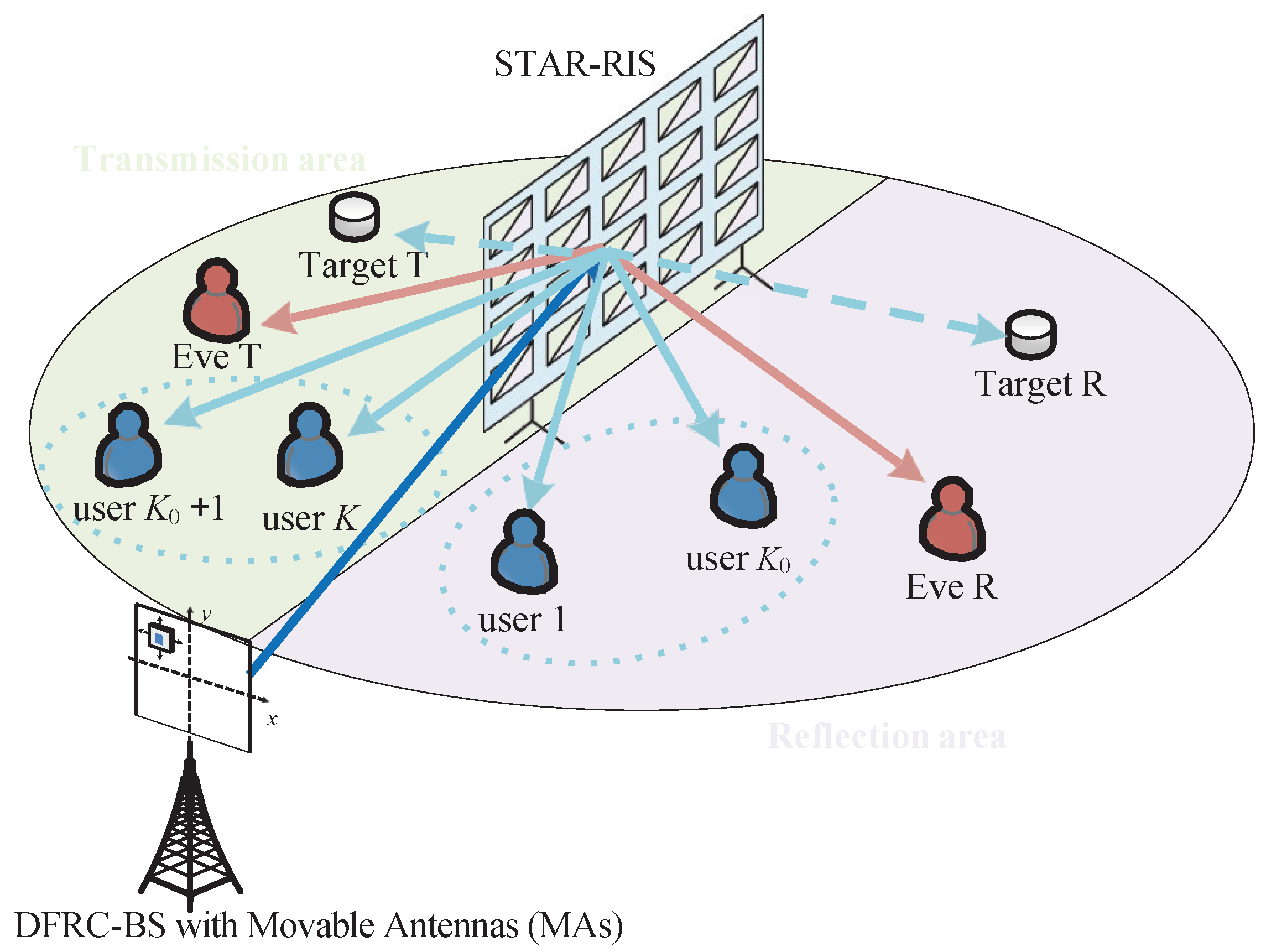
1. Introduction
The evolution towards sixth-generation (6G) wireless systems is driven by a vision that extends far beyond incremental increases in data rates. 6G wireless systems may introduce a new era of providing multiple services for users, including holographic communications, augmented reality, and the Internet of Everything. These applications require ultra-reliable, low-latency communication and the real-time awareness of the physical environment of the users. The multiple requirements accelerate the development of the integrated sensing and communications (ISAC) as a fundamental 6G function. ISAC may realize improvements in spectral and energy efficiency, as well as reduced hardware and software costs, by jointly designing the communication and sensing functionalities with shared hardware and spectrum resources. The smooth transition to ISAC in the 6G wireless system is a natural need for resource optimization from an engineering perspective to fuse the digital and physical environments. In certain scenarios, such as industrial automation and autonomous driving, the 6G wireless system must act as a sensing and communication center to serve users by enhancing both functionalities.
Despite the huge potential advantage of the deployment of the ISAC systems, engineering problems must be considered. Firstly, the requirements for higher data rates and sensing accuracy push wireless systems to operate in higher frequency bands, where signals may be blocked, leading to performance degradation. Secondly, the multiple functionalities of the ISAC signals may pose a critical security challenge. Signals transmitted to detect a specific target may be intercepted by potential eavesdroppers, posing a threat to data security and personal privacy. This enhances the importance of Physical Layer Security (PLS), which aims to transmit signals securely by integrating the wireless channels, especially for a robust ISAC wireless communications system.
To address these security challenges, several research papers have focused on the beamforming design. A common objective of the research is to maximize the secrecy rate under multiple constraints, such as the quality of service for communication and sensing. Optimization techniques like semidefinite relaxation (SDR) and successive convex approximation (SCA) are often used to handle the non-convexity of the optimization problem [
1]. Researchers have integrated multiple access schemes with the proposed secure beamforming ISAC frameworks, such as Non-Orthogonal Multiple Access (NOMA) [
2] and Rate-Splitting Multiple Access (RSMA) [
3]. The mobile scenarios have been considered in the optimization problems, such as systems with Autonomous Aerial Vehicles (AAVs), where trajectory planning is jointly optimized with beamforming to maximize the average secrecy rate [
4]. Moreover, some research papers have focused on sensing metrics like the Cramér–Rao Bound (CRB) with imperfect channel state information (CSI) to ensure the security performance [
5]. Recently, Reconfigurable Intelligent Surfaces (RISs) have been introduced into ISAC systems to control the propagation environment and address blockages, thereby enhancing PLS performance by strengthening legitimate links and suppressing eavesdropping channels [
6]. Introducing more degrees of freedom and intelligent propagation control is a key step to mitigate the physical blockages and security threats.
Reconfigurable Intelligent Surfaces (RISs) can reflect incident signals to control the propagation environment to combat physical signal blockages. This function is limited in scenarios where users and eavesdroppers are present in both the transmission and reflection areas. The Simultaneously Transmitting and Reflecting RIS (STAR-RIS) is a key breakthrough in this technology, which can provide full-space coverage [
7]. This capability is beneficial for system security and flexibility.
Recent studies have demonstrated the superiority of STAR-RIS in PLS performance across different scenarios. The STAR-RIS can significantly improve the secrecy rate in ISAC networks by controlling signals in the full-space [
8,
9]. Its effectiveness has been confirmed in the following research papers, enhancing security in multi-user NOMA systems [
10] and enabling robust transmissions with uncertain eavesdropper locations and imperfect channel state information [
11,
12]. Furthermore, STAR-RIS can be used for joint secure and covert communications; the full-space control is leveraged to transmit confidential data while hiding the communication itself [
13,
14,
15]. The active STAR-RIS has been studied to further amplify signals to mitigate severe path loss, providing security enhancement against jamming and eavesdropping [
16]. The growing interest in related research papers has demonstrated that the full-space control capability of the STAR-RIS fulfills the need for ISAC systems. The communication users, sensing targets, and potential eavesdroppers may be distributed randomly in the full space. The STAR-RIS can provide flexibility and security at the system design level.
Traditional wireless systems have Fixed-Position Antenna (FPA) arrays that remain in static positions. The recently proposed concept of Movable Antennas (MAs) introduces a new degree of freedom by allowing antenna positions to be dynamically and continuously adjusted within a certain region [
17]. This movement provides spatial diversity, enabling the wireless communication system to intelligently reconfigure the wireless channel. An MA-aided system can seek positions that maximize the desired signal and minimize interference, thereby enhancing performance in communication and sensing. This function provides a powerful degree of freedom for system optimization.
The potential benefits of MAs have been studied in different scenarios. There is a growing interest in its application to ISAC and PLS. MAs have been shown to improve the trade-off between sensing and communication performance in the ISAC area. MA-aided ISAC systems can enhance the sensing and communication rate region [
18], minimize transmit power [
19], and improve beam pattern gains [
20] by jointly optimizing antenna positions with transmit and receive beamforming. This improvement has been validated in multiple scenarios, including bistatic systems for airborne vehicles [
21], full-duplex monostatic systems with self-interference mitigation [
22], and even in the near-field communication scenario [
23,
24]. The integration of MAs with other technologies is also important. For instance, the integration of MAs with RIS has been shown to further boost ISAC performance in dead zones [
25].
Recently, MAs have been extended to enhance the PLS performance of the wireless systems. Several research papers have shown that MAs can increase the secrecy rate by jointly optimizing the beamforming and antenna positions, even with imperfect eavesdropper channel state information [
26,
27]. This function has been introduced in multiple security-related scenarios, including covert communications [
28] and secure simultaneous wireless information and power transfer (SWIPT) [
29]. Several works have already combined these promising technologies to investigate secure beamforming design in MA-aided ISAC systems. Another paper has used deep reinforcement learning to handle complex scenarios [
30]. These works validate the fact that MAs are an important tool for enhancing the security performance of the 6G wireless system by providing additional spatial degrees of freedom.
While the ISAC, STAR-RIS, and MAs have been investigated individually. The integration of these technologies into a secure framework remains a critical research direction. The existing papers lack a comprehensive design that jointly leverages the full-space coverage of STAR-RIS and the additional spatial DoFs of MAs to address eavesdropping in a multi-user ISAC system.
The primary motivation for this work is to fill this gap. However, the joint design presents a huge optimization challenge. The optimization problem needs to optimize the BS beamforming, the passive beamforming at the STAR-RIS, and the position variables of the MAs. This optimization problem is highly non-convex, with multiple constraints, including rank-one constraints on the covariance matrices, unit-modulus constraints on the STAR-RIS coefficients, and non-convex inter-antenna distance constraints for the MAs. This is intractable for the standard convex optimization solvers due to the coupled variables in the optimization problem. There is a need to develop a novel, computationally efficient algorithmic solution to the optimization problem.
This paper demonstrates a secure MA-aided STAR-RIS ISAC system. The main contributions are summarized as follows:
We propose a novel secure ISAC framework that integrates MAs at the BS with a STAR-RIS. This architecture combines the spatial degree of freedom of MAs with the STAR-RIS, which can enhance the communication security and sensing performance in the meantime.
We formulate an optimization problem that maximizes the max-min secrecy rate to ensure fairness. This framework optimizes the BS active beamforming, STAR-RIS passive beamforming, and MA positions iteratively. And the optimization problem is subject to constraints on sensing SNR, user QoS, total transmit power, and the physical limitations of the hardware.
We develop an efficient algorithm based on the Alternating Optimization (AO) framework to solve the highly non-convex optimization problem. We decompose the optimization problem into several subproblems by leveraging SCA and SDR techniques. The decomposition provides a high-quality solution efficiently.
We provided numerical results that validated the effectiveness of the proposed MA-aided STAR-RIS scheme. The results show visible gains in secrecy rate compared to other benchmark schemes, which demonstrates the benefits of the integrated design.
The remainder of this paper is organized as follows. In
Section 2, we present the system model for the movable antenna and STAR-RIS-aided ISAC system. And we formulate the optimization problem for maximizing the minimum secrecy rate. In
Section 3, we propose an efficient algorithm based on the alternating optimization (AO) framework to solve the formulated non-convex problem by decomposing it into three subproblems.
Section 4 provides extensive simulation results to validate the effectiveness and superiority of our proposed scheme. Finally,
Section 5 concludes the paper.
Notations: Matrices and vectors are denoted by bold uppercase and lowercase letters, respectively.
,
, and
denote the transpose, conjugate, and conjugate transpose, respectively.
denotes the statistical expectation.
denotes the space of
complex matrices.
denotes a diagonal matrix with the elements of the vector
on its main diagonal.
and
denote the trace and rank of a matrix
, respectively.
indicates that
is a positive semidefinite matrix. The description of key symbols is summarized in
Table 1.
3. Proposed Solution
The formulated problem (11) is highly intractable. We propose an efficient iterative algorithm based on the alternating optimization (AO) framework. The core idea is to divide the optimization problem into three sub-problems—active beamforming matrices , passive beamforming vectors , and MA positions . Then optimize one problem at a time. This process is repeated until convergence. The overall AO algorithm consists of three main blocks that are solved iteratively. Each block (Algorithms 1–3) is solved using an SCA-based method, which involves solving a convex program at each step. This ensures that the objective of each subproblem is non-decreasing. As each step of the AO framework improves (or at least does not degrade) the overall objective function, the proposed Algorithm 4 is guaranteed to converge monotonically to a locally optimal solution.
3.1. Active Beamforming Optimization
With fixed passive beamforming and MA positions, we first apply SDR by dropping the rank-one constraints (
11f). The subproblem for optimizing the active beamforming covariance matrices, denoted by
, is as follows:
This problem is still non-convex due to the max-min objective function. We can rewrite it by introducing an epigraph variable
as follows:
The main challenges are the non-concave secrecy rate constraint (
13b) and the rank-one constraint. We propose an iterative algorithm based on the SCA framework to deal with this.
We approximate the function
with a concave lower bound at each iteration of the SCA algorithm. Then let
be the set of covariance matrices obtained at the
i-the SCA iteration. For the
-th iteration, the constraint (
13b) is replaced by its first-order Taylor expansion:
The gradient
can be derived. This transforms the constraint into a linear constraint.
Second, simply dropping the rank-one constraint often yields a solution with a rank greater than one. To address this, we employ an iteratively reweighted penalty method to encourage rank-one solutions. This method is based on the property that a positive semidefinite matrix
is rank-one if and only if
, where
is the maximum eigenvalue of
. We add a penalty term to the objective function to minimize this difference. Since
is a convex function, we approximate it with its affine lower bound obtained from the first-order Taylor expansion at
:
where
is the eigenvector corresponding to the maximum eigenvalue of
. Let us denote the right-hand side of the inequality as
.
By combining the SCA approximation for the secrecy rate and the penalty method for the rank-one constraint, the active beamforming optimization subproblem at each iteration is formulated as the following standard SDP:
Here,
and
are penalty factors that are gradually increased in each iteration to progressively enforce the rank-one property. This SDP can be efficiently solved using standard convex optimization solvers like CVX. If the resulting matrices are not exactly rank-one, a rank-one solution can be constructed from the dominant eigenvector, which is a standard procedure for this method.
The overall iterative procedure for solving the active beamforming subproblem (12) is summarized in Algorithm 1. In each iteration, we solve the convex SDP problem (16) to obtain an updated set of covariance matrices. The penalty factors are progressively increased to ensure that the resulting solution converges to a rank-one solution. After the algorithm converges, a standard rank-one approximation step is performed if the resulting matrices are not of perfect rank one.
| Algorithm 1 SCA-based Algorithm for Active Beamforming Optimization |
- 1:
Input: Fixed passive beamforming and MA positions . - 2:
Initialize: Feasible covariance matrices , SCA iteration counter , penalty factors , and update parameter . - 3:
repeat - 4:
Obtain the concave lower bound of for all by applying the first-order Taylor expansion at . - 5:
Find the principal eigenvectors of and of to construct the affine lower bound of the maximum eigenvalues and . - 6:
Solve the convex SDP subproblem in (16) to obtain the solution . - 7:
Update the covariance matrices: . - 8:
Update penalty factors: , . - 9:
. - 10:
until the objective function converges or the maximum number of iterations is reached. - 11:
Output: The optimized rank-one covariance matrices , obtained by extracting the principal eigenvectors from the final matrices in .
|
3.2. Passive Beamforming Optimization
In this subsection, with the active beamforming matrices
and MA positions
fixed from the previous steps, we focus on optimizing the passive beamforming at the STAR-RIS. This involves finding the optimal reflection and transmission coefficient matrices, denoted by
and
. The optimization subproblem can be formulated as follows:
where we have defined
and
. This problem is non-convex due to the coupled variables in the secrecy rate expression (
17b) and the non-convex unit-modulus and rank-one constraints in (
17d) and (
17e). To tackle this, we employ a combination of Semidefinite Relaxation (SDR) and Successive Convex Approximation (SCA), augmented by a penalty method to handle the rank-one constraint.
First, we apply SDR by dropping the non-convex rank-one constraints (
17e), which relaxes
and
to be positive semidefinite matrices, i.e.,
and
. The unit-modulus constraint (
17d) is equivalent to constraining the diagonal elements of the sum of these matrices, i.e.,
.
The secrecy rate constraint (
17b) remains non-convex. We can rewrite the achievable rates for user
k and the eavesdropper as functions of
and
. For instance, for a transmission user
:
where the matrices
,
, and
are derived from the channel matrices and active beamformers. Similar expressions can be obtained for reflection users. The non-convexity arises from the difference of two concave functions. We apply SCA by computing the first-order Taylor expansion of the concave parts of the rate expressions. For example, for user
k, we obtain the convex lower bound
for
and a convex upper bound
for
around the feasible points
and
from the
i-th iteration.
Even after applying SDR and SCA, the rank-one constraints are still violated. To enforce the rank-one property, we introduce a penalty term into the objective function. The rank of a semidefinite matrix
is one if and only if
, where
is the maximum eigenvalue. Since
is a convex but non-smooth function, we approximate it by its upper bound
, where
is the eigenvector corresponding to the maximum eigenvalue of
in the previous iteration. By linearizing this approximation, we construct a penalty term that is concave with respect to
. This leads to the penalized objective function for the
-th SCA iteration:
where
and
are penalty factors that are gradually increased with each iteration (i.e.,
with
). The terms
and
are the first-order approximations of the maximum eigenvalues of
and
at the current iterate, given by the following:
where
and
are the principal eigenvectors of
and
, respectively.
By integrating the SCA approximations and the penalty terms, the problem at each iteration becomes a standard semidefinite program (SDP), which can be efficiently solved using convex optimization tools like CVX.
Once the algorithm converges, if the resulting matrices and are not perfectly rank-one, we use Gaussian randomization or simply extract the principal eigenvector to construct a high-quality rank-one approximate solution. We apply the eigenvector extraction method: , where is the corresponding eigenvector.
The overall procedure for solving the passive beamforming subproblem (P3) is summarized in Algorithm 2. We employ an iterative SCA-based approach, where in each step, a convex SDP is solved. The penalty terms are progressively increased to ensure the eventual recovery of rank-one solutions.
| Algorithm 2 SCA-based Algorithm for Passive Beamforming Optimization |
- 1:
Input: Fixed active beamforming and MA positions . - 2:
Initialize: Feasible matrices , SCA iteration counter , penalty factors , and update parameter . - 3:
repeat - 4:
Compute the first-order Taylor approximations for the secrecy rate constraints at the current point . - 5:
Find the principal eigenvectors of and to update the penalty terms for promoting rank-one solutions. - 6:
Solve the convex SDP subproblem formulated in Section 3.2 to obtain the solution . - 7:
Update the matrices: , . - 8:
Update penalty factors: , . - 9:
. - 10:
until the objective function converges or the maximum number of iterations is reached. - 11:
Output: The optimized rank-one vectors , recovered from the principal eigenvectors of the final matrices.
|
3.3. MA Position Optimization
With the active and passive beamforming matrices fixed, the subproblem of optimizing the MA positions
remains. This is the most challenging part due to the highly non-linear and non-convex dependency of the channel matrices on
via complex exponential functions. The subproblem can be formulated as follows:
Directly solving problem (23) with respect to the entire matrix
is computationally prohibitive.
Instead, we propose an efficient algorithm that combines the block coordinate descent (BCD) and successive convex approximation (SCA) techniques. Specifically, we optimize the position of one MA at a time, while keeping the positions of the other MAs fixed. This process is repeated for all MAs until convergence is achieved.
Let’s focus on optimizing the position of the m-th MA, , with the positions of other antennas being fixed. Let be the MA positions obtained at the i-th iteration. The subproblem for is then solved using the SCA method by replacing the non-convex objective and constraints with their first-order Taylor approximations around the current point .
3.3.1. Approximation of Objective and Constraints
By introducing an epigraph variable
, the objective becomes maximizing
subject to
for all
. We linearize the secrecy rate function at
:
The gradient
can be computed using the chain rule, as detailed in
Section 3.3.1 of the original paper. The key lies in deriving the gradient of the channel matrix
with respect to
.
Similarly, the non-convex SINR/SNR constraints are replaced by their linear approximations. For instance, the QoS constraint
is rewritten as
and then approximated as follows:
The gradient
can be derived straightforwardly. The sensing constraint
is handled in the same manner.
The inter-antenna distance constraint (
11i),
for
, is non-convex as it lower-bounds a convex function. We can obtain a convex inner approximation by applying the first-order Taylor expansion to the convex function
at the point
:
This formulation provides a linear and thus convex constraint for the optimization problem.
3.3.2. The Convex Subproblem with Trust Region
By applying the SCA steps, we can formulate a convex program.
However, the first-order approximations are accurate only within a small neighborhood of the expansion point
. To ensure the validity of the approximations and improve the convergence stability of the SCA algorithm, we introduce a trust region constraint that limits the maximum displacement of the MA in each iteration:
where
is the trust region radius, which serves as a step-size control parameter.
Finally, by integrating the BCD framework with the SCA method and the trust region constraint, the subproblem to find the updated position
becomes the following convex program, which can be solved efficiently:
The overall procedure for solving the passive beamforming subproblem (P3) is summarized in Algorithm 3. We employ an iterative SCA-based approach, where in each step, a convex SDP is solved. The penalty terms are progressively increased to ensure the eventual recovery of rank-one solutions.
| Algorithm 3 BCD-SCA Algorithm for MA Position Optimization |
- 1:
Input: Fixed active beamforming , passive beamforming . - 2:
Initialize: MA positions , BCD iteration counter . - 3:
while objective function has not converged do - 4:
. - 5:
for do - 6:
Initialize and SCA counter . - 7:
repeat - 8:
Solve the convex subproblem in (28) at point to obtain . - 9:
. - 10:
until . - 11:
. - 12:
end for - 13:
. - 14:
. - 15:
end while - 16:
Output: The optimized MA positions .
|
The overall procedure for solving the problem (11) is summarized in Algorithm 4. We employ an AO framework that iteratively solves three subproblems: active beamforming optimization, passive beamforming optimization, and MA position optimization, until the objective function value converges.
| Algorithm 4 Proposed AO-based Algorithm for Problem (11) |
- 1:
Initialize: Feasible active beamforming matrices , passive beamforming vectors , and MA positions . Set AO iteration counter . - 2:
repeat - 3:
Step 1: Active Beamforming Optimization - 4:
With fixed and , solve the subproblem (12) for active beamforming. - 5:
Obtain updated matrices by using the SCA-based method summarized in Algorithm 1. - 6:
Step 2: Passive Beamforming Optimization - 7:
With fixed and , solve the subproblem in Section 3.2 for passive beamforming. - 8:
Obtain updated vectors by using the SCA-based method summarized in Algorithm 2. - 9:
Step 3: MA Position Optimization - 10:
With fixed and , solve the subproblem (23) for MA positions. - 11:
Update the position of each MA sequentially by applying the BCD and SCA techniques to solve the convex subproblem (28), which yields the updated positions . - 12:
Update the iteration counter: . - 13:
until the fractional increase of the minimum secrecy rate is below a threshold or the maximum number of iterations is reached. - 14:
Output: The optimized active beamforming matrices , passive beamforming vectors , and MA positions .
|
3.4. Computational Complexity Analysis
We now analyze the computational complexity of the proposed AO-based algorithm (Algorithm 4), which is determined by the complexities of the three subproblems solved in each AO iteration. Let denote the number of iterations for the main AO loop. Let and denote the number of iterations required for the SCA-based Algorithm 1 and Algorithm 2, respectively. Finally, let and denote the number of iterations for the outer BCD loop and the inner SCA loop (for each antenna m) in Algorithm 3, respectively.
Algorithm 1 (Active Beamforming Optimization): This algorithm iteratively solves a Semidefinite Program (SDP), as formulated in (16). The problem involves positive semidefinite matrix variables of size , along with linear constraints. The complexity of solving this SDP in each SCA iteration using interior-point methods (IPMs) can be approximated as . Therefore, the total complexity of Algorithm 1 is .
Algorithm 2 (Passive Beamforming Optimization): This algorithm, detailed in
Section 3.2, also solves an SDP. The problem involves two main matrix variables (
) of size
. The complexity per SCA iteration is dominated by solving this SDP, which is
. Thus, the total complexity of Algorithm 2 is
.
Algorithm 3 (MA Position Optimization): This algorithm uses a BCD approach, iterating M times (once for each antenna) within its loops. In each of the M blocks, it solves a convex subproblem (28) using an inner SCA loop that runs for iterations. This subproblem (28) is a small convex program (CP), likely a Second-Order Cone Program (SOCP), with only three scalar variables ( and ) and constraints. Let denote the low polynomial cost of solving this small CP. The total complexity of Algorithm 3 is .
The overall computational complexity of the proposed Algorithm 4 is the sum of these components within the main AO loop:
In typical massive RIS-assisted systems, the number of RIS elements
N is very large (i.e.,
and
). Consequently, the overall complexity is expected to be dominated by the passive beamforming optimization (Algorithm 2), i.e.,
.
4. Numerical Results
In this section, we provide numerical results to validate the performance of our proposed algorithm in a multi-user, multi-eavesdropper scenario. We consider a three-dimensional Cartesian coordinate system in which the Base Station (BS), equipped with movable antennas, is located at m. The STAR-RIS, comprising elements, is deployed at m. To rigorously test the system’s capabilities, we model a scenario with a total of legitimate users. One user is located in the transmission space, and the other is located in the reflection space. We also consider two eavesdroppers. One in the transmission space at m. And the other one in the reflection space at m. Meanwhile, the positions of the two users are randomly generated in each Monte Carlo simulation. The user located in the transmission space is uniformly distributed within a circular area centered at m. The user located in the reflection space is uniformly distributed within a circular area centered at m. The optimization problem is to maximize the minimum secrecy rate between the two users.
The channel model for the BS-RIS link is assumed to follow Rician fading with a Rician factor of dB, reflecting a dominant line-of-sight (LoS) path. All other links are modeled using Rayleigh fading. The large-scale path loss is modeled as , where dB is the path loss at a reference distance of 1 m. The path loss exponents for the BS-RIS and RIS-Users/Eve links are set to and , respectively. The maximum transmit power at the BS is dBm, and the noise power is dBm. The carrier frequency is GHz. Our iterative algorithm terminates when the fractional increase of the objective function is below a tolerance of or after a maximum of 15 iterations. The final results are averaged over 200 Monte Carlo trials.
4.1. Benchmark Schemes for Comparison
To validate the contributions of the key components in our proposed design, namely the joint optimization of movable antennas and the utilization of STAR-RIS, we consider the following three benchmark schemes:
Scheme 1: Reflecting-only RIS. This scheme replaces the STAR-RIS with a conventional reflecting-only RIS. This scheme quantifies the performance gain by the STAR-RIS.
Scheme 2: FPA (Fixed-Position Antenna). This scheme replaces the MAs at the BS with a conventional fixed-position uniform linear array (ULA). The positions of the antennas are not subject to optimization. This highlights the performance gain by the optimization of the positions of the MAs.
Scheme 3: RPA (Random-Position Antenna). The antenna positions are randomly selected in each simulation. This benchmark demonstrates the performance gains from the optimization of the MAs.
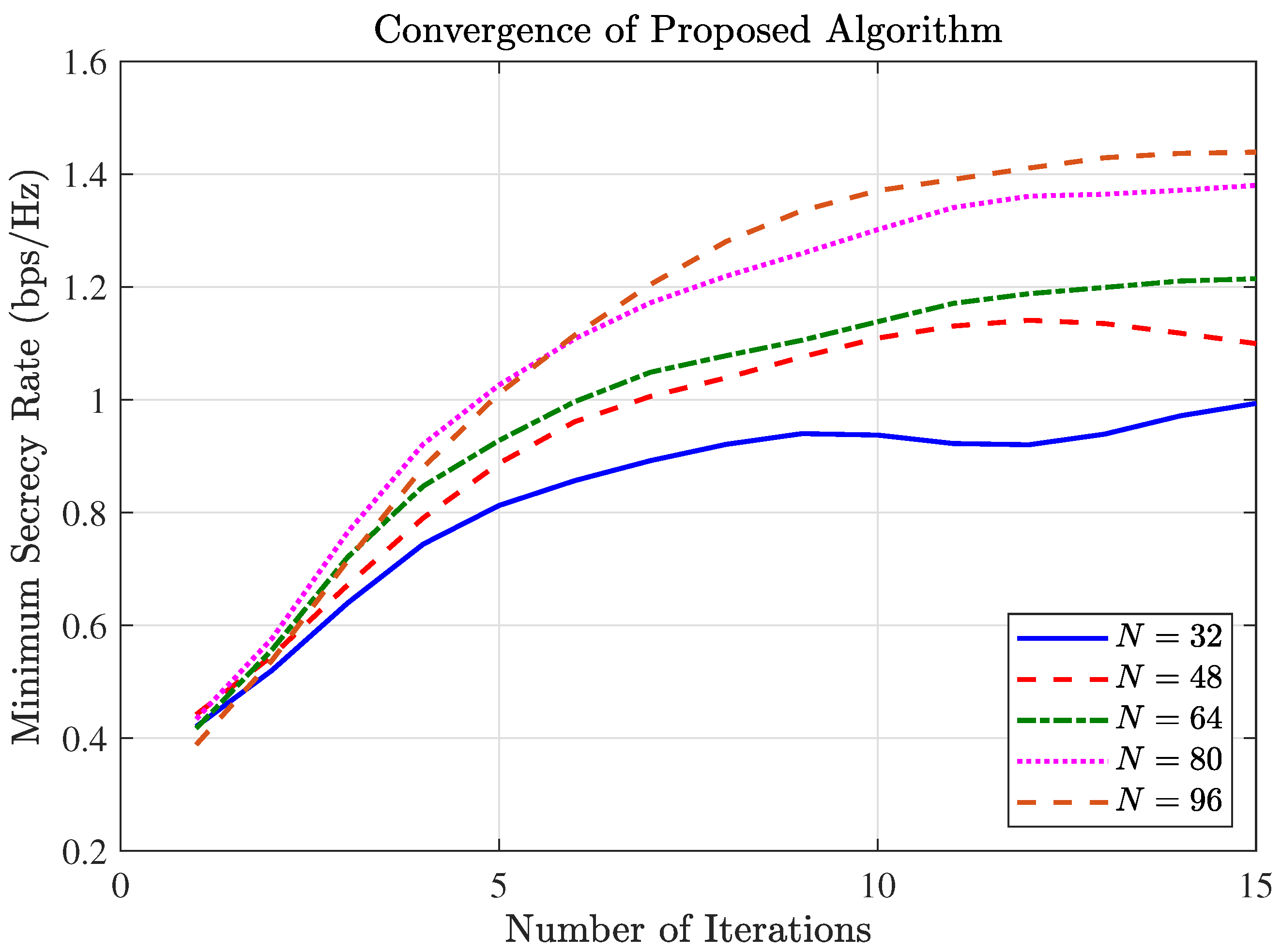
4.2. Convergence Analysis
Figure 2 demonstrated the convergence behavior of the proposed AO algorithm. As observed in
Figure 2, the secrecy rate increases monotonically and typically reaches a stable plateau after approximately 10 iterations. This behavior confirms that the algorithm satisfies the convergence criterion (fractional increase below
) well within the maximum limit of 15 iterations. This rapid convergence validates the effectiveness and computational efficiency of the proposed algorithm. The convergence behavior confirms that the SCA and SDR techniques are effective at finding high-quality solutions.
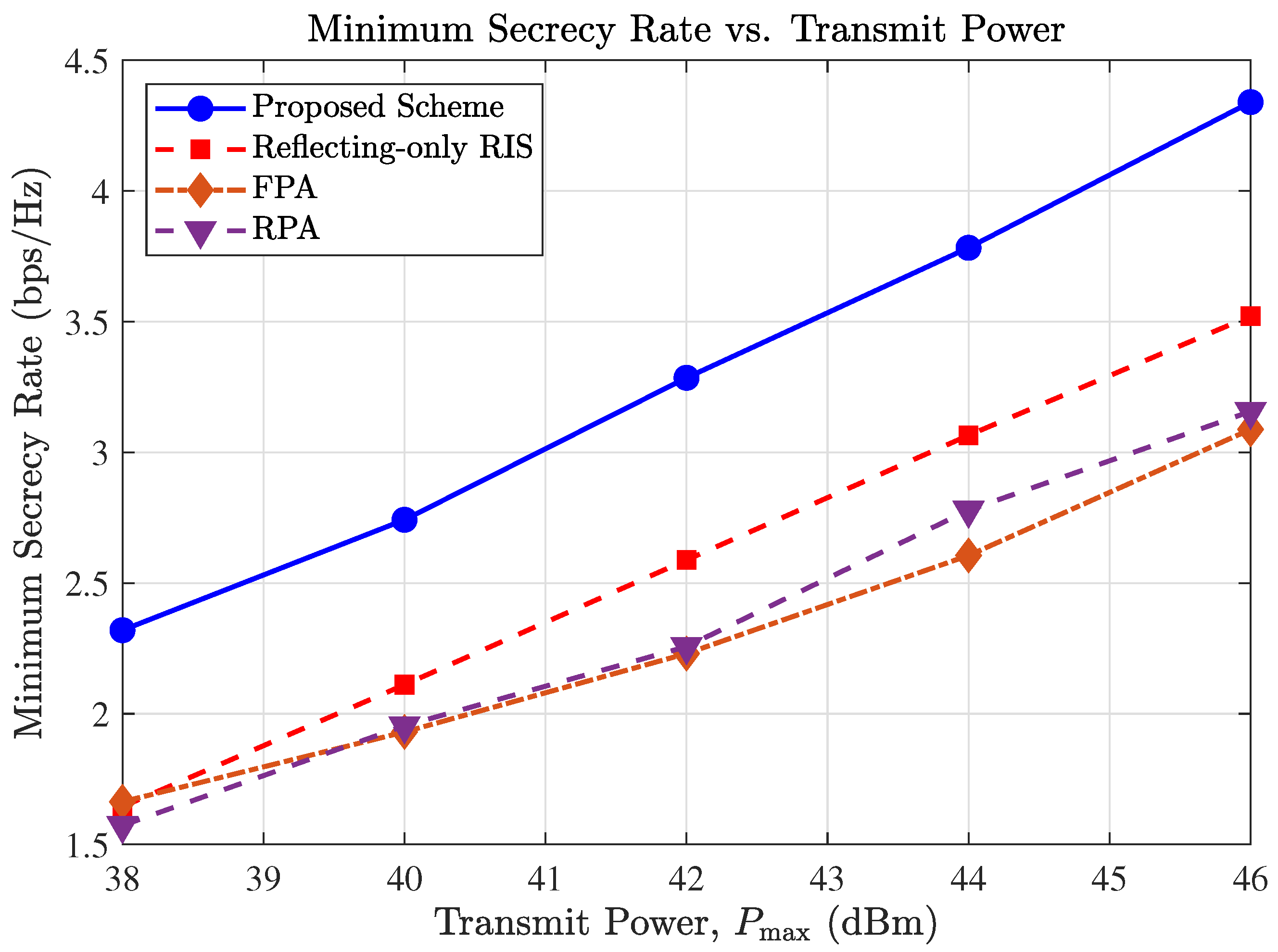
4.3. Impact of BS Transmit Power
Figure 3 illustrates the minimum secrecy rate versus the maximum transmit power at the BS,
. As expected, the secrecy rates of all schemes improve as the transmit power increases. However, the proposed MA-aided STAR-RIS scheme exhibits the steepest slope, indicating superior power efficiency compared to the benchmarks.
Specifically, the performance gap between the proposed scheme and the fixed-position antenna (FPA) benchmark widens significantly in the high-SNR regime. This trend can be attributed to the spatial flexibility of MAs. In high-power regimes, the system is often limited by interference or channel correlation rather than noise. Fixed antennas (FPA) may be stuck in positions with deep fading or high correlation between legitimate and eavesdropping channels. In contrast, MAs can dynamically maneuver to spatial “sweet spots” that maximize the channel gain difference between the legitimate user and the eavesdropper. This capability allows the system to convert increased transmit power into secrecy capacity more effectively.
Furthermore, the proposed scheme significantly outperforms the “Reflecting-only RIS” benchmark. This confirms the critical advantage of the STAR-RIS architecture, which enables full-space coverage () to serve users in both transmission and reflection regions simultaneously, whereas a conventional reflecting-only RIS fails to effectively cover the transmission space.
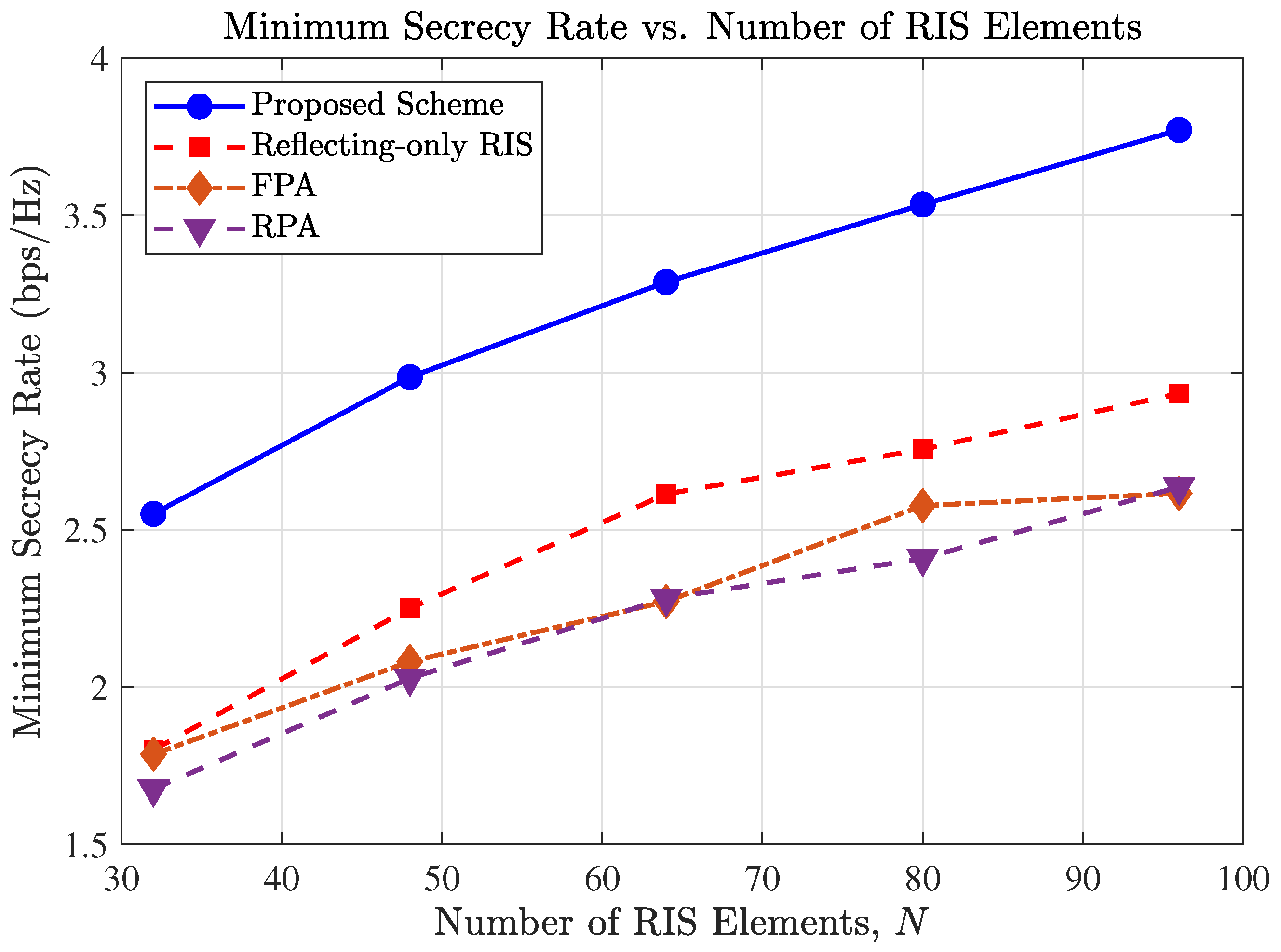
4.4. Impact of the Number of RIS Elements
Figure 4 depicts the impact of the number of STAR-RIS elements,
N, on the minimum secrecy rate. It is observed that increasing
N leads to substantial performance gains across all RIS-assisted schemes, primarily due to the enhanced passive beamforming gain and higher spatial resolution provided by the larger aperture.
Notably, the proposed scheme maintains a distinct and growing advantage over the FPA scheme as N increases. This highlights a unique synergistic effect between the MAs and the STAR-RIS. The optimization of MA positions does not merely improve the direct links; crucially, it reconfigures the BS-to-RIS channel () to align with the STAR-RIS array response. By moving the antennas, the BS can “illuminate” the STAR-RIS more effectively, maximizing the signal power that reaches the RIS elements.
Consequently, the large-scale STAR-RIS can manipulate a stronger incident signal, leading to a multiplicative gain in the cascaded link. In contrast, the FPA scheme is constrained by a fixed, potentially suboptimal , which creates a bottleneck that prevents the system from fully exploiting the potential of a large N. The “Reflecting-only RIS” and “RPA” schemes exhibit the lowest performance, further validating the necessity of the proposed joint design.