability ensures that it is difficult for an adversary to trace or link different sessions to the same user by eavesdropping. Recall that, in each session, the messages transmitted over the public channel are , and . Note that, in each session, user invokes and and sets and . As a result, each parameter is randomized. Similarly, every parameter in both and is randomized. Thus, the absence of transmission of static parameters ensures user untraceability.
- replay attack: In the authentication phase, the message sent by user involves a random key and a timestamp , and the message sent by the server involves a random key and a timestamp . The involvement of random keys and timestamps helps our protocol resist replay attacks, specifically if an attacker eavesdrops and performs a replay attack using . Upon receiving , will check whether both and are true. If not, it ends the session. By the security of the underlying hash function, random key and timestamp , the server will end the session with overwhelming probability. Similar analysis can be applied to .
- privileged insider attack: In our protocol, in the registration phase, user transmits and to the . Note that, is generated by and a is a random nonce. As long as the biometric data contain sufficient entropy, is uniformly random. Additionally, the hash function has the property of pre-image resistance. Therefore, it is hard for an insider to derive , even if the registration message is leaked.
- offline password guessing attack: Suppose that the adversary has obtained the information stored on the smart card and is attempting to guess the user’s password offline. Note that contains the information of . If an attacker attempts to guess from , it is required to guess , and a simultaneously. Recall that , , and a is a random nonce. The fuzzy extractor guarantees that as long as has enough entropy, is almost uniformly distributed even if is public. Due to the security of the hash function, is pseudorandom. a is pseudorandom-conditioned on . Therefore, the adversary cannot obtain from . Thereby, our protocol can resist offline password guessing attacks.
- stolen smart card attack: Suppose that the smart card is stolen by an adversary , who can extract all the information stored in the smart card. If wants to log in, needs to compute , where a is a random nonce. a is concealed by and . Recall that and . This means that if wants to compute , needs to guess , and simultaneously. Since has enough entropy, it is hard for to guess . As a result, it is difficult for to log in just with a smart card.
- user impersonation attack: A user impersonation attack refers to when an attacker pretends to be a legitimate user to illegally obtain information services from servers. Impersonating a legitimate user , the attacker must be able to forge a valid login request. In our protocol, this means that needs to successfully compute where .
- -
- Through eavesdropping, can easily obtain . In our protocol, is masked by . By the security of Kyber.KEM, is pseudorandom. As a result, cannot obtain from eavesdropping.
- -
- Assume that obtains the smart card and biometric data . Recall that , and , where a is a random nonce. Since a is random, is masked by a. As a result, cannot launch a user ID guessing attack. Therefore, cannot compute .
- -
- Assume that obtains the smart card and password and user identity . As long as biometric data have enough entropy, is almost uniform. As a result, cannot compute .
- -
- Assume that obtains the biometric data and password and . If wants to compute , needs to invoke to obtain . Since is stored in the smart card, cannot invoke . As a result, cannot compute .
- man-in-the-middle attack: The adversary pretends to be the server in a conversation with the user and also pretends to be the user in a conversation with the server.
- -
- Every legal server has its own . Without the , cannot compute and forge . Therefore, cannot make believe that is the specific legitimate server.
- -
- Every legal user has her/his own and . As long as the adversary does not obtain all three factors of the user who they want to impersonate, cannot compute . As a result, verification of the server would not be passed.
- backward and forward secrecy: In our protocol, even if a participant’s long-term secret is compromised, it remains difficult for an adversary to derive either previously generated or future possible keys. Note that in each session, the user will invoke and send to the server . The server will invoke . The session key is . Although are transmitted over the public channel, due to the the security of the Kyber KEM, it is hard for to obtain . The forward and backward secrecy of the protocol is ensured.
- key compromise impersonation attack: The multi-server architecture comprises multiple cloud servers and user entities. A key compromise impersonation attack occurs when an adversary obtains the long-term secrets of some participants and attempts to impersonate another user or server . Assuming that comprises a subset of users and a subset of servers , our protocol ensures that cannot impersonate any uncompromised user or server .
- -
- The adversary cannot impersonate any user . To impersonate a legitimate user , the adversary must forge a valid login request. In our protocol, this requires to successfully compute , where . Since does not comprise user , gains no information about . Given that has enough entropy, the security of fuzzy extractor ensures that is nearly uniformly distributed. As a result, cannot compute .
- -
- The adversary cannot impersonate any server . To impersonate a legitimate server , the adversary must compute the correct message to pass the verification, where , , and . To compute , the adversary needs to correctly decapsulate . Due to the security of the underlying Kyber.KEM, without the secret key , is pseudorandom. As a result, adversary cannot compute the correct message .
- RC root key exposure attack: In this attack, the RC’s root key K is leaked to the adversary .
- -
- The adversary cannot learn the identity of user . Recall that in the registration phase, the user selects an identity and a password and then imprints . The user then invokes , generates a random nonce a, and computes , and .Note that , where is generated by the fuzzy extractor and a is a random nonce in the computation of . As long as has enough entropy, the output is almost uniformly distributed due to the security of the fuzzy extractor. Consequently, the user’s identity remains concealed from the adversary.
- -
- The adversary cannot impersonate a legitimate server . Recall that in the registration phase, the server selects , computes and sends over a secure channel to the RC. Then, the RC computes , publishes , and stores . We can see that even if the root key K is exposed to , obtains no information about the secret key . Without , cannot impersonate a legitimate server .
5. Performance
6. Conclusions
Author Contributions
Funding
Data Availability Statement
Conflicts of Interest
References
- Lamport, L. Password authentication with insecure communication. Commun. ACM 1981, 24, 770–772. [Google Scholar] [CrossRef]
- Ali, R.; Pal, A.K.; Kumari, S.; Karuppiah, M.; Conti, M. A secure user authentication and key-agreement scheme using wireless sensor networks for agriculture monitoring. Future Gener. Comput. Syst. 2018, 84, 200–215. [Google Scholar] [CrossRef]
- Messerges, T.; Dabbish, E.; Sloan, R. Examining smart-card security under the threat of power analysis attacks. IEEE Trans. Comput. 2002, 51, 541–552. [Google Scholar] [CrossRef]
- Yoon, E.; Yoo, K. Robust biometrics-based multi-server authentication with key agreement scheme for smart cards on elliptic curve cryptosystem. J. Supercomput. 2013, 63, 235–255. [Google Scholar] [CrossRef]
- Khan, A.S.; Javed, Y.; Saqib, R.M.; Ahmad, Z.; Abdullah, J.; Zen, K.; Abbasi, I.A.; Khan, N.A. Lightweight Multifactor Authentication Scheme for NextGen Cellular Networks. IEEE Access 2022, 10, 31273–31288. [Google Scholar] [CrossRef]
- Tyagi, G.; Kumar, R. An Improved Multifactor User Authentication Scheme for Wireless Sensor Networks. Wirel. Pers. Commun. 2022, 123, 1311–1343. [Google Scholar] [CrossRef]
- Pradhan, M.; Mohanty, S. A Blockchain-Assisted Multifactor Authentication Protocol for Enhancing IoMT Security. IEEE Internet Things J. 2024, 11, 39323–39332. [Google Scholar] [CrossRef]
- Kumari, S.; Li, X.; Wu, F.; Das, A.K.; Choo, K.K.R.; Shen, J. Design of a provably secure biometrics-based multi-cloud-server authentication scheme. Future Gener. Comput. Syst. 2017, 68, 320–330. [Google Scholar] [CrossRef]
- Chuang, M.C.; Chen, M.C. An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Syst. Appl. 2014, 41, 1411–1418. [Google Scholar] [CrossRef]
- Kumari, A.; Jangirala, S.; Abbasi, M.Y.; Kumar, V.; Alam, M. ESEAP: ECC based secure and efficient mutual authentication protocol using smart card. J. Inf. Secur. Appl. 2020, 51, 102443. [Google Scholar] [CrossRef]
- Li, C.T.; Hwang, M.S. An efficient biometrics-based remote user authentication scheme using smart cards. J. Netw. Comput. Appl. 2010, 33, 1–5. [Google Scholar] [CrossRef]
- Arshad, H.; Nikooghadam Nikoughadam, M. Three-Factor Anonymous Authentication and Key Agreement Scheme for Telecare Medicine Information Systems. J. Med. Syst. 2014, 38, 136. [Google Scholar] [CrossRef] [PubMed]
- Shao, Z.; Li, Z.; Wu, P.; Chen, L.; Zhang, X. Multi-factor combination authentication using fuzzy graph domination model. J. Intell. Fuzzy Syst. 2019, 37, 4979–4985. [Google Scholar] [CrossRef]
- Iftikhar, J.; Hussain, S.; Mansoor, K.; Ali, Z.; Chaudhry, S.A. Symmetric-Key Multi-factor Biometric Authentication Scheme. In Proceedings of the 2019 2nd International Conference on Communication, Computing and Digital systems (C-CODE), Islamabad, Pakistan, 6–7 March 2019; pp. 288–292. [Google Scholar] [CrossRef]
- Feng, Q.; He, D.; Zeadally, S.; Wang, H. Anonymous biometrics-based authentication scheme with key distribution for mobile multi-server environment. Future Gener. Comput. Syst. 2018, 84, 239–251. [Google Scholar] [CrossRef]
- Barman, S.; Das, A.K.; Samanta, D.; Chattopadhyay, S.; Rodrigues, J.J.P.C.; Park, Y. Provably Secure Multi-Server Authentication Protocol Using Fuzzy Commitment. IEEE Access 2018, 6, 38578–38594. [Google Scholar] [CrossRef]
- Barman, S.; Shum, H.P.H.; Chattopadhyay, S.; Samanta, D. A Secure Authentication Protocol for Multi-Server-Based E-Healthcare Using a Fuzzy Commitment Scheme. IEEE Access 2019, 7, 12557–12574. [Google Scholar] [CrossRef]
- Ali, Z.; Hussain, S.; Rehman, R.H.U.; Munshi, A.; Liaqat, M.; Kumar, N.; Chaudhry, S.A. ITSSAKA-MS: An Improved Three-Factor Symmetric-Key Based Secure AKA Scheme for Multi-Server Environments. IEEE Access 2020, 8, 107993–108003. [Google Scholar] [CrossRef]
- Mishra, D.; Das, A.K.; Mukhopadhyay, S. A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Syst. Appl. 2014, 41, 8129–8143. [Google Scholar] [CrossRef]
- Chaturvedi, A.; Das, A.K.; Mishra, D.; Mukhopadhyay, S. Design of a secure smart card-based multi-server authentication scheme. J. Inf. Secur. Appl. 2016, 30, 64–80. [Google Scholar] [CrossRef]
- Luo, H.; Wang, F.; Xu, G.; Meng, W. Provably Secure ECC-Based Three-Factor Authentication Scheme for Mobile Cloud Computing with Offline Registration Centre. Wirel. Commun. Mob. Comput. 2021, 2021, 8848032. [Google Scholar] [CrossRef]
- Shukla, S.; Patel, S.J. A design of provably secure multi-factor ECC-based authentication protocol in multi-server cloud architecture. Clust. Comput. 2023, 27, 1559–1580. [Google Scholar] [CrossRef]
- Ajtai, M.; Dwork, C. A public-key cryptosystem with worst-case/average-case equivalence. In Proceedings of the Twenty-Ninth Annual ACM Symposium on Theory of Computing, STOC ’97, El Paso, TX, USA, 4–6 May 1997; pp. 284–293. [Google Scholar] [CrossRef]
- Applebaum, B.; Cash, D.; Peikert, C.; Sahai, A. Fast Cryptographic Primitives and Circular-Secure Encryption Based on Hard Learning Problems. In Proceedings of the Advances in Cryptology-CRYPTO 2009: 29th Annual International Cryptology Conference, Santa Barbara, CA, USA, 16–20 August 2009; Halevi, S., Ed.; Springer: Berlin/Heidelberg, Germany, 2009; pp. 595–618. [Google Scholar]
- Lyubashevsky, V.; Peikert, C.; Regev, O. On Ideal Lattices and Learning with Errors over Rings. In Proceedings of the Advances in Cryptology–EUROCRYPT 2010: 29th Annual International Conference on the Theory and Applications of Cryptographic Techniques, French Riviera, France, 30 May–3 June 2010; Gilbert, H., Ed.; Springer: Berlin/Heidelberg, Germany, 2010; pp. 1–23. [Google Scholar]
- Bos, J.; Ducas, L.; Kiltz, E.; Lepoint, T.; Lyubashevsky, V.; Schanck, J.M.; Schwabe, P.; Seiler, G.; Stehle, D. CRYSTALS-Kyber: A CCA-Secure Module-Lattice-Based KEM. In Proceedings of the 2018 IEEE European Symposium on Security and Privacy (EuroS P), London, UK, 24–26 April 2018; pp. 353–367. [Google Scholar] [CrossRef]
- Bahache, A.N.; Chikouche, N.; Akleylek, S. Securing Cloud-based Healthcare Applications with a Quantum-resistant Authentication and Key Agreement Framework. Internet Things 2024, 26, 101200. [Google Scholar] [CrossRef]
- Ahmad, A.; Jagatheswari, S. Quantum Safe Multi-Factor User Authentication Protocol for Cloud-Assisted Medical IoT. IEEE Access 2025, 13, 3532–3545. [Google Scholar] [CrossRef]
- Palaniswamy, B.; Karati, A. QPTA: Quantum-Safe Privacy-Preserving Multi-Factor Authentication Scheme for Lightweight Devices. In Proceedings of the 21st International Conference on Security and Cryptography—SECRYPT, Dijon, France, 8–10 July 2024; pp. 804–811. [Google Scholar] [CrossRef]
- Dodis, Y.; Ostrovsky, R.; Reyzin, L.; Smith, A. Fuzzy Extractors: How to Generate Strong Keys from Biometrics and Other Noisy Data. SIAM J. Comput. 2008, 38, 97–139. [Google Scholar] [CrossRef]
- Dolev, D.; Yao, A.C. On the Security of Public Key Protocols (Extended Abstract). In Proceedings of the 22nd Annual Symposium on Foundations of Computer Science (sfcs 1981), Nashville, TN, USA, 28–30 October 1981; pp. 350–357. [Google Scholar] [CrossRef]
- Amin, R.; Biswas, G.P. A Novel User Authentication and Key Agreement Protocol for Accessing Multi-Medical Server Usable in TMIS. J. Med. Syst. 2015, 39, 1–17. [Google Scholar] [CrossRef]
- Ryu, J.; Oh, J.; Kwon, D.; Son, S.; Lee, J.; Park, Y.; Park, Y. Secure ECC-Based Three-Factor Mutual Authentication Protocol for Telecare Medical Information System. IEEE Access 2022, 10, 11511–11526. [Google Scholar] [CrossRef]
- Rehman, H.U.; Ghani, A.; Chaudhry, S.A.; Alsharif, M.H.; Nabipour, N. A secure and improved multi server authentication protocol using fuzzy commitment. Multimed. Tools Appl. 2021, 80, 16907–16931. [Google Scholar] [CrossRef]
- Ali, R.; Pal, A.K. Three-Factor-Based Confidentiality-Preserving Remote User Authentication Scheme in Multi-server Environment. Arab. J. Sci. Eng. 2017, 42, 3655–3672. [Google Scholar] [CrossRef]
| Notation | Description |
|---|---|
| Registration Center | |
| ith user | |
| , , | Identity, password, and biometric of |
| jth server | |
| Identity of | |
| K | Private key of |
| , | Private key, public key of the Kyber KEM for |
| , | Private key, public key of the Kyber KEM for |
| Session key between and | |
| , , | Current time stamps |
| Hash function | |
| ⊕, ‖ | Bitwise XOR, concatenation |
| Acceptable transmission delay threshold | |
| Smart card of | |
| Adversary |
| Server | ||
|---|---|---|
| Select unique | ||
| Select | ||
| Compute | ||
| Store | ||
| Check | ||
| Compute | ||
| Publish | ||
| Store | ||
| Compare | ||
| Store |
| User | RC | |
|---|---|---|
| Select , | ||
| Imprint | ||
| Generate a random nonce a | ||
| Check whether the is unique | ||
| if unique, store in the database | ||
| for , compute | ||
| store | ||
| in a smart card | ||
| Store , , in |
| User | Server | |
|---|---|---|
| inserts | ||
| inputs , , | ||
| Compute | ||
| If | ||
| ends the session | ||
| Else continue | ||
| Compute | ||
| If , continue | ||
| Compute | ||
| If , continue | ||
| Compute | ||
| If , continue | ||
| Compute | ||
| If , continue | ||
| Compute | ||
| If , continue. | ||
| Compute | ||
| If , | ||
| the session key is established. |
| [9] | [28] | [32] | [20] | [8] | [15] | [16] | [17] | [18] | [21] | [33] | [22] | [29] | Our | |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| User anonymity | ✔ | ✗ | ✔ | ✗ | ✗ | ✔ | ✗ | ✗ | ✔ | ✔ | ✔ | ✔ | ✗ | ✔ |
| User untraceability | ✔ | ✔ | ✔ | ✗ | ✗ | ✔ | ✗ | ✗ | ✗ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Mutual authentication | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✗ | ✔ | ✔ | ✔ | ✔ | ✔ |
| security | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✗ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Secure smart card revocation | ✔ | ✗ | ✗ | ✗ | ✗ | ✗ | ✔ | ✔ | ✔ | ✔ | ✗ | ✔ | ✗ | ✔ |
| Resist replay attack | ✔ | ✔ | ✔ | ✔ | ✗ | ✗ | ✔ | ✔ | ✔ | ✗ | ✔ | ✔ | ✔ | ✔ |
| Resist privileged insider | ✔ | ✔ | ✔ | ✔ | ✗ | ✔ | ✔ | ✔ | ✔ | ✔ | ✗ | ✔ | ✗ | ✔ |
| Resists offline password guessing attack | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Resist smart card stolen | ✗ | ✔ | ✔ | ✔ | ✔ | ✔ | ✗ | ✔ | ✔ | ✔ | ✗ | ✔ | ✔ | ✔ |
| Resists user impersonation | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✗ | ✗ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Resists DoS | ✔ | ✗ | ✔ | ✔ | ✗ | ✗ | ✔ | ✔ | ✔ | ✗ | ✔ | ✔ | ✔ | ✔ |
| Forward secrecy | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ | ✔ |
| Post-quantum security | ✔ | ✔ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✗ | ✔ | ✔ |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wen, Y.; Su, Y.; Li, W. Post-Quantum Secure Multi-Factor Authentication Protocol for Multi-Server Architecture. Entropy 2025, 27, 765. https://doi.org/10.3390/e27070765
Wen Y, Su Y, Li W. Post-Quantum Secure Multi-Factor Authentication Protocol for Multi-Server Architecture. Entropy. 2025; 27(7):765. https://doi.org/10.3390/e27070765
Chicago/Turabian StyleWen, Yunhua, Yandong Su, and Wei Li. 2025. "Post-Quantum Secure Multi-Factor Authentication Protocol for Multi-Server Architecture" Entropy 27, no. 7: 765. https://doi.org/10.3390/e27070765
APA StyleWen, Y., Su, Y., & Li, W. (2025). Post-Quantum Secure Multi-Factor Authentication Protocol for Multi-Server Architecture. Entropy, 27(7), 765. https://doi.org/10.3390/e27070765






