Entropy of the Quantum–Classical Interface: A Potential Metric for Security
Abstract
1. Introduction
2. Hybrid Quantum–Classical Dynamics
3. Hybrid Equations of Motion
4. Preliminaries
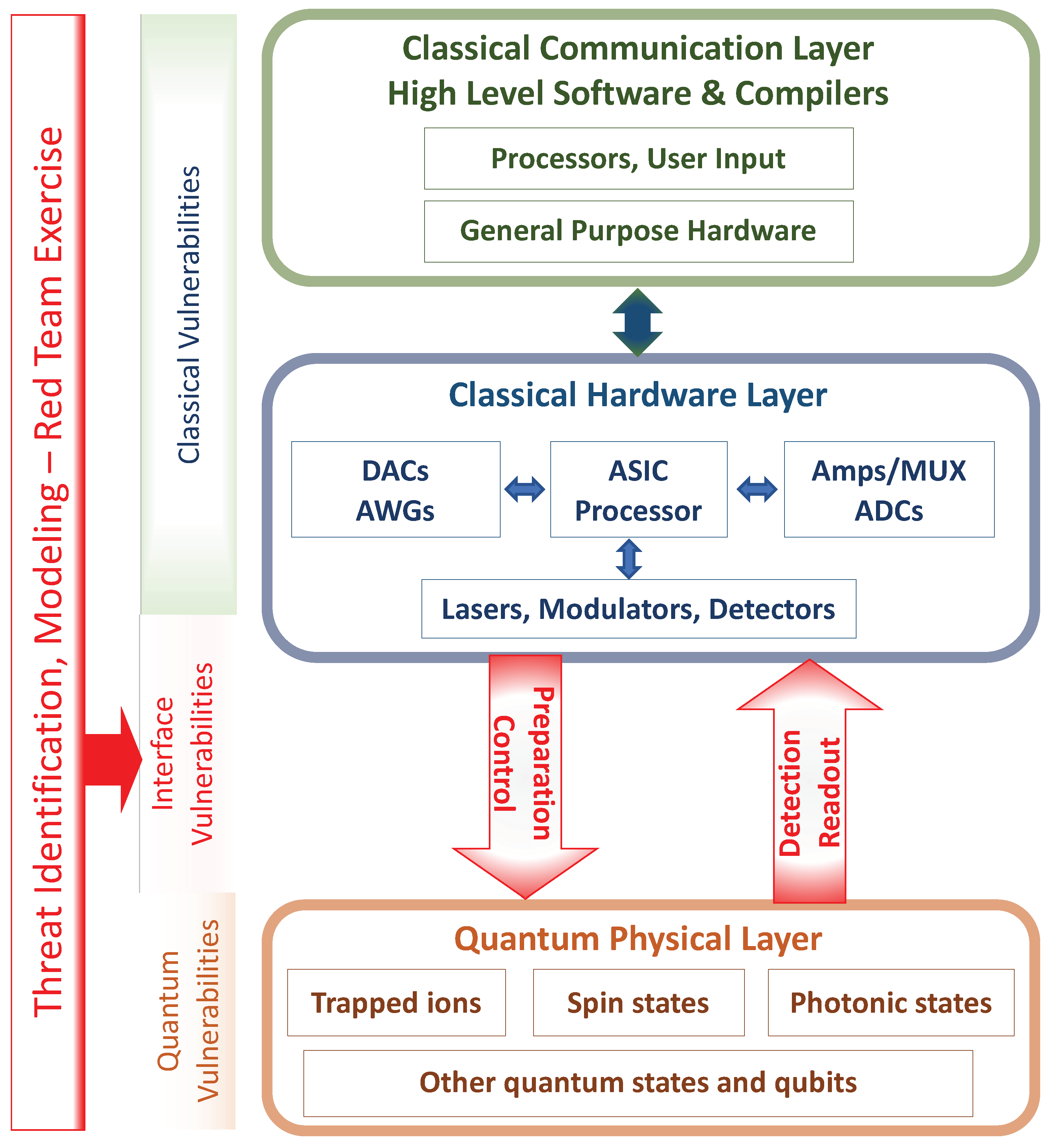
4.1. Formalization of an Interface
4.2. Interface from a Hamiltonian
4.3. Classical Interfaces and Security
4.4. Quantum–Classical Interface (QCI)
4.5. A QCI Example: Classical and Quantum Langevin Equations
5. Entropic Approach to QCI Security
5.1. Classical Entropy
5.2. Quantum Entropy
5.3. QCI Entropy
5.4. Information Flow at QCI
5.4.1. Quantum-to-Classical ()
5.4.2. Classical-to-Quantum ()
5.4.3. Interplay at QCI
5.5. Inferring Information Flow Using Entropy at the QCI
5.6. Quantum Phenomena and Their Influence on QCI Entropy
6. Other Metrics
7. Criteria for QCI Security
- Information leakage;
- Anomalies in mutual information at the QCI, indicating unintended data transfer;
- Consistency in entropic dynamics;
- Assessments of relative entropy between expected and observed values (states) reveal unexpected perturbations, suggesting possible data injection or tampering;
- Control entropy decreases via data processing.
Classical Security Approaches
- Threat modeling: Identify, rank, and describe cyber threats by analyzing relationships between business or organizational risk, threat actor models, and system weaknesses [40]. This process provides a high-level context for the security needs, location, and disposition of QCIs.
- Static/formal analysis: Locates potential vulnerabilities by programmatically analyzing system specifications or the source code [41]. This general technique could be modified to identify high-sensitivity QCIs and describe their expected entropy dynamics.
- Digital twin: Compare measurements of the QIS with a system-state-aware computational model. A divergence in QCI entropy can be compared in real-time to other system variables, allowing for rapid fault diagnosis.
- Integrated countermeasure: Analyze and rewrite the quantum program to create QCIs where entropy dynamics are easier to profile or measure.
8. Discussions
9. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| ORNL | Oak Ridge National Laboratory |
| QCI | Quantum–classical interface |
References
- Brizuela, D.; Uría, S.F. Hybrid classical-quantum systems in terms of moments. Phys. Rev. A 2024, 109, 032209. [Google Scholar] [CrossRef]
- Passian, A.; Dawson, J.; Prowell, S.; Grice, W. Simulating quantum-classical interfaces via the Lindblad master equation. Phys. Rev. A 2025, 111, 042626. [Google Scholar] [CrossRef]
- Wiseman, H.M.; Milburn, G.J. Quantum Measurement and Control; Cambridge University Press: Cambridge, UK, 2009. [Google Scholar] [CrossRef]
- Cong, S. Control of Quantum Systems: Theory and Methods; John Wiley & Sons: Hoboken, NJ, USA, 2014. [Google Scholar] [CrossRef]
- Elze, H.T. Quantum-classical hybrid dynamics—A summary. In Proceedings of the Journal of Physics: Conference Series; IOP Publishing: Bristol, UK, 2013; Volume 442, p. 012007. [Google Scholar] [CrossRef]
- Dammeier, L.; Werner, R.F. Quantum-Classical Hybrid Systems and their Quasifree Transformations. Quantum 2023, 7, 1068. [Google Scholar] [CrossRef]
- Koopman, B.O.; von Neumann, J. Dynamical systems of continuous spectra. Proc. Natl. Acad. Sci. USA 1931, 17, 315–318. [Google Scholar] [CrossRef] [PubMed]
- Lambert, R.; Makri, N. Quantum-classical path integral: I. Classical memory and weak quantum nonlocality. J. Chem. Phys. 2012, 137, 22A552. [Google Scholar] [CrossRef]
- Ananth, N. Path Integrals for Nonadiabatic Dynamics: Multistate Ring Polymer Molecular Dynamics. Annu. Rev. Phys. Chem. 2022, 73, 299–322. [Google Scholar] [CrossRef]
- Tully, J.C. Molecular dynamics with electronic transitions. J. Chem. Phys. 1990, 93, 1061–1071. [Google Scholar] [CrossRef]
- Tully, J.C. Perspective: Nonadiabatic dynamics theory. J. Chem. Phys. 2012, 137, 22A301. [Google Scholar] [CrossRef]
- Prezhdo, O.V.; Kisil, V.V. Mixing quantum and classical mechanics. Phys. Rev. A 1997, 56, 162–175. [Google Scholar] [CrossRef]
- Kapral, R.; Ciccotti, G. Mixed quantum-classical dynamics. J. Chem. Phys. 1999, 110, 8919–8929. [Google Scholar] [CrossRef]
- Kapral, R. Progress in the theory of mixed quantum-classical dynamics. Annu. Rev. Phys. Chem. 2006, 57, 129–157. [Google Scholar] [CrossRef] [PubMed]
- Fratino, L.; Lampo, A.; Elze, H.T. Entanglement dynamics in a quantum—Classical hybrid of two q-bits and one oscillator. Phys. Scr. 2014, T163, 014005. [Google Scholar] [CrossRef]
- Sergi, A.; Lamberto, D.; Migliore, A.; Messina, A. Quantum–Classical Hybrid Systems and Ehrenfest’s Theorem. Entropy 2023, 25, 602. [Google Scholar] [CrossRef]
- Crespo-Otero, R.; Barbatti, M. Recent Advances and Perspectives on Nonadiabatic Mixed Quantum–Classical Dynamics. Chem. Rev. 2018, 118, 7026–7068. [Google Scholar] [CrossRef] [PubMed]
- Goldsmith, A. Wireless Communications; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar] [CrossRef]
- Stallings, W. Cryptopgraphy and Network Security: Principles and Practice, 4th ed.; Pearson: London, UK, 2016; Available online: https://www.pearson.com/en-us/subject-catalog/p/cryptography-and-network-security-principles-and-practice/P200000003477/9780135764213 (accessed on 8 February 2025).
- Momot, F.; Bratus, S.; Hallberg, S.M.; Patterson, M.L. The Seven Turrets of Babel: A Taxonomy of LangSec Errors and How to Expunge Them. In Proceedings of the 2016 IEEE Cybersecurity Development (SecDev), Boston, MA, USA, 3–4 November 2016; pp. 45–52. [Google Scholar] [CrossRef]
- Anderson, R.J. Security Engineering: A Guide to Building Dependable Distributed Systems; John Wiley & Sons: Hoboken, NJ, USA, 2010. [Google Scholar] [CrossRef]
- Milburn, G. Decoherence and the conditions for the classical control of quantum systems. Philos. Trans. R. Soc. A Math. Phys. Eng. Sci. 2012, 370, 4469–4486. [Google Scholar] [CrossRef]
- Coffey, W.T.; Kalmykov, Y.P.; Waldron, J.T. The Langevin Equation: With Applications to Stochastic Problems in Physics, Chemistry and Electrical Engineering; World Scientific: Singapore, 2004. [Google Scholar] [CrossRef]
- De Oliveira, M.J. Quantum Langevin equation. J. Stat. Mech. Theory Exp. 2020, 2020, 023106. [Google Scholar] [CrossRef]
- Gardiner, C.; Zoller, P. Quantum Noise: A Handbook of Markovian and Non-Markovian Quantum Stochastic Methods with Applications to Quantum Optics; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2004; Available online: https://link.springer.com/book/9783540223016 (accessed on 8 February 2025).
- Walls, D.; Milburn, G.J. Quantum Information. In Quantum Optics; Springer: Berlin/Heidelberg, Germany, 2008; pp. 307–346. [Google Scholar] [CrossRef]
- Carmichael, H. An Open Systems Approach to Quantum Optics: Lectures Presented at the Université Libre de Bruxelles, October 28 to November 4, 1991; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2009; Volume 18. [Google Scholar] [CrossRef]
- Lee, C.; Sohn, I.; Lee, W. Eavesdropping detection in BB84 quantum key distribution protocols. IEEE Trans. Netw. Serv. Manag. 2022, 19, 2689–2701. [Google Scholar] [CrossRef]
- Wilde, M. Quantum Information Theory; Cambridge University Press: Cambridge, UK, 2013; Volume 1. [Google Scholar] [CrossRef]
- Petersen, I. Control of Quantum Systems. In Encyclopedia of Systems and Control; Springer: London, UK, 2013; pp. 1–10. [Google Scholar] [CrossRef]
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum Cryptography. Rev. Mod. Phys. 2002, 74, 145–195. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.L.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in Quantum Cryptography. Adv. Opt. Photonics 2020, 12, 1012–1236. [Google Scholar] [CrossRef]
- Xu, F.; Qi, B.; Lo, H.K. Experimental Demonstration of Phase-Remapping Attack in a Practical Quantum Key Distribution System. New J. Phys. 2020, 12, 113026. [Google Scholar] [CrossRef]
- Lo, H.K.; Curty, M.; Tamaki, K. Secure Quantum Key Distribution. Nat. Photonics 2014, 8, 595–604. [Google Scholar] [CrossRef]
- Steven, M.K. Fundamentals of Statistical Signal Processing, Volume 1: Estimation Theory; PTR Prentice-Hall: Englewood Cliffs, NJ, USA, 1993; Volume 10, p. 148. Available online: https://www.pearson.com/en-us/subject-catalog/p/fundamentals-of-statistical-processing-estimation-theory-volume-1/P200000009271/9780133457117?srsltid=AfmBOooCqGCXfEcX9V9e80-7ys_yLjY4XEpNcR03OYSXdl6lEhgwdwkA (accessed on 8 February 2025).
- Song, Z.; Chen, Y.; Sastry, C.R.; Tas, N.C. Optimal Observation for Cyber-Physical Systems: A Fisher-Information-Matrix-Based Approach; Springer Science & Business Media: Berlin/Heidelberg, Germany, 2009. [Google Scholar] [CrossRef]
- Hall, M.J. Quantum properties of classical Fisher information. Phys. Rev. A 2000, 62, 012107. [Google Scholar] [CrossRef]
- Petz, D.; Ghinea, C. Introduction to quantum Fisher information. In Quantum Probability and Related Topics; World Scientific: Singapore, 2011; pp. 261–281. [Google Scholar] [CrossRef]
- Paris, M.G. Quantum estimation for quantum technology. Int. J. Quantum Inf. 2009, 7, 125–137. [Google Scholar] [CrossRef]
- Shostack, S. The Ultimate Beginner’s Guide to Threat Modeling. 2023. Available online: https://shostack.org/resources/threat-modeling.html (accessed on 7 April 2025).
- Chess, B.; McGraw, G. Static analysis for security. IEEE Secur. Priv. 2004, 2, 76–79. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chehade, S.; Dawson, J.A.; Prowell, S.; Passian, A. Entropy of the Quantum–Classical Interface: A Potential Metric for Security. Entropy 2025, 27, 517. https://doi.org/10.3390/e27050517
Chehade S, Dawson JA, Prowell S, Passian A. Entropy of the Quantum–Classical Interface: A Potential Metric for Security. Entropy. 2025; 27(5):517. https://doi.org/10.3390/e27050517
Chicago/Turabian StyleChehade, Sarah, Joel A. Dawson, Stacy Prowell, and Ali Passian. 2025. "Entropy of the Quantum–Classical Interface: A Potential Metric for Security" Entropy 27, no. 5: 517. https://doi.org/10.3390/e27050517
APA StyleChehade, S., Dawson, J. A., Prowell, S., & Passian, A. (2025). Entropy of the Quantum–Classical Interface: A Potential Metric for Security. Entropy, 27(5), 517. https://doi.org/10.3390/e27050517






