Trust-Aware Causal Consistency Routing for Quantum Key Distribution Networks Against Malicious Nodes
Abstract
1. Introduction
- We propose a Causal Consistency Key-State Update mechanism, enabling all nodes in the network to reach consensus regarding the key states of each link. Routing decisions are then made based on these results, effectively preventing honest nodes from misjudging the routing states of other links.
- We develop a Trust-Aware Multi-path Flow Optimization framework. Within the Causal Consistency Key-State Update process, discrepancies between the link-state information reported by the two endpoints of the same link are computed. These discrepancies are used as quantitative indicators of the trustworthiness of the corresponding links and are incorporated into a new multi-path routing optimization model.
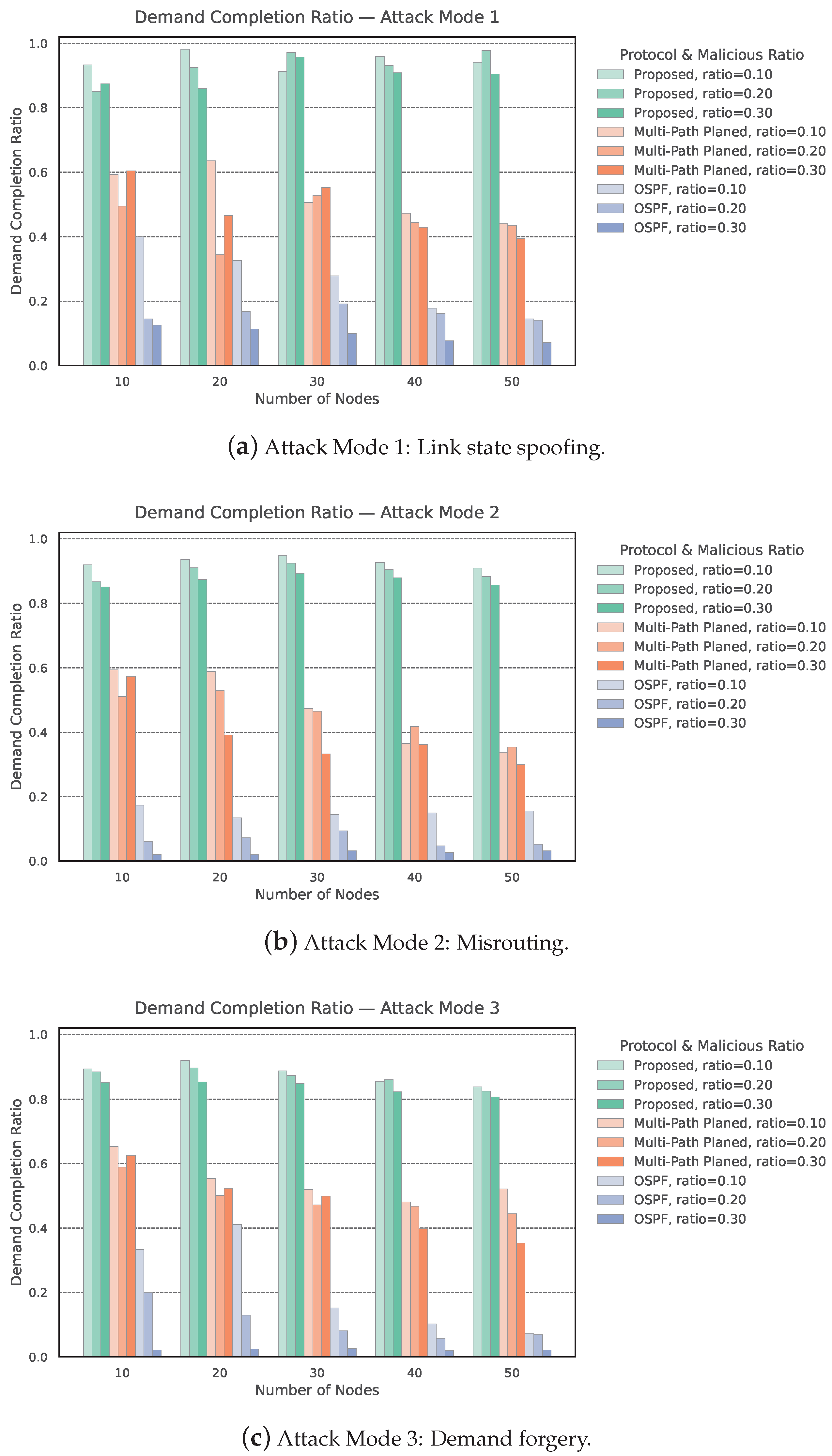
- Extensive simulations on 50-node topologies with malicious-node ratios up to 30% demonstrate the significant superiority of our approach: the proposed protocol consistently sustains high demand completion ratios (DCR ) while keeping key utilization efficiency (KUE) as low as ≈16.6 keys per demand. In contrast, Multi-Path Planned achieves only moderate performance (DCR , KUE ), and OSPF collapses with extremely poor reliability (DCR ) and prohibitive inefficiency (KUE up to 1601 keys per demand). These results highlight that our design achieves an order-of-magnitude improvement in efficiency and reliability across all attack modes.
2. Preliminary
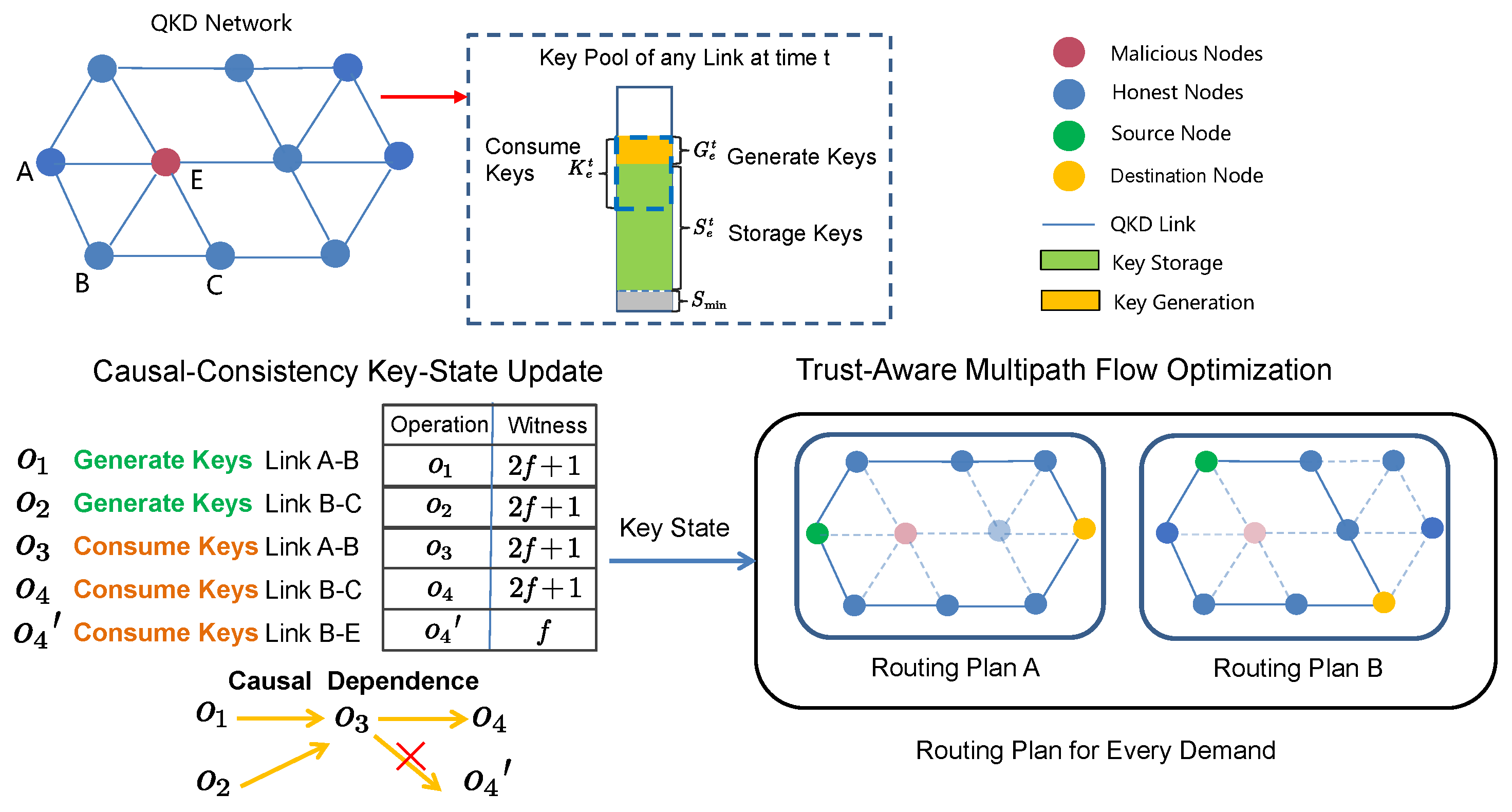
2.1. Routing Problem in QKD Networks
- Flow Conservation Constraint: For each node v, the total incoming and outgoing key flows must balance, except at the source and destination nodes:represents the incoming key flow on link e at time t.represents the outgoing key flow on link e at time t.denotes the set of incoming links to node v.denotes the set of outgoing links from node v.represents the key demand from source i to destination j at time t.
- Key Consumption on Links: The total key consumption on link e is given by
- Key Pool Dynamics: The key pool storage generally varies dynamically over time, as it depends on both the generated and consumed key amounts at each time step. This can be expressed asis the key pool storage at time t.represents the key generation rate on link e.is the total key consumption on link e.
- Key Storage Constraint: The key consumption should respect the available key storage while maintaining a minimum threshold:
2.2. Malicious Nodes Assumption
- In Attack Mode 1, malicious nodes alter a part of the routing key-state values and .
- In Attack Mode 2, malicious nodes abuse their control to arbitrarily alter the flow variables and , thereby misrouting key forwarding along suboptimal paths.
- In Attack Mode 3, malicious nodes can add external demand variables .
3. Trust-Aware Causal Consistency Routing Against Malicious Nodes
3.1. Overview
3.2. Causal Consistency Key-State Update
- Program order: They are issued by the same process and must appear before or depending on the result of .
- Reads-from: writes to some object, and later reads that same object value.
- Transitivity: There is an intermediate operation such that and .
- Key Consumption Across Multiple Paths: Suppose two operations and consume keys on the same link’s key pool. If depends on the key amount reduced by , then . Causal consistency requires that no correct node applies without first having observed the updated capacity after .
- Key Regeneration and Route Advertisement: Consider a link whose key resources are initially exhausted (capacity ) and then replenished at time t through a new round of key generation. This regeneration is an operation . Later, a routing protocol advertises to be used in a new route . Because depends on the prior knowledge that has available key material, we have . Causal consistency ensures that every node that accepts must have first observed .
3.2.1. Protocol Definition and Setup
- If an update receives fewer than witnesses, it is considered potentially forged and not acknowledged.
- If it has at least witnesses, it is partially validated but not yet committed.
- Only when an update accumulates at least witnesses can it be safely delivered and causally applied.
- A vector clock , with all entries initially set to zero.
- A pending queue for delayed updates with unmet dependencies.
- A witness_log for storing witnessed updates from other nodes.
- A commit_log for recording locally applied and confirmed updates.
- A view of the current round number r, with leader .
- Update Message:An update message is generated whenever a node performs a key-state change or a routing-plan update. It carries the following:
- –
- The incremented vc field, which reflects the updated vector clock entry corresponding to the event.
- –
- A dependency set, deps, which is a snapshot of the sender’s current VC. This ensures causal ordering: if a receiver’s local VC is behind any entry in deps, the update is placed into the pending queue until the missing dependencies are applied.
- –
- The Update_set, which contains either the local key-state increments on adjacent links or a multi-path routing plan involving those links.
- –
- A type field indicating whether the update is a KeyState or RoutePlan.
- –
- Witness Acknowledgment:A witness acknowledgment confirms receipt and validation of an update. It includes the hash of the acknowledged update, the witness node’s signature, and the sender’s identifier.
3.2.2. Causal Consistency Key-State Update in Round r
- Check Key-State Witnesses
- For each link, verify that the latest updates satisfy all dependencies in .
- Filter the key states that have accumulated more than witnesses. Since key states are broadcast by nodes, we check whether both adjacent nodes i and j have witness counts exceeding . If this condition is satisfied, the key state of link is included in the valid key states.
- Compute and Broadcast New Plan
- Computes a new multi-path route plan as the method in Section 3.3 based on the valid key states and communication demands.
- Records all edges scheduled to consume keys, along with the corresponding key consumption amounts in the update_set. Records in deps the vector-clock values of these edges from their most recent routing states. Forms a batched RoutePlan update message:
- Broadcasts the new RoutePlan message to all nodes for witness collection.
- Update Local State:
- Broadcasts the current local state and communication demands, including the following:
- –
- Latest key states on adjacent links.
- –
- Communication demands with the current node as the source.
- Receive and Verify Route Plan:
- Upon receiving a RoutePlan update from the leader, verify the following:
- –
- The leader’s signature.
- –
- Whether the update’s deps are satisfied by local vector clocks.
- –
- Whether the leader issued conflicting route plans (equivocation).
- If verification passes, sends a Witness Acknowledgment:
- If conflict is detected, broadcasts a Conflict Witness Acknowledgment:
- Apply Finalized Updates:Once any KeyState or RoutePlan update receives at least witness acknowledgments and all dependencies are met, the node performs the following:
- Verifies its causal dependencies. Specifically, for each entry in the update U, the node checks whether:
- If any dependency is not yet satisfied, the update is placed into a pending queue, else move the update to commit_log.
- Applies the corresponding key state change to local state.
3.3. Trust-Aware Multi-Path Flow Optimization
- Using link state perception discrepancies as a measure of trustworthiness, allowing the system to quantify the reliability of each link based on the consistency of reported states from connected nodes.
- Extending the original routing strategy to a multi-path routing formulation, which enhances resilience against malicious behavior by diversifying key distribution paths and reducing reliance on any single potentially compromised route.
- We can pre-compute per-link trust levels and, for each demand , enumerate a small set of candidate node-disjoint paths (e.g., K trusted shortest/vertex-disjoint paths). In the optimization, binary decisions are attached to paths (select/not-select) rather than to edges.
- We can apply a trust threshold to retain only high-confidence candidate paths before optimization, thereby removing low-trust routes that would be down-weighted or eliminated by the solver anyway. In addition, the number of required node-disjoint paths can be fixed (e.g., ), avoiding a combinatorial search. This restriction further shrinks the integer feasible set and stabilizes solve times under rapid trust/key-rate fluctuations.
- We can relax the global fairness coupling by choosing a larger fairness variable (or by softening fairness into a penalty in the objective with an increased weight ). This allows a controlled relaxation of fairness to substantially reduce solve time and improve stability.
4. Simulation
4.1. Simulation Setup
- Inconsistent routing broadcasts (Attack Mode 1): Malicious nodes disseminate conflicting routing information during state broadcasts. On each broadcast, with probability 50%, the attacker perturbs the routing state by a random percentage (uniform from [−0.30, +0.30]).
- Incorrect forwarding paths (Attack Mode 2): Malicious nodes are free to make routing decisions in their own way, without being constrained by the protocol. The malicious nodes randomly select a suboptimal feasible next hop.
- Excessive key demands (Attack Mode 3): Malicious nodes generate inflated key requests to exhaust available resources. Every pair of non-adjacent malicious nodes generates additional demands (same to honest nodes).
4.2. Simulation Results
4.2.1. Simulation Results About Demand Completion Ratio
4.2.2. Simulation Results About Key Utilization Efficiency
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Abbreviations
| QKD | Quantum Key Distribution |
| DCR | Demand Completion Ratio |
| KUE | Key Utilization Efficiency |
| ITS | Information-Theoretic Security |
| TLS | Transport Layer Security |
| IEEE | Institute of Electrical and Electronics Engineers |
| ACM | Association for Computing Machinery |
| PRX | Physical Review X |
| SIAM | Society for Industrial and Applied Mathematics |
| RFC | Request for Comments |
| OSPF | Open Shortest Path First |
| IS-IS | Intermediate System to Intermediate System |
| AI | Artificial Intelligence |
| ILP | Integer Linear Program |
References
- Bennett, C.H.; Brassard, G. Quantum cryptography: Public key distribution and coin tossing. Theor. Comput. Sci. 1984, 560, 7–11. [Google Scholar] [CrossRef]
- Xu, F.; Ma, X.; Zhang, Q.; Lo, H.K.; Pan, J.W. Secure quantum key distribution with realistic devices. Rev. Mod. Phys. 2020, 92, 025002. [Google Scholar] [CrossRef]
- Zhang, Y.; Bian, Y.; Li, Z.; Yu, S.; Guo, H. Continuous-variable quantum key distribution system: Past, present, and future. Appl. Phys. Rev. 2024, 11, 011318. [Google Scholar] [CrossRef]
- Portmann, C.; Renner, R. Security in quantum cryptography. Rev. Mod. Phys. 2022, 94, 025008. [Google Scholar] [CrossRef]
- Hu, C.; Wang, W.; Chan, K.S.; Yuan, Z.; Lo, H.K. Proof-of-Principle Demonstration of Fully-Passive Quantum Key Distribution. arXiv 2023, arXiv:2304.10374. [Google Scholar] [CrossRef]
- Wang, S.; Chen, W.; Yin, Z.Q.; Li, H.W.; He, D.Y.; Li, Y.H.; Zhou, Z.; Song, X.T.; Li, F.Y.; Wang, D.; et al. Field and long-term demonstration of a wide area quantum key distribution network. Opt. Express 2014, 22, 21739. [Google Scholar] [CrossRef] [PubMed]
- Mao, Y.; Wang, B.X.; Zhao, C.; Wang, G.; Wang, R.; Wang, H.; Zhou, F.; Nie, J.; Chen, Q.; Zhao, Y.; et al. Integrating quantum key distribution with classical communications in backbone fiber network. Opt. Express 2018, 26, 6010. [Google Scholar] [CrossRef] [PubMed]
- Sasaki, M.; Fujiwara, M.; Ishizuka, H.; Klaus, W.; Wakui, K.; Takeoka, M.; Miki, S.; Yamashita, T.; Wang, Z.; Tanaka, A.; et al. Field test of quantum key distribution in the Tokyo QKD Network. Opt. Express 2011, 19, 10387. [Google Scholar] [CrossRef]
- Dynes, J.F.; Wonfor, A.; Tam, W.W.S.; Sharpe, A.W.; Takahashi, R.; Lucamarini, M.; Plews, A.; Yuan, Z.L.; Dixon, A.R.; Cho, J.; et al. Cambridge quantum network. npj Quantum Inf. 2019, 5, 101. [Google Scholar] [CrossRef]
- Chen, T.Y.; Jiang, X.; Tang, S.B.; Zhou, L.; Yuan, X.; Zhou, H.; Wang, J.; Liu, Y.; Chen, L.K.; Liu, W.Y.; et al. Implementation of a 46-node quantum metropolitan area network. npj Quantum Inf. 2021, 7, 134. [Google Scholar] [CrossRef]
- Tsai, C.W.; Yang, C.W.; Lin, J.; Chang, Y.C.; Chang, R.S. Quantum Key Distribution Networks: Challenges and Future Research Issues in Security. Appl. Sci. 2021, 11, 3767. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.; Wang, Q.; Zhang, J.; Ng, S.X.; Hanzo, L. The Evolution of Quantum Key Distribution Networks: On the Road to the Qinternet. IEEE Commun. Surv. Tutor. 2022, 24, 839–894. [Google Scholar] [CrossRef]
- Dervisevic, E.; Tankovic, A.; Fazel, E.; Kompella, R.; Fazio, P.; Voznak, M.; Mehic, M. Quantum Key Distribution Networks—Key Management: A Survey. ACM Comput. Surv. 2025, 57, 1–36. [Google Scholar] [CrossRef]
- Kong, P.Y. Challenges of Routing in Quantum Key Distribution Networks with Trusted Nodes for Key Relaying. IEEE Commun. Mag. 2023, 62, 124–130. [Google Scholar] [CrossRef]
- Kong, P.Y. Routing with Minimum Activated Trusted Nodes in Quantum Key Distribution Networks for Secure Communications. IEEE Internet Things J. 2024, 11, 15219–15228. [Google Scholar] [CrossRef]
- Mehic, M.; Fazio, P.; Rass, S.; Maurhart, O.; Peev, M.; Poppe, A.; Rozhon, J.; Niemiec, M.; Voznak, M. A Novel Approach to Quality-of-Service Provisioning in Trusted Relay Quantum Key Distribution Networks. IEEE/ACM Trans. Netw. 2020, 28, 168–181. [Google Scholar] [CrossRef]
- He, X.; Li, L.; Han, D.; Zhao, Y.; Nag, A.; Wang, W.; Wang, H.; Cao, Y.; Zhang, J. Routing and secret key assignment for secure multicast services in quantum satellite networks. J. Opt. Commun. Netw. 2022, 14, 190–203. [Google Scholar] [CrossRef]
- Zhang, Q.; Ayoub, O.; Gatto, A.; Wu, J.; Lin, X.; Musumeci, F.; Verticale, G.; Tornatore, M. Joint Routing, Channel, and Key-Rate Assignment for Resource-Efficient QKD Networking. In Proceedings of the GLOBECOM 2022—2022 IEEE Global Communications Conference, Rio de Janeiro, Brazi, 4–8 December 2022. [Google Scholar] [CrossRef]
- Zhu, Q.; Yu, X.; Wang, Z.; Zhao, Y.; Nag, A.; Wang, S.; Chen, W.; Zhang, J. Autonomic end-to-end quality-of-service assurance over QKD-secured optical networks. Opt. Express 2024, 32, 18317. [Google Scholar] [CrossRef]
- Akhtar, M.S.; G, K.; B, V.; Sinha, A. Fast and Secure Routing Algorithms for Quantum Key Distribution Networks. IEEE/ACM Trans. Netw. 2023, 31, 2281–2296. [Google Scholar] [CrossRef]
- Kiktenko, E.O.; Tayduganov, A.; Fedorov, A.K. Routing Algorithm Within the Multiple Non-Overlapping Paths’ Approach for Quantum Key Distribution Networks. Entropy 2024, 26, 1102. [Google Scholar] [CrossRef]
- Sun, Z.Z.; Cheng, Y.B.; Ruan, D.; Pan, D.; Zhang, F.H.; Long, G.L. Quantum communication network routing with circuit and packet switching strategies. IEEE J. Sel. Areas Commun. 2025, 43, 1887–1900. [Google Scholar] [CrossRef]
- Johann, T.; Wenning, M.; Giemsa, D.; Dochhan, A.; Gunkel, M.; Fehenberger, T.; Pachnicke, S. Comparison and optimization of different routing methods for meshed QKD networks using trusted nodes. J. Opt. Commun. Netw. 2024, 16, 382–391. [Google Scholar] [CrossRef]
- Cao, Y.; Zhao, Y.; Li, J.; Lin, R.; Zhang, J.; Chen, J. Hybrid Trusted/Untrusted Relay-Based Quantum Key Distribution Over Optical Backbone Networks. IEEE J. Sel. Areas Commun. 2021, 39, 2701–2718. [Google Scholar] [CrossRef]
- Huang, Y.; Zhang, X.; Ma, X. Stream Privacy Amplification for Quantum Cryptography. PRX Quantum 2022, 3, 020353. [Google Scholar] [CrossRef]
- Curty, M.; Lo, H.K. Foiling covert channels and malicious classical post-processing units in quantum key distribution. npj Quantum Inf. 2019, 5, 14. [Google Scholar] [CrossRef]
- Zapatero, V.; Curty, M. Secure quantum key distribution with a subset of malicious devices. npj Quantum Inf. 2021, 7, 26. [Google Scholar] [CrossRef]
- Zhou, H.; Lv, K.; Huang, L.; Ma, X. Quantum Network: Security Assessment and Key Management. IEEE/ACM Trans. Netw. 2022, 30, 1328–1339. [Google Scholar] [CrossRef]
- Lo, H.K.; Montagna, M.; von Willich, M. Distributed Symmetric Key Exchange: A scalable, quantum-proof key distribution system. arXiv 2022, arXiv:2205.00615. [Google Scholar] [CrossRef]
- Moy, J. OSPF, Version 2; RFC 2328; Internet Engineering Task Force (IETF): Fremont, CA, USA, 1998; Available online: https://www.rfc-editor.org/rfc/rfc2328 (accessed on 5 September 2025).
- Li, T.; Atkinson, R. IS-IS Cryptographic Authentication; RFC 5304; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2008; Available online: https://www.rfc-editor.org/rfc/rfc5304 (accessed on 5 September 2025).
- Rescorla, E. The Transport Layer Security (TLS) Protocol Version 1.3; RFC 8446; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2018; Available online: https://www.rfc-editor.org/rfc/rfc8446 (accessed on 5 September 2025).
- Kent, S.; Seo, K. Security Architecture for the Internet Protocol; RFC 4301; Internet Engineering Task Force (IETF): Fremont, CA, USA, 2005; Available online: https://www.rfc-editor.org/rfc/rfc4301 (accessed on 5 September 2025).
- Shor, P.W. Polynomial-Time Algorithms for Prime Factorization and Discrete Logarithms on a Quantum Computer. SIAM J. Comput. 1997, 26, 1484–1509. [Google Scholar] [CrossRef]
- Lamport, L.; Shostak, R.; Pease, M. The Byzantine Generals Problem. ACM Trans. Program. Lang. Syst. 1982, 4, 382–401. [Google Scholar] [CrossRef]
- Ahamad, M.; Neiger, G.; Burns, J.E.; Kohli, P.; Hutto, P.W. Causal memory: Definitions, implementation, and programming. Distrib. Comput. 1995, 9, 37–49. [Google Scholar] [CrossRef]
- Terry, D.B.; Demers, A.J.; Petersen, K.; Spreitzer, M.J.; Theimer, M.M.; Welch, B.B. Session guarantees for weakly consistent replicated data. In Proceedings of the 3rd International Conference on Parallel and Distributed Information Systems, Austin, TX, USA, 28–30 September 1994; pp. 140–149. [Google Scholar]
- Bailis, P.; Fekete, A.; Franklin, M.J.; Ghodsi, A.; Hellerstein, J.M.; Stoica, I. Coordination avoidance in database systems. Proc. VLDB Endow. 2014, 8, 185–196. [Google Scholar] [CrossRef]
- Kiktenko, E.O.; Zelenetsky, A.S.; Fedorov, A.K. Practical quantum multiparty signatures using quantum-key-distribution networks. Phys. Rev. A 2022, 105, 012408. [Google Scholar] [CrossRef]
- Luo, Y.; Li, Q.; Mao, H.K. Distributed information-theoretical secure protocols for quantum key distribution networks against malicious nodes. J. Opt. Commun. Netw. 2024, 16, 956–968. [Google Scholar] [CrossRef]
- Luo, Y.; Mao, H.K.; Li, Q.; Chen, N. An Information-Theoretic Secure Group Authentication Scheme for Quantum Key Distribution Networks. IEEE Trans. Commun. 2023, 71, 5420–5431. [Google Scholar] [CrossRef]
- Wang, Y.; Li, Q.; Han, Q.; Wang, Y. Modeling and simulation of practical quantum secure communication network. Quantum Inf. Process. 2019, 18, 278. [Google Scholar] [CrossRef]


Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2025 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Luo, Y.; Li, Q. Trust-Aware Causal Consistency Routing for Quantum Key Distribution Networks Against Malicious Nodes. Entropy 2025, 27, 1100. https://doi.org/10.3390/e27111100
Luo Y, Li Q. Trust-Aware Causal Consistency Routing for Quantum Key Distribution Networks Against Malicious Nodes. Entropy. 2025; 27(11):1100. https://doi.org/10.3390/e27111100
Chicago/Turabian StyleLuo, Yi, and Qiong Li. 2025. "Trust-Aware Causal Consistency Routing for Quantum Key Distribution Networks Against Malicious Nodes" Entropy 27, no. 11: 1100. https://doi.org/10.3390/e27111100
APA StyleLuo, Y., & Li, Q. (2025). Trust-Aware Causal Consistency Routing for Quantum Key Distribution Networks Against Malicious Nodes. Entropy, 27(11), 1100. https://doi.org/10.3390/e27111100





