Applicability and Design Considerations of Chaotic and Quantum Entropy Sources for Random Number Generation in IoT Devices
Abstract
1. Introduction
1.1. General Consideration
1.2. Motivation
- Miniaturization and integration with the hardware layer of IoT devices. This criterion reflects the importance of seamless hardware-level incorporation of the entropy source in the resource-constrained embedded systems.
- Level and performance of randomness source in IoT environments. The rigorous evaluation of a randomness level and performance in IoT environment is absolutely critical because of the principles (foundation) of the cryptographic security. Without consistently maintaining strong entropy, IoT devices become highly susceptible to sophisticated attacks, leading potentially to data breaches, unauthorized access, and compromised system integrity. Therefore, assessing both the statistical randomness level and the rate at which these random numbers are created is essential to ensure the long-term resilience and trustworthiness of IoT deployments.
- Feasibility of implementing a reseeding mechanism (access to diverse seed values). This aspect addresses the practical and architectural constraints associated with ensuring sufficient (high quality) entropy inputs during device operation. In particular, the article discusses the challenges posed by limited or intermittent access to high quality entropy sources, which can significantly impact the reliability and unpredictability of pseudorandom generators in real-world IoT deployments.
2. Chaotic Logistic Map as a Source of Randomness for IoT
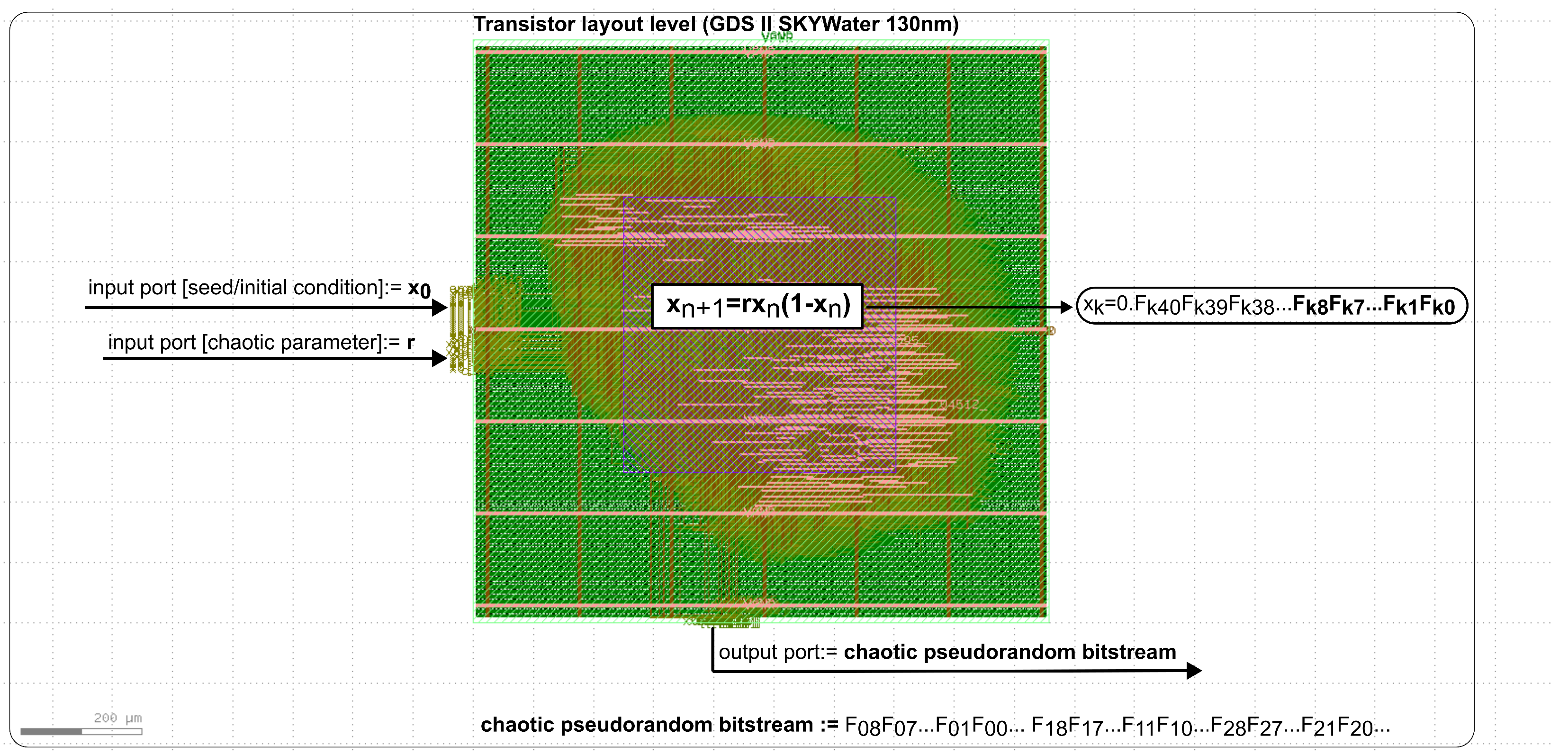
2.1. Integration of Chaotic Source
- Hardware Description in HDL—This step involves expressing the logistic equation using the HDL hardware description language. The HDL code defines the architecture of the digital system, including its input and output ports, registers storing the current state of the generator, and computational units performing calculations based on the mathematical formula.
- HDL Synthesis—After creating the pseudorandom generator description in HDL, the next step is to synthesize it using the OpenLane tool. The synthesis process transforms the logical design description into a transistor-level schematic suitable for fabrication.
- Circuit Optimization—The optimization phase aims to improve the system’s performance, including reducing the power consumption, shortening the computation time, and minimizing the chip area.
- Layout Generation—Following optimization, OpenLane generates the ASIC layout, which is the physical representation of the logical design. For a pseudorandom generator based on the logistic equation, the layout includes the careful placement of logic components. It also adheres to technological constraints defined in the SkyWater PDK, which specify the design rules for element placement and routing in the fabrication process.
- Preparation for Fabrication—At this stage, OpenLane performs additional verification steps such as Design Rule Check (DRC), Layout Versus Schematic (LVS), and Parasitic Extraction (PEX) to ensure that the layout complies with the technological requirements and is ready for manufacturing.
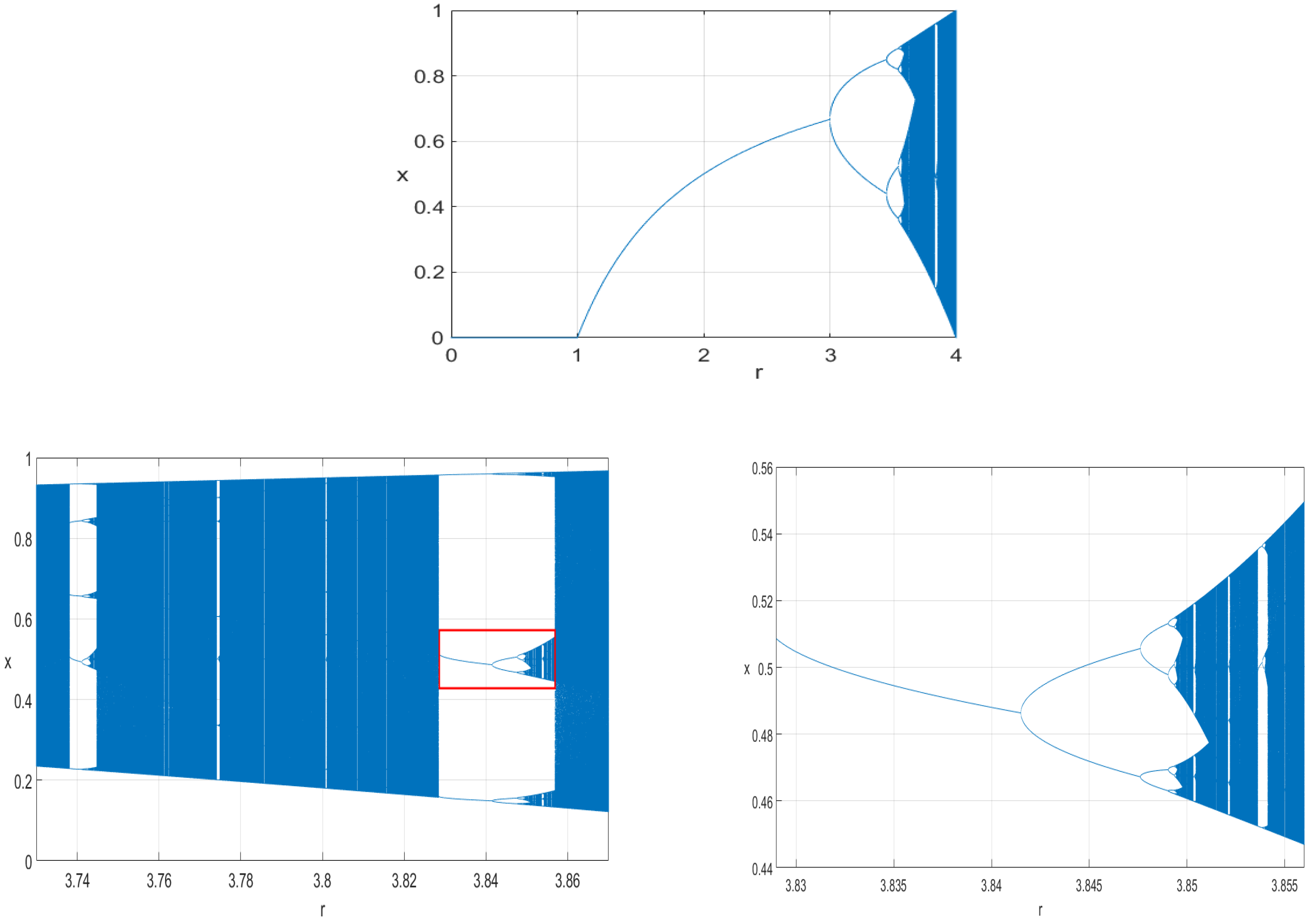
2.2. Randomness Quality and Performance of Chaotic Source
2.3. Access to Diverse Seed Values
3. Quantum Phenomena as Sources of Randomness for IoT
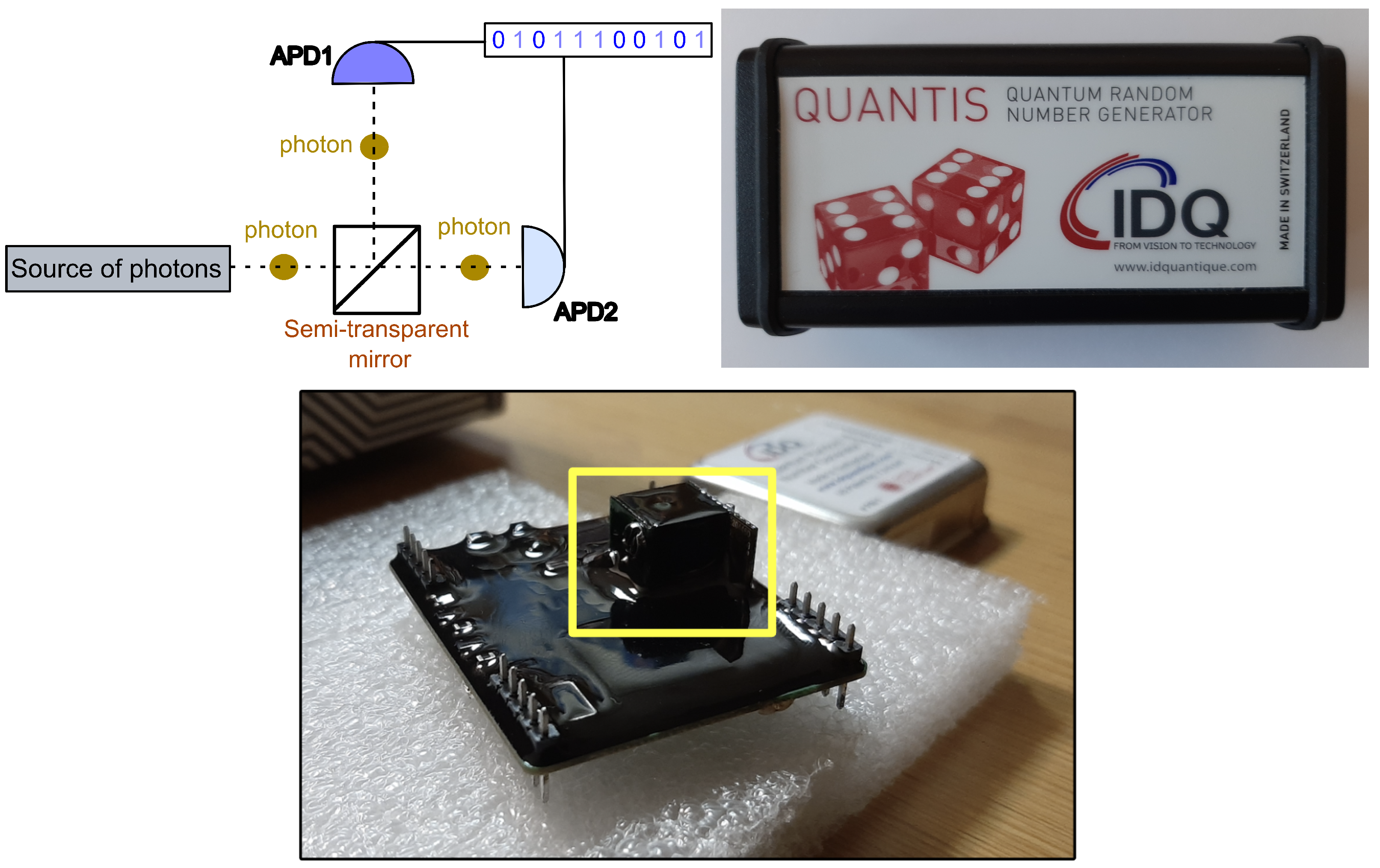
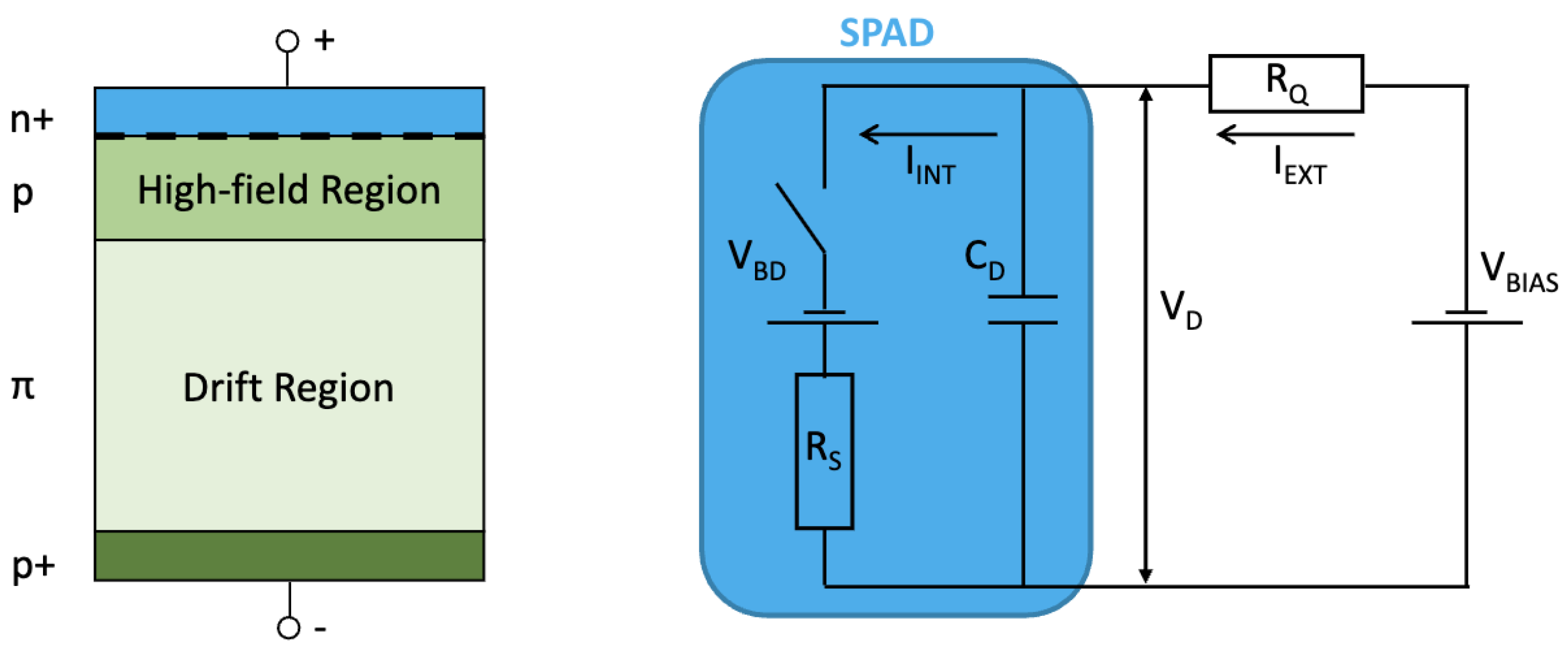
3.1. Single-Photon Avalanche Diodes (SPADs)
- A high-electric field region in the p-n junction (obtained by the application of a high reverse bias voltage, exceeding the so-called breakdown voltage ), where the creation of an electron–hole pair by a single photon incident on the photosensitive device area can trigger an avalanche of secondary carriers (through impact ionization, i.e., collision of the primary carriers with the lattice atoms); this results in a divergent (avalanche) multiplication.
- An external circuit, which quenches the discharge, i.e., stops the avalanche current.
- Breakdown voltageAs already indicated, this parameter denotes the lower limit of the bias voltage, exceeding which brings the diode to operate in Geiger’s mode. The factors important in the applications include the value and temperature dependence, as well as uniformity for the sets of individual devices.
- Photodetection efficiency (PDE)This is the ratio of the number of photons detected and the total number of the photons incident on the device. In order to facilitate our analysis of the impact of various parameters, the PDE can be factorized as follows:The indicated parameters depend on the wavelength and the bias voltage V. The denotes the quantum efficiency (the probability of the creation of an electron–hole pair by the absorption of an incident photon), is the SiPM cell fill factor, i.e., the ratio of the active area to the total area of the cell, and is the avalanche breakdown triggering probability (also referred to as the Geiger discharge probability).
- Primary and correlated noiseThere are two main relevant categories of noise: primary noise (not related to photon absorption, but to accidental carrier creation by, e.g., thermal excitation, which is followed by an avalanche event), and correlated noise (an avalanche event generated as a consequence of a preceding avalanche event, regardless of its origin. The most important parameters include the following:
- Primary Dark Count Rate (DCR [counts per second, cps]).
- Primary Dark Count Rate dependence on temperature.
- Optical cross-talk (emission of the so-called “cross-talk” photons by the hot carriers passing through the high-field zone).
- Afterpulsing (second avalanches triggered occasionally by carriers captured by trapping centers in the high-field zone and then re-emitted).
- Optically induced afterpulsing (afterpulsing caused by cross-talking photons).
- Timing propertiesA relevant measure of the timing performance is the Single-Photon Time Resolution (SPTR). This parameter denotes the precision of the estimate of the time of arrival for a photon in the visible spectral region, incident on the detector surface at a random position. This timing parameter is obviously dependent on the characteristics of the detector itself, but also on the read-out.
3.2. Photon Statistics
- The intrinsic photon statistics of the light beam.
- The statistical nature of the photodetection process.
- For ideal quantum efficiency , we have , which represents a strict correlation between the fluctuations of photocounts and incident photons.
- For Poissonian statistics of the incident light beam, the following relation holds, independent of : ; . This means that the photocount statistics are also Poissonian.
- For the limiting case of a very low quantum efficiency , the photocount variance , i.e., the photocount statistics are Poissonian, irrespective of the underlying photon statistics.
3.3. Integration of Quantum Source
3.4. Randomness Quality and Performance of Quantum Source
4. Entropy Source Selection for IoT Devices
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ASIC | Application Specific Integrated Circuit |
| PDK | Process Design Kit |
| FPGA | Field Programmable Gate Array |
| NIST | National Institute of Standards and Technology |
| QRNG | Quantum Random Number Generator |
| AES | Advanced Encryption Standard |
| PMT | Photomultiplier Tube |
| HDL | Hardware Description Language |
| PCB | Printed Circuit Board |
| IP Core | Intellectual Property Core |
| EDA | Electronic Design Automation |
| CMOS | Complementary Metal Oxide Semiconductor |
| APD | Avalanche Photo Diode |
| LED | Light-Emitting Diode |
| SBC | Single Board Computer |
| CHSH | Clauser–Horne–Shimony–Holt |
| SiPM | Silicon Photomultiplier |
References
- Paar, C.; Pelzl, J. Understanding Cryptography: A Textbook for Students and Practitioners; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2009. [Google Scholar]
- Fischer, V.; Drutarovskỳ, M. True random number generator embedded in reconfigurable hardware. In Proceedings of the International Workshop on Cryptographic Hardware and Embedded Systems, Redwood Shores, CA, USA, 13–15 August 2002; Springer: Berlin/Heidelberg, Germany, 2002; pp. 415–430. [Google Scholar]
- Thabit, F.; Can, O.; Aljahdali, A.O.; Al-Gaphari, G.H.; Alkhzaimi, H.A. Cryptography algorithms for enhancing IoT security. Internet Things 2023, 22, 100759. [Google Scholar] [CrossRef]
- Rana, M.; Mamun, Q.; Islam, R. Lightweight cryptography in IoT networks: A survey. Future Gener. Comput. Syst. 2022, 129, 77–89. [Google Scholar] [CrossRef]
- Bikos, A.; Nastou, P.E.; Petroudis, G.; Stamatiou, Y.C. Random number generators: Principles and applications. Cryptography 2023, 7, 54. [Google Scholar] [CrossRef]
- Bordel, B.; Orúe, A.B.; Alcarria, R.; Sánchez-De-Rivera, D. An intra-slice security solution for emerging 5G networks based on pseudo-random number generators. IEEE Access 2018, 6, 16149–16164. [Google Scholar] [CrossRef]
- Hughes, J.P.; Diffie, W. The Challenges of IoT, TLS, and Random Number Generators in the Real World: Bad random numbers are still with us and are proliferating in modern systems. Queue 2022, 20, 18–40. [Google Scholar] [CrossRef]
- Manucom, E.M.M.; Gerardo, B.D.; Medina, R.P. Analysis of key randomness in improved one-time pad cryptography. In Proceedings of the 2019 IEEE 13th International Conference on Anti-Counterfeiting, Security, and Identification (ASID), Xiamen, China, 25–27 October 2019; pp. 11–16. [Google Scholar]
- Boakye-Boateng, K.; Kuada, E.; Antwi-Boasiako, E.; Djaba, E. Encryption protocol for resource-constrained devices in fog-based IoT using one-time pads. IEEE Internet Things J. 2019, 6, 3925–3933. [Google Scholar] [CrossRef]
- Yalçin, M.E.; Suykens, J.A.; Vandewalle, J. True random bit generation from a double-scroll attractor. IEEE Trans. Circuits Syst. I Regul. Pap. 2004, 51, 1395–1404. [Google Scholar] [CrossRef]
- De Micco, L.; Antonelli, M.; Rosso, O.A. From continuous-time chaotic systems to pseudo random number generators: Analysis and generalized methodology. Entropy 2021, 23, 671. [Google Scholar] [CrossRef]
- Yu, F.; Li, L.; Tang, Q.; Cai, S.; Song, Y.; Xu, Q. A survey on true random number generators based on chaos. Discret. Dyn. Nat. Soc. 2019, 2019, 2545123. [Google Scholar] [CrossRef]
- Moqadasi, H.; Ghaznavi-Ghoushchi, M. A new Chua’s circuit with monolithic Chua’s diode and its use for efficient true random number generation in CMOS 180 nm. Analog. Integr. Circuits Signal Process. 2015, 82, 719–731. [Google Scholar] [CrossRef]
- Li, P.; Li, Q.; Tang, W.; Wang, W.; Zhang, W.; Little, B.E.; Chu, S.T.; Shore, K.A.; Qin, Y.; Wang, Y. Scalable parallel ultrafast optical random bit generation based on a single chaotic microcomb. Light. Sci. Appl. 2024, 13, 66. [Google Scholar] [CrossRef]
- Gao, H.; Zhang, Y.; Liang, S.; Li, D. A new chaotic algorithm for image encryption. Chaos Soliton. Fract. 2006, 29, 393–399. [Google Scholar] [CrossRef]
- Li, C.; Luo, G.; Qin, K.; Li, C. An image encryption scheme based on chaotic tent map. Nonlinear Dyn. 2017, 87, 127–133. [Google Scholar] [CrossRef]
- Garcia-Bosque, M.; Pérez-Resa, A.; Sánchez-Azqueta, C.; Aldea, C.; Celma, S. Chaos-based bitwise dynamical pseudorandom number generator on FPGA. IEEE Trans. Instrum. Meas. 2018, 68, 291–293. [Google Scholar] [CrossRef]
- Chen, S.; Yu, S.; Lü, J.; Chen, G.; He, J. Design and FPGA-based realization of a chaotic secure video communication system. IEEE Trans. Circuits Syst. Video Technol. 2017, 28, 2359–2371. [Google Scholar] [CrossRef]
- Elmanfaloty, R.A.; Abou-Bakr, E. Random property enhancement of a 1D chaotic PRNG with finite precision implementation. Chaos Solitons Fractals 2019, 118, 134–144. [Google Scholar] [CrossRef]
- Melosik, M.; Marszalek, W. Strengthening quality of chaotic bit sequences. Electronics 2022, 11, 272. [Google Scholar] [CrossRef]
- Melosik, M.; Marszalek, W. A hybrid chaos-based pseudo-random bit generator in VHDL-AMS. In Proceedings of the 2014 IEEE 57th International Midwest Symposium on Circuits and Systems (MWSCAS), College Station, TX, USA, 3–8 August 2014; pp. 435–438. [Google Scholar]
- Ausloos, M. The Logistic Map and the Route to Chaos: From the Beginnings to Modern Applications; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2006. [Google Scholar]
- Oravec, J.; Ovsenik, L.; Papaj, J. An image encryption algorithm using logistic map with plaintext-related parameter values. Entropy 2021, 23, 1373. [Google Scholar] [CrossRef]
- Available online: https://geoffboeing.com/2015/03/chaos-theory-logistic-map/ (accessed on 24 May 2025).
- Available online: https://en.wikipedia.org/wiki/Logistic_map (accessed on 24 May 2025).
- Sayed, W.S.; Radwan, A.G.; Rezk, A.A.; Fahmy, H.A. Finite precision logistic map between computational efficiency and accuracy with encryption applications. Complexity 2017, 2017, 8692046. [Google Scholar] [CrossRef]
- Antonelli, M.; De Micco, L.; Larrondo, H.; Rosso, O.A. Complexity of simple, switched and skipped chaotic maps in finite precision. Entropy 2018, 20, 135. [Google Scholar] [CrossRef]
- de la Fraga, L.G.; Torres-Pérez, E.; Tlelo-Cuautle, E.; Mancillas-López, C. Hardware implementation of pseudo-random number generators based on chaotic maps. Nonlinear Dyn. 2017, 90, 1661–1670. [Google Scholar] [CrossRef]
- Tolba, M.F.; Sayed, W.S.; Radwan, A.G.; Abd-El-Hafiz, S.K. FPGA realization of speech encryption based on modified chaotic logistic map. In Proceedings of the 2018 IEEE International Conference on Industrial Technology (ICIT), Lyon, France, 20–22 February 2018; pp. 1412–1417. [Google Scholar]
- Hasan, F.S.; Saffo, M.A. FPGA hardware co-simulation of image encryption using stream cipher based on chaotic maps. Sens. Imaging 2020, 21, 35. [Google Scholar] [CrossRef]
- Available online: https://www.mathworks.com/products/simulink.html (accessed on 24 May 2025).
- Fournaris, A.P.; Alexakos, C.; Anagnostopoulos, C.; Koulamas, C.; Kalogeras, A. Introducing hardware-based intelligence and reconfigurability on industrial IoT edge nodes. IEEE Des. Test 2019, 36, 15–23. [Google Scholar] [CrossRef]
- Caraveo-Cacep, M.A.; Vázquez-Medina, R.; Zavala, A.H. A survey on low-cost development boards for applying cryptography in IoT systems. Internet Things 2023, 22, 100743. [Google Scholar] [CrossRef]
- Soto-Cruz, J.; Ruiz-Ibarra, E.; Vázquez-Castillo, J.; Espinoza-Ruiz, A.; Castillo-Atoche, A.; Mass-Sanchez, J. A Survey of Efficient Lightweight Cryptography for Power-Constrained Microcontrollers. Technologies 2024, 13, 3. [Google Scholar] [CrossRef]
- Nguyen, K.D.; Dang, T.K.; Kieu-Do-Nguyen, B.; Le, D.H.; Pham, C.K.; Hoang, T.T. ASIC Implementation of ASCON Lightweight Cryptography for IoT Applications. IEEE Trans. Circuits Syst. II Express Briefs 2025, 72, 278–282. [Google Scholar] [CrossRef]
- Konstantopoulou, E.; Athanasiou, G.; Sklavos, N. Review and Analysis of FPGA and ASIC Implementations of NIST Lightweight Cryptography Finalists. ACM Comput. Surv. 2025, 52, 1–35. [Google Scholar] [CrossRef]
- Chinnery, D.; Keutzer, K.W. Closing the Gap Between ASIC & Custom: Tools and Techniques for High-Performance ASIC Design; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2002. [Google Scholar]
- Handkiewicz, A.; Szcze, S.; Naumowicz, M.; Katarzyński, P.; Melosik, M.; Śniatała, P.; Kropidłowski, M. SI-Studio, a layout generator of current mode circuits. Expert Syst. Appl. 2015, 42, 3205–3218. [Google Scholar] [CrossRef]
- Hesham, S.; Shalan, M.; El-Kharashi, M.W.; Dessouky, M. Digital asic implementation of risc-v: Openlane and commercial approaches in comparison. In Proceedings of the 2021 IEEE International Midwest Symposium on Circuits and Systems (MWSCAS), Springfield, MA, USA, 11–14 August 2021; pp. 498–502. [Google Scholar]
- Edwards, R.T.; Shalan, M.; Kassem, M. Real silicon using open-source EDA. IEEE Des. Test 2021, 38, 38–44. [Google Scholar] [CrossRef]
- Fauzan, M.; Yanuarsyah, R.F.; Hibatullah, M.H.; Arisaputra, R.; Syafalni, I.; Sutisna, N.; Adiono, T.; Ikeda, M. Physical Design of RISC-V based System-on-Chip using OpenLane. In Proceedings of the 2024 IEEE Asia Pacific Conference on Circuits and Systems (APCCAS), Taipei, Taiwan, 7–9 November 2024; pp. 529–533. [Google Scholar]
- Naumowicz, M.; Melosik, M.; Katarzynski, P.; Handkiewicz, A. Automation of CMOS technology migration illustrated by RGB to YCrCb analogue converter. Opto-Electron. Rev. 2013, 21, 326–331. [Google Scholar] [CrossRef]
- Baungarten-Leon, E.I.; Ortega-Cisneros, S.; Pinedo-Diaz, G.; Rivera-Acosta, M.; Rodriguez-Navarrete, F.J.; Jaramillo-Toral, U.; Torres, C.; Lopez, J.C.G. Macro memory cell generator for sky130 pdk. IEEE Access 2024, 12, 59688–59701. [Google Scholar] [CrossRef]
- Available online: https://github.com/mnaumowicz/entropy (accessed on 24 May 2025).
- Bassham, L.; Rukhin, A.; Soto, J.; Nechvatal, J.; Smid, M.; Leigh, S.; Levenson, M.; Vangel, M.; Heckert, N.; Banks, D. A Statistical Test Suite for Random and Pseudorandom Number Generators for Cryptographic Applications; Special Publication (NIST SP)’ National Institute of Standards and Technology: Gaithersburg, MD, USA, 2010. [Google Scholar]
- Persohn, K.; Povinelli, R.J. Analyzing logistic map pseudorandom number generators for periodicity induced by finite precision floating-point representation. Chaos Soliton. Fract. 2012, 45, 238–245. [Google Scholar] [CrossRef]
- Fan, C.; Ding, Q.; Tse, C.K. Counteracting the dynamical degradation of digital chaos by applying stochastic jump of chaotic orbits. Int. J. Bifurc. Chaos 2019, 29, 1930023. [Google Scholar] [CrossRef]
- Liu, L.; Miao, S. A universal method for improving the dynamical degradation of a digital chaotic system. Phys. Scr. 2015, 90, 085205. [Google Scholar] [CrossRef]
- Walker, J. ENT: A Pseudorandom Number Sequence Test Program—Fourmilab. 2008. Available online: http://www.fourmilab.ch/random/ (accessed on 24 May 2025).
- Yu, W.K.; Li, S.; Yao, X.R.; Liu, X.F.; Wu, L.A.; Zhai, G.J. Protocol based on compressed sensing for high-speed authentication and cryptographic key distribution over a multiparty optical network. Appl. Opt. 2013, 52, 7882–7888. [Google Scholar] [CrossRef]
- Melosik, M.; Marszalek, W. Trojan attack on the initialization of pseudo-random bit generators using synchronization of chaotic input sources. IEEE Access 2021, 9, 161846–161853. [Google Scholar] [CrossRef]
- Melosik, M.; Galan, M.; Naumowicz, M.; Tylczyński, P.; Koziol, S. Cryptographically Secure PseudoRandom Bit Generator for Wearable Technology. Entropy 2023, 25, 976. [Google Scholar] [CrossRef]
- Barker, E.B.; Kelsey, J.M. Recommendation for Random Number Generation Using Deterministic Random Bit Generators (Revised); US Department of Commerce, Technology Administration, National Institute of Standars and Technology: Gaithersburg, MD, USA, 2007. [Google Scholar]
- Available online: https://www.idquantique.com (accessed on 24 May 2025).
- Herrero-Collantes, M.; Garcia-Escartin, J.C. Quantum random number generators. Rev. Mod. Phys. 2017, 89, 015004. [Google Scholar] [CrossRef]
- Mannalatha, V.; Mishra, S.; Pathak, A. A comprehensive review of quantum random number generators: Concepts, classification and the origin of randomness. Quantum Inf. Process. 2023, 22, 439. [Google Scholar] [CrossRef]
- Webb, P.P.; McIntyre, R.J. Single photon detection with avalanche photodiodes; Bulletin of the American Physical Society: Woodbury, NY, USA, 1970; Volume 15, p. 813. [Google Scholar]
- Piemonte, C.; Gola, A. Overview on the main parameters and technology of modern Silicon Photomultipliers. Nucl. Instruments Methods Phys. Res. Sect. A Accel. Spectrometers Detect. Assoc. Equip. 2019, 926, 2–15. [Google Scholar] [CrossRef]
- Fox, A.M. Quantum Optics: An Introduction; Oxford University Press: Oxford, UK, 2006; Volume 15. [Google Scholar]
- Haroche, S.; Raimond, J.M. Exploring the Quantum: Atoms, Cavities, and Photons; Oxford University Press: Oxford, UK, 2006. [Google Scholar]
- Aharonovich, I.; Castelletto, S.; Simpson, D.A.; Su, C.H.; Greentree, A.D.; Prawer, S. Diamond-based single-photon emitters. Rep. Prog. Phys. 2011, 74, 076501. [Google Scholar] [CrossRef]
- Aharonovich, I.; Englund, D.; Toth, M. Solid-state single-photon emitters. Nat. Photon. 2016, 10, 631–641. [Google Scholar] [CrossRef]
- Toyli, D.M.; Christle, D.J.; Alkauskas, A.; Buckley, B.B.; Van De Walle, C.G.; Awschalom, D.D. Measurement and Control of Single Nitrogen-Vacancy Center Spins above 600 K. Phys. Rev. X 2012, 2, 31001. [Google Scholar] [CrossRef]
- Ernst, S.; Scheidegger, P.J.; Diesch, S.; Lorenzelli, L.; Degen, C.L. Temperature Dependence of Photoluminescence Intensity and Spin Contrast in Nitrogen-Vacancy Centers. Phys. Rev. Lett. 2023, 131, 086903. [Google Scholar] [CrossRef]
- Szawioła, G.; Mieloch, S.; Stefańska, D.; Głowacki, P.; Frajtak, A.; Michalczyk, J.; Murawski, K.; Pruchlat, A.; Raczyński, J.; Schmidt, M.; et al. Thermal effects in optically detected magnetic resonance of nitrogen vacancies in diamond: A quantum thermometer for a graduate teaching lab. J. Chem. Educ. 2025, 102, 1949–1959. [Google Scholar] [CrossRef]
- Szymaniec, K.; Lea, S.N.; Gibble, K.; Park, S.E.; Liu, K.; Głowacki, P. NPL Cs fountain frequency standards and the quest for the ultimate accuracy. J. Phys. Conf. Ser. 2016, 723, 012003. [Google Scholar] [CrossRef]
- Morzyński, P.; Bober, M.; Bartoszek-Bober, D.; Nawrocki, J.; Krehlik, P.; Śliwczyński, L.; Lipiński, M.; Masłowski, P.; Cygan, A.; Dunst, P.; et al. Absolute measurement of the 1S0 − 3P0 clock transition in neutral 88Sr over the 330 km-long stabilized fibre optic link. Sci. Rep. 2015, 5, 17495. [Google Scholar] [CrossRef]
- Thielking, J.; Okhapkin, M.V.; Głowacki, P.; Meier, D.M.; von der Wense, L.; Seiferle, B.; Düllmann, C.E.; Thirolf, P.G.; Peik, E. Laser spectroscopic characterization of the nuclear-clock isomer 229mTh. Nature 2018, 556, 321–325. [Google Scholar] [CrossRef]
- Zhang, C.; Ooi, T.; Higgins, J.S.; Doyle, J.F.; von der Wense, L.; Beeks, K.; Leitner, A.; Kazakov, G.A.; Li, P.; Thirolf, P.G.; et al. Frequency ratio of the 229mTh nuclear isomeric transition and the 87Sr atomic clock. Nature 2024, 633, 63–70. [Google Scholar] [CrossRef]
- Bhunia, S.; Tehranipoor, M. The Hardware Trojan War; Springer: Cham, Switzerland, 2018. [Google Scholar]
- Jin, Y.; Kupp, N.; Makris, Y. Experiences in hardware Trojan design and implementation. In Proceedings of the 2009 IEEE International Workshop on Hardware-Oriented Security and Trust, San Francisco, CA, USA, 27 July 2009; pp. 50–57. [Google Scholar]
- Yaacoub, J.P.A.; Noura, H.N.; Salman, O.; Chehab, A. Ethical hacking for IoT: Security issues, challenges, solutions and recommendations. Internet Things Cyber-Phys. Syst. 2023, 3, 280–308. [Google Scholar] [CrossRef]
- Piliposyan, G.; Khursheed, S.; Rossi, D. Hardware trojan detection on a PCB through differential power monitoring. IEEE Trans. Emerg. Top. Comput. 2020, 10, 740–751. [Google Scholar] [CrossRef]
- Ghosh, S.; Basak, A.; Bhunia, S. How secure are printed circuit boards against trojan attacks? IEEE Des. Test 2014, 32, 7–16. [Google Scholar] [CrossRef]
- Troyer, M.; Renner, R. A Randomness Extractor for the Quantis Device. ID Quantique Technical Paper on Randomness Extractor. 2012. Available online: https://www.scribd.com/document/704258573/troyer-id-quantique-2012-A-randomness-extractor-for-the-Quantis-device (accessed on 24 May 2025).
- Khrennikov, A.Y. Probability and Randomness: Quantum Versus Classical; World Scientific: Singapore, 2016. [Google Scholar]
- Clauser, J.F.; Horne, M.A.; Shimony, A.; Holt, R.A. Proposed experiment to test local hidden-variable theories. Phys. Rev. Lett. 1969, 23, 880. [Google Scholar] [CrossRef]
- Liu, Y.; Zhao, Q.; Li, M.H.; Guan, J.Y.; Zhang, Y.; Bai, B.; Zhang, W.; Liu, W.Z.; Wu, C.; Yuan, X.; et al. Device-independent quantum random-number generation. Nature 2018, 562, 548–551. [Google Scholar] [CrossRef]
- Li, Y.; Fei, Y.; Wang, W.; Meng, X.; Wang, H.; Duan, Q.; Ma, Z. Analysis of the effects of temperature increase on quantum random number generator. Eur. Phys. J. D 2021, 75, 1–9. [Google Scholar] [CrossRef]


| Metric | Value |
|---|---|
| Core Area [μm2] | 896,089.4208 |
| CLK Frequency [MHz] | 47.61904762 |
| Number of Cells by Type | |
| ANDNOT | 9180 |
| AND | 423 |
| DFFE PP | 45 |
| MUX | 48 |
| NAND | 533 |
| NOR | 5281 |
| NOT | 1084 |
| ORNOT | 900 |
| OR | 3378 |
| XNOR | 3479 |
| XOR | 6821 |
| Total Number of Cells | 31,172 |
| Test Name | 10 × 1,000,000 | 100 × 1,000,000 | 10 × 10,000,000 |
|---|---|---|---|
| Frequency | 10/10 | 100/100 | 10/10 |
| BlockFrequency | 9/10 | 97/100 | 9/10 |
| Cumulative Sums (Forward) | 10/10 | 100/100 | 10/10 |
| Cumulative Sums (Reverse) | 10/10 | 100/100 | 10/10 |
| Runs | 10/10 | 99/100 | 10/10 |
| Longest Run of Ones | 10/10 | 100/100 | 10/10 |
| Rank | 10/10 | 96/100 | 10/10 |
| FFT | 10/10 | 100/100 | 0/10 |
| Non-Overlapping Templates + | 1463/1480 | 9589/9900 | 1375/1480 |
| Overlapping Templates | 10/10 | 100/100 | 6/10 |
| Universal | 10/10 | 100/100 | 10/10 |
| Approximate Entropy | 10/10 | 100/100 | 0/10 |
| Random Excursions + | 79/80 | 521/528 | 71/72 |
| Random Excursions Variant + | 177/180 | 1174/1188 | 160/162 |
| Serial 1 | 10/10 | 94/100 | 0/10 |
| Serial 2 | 10/10 | 100/100 | 0/10 |
| Linear Complexity | 10/10 | 100/100 | 10/10 |
| no issues | issues recorded | issues recorded |
| Entropy and Basic Randomness Measurements for Logistic Map | ||
|---|---|---|
| Test | Volume 1 | Volume 2 |
| Entropy (bits per byte) | 7.999836 | 7.999656 |
| Optimum Compression rate in % | 0 | 0 |
| Chi-square distribution | 283.96 and 10.28% | 5959.49 and 0.01% |
| Arithmetic mean value (127.5 = random) | 127.4484 | 127.4880 |
| Monte Carlo approximation | 3.140875425 (error 0.02 %) | 3.137985142 (error 0.11%) |
| Serial correlation coeff. (totally uncorr. = 0.0) | −0.001300 | −0.000630 |
| Entropy and basic randomness measurements for QUANTIS-USB-4M | ||
| Test | Volume 1 | Volume 2 |
| Entropy (bits per byte) | 7.999848 | 7.999984 |
| Optimum Compression rate in % | 0 | 0 |
| Chi-square distribution | 262.54 and 35.94% | 269.65 and 25.27% |
| Arithmetic mean value (127.5 = random) | 127.4491 | 127.4917 |
| Monte Carlo approximation | 3.139838624 (error 0.05%) | 3.142840823 (error 0.04%) |
| Serial correlation coeff. (totally uncorr. = 0.0) | 0.000663 | −0.000353 |
| Test Name for QUANTIS | 10 × 1,000,000 | 100 × 1,000,000 | 10 × 10,000,000 |
|---|---|---|---|
| Frequency | 10/10 | 99/100 | 10/10 |
| BlockFrequency | 10/10 | 100/100 | 9/10 |
| Cumulative Sums (Forward) | 10/10 | 98/100 | 10/10 |
| Cumulative Sums (Reverse) | 10/10 | 98/100 | 10/10 |
| Runs | 10/10 | 100/100 | 9/10 |
| Longest Run of Ones | 10/10 | 98/100 | 10/10 |
| Rank | 10/10 | 100/100 | 10/10 |
| FFT | 10/10 | 99/100 | 10/10 |
| Non-Overlapping Templates + | 999/996 | 9864/9900 | 788/850 |
| Overlapping Templates | 10/10 | 97/100 | 10/10 |
| Universal | 10/10 | 99/100 | 10/10 |
| Approximate Entropy | 10/10 | 99/100 | 10/10 |
| Random Excursions + | 40/40 | 405/408 | 63/64 |
| Random Excursions Variant + | 90/90 | 908/912 | 144/144 |
| Serial 1 | 10/10 | 100/100 | 10/10 |
| Serial 2 | 10/10 | 100/100 | 10/10 |
| Linear Complexity | 10/10 | 99/100 | 10/10 |
| random (no issue) | random (no issue) | random (no issue) |
| Factor | Low | High |
|---|---|---|
| Random data volume | from 500 to 50,000 | over 50,000 |
| Device size | up to 10 cm × 10 cm × 10 cm | over 10 cm × 10 cm × 10 cm |
| Budget | up to EUR 1000 | over EUR 1000 |
| Available | Limited | |
| Reseeding capability | two or more external sensors | no or one external sensor |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Marszalek, W.; Melosik, M.; Naumowicz, M.; Głowacki, P. Applicability and Design Considerations of Chaotic and Quantum Entropy Sources for Random Number Generation in IoT Devices. Entropy 2025, 27, 726. https://doi.org/10.3390/e27070726
Marszalek W, Melosik M, Naumowicz M, Głowacki P. Applicability and Design Considerations of Chaotic and Quantum Entropy Sources for Random Number Generation in IoT Devices. Entropy. 2025; 27(7):726. https://doi.org/10.3390/e27070726
Chicago/Turabian StyleMarszalek, Wieslaw, Michał Melosik, Mariusz Naumowicz, and Przemysław Głowacki. 2025. "Applicability and Design Considerations of Chaotic and Quantum Entropy Sources for Random Number Generation in IoT Devices" Entropy 27, no. 7: 726. https://doi.org/10.3390/e27070726
APA StyleMarszalek, W., Melosik, M., Naumowicz, M., & Głowacki, P. (2025). Applicability and Design Considerations of Chaotic and Quantum Entropy Sources for Random Number Generation in IoT Devices. Entropy, 27(7), 726. https://doi.org/10.3390/e27070726






