Multi-Party Controlled Semi-Quantum Dialogue Protocol Based on Hyperentangled Bell States
Abstract
1. Introduction
2. MCSQD Protocol
2.1. Preliminary Preparations
2.1.1. Preparation of Quantum States
- (1)
- Measure and prepare qubits exclusively in the Z-basis;
- (2)
- Reflect qubits to other participants without any disturbance;
- (3)
- Reorder qubits using different delay lines.
2.1.2. Huffman Compression Coding
- (1)
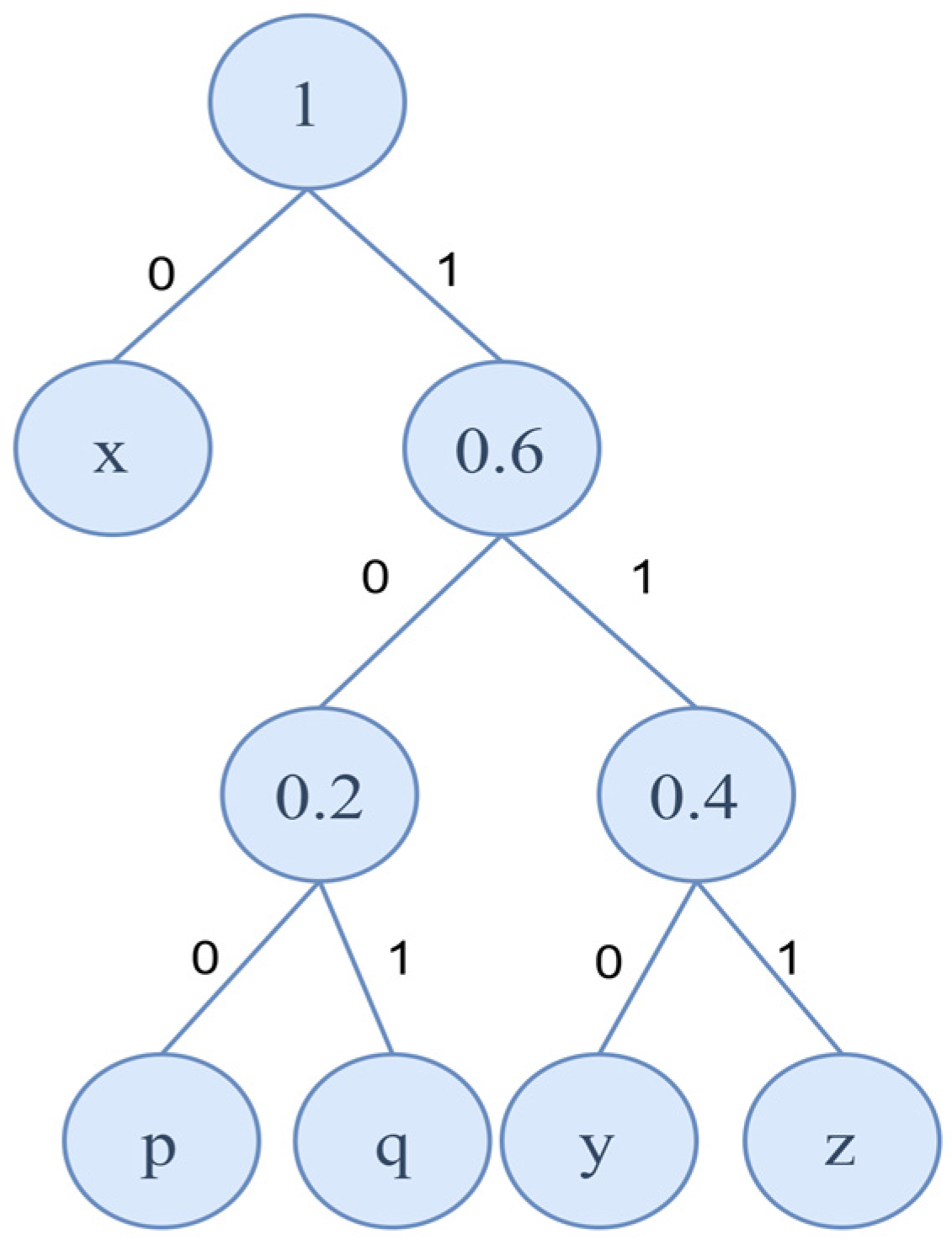
- Frequency Calculation: First, calculate the frequency of each character in the data to be compressed. For example, in the string “” that Bob intends to transmit, the frequencies of the characters are as follows: , and .
- (2)
- Building the Huffman Tree: Treat each character and its frequency as a leaf node and arrange them in ascending order of frequency. Repeat the following steps until only one root node remains:
- Extract the two nodes with the smallest frequencies, merge them into a new node, and set the frequency of the new node as the sum of the two frequencies.
- Reinsert the new node back into the queue.
- (3)
- Assigning Codes: Starting from the root node, assign a ‘0’ for moving to the left subtree and a ‘1’ for moving to the right subtree. The binary sequence along the path from the root node to a specific character represents the encoding of that character. Figure 1 illustrates the Huffman tree constructed using the string “” as an example.
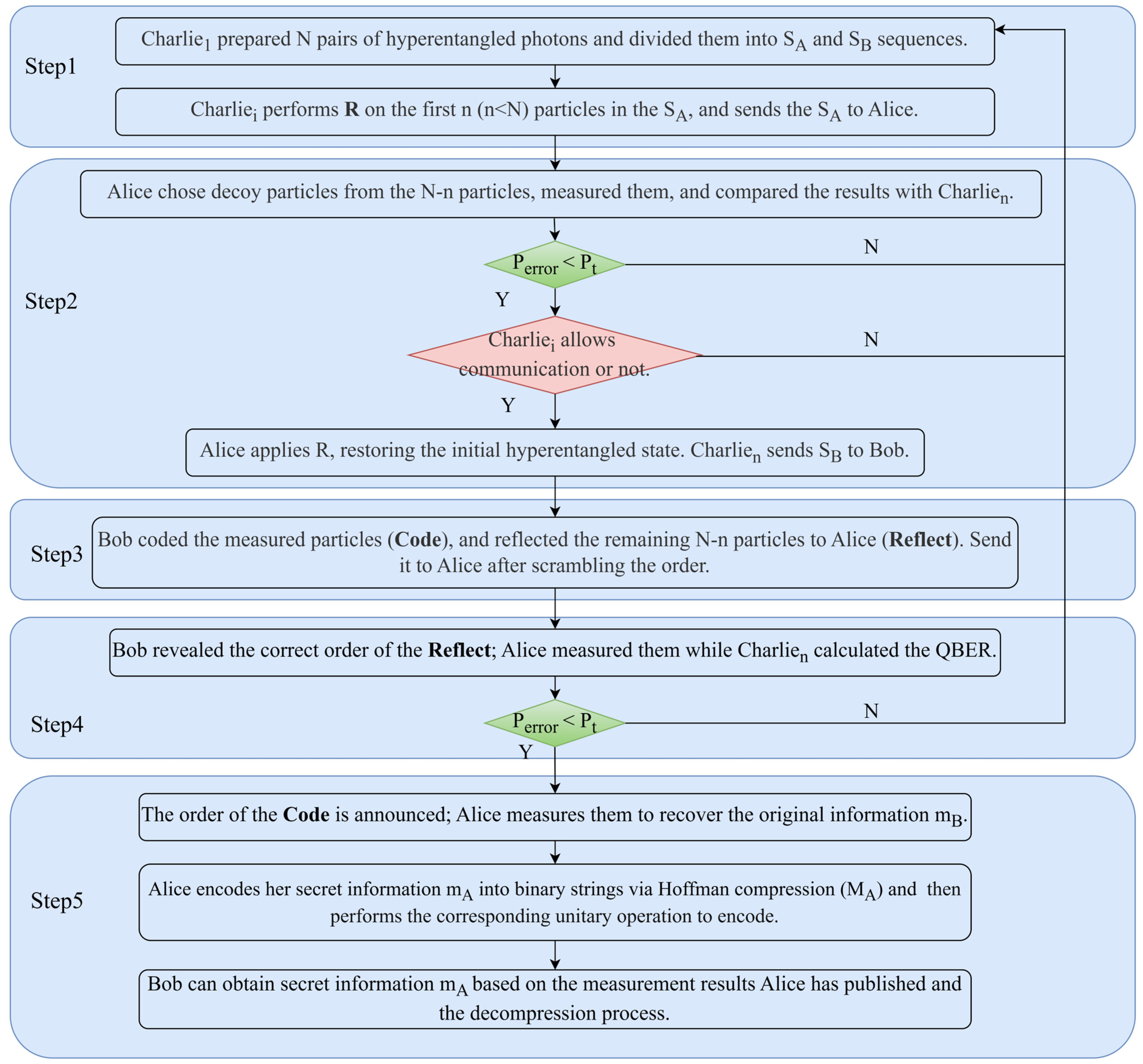
2.2. Protocol Process
3. Security Analysis
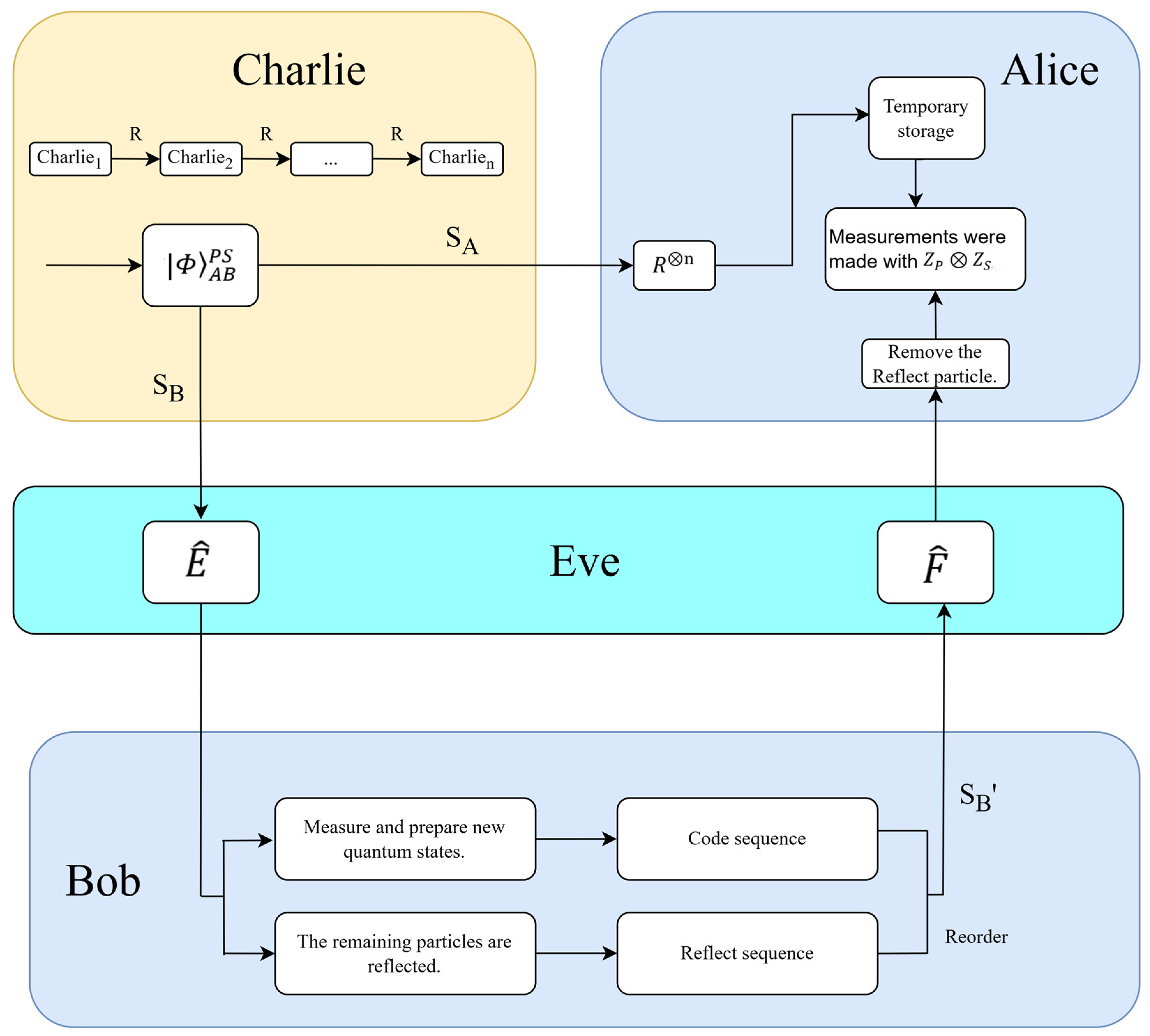
3.1. The Trojan Horse Attack
3.2. The Measure-Resend Attack
3.3. The Entangle-Measure Attack
3.4. Attacks by the Dishonest Controller
3.4.1. Entanglement Substitution
3.4.2. Operation Tampering
3.4.3. Deliberate Disclosure
3.5. Attack by the Dishonest Party
4. Efficiency Analysis
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Long, G.L.; Liu, X.S. Theoretically efficient high-capacity quantum-key-distribution scheme. Phys.Rev. A 2002, 65, 032302. [Google Scholar] [CrossRef]
- Deng, F.G.; Long, G.L.; Liu, X.S. Two-step quantum direct communication protocol using the EinsteinPodolsky-Rosen pair block. Phys. Rev. A 2003, 68, 042317. [Google Scholar] [CrossRef]
- Zhou, Z.R.; Sheng, Y.B.; Niu, P.H.; Yin, L.G.; Long, G.L.; Hanzo, L. Measurement-device-independent quantum secure direct communication. Sci. China Phys. Mech. Astron. 2020, 63, 230362. [Google Scholar] [CrossRef]
- Wu, X.D.; Zhou, L.; Zhong, W.; Sheng, Y.B. High-capacity measurement-device-independent quantum secure direct communication. Quantum Inf. Process. 2020, 19, 354. [Google Scholar] [CrossRef]
- Zhu, F.; Zhang, W.; Sheng, Y.B.; Huang, Y.D. Experimental long-distance quantum secure direct communication. Sci. Bull. 2017, 62, 1519–1524. [Google Scholar] [CrossRef]
- Qi, R.Y.; Sun, Z.; Lin, Z.S.; Niu, P.H.; Hao, W.T.; Song, L.Y.; Huang, Q.; Gao, J.C.; Yin, L.G.; Long, G.L. Implementation and security analysis of practical quantum secure direct communication. Light Sci. Appl. 2019, 8, 22. [Google Scholar] [CrossRef]
- Qi, Z.T.; Li, Y.H.; Huang, Y.W.; Feng, J.; Zheng, Y.L.; Chen, X.F. A 15-user quantum secure direct communication network. Light Sci. Appl. 2021, 10, 183. [Google Scholar] [CrossRef]
- Wang, M.; Zhang, W.; Guo, J.; Song, X.; Long, G. Experimental demonstration of secure relay in quantum secure direct communication network. Entropy 2023, 25, 1548. [Google Scholar] [CrossRef]
- Nguyen, B.A. Quantum dialogue. Phys. Lett. A 2004, 328, 6–10. [Google Scholar] [CrossRef]
- Gao, F.; Guo, F.; Wen, Q.; Zhu, F. Revisiting the security of quantum dialogue and bidirectional quantum secure direct communication. Sci. China Ser. G Phys. Mech. Astron. 2008, 51, 559–566. [Google Scholar] [CrossRef]
- Ye, T.Y. Quantum secure dialogue with quantum encryption. Commun. Theor. Phys. 2014, 62, 338. [Google Scholar] [CrossRef]
- Yin, A.H.; Tang, Z.H.; Chen, D. Efficient quantum dialogue without information leakage. Mod. Phys. Lett. B 2015, 29, 1550018. [Google Scholar] [CrossRef]
- Qi, J.M.; Xu, G.; Chen, X.B.; Wang, T.Y.; Cai, X.Q.; Yang, Y.X. Two authenticated quantum dialogue protocols based on three-particle entangled states. Quantum Inf. Process. 2018, 17, 247. [Google Scholar] [CrossRef]
- Han, K.Q.; Zhou, L.; Zhong, W.; Sheng, Y.B. Measurement-device-independent quantum dialogue based on hyperentanglement. Quantum Inf. Process. 2021, 20, 280. [Google Scholar] [CrossRef]
- Lin, J.; Chang, C.Y. Efficient fault-tolerant quantum dialogue protocols using a quantum reordering circuit of EPR pairs. Phys. Scr. 2023, 98, 095110. [Google Scholar] [CrossRef]
- Zhu, P.H.; Zhong, W.; Du, M.M.; Li, X.Y.; Zhou, L.; Sheng, Y.B. One-step quantum dialogue. Chin. Phys. B 2024, 33, 030302. [Google Scholar] [CrossRef]
- Wang, Y.; Yang, T.; Xu, J.; Chen, X. A dialogue protocol of quantum communication network based on cluster states. Quantum Inf. Process. 2024, 23, 13. [Google Scholar] [CrossRef]
- Lang, Y.F.; Cai, C.C. Fast quantum dialogue. EPJ Quantum Technol. 2025, 12, 59. [Google Scholar] [CrossRef]
- Huang, R.-C.; Yang, Y.-G.; Xu, G.-B.; Jiang, D.-H.; Zhou, Y.-H.; Shi, W.-M. Counterfactual controlled quantum dialogue protocol. Quantum Inf. Process. 2025, 24, 63. [Google Scholar] [CrossRef]
- Boyer, M.; Gelles, R.; Kenigsberg, D.; Mor, T. Semi-quantum key distribution. Phys. Rev. A 2009, 79, 032341. [Google Scholar] [CrossRef]
- Shukla, C.; Thapliyal, K. Pathak, A. Semi-quantum communication: Protocols for key agreement, controlled secure direct communication and dialogue. Quantum Inf. Process. 2017, 16, 295. [Google Scholar] [CrossRef]
- Rong, Z.; Qiu, D.; Mateus, P.; Zou, X. Mediated semi-quantum secure direct communication. Quantum Inf. Process. 2021, 20, 58. [Google Scholar] [CrossRef]
- Shi, G.F. Semi-quantum dialogue scheme based on hyperentangled Bell states. Phys. Scr. 2023, 98, 115120. [Google Scholar] [CrossRef]
- Li, Z.Z.; He, R.Z.; Zhang, Z.Z.; Ding, H.Y.; Wang, D.F. Semi-quantum dialogue protocol based on four-particle Ω state. Chin. J. Phys. 2025, 95, 348–357. [Google Scholar] [CrossRef]
- Zhang, L.; Liu, X.; Xin, X.-J.; Li, P. Semi-Quantum Dialogue with d-Dimensional Single Particles. Int. J. Theor. Phys. 2025, 64, 133. [Google Scholar] [CrossRef]
- Yang, T.; Zhang, Q.; Zhang, J.; Yin, J.; Zhao, Z.; Żukowski, M.; Pan, J.W. All-versus-nothing violation of local realism by two-photon, four-dimensional entanglement. Phys. Rev. Lett. 2005, 95, 240406. [Google Scholar] [CrossRef]
- Sheng, Y.B.; Deng, F.G.; Long, G.L. Complete hyperentangled-Bell-state analysis for quantum communication. Phys. Rev. A—At. Mol. Opt. Phys. 2010, 82, 032318. [Google Scholar] [CrossRef]
- Ren, B.C.; Wei, H.R.; Hua, M.; Li, T.; Deng, F.G. Complete hyperentangled-Bell-state analysis for photon systems assisted by quantum-dot spins in optical microcavities. Opt. Express 2012, 20, 24664–24677. [Google Scholar] [CrossRef]
- Habib, A.; Rahman, M.S. Balancing decoding speed and memory usage for Huffman codes using quaternary tree. Appl. Inform. 2017, 4, 5. [Google Scholar] [CrossRef]
- Chuang, I.L.; Modha, D.S. Reversible arithmetic coding for quantum data compression. IEEE Trans. Inf. Theory 2000, 46, 1104–1116. [Google Scholar] [CrossRef]
- Li, X.H.; Deng, F.G.; Zhou, H.Y. Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A—At. Mol. Opt. Phys. 2006, 74, 054302. [Google Scholar] [CrossRef]
- Cai, Q.Y. Eavesdropping on the two-way quantum communication protocols with invisible photons. Phys. Lett. A 2006, 351, 23–25. [Google Scholar] [CrossRef]
- Deng, F.G.; Li, X.H.; Zhou, H.Y.; Zhang, Z.J. Improving the security of multiparty quantum secret sharing against Trojan horse attack. Phys. Rev. A—At. Mol. Opt. Phys. 2005, 72, 044302. [Google Scholar] [CrossRef]
- Cabello, A. Quantum key distribution in the Holevo limit. Phys. Rev. Lett. 2000, 85, 5635. [Google Scholar] [CrossRef]
- Feng, Y.H.; Zhou, R.G.; Zhang, X.X. Controlled bidirectional quantum secure direct communication with hyperentangled Bell states. Phys. Scr. 2025, 100, 025104. [Google Scholar] [CrossRef]
- Zhou, R.G.; Zhang, X.X.; Li, F. Three-party semi-quantum protocol for deterministic secure quantum dialogue based on GHZ states. Quantum Inf. Process. 2021, 20, 153. [Google Scholar] [CrossRef]
- Pan, H.M. Semi-Quantum Dialogue with Bell Entangled States. Int. J. Theor. Phys. 2020, 59, 1364–1371. [Google Scholar] [CrossRef]
- Shi, G.F. Cryptanalysis and Improvement of Semi-Quantum Dialogue with Bell Entangled States. Int. J. Theor. Phys. 2023, 62, 224. [Google Scholar] [CrossRef]
| Character Values | Binary Encoding |
|---|---|
| 0 | |
| 110 | |
| 111 | |
| 100 | |
| 101 |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhao, M.-N.; Zhou, R.-G.; Feng, Y.-H. Multi-Party Controlled Semi-Quantum Dialogue Protocol Based on Hyperentangled Bell States. Entropy 2025, 27, 666. https://doi.org/10.3390/e27070666
Zhao M-N, Zhou R-G, Feng Y-H. Multi-Party Controlled Semi-Quantum Dialogue Protocol Based on Hyperentangled Bell States. Entropy. 2025; 27(7):666. https://doi.org/10.3390/e27070666
Chicago/Turabian StyleZhao, Meng-Na, Ri-Gui Zhou, and Yun-Hao Feng. 2025. "Multi-Party Controlled Semi-Quantum Dialogue Protocol Based on Hyperentangled Bell States" Entropy 27, no. 7: 666. https://doi.org/10.3390/e27070666
APA StyleZhao, M.-N., Zhou, R.-G., & Feng, Y.-H. (2025). Multi-Party Controlled Semi-Quantum Dialogue Protocol Based on Hyperentangled Bell States. Entropy, 27(7), 666. https://doi.org/10.3390/e27070666





