A Kind of (t, n) Threshold Quantum Secret Sharing with Identity Authentication
Abstract
1. Introduction
2. Preliminaries
2.1. Quantum Measurement
2.2. Mutually Unbiased Bases
2.3. QFT, IQFT
2.4. Operation
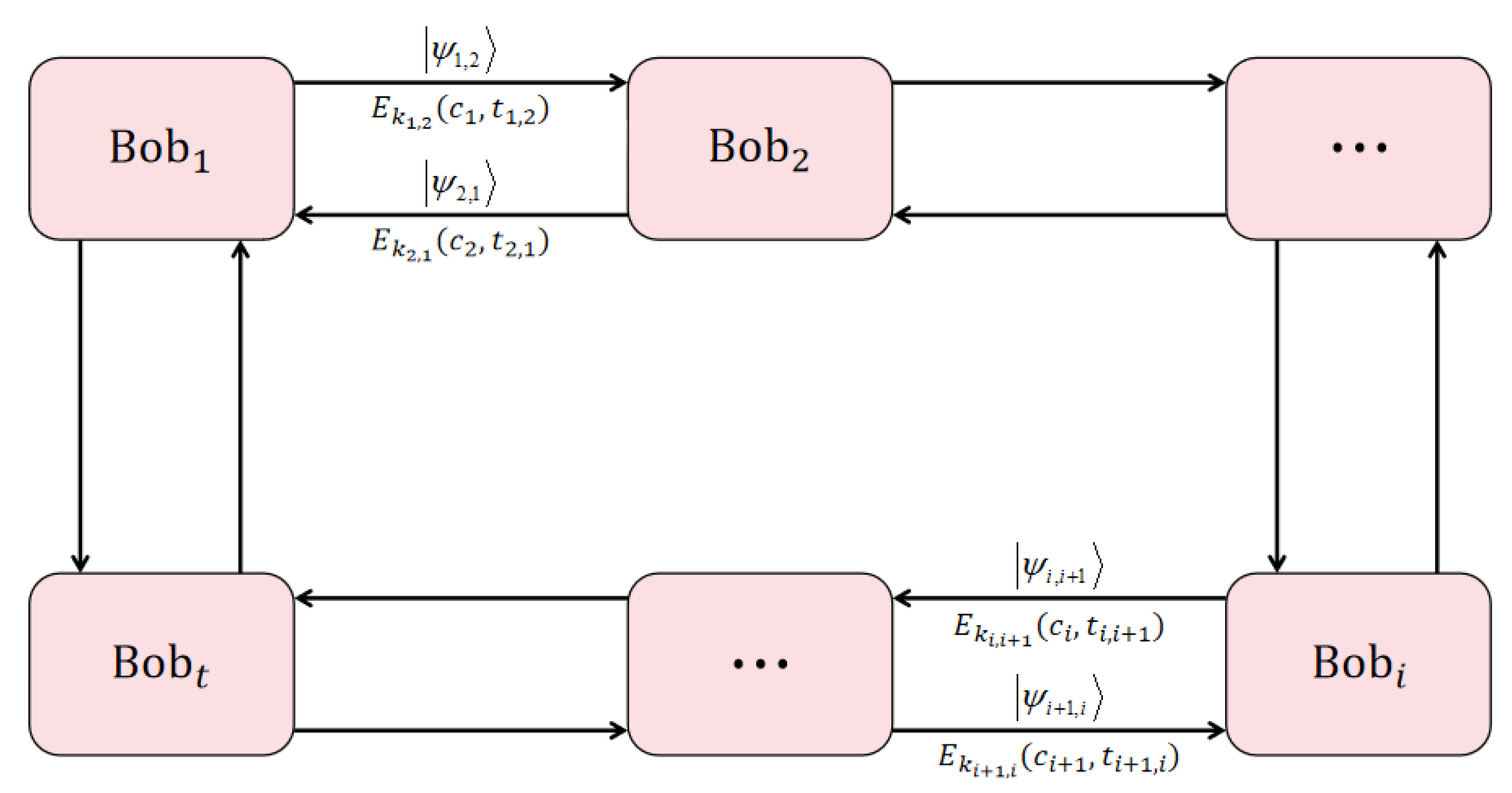
3. Proposed Protocol
3.1. Secret-Sharing Phase
3.2. Secret-Recovery Phase
4. Correctness Analysis
5. Security Analysis
5.1. Intercept–Resend Attack
5.2. Entangle–Measure Attack
5.3. Collusion Attack
5.4. Forgery Attack
6. Scheme Comparison
7. Example
7.1. Secret-Sharing Phase
7.2. Secret-Recovery Phase
8. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Shamir, A. How to share a secret. Commun. ACM 1979, 22, 612–613. [Google Scholar] [CrossRef]
- Hillery, M.; Buzk, V.; Berthiaume, A. Quantum secret sharing. Phys. Rev. A 1999, 59, 1829–1834. [Google Scholar] [CrossRef]
- Yang, W.; Huang, L.; Shi, R. Secret sharing based on quantum Fourier transform. Quantum Inf. Process. 2013, 12, 2465–2474. [Google Scholar] [CrossRef]
- Tavakoli, A.; Herbauts, I.; Zukowski, M.; Bourennane, M. Secret sharing with a single d-level quantum system. Phys. Rev. A 2015, 92, 030302. [Google Scholar] [CrossRef]
- Tsai, C.W.; Yang, C.W.; Lin, J. Multiparty mediated semi-quantum secret sharing protocol. Quantum Inf. Process. 2022, 21, 63. [Google Scholar] [CrossRef]
- Chou, Y.H.; Zeng, G.J.; Chen, X.Y.; Kuo, S.Y. Multiparty weighted threshold quantum secret sharing based on the Chinese remainder theorem to share quantum information. Sci. Rep. 2021, 11, 6093. [Google Scholar] [CrossRef]
- Song, X.L.; Liu, Y.B.; Deng, H.Y.; Xiao, Y.G. (t, n) Threshold d-Level Quantum Secret Sharing. Sci. Rep. 2017, 7, 6366. [Google Scholar] [CrossRef]
- Sutradhar, K.; Om, H. Efficient quantum secret sharing without a trusted player. Quantum Inf. Process. 2020, 19, 73. [Google Scholar] [CrossRef]
- Mashhadi, S. Improvement of a (t, n) threshold d-level quantum secret sharing scheme. J. Appl. Secur. Res. 2022, 17, 123–134. [Google Scholar] [CrossRef]
- Li, F.L.; Yan, J.Y.; Zhu, S.X. General quantum secret sharing scheme based on two qudit. Quantum Inf. Process. 2021, 20, 328. [Google Scholar] [CrossRef]
- Cao, W.F.; Yang, Y.G. Verififiable quantum secret sharing protocols based on four-qubit entangled states. Int. J. Theor. Phys. 2019, 58, 1202–1214. [Google Scholar] [CrossRef]
- Lu, C.B.; Miao, F.Y.; Hou, J.P.; Huang, W.C.; Y, X. A verifiable framework of entanglement-free quantum secret sharing with information-theoretical security. Quantum Inf. Process. 2020, 19, 24. [Google Scholar] [CrossRef]
- Li, F.L.; Hu, H.; Zhu, S.X.; Yan, J.Y.; Ding, J. A verifiable (k, n) threshold dynamic quantum secret sharing scheme. Quantum Inf. Process. 2022, 21, 259. [Google Scholar] [CrossRef]
- Yan, C.H.; Li, Z.H.; Liu, L.; Lu, D.J. Cheating identifiable (k, n) threshold quantum secret sharing scheme. Quantum Inf. Process. 2022, 21, 8. [Google Scholar] [CrossRef]
- Yang, Y.G.; Wen, Q.Y.; Zhang, X. Multiparty simultaneous quantum identity authentication with secret sharing. Sci. China Phys. Mech. Astron. 2008, 51, 321–327. [Google Scholar] [CrossRef]
- Abulkasim, H.; Hamad, S.; Khalifa, A.; Bahnasy, K.E. Quantum secret sharing with identity authentication based on Bell states. Int. J. Quantum Inf. 2017, 15, 1750023. [Google Scholar] [CrossRef]
- Hu, W.W.; Zhou, R.G.; Li, X.; Fan, P.; Tan, C.Y. A novel dynamic quantum secret sharing in high-dimensional quantum system. Quantum Inf. Process. 2021, 20, 159. [Google Scholar] [CrossRef]
- Liu, J.Y.; Zhou, X.Y.; Wang, Q. Reference-frame-independent measurement-device-independent quantum key distribution using fewer states. Phys. Rev. A 2021, 103, 022602. [Google Scholar] [CrossRef]
- Li, W.; Wang, L.; Zhao, S.M. Extended single-photon entanglement based phase-matching quantum key distribution. Quantum Inf. Process. 2022, 21, 124. [Google Scholar] [CrossRef]
- Liu, B.; Gao, Z.; Xiao, D.; Huang, W.; Liu, X.; Xu, B. Quantum identity authentication in the orthogonal-state-encoding QKD system. Quantum Inf. Process. 2019, 18, 137. [Google Scholar] [CrossRef]
- Ljunggren, D.; Bourennane, M.; Karlsson, A. Authority-based user authentication in quantum key distribution. Phys. Rev. A 2002, 62, 022305. [Google Scholar] [CrossRef]
- Dutta, A.; Pathak, A. A short review on quantum identity authentication protocols: How would bob know that he is talking with alice? Quantum Inf. Process. 2022, 21, 369. [Google Scholar] [CrossRef]
- Bostrom, K.; Felbinger, T. Deterministic secure direct communicationusing entanglement. Phys. Rev. Lett. 2002, 89, 187902. [Google Scholar] [CrossRef] [PubMed]
- Bufalo, M.; Bufalo, D.; Orlando, G. A Note on the Computation of the Modular Inverse for Cryptography. Axioms 2021, 10, 116. [Google Scholar] [CrossRef]
- Zou, X.F.; W, Q.D. Security analysis and improvements of arbitrated quantum signature schemes. Phys. Rev. A 2010, 82, 042325. [Google Scholar] [CrossRef]
- Wang, T.Y.; Wen, Q.Y. Security of a kind of quantum secret sharing with single photons. Quant. Inf. Comput. 2011, 11, 434–443. [Google Scholar] [CrossRef]
- Wang, T.Y.; Liu, Y.Z.; Wei, C.Y.; Cai, X.Q.; Ma, J.F. Security of a kind of quantum secret sharing with entangled states. Sci. Rep. 2017, 7, 2485. [Google Scholar] [CrossRef]
- Colbeck, R. Impossibility of secure two-party classical computation. Phys. Rev. A 2007, 76, 062308. [Google Scholar] [CrossRef]
- Mayers, D. Unconditional security in quantum cryptography. J. ACM 2001, 48, 351–406. [Google Scholar] [CrossRef]

| Protocols | Yang [3] | Song [7] | Sutradhar [8] | Mashhadi [9] | Our |
|---|---|---|---|---|---|
| N | Y | Y | Y | Y | |
| QFT | n | 1 | 2 | 1 | 1 |
| IQFT | - | 1 | 2 | t | 1 |
| measurement operation | n | 1 | 2 | t | |
| dimensional space | d | d | d | d | d |
| message particle | t | t | |||
| hash function | 2 | 2 | 2 | 2 | 2 |
| intercept–resend | - | Y | Y | N | Y |
| entangle–measure | - | Y | Y | Y | Y |
| collusive attack | N | Y | N | N | Y |
| forgery attack | - | Y | Y | Y | Y |
| identity authentication | N | N | N | N | Y |
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Meng, D.; Li, Z.; Luo, S.; Han, Z. A Kind of (t, n) Threshold Quantum Secret Sharing with Identity Authentication. Entropy 2023, 25, 827. https://doi.org/10.3390/e25050827
Meng D, Li Z, Luo S, Han Z. A Kind of (t, n) Threshold Quantum Secret Sharing with Identity Authentication. Entropy. 2023; 25(5):827. https://doi.org/10.3390/e25050827
Chicago/Turabian StyleMeng, Depeng, Zhihui Li, Shuangshuang Luo, and Zhaowei Han. 2023. "A Kind of (t, n) Threshold Quantum Secret Sharing with Identity Authentication" Entropy 25, no. 5: 827. https://doi.org/10.3390/e25050827
APA StyleMeng, D., Li, Z., Luo, S., & Han, Z. (2023). A Kind of (t, n) Threshold Quantum Secret Sharing with Identity Authentication. Entropy, 25(5), 827. https://doi.org/10.3390/e25050827








