Abstract
Quantum key distribution (QKD) allows two remote parties to share information-theoretic secret keys. Many QKD protocols assume the phase of encoding state can be continuous randomized from 0 to , which, however, may be questionable in the experiment. This is particularly the case in the recently proposed twin-field (TF) QKD, which has received a lot of attention since it can increase the key rate significantly and even beat some theoretical rate-loss limits. As an intuitive solution, one may introduce discrete-phase randomization instead of continuous randomization. However, a security proof for a QKD protocol with discrete-phase randomization in the finite-key region is still missing. Here, we develop a technique based on conjugate measurement and quantum state distinguishment to analyze the security in this case. Our results show that TF-QKD with a reasonable number of discrete random phases, e.g., 8 phases from , can achieve satisfactory performance. On the other hand, we find the finite-size effects become more notable than before, which implies that more pulses should be emit in this case. More importantly, as a the first proof for TF-QKD with discrete-phase randomization in the finite-key region, our method is also applicable in other QKD protocols.
1. Introduction
Quantum key distribution (QKD) [1,2],one of the most successful and mature applications in quantum information science, allows for two legitimate parties (Alice and Bob) to share information-theoretic secret keys. In theory, its security has been proved [3,4,5], while experiments towards a higher key rate [6] and longer achievable distance [7,8,9,10] have been demonstrated. Still, some large scale QKD networks are emerging [11,12,13,14]. However, owing to the inherent photon-loss in the channel, it meets a vital bottleneck that limits the communication distance and key generation rate. Specifically, some fundamental rate-loss limits [15,16] impose a restriction on any point-to-point QKD without repeaters. More precisely, the key rate R is bounded by the channel transmission probability with the linear PLOB bound [16]. Delightfully, M.Lucamarini et al. made a breakthrough by proposing twin-field (TF) QKD in 2018. The essential idea of TF-QKD is in code mode extracting the key bit from a single-photon click event of the measurement station located in the middle of channel, which happens with a probability proportional to ; thus, surpassing the linear PLOB bound becomes possible, and a so-called phase-error rate may be estimated in decoy mode [17,18,19] to monitor security. Driven by this, several TF-type QKD protocols [20,21,22,23,24,25,26] were proposed later to complete security proofs and improve performance. Based on these protocols, experimentalists also made great efforts to realize TF-QKD [27,28,29,30,31,32,33,34,35].
Since TF-QKD inherits measurement-device-independent (MDI)-QKD’s [36] merit that is immune to all side-channel attacks to measurement devices and all measurement-device imperfections [37,38], one does not need to take the detection loopholes into account within the TF-type QKD system. In spite of this, the security issues of the state preparation in TF-QKD must be carefully considered. In practice, the laser source of TF-QKD is usually a continuous source emitting coherent states with a fixed phase. Meanwhile, continuous phase-randomization from 0 to is required in the TF-QKD. More specifically, this continuous phase-randomization is assumed in both the code and test modes in Refs. [21,23,26], or at least in the test mode in Refs. [22,24,39]. To fulfill this requirement, Alice and Bob must randomize the global phase continuously and uniformly. Unluckily, two ways to achieve phase randomization introduce different problems in the experiment. Passive randomization will lead to phase correlations between adjacent pulses [40,41], while active randomization can only randomize the phase over discrete set of values.
To bridge this gap between theory and experiment, two works that analyzed the security of fully discrete-phase randomization TF-QKD protocol have been proposed [42,43,44] in these days. However, a security proof in the finite-key region is still missing. Hence, one natural question is that whether TF-QKD with fully discrete-phase randomization can work well non-asymptotically. This work affirms that it can.
In this paper, we analyze the security of TF-QKD protocol with fully discrete randomization in a finite-key region. Interestingly, our analysis leads to comparable performance with the continuous one. Since taking the discrete phase into account, our results make the TF-QKD more practical and can be applied to the future TF-QKD experiment. More importantly, some techniques proposed here, e.g., Lemma A1 (introduced later), can be utilized to analyze the security of other QKD protocols with discrete-phase randomization.
This work is organized as follows. In Section 2, we give a description of the TF-QKD protocol with fully discrete-phase randomization, and the sketch of the security proof is given in Section 3. Note that the proof is detailed in Appendix A. In Section 4, by the numerical simulation, we show this protocol can still beat the linear PLOB bound [16] and has satisfactory performance. Finally, a conclusion is given in Section 5.
2. Protocol Description
Indeed, the protocol analyzed here has been depicted in Ref. [43]. For ease of understanding, we illustrate the protocol as follows.
Step 1: Alice (Bob) chooses a label from with probabilities , according to the label she (he) chooses, she (he) takes one of the following actions:
: she (he) randomly picks an integer () from with equal probability where M is an even integer. This means that the phase 2 is divided into M parts. Then, she (he) randomly chooses a key bit where . Finally, she (he) sends a pulse with a coherent state ( ).
: she (he) sends the vacumm state.
: she (he) randomly picks an integer and from with equal probability where M is an even integer. This means that the phase 2 is divided into M parts. Then, she (he) sends a pulse with a coherent state ( ).
The first case is called code mode, while the other cases are decoy mode.
Step 2: Alice and Bob repeat Step 1 in total of times.
Step 3: After receiving pairs of pulses from Alice and Bob, interfering each pair at a beamsplitter and measuring the two outputs with his single photon detectors (SPDs), an honest Eve announces whether or not each measurement is successful. Here, ’successful’ means only one SPD (left SPD or right SPD) clicks in the corresponding measurement, and if so, Eve reports the specific SPD clicked.
Step 4: For those rounds Eve announcing successful click, Alice and Bob announce the intensities they chose as well as the values of and . Then, Alice and Bob only retain those successful rounds in which the intensities of the coherent state they sent are same while the in-phase () or anti-phase () condition is also met. Let () be the number of the retained rounds when both Alice and Bob chose the same intensity of the coherent state and the in-phase (anti-phase) is also met. Note that we assume always holds in the case of . Alice and Bob generate their sifted keys from retained rounds in code mode, thus the length of sifted key bits . Note that if it is an in-phase (anti-phase) round with right (left) SPD clicking, Bob may flip his corresponding sifted key bit.
Step 5: With all of the quantities , Alice and Bob use linear programming to obtain an upper bound on the number of phase errors(defined later) with a failure probability no more than ; then, they can calculate the upper bound .
Step 6: Step 6 consists of error correction and privacy amplification.
Step 6a: Alice sends bits of syndrome information of her sifted key bits to Bob through an authenticated public channel. Then, Bob uses it to correct errors in his sifted keys. Alice and Bob calculate a hash of their error-corrected keys with a random universal hash function and check whether they are equal. If equal, they continue to the next step; otherwise, they abort the protocol.
Step 6b: Alice and Bob apply the privacy amplification to obtain their final secret keys. If the length of their secret key satisfies where denotes the binary Shannon entropy, this protocol must be -correct and -secret with . Here, () represents the protocol is correct (secret) with a failure probability no more than . Hence, the total security parameter is -secure where . It is elaborated thoroughly in the widely-used universally composable security framework [45,46].
3. Security Proof
In this section, we present the security proof of this protocol. The main task of the security proof is to bound the information Eve holds. To accomplish this task, one can calculate a so-called phase-error rate. Firstly, we construct an equivalent virtual protocol, in which Alice and Bob prepare some entangled states between local states and traveling states, but traveling states must have the same density matrices as actual protocol in the channel. The sifted key bits can be seen as the outputs of measurement with Z-basis on local states made by Alice and Bob; then, the so-called phase-error rate is defined as the error rate for the outputs of measurement with the X-basis made by them. According to the complementarity argument [47], the phase-error rate can be used to bound Eve’s information on the sifted keys. In the following, we give the virtual protocol and show how to bound the phase-error rate.
3.1. Equivalent Virtual Protocol
In our virtual protocol, Alice generates secret keys from the code mode in which she prepares the state
where and A are the local quantum systems in Alice’s side, and a is the traveling quantum state Alice sent to Eve. Similarly, Bob prepares defined analogously to . Obviously, Alice (Bob) measures with Z-basis to obtain sifted key, i.e., for bit 0 and for bit 1. In order to obtain the phase-error rate, they measure in X-basis after Eve’s attack. As for the test mode, we assume Alice prepares the following states
here, the local states of are encoded in photon-number states, and Alice can measure ’s photon-number to learn the phase of sent states.
Finally, we can describe the process of state preparation above with a single state, namely,
where Alice’s additional local ancilla is in the photon number states. Similarly, Bob can prepare defined analogously to . Though Alice (Bob) may measure (),, and A(B) after or before Eve announcing her measurement results, Alice (Bob) must announce the measurement results after Eve’s announcement then post-select the successful rounds. The following is a detailed illustration of our equivalent virtual protocol.
Step 1:
Alice and Bob prepare a gigantic quantum state and send all subsystems a and b to Eve through an insecure quantum channel.
Step 2:
After performing an arbitrary quantum operation on all subsystems a and b from Alice and Bob, Eve announces whether it has a successful click (only one of her SPDs clicks) or not for each round. For a successful round, Eve continues to announce whether the left SPD clicks or the right SPD clicks. We use () to denote the set of successful (unsuccessful) rounds.
Step 3:
For those rounds in which Eve announces success, Alice and Bob jointly measure the subsystem () and in the photon-number basis to learn whether the intensities of the coherent state they send are same or not and whether it is in-phase or anti-phase. Then, they only retain those rounds where in-phase or anti-phase is met, and they choose the same intensities. Let denote the set of those retained rounds, while denotes those rounds that are in but not in .
Step 4:
For these rounds in , Alice (Bob) measures the subsystem () in Fock basis to learn the phase and intensity of the coherent states she (he) sent. If the result of () is in state (), she (he) measures subsystems A(B) in the Z basis to decide her (his) sifted key, respectively; otherwise, she (he) measures subsystem A(B) in the Z basis but does not incorporate these measurement outcomes in her (his) sifted key.
Step 5 to Step 6:
Let be the number of rounds in satisfying that both Alice and Bob chose the intensity . With parameters , perform the same operations as Step 5 to Step 6, respectively, in the actual protocol given in Section 2.
3.2. Estimation of Phase-Error Rate
The essential of security proof is to estimate the upper-bound of the phase-error rate of the sifted keys, i.e., how many same or different outcomes Alice and Bob have if they measure A and B with X-basis hypothetically in the rounds where sifted keys are generated. Specifically, in our protocol, we define the number of the same outcomes they have as , i.e., the number of phase-error events. Provided that is bounded, one can generate the final secret key with an appropriate value as given in Step6.b of the actual protocol.
A detailed proof for how to estimate is present in Appendix A. Here, a sketch of this proof is given.
Though analyzing the equivalent protocol, it is proven that if Alice and Bob both chose intensity , and in-phase or anti-phase is also met, they actually prepare a mixture , which consists of component . Moreover, each phase-error event is a click by some particular components of that mixture , i.e., . These results imply that
where denotes the number of rounds in , in which Alice and Bob both chose intensity , but is actually . Meanwhile, is the set of even numbers. Now, the hypothetical value is related to some experimentally observed values. However, just with these equations it is difficult to bound tightly since cannot be known directly.
On the other hand, both and are very close to Fock-state . Accordingly, it is intuitive to consider if there are constraints on the gap between and . Then, we developed Lemma A1 (see Appendix A for details) to bound the gap between the yields of two distinct quantum states in a non-asymptotic situation. Applying this lemma, we obtained a series of constraints on and . Finally, combined with Equation (4), an analytical upper bound of (given in the end of the Appendix A) was calculated to find the upper bound of phase-error rate .
4. Numerical Simulation
In this section, we simulate the final secret key rate with the parameters listed in Table 1.

Table 1.
List of parameters uesd in the numerical simulations. Here, is loss-independent misalignment error rate due to optical imperfect interference, is dark counting probability for each SPD, is fiber loss constant, denotes detection efficiency of each SPD, f is error-correction inefficiency, and denotes the total security coefficient.
It is reasonable to simulate the experimentally observed values , and with their mean values. Let be the probability of only one click from left (right) SPD when both Alice and Bob prepare coherent states with intensity and a phase difference of 0 (), and be the probability of only one click from left (right) SPD when both Alice and Bob prepare coherent states with intensity and phase difference of (0). Then, we have
where and L is the channel distance between Alice and Bob. Accordingly, in the simulation, we assume for . Note that , and . With these values, setting and the failure probability of estimating phase error , one can obtain the upper-bound of phase-error rate by the linear programming given by (A41) in Appendix A. Moreover, the amount of is , , and , which leads to a secret key of length with and the total security parameter .
Finally, we numerically optimize the intensities and corresponding probabilities to maximize l in the cases of the total number of pulses is . Note that because this numerical problem is very time-comsuming, these intensities and probabilities are not optimized at each distance. Additionally, we use some typical parameters instead. The simulate results ( v.s. L) are illustrated below.
As Figure 1 shows, we obtain considerable secret key rates when the total number of pulses is , , or . Through numerical simulations, it is confirmed that TF-QKD with discrete-phase randomization has satisfactory performance. On the other hand, it is verified that finite-size effects become more notable here compared with the original protocol with continuous phase randomization; it seems that one has to prepare pulses to surpass the PLOB linear bound. This is because the statistical fluctuations in Lemma A1 are proportional to the square root of the total number of emitting pulse , which leads to alarge phase-error rate when is not sufficiently large.
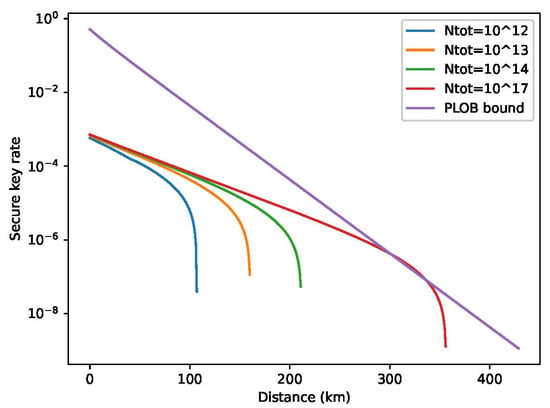
Figure 1.
Secret key rate () of fully discrete TF-QKD [43]. In this figure, the key rate corresponding to the total number of pulses is , plotted above. Note that we set in the simulation.
5. Conclusions
In real setups of TF-QKD, continuous randomization is usually realized by actively adding a random signal to a phase modulator. On the other hand, random numbers are generated discretely in most schemes. Therefore, TF-QKD with discrete-phase randomization is more practical. It is necessary to analyze the security of TF-QKD with discrete-phase randomization. Based on conjugate measurement, the security proof of a QKD protocol is to estimate the phase-error rate. Then in case of discrete-phase randomization, a critical step is knowing how to bound the gap between yields of two distinct but very close quantum states in a non-asymptotic situation. To achieve this goal, Lemma A1 is developed to find the upper bound of this gap. With the help of Lemma 1, linear programming is proposed to calculate the phase-error rate, and the key length is then straightforward. Through numerical simulations, it is confirmed that TF-QKD with discrete-phase randomization has satisfactory performance. On the other hand, we also find that more pulses should be prepared to alleviate the finite-size effects than previous protocol.
Moreover, it is worth noting that Lemma A1 is quite useful in a variety of scenarios, not just in the security proof of TF-QKD. For instance, if one considers the BB84 with discrete-phase randomization [48], the Lemma A1 can be utilized to bound the yield of single photon state, so then it is not difficult to give a relevant security proof. To summarize, we give the first security proof for TF-QKD with finite discrete-phase randomization in non-asymptotic scenarios. Although the proof is tailored for TF-QKD, the framework of this proof, i.e. Lemma A1, can be adapted in other protocols.
Author Contributions
Methodology, R.-Q.W.; Software, R.-Q.W. and X.-H.J.; Validation, R.-Q.W., Z.-Q.Y. and X.-H.J.; Formal analysis, R.-Q.W. and R.W.; Resources, S.W., W.C., Z.-F.H. and G.-C.G.; Data curation, X.-H.J.; Writing—original draft, R.-Q.W.; Writing—review and editing, Z.-Q.Y.; Visualization, R.-Q.W.; Project administration, Z.-Q.Y.; Funding acquisition, Z.-Q.Y. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Key Research and Development Program of China (Grant No. 2020YFA0309802),the National Natural Science Foundation of China (Grant Nos. 62171424, 61961136004).
Institutional Review Board Statement
Not applicable.
Informed Consent Statement
Not applicable.
Data Availability Statement
Not applicable.
Acknowledgments
We thank Rong-Wang for constructive discussion.
Conflicts of Interest
The authors declare no conflict of interest.
Appendix A
Appendix A.1. Formula for the Number of Phase-Error Events
In this section, we show how to obtain the relation between the hypothetical phase-error events and some experimental observations.
The main result obtained here is that each key bit is a successful click from a mixed state of prepared by Alice and Bob. More importantly, the number of phase-error events among these key bits corresponds to . Therefore, if we denote the length of the raw key by and the number of successful clicks of by , , the number of phase-error events must hold, where is the set of even integers. Next, a proof is present to show how to obtain this result.
Following the symbols in [49], let us consider the evolution of the gigantic quantum state sent to Eve. After Step 2, where Eve performs her measurement on the subsystem , the initial quantum state is transformed to , where denotes the measurement operator of Eve. After measurement, Eve announces whether the measurement outcome is successful or not for each round. Hence, we reorder the quantum state as , where denotes the successful (unsuccessful) rounds. Then, in Step 3 of the virtual protocol, using measurement operators , Alice and Bob measure the subsystem and for those rounds that are announced successful in Step 2 and retain the trials in which and are collapsed into as the final successful rounds. Hence, we reorder where () denotes the successful(unsuccessful) rounds finally. Before they measure the subsystem to generate their sifted key in Step 3, the unnormalized quantum state is given by
Next, in Step 4, Alice and Bob measure the subsystem and for all rounds in , one by one. We use to denote the different rounds in and to denote the measurement outcome of the -th subsystem. What is more, is used to denote the associated operator. Hence, the unnormalized state before the measurement of the -th rounds in is
because we are only interested in the reduced state of the -th round in , we trace out the other rounds which we denote by and obtain
where
and the quantum states represent the basis for the subsystems of all rounds in the protocol except the -th round in .
Next, to derive the number of phase error, we expand the quantum state as
where
and
To summarize, each key bit can be viewed as an event in which Eve announces a successful click conditioned by Alice and prepares and measures with Z-basis. Since the measurement on made by Alice and Bob can be delayed after Eve’s announcement of a successful click, the phase error can be estimated by Alice and Bob measuring with X-basis rather than Z-basis. To obtain the phase error of this part, we rewrite under X-bases of as
where
and . For the purpose of clarification, we define some quantum states below:
and
where and is the set of even numbers. Indeed, is a quantum state satisfying that the total photon-number of a and b is j. Moreover, another similar quantum state is defined below:
and
where . With these definitions, we can write the quantum states and in a more simplified way, namely
and
obviously, the measurement outcome of and can be defined as phase-error event. Recall the whole density matrix given in Equation (A8); we can obtain the part corresponding to the phase-error event,
according to Equations (2.5)–(2.7) of Ref [48], can be rewritten as
where , is the the probability of finding j photons in a Poisson source with mean photon-number , and , and .
For ease of understanding, we can easily interpret the formula of . It is easy to see that is a mixture of , which consists of photon-number state , and the probability of finding photons is proportional to . Let be the normalized ; then, a phase-error event for a key bit is equivalent to a successful click announced by Eve on the condition that a mixture prepared by Alice and Bob, and the probability of preparing such a mixture is obviously .
To find a way to estimate the number of phase errors, we can give the density matrices Alice and Bob prepared in code mode and decoy mode. If we trace out of the quantum state , i.e., regardless of whether the measurement outcome on is phase error or not, we have
we define as the normalized . The generation of a key bit is equivalent to a successful click announced by Eve conditioned on the premise that a mixture is prepared by Alice and Bob, and the probability of preparing such a mixture is obviously .
Now we are approaching a main result of above derivations. In the rounds, Alice and Bob prepare with the probability ; the number of its successful rounds is denoted by . Of course, the key bits are generated in these rounds, thus . Since is a mixture of , the successful clicks are the sum of clicks by . Then, holds evidently, in which is the number of successful clicks by . Recall that the phase errors for these events are from clicks by ; one can assert that the number of phase-error events must hold. This is a main result we have so far.
Appendix A.2. The Upper Bound of the Number of Phase-Error Events
We have proved that with the constraint . Obviously, this is not sufficient for estimating tightly. Here, we resort to decoy states to obtain more constraints to bound .
Similarly with the analysis of clicks by , a successful click from decoy mode with intensity means that Alice and Bob prepare
accordingly, we also have . Here, and are defined analogously to and , respectively. Intuitively, and are the numbers of successful clicks for and respectively. Typically, is satisfied; then both and are very close to the photon-number state . This implies that the gap between and can be bounded, and then we may estimate . Indeed, with the result in appendix B of ref [48], the gap between and in the asymptotic case can be obtained. Here, we develop Lemma A1 to bound this gap in finite-key situations.
Lemma A1.
If Alice prepares pairs of particles A and B with the quantum state where and she sends the B part in each pair to Eve. For every round, Eve announces if the measurement is successful or unsuccessful, which is denoted by or , respectively. Then, Alice measures the subsystem A with projectors to which quantum state she sent for the pairs that Eve announced . Let denote the number of yields for the quantum state . If , we have that the constraints between and , say,
holds with a failure probability , where
Proof.
Since we are only interested in the statistics of and , it is not restrictive to rewrite the quantum state as
Here, we virtually define and , which do not change the density matrix of B; thus, have no impact on Eve’s operation and statistics of and . Let () denote the number of detection for the quantum state () when Eve announces a successful measurement. Apparently, we know that .
Let us focus on the state , by which the relation between and can be analyzed. The essential idea is reinterpreting the detection of B to a game of Eve guessing which states or Alice prepared for all of the trials. Specifically, we consider a virtual experiment illustrated below.
Alice prepares the quantum state ; then, she sends the B part to Eve. Eve measures each B she received. If she obtains a successful measurement, she will announce . Otherwise, she will announce . Up to now, there is no difference from the previous protocol. A critical step is that for any trial that Eve announces , Alice flips corresponding M with probability . Finally, Alice measures all partials A locally. It is obvious that if Alice prepares two quantum states and at random, the maximal probability of Eve guessing correctly which state is prepared is where . With the flip operation, we can apply this maximal probability to our analysis below. In this case, we reinterpret that () means that Eve guessed the quantum state Alice prepared is (), which justifies the lossless assumption. Note that this does not compromise security because as an adversary, Eve can guess in this way. In other words, we can now treat this virtual experiment as a game where Eve tries to guess whether Alice is preparing or . For each of all the trials in such a game, it is well known that Eve’s maximal probability of guessing correctly is . Now, we are ready to find the relation between and by calculating how many trials in which Eve’s guessing is correct. First, means that announcing at first and Alice also preparing , which of course leads to guessing correctly. Then, let () denote Alice preparing the state (), which implies that . As a result, there are trials in which Eve announces at first and then a random flipping operation on M follows; for every such trial, the probability of guessing correctly is obviously . Further considering the potential statistical fluctuations made by the random flipping, with a failure probability of , the number of Eve guessing correctly in the trials is no larger than
where is the upper bound of the statistical fluctuation made by the random flipping of the trials. We let be the probability of the amount of successful detection of quantum state reach . Hence the probability that we get the quantity denoted by Equarion (A24) is . On the other hand, in the trials of guessing and prepared by Alice at random, the probability of Eve guessing correctly is no larger than [50], because the fidelity of and is , Hence, one can assert that when , In this case, we let . Hence, one can assert that with a failure probability ,
holds, where is the upper bound of the statistical fluctuation when Eve’s guessing probability for each trial achieves the upper-bound . Note that because in such a guessing game, conditioned on other trials, the probability of guessing correctly for any fixed trial cannot be larger than , this lemma is applied to any attack. Furthermore, the probability of guessing correctly reaches its maximum, which equals a constant; then, the assumpution of iid holds and the Bernoulli distribution is applied to this case. However, since it is hard to calculate the statistical fluctuation, we use the Chernoff bound to approximate it [51].
According to Equation (A25), we can obtain an upper bound of with a failure probability , say
similarly, if we redefine the guessing correctly as corresponding to and corresponding to , we have that
combining Equation (A26) and Equation (A27), we are clear that
holds with a failure probability .
For simplicity’s sake, we enlarge the R.H.S of Equation (A28). Concretely, we replace by in Equation (A28), say
note that these bounds of statistical fluctuations can be derived by the Chernoff bound [52].
Similarly, because of the probability that Alice sends the quantum state is , using the well-known Chernoff bound [52], we know that
Combing Equation (A29) and Equation (A30), we know that
holds with a failure probability , where and
Finally, to derive the relation between and , we have to consider the relations between and . It is easy to know that on average since there is no way for Eve to distinguish and . Hence, using the Chernoff bound [52] again, we know that
combining Equation (A31) and Equation (A32), we can obtain the inequality Equation (A21).
In conclusion, we complete the proof. □
With Lemma A1, we can derive the constrains between and . Since Alice and Bob send the quantum state ( ) with the probability () and the fidelity between them is . By Lemma A1, we can obtain the relation between and which reads
We let and . If , we have , and
where and
If , we have that , and
where and
One can know that the constraints Equations (A34) and (A35) are nonlinear because of the in or in . To keep the linearity of these constraints for ease of numerical calculations, we replace with and replace with in . That is to say, without compromising the security, we replace Equation (A34) by
and replace Equation (A35) by
moreover, recalling Alice and Bob may both choose intensity 0 and obtain the corresponding number of successful clicks , we have two additional constraints between and which reads
since the probability of both Alice and Bob sending the quantum state is and the fidelity between and ( ) is (), we can obtain the coefficients of these two constraints according to Lemma A1. For simplicity’s sake’s sake, we let and ; then, if , we have and
where and ; otherwise, we have and and
where and .
Similarly, we let and ; then, if , we have and
where and ; otherwise, we have and and
where and .
Now the gaps between v.s. , v.s. , and v.s. have been given. To bound , we can now resort to linear programming below:
For ease of calculation, in all these constraints we let ; then, the total failure probability that we obtain the bound is . Meanwhile, the failure probability that we obtain the last two bounds on is . Hence, the total failure probability of all these constraints is . To conclude, with the help of the linear programming in Equation (A41), one can calculate the upper-bound of .
For simplicity’s sake, we give the analytical solution of this linear programming below. We divide into two parts, say
according to the inequality , we can obtain that the bounds of are
similarly, with the inequality , we have the bounds of , i.e.,
besides the bound , we need to calculate the upper bound of which we derive below. If we set and , according to Equation A33, we have
for . Hence, where hold. Then, combing with the equality , we have
It is easy to prove that
for holds in the case of and . Consequently, we can know that
Finally, we have the upper bound of , say
References
- Ekert, A.K. Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 1991, 67, 661. [Google Scholar] [CrossRef] [PubMed]
- Bennett, C.H.; Brassard, G. Quantum Cryptography: Public Key Distribution and Coin Tossing. In Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, India, 9–12 December 1984. [Google Scholar]
- Mayers, D. Unconditional Security in Quantum Cryptography. J. ACM 2001, 48, 351–406. [Google Scholar] [CrossRef]
- Lo, H.K.; Chau, H.F. Unconditional security of quantum key distribution over arbitrarily long distances. Science 1999, 283, 2050–2056. [Google Scholar] [CrossRef]
- Shor, P.W.; Preskill, J. Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 2000, 85, 441. [Google Scholar] [CrossRef] [PubMed]
- Dixon, A.; Dynes, J.; Lucamarini, M.; Fröhlich, B.; Sharpe, A.; Plews, A.; Tam, S.; Yuan, Z.; Tanizawa, Y.; Sato, H.; et al. High speed prototype quantum key distribution system and long term field trial. Opt. Express 2015, 23, 7583–7592. [Google Scholar] [CrossRef]
- Yin, H.L.; Chen, T.Y.; Yu, Z.W.; Liu, H.; You, L.X.; Zhou, Y.H.; Chen, S.J.; Mao, Y.; Huang, M.Q.; Zhang, W.J.; et al. Measurement-device-independent quantum key distribution over a 404 km optical fiber. Phys. Rev. Lett. 2016, 117, 190501. [Google Scholar] [CrossRef]
- Zhou, Y.H.; Yu, Z.W.; Wang, X.B. Making the decoy-state measurement-device-independent quantum key distribution practically useful. Phys. Rev. A 2016, 93, 042324. [Google Scholar] [CrossRef]
- Liao, S.K.; Cai, W.Q.; Liu, W.Y.; Zhang, L.; Li, Y.; Ren, J.G.; Yin, J.; Shen, Q.; Cao, Y.; Li, Z.P.; et al. Satellite-to-ground quantum key distribution. Nature 2017, 549, 43–47. [Google Scholar] [CrossRef]
- Boaron, A.; Boso, G.; Rusca, D.; Vulliez, C.; Autebert, C.; Caloz, M.; Perrenoud, M.; Gras, G.; Bussières, F.; Li, M.J.; et al. Secure quantum key distribution over 421 km of optical fiber. Phys. Rev. Lett. 2018, 121, 190502. [Google Scholar] [CrossRef] [PubMed]
- Poppe, A.; Peev, M.; Maurhart, O. Outline of the SECOQC quantum-key-distribution network in Vienna. Int. J. Quantum Inf. 2008, 6, 209–218. [Google Scholar] [CrossRef]
- Sasaki, M.; Fujiwara, M.; Ishizuka, H.; Klaus, W.; Wakui, K.; Takeoka, M.; Miki, S.; Yamashita, T.; Wang, Z.; Tanaka, A.; et al. Field test of quantum key distribution in the Tokyo QKD Network. Opt. Express 2011, 19, 10387–10409. [Google Scholar] [CrossRef] [PubMed]
- Wang, S.; Chen, W.; Yin, Z.Q.; Li, H.W.; He, D.Y.; Li, Y.H.; Zhou, Z.; Song, X.T.; Li, F.Y.; Wang, D.; et al. Field and long-term demonstration of a wide area quantum key distribution network. Opt. Express 2014, 22, 21739–21756. [Google Scholar] [CrossRef]
- Chen, Y.A.; Zhang, Q.; Chen, T.Y.; Cai, W.Q.; Liao, S.K.; Zhang, J.; Chen, K.; Yin, J.; Ren, J.G.; Chen, Z.; et al. An integrated space-to-ground quantum communication network over 4,600 kilometres. Nature 2021, 589, 214–219. [Google Scholar] [CrossRef] [PubMed]
- Takeoka, M.; Guha, S.; Wilde, M.M. Fundamental rate-loss tradeoff for optical quantum key distribution. Nat. Commun. 2014, 5, 1–7. [Google Scholar] [CrossRef] [PubMed]
- Pirandola, S.; Laurenza, R.; Ottaviani, C.; Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 2017, 8, 1–15. [Google Scholar] [CrossRef]
- Hwang, W.Y. Quantum key distribution with high loss: Toward global secure communication. Phys. Rev. Lett. 2003, 91, 057901. [Google Scholar] [CrossRef]
- Lo, H.K.; Ma, X.; Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 2005, 94, 230504. [Google Scholar] [CrossRef]
- Wang, X.B. Beating the photon-number-splitting attack in practical quantum cryptography. Phys. Rev. Lett. 2005, 94, 230503. [Google Scholar] [CrossRef]
- Tamaki, K.; Lo, H.K.; Wang, W.; Lucamarini, M. Information theoretic security of quantum key distribution overcoming the repeaterless secret key capacity bound. arXiv 2018, arXiv:1805.05511. [Google Scholar]
- Ma, X.; Zeng, P.; Zhou, H. Phase-matching quantum key distribution. Phys. Rev. X 2018, 8, 031043. [Google Scholar] [CrossRef]
- Curty, M.; Azuma, K.; Lo, H.K. Simple security proof of twin-field type quantum key distribution protocol. NPJ Quantum Inf. 2019, 5, 1–6. [Google Scholar] [CrossRef]
- Wang, X.B.; Yu, Z.W.; Hu, X.L. Twin-field quantum key distribution with large misalignment error. Phys. Rev. A 2018, 98, 062323. [Google Scholar] [CrossRef]
- Lin, J.; Lütkenhaus, N. Simple security analysis of phase-matching measurement-device-independent quantum key distribution. Phys. Rev. A 2018, 98, 042332. [Google Scholar] [CrossRef]
- Yin, H.L.; Fu, Y. Measurement-device-independent twin-field quantum key distribution. Sci. Rep. 2019, 9, 1–13. [Google Scholar] [CrossRef] [PubMed]
- Wang, R.; Yin, Z.Q.; Lu, F.Y.; Wang, S.; Chen, W.; Zhang, C.M.; Huang, W.; Xu, B.J.; Guo, G.C.; Han, Z.F. Optimized protocol for twin-field quantum key distribution. Commun. Phys. 2020, 3, 1–7. [Google Scholar] [CrossRef]
- Minder, M.; Pittaluga, M.; Roberts, G.; Lucamarini, M.; Dynes, J.; Yuan, Z.; Shields, A. Experimental quantum key distribution beyond the repeaterless secret key capacity. Nat. Photonics 2019, 13, 334–338. [Google Scholar] [CrossRef]
- Pittaluga, M.; Minder, M.; Lucamarini, M.; Sanzaro, M.; Woodward, R.I.; Li, M.J.; Yuan, Z.; Shields, A.J. 600-km repeater-like quantum communications with dual-band stabilization. Nat. Photonics 2021, 15, 530–535. [Google Scholar] [CrossRef]
- Chen, J.P.; Zhang, C.; Liu, Y.; Jiang, C.; Zhang, W.J.; Han, Z.Y.; Ma, S.Z.; Hu, X.L.; Li, Y.H.; Liu, H.; et al. Twin-field quantum key distribution over a 511 km optical fibre linking two distant metropolitan areas. Nat. Photonics 2021, 5, 570–575. [Google Scholar] [CrossRef]
- Wang, S.; He, D.Y.; Yin, Z.Q.; Lu, F.Y.; Cui, C.H.; Chen, W.; Zhou, Z.; Guo, G.C.; Han, Z.F. Beating the fundamental rate-distance limit in a proof-of-principle quantum key distribution system. Phys. Rev. X 2019, 9, 021046. [Google Scholar] [CrossRef]
- Zhong, X.; Hu, J.; Curty, M.; Qian, L.; Lo, H.K. Proof-of-principle experimental demonstration of twin-field type quantum key distribution. Phys. Rev. Lett. 2019, 123, 100506. [Google Scholar] [CrossRef]
- Fang, X.T.; Zeng, P.; Liu, H.; Zou, M.; Wu, W.; Tang, Y.L.; Sheng, Y.J.; Xiang, Y.; Zhang, W.; Li, H.; et al. Implementation of quantum key distribution surpassing the linear rate-transmittance bound. Nat. Photonics 2020, 14, 422–425. [Google Scholar] [CrossRef]
- Liu, Y.; Yu, Z.W.; Zhang, W.; Guan, J.Y.; Chen, J.P.; Zhang, C.; Hu, X.L.; Li, H.; Jiang, C.; Lin, J.; et al. Experimental twin-field quantum key distribution through sending or not sending. Phys. Rev. Lett. 2019, 123, 100505. [Google Scholar] [CrossRef]
- Chen, J.P.; Zhang, C.; Liu, Y.; Jiang, C.; Zhang, W.; Hu, X.L.; Guan, J.Y.; Yu, Z.W.; Xu, H.; Lin, J.; et al. Sending-or-Not-Sending with Independent Lasers: Secure Twin-Field Quantum Key Distribution over 509 km. Phys. Rev. Lett. 2020, 124, 070501. [Google Scholar] [CrossRef] [PubMed]
- Yin, Z.Q.; Lu, F.Y.; Teng, J.; Wang, S.; Chen, W.; Guo, G.C.; Han, Z.F. Twin-field protocols: Towards intercity quantum key distribution without quantum repeaters. Fundam. Res. 2021, 1, 93–95. [Google Scholar] [CrossRef]
- Lo, H.K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef]
- Kwek, L.C.; Cao, L.; Luo, W.; Wang, Y.; Sun, S.; Wang, X.; Liu, A.Q. Chip-based quantum key distribution. AAPPS Bull. 2021, 31, 1–8. [Google Scholar] [CrossRef]
- Fan-Yuan, G.J.; Wang, S.; Yin, Z.Q.; Chen, W.; He, D.Y.; Guo, G.C.; Han, Z.F. Afterpulse analysis for passive decoy quantum key distribution. Quantum Eng. 2020, 2, e56. [Google Scholar] [CrossRef]
- Cui, C.; Yin, Z.Q.; Wang, R.; Chen, W.; Wang, S.; Guo, G.C.; Han, Z.F. Twin-field quantum key distribution without phase postselection. Phys. Rev. Appl. 2019, 11, 034053. [Google Scholar] [CrossRef]
- Xu, F.; Qi, B.; Ma, X.; Xu, H.; Zheng, H.; Lo, H.K. Ultrafast quantum random number generation based on quantum phase fluctuations. Opt. Express 2012, 20, 12366–12377. [Google Scholar] [CrossRef] [PubMed]
- Abellán, C.; Amaya, W.; Jofre, M.; Curty, M.; Acín, A.; Capmany, J.; Pruneri, V.; Mitchell, M. Ultra-fast quantum randomness generation by accelerated phase diffusion in a pulsed laser diode. Opt. Express 2014, 22, 1645–1654. [Google Scholar] [CrossRef]
- Zhang, C.M.; Xu, Y.W.; Wang, R.; Wang, Q. Twin-Field Quantum Key Distribution with Discrete-Phase-Randomized Sources. Phys. Rev. Appl. 2020, 14, 064070. [Google Scholar] [CrossRef]
- Curras Lorenzo, G.; Wooltorton, L.; Razavi, M. Twin-field quantum key distribution with fully discrete phase randomization. Phys. Rev. Appl. 2020, 15, 014016. [Google Scholar] [CrossRef]
- Jiang, C.; Yu, Z.W.; Hu, X.L.; Wang, X.B. Sending-or-not-sending twin-field quantum key distribution with discrete-phase-randomized weak coherent states. Phys. Rev. Res. 2020, 2, 043304. [Google Scholar] [CrossRef]
- Ben-Or, M.; Horodecki, M.; Leung, D.W.; Mayers, D.; Oppenheim, J. The universal composable security of quantum key distribution. In Proceedings of the Theory of Cryptography Conference, Cambridge, MA, USA, 10–12 February 2005; Springer: Berlin/Heidelberg, Germany, 2005; pp. 386–406. [Google Scholar]
- Müller-Quade, J.; Renner, R. Composability in quantum cryptography. New J. Phys. 2009, 11, 085006. [Google Scholar] [CrossRef]
- Koashi, M. Simple security proof of quantum key distribution based on complementarity. New J. Phys. 2009, 11, 045018. [Google Scholar] [CrossRef]
- Cao, Z.; Zhang, Z.; Lo, H.K.; Ma, X. Discrete-phase-randomized coherent state source and its application in quantum key distribution. New J. Phys. 2015, 17, 053014. [Google Scholar] [CrossRef]
- Currás-Lorenzo, G.; Navarrete, Á.; Azuma, K.; Kato, G.; Curty, M.; Razavi, M. Tight finite-key security for twin-field quantum key distribution. NPJ Quantum Inf. 2021, 7, 1–9. [Google Scholar] [CrossRef]
- Ivanovic, I.D. How to differentiate between non-orthogonal states. Phys. Lett. A 1987, 123, 257–259. [Google Scholar] [CrossRef]
- Maeda, K.; Sasaki, T.; Koashi, M. Repeaterless quantum key distribution with efficient finite-key analysis overcoming the rate-distance limit. Nat. Commun. 2019, 10, 1–8. [Google Scholar] [CrossRef] [PubMed]
- Zhang, Z.; Zhao, Q.; Razavi, M.; Ma, X. Improved key-rate bounds for practical decoy-state quantum-key-distribution systems. Phys. Rev. A 2017, 95, 012333. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).