Abstract
This study presents a novel two-dimensional hyperchaotic map, referred to as the 2D exponent-logarithm-sine chaotic map (2D-ELSCM), which is intricately designed through the interplay of exponential, logarithmic, and sine functions. To comprehensively evaluate the chaotic performance of the 2D-ELSCM, several critical metrics are employed, including the largest Lyapunov exponent (LLE), permutation entropy (PE), sample entropy (SE), Kolmogorov entropy (KE), and the results of the 0–1 test, which yield values of 8.3175, 0.9998, 1.9826, 2.1117, and 0.9970, respectively. Furthermore, the 2D-ELSCM successfully passes the NIST randomness tests, collectively confirming its exceptional randomness and complexity. Building upon this robust chaotic map, we develop a distinctive chaotic image encryption scheme that employs an improved Knuth-Durstenfeld shuffle (IKDS) to rearrange pixel positions, effectively disrupting the correlation between adjacent pixels. Complementing this, we introduce a dynamic diffusion mechanism that integrates DNA encoding with the Zigzag transform, thereby promoting global pixel diffusion and enhancing encryption security. The initial conditions of the chaotic map are generated from the SHA-512 hash of the plaintext image in conjunction with an external key, which not only expands the key space but also significantly improves key sensitivity. Simulation results demonstrate that the proposed encryption scheme achieves correlation coefficients approaching 0 in the encrypted test images, with an average NPCR of 99.6090% and UACI of 33.4707%. These findings indicate a strong resistance to various attacks and showcase excellent encryption quality, thereby underscoring the scheme’s potential for secure image transmission and storage.
1. Introduction
In an era of rapid technological advancement and exponential growth in digital data, ensuring the security of multimedia information has become a critical concern. Among various forms of multimedia, images are particularly significant in applications such as medical imaging, military reconnaissance, and secure communication. However, the widespread distribution and exchange of digital images over public networks expose them to risks such as unauthorized access, tampering, and data theft. As a result, the development of robust image encryption techniques has become a key area of research in information security. Traditional encryption algorithms, such as the Advanced Encryption Standard (AES) [1] and the Rivest-Shamir-Adleman (RSA) algorithm [2], have been widely used for securing textual data. While these methods are effective for general-purpose encryption, they often struggle with the large data volumes and pixel-level correlations inherent in digital images. These limitations have driven researchers to explore novel approaches specifically designed for image encryption, with the goal of achieving high security, efficiency, and robustness against various cryptographic attacks.
In recent years, chaos theory has garnered significant attention in image encryption due to its unique characteristics, such as sensitivity to initial conditions, ergodicity, and unpredictability. Chaotic systems used in encryption are typically categorized into one-dimensional (1D) and high-dimensional (HD) types. 1D chaotic systems are widely adopted in chaos-based image encryption algorithms because of their simplicity in implementation. For instance, Zhou et al. [3] proposed a novel combination chaotic system (NCCS) for image encryption, demonstrating strong chaotic behavior and robust security. Liang et al. [4] introduced a 1D Sine-Cosine chaotic map (SCCM) and developed an image encryption algorithm that integrates SCCM with random DNA operations. Similarly, Kocak et al. [5] introduced a 1D modular integrated logistic exponential (MILE) map and applied it to a PSO-based image encryption scheme. Despite their effectiveness, image encryption algorithms based on 1D chaotic systems are typically constrained by narrow parameter ranges and weak sensitivity, which limits their ability to provide robust information security. As a result, researchers have increasingly focused on HD chaotic systems, which provide larger key spaces and more complex chaotic behavior, thereby helping to address these limitations [6]. Wang et al. [7] proposed a method utilizing a four-dimensional (4D) chaotic system to generate four chaotic sequences, which were then employed to determine the DNA encoding, decoding, and operational methods. Darani et al. [8] introduced a secure cryptographic algorithm based on a novel three-dimensional (3D) chaotic system (P3DCS), which effectively resists cropping and noise attacks. However, HD chaotic systems tend to be more expensive to implement in terms of both hardware and software due to their higher computational complexity. Therefore, finding the right balance between 1D and HD chaotic maps to design an optimal chaotic map has become a significant challenge. In this context, two-dimensional (2D) chaotic systems are often preferred due to their ease of implementation and strong randomness, making them widely adopted. For example, Wang et al. [9] developed an image encryption algorithm based on a new 2D chaotic system, 2D-SLTCM, achieving high-security performance. Chen et al. [10] proposed a novel 2D logarithm-exponent-squared-sine coupling map (2D-LESSCM), and designed an adaptive image compression and encryption scheme, demonstrating exceptional security and robustness. Pak et al. [11] proposed a novel 2D Infinite Collapse Coupling Map (2D-ICCM) and designed a simple-structured pixel-level image encryption algorithm based on 2D-ICCM to achieve higher security and efficiency. More recently, Tang et al. [12] proposed a 2D sine-power coupling map (2D-SPCM) exhibiting enhanced chaotic behavior, and developed a cross-plane color image encryption algorithm (CPCIE-SPCM) integrated within an asymmetric encryption framework (ACIES-ECC), further improving key security and resistance to ciphertext tampering. Du et al. [13] constructed a cross-feedback discrete hyperchaotic system (LCF-CFDHS) by coupling one 2D and two 1D chaotic maps, significantly expanding the chaotic region and improving encryption robustness. Zhou et al. [14] introduced a novel 2D hyperchaotic map with larger Lyapunov exponents and designed a dynamic RNA computing-based encryption method with enhanced security.
Although 2D chaotic systems are widely used in image encryption due to their simplicity and strong randomness, they still face several limitations. Many existing 2D chaotic maps suffer from small key spaces, low complexity, and periodicity issues, making them susceptible to brute-force and statistical attacks. Additionally, their randomness and sensitivity may not fully meet modern security demands. To address these issues, this study proposes a novel 2D hyperchaotic map, the 2D exponent-logarithm-sine chaotic map (2D-ELSCM), which integrates exponential, logarithmic, and sine functions to provide a larger key space and enhanced unpredictability. Performance evaluations demonstrate its potential for robust image encryption.
However, achieving an optimal balance between security and computational efficiency remains a significant challenge in the field of image encryption. To address this, researchers have explored hybrid approaches that combine chaotic maps with complementary techniques. Among these, DNA-based encryption has emerged as a promising solution due to its high information density and parallel processing capabilities [15]. By leveraging the molecular structure of DNA, researchers have proposed encryption schemes that encode digital information into DNA sequences, offering a novel biologically inspired approach to ensure secure data transmission. For instance, Yu et al. [16] proposed an image encryption algorithm that integrates a novel DNA sequence operation with a hyperchaotic system, introducing a DNA triploid mutation (DNA-TM) operation to achieve cryptographic transformation of DNA bases. Similarly, Wang et al. [17] designed a 2D hyperchaotic map (2D-CICM), which combines the Cubic map with the Infinite Collapse Map (ICM) and incorporates a 3D L-shaped transformation along with DNA crossover and mutation techniques to further enhance security. Additionally, Kumar et al. [18] utilized an innovative exponent-sine-cosine (ESC) chaotic map in conjunction with dynamic permutation and DNA-based diffusion to achieve multiple-image encryption. Furthermore, Zhou et al. [19] developed a multi-image encryption scheme based on a new 2D hyperchaotic model combined with cyclic shift coding of DNA. By introducing a cross-coupling chaotic system and a DNA cyclic shift encoding strategy, their approach not only reduced system complexity but also improved the randomness, security, and resistance against differential attacks.
Although DNA-based encryption techniques have made significant progress, numerous challenges still remain. Many existing schemes rely solely on a limited set of DNA rules, which restricts the key space and makes them vulnerable to brute-force attacks. Moreover, the inadequate integration with chaotic systems may result in insufficient randomness and reduced sensitivity to initial conditions, thereby weakening the overall encryption strength. To address these challenges, it is essential to optimize the DNA encoding process, improve key generation mechanisms, and incorporate advanced chaotic systems to enhance encryption randomness. Based on these considerations, this paper proposes an image encryption algorithm that integrates chaotic systems with an improved DNA diffusion technique to enhance encryption performance. The contributions of this study are as follows: (i) The 2D-ELSCM is designed to provide a larger key space and more complex chaotic dynamics, increasing randomness and security. (ii) The improved DNA encoding and Zigzag transformation are integrated to achieve efficient pixel diffusion, thereby enhancing attack resistance and encryption strength. (iii) An optimized key generation mechanism and an efficient image encryption scheme are proposed to balance security and computational efficiency, meeting practical application requirements.
The rest of this paper is structured as follows: Section 2 provides an overview of the techniques employed in this study. Section 3 introduces the proposed 2D-ELSCM hyperchaotic system and highlights its superior performance. Section 4 elaborates on the proposed encryption algorithm, including its architecture, key generation process, and encryption procedures. Section 5 presents the experimental results and security analysis. Finally, Section 6 summarizes the paper and suggests potential future research directions.
2. Preliminary Works
2.1. Classic Knuth-Durstenfeld Shuffle Algorithm
The classic Knuth-Durstenfeld shuffle (CKDS) algorithm [20], an optimized version of the Fisher-Yates shuffle, is a widely adopted method for generating unbiased random permutations of a finite sequence. It operates in-place with a time complexity of , making it both computationally efficient and memory-conserving.
The algorithm operates by iterating backward through the array, starting from the last element. At each step, it randomly selects an index from the unshuffled portion of the array and swaps the corresponding elements. This process guarantees that all possible permutations are equally probable. The pseudocode for this algorithm is presented in Algorithm 1. Owing to its efficiency and reliability, CKDS algorithm finds extensive applications in cryptographic systems, random sampling, and other scenarios requiring unbiased data shuffling.
| Algorithm 1 Pseudocode for CKDS algorithm |
|
2.2. Zigzag Transformation
Zigzag transformation [21] is a widely employed technique in image processing and encryption, designed to enhancing the security and randomness of data arrangements. The primary function of the Zigzag operation is to reorder the elements of a matrix in a non-linear manner, following a predefined diagonal traversal pattern.
Typically, the Zigzag operation begins at the top-left corner of the matrix and moves diagonally, alternating between upward and downward directions, until all elements are traversed. This traversal pattern transforms the original sequential arrangement of data into a scrambled order, effectively reducing spatial correlation among neighboring elements. Figure 1 illustrates the scanning process in detail for a fourth-order square matrix.
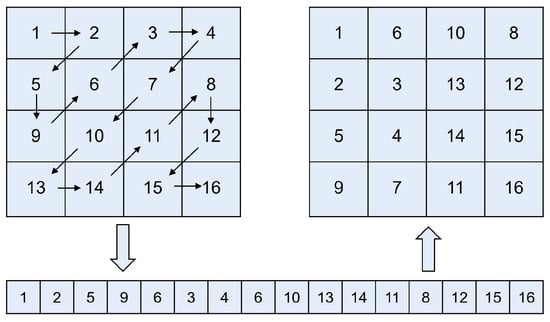
Figure 1.
Scanning process of the standard Zigzag transformation.
2.3. DNA Coding
A DNA sequence is composed of four nucleotides [4]: A (adenine), T (thymine), C (cytosine), and G (guanine), where A pairs with T and C pairs with G based on the principle of complementary base pairing. Similarly, in binary sequences, 0 and 1 are considered complements. Based on this analogy, the nucleotides A, T, C, and G can be represented by binary values such as 00, 01, 10, and 11, respectively. This mapping enables the four nucleotides to correspond to four unique binary codes, resulting in a total of 24 possible encoding schemes. However, only 8 of these encoding methods comply with the Watson-Crick complementarity rule [22], as illustrated in Table 1.

Table 1.
Rules of DNA encoding and decoding.
For instance, the pixel value 45 of the image can be expressed in binary as “00101101”, and by applying coding rule 3 from Table 1, the DNA sequence “TGAC” can be derived. Likewise, decoding the DNA sequence “TGAC” using rule 3 reconstructs the binary value “00101101” corresponding to the pixel value 45. However, using other rules for decoding results in a different value. For example, applying rule 8 to the binary number “01001011” yields the pixel value 180. It is evident that the DNA encoding and decoding processes effectively alter the pixel values, thereby providing an encryption effect. For DNA sequences, operations such as addition, subtraction, XOR, and complementary transformations are commonly employed to enhance the complexity of the sequence. Table 2 provides a detailed demonstration of the XOR operation applied to nucleic acid bases, illustrating how this process contributes to the overall robustness of DNA-based encryption schemes.

Table 2.
XOR operations of DNA coding.
3. Hyperchaotic Map
In this section, we present the mathematical definition of the 2D-ELSCM and assess its performance based on specific assessment indicators. Furthermore, the proposed hyperchaotic map demonstrates superior behavior compared to several existing chaotic systems in terms of quantitative evaluation metrics. The results suggest that the dynamical characteristics of this system surpass those of other systems, exhibiting higher complexity and enhanced randomness.
3.1. Definition of 2D-ELSCM
To address the limitations of traditional 1D and HD chaotic systems, this study proposes a novel 2D chaotic model that couples a logarithmic-exponential function with a squared sine function, as defined in Equation (1):
where and represent the states of 2D-ELSCM, and m and n are control parameters with .
The proposed system exhibits strong nonlinear dynamics due to the combined effects of the logarithmic function and the exponential function . The singular behavior of the logarithmic function, coupled with the rapid growth of the exponential function, enhances the chaotic characteristics of the system, particularly as the values of and vary, leading to high sensitivity to initial conditions. Additionally, the use of the function constrains the iterative results to the range . This newly proposed map not only amplifies the unpredictability of numerical values but also further enhances the chaotic nature of the system, making it highly suitable for applications requiring robust chaotic behavior.
3.2. Performance of 2D-ELSCM
This section analyzes the 2D-ELSCM using various test metrics, including bifurcation diagrams, trajectory diagrams, Lyapunov exponent, sample entropy, permutation entropy, Kolmogorov entropy, the 0–1 test, and the NIST randomness test. Furthermore, the newly proposed map is compared with six existing 2D chaotic maps to provide a more comprehensive performance analysis. The mathematical definitions of these maps are concisely summarized in Table 3.

Table 3.
Comparison among the existing 2D chaotic systems.
3.2.1. Bifurcation and Phase Plane Trajectory Diagram
The bifurcation diagram highlights the elements of the chaotic sequence with respect to control parameters [28], providing a direct visualization of the system’s evolution process.
In this section, the bifurcation diagram of the 2D-ELSCM is presented in Figure 2, where the initial values () are set to (0.5, 0.5). Figure 2a illustrates the variation of the state variable as the control parameters and change. Similarly, Figure 2b demonstrates the variation of the state variable under the same conditions.
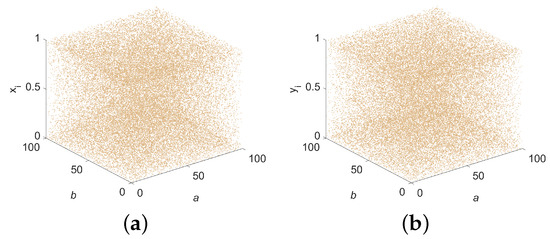
Figure 2.
Bifurcation diagram of 2D-ELSCM. (a) State variable ; (b) State variable .
The 3D bifurcation diagram of the 2D-ELSCM, also shown in Figure 2, depicts how the state variables and evolve as the control parameters vary over the same range. Clearly, the proposed system spans the entire parameter space rather than being confined to specific regions. This indicates that the hyperchaotic sequences generated by the system exhibit high sensitivity to initial conditions and control parameters, as well as strong ergodicity.
The phase space trajectory provides an intuitive method for observing system dynamics. When the points representing the chaotic sequence densely populate the coordinate space, it implies that the nonlinear system’s output exhibits enhanced randomness. Figure 3a presents 2D phase space trajectory diagrams of versus , while Figure 3b illustrates the 3D phase space trajectory formed by v + 2, v + 1, and v, where v denotes the combined x and y series.
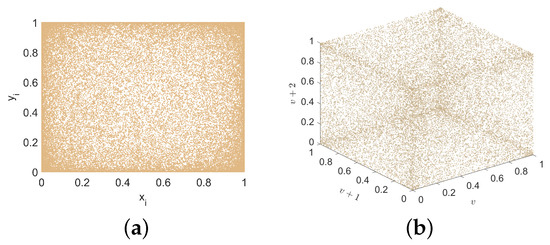
Figure 3.
Trajectory diagram of 2D-ELSCM for a = 15 and b = 15 (Initial values = 0.5, = 0.5). (a) 2D trajectory; (b) 3D trajectory.
3.2.2. Lyapunov Exponent
The Lyapunov exponent (LE) serves as an objective metric for evaluating chaotic behavior in nonlinear systems, where the number of exponents corresponds to the dimensionality. A positive LE indicates instability and sensitivity to initial conditions, reflecting inherent unpredictability.
A 2D chaotic system typically has two LEs, denoted as and . In this section, the 3D plots of and for 2D-ELSCM, varying with respect to parameters a and b in the range of [1, 100], are presented in Figure 4. As observed, with changes in the control parameters a and b, both and remain positive. This confirms that the 2D-ELSCM exhibits hyperchaotic behavior over a broad range.
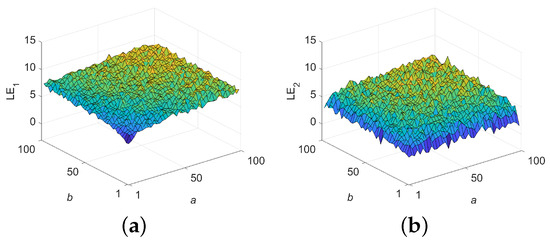
Figure 4.
LEs of 2D-ELSCM. (a) 3D illustration of ; (b) 3D illustration of .
The largest Lyapunov exponent (LLE) is a critical metric for quantifying the chaotic behavior of a dynamic system. A higher LLE value indicates a greater degree of chaos, reflecting stronger sensitivity to initial conditions, as well as increased uncertainty and unpredictability [27]. Figure 5 presents a comparison of the LLE values across different 2D chaotic systems. Additionally, the average LLE values for 2D-ELSCM and other chaotic systems are summarized in Table 4. Notably, the proposed map exhibits larger LLE values, confirming that the 2D-ELSCM demonstrates enhanced dynamic behavior and stronger chaotic properties.
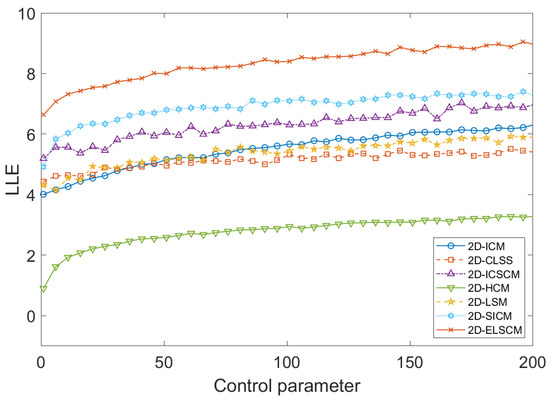
Figure 5.
Comparison of of existing 2D maps.

Table 4.
Comparative analysis of the average chaotic metrics for various 2D chaotic maps.
3.2.3. Permutation Entropy
Permutation entropy (PE) is a widely employed metric for quantifying the complexity and chaotic characteristics of a time series, providing valuable insights into the system’s dynamic behavior. By examining the relative ordering patterns of elements within the time series, PE effectively measures the system’s unpredictability and degree of chaos. The PE value ranges from 0 to 1, where values closer to 1 indicate higher complexity and greater chaotic behavior, reflecting highly unpredictable dynamics. Consequently, PE serves as an effective tool for detecting chaotic behavior and evaluating the intrinsic complexity of nonlinear systems.
In the context of the proposed 2D-ELSCM system, a comparative analysis of PE values with several recent chaotic systems is presented in Figure 6a. The average PE values for each system are summarized in Table 4, offering a clear comparison of their chaotic characteristics. From this analysis, it is evident that the 2D-ELSCM achieves the highest mean PE value, outperforming other established chaotic systems. This superior PE value underscores the exceptional randomness and complexity of the 2D-ELSCM, reinforcing its suitability for cryptographic applications where high unpredictability is critical for security.
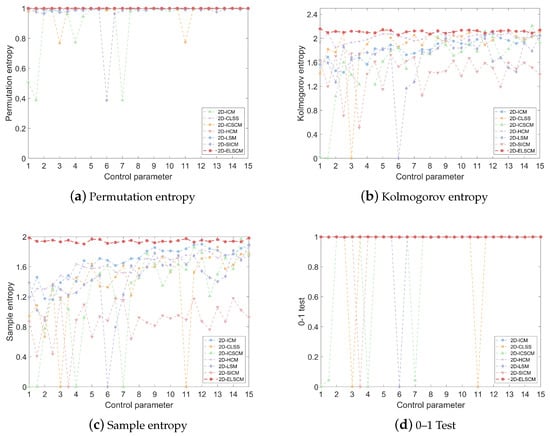
Figure 6.
Comparative visualization of chaotic metrics for various 2D chaotic maps.
3.2.4. Kolmogorov Entropy
The Kolmogorov entropy (KE) is a key metric used to assess the randomness or disorder within a dynamical system. It quantifies the rate at which the system’s trajectories diverge, offering insights into the system’s unpredictability. A system with high KE values indicates highly chaotic and irregular behavior, making future states difficult to predict. In contrast, a system with low KE values tends to exhibit more regular or predictable patterns, implying lower complexity and reduced sensitivity to initial conditions.
For the 2D-ELSCM, the KE values are computed using the method proposed by [29]. The KE values of the 2D-ELSCM are then compared with those of six other recently proposed chaotic systems, as shown in Figure 6b. The analysis reveals that the 2D-ELSCM consistently exhibits larger positive KE values across a wide range of parameter settings, outperforming other chaotic maps. This suggests that the proposed system encompasses a broader chaotic range and demonstrates stronger unpredictability. Such characteristics are crucial for cryptographic applications, where a high level of randomness and disorder is necessary to ensure data security.
Furthermore, the average KE values summarized in Table 4 further underscore the superior performance of the 2D-ELSCM. The table illustrates that the proposed map generates chaotic sequences with the highest complexity among those analyzed. This demonstrates that the 2D-ELSCM is not only more chaotic but also capable of offering stronger resistance to attacks, thereby enhancing its effectiveness in cryptographic systems.
3.2.5. Sample Entropy
Sample entropy (SE) is a quantitative measure used to assess the complexity, irregularity, or unpredictability of time series data, particularly in the context of chaotic systems. It improves upon approximate entropy (AE) by focusing on evaluating the likelihood that similar patterns will recur at different times within the series. Essentially, SE quantifies the degree of unpredictability by analyzing the probability of recurrence of similar sequences over time. A higher SE value indicates that the system is more complex, less predictable, and demonstrates a higher level of chaotic behavior, making it a valuable tool for analyzing chaotic systems, especially in cryptographic applications.
In Figure 6c, the SE values for the 2D-ELSCM are presented alongside those from other recently proposed chaotic systems. This comparison underscores the superior performance of the 2D-ELSCM in terms of SE. Additionally, the corresponding average SE values are summarized in Table 4, which clearly shows that the proposed hyperchaotic map consistently achieves higher SE values than the other six chaotic systems. These results suggest that the 2D-ELSCM exhibits significantly greater complexity and randomness, essential characteristics for ensuring the security of cryptographic applications.
3.2.6. 0–1 Test
The core idea of the 0–1 test is to analyze the relative positions of system trajectory points to determine whether the system exhibits chaotic behavior. If the trajectory points are randomly distributed in the phase space without any discernible regularity, the test value will approach 1, indicating chaotic dynamics. Conversely, if the trajectory demonstrates periodicity or stability, the test value will approach 0, indicating non-chaotic behavior.
The 0–1 test results, compared with those of other recent chaotic maps, are presented in Figure 6d, which underscores the robust performance of the proposed system. The average 0–1 test values are provided in Table 4, with the 2D-ELSCM achieving the highest mean value of 0.9970. This exceptional result highlights the superior chaotic dynamics of the 2D-ELSCM, further reinforcing its suitability for advanced cryptographic applications.
3.2.7. NIST SP800-22 Test
The NIST SP800-22 test suite is a well-established statistical framework used to assess the randomness of pseudo-random number sequences, which is critical for cryptographic applications. The suite comprises 15 distinct sub-tests, each producing a p-value that reflects the statistical quality of the sequence. If the p-value of a sub-test exceeds 0.01, it indicates that the sequence has passed that particular test, confirming its randomness and unpredictability [30]. This ensures that the generated sequence is not easily predictable, a crucial requirement for secure encryption.
In this study, the NIST SP800-22 test results for the 2D-ELSCM are summarized in Table 5. As shown, the pseudo-random number sequences generated by the proposed 2D-ELSCM pass all 15 sub-tests successfully. The high p-values across all tests demonstrate that the generated sequences exhibit excellent randomness, which is essential for ensuring the unpredictability of the encryption process. Consequently, the 2D-ELSCM proves to be highly suitable for image cryptography, providing a robust and secure foundation for encrypting sensitive data.

Table 5.
NIST randomness test results of 2D-ELSCM.
4. Novel Chaotic Image Encryption Scheme
Based on the 2D-ELSCM, this study proposes an innovative chaotic image encryption method to ensure the security of image information. The framework of the proposed cryptographic scheme is depicted in Figure 7.
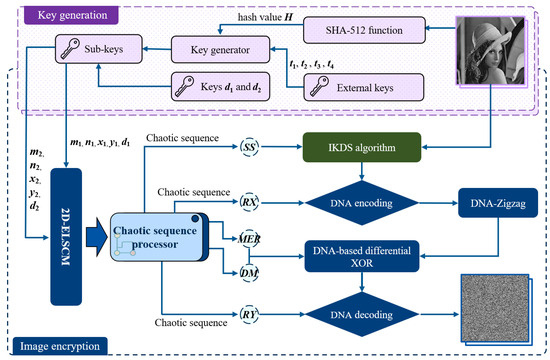
Figure 7.
Framework of the proposed cryptographic scheme including key generation and encryption.
The algorithm consists of two main components: key generation and encryption. In the key generation phase, external keys {} within the interval and the hash value of the plaintext image are jointly used to generate the sub-keys {} for iterating the 2D-ELSCM system. In addition, the parameters and are set to discard the initial chaotic sequence elements in order to eliminate transient effects and ensure the chaotic behavior of the generated sequences. This selection aims to achieve a substantial expansion of the key space and enhance the unpredictability of the generated sequences, while simultaneously maintaining a reasonable level of computational overhead. In the encryption phase, a scrambling and diffusion strategy is adopted to achieve high security. First, the IKDS algorithm is employed to scramble the pixel matrix of the plaintext image, where the shuffling indices are dynamically controlled by chaotic sequences to enhance the randomness of pixel positions. Subsequently, the scrambled image undergoes dynamic diffusion based on the DNA-Zigzag algorithm, in which the DNA rules are determined by chaotic sequences. This process not only increases the sensitivity to initial conditions but also enhances the algorithm’s resistance against common cryptographic attacks. The detailed encryption steps are described in the following subsections.
4.1. Key Generation Stage
To resist plaintext attacks, the proposed encryption scheme enhances the correlation with the original image by computing its hash value. External keys are then utilized to determine the initial values and parameters of the 2D-ELSCM. The specific steps are outlined below.
Step 1: The plaintext image serves as input to the SHA-512 hash function, generating a 512-bit hash value denoted as H.
Step 2: The hash value H is partitioned into 64 groups of decimal numbers, which are represented as , , , …, , respectively.
Step 3: The intermediate parameters , , , , , and are generated by the following equations:
where are external keys. Additionally, (x, y) denotes a function that calculates the XOR result between numbers x and y, (x, y) represents the maximum value from x to y, and (x, y) calculates the total sum of values from x to y.
Step 4: Bring , , , , , and into the following formula to obtain the initial values and the control parameters for 2D-ELSCM:
where denotes the floor function, which returns the greatest integer less than or equal to the value inside, and represents the modulo operation. Additionally, the parameters generated by Equation (3) are specifically employed in the scrambling step of the encryption process, enhancing the randomness of the image. Meanwhile, the parameters derived from Equation (4) are utilized in the diffusion step, ensuring a more uniform distribution of pixel values.
4.2. Encryption and Decryption Process
This study presents a robust encryption algorithm designed to ensure the security of image data. The following sections offer a comprehensive explanation of the scrambling and diffusion algorithms, along with a in-depth description of the specific encryption steps.
4.2.1. Improved Knuth-Durstenfeld Shuffle Algorithm
Building upon the CKDS algorithm, the proposed improved Knuth-Durstenfeld shuffle (IKDS) algorithm integrates a chaotic system, leveraging the inherent unpredictability of chaotic sequences to control index selection during the shuffling process. This enhancement replaces conventional random number generation with indices derived from chaotic sequence values, thereby achieving permutations with improved randomness and security. Compared to traditional shuffling techniques, the incorporation of a chaotic system increases both the algorithm’s complexity and randomness, making it particularly suitable for security applications. The complete procedure of the IKDS algorithm is presented in Algorithm 2. Specifically, the algorithm traverses the array from the last element to the first. In each iteration, it computes an index by multiplying the corresponding chaotic sequence value by the current index plus one and applying the floor operation. Two elements at the current and computed positions are then swapped using a temporary variable. By utilizing the chaotic sequence in this manner, the IKDS algorithm ensures a high degree of unpredictability throughout the permutation process. Assuming the plaintext image has dimensions , it is permuted following the steps outlined below.
Step 1: Input parameters , , , and , generated by Equation (3), into the 2D-ELSCM. Iterate the system times, discarding the first elements. Subsequently, chaotic sequences and are obtained.
Step 2: Modify the sequences and to generate a combined sequence using Equation (5):
where i represents the i-th element of the sequence.
Step 3: Convert the 2D image matrix into a 1D sequence, which is then shuffled using Algorithm 2. Notably, this process relies on the chaotic sequence generated in Step 2 to ensure randomness. The resulting shuffled sequence is denoted as .
Step 4: Transform the shuffled sequence back into a 2D format to restore the structural layout of the image. This output, denoted as , is prepared for the subsequent diffusion step. At this stage, the scrambling process is complete.
| Algorithm 2 Pseudocode for IKDS algorithm |
|
4.2.2. Dynamic DNA-Zigzag Diffusion Algorithm
Previous research integrated the Zigzag algorithm into the scrambling process, yielding satisfactory results. In this study, we further refine this approach by incorporating dynamic DNA encoding and extending its application to the diffusion process.
The proposed DNA-Zigzag method merges DNA encoding with Zigzag scanning techniques to enhance the security and randomness of image encryption. Initially, the image data is transformed into a DNA sequence and organized into a matrix. Subsequently, a new sequence is generated through Zigzag scanning. This approach significantly increases encryption complexity, making it well-suited for applications in secure communication and data storage, thereby addressing the growing demand for high-security encryption. The detailed encryption steps are outlined below, with the core algorithm presented in Algorithm 3.
| Algorithm 3 Implementation process of the DNA-Zigzag |
|
Step 1: Input parameters , , , and , generated by Equation (4), into the 2D-ELSCM. Iterate the system times. Discard the first elements from the resulting sequences, and obtain the chaotic sequences , , , and , each with a length of .
Step 2: To further enhance the complexity and security of the encryption algorithm, multiple chaotic sequences are generated using Equation (6):
where , , , and represent elements from the chaotic sequences , , , and , respectively, and i denotes the i-th element of these sequences.
Step 3: Convert the input image matrix into a binary sequence. Then, utilize the elements from the chaotic sequence as encoding rules to dynamically encode the binary sequence into a DNA sequence .
Step 4: In this step, the dynamic DNA-Zigzag diffusion process, as detailed in Algorithm 3, is applied to the DNA sequence, where the sequence undergoes a transformation that rearranges its elements based on the zigzag pattern, ultimately generating a disordered version of the original sequence, which is denoted as .
Step 5: DNA mask and differential XOR operation. The sequence is used as the mask encoding rule to encode the into sequence . Subsequently, the is obtained by XORing with specified in Table 2 and calculated using Equation (7). This ensures the diffusion process is interdependent among the chaotic sequences:
where , , and denote the i-th elements of the sequences , , and , respectively.
Step 6: Decode the DNA ciphertext into a binary sequence using the chaotic sequence . Subsequently, convert the binary sequence into a grayscale image to reconstruct the original image structure, yielding the ciphertext image .
Up to this point, the encryption algorithm has been fully described. The decryption process, serving as the inverse of the encryption, recovers the original image using the correct key. Therefore, a detailed discussion of the decryption procedure is omitted for brevity. It is important to note that for color images, the R, G, and B channels are separated, independently encrypted, and then recombined to produce the final encrypted color image.
5. Experimental Simulation and Security Analysis
5.1. Simulation Environment and Results
The proposed encryption scheme was implemented using Python 3.8.1 within the PyCharm 2023.1.3 (Community Edition) development environment. The implementation was carried out on a system equipped with 16.00 GB of RAM and an Intel(R) Core(TM) i5-12600 CPU running at 3.30 GHz, operating on the Windows 10 platform. This section presents a performance evaluation of the proposed encryption algorithm from several perspectives. Additionally, a summary of the external keys and other experimental parameters utilized in the simulations is provided in Table 6.

Table 6.
Experimental parameters and values.
5.2. Histogram Analysis
In the domain of image encryption, histogram analysis serves as a critical method for assessing the effectiveness of encryption algorithms. An ideal encryption algorithm should significantly alter the pixel distribution of the original image, producing a ciphertext image with a uniformly distributed histogram to ensure privacy and unpredictability.
Figure 8 displays the original image, the encrypted image, and their corresponding histograms. As shown in Figure 8a,c,e, the proposed algorithm effectively transforms the original image into a noise-like structure while enabling its lossless reconstruction. Additionally, in Figure 8b,d, the histogram of the ciphertext image exhibits a uniform distribution, which contrasts sharply with the plaintext histogram. This result highlights the algorithm’s ability to disrupt the statistical properties of the image, thereby rendering the ciphertext image highly resistant to analysis through basic statistical methods.
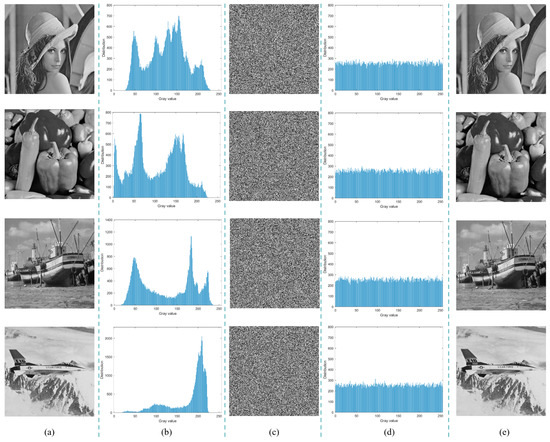
Figure 8.
Simulation test of encryption algorithm: (a) plaintext images (256 × 256); (b) histograms of the plain images; (c) cipher images; (d) histograms of the ciphertext images; (e) decrypted images.
5.3. Chi-Square Test
In the field of image encryption, the Chi-square () test is commonly utilized to evaluate the statistical characteristics of encrypted images. This test assesses whether the encryption algorithm effectively disrupts the original pixel distribution, ensuring randomness and uniformity in the ciphertext image. The Chi-square statistic is mathematically expressed as [12]:
where i denotes the number of gray levels, while and represent the observed and expected frequencies, respectively. The histogram distribution is deemed uniform if the Chi-square value falls below 293.24783. Table 7 summarizes the Chi-square values for 256 × 256 plaintext and ciphertext images. Notably, the Chi-square values of the ciphertext images are significantly lower than those of the plaintext images, and all ciphertext values satisfy the criteria for passing the Chi-square test.

Table 7.
Chi-square values for test plaintext and ciphertext images.
5.4. Correlation Analysis
Correlation analysis is a crucial technique for assessing the security of image encryption algorithms. It quantifies the extent to which the encryption process disrupts the statistical properties of an image by calculating the correlation coefficients between adjacent pixels in the horizontal, vertical, and diagonal directions. The correlation coefficient between adjacent pixels x and y is defined as follows [13]:
where N denotes the total number of pixels, and and represent the mean values of x and y, respectively. From Equation (9), it is evident that the correlation coefficients lie within the range [0, 1]. Original images typically exhibit high correlation, whereas an ideal encrypted image should display correlation coefficients close to 0, indicating that the correlations between adjacent pixels have been effectively eliminated.
The 3D diagrams of correlation coefficients in three directions for both the test images and their encrypted counterparts are shown in Figure 9. As illustrated, the correlation in all directions is uniformly distributed across the entire coordinate space. Furthermore, the correlation analysis results of various methods are presented in Table 8. It is evident that the correlation coefficients of the ciphertext images generated by the proposed algorithm are closer to 0 compared to those of other algorithms, demonstrating its enhanced resistance to statistical attacks.
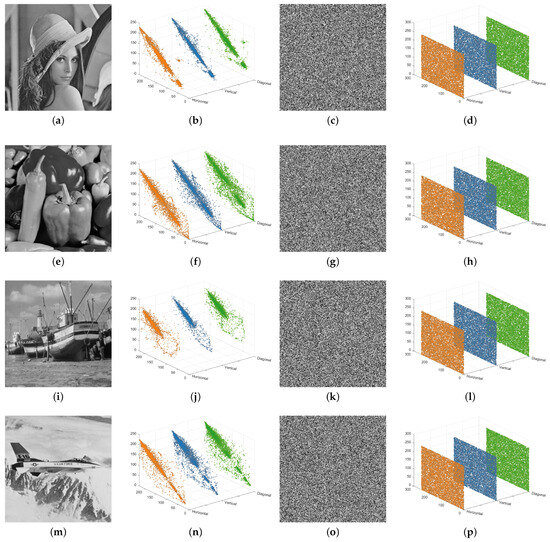
Figure 9.
Correlation distributions: (a,e,i,m) plain images; (b,f,j,n) histograms of those plain images in three directions; (c,g,k,o) cipher images of (a,e,i,m); (d,h,l,p) histograms of those cipher images in three directions.

Table 8.
Correlation coefficients of different images using various algorithms.
5.5. Differential Attack Analysis
The Number of Pixels Change Rate (NPCR) and Unified Average Changing Intensity (UACI) are widely used metrics for evaluating the ability of encryption algorithms to resist differential attacks. The mathematical expressions for NPCR and UACI are given as follows [34]:
where and denote the cipher images of the original plaintext image and the plaintext image with one pixel altered, respectively. M and N are the height and width of the test images, and F is the maximum allowable pixel value of the image. Additionally, the ideal values for the NPCR and UACI tests are 99.6094% and 33.4635%, respectively.
A novel evaluation criterion for the NPCR and UACI tests was introduced by [35]. The NPCR test is considered successful if the NPCR value exceeds the one-sided hypothesis threshold determined by the significance level (). This can be expressed as follows:
where represents the inverse cumulative density function (CDF) of the standard normal distribution. Meanwhile, denotes the test level and it is set to 0.01 and 0.05 in subsequent testing scenarios [4].
In a similar manner, the UACI test is deemed successful if the calculated UACI value lies within the range of (, ), where and are specified as
In this subsection, several test images with resolutions of and were selected to evaluate the algorithm’s sensitivity to minor modifications. For each image, 100 trials were conducted by randomly selecting a pixel and increasing its value by 1. The NPCR and UACI results under different values of are summarized in Table 9 and Table 10. When , the pass rates for both metrics exceed 90%; when , the pass rates approach 100%. The proposed algorithm achieves average NPCR and UACI values that are very close to the ideal theoretical values. Furthermore, Table 11 presents a detailed comparison of NPCR and UACI values across different test images. The proposed method consistently outperforms or matches the performance of the approaches reported in [4,36], further confirming its robustness against differential attacks.

Table 9.
NPCRs of different images using the proposed scheme.

Table 10.
UACIs of different images using the proposed scheme.

Table 11.
Comparison of the NPCR and UACI values using various algorithms.
5.6. Information Entropy
Information entropy reflects the randomness in the distribution of pixel intensity values in an image. For an ideally encrypted image, the entropy approaching its theoretical maximum value. The formula for information entropy H is given by:
where represents the probability of pixel intensity , and N denotes the number of intensity levels, which is commonly set to 256. When the information entropy of an encrypted image approaches the theoretical maximum of 8, it indicates a nearly uniform and random distribution of pixel intensities [32]. To comprehensively evaluate the encryption performance, images of different sizes were selected to calculate the information entropy values for both plaintext and ciphertext images, as defined in Equation (15). Table 12 presents the entropy results for grayscale and color images with resolutions of 256 × 256 and 512 × 512, respectively. The ciphertext images exhibit entropy values consistently close to the theoretical maximum value of 8, indicating that the proposed encryption algorithm effectively disrupts the original pixel distribution and demonstrates good applicability and encryption performance for both grayscale and color images. To provide a more comprehensive evaluation of the encryption performance, a comparative analysis of information entropy across two types of images was conducted. As summarized in Table 13 and Table 14, the proposed scheme consistently achieves comparable or higher entropy values for ciphertext images relative to most state-of-the-art methods, thereby demonstrating improved randomness and robustness. These results highlight the scheme’s effectiveness in enhancing the security of encrypted image data against potential cryptographic attacks.

Table 12.
Information Entropy analysis of various plain and encrypted test images.

Table 13.
Information entropy comparison of different algorithms (256 × 256).

Table 14.
Information entropy comparison of different algorithms (512 × 512).
5.7. Key Analysis
Key analysis is a vital component in evaluating the performance of an encryption algorithm. This section will validate the security and robustness of the algorithm from two key aspects: key space and key sensitivity.
5.7.1. Key Space Analysis
The key space is a crucial metric for assessing the security of an encryption algorithm, as its size directly impacts the algorithm’s resistance to brute-force attacks. An encryption algorithm with a sufficiently large key space can effectively thwart attackers attempting to decrypt data by exhaustively searching all possible keys. According to [38], the key space should exceed to guarantee the security of encryption algorithm.
The proposed encryption algorithm features a robust key design, consisting of the following components: (i) 512-bit hash key generated by the original image; (ii) the external parameter , , , ; and (iii) the abandoning number and of chaotic sequences. Assuming that the calculation accuracy in this experimental environment is , the key space of this algorithm is . The key space of the proposed algorithm is compared with that of other schemes, and the results are presented in Table 15. The results clearly demonstrate that the proposed algorithm achieves the largest key space, significantly enhancing security and resistance to brute-force attacks.

Table 15.
Comparison of key space among various algorithms.
5.7.2. Key Sensitivity Analysis
An encryption algorithm with high sensitivity ensures that even a slight change in the key results in completely different encrypted images, making it difficult for attackers to recover the original image or obtain any information about the key. To evaluate key sensitivity quantitatively, the number of bit change rate (NBCR) [40] is utilized. For two bit sequences and of length , the NBCR is determined using:
where Hm is the Hamming distance of and . If the sequences and are approximately independent, the NBCR value will approach 50%. The test process for key sensitivity is as follows:
(i) The original SHA-512 key, denoted as K, is initially prepared, and a modified version is derived by altering a single bit in K to evaluate sensitivity.
(ii) The encryption of the original image is performed with both K and , generating ciphertext images and (). The normalized bit change rate (NBCR) between the ciphertexts is calculated to measure key sensitivity.
(iii) The decryption of both ciphertext sets is carried out using , resulting in decrypted images and (). The values are then evaluated to verify the algorithm’s sensitivity during decryption.
As illustrated in Figure 10, the NBCR value curves for both ciphertext and decrypted images remain approximately 50%. This observation highlights the proposed encryption scheme’s high key sensitivity and its ability to prevent unauthorized access through minor key modifications.
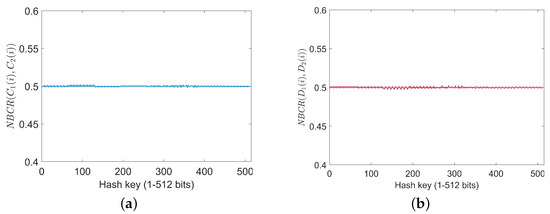
Figure 10.
NBCR analysis for encrypted and decrypted images: (a) NBCR of encrypted images with a one-bit key change; (b) NBCR of decrypted images with a one-bit key change.
5.8. Robustness Analysis
Image transmission and storage processes are often subject to various forms of interference and attacks. A robust image encryption algorithm is expected to effectively resist these disturbances and environmental variations, ensuring that the decrypted image closely resembles the original. Evaluations of the proposed algorithm’s robustness are conducted through noise and cropping attack analyses.
5.8.1. Noise Attack Analysis
Resistance to noise attacks is a critical attribute of a robust image encryption algorithm, enabling successful decryption despite interference. In this study, the application of salt-and-pepper noise (SPN), Gaussian noise (GN), and speckle noise (SN) to encrypted images simulates realistic transmission scenarios involving noise attacks. The decrypted results from noisy images are displayed in Figure 11. Observations reveal that, even with added noise, the decryption process effectively restores the original images with high visual quality.

Figure 11.
Decryption results of cipher images with different densities of SPN, GN, and SN.
5.8.2. Data Loss Attack Analysis
During image transmission, interference within the channel often causes significant data loss, posing challenges to data integrity. The evaluation of an encryption algorithm’s robustness against cropping attacks is therefore essential to assess its performance under such conditions.
Figure 12 and Figure 13 present the restoration results of two test cipher images subjected to pixel block losses of 1/16, 1/8, 3/16, and 1/4, respectively. The results indicate that, despite varying degrees of data loss, a substantial portion of the original image’s information remains visible in the decrypted outputs. These findings highlight the proposed algorithm’s strong capability to preserve critical information and resist cropping attacks effectively.
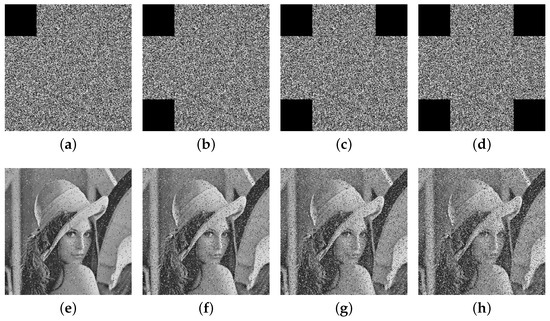
Figure 12.
The encryption images with cropping attack (a) 1/16, (b) 1/8, (c) 3/16, (d) 1/4 and (e–h) represent their respective decrypted images.
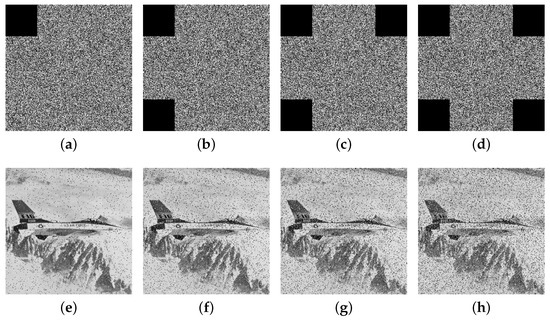
Figure 13.
The encryption images with cropping attack (a) 1/16, (b) 1/8, (c) 3/16, (d) 1/4 and (e–h) represent their respective decrypted images.
5.9. Time Complexity Analysis
To validate its practical value, an encryption algorithm should minimize time complexity without compromising security. This subsection evaluates the time complexity of the proposed approach.
For a plain image of size , the computational complexity of the proposed algorithm primarily arises from the operations in the permutation and diffusion stages. During the shuffle permutation process, the first step involves generating two chaotic sequences, resulting in a computational complexity of . The second step modifies these chaotic sequences, contributing a time complexity of . The third step performs the IKDS algorithm, which has a time complexity of .
The time complexity analysis for the DNA-based diffusion process is as follows. In the first step, chaotic sequences are generated by iterating the 2D-ELSCM model to produce four sequences, leading to a time complexity of . The subsequent step modifies these chaotic sequences, also contributing a time complexity of . Steps 3 and 6 involve DNA encoding and decoding operations, each with a time complexity of . Step 4 executes the DNA-zigzag operation, with a time complexity of . Finally, Step 5 performs the DNA differential XOR operation, which has a time complexity of .
As a result, the overall time complexity of the proposed encryption scheme is . To further verify the practical efficiency of the proposed algorithm, the actual encryption and decryption times were measured and compared with existing methods. As shown in Table 16, the proposed algorithm achieves encryption and decryption times that are comparable to those of reference [4] and significantly lower than those reported in reference [34]. These results demonstrate that the proposed approach not only ensures robust security but also maintains high computational efficiency, making it suitable for real-time and resource-constrained applications.

Table 16.
Time test result of different algorithms.
6. Conclusions
This study presents a novel 2D hyperchaotic map, referred to as the 2D-ELSCM, developed by integrating exponential, logarithmic, and sine functions. Its chaotic characteristics were thoroughly evaluated, yielding an LLE of 8.3175, PE of 0.9998, SE of 1.9826, KE of 2.1117, and a 0–1 test result of 0.9970. Furthermore, the 2D-ELSCM successfully passed the NIST randomness tests, collectively confirming its strong randomness and unpredictability.
Building upon the 2D-ELSCM, an advanced image encryption scheme was developed. It integrates an IKDS algorithm to disrupt local pixel correlations, and a dynamic diffusion mechanism combining DNA encoding and the Zigzag transform to achieve global pixel diffusion. Key sensitivity and space are enhanced by deriving initial conditions from the SHA-512 hash of the plaintext image combined with an external key. Notably, the scheme is applicable to both grayscale and color images, with color encryption performed through independent processing of the R, G, and B channels. The encrypted color images also exhibit excellent randomness, ensuring the robustness and effectiveness of the proposed method in practical scenarios. Extensive simulations validate the scheme’s effectiveness, achieving correlation coefficients close to 0, an average NPCR of 99.6090%, and UACI of 33.4707%, thereby demonstrating strong resistance against differential attacks and excellent encryption quality for secure image transmission and storage.
Although the proposed method exhibits robust security and efficiency, further improvements are planned. Future work will focus on enhancing diffusion unpredictability by employing chaotic sequences to generate nonlinear, fluctuating Zigzag paths, thereby surmounting the constraints of fixed patterns. Moreover, the integration of digital signature techniques and key exchange protocols will be explored to further strengthen the security of key generation and transmission, ultimately contributing to a more secure and adaptable encryption framework.
Author Contributions
H.Z.: Conceptualization, Methodology, Validation, Writing—original draft. X.L.: Methodology, Data curation, Validation, Writing—original draft. K.C.: Investigation, Formal analysis, Writing—review and editing. R.T.: Investigation, Funding acquisition, Writing—review and editing. F.Y.: Supervision, Funding acquisition, Writing—review and editing. All authors have read and agreed to the published version of the manuscript.
Funding
This work was sponsored by Natural Science Foundation of Chongqing, China (No. CSTB2022NSCQ–MSX1520) and Jilin Provincial Department of Science and Technology, China (No. 20230201084GX).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
All authors read and agreed to participate in the final manuscript. All authors agreed to publish this paper, if accepted.
Data Availability Statement
The original data presented in the study are openly available in the USC-SIPI image database at https://sipi.usc.edu/database/ (accessed on 9 April 2025).
Conflicts of Interest
Author Rigen Te was employed by the company Chang Guang Satellite Technology Co., Ltd. The remaining authors declare that the research was conducted in the absence of any commercial or financial relationships that could be construed as a potential conflict of interest.
References
- Abdullah, A.M. Advanced encryption standard (AES) algorithm to encrypt and decrypt data. Cryptogr. Netw. Secur. 2017, 16, 11. [Google Scholar]
- Du, S.; Ye, G. IWT and RSA based asymmetric image encryption algorithm. Alex. Eng. J. 2023, 66, 979–991. [Google Scholar] [CrossRef]
- Zhou, W.; Wang, X.; Wang, M.; Li, D. A new combination chaotic system and its application in a new Bit-level image encryption scheme. Opt. Lasers Eng. 2022, 149, 106782. [Google Scholar] [CrossRef]
- Liang, Q.; Zhu, C. A new one-dimensional chaotic map for image encryption scheme based on random DNA coding. Opt. Laser Technol. 2023, 160, 109033. [Google Scholar] [CrossRef]
- Kocak, O.; Erkan, U.; Toktas, A.; Gao, S. PSO-based image encryption scheme using modular integrated logistic exponential map. Expert Syst. Appl. 2024, 237, 121452. [Google Scholar] [CrossRef]
- Wang, P.; Ding, L. Research on Variable Parameter Color Image Encryption Based on Five-Dimensional Tri-Valued Memristor Chaotic System. Entropy 2024, 26, 536. [Google Scholar] [CrossRef]
- Wang, S.; Peng, Q.; Du, B. Chaotic color image encryption based on 4D chaotic maps and DNA sequence. Opt. Laser Technol. 2022, 148, 107753. [Google Scholar] [CrossRef]
- Darani, A.Y.; Yengejeh, Y.K.; Pakmanesh, H.; Navarro, G. Image encryption algorithm based on a new 3D chaotic system using cellular automata. Chaos Solitons Fractals 2024, 179, 114396. [Google Scholar] [CrossRef]
- Wang, X.; Guan, N. 2D sine-logistic-tent-coupling map for image encryption. J. Ambient Intell. Humaniz. Comput. 2023, 14, 13399–13419. [Google Scholar] [CrossRef]
- Chen, K.; Zhang, H.; Yan, F. An adaptive image compression–encryption scheme using 2D logarithm-exponent-squared-sine coupling map. Nonlinear Dyn. 2024, 113, 1827–1856. [Google Scholar] [CrossRef]
- Pak, C.; Jong, C.; Pang, R.; Ri, S.; Kim, J. A new image encryption algorithm using 2D infinite collapse coupling map. Multimed. Tools Appl. 2024, 83, 50619–50643. [Google Scholar] [CrossRef]
- Tang, J.; Lu, M.; Zhang, Z.; Huang, X.; Huang, T.; Wang, J. Novel asymmetrical color image encryption using 2D sine-power coupling map. Nonlinear Dyn. 2024, 112, 11547–11569. [Google Scholar] [CrossRef]
- Du, J.; Zhao, Z.; Li, S.; Lu, B.; Zhang, J. A novel image encryption algorithm based on hyperchaotic system with cross-feedback structure and diffusive DNA coding operations. Nonlinear Dyn. 2024, 112, 12579–12596. [Google Scholar] [CrossRef]
- Zhou, S.; Wei, Y.; Zhang, Y.; Iu, H.H.-C.; Zhang, H. Image encryption algorithm based on the dynamic RNA computing and a new chaotic map. Integration 2025, 101, 102336. [Google Scholar] [CrossRef]
- Zhao, Y.; Shi, Q.; Ding, Q. Cryptanalysis of an Image Encryption Algorithm Using DNA Coding and Chaos. Entropy 2025, 27, 40. [Google Scholar] [CrossRef]
- Yu, J.; Xie, W.; Zhong, Z.; Wang, H. Image encryption algorithm based on hyperchaotic system and a new DNA sequence operation. Chaos Solitons Fractals 2022, 162, 112456. [Google Scholar] [CrossRef]
- Wang, Q.; Zhang, X.; Zhao, X. Color image encryption algorithm based on novel 2D hyper-chaotic system and DNA crossover and mutation. Nonlinear Dyn. 2023, 111, 22679–22705. [Google Scholar] [CrossRef]
- Kumar, A.; Dua, M. A novel exponent-sine-cosine chaos map-based multiple-image encryption technique. Multimed. Syst. 2024, 30, 141. [Google Scholar] [CrossRef]
- Zhou, L.; Lin, Z.; Tan, F.; Chen, P. Multi-image encryption based on new two-dimensional hyperchaotic model via cyclic shift coding of deoxyribonucleic acid. Expert Syst. Appl. 2025, 281, 127475. [Google Scholar] [CrossRef]
- Wang, S.; Wang, C.; Xu, C. An image encryption algorithm based on a hidden attractor chaos system and the Knuth–Durstenfeld algorithm. Opt. Lasers Eng. 2020, 128, 105995. [Google Scholar] [CrossRef]
- Wang, X.; Du, X. Chaotic image encryption method based on improved zigzag permutation and DNA rules. Multimed. Tools Appl. 2022, 81, 43777–43803. [Google Scholar] [CrossRef]
- Watson, J.D.; Crick, F.H. Molecular structure of nucleic acids: A structure for deoxyribose nucleic acid. Nature 1953, 171, 737–738. [Google Scholar] [CrossRef] [PubMed]
- Cao, W.; Mao, Y.; Zhou, Y. Designing a 2D infinite collapse map for image encryption. Signal Process. 2020, 171, 107457. [Google Scholar] [CrossRef]
- Teng, L.; Wang, X.; Xian, Y. Image encryption algorithm based on a 2D-CLSS hyperchaotic map using simultaneous permutation and diffusion. Inf. Sci. 2022, 605, 71–85. [Google Scholar] [CrossRef]
- Teng, L.; Wang, X.; Yang, F.; Xian, Y. Color image encryption based on cross 2D hyperchaotic map using combined cycle shift scrambling and selecting diffusion. Nonlinear Dyn. 2021, 105, 1859–1876. [Google Scholar] [CrossRef]
- Gao, X. Image encryption algorithm based on 2D hyperchaotic map. Opt. Laser Technol. 2021, 142, 107252. [Google Scholar] [CrossRef]
- Hua, Z.; Zhu, Z.; Chen, Y.; Li, Y. Color image encryption using orthogonal Latin squares and a new 2D chaotic system. Nonlinear Dyn. 2021, 104, 4505–4522. [Google Scholar] [CrossRef]
- Hua, Z.; Zhou, Y.; Huang, H. Cosine-transform-based chaotic system for image encryption. Inf. Sci. 2019, 480, 403–419. [Google Scholar] [CrossRef]
- Grassberger, P.; Procaccia, I. Estimation of the Kolmogorov entropy from a chaotic signal. Phys. Rev. A 1983, 28, 2591. [Google Scholar] [CrossRef]
- Nardo, L.G.; Nepomuceno, E.G.; Arias-Garcia, J.; Butusov, D.N. Image encryption using finite-precision error. Chaos Solitons Fractals 2019, 123, 69–78. [Google Scholar] [CrossRef]
- Lai, Q.; Hu, G.; Erkan, U.; Toktas, A. A novel pixel-split image encryption scheme based on 2D Salomon map. Expert Syst. Appl. 2023, 213, 118845. [Google Scholar] [CrossRef]
- Wang, X.; Su, Y.; Xu, M.; Zhang, H.; Zhang, Y. A new image encryption algorithm based on Latin square matrix. Nonlinear Dyn. 2022, 107, 1277–1293. [Google Scholar] [CrossRef]
- Parida, P.; Pradhan, C.; Alzubi, J.A.; Javadpour, A.; Gheisari, M.; Liu, Y.; Lee, C.C. Elliptic curve cryptographic image encryption using Henon map and Hopfield chaotic neural network. Multimed. Tools Appl. 2023, 82, 33637–33662. [Google Scholar] [CrossRef]
- Zang, H.; Tai, M.; Wei, X. Image encryption schemes based on a class of uniformly distributed chaotic systems. Mathematics 2022, 10, 1027. [Google Scholar] [CrossRef]
- Wu, Y.; Noonan, J.P.; Agaian, S. NPCR and UACI randomness tests for image encryption. Cyber J. Multidiscip. J. Sci. Technol. J. Sel. Areas Telecommun. (JSAT) 2011, 1, 31–38. [Google Scholar]
- Du, L.; Teng, L.; Liu, H.; Lu, H. Multiple face images encryption based on a new non-adjacent dynamic coupled mapping lattice. Expert Syst. Appl. 2024, 238, 121728. [Google Scholar] [CrossRef]
- Khan, S.; Peng, H. A secure and adaptive block-based image encryption: A novel high-speed approach. Nonlinear Dyn. 2024, 112, 16445–16473. [Google Scholar] [CrossRef]
- Alvarez, G.; Li, S. Some basic cryptographic requirements for chaos-based cryptosystems. Int. J. Bifurc. Chaos 2006, 16, 2129–2151. [Google Scholar] [CrossRef]
- Wei, D.; Jiang, M.; Deng, Y. A secure image encryption algorithm based on hyper-chaotic and bit-level permutation. Expert Syst. Appl. 2023, 213, 119074. [Google Scholar] [CrossRef]
- Hua, Z.; Jin, F.; Xu, B.; Huang, H. 2D Logistic-Sine-coupling map for image encryption. Signal Process. 2018, 149, 148–161. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).