1. Introduction
In an era of rapid technological advancement and exponential growth in digital data, ensuring the security of multimedia information has become a critical concern. Among various forms of multimedia, images are particularly significant in applications such as medical imaging, military reconnaissance, and secure communication. However, the widespread distribution and exchange of digital images over public networks expose them to risks such as unauthorized access, tampering, and data theft. As a result, the development of robust image encryption techniques has become a key area of research in information security. Traditional encryption algorithms, such as the Advanced Encryption Standard (AES) [
1] and the Rivest-Shamir-Adleman (RSA) algorithm [
2], have been widely used for securing textual data. While these methods are effective for general-purpose encryption, they often struggle with the large data volumes and pixel-level correlations inherent in digital images. These limitations have driven researchers to explore novel approaches specifically designed for image encryption, with the goal of achieving high security, efficiency, and robustness against various cryptographic attacks.
In recent years, chaos theory has garnered significant attention in image encryption due to its unique characteristics, such as sensitivity to initial conditions, ergodicity, and unpredictability. Chaotic systems used in encryption are typically categorized into one-dimensional (1D) and high-dimensional (HD) types. 1D chaotic systems are widely adopted in chaos-based image encryption algorithms because of their simplicity in implementation. For instance, Zhou et al. [
3] proposed a novel combination chaotic system (NCCS) for image encryption, demonstrating strong chaotic behavior and robust security. Liang et al. [
4] introduced a 1D Sine-Cosine chaotic map (SCCM) and developed an image encryption algorithm that integrates SCCM with random DNA operations. Similarly, Kocak et al. [
5] introduced a 1D modular integrated logistic exponential (MILE) map and applied it to a PSO-based image encryption scheme. Despite their effectiveness, image encryption algorithms based on 1D chaotic systems are typically constrained by narrow parameter ranges and weak sensitivity, which limits their ability to provide robust information security. As a result, researchers have increasingly focused on HD chaotic systems, which provide larger key spaces and more complex chaotic behavior, thereby helping to address these limitations [
6]. Wang et al. [
7] proposed a method utilizing a four-dimensional (4D) chaotic system to generate four chaotic sequences, which were then employed to determine the DNA encoding, decoding, and operational methods. Darani et al. [
8] introduced a secure cryptographic algorithm based on a novel three-dimensional (3D) chaotic system (P3DCS), which effectively resists cropping and noise attacks. However, HD chaotic systems tend to be more expensive to implement in terms of both hardware and software due to their higher computational complexity. Therefore, finding the right balance between 1D and HD chaotic maps to design an optimal chaotic map has become a significant challenge. In this context, two-dimensional (2D) chaotic systems are often preferred due to their ease of implementation and strong randomness, making them widely adopted. For example, Wang et al. [
9] developed an image encryption algorithm based on a new 2D chaotic system, 2D-SLTCM, achieving high-security performance. Chen et al. [
10] proposed a novel 2D logarithm-exponent-squared-sine coupling map (2D-LESSCM), and designed an adaptive image compression and encryption scheme, demonstrating exceptional security and robustness. Pak et al. [
11] proposed a novel 2D Infinite Collapse Coupling Map (2D-ICCM) and designed a simple-structured pixel-level image encryption algorithm based on 2D-ICCM to achieve higher security and efficiency. More recently, Tang et al. [
12] proposed a 2D sine-power coupling map (2D-SPCM) exhibiting enhanced chaotic behavior, and developed a cross-plane color image encryption algorithm (CPCIE-SPCM) integrated within an asymmetric encryption framework (ACIES-ECC), further improving key security and resistance to ciphertext tampering. Du et al. [
13] constructed a cross-feedback discrete hyperchaotic system (LCF-CFDHS) by coupling one 2D and two 1D chaotic maps, significantly expanding the chaotic region and improving encryption robustness. Zhou et al. [
14] introduced a novel 2D hyperchaotic map with larger Lyapunov exponents and designed a dynamic RNA computing-based encryption method with enhanced security.
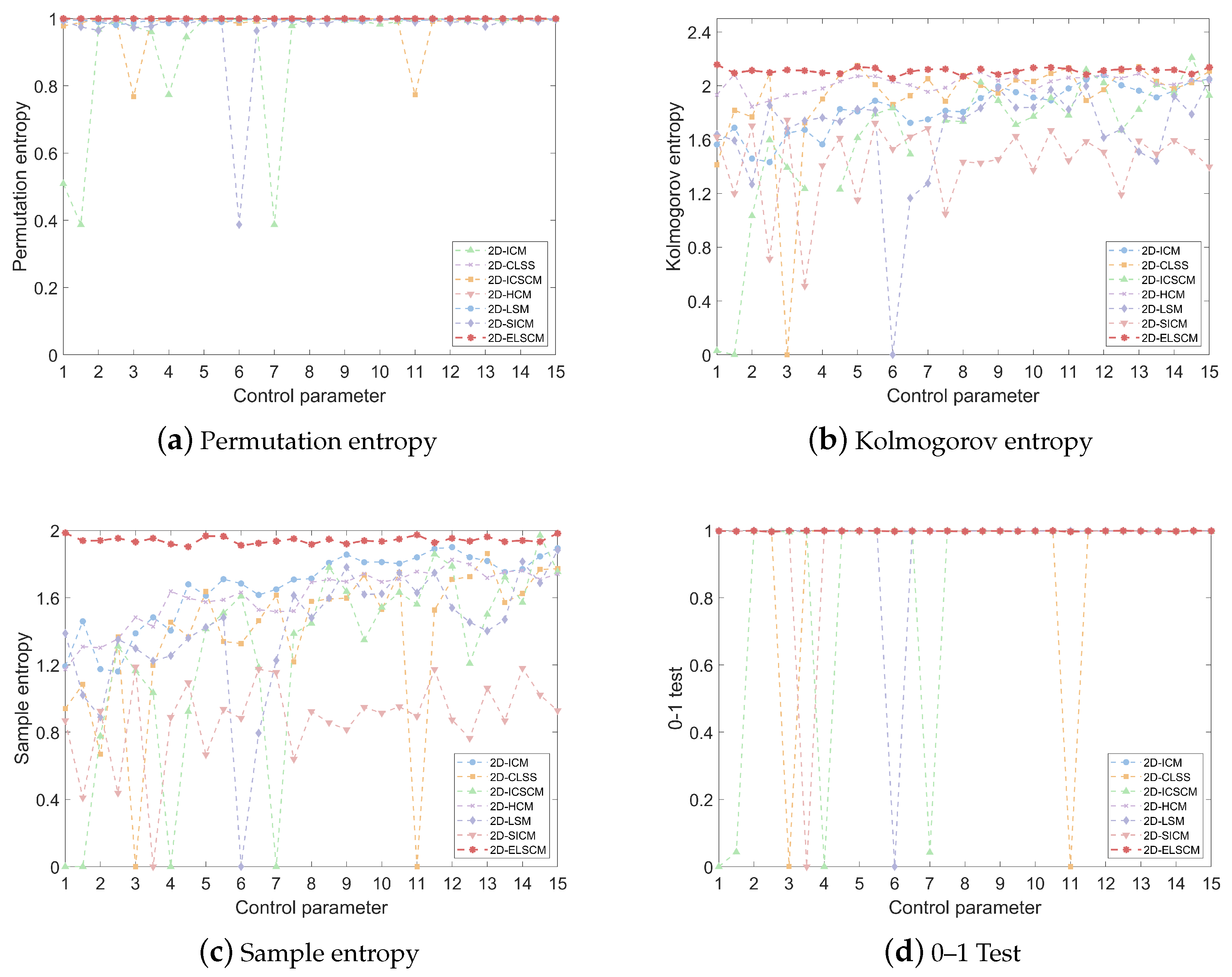
Although 2D chaotic systems are widely used in image encryption due to their simplicity and strong randomness, they still face several limitations. Many existing 2D chaotic maps suffer from small key spaces, low complexity, and periodicity issues, making them susceptible to brute-force and statistical attacks. Additionally, their randomness and sensitivity may not fully meet modern security demands. To address these issues, this study proposes a novel 2D hyperchaotic map, the 2D exponent-logarithm-sine chaotic map (2D-ELSCM), which integrates exponential, logarithmic, and sine functions to provide a larger key space and enhanced unpredictability. Performance evaluations demonstrate its potential for robust image encryption.
However, achieving an optimal balance between security and computational efficiency remains a significant challenge in the field of image encryption. To address this, researchers have explored hybrid approaches that combine chaotic maps with complementary techniques. Among these, DNA-based encryption has emerged as a promising solution due to its high information density and parallel processing capabilities [
15]. By leveraging the molecular structure of DNA, researchers have proposed encryption schemes that encode digital information into DNA sequences, offering a novel biologically inspired approach to ensure secure data transmission. For instance, Yu et al. [
16] proposed an image encryption algorithm that integrates a novel DNA sequence operation with a hyperchaotic system, introducing a DNA triploid mutation (DNA-TM) operation to achieve cryptographic transformation of DNA bases. Similarly, Wang et al. [
17] designed a 2D hyperchaotic map (2D-CICM), which combines the Cubic map with the Infinite Collapse Map (ICM) and incorporates a 3D L-shaped transformation along with DNA crossover and mutation techniques to further enhance security. Additionally, Kumar et al. [
18] utilized an innovative exponent-sine-cosine (ESC) chaotic map in conjunction with dynamic permutation and DNA-based diffusion to achieve multiple-image encryption. Furthermore, Zhou et al. [
19] developed a multi-image encryption scheme based on a new 2D hyperchaotic model combined with cyclic shift coding of DNA. By introducing a cross-coupling chaotic system and a DNA cyclic shift encoding strategy, their approach not only reduced system complexity but also improved the randomness, security, and resistance against differential attacks.
Although DNA-based encryption techniques have made significant progress, numerous challenges still remain. Many existing schemes rely solely on a limited set of DNA rules, which restricts the key space and makes them vulnerable to brute-force attacks. Moreover, the inadequate integration with chaotic systems may result in insufficient randomness and reduced sensitivity to initial conditions, thereby weakening the overall encryption strength. To address these challenges, it is essential to optimize the DNA encoding process, improve key generation mechanisms, and incorporate advanced chaotic systems to enhance encryption randomness. Based on these considerations, this paper proposes an image encryption algorithm that integrates chaotic systems with an improved DNA diffusion technique to enhance encryption performance. The contributions of this study are as follows: (i) The 2D-ELSCM is designed to provide a larger key space and more complex chaotic dynamics, increasing randomness and security. (ii) The improved DNA encoding and Zigzag transformation are integrated to achieve efficient pixel diffusion, thereby enhancing attack resistance and encryption strength. (iii) An optimized key generation mechanism and an efficient image encryption scheme are proposed to balance security and computational efficiency, meeting practical application requirements.
The rest of this paper is structured as follows:
Section 2 provides an overview of the techniques employed in this study.
Section 3 introduces the proposed 2D-ELSCM hyperchaotic system and highlights its superior performance.
Section 4 elaborates on the proposed encryption algorithm, including its architecture, key generation process, and encryption procedures.
Section 5 presents the experimental results and security analysis. Finally,
Section 6 summarizes the paper and suggests potential future research directions.
4. Novel Chaotic Image Encryption Scheme
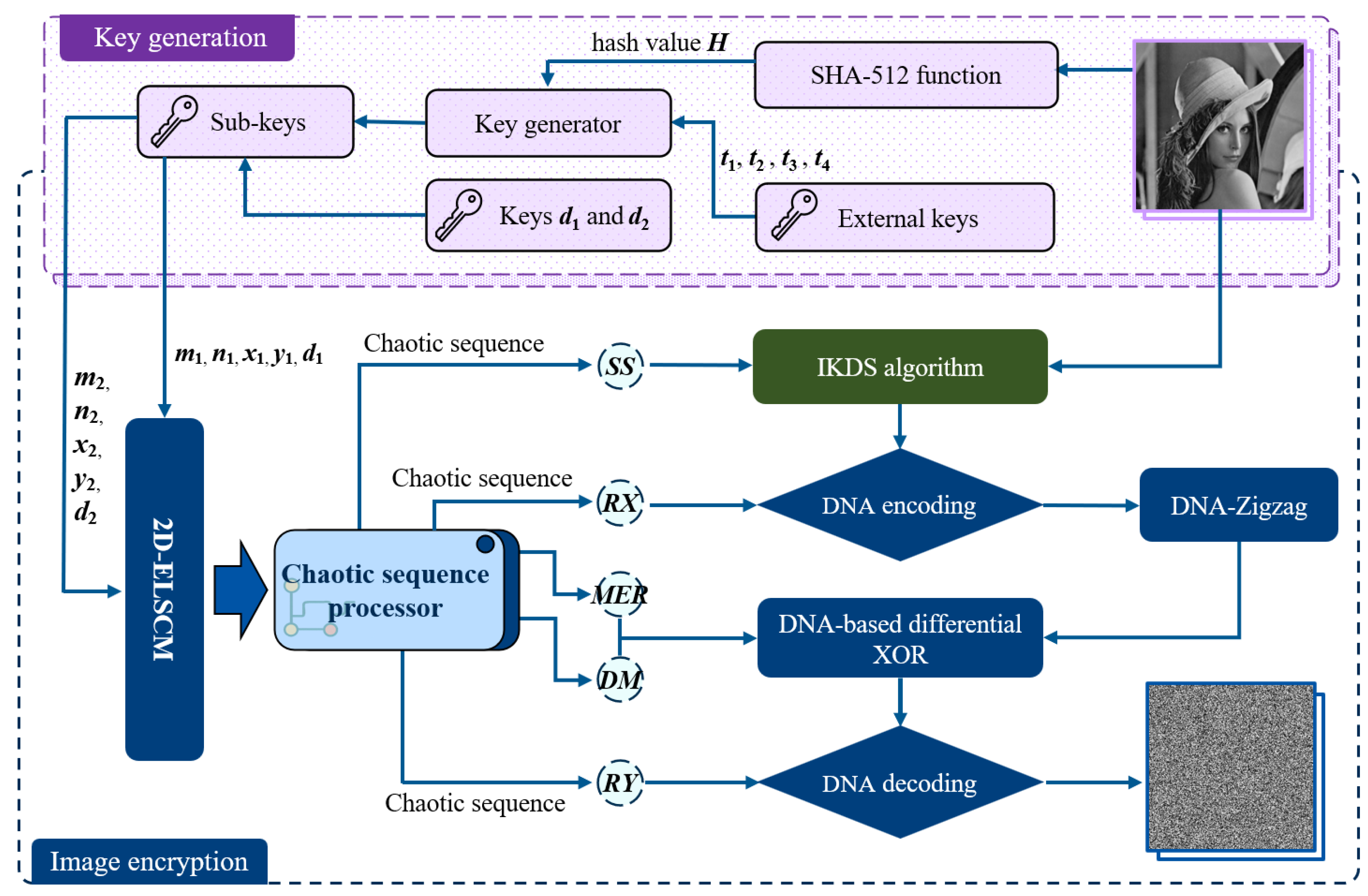
Based on the 2D-ELSCM, this study proposes an innovative chaotic image encryption method to ensure the security of image information. The framework of the proposed cryptographic scheme is depicted in
Figure 7.
The algorithm consists of two main components: key generation and encryption. In the key generation phase, external keys {} within the interval and the hash value of the plaintext image are jointly used to generate the sub-keys {} for iterating the 2D-ELSCM system. In addition, the parameters and are set to discard the initial chaotic sequence elements in order to eliminate transient effects and ensure the chaotic behavior of the generated sequences. This selection aims to achieve a substantial expansion of the key space and enhance the unpredictability of the generated sequences, while simultaneously maintaining a reasonable level of computational overhead. In the encryption phase, a scrambling and diffusion strategy is adopted to achieve high security. First, the IKDS algorithm is employed to scramble the pixel matrix of the plaintext image, where the shuffling indices are dynamically controlled by chaotic sequences to enhance the randomness of pixel positions. Subsequently, the scrambled image undergoes dynamic diffusion based on the DNA-Zigzag algorithm, in which the DNA rules are determined by chaotic sequences. This process not only increases the sensitivity to initial conditions but also enhances the algorithm’s resistance against common cryptographic attacks. The detailed encryption steps are described in the following subsections.
4.1. Key Generation Stage
To resist plaintext attacks, the proposed encryption scheme enhances the correlation with the original image by computing its hash value. External keys are then utilized to determine the initial values and parameters of the 2D-ELSCM. The specific steps are outlined below.
Step 1: The plaintext image serves as input to the SHA-512 hash function, generating a 512-bit hash value denoted as H.
Step 2: The hash value H is partitioned into 64 groups of decimal numbers, which are represented as , , , …, , respectively.
Step 3: The intermediate parameters
,
,
,
,
, and
are generated by the following equations:
where
are external keys. Additionally,
(
x,
y) denotes a function that calculates the XOR result between numbers
x and
y,
(
x,
y) represents the maximum value from
x to
y, and
(
x,
y) calculates the total sum of values from
x to
y.
Step 4: Bring
,
,
,
,
, and
into the following formula to obtain the initial values and the control parameters for 2D-ELSCM:
where
denotes the floor function, which returns the greatest integer less than or equal to the value inside, and
represents the modulo operation. Additionally, the parameters generated by Equation (
3) are specifically employed in the scrambling step of the encryption process, enhancing the randomness of the image. Meanwhile, the parameters derived from Equation (
4) are utilized in the diffusion step, ensuring a more uniform distribution of pixel values.
4.2. Encryption and Decryption Process
This study presents a robust encryption algorithm designed to ensure the security of image data. The following sections offer a comprehensive explanation of the scrambling and diffusion algorithms, along with a in-depth description of the specific encryption steps.
4.2.1. Improved Knuth-Durstenfeld Shuffle Algorithm
Building upon the CKDS algorithm, the proposed improved Knuth-Durstenfeld shuffle (IKDS) algorithm integrates a chaotic system, leveraging the inherent unpredictability of chaotic sequences to control index selection during the shuffling process. This enhancement replaces conventional random number generation with indices derived from chaotic sequence values, thereby achieving permutations with improved randomness and security. Compared to traditional shuffling techniques, the incorporation of a chaotic system increases both the algorithm’s complexity and randomness, making it particularly suitable for security applications. The complete procedure of the IKDS algorithm is presented in Algorithm 2. Specifically, the algorithm traverses the array from the last element to the first. In each iteration, it computes an index by multiplying the corresponding chaotic sequence value by the current index plus one and applying the floor operation. Two elements at the current and computed positions are then swapped using a temporary variable. By utilizing the chaotic sequence in this manner, the IKDS algorithm ensures a high degree of unpredictability throughout the permutation process. Assuming the plaintext image has dimensions , it is permuted following the steps outlined below.
Step 1: Input parameters
,
,
, and
, generated by Equation (
3), into the 2D-ELSCM. Iterate the system
times, discarding the first
elements. Subsequently, chaotic sequences
and
are obtained.
Step 2: Modify the sequences
and
to generate a combined sequence
using Equation (
5):
where
i represents the
i-th element of the sequence.
Step 3: Convert the 2D image matrix into a 1D sequence, which is then shuffled using Algorithm 2. Notably, this process relies on the chaotic sequence generated in Step 2 to ensure randomness. The resulting shuffled sequence is denoted as .
Step 4: Transform the shuffled sequence back into a 2D format to restore the structural layout of the image. This output, denoted as
, is prepared for the subsequent diffusion step. At this stage, the scrambling process is complete.
| Algorithm 2 Pseudocode for IKDS algorithm |
- Require:
An array of length n; a chaotic sequence of length n; temporary variable ; - Ensure:
A shuffled array - 1:
for to 1 do - 2:
- 3:
- 4:
- 5:
- 6:
end for - 7:
return
|
4.2.2. Dynamic DNA-Zigzag Diffusion Algorithm
Previous research integrated the Zigzag algorithm into the scrambling process, yielding satisfactory results. In this study, we further refine this approach by incorporating dynamic DNA encoding and extending its application to the diffusion process.
The proposed DNA-Zigzag method merges DNA encoding with Zigzag scanning techniques to enhance the security and randomness of image encryption. Initially, the image data is transformed into a DNA sequence and organized into a matrix. Subsequently, a new sequence is generated through Zigzag scanning. This approach significantly increases encryption complexity, making it well-suited for applications in secure communication and data storage, thereby addressing the growing demand for high-security encryption. The detailed encryption steps are outlined below, with the core algorithm presented in Algorithm 3.
| Algorithm 3 Implementation process of the DNA-Zigzag |
- Require:
A DNA sequence seq, dimensions height and width - 1:
- 2:
if
then - 3:
Error - 4:
end if - 5:
matrix ← 2D array of size - 6:
zigzag_seq ← empty list - 7:
for to do - 8:
for to do - 9:
- 10:
end for - 11:
end for - 12:
for to do - 13:
if then - 14:
for to do - 15:
zigzag_seq.append() - 16:
end for - 17:
else - 18:
for to 0 by do - 19:
zigzag_seq.append() - 20:
end for - 21:
end if - 22:
end for - 23:
return zigzag_seq
|
Step 1: Input parameters
,
,
, and
, generated by Equation (
4), into the 2D-ELSCM. Iterate the system
times. Discard the first
elements from the resulting sequences, and obtain the chaotic sequences
,
,
, and
, each with a length of
.
Step 2: To further enhance the complexity and security of the encryption algorithm, multiple chaotic sequences are generated using Equation (
6):
where
,
,
, and
represent elements from the chaotic sequences
,
,
, and
, respectively, and
i denotes the
i-th element of these sequences.
Step 3: Convert the input image matrix into a binary sequence. Then, utilize the elements from the chaotic sequence as encoding rules to dynamically encode the binary sequence into a DNA sequence .
Step 4: In this step, the dynamic DNA-Zigzag diffusion process, as detailed in Algorithm 3, is applied to the DNA sequence, where the sequence undergoes a transformation that rearranges its elements based on the zigzag pattern, ultimately generating a disordered version of the original sequence, which is denoted as .
Step 5: DNA mask and differential XOR operation. The sequence
is used as the mask encoding rule to encode the
into sequence
. Subsequently, the
is obtained by XORing
with
specified in
Table 2 and calculated using Equation (
7). This ensures the diffusion process is interdependent among the chaotic sequences:
where
,
, and
denote the
i-th elements of the sequences
,
, and
, respectively.
Step 6: Decode the DNA ciphertext into a binary sequence using the chaotic sequence . Subsequently, convert the binary sequence into a grayscale image to reconstruct the original image structure, yielding the ciphertext image .
Up to this point, the encryption algorithm has been fully described. The decryption process, serving as the inverse of the encryption, recovers the original image using the correct key. Therefore, a detailed discussion of the decryption procedure is omitted for brevity. It is important to note that for color images, the R, G, and B channels are separated, independently encrypted, and then recombined to produce the final encrypted color image.
6. Conclusions
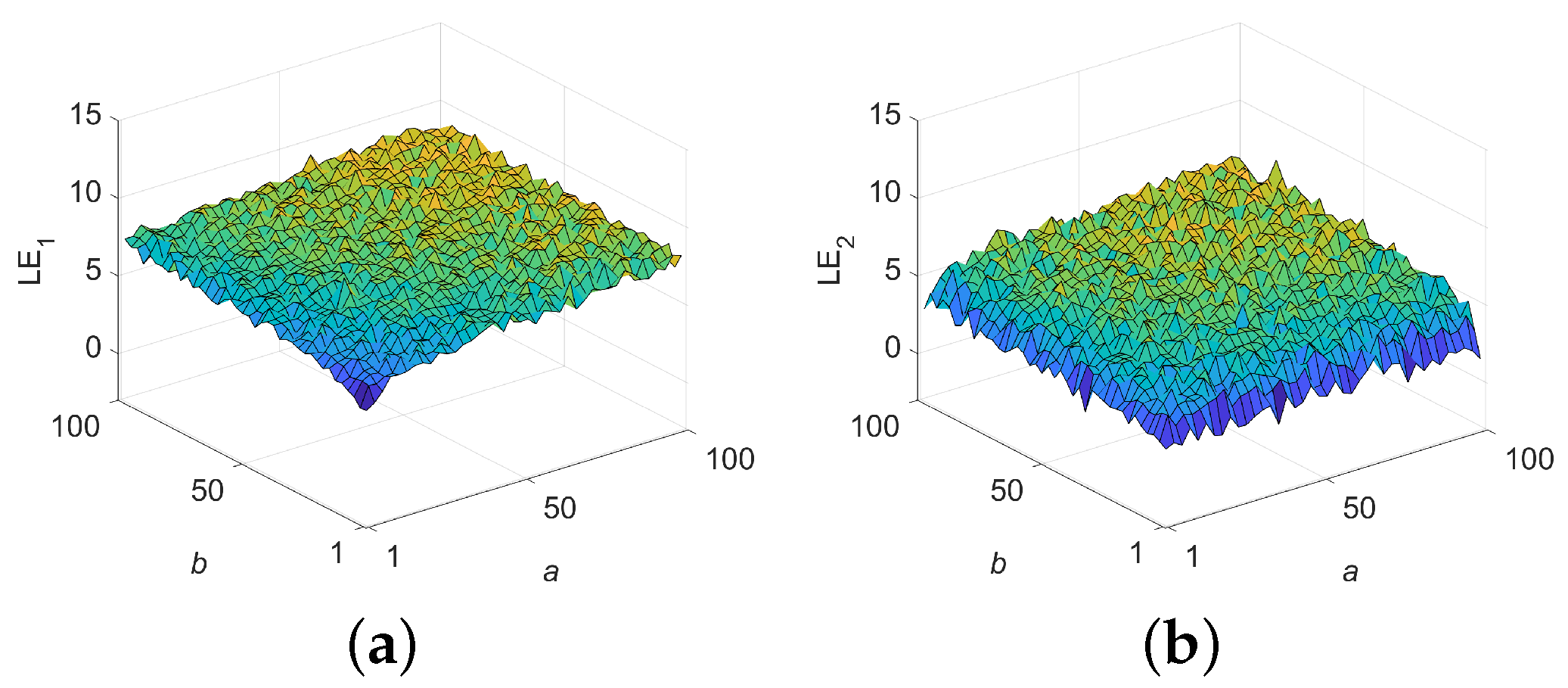
This study presents a novel 2D hyperchaotic map, referred to as the 2D-ELSCM, developed by integrating exponential, logarithmic, and sine functions. Its chaotic characteristics were thoroughly evaluated, yielding an LLE of 8.3175, PE of 0.9998, SE of 1.9826, KE of 2.1117, and a 0–1 test result of 0.9970. Furthermore, the 2D-ELSCM successfully passed the NIST randomness tests, collectively confirming its strong randomness and unpredictability.
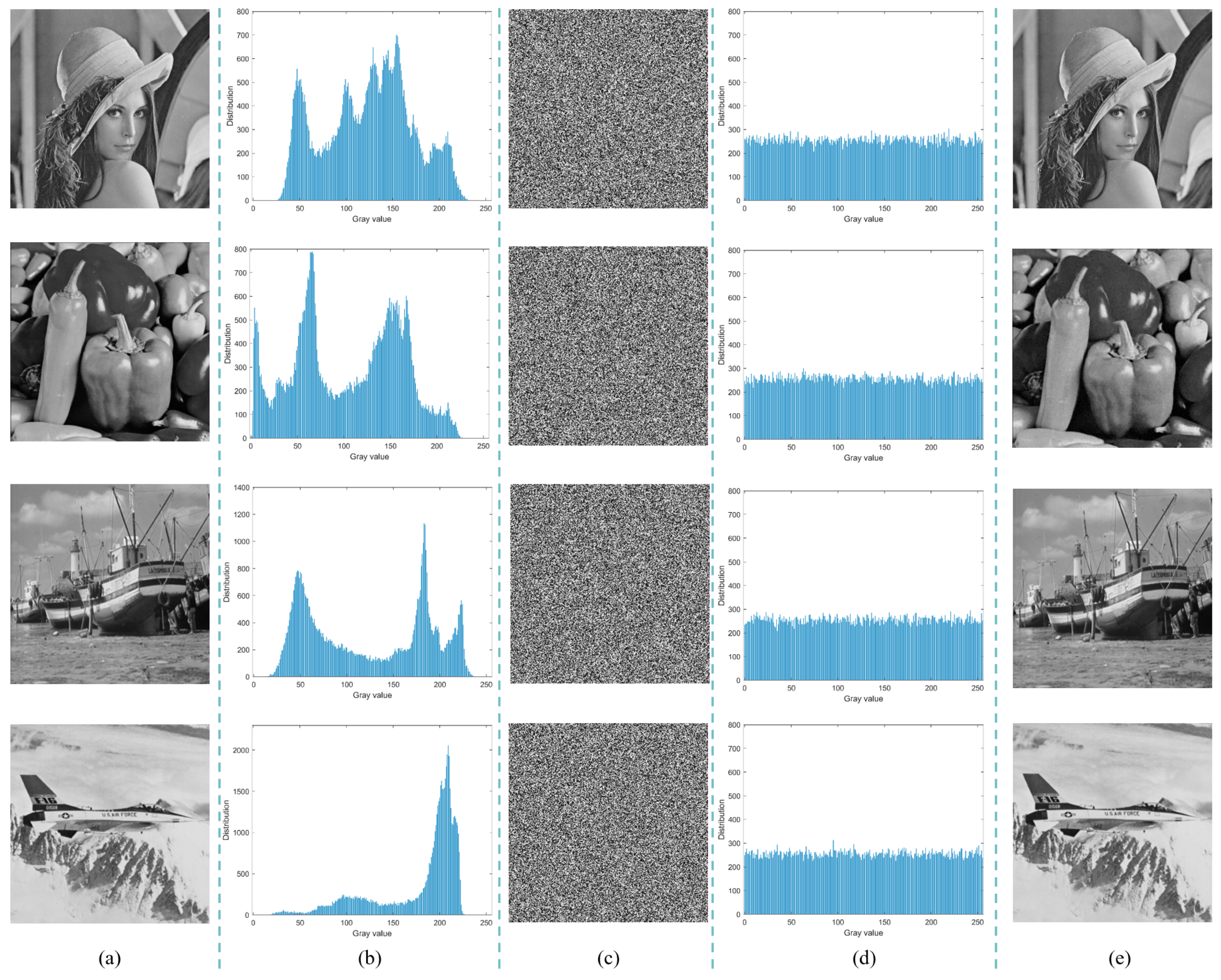
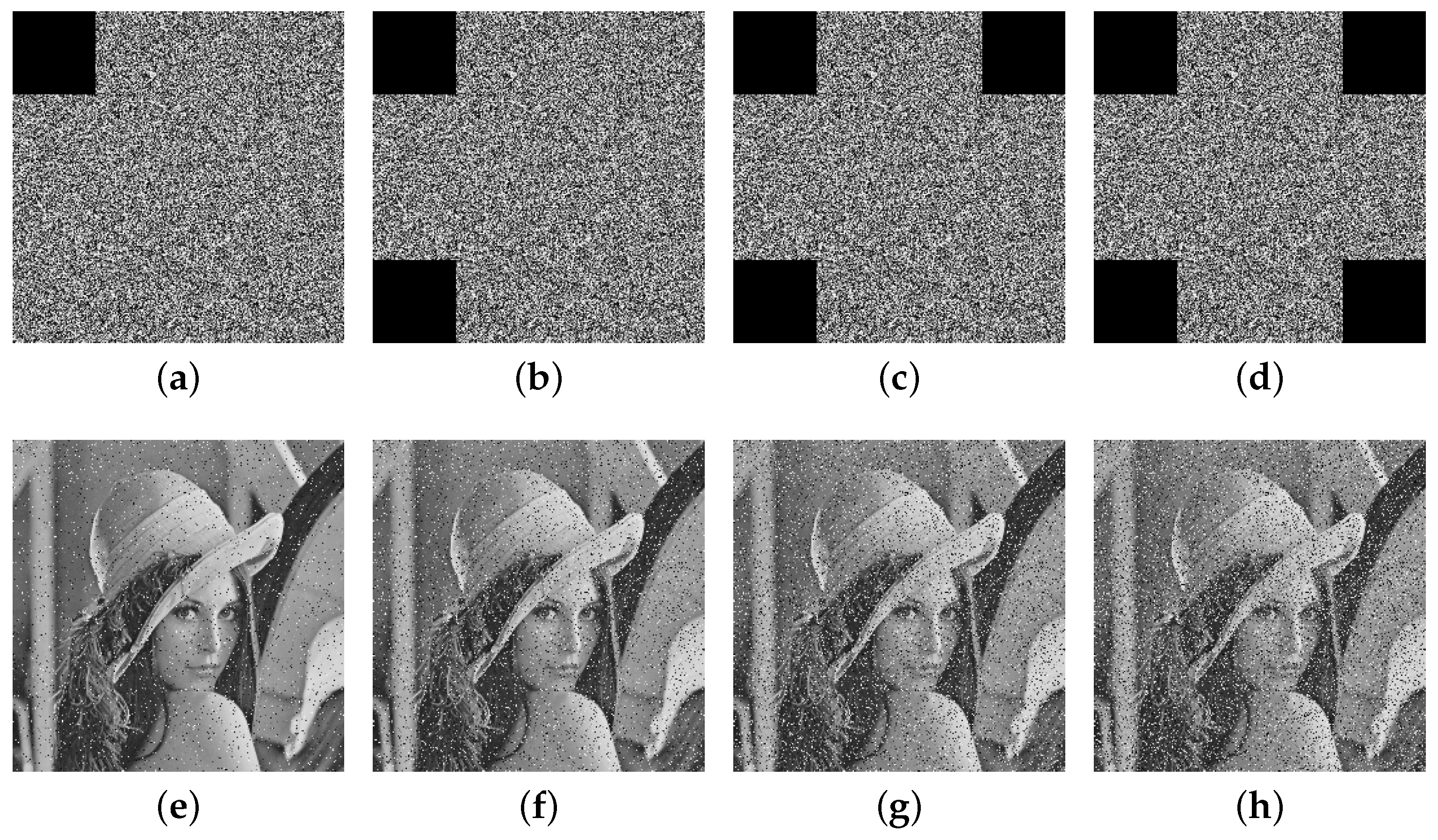
Building upon the 2D-ELSCM, an advanced image encryption scheme was developed. It integrates an IKDS algorithm to disrupt local pixel correlations, and a dynamic diffusion mechanism combining DNA encoding and the Zigzag transform to achieve global pixel diffusion. Key sensitivity and space are enhanced by deriving initial conditions from the SHA-512 hash of the plaintext image combined with an external key. Notably, the scheme is applicable to both grayscale and color images, with color encryption performed through independent processing of the R, G, and B channels. The encrypted color images also exhibit excellent randomness, ensuring the robustness and effectiveness of the proposed method in practical scenarios. Extensive simulations validate the scheme’s effectiveness, achieving correlation coefficients close to 0, an average NPCR of 99.6090%, and UACI of 33.4707%, thereby demonstrating strong resistance against differential attacks and excellent encryption quality for secure image transmission and storage.
Although the proposed method exhibits robust security and efficiency, further improvements are planned. Future work will focus on enhancing diffusion unpredictability by employing chaotic sequences to generate nonlinear, fluctuating Zigzag paths, thereby surmounting the constraints of fixed patterns. Moreover, the integration of digital signature techniques and key exchange protocols will be explored to further strengthen the security of key generation and transmission, ultimately contributing to a more secure and adaptable encryption framework.