A Lightweight CP-ABE Scheme with Direct Attribute Revocation for Vehicular Ad Hoc Network
Abstract
1. Introduction
- (1)
- Aiming at the problem that using an indirect revocation mechanism to realize attribute revocation leads to large system consumption and complicated operation, by separating the static and dynamic attributes of the vehicle terminal, our scheme establishes a two-level decryption architecture of RSU and OBU and realizes the direct revocation of attributes based on an RSU agent, reducing system consumption due to frequent updating and revoking attributes.
- (2)
- To address the problem of excessive computational overhead due to the use of bilinear pairing operations, our scheme is based on elliptic curve cryptography, using scalar multiplication instead of complex bilinear pairing operations, and outsourcing the decryption operations originally belonging to OBU to RSU to reduce computational costs and improve overall efficiency.
- (3)
- The security analysis proves that our scheme is secure under a chosen plaintext attack. Theoretical and simulation experiments prove that our scheme is more efficient and less computationally expensive than the existing schemes.
2. Preliminaries
2.1. Elliptic Curve Discrete Logarithm Problem
2.2. Access Structure
2.3. Linear Secret Sharing Scheme
- (1)
- The secret shares held by each participant form a vector over .
- (2)
- Each corresponds to a generator matrix , and maps each row of M to a participant , where is an injective function. Consider the vector , where is the secret value and are randomly chosen, the shares of the secret value can be recorded as , where is the i-th share of the secret value , and belongs to .
2.4. Decisional Diffie–Hellman Assumption
3. Proposed Scheme
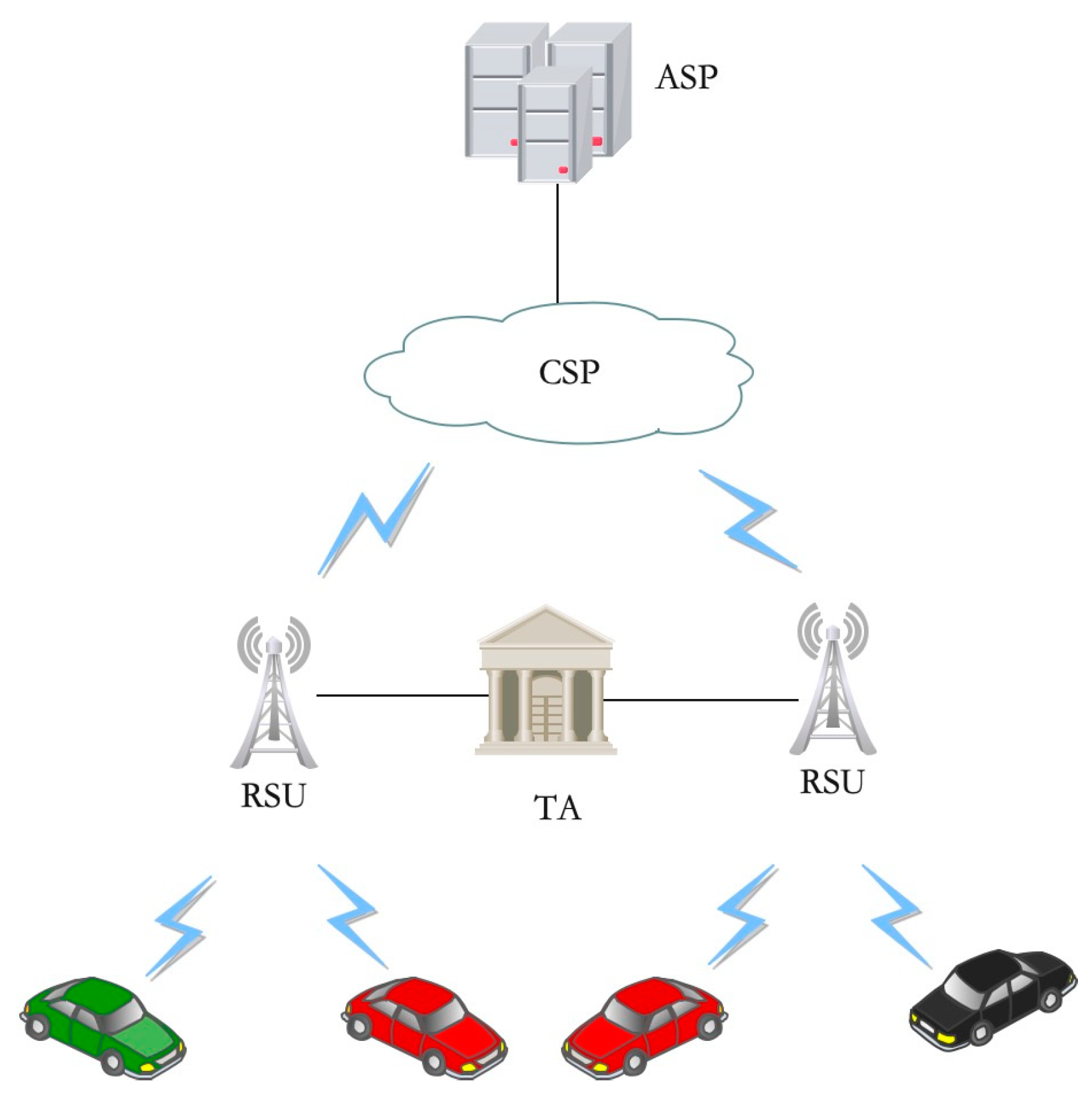
3.1. System Mode
- (1)
- TA: The TA is a fully trusted server with high computing power, regulated by government authorities and always online. The TA is responsible for initializing system parameters and generating system public and master keys. The TA generates attribute keys for all attributes defined by the system and publishes their public keys. The attributes defined by the system are divided into static and dynamic attributes. Among them, static attributes include vehicle type, make, registration number and company, etc., which will not change in a short time for the OBU; dynamic attributes include the current driving city, street and driving direction, etc., which will change frequently for the OBU. The TA is responsible for RSU and OBU registration, binds the unique user identity identifier UID_RSU or UID_OBU for the user, and generates the user decryption key according to its attributes. In addition, the TA will also generate a certificate for the OBU to authenticate with the RSU.
- (2)
- CSPs: The CSPs have abundant storage space, store encrypted data uploaded by ASPs or OBUs and send encrypted data to authorized entities according to the request. In the scheme design of this paper, the CSP is honest but curious, i.e., it will honestly perform related tasks and additionally infer private information.
- (3)
- ASPs: The ASPs are responsible for providing applications or services to vehicles, such as GPS service providers who can collect traffic data provided by vehicles from CSPs and then process the collected data to serve different users through different GPS services. Alternatively, if a taxi company only wants to provide services to its vehicles in a certain area, it can encrypt the application data according to its own defined access policy and upload it to the CSP.
- (4)
- RSUs: The RSUs are widely deployed at roadsides and intersections, have relatively abundant computing and storage space and are regulated by government departments. When the local traffic management department deploys the RSU, it will apply to the TA for the unique identity UID_RSU and the attribute decryption key according to the attributes such as the deployed city, road and lane direction.
- (5)
- OBUs: When the vehicle production is completed, the company will apply to the TA for the unique identity UID_OBU, attribute decryption key and digital certificate for OBU through the local traffic management department according to its vehicle type, brand and registration number.
3.2. Specific Implementation
3.2.1. Setup
3.2.2. TASetup
3.2.3. KeyGen
3.2.4. TransKeyGen
3.2.5. Encrypt
3.2.6. Decrypt
- (1)
- : The algorithm takes the system public parameter , the ciphertext , the user private key of RSU and the proxy decryption key provided by OBU as input, and outputs the converted ciphertext . The algorithm consists of two stages.
- (2)
- : The algorithm takes the system public parameter , the converted ciphertext and the converted key as input, and outputs the original data information . After the OBU obtains , it can be calculated by using and as
3.2.7. Direct Revocation
- (1)
- User revocation: In the scheme proposed in this paper, for the user revocation of an OBU, the local traffic management department can initiate a user revocation request to the TA, and the TA will add the certificate of the OBU user to the certificate revocation list (CRL) to make the RSU reject the access authentication of the OBU user.
- (2)
- Dynamic attribute revocation: Since the part of the ciphertext encrypted with the dynamic attribute access control policy is decrypted by the RSU, when the OBU leaves the coverage area of a particular RSU, it no longer receives the converted ciphertext sent by the RSU, thus realizing the direct revocation of the dynamic attributes of the vehicle terminal.
- (3)
- Static attribute revocation: In the design of this scheme, when the OBU requests an attribute decryption key for an attribute, the TA sets the validity period of the attribute in the certificate . Therefore, after the OBU sends the certificate to the RSU, the RSU can obtain the valid static attribute set of the OBU and then obtain the decryption key of the valid attribute from the proxy decryption key . If a static attribute has expired, the valid static attribute set obtained by the RSU will not contain that attribute. When a static attribute has not expired but still needs to be revoked, the local traffic management department can initiate an attribute revocation request to the TA, and the TA will modify the certificate of the OBU user and delete the attribute from . The effective static attribute set obtained by the RSU will also not contain this attribute, thereby realizing the direct revocation of the static attribute.
4. Security Discussion and Analysis
4.1. Security Discussion
- (1)
- Anti-collusion security: In the scheme proposed in this paper, the user keys distributed from TA to OBU are all bound to their unique identities. Therefore, even if multiple users who do not meet the access structure collude with each other to share keys, due to their different identities, it is impossible to eliminate redundant elements by combination to obtain the hidden secret value, thus ensuring that the scheme has anti-collusion security.
- (2)
- Forward security: For a given user revocation, the TA adds the certificate of the OBU to the CRL so that the OBU cannot be connected to the RSU and the decryption of the ciphertext cannot be completed by the RSU. For a particular attribute, the direct revocation of the attribute can be realized based on the RSU proxy. The above two revocation methods ensure the forward security of the proposed scheme.
- (3)
- Correctness of outsourced decryption: In the scheme proposed in this paper, OBU can calculate the keys and after obtaining , and then use the key to obtain the data , use the key to calculate and compare it with the contained in the converted ciphertext to judge the correctness of the outsourced decryption.
4.2. Security Model
- (1)
- Initialization: The TA first runs the Setup and TASetup algorithms to generate the system public parameters , public key and attribute public key to provide to the attacker. The attacker then selects a set of challenge access structures to send to the challenger.
- (2)
- Phase 1: The attacker can request to query the private key of any attribute not in the challenge access structure.
- (3)
- Challenge: The attacker submits two randomly selected messages and of equal length to the challenger. The challenger first randomly selects and then encrypts the message according to the challenge access structure submitted by the attacker.
- (4)
- Phase 2: As in Phase 1, the attacker can request to query any attribute private key that cannot be used to decrypt the challenge ciphertext.
- (5)
- Guess: The attacker outputs the guess result of . The advantage of the attacker in this game process is defined as .
4.3. Security Analysis
- (1)
- Initialization: Simulator first runs the Setup and TASetup algorithms to generate system public parameters , master private key , system public key , attribute private key and attribute public key for each attribute . Then, simulator provides , and to attacker . Finally, simulator initializes a list for recording interactions with attacker . Attacker chooses a set of challenge access structures and sends them to simulator .
- (2)
- Phase 1: Attacker can submit to simulator to query the private key of any attribute not in the challenge access structure. The simulator verifies whether the element is already contained in the list . If already exists in the list , the simulator responds with the in . Otherwise, the simulator randomly selects , calculates as a response and stores the element in the list .
- (3)
- Challenge: Attacker submits two randomly selected messages and of equal length to Simulator . Simulator first randomly selects . Then, Simulator randomly selects two elements , uses as a symmetric key to encrypt data to obtain , uses as a key to obtain the message authentication code of data , uses as a symmetric key to encrypt data to obtain and uses as a key to obtain the message authentication code of data . Next, simulator randomly selects four vectors and , where the first element of is , the first element of is 1, the first element of is , and the first element of is 0, and calculates , , and . Finally, the simulator calculates and obtains , , and . The simulator generates the challenge ciphertext of the information and sends it to the attacker .
- (4)
- Phase 2: Similar to Phase 1.
- (5)
- Guess: Attacker outputs the guess result of . If , simulator outputs 0 to indicate that the guess result is . Otherwise, simulator outputs 1 to indicate that the guess result is .
5. Performance Analysis
5.1. Theoretical Analysis
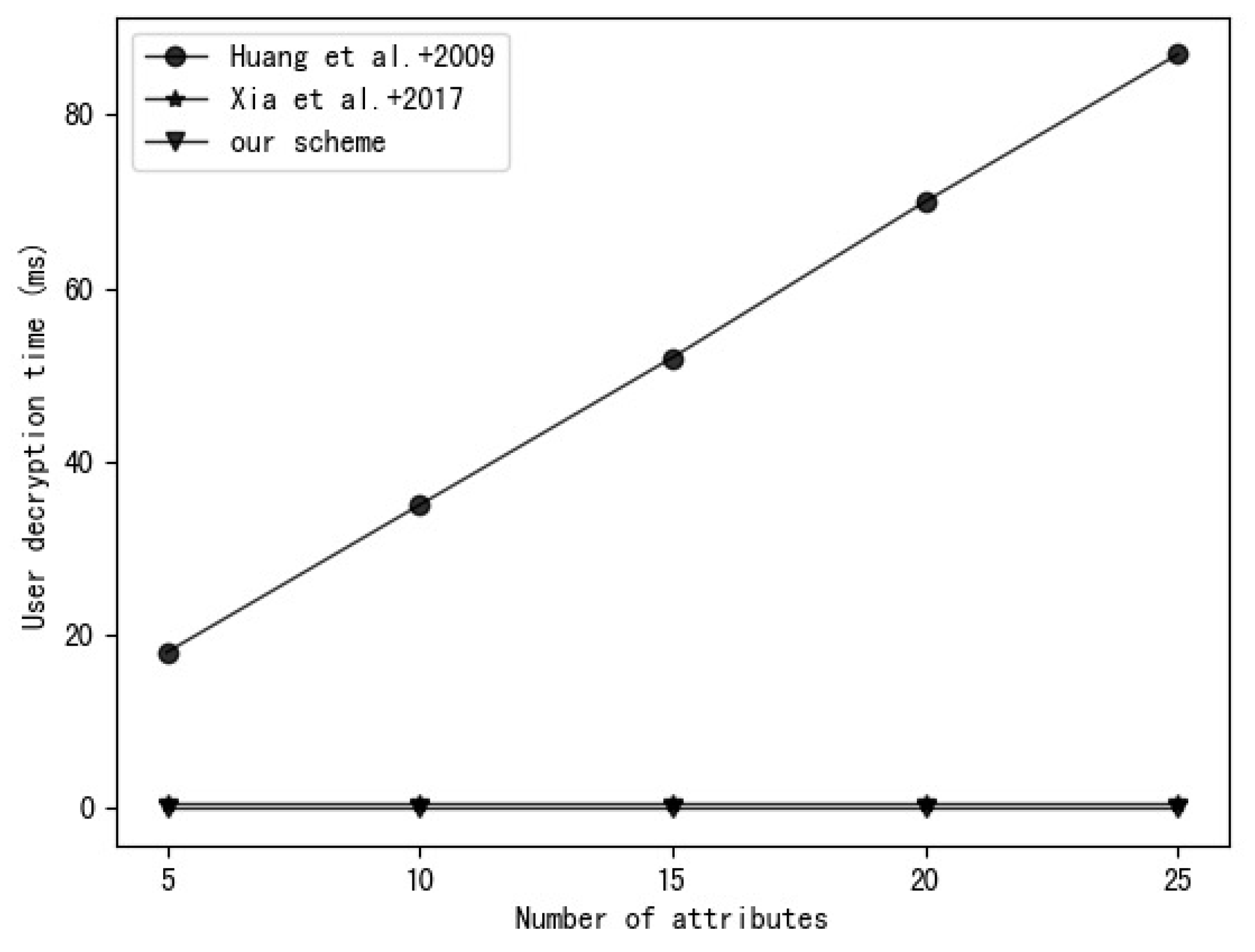
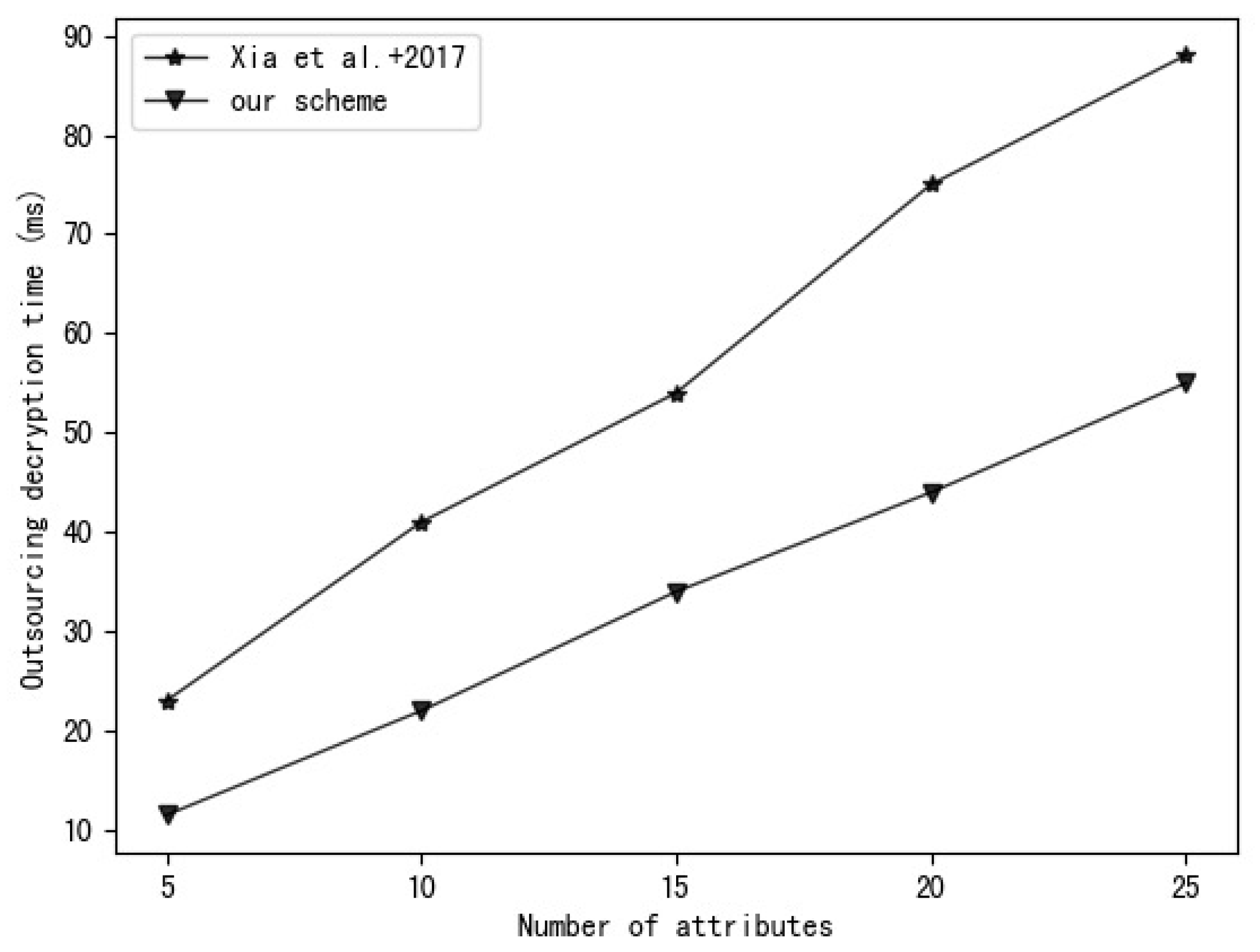
5.2. Experiment Analysis
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
References
- Kumar, V.; Mishra, S.; Chand, N. Applications of VANETs: Present & Future. Commun. Netw. 2013, 5, 12–15. [Google Scholar]
- Di Pietro, R.; Guarino, S.; Verde, N.V.; Domingo-Ferrer, J. Security in wireless ad-hoc networks—A survey. Comput. Commun. 2014, 51, 1–20. [Google Scholar] [CrossRef]
- Servos, D.; Osborn, S.L. Current Research and Open Problems in Attribute-Based Access Control. ACM Comput. Surv. 2017, 49, 4. [Google Scholar] [CrossRef]
- Aftab, M.U.; Habib, M.A.; Mehmood, N.; Aslam, M.; Irfan, M. Attributed role based access control model. In Proceedings of the 2015 Conference on Information Assurance and Cyber Security (CIACS), Rawalpindi, Pakistan, 18 December 2015; IEEE: Piscataway, NJ, USA, 2015; pp. 83–89. [Google Scholar]
- Ostrovsky, R.; Sahai, A.; Waters, B. Attribute-based encryption with non-monotonic access structures. In Proceedings of the 14th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 31 October–2 November 2007; Association for Computing Machinery: New York, NY, USA, 2007; pp. 195–203. [Google Scholar]
- Cheung, L.; Newport, C. Provably secure ciphertext policy ABE. In Proceedings of the 14th ACM conference on Computer and Communications Security, Alexandria, VA, USA, 31 October–2 November 2007; pp. 456–465. [Google Scholar]
- Sahai, A.; Waters, B. Fuzzy identity-based encryption. In Proceedings of the Advances in Cryptology—EUROCRYPT 2005: 24th Annual International Conference on the Theory and Applications of Cryptographic Techniques, Aarhus, Denmark, 22–26 May 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 457–473. [Google Scholar]
- Goyal, V.; Pandey, O.; Sahai, A.; Waters, B. Attribute-based encryption for fine-grained access control of encrypted data. In Proceedings of the 13th ACM Conference on Computer and Communications Security, Alexandria, VA, USA, 30 October–3 November 2006; Association for Computing Machinery: New York, NY, USA, 2006; pp. 89–98. [Google Scholar]
- Bethencourt, J.; Sahai, A.; Waters, B. Ciphertext-policy attribute-based encryption. In Proceedings of the 2007 IEEE Symposium on Security and Privacy (SP’07), Berkeley, CA, USA, 20–23 May 2007; IEEE: Piscataway, NJ, USA, 2007; pp. 321–334. [Google Scholar]
- Liu, J.K.; Yuen, T.H.; Zhang, P.; Liang, K. Time-based direct revocable ciphertext-policy attribute-based encryption with short revocation list. In Proceedings of the Applied Cryptography and Network Security: 16th International Conference, ACNS 2018, Leuven, Belgium, 2–4 July 2018; Springer International Publishing: Berlin/Heidelberg, Germany, 2018; pp. 516–534. [Google Scholar]
- Wang, H.; Zheng, Z.; Wu, L.; Li, P. New directly revocable attribute-based encryption scheme and its application in cloud storage environment. Clust. Comput. 2017, 20, 2385–2392. [Google Scholar] [CrossRef]
- Li, J.; Sha, F.; Zhang, Y.; Huang, X.; Shen, J. Verifiable outsourced decryption of attribute-based encryption with constant ciphertext length. Secur. Commun. Netw. 2017, 2017, 3596205. [Google Scholar] [CrossRef]
- Zhang, R.; Ma, H.; Lu, Y. Fine-grained access control system based on fully outsourced attribute-based encryption. J. Syst. Softw. 2017, 125, 344–353. [Google Scholar] [CrossRef]
- Wang, W.; Qi, F.; Wu, X.; Tang, Z. Distributed multi-authority attribute-based encryption scheme for friend discovery in mobile social networks. Procedia Comput. Sci. 2016, 80, 617–626. [Google Scholar] [CrossRef]
- Fu, X.; Nie, X.; Li, F. Black box traceable ciphertext policy attribute-based encryption scheme. Information 2015, 6, 481–493. [Google Scholar] [CrossRef]
- Odelu, V.; Das, A.K. Design of a new CP-ABE with constant-size secret keys for lightweight devices using elliptic curve cryptography. Secur. Commun. Netw. 2016, 9, 4048–4059. [Google Scholar] [CrossRef]
- Ding, S.; Li, C.; Li, H. A novel efficient pairing-free CP-ABE based on elliptic curve cryptography for IoT. IEEE Access 2018, 6, 27336–27345. [Google Scholar] [CrossRef]
- Huang, D.; Verma, M. ASPE: Attribute-based secure policy enforcement in vehicular ad hoc networks. Ad Hoc Netw. 2009, 7, 1526–1535. [Google Scholar] [CrossRef]
- Horng, S.J.; Lu, C.C.; Zhou, W. An identity-based and revocable data-sharing scheme in VANETs. IEEE Trans. Veh. Technol. 2020, 69, 15933–15946. [Google Scholar] [CrossRef]
- Xia, Y.; Chen, W.; Liu, X.; Zhang, L.; Li, X.; Xiang, Y. Adaptive multimedia data forwarding for privacy preservation in vehicular ad-hoc networks. IEEE Trans. Intell. Transp. Syst. 2017, 18, 2629–2641. [Google Scholar] [CrossRef]
- Zhang, J.; Li, T.; Obaidat, M.S.; Lin, C.; Ma, J. Enabling efficient data sharing with auditable user revocation for IoV systems. IEEE Syst. J. 2021, 16, 1355–1366. [Google Scholar] [CrossRef]
- Wang, T.; Kang, L.; Duan, J. Dynamic fine-grained access control scheme for vehicular ad hoc networks. Comput. Netw. 2021, 188, 107872. [Google Scholar] [CrossRef]
- Jahid, S.; Borisov, N. Piratte: Proxy-based immediate revocation of attribute-based encryption. arXiv 2012, arXiv:1208.4877. [Google Scholar]
- Umayya, Z.; Sethia, D. Pro-SRCC: Proxy-based scalable revocation for constant ciphertext length. In Proceedings of the SECURWARE 2018: The Twelfth International Conference on Emerging Security Information, Systems and Technologies, Venice, Italy, 16–20 September 2018; pp. 58–66. [Google Scholar]



| Scheme | Bilinear Pairing | Scalar Multiplication | Outsourced Computing | Integrit yVerification |
|---|---|---|---|---|
| Scheme in [16] | No | Yes | No | No |
| Scheme in [17] | No | Yes | No | No |
| Scheme in [18] | Yes | No | No | No |
| Scheme in [20] | Yes | No | Yes | No |
| Our Scheme | No | Yes | Yes | Yes |
| Scheme | User Encryption | User Decryption | Outsourcing Decryption |
|---|---|---|---|
| Scheme in [16] | — | ||
| Scheme in [17] | — | ||
| Scheme in [18] | — | ||
| Scheme in [20] | |||
| Our Scheme |
| Operations | |||
|---|---|---|---|
| Time | 3.5 ms | 1.76 ms | 1.16 ms |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Liu, Y.; Xu, S.; Yue, Z. A Lightweight CP-ABE Scheme with Direct Attribute Revocation for Vehicular Ad Hoc Network. Entropy 2023, 25, 979. https://doi.org/10.3390/e25070979
Liu Y, Xu S, Yue Z. A Lightweight CP-ABE Scheme with Direct Attribute Revocation for Vehicular Ad Hoc Network. Entropy. 2023; 25(7):979. https://doi.org/10.3390/e25070979
Chicago/Turabian StyleLiu, Yilong, Shengwei Xu, and Ziyan Yue. 2023. "A Lightweight CP-ABE Scheme with Direct Attribute Revocation for Vehicular Ad Hoc Network" Entropy 25, no. 7: 979. https://doi.org/10.3390/e25070979
APA StyleLiu, Y., Xu, S., & Yue, Z. (2023). A Lightweight CP-ABE Scheme with Direct Attribute Revocation for Vehicular Ad Hoc Network. Entropy, 25(7), 979. https://doi.org/10.3390/e25070979







