Abstract
This paper studies the performance of location-based beamforming with the presence of artificial noise (AN). Secure transmission can be achieved using the location information of the user. However, the shape of the beam depends on the number of antennas used. When the scale of the antenna array is not sufficiently large, it becomes difficult to differentiate the performance between the legitimate user and eavesdroppers nearby. In this paper, we leverage AN to minimize the area near the user with eavesdropping risk. The impact of AN is considered for both the legitimate user and the eavesdropper. Closed-form expressions are derived for the expectations of the signal to interference plus noise ratios (SINRs) and the bit error rates. Then, a secure beamforming scheme is proposed to ensure a minimum SINR requirement for the legitimate user and minimize the SINR of the eavesdropper. Numerical results show that, even with a small number of antennas, the proposed beamforming scheme can effectively degrade the performance of eavesdroppers near the legitimate user.
1. Introduction
Due to the broadcast nature of wireless networks, they face a variety of security threats. Passive eavesdropping is difficult to detect and prevent in wireless communication systems. Although legitimate users can engage in encrypted communication, the cost of secret key distribution is also significant. Physical layer security is promising to achieve secure transmission without key distribution. Physical layer security techniques include artificial noise, security-oriented beamforming, diversity-assisted security approaches, etc. [1,2,3]. Their security is independent of the computational capability of eavesdroppers. The multiple-input multiple-output (MIMO) technique can be used to enhance transmission security thanks to the diversity gain of beamforming.
Based on the channel state information (CSI) of the legitimate user, beamforming can be achieved towards the desired user, with a power gain higher than that of other users in different locations [4,5]. As more antennas are used at the base station, the beam becomes more concentrated. Moreover, artificial noise (AN) can be applied in the null space of the channel of the legitimate user to prevent potential eavesdropping [6,7,8,9]. Closed-form expressions for the secure transmission probability and the effective secrecy throughput are derived in [10] for a Rayleigh fading channel. The impact of the imperfect CSI is considered in [11]. A two-phase transmission scheme with AN injection is proposed in [12] to achieve zero secrecy outage probability under imperfect channel estimation. By assuming that the statistical CSI of the eavesdropper is also available at the base station [13,14,15,16], secure beamforming schemes have been proposed where the secrecy rate is maximized. Moreover, under the assumption that the CSIs of both the legitimate user and the eavesdropper are available at the base station, a secrecy capacity optimization artificial noise is proposed in [17], which is not aligned into the null space of the legitimate channel.
However, the CSI of the user is difficult to obtain by the base station in certain scenarios, such as when the user has not yet connected to the network. In addition, after the user has connected to the network, an eavesdropper can also disrupt beamforming and achieve eavesdropping through pilot contamination attacks [18,19,20]. For millimeter wave (mmWave) systems, the estimation of CSI requires a huge overhead for channel training [21].
Therefore, some works consider using alternative user information for beamforming, such as statistical CSI [13,15,16] and location information [21,22,23,24,25]. In certain scenarios, the location information of the user could be available. For example, the legitimate user is within a confidential area and dedicated networks can only be accessed within this area. We hope that users outside the confidential area cannot eavesdrop on the information of the dedicated network, because attackers can launch jamming, spoofing [26], or distributed denial-of-service attacks based on the network information. Location-based beamforming can be used to protect the dedicated networks.
The performance of location-based beamforming has been studied in [22] in Rician wiretap channels. Based on the location information of the legitimate user and the eavesdropper, the optimal location-based beamformer has been determined for the legitimate user through a grid search algorithm, which minimizes the secrecy outage probability of the system. Due to the absence of AN, eavesdroppers near legitimate users have a high secrecy outage probability when the number of antennas at the base station is small. The authors in [23] considered a wiretap system with the presence of a jammer. By assuming that the CSI of the legitimate user is known to the base station and the jammer, while the location of the eavesdropper is also available at the base station, the optimal beamformer that minimizes the secrecy outage probability has been proposed. Because the CSI between the legitimate user and the jammer is known, the AN signal is transmitted in the null space of the channel of the legitimate user. The authors of [25] studied the covert threat region of three-dimensional (3D) location-based beamforming, and the covertness performance for resisting detection from a location-unknown warden has been evaluated and compared with that of the conventional maximal ratio transmitting scheme.
In this paper, we study the performance of location-based beamforming with the assistance of AN. Based on the location information of the legitimate user, we minimize the area near the user that has eavesdropping risks. Hence, the eavesdropping performance of eavesdroppers at different locations next to the user has been studied. The impact of AN has been considered for both the legitimate user and the eavesdropper. The main contributions of this paper can be summarized as follows:
- Based on the location information of the legitimate user and the eavesdropper, the signal to interference plus noise ratio (SINR) expressions have been derived for both the user and the eavesdropper, and the impact of AN has been considered. Close approximations of the probability density functions (PDFs) of SINRs have been proposed for Rician channels.
- The expectations of SINRs have been derived in closed-form expressions. Moreover, the bit error rate (BER) expressions are derived using Gaussian-Laguerre (GL) approximation.
- A quality of service (QoS)-based beamforming scheme is proposed to minimize the SINR of the eavesdropper and ensure the minimum SINR requirement of the legitimate user. Simulation results show that, when eight antennas are used at the base station, the block error rate (BLER) of eavesdroppers located 5° away from the legitimate user reaches 1.
Some works in the literature considered using ergodic secrecy rate [16,27] or secrecy outage probability [22,28] to design a secure transmission strategy. The ergodic secrecy rate refers to the difference in ergodic rate between the legitimate user and the eavesdropper. Ref. [16] proposed a power allocation algorithm for a discrete Fourier transform (DFT) beamforming matrix to maximize the ergodic secrecy rate. A deep neural network (DNN)-based secure precoding scheme is proposed in [29] to jointly design the precoder and AN signal when the channel estimation is imperfect and the channels are spatially correlated. Because the secrecy rate cannot be arbitrary values in real systems, the authors in [22,28] minimize the secrecy outage probability when a specific target secrecy rate is chosen. However, maximizing the secrecy rate does not imply that the capacity of the eavesdropper is sufficiently small. Due to the application of error correcting code (ECC) in the communication systems, an eavesdropper can successfully decode the information when the minimum SINR requirement is satisfied. To reduce the risk of eavesdropping, we consider maximizing the BLER of the eavesdropper by minimizing the SINR of the eavesdropper. QoS-based transmit beamforming has proven to be a viable and versatile approach [30]. The QoS is measured by the average SINR. Two design formulations are proposed in [30] for AN-aided secret transmit beamforming, namely a total power minimization formulation and a user’s SINR maximization formulation. The signal-to-noise ratio (SNR) outage probability criterion is proposed in [31]. In this paper, based on the error correction capability of ECC, a beamforming design scheme is proposed to minimize the SINR of an eavesdropper and maintain the minimum SINR requirement of the legitimate user. The performance of the proposed scheme is verified through simulations using Polar code [32].
Location-based beamforming can be implemented with low-cost at an analog beamforming module. Analog circuits can significantly improve the power efficiency of the device compared to digital circuits [33]. Due to the non-linear characteristics of power amplifiers, it is not suggested to adjust the amplitude of the signals for beamforming use at the radio frequency (RF) module [34]. The location-based beamformer only shifts the phase of the signal without changing its modulus, which can be considered as a phase-adjusted DFT beamformer. DFT codebook can be embedded on field-programmable analog arrays [33] with reduced power consumption. We note that when the system operates at mmWave band with an extremely large-scale antenna array (ELAA), near-field propagation needs to be considered [35]. Due to the spherical wavefront of near-field radiation, the DFT type beamforming is no longer applicable [36,37]. Secure beamforming with ELAA can be considered for our future work.
The rest of this paper is organized as follows. Section 2 introduces the system model, where the SINR expressions of the legitimate user and the eavesdropper are derived. In Section 3, the approximate PDFs of the SINRs are derived, and then the expectations of the SINRs and the BERs are deduced. In Section 4, the beamforming design scheme is proposed to minimize the SINR of the eavesdropper. The simulation results are presented in Section 5. Section 6 concludes this paper.
2. System Model
We consider a typical wiretap scenario, where a base station Alice and an eavesdropper Eve are equipped with uniform linear arrays (ULA) with M and N antenna elements, respectively. A legitimate user Bob is equipped with a single antenna. To facilitate the presentation of location for the users, we adopt the polar coordinate system and Alice is considered as the origin [22]. Then, the locations of Bob and Eve can be denoted as and , respectively. We assume that the location of Bob is known to Alice. To investigate the impact of Eve’s location on eavesdropping performance, we assume that the location of Eve is also known to Alice. Then, an optimal beamforming scheme can be designed using AN. In the case where the location of Eve is unknown to Alice, the beamforming scheme can still be used to minimize the area with eavesdropping risk. We note that the CSIs of Bob and Eve are unknown to Alice. Based on the location information of Bob, Alice is able to transmit confidential information via a beam aiming to Bob. Moreover, Alice may transmit a jamming signal via another beam aiming to Eve. We assume that all of the channels are subject to quasi-static independent and identically distributed (i.i.d) Rician fading with different Rician K-factors, and that the K-factors are known to Alice via some a priori measurement campaigns. Hence, the channel vector from Alice to Bob, denoted as , can be written as
where is the Rician K-factor of , denotes the LOS component, and denotes the scattered component, the elements of which are assumed to be i.i.d. complex Gaussian random variables with zero mean and unit variance, i.e., . Moreover, can be written as
where , is the carrier frequency, is the space between two adjacent antenna elements of the ULA of Alice, and c is the speed of propagation of the plane wave. When is equal to a half wavelength, i.e., , we have .
Likewise, the channel matrix from Alice to Eve, denoted as , can be written as
where is the Rician K-factor of , denotes the LOS component, and denotes the scattered component with i.i.d circularly-symmetric complex Gaussian random variables with zero mean and unit variance. Moreover, can be written as
where and are the array responses at Eve and Alice, respectively, which can be written as
where , is the space between two adjacent antenna elements of the ULA of Eve and is the direction of arrival from Alice to Eve.
The signal transmitted at Alice can be expressed as
where is the normalized information signal, is the normalized jamming signal, i.e., , is the normalized beamformer for Bob, is the normalized beamformer for jamming signal, i.e., , is the power allocated to the information signal, and is the power allocated to the jamming signal. Without loss of generality, the total transmit power of Alice is normalized to 1 and hence we have .
Therefore, the signal received at Bob can be expressed as
where represents the complex baseband thermal noise at Bob, such that .
Likewise, the signal received at Eve can be expressed as
where represents the complex baseband thermal noise at Eve, such that .
Then, the SINR at Bob can be written as
where and .
Moreover, assuming Eve applies maximum ratio combining (MRC) to combine the signals received from different antennas, the SINR at Eve can be written as
where and , denotes the square of the norm of a vector.
3. Performance Analysis
In this section, we first derive the PDF of the SINR for Bob and Eve, and then the expectation of the SINR and the BER performance can be deduced.
3.1. Distribution of the SINR
According to (1), we have
The distribution of has been analyzed in [22] for a general . It has been shown that is deterministic and is a complex Gaussian random variable with zero mean and unit variance. Hence, follows a Rician distribution with the parameters [22]:
The PDF of the Rician distribution involves the modified Bessel function of the first kind, which is difficult to derive. However, the Rician distribution can be closely approximated by Nakagami distribution [38], with the parameters and . Hence, can be approximated by a gamma distribution with the PDF written as
where , and is the gamma function.
Furthermore, we have
Similarly, we can obtain that can also be approximated by a gamma distribution, with the parameters and where
Because and are independent, and can be considered as independent. Hence, the PDF of can be obtained following a similar derivation as in [39]
where is the confluent hypergeometric function of the second kind, which is defined as [39]
For the case , we have .
For the SINR of the eavesdropper in (11), we have
where is the row of which can be written as
where is the element of , i.e., and is the row of . Hence, , the PDF of can be approximated by a gamma distribution with the parameters and where
Because the rows of are independent from each other, the PDF of term can also be approximated by a gamma distribution with the parameters and . Moreover, the PDF of term can also be approximated by a gamma distribution with the parameters and where
Therefore, the PDF of , denoted as , can be expressed by replacing , , , and with , , , and in (19).
3.2. Expectation of SINR
The expectation of SINR can be used to design a QoS-based beamforming scheme [30]. Using the PDF of SINR in (19), the expectation of SINR for Bob can be derived as
According to [40], we have the equation
where is the Meijer’s G-function ([41], 9.301). Then, by performing a change of variable , a closed-form expression for expectation of SINR for Bob can be derived using [42]
For the case , the expectation of SINR for Bob can be derived using ([41], 3.326), such that
3.3. BER Analysis
BER is an important metric for transmission performance. Based on the PDF of SINR in (19), the BER expression of Bob can be written as [39]
The closed-form BER expression has been derived in [39] when the parameters and are integers. Otherwise, the integration cannot be expressed in closed-form. In this paper, we use GL quadrature sum [43] to approximate the value of . GL quadrature sum approximation can be expressed as
where and are the abscissas and weight factors for the GL integration, which can be tabulated ([44], eq. (25.4.45)) or can be generated efficiently in software such as MATLAB R2020b. The accuracy of the GL quadrature sum increases with the number of terms [44].
Hence, with a change of variable , the integration can be expressed as
The integration can be approximated by , which can be expressed as
It is shown in Section 5 that the approximation curves perfectly match numerical results for .
For the case , the BER expression can be derived using [45], such that
where is the hypergeometric function ([41], Ch. 9.1).
4. Optimal Location-Based Beamforming
A location-based beamformer can be expressed as [22]
where is the beamforming direction. The optimal beamformers can be denoted as and where and are the optimal beam directions for useful signal and AN, respectively.
In this paper, the beamforming scheme is designed based on the QoS of Bob and Eve. Because ECC has been widely used in wireless communication systems, the redundancy of code allows the receiver to correct a limited number of error bits. Hence, the receiver can successfully decode the message when the minimum SINR requirement is satisfied. On the other hand, AN needs to be strong enough at the eavesdropper side to make the BLER of the eavesdropper close to 1. When the scale of the antenna array is not sufficiently large at Alice, it is difficult to differentiate the performance between Bob and Eve nearby. In order to minimize the area near Bob with eavesdropping risk, it is necessary to increase the AN at Eve as much as possible without affecting the BLER of Bob. Hence, the beamforming design formulation ensures a minimum SINR requirement of Bob, denoted as , while minimizing the SINR of Eve. In this case, the BLER of Eve is maximized.
We note that for each pair, the resulted monotonically increases with . Hence, when there exists values of such that the corresponding , the values of can be approached through Algorithm 1.
| Algorithm 1 Algorithm to Determine , , for Location-based Beamforming |
Require: , Ensure: , , 1: for with step size do 2: calculate and using (36). 3: while with step size do 4: calculate using (29) 5: if then 6: 7: calculate using (29) and the parameters of Eve 8: 9: break 10: end if 11: end while 12: end for 13: Choose , that achieve the minimum , takes the value of the corresponding . |
5. Simulation Results
In this section, we first verify the analytical expressions derived above through simulations. Then, the performance of the proposed beamforming scheme Algorithm 1 is simulated for different and M values. The channel parameters are set as dB and dB and the SNR of the system is dB for both Bob and Eve.
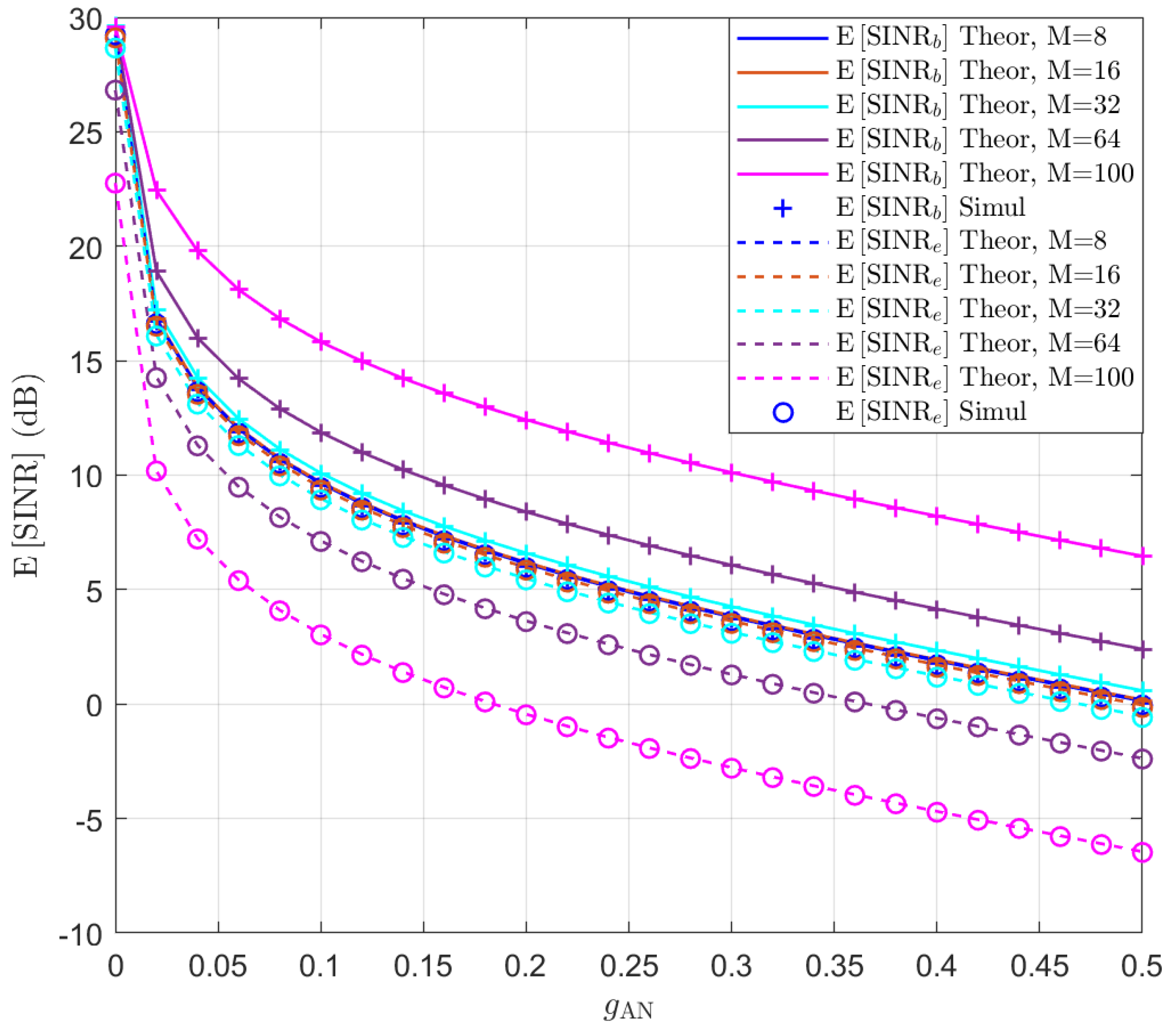
The SINR expectation expression in (29) is tested at first assuming that and . Without beamforming optimization, we align the signal beam towards Bob and the AN beam towards Eve, i.e., and . The expectation of and is simulated for different M and values and the results are presented in Figure 1. The theoretical values of the expectation of SINR are also displayed in lines. It can be seen that the theoretical curves perfectly match the simulation results. Additionally, due to the close proximity of Bob and Eve, it can be observed that when the number of antennas is small, i.e., , the performance of Bob and Eve is almost the same, regardless of whether AN is used. This is because the beam is wide for these cases. As the number of antennas increases, the beam becomes more focused, and even without using AN, the performance of Bob and Eve becomes distinguishable. When AN is added, the performance of both Bob and Eve decreases, but the performance of Eve decreases more significantly. The simulation results show that, without beam optimization, a large number of antennas is required to differentiate the performance of Bob and Eve.
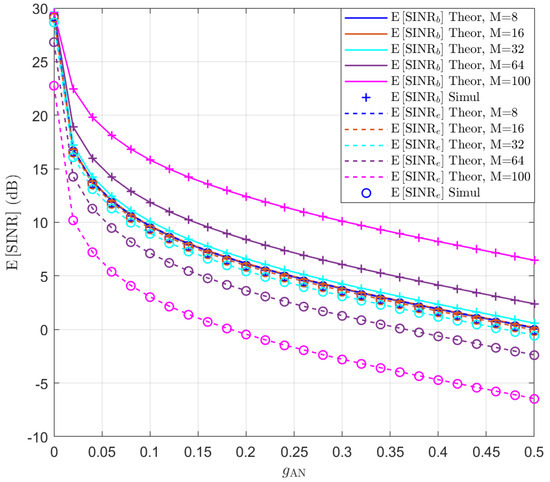
Figure 1.
The expectation of and in the function of for .
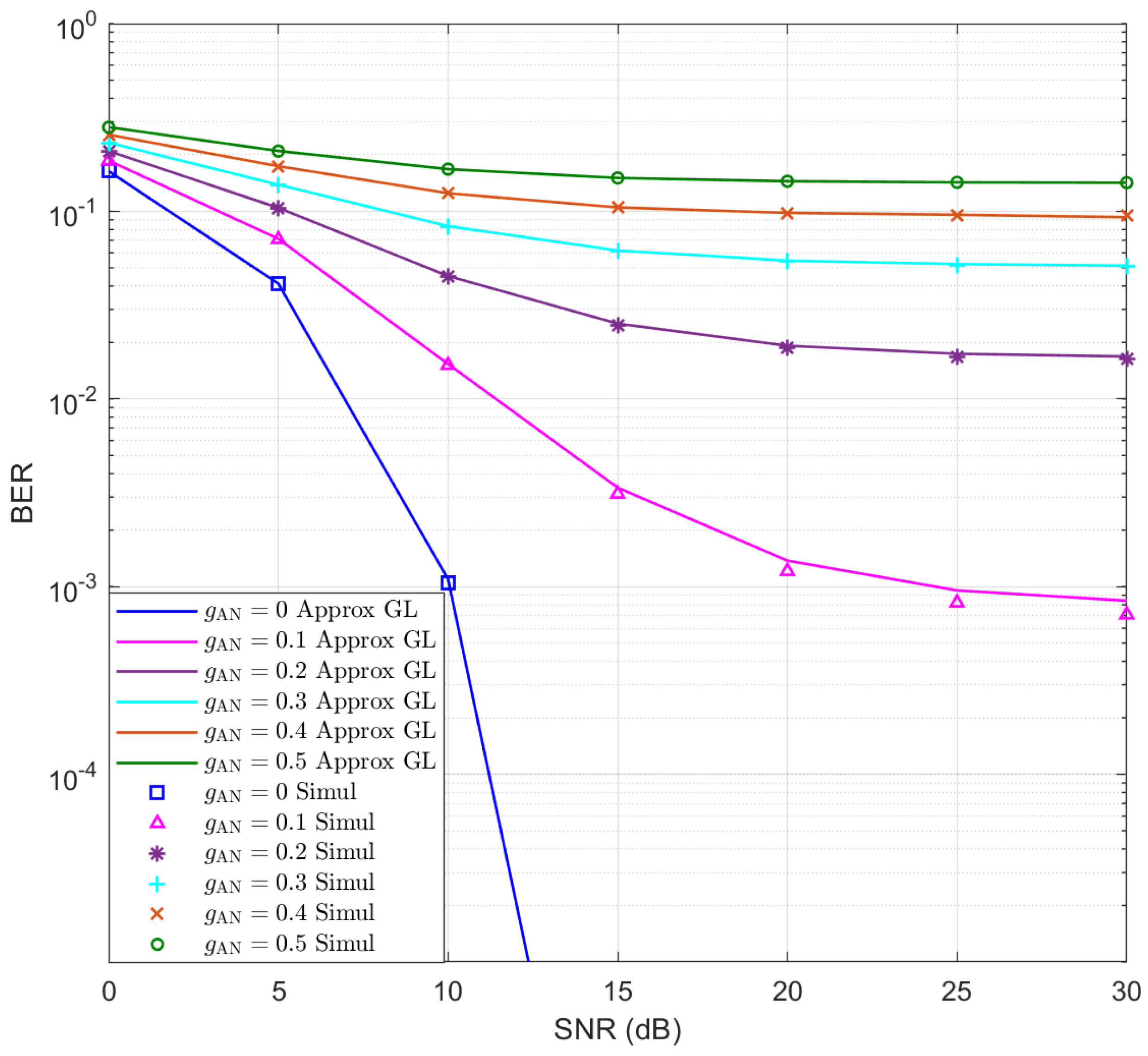
Moreover, based on the above assumptions, the BER performance of Eve is simulated for and the results are presented in Figure 2 for different values. The approximate BERs using GL quadrature sum with are presented as continuous lines, which exhibit good accuracy compared to the simulation results. Moreover, it can be seen that as increases, the BER of Eve increases rapidly.
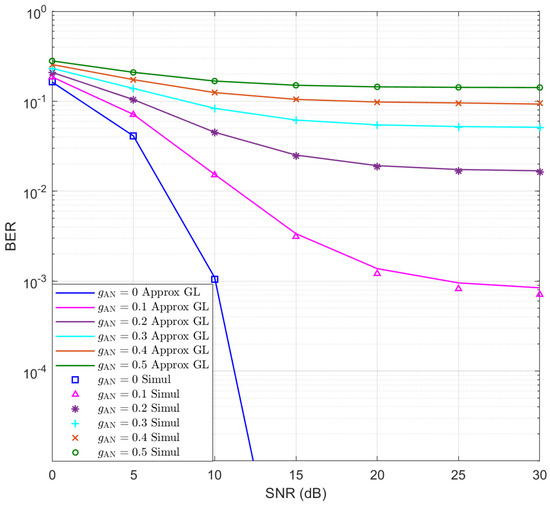
Figure 2.
The simulated and approximate BERs of Eve for .
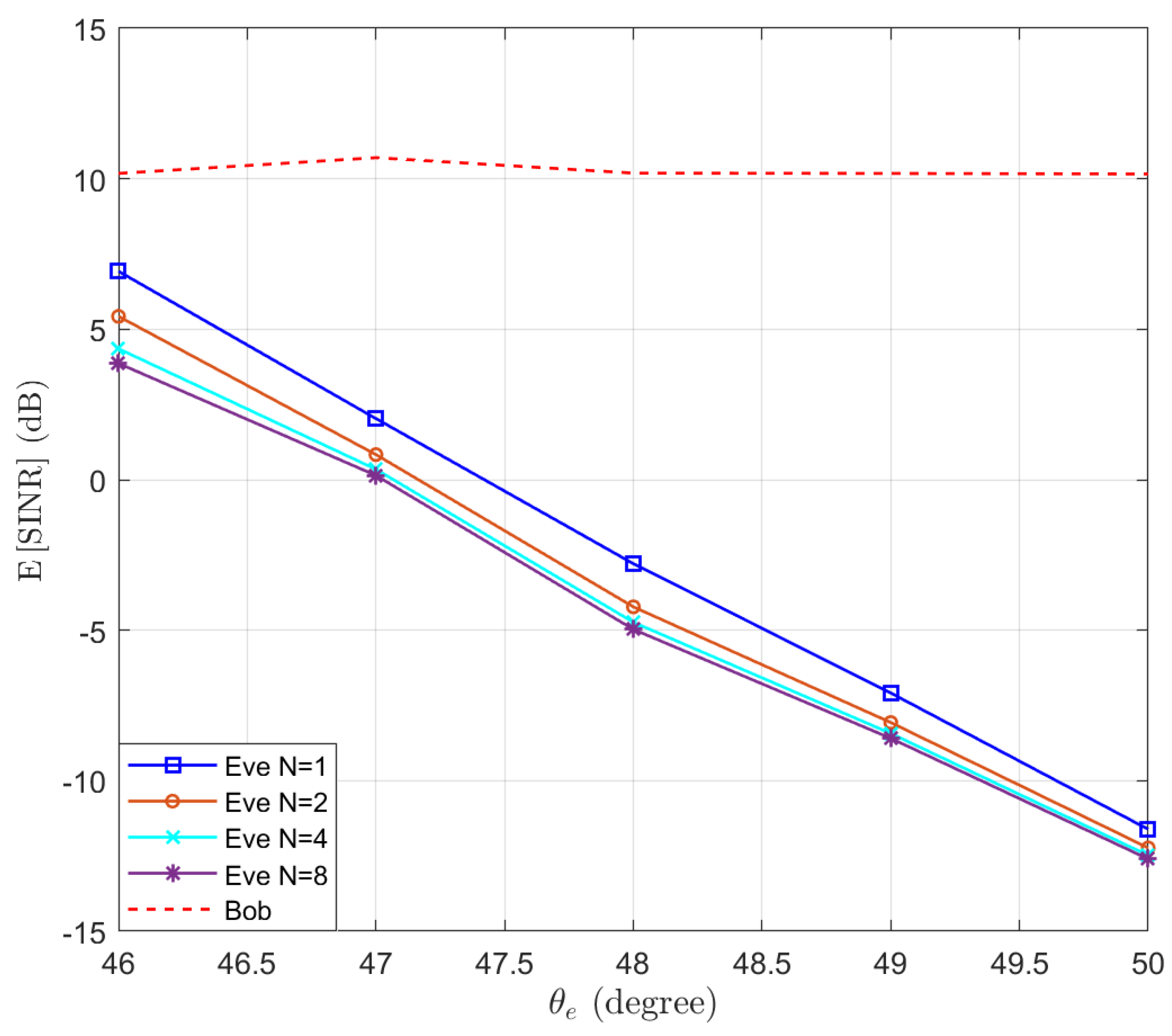
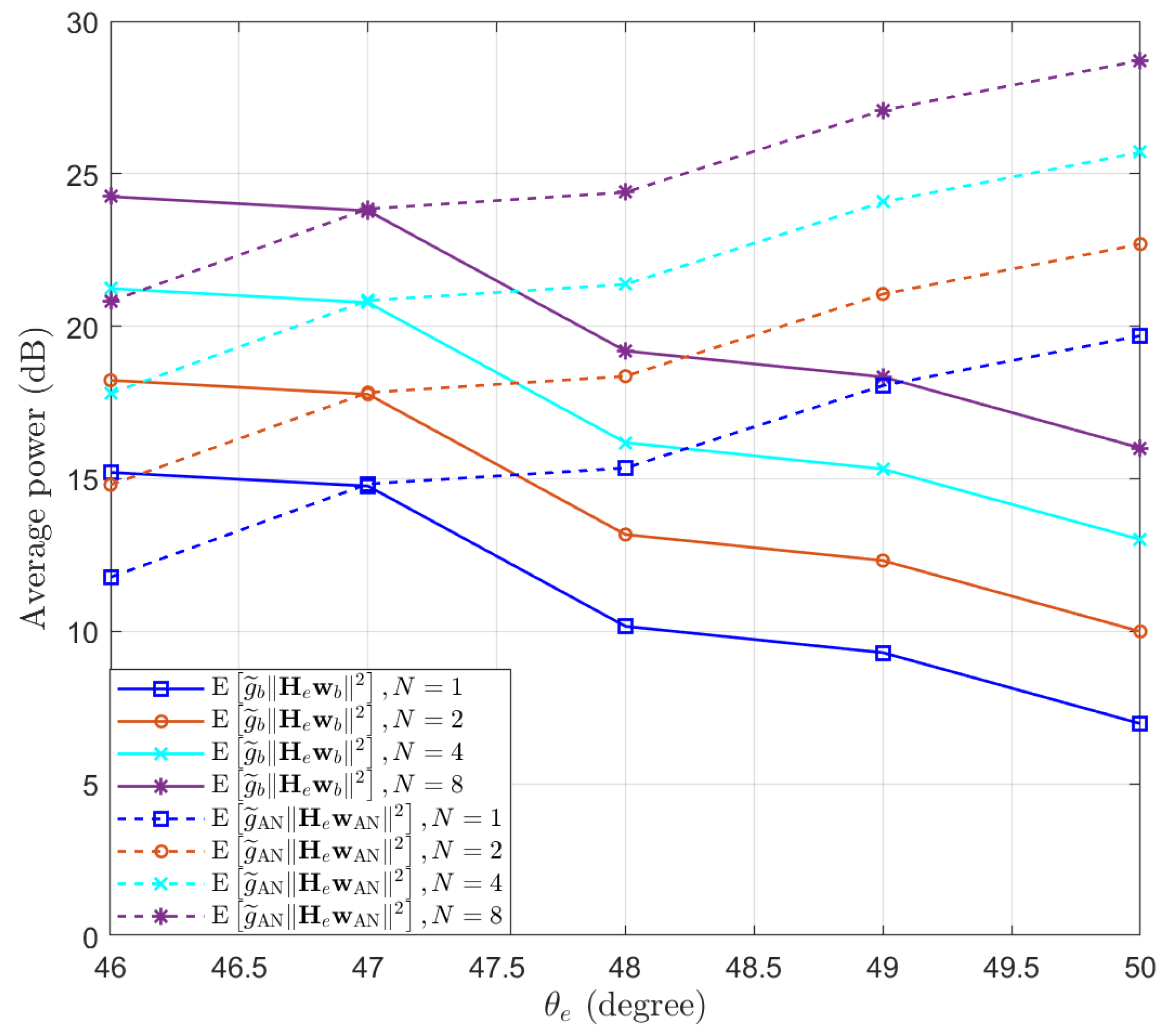
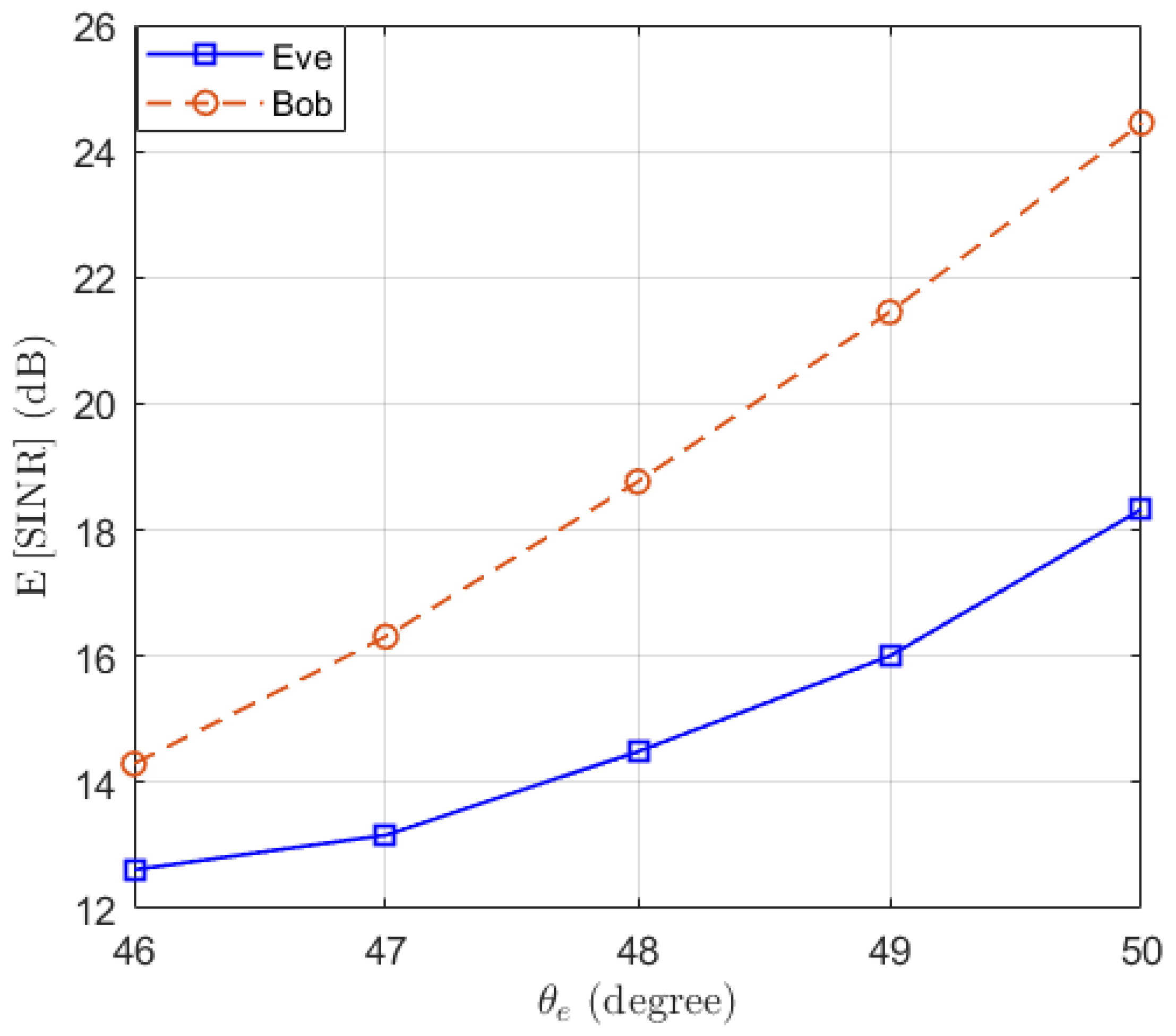
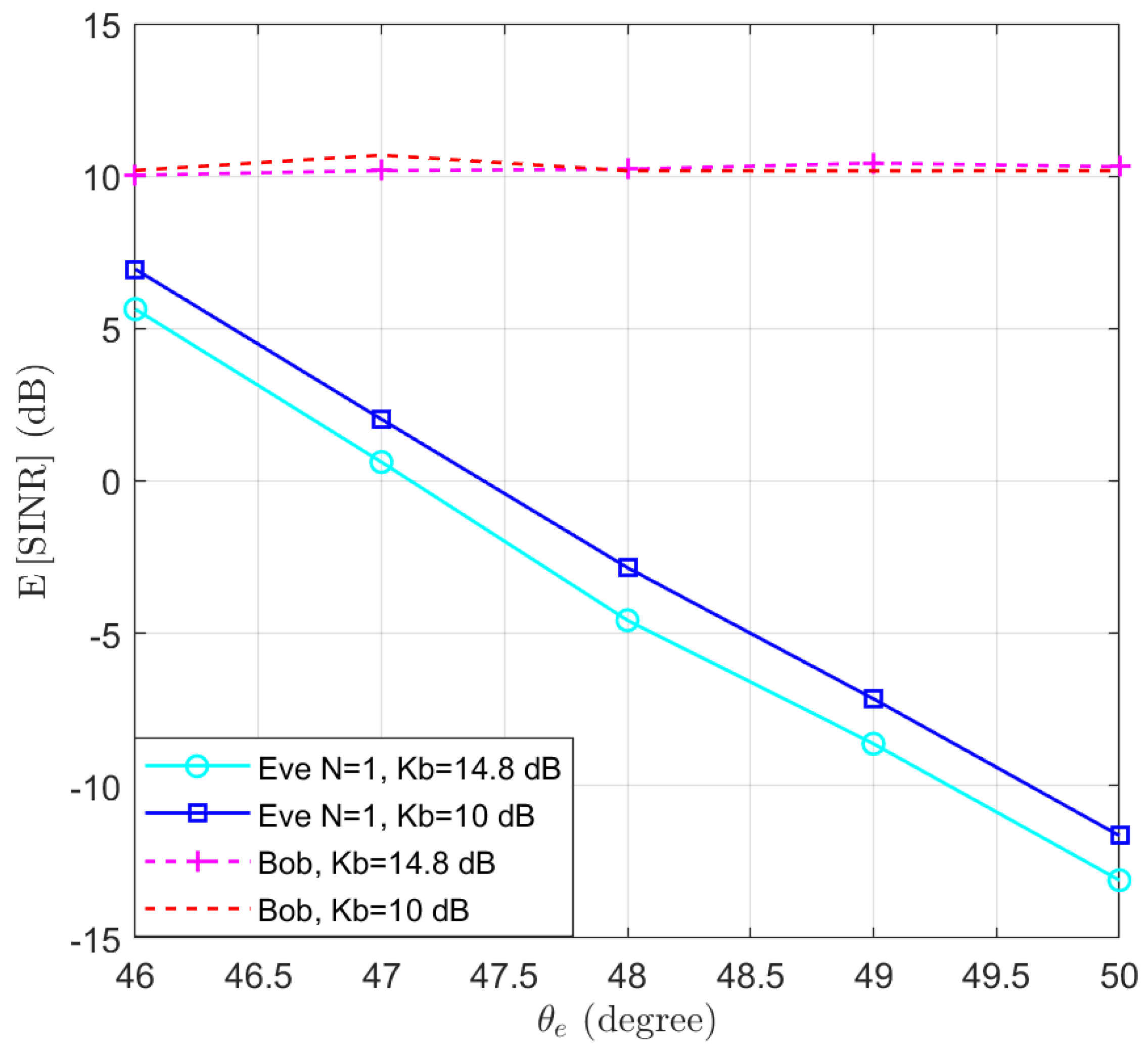
Then, we test the performance of the proposed Algorithm 1 in preventing eavesdropping with a small scale of antennas. The locations of Bob and Eve remain unchanged. We set , and . We test the performance of Eve at different locations, such that . Assuming and , the expectations of and are simulated and the results are presented in Figure 3. We can see that the performance of Bob remains above the threshold dB, while the performance of Eve decreases when increasing the distance between Eve and Bob. Moreover, we note that when the number of antennas of Eve increases, the SINR of Eve actually decreases. This is because as the number of antennas N increases, the power of the desired signal and AN received by Eve both increase proportionally, resulting in a decrease in overall SINR. To clarify this point, the expectation of the power of the desired signal and AN received by Eve are displayed in Figure 4. It can be observed that as the number of receiving antennas doubles, the received power is also doubled. However, since the power of the desired signal and AN follow different distributions, the expected SINR changes with the number of receiving antennas.
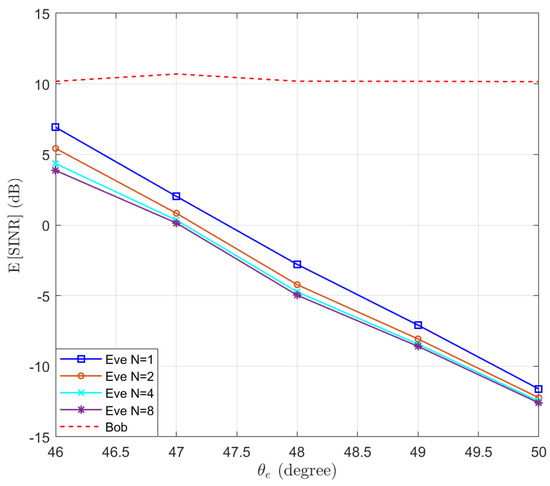
Figure 3.
The expectation of and with optimal beamforming in the function of the location of Eve .
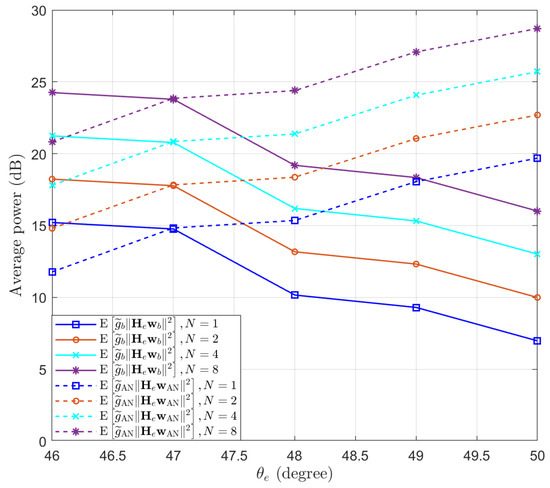
Figure 4.
The expectation of the power of the desired signal and AN received by Eve, with different numbers of receive antennas at Eve.
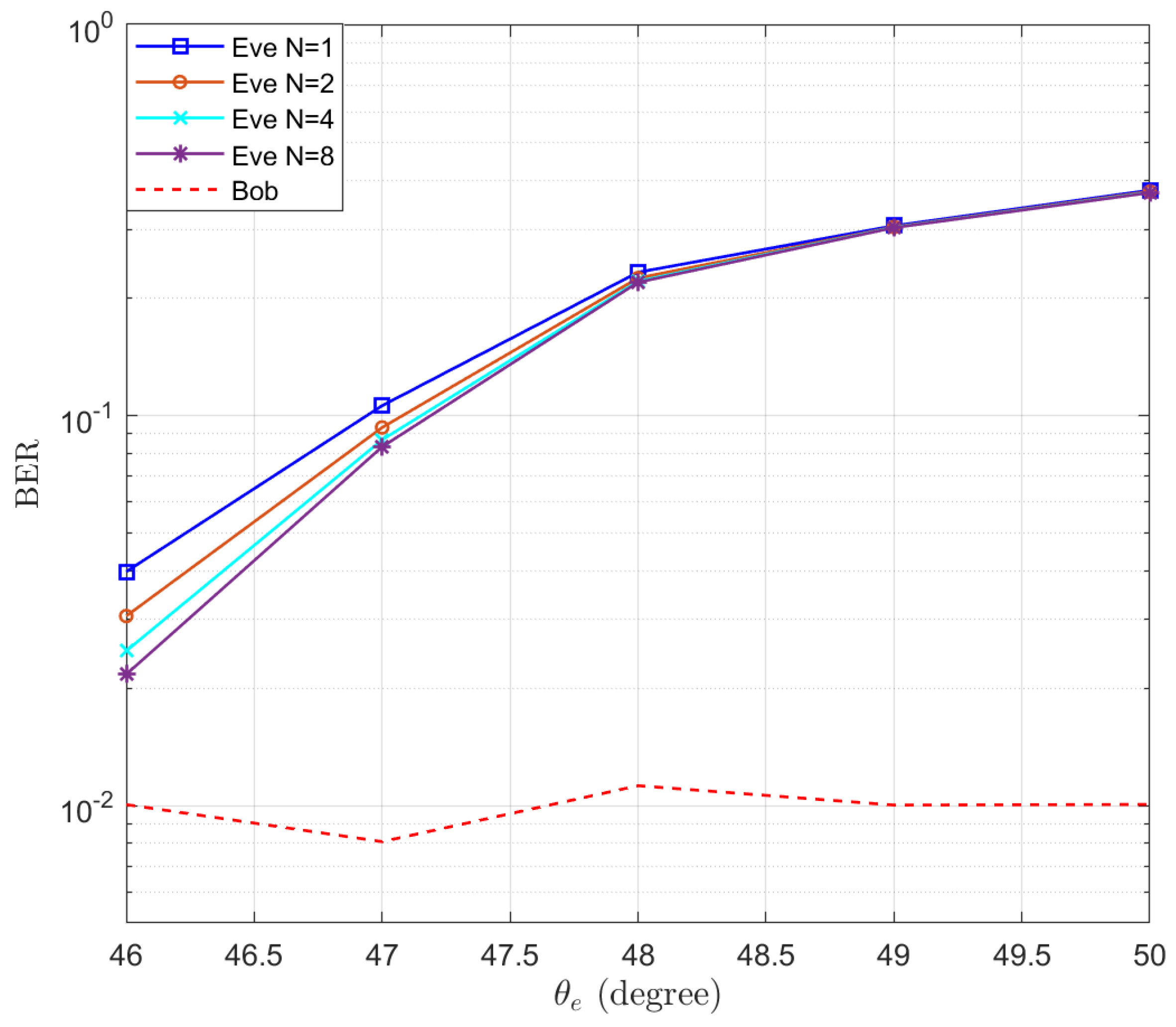
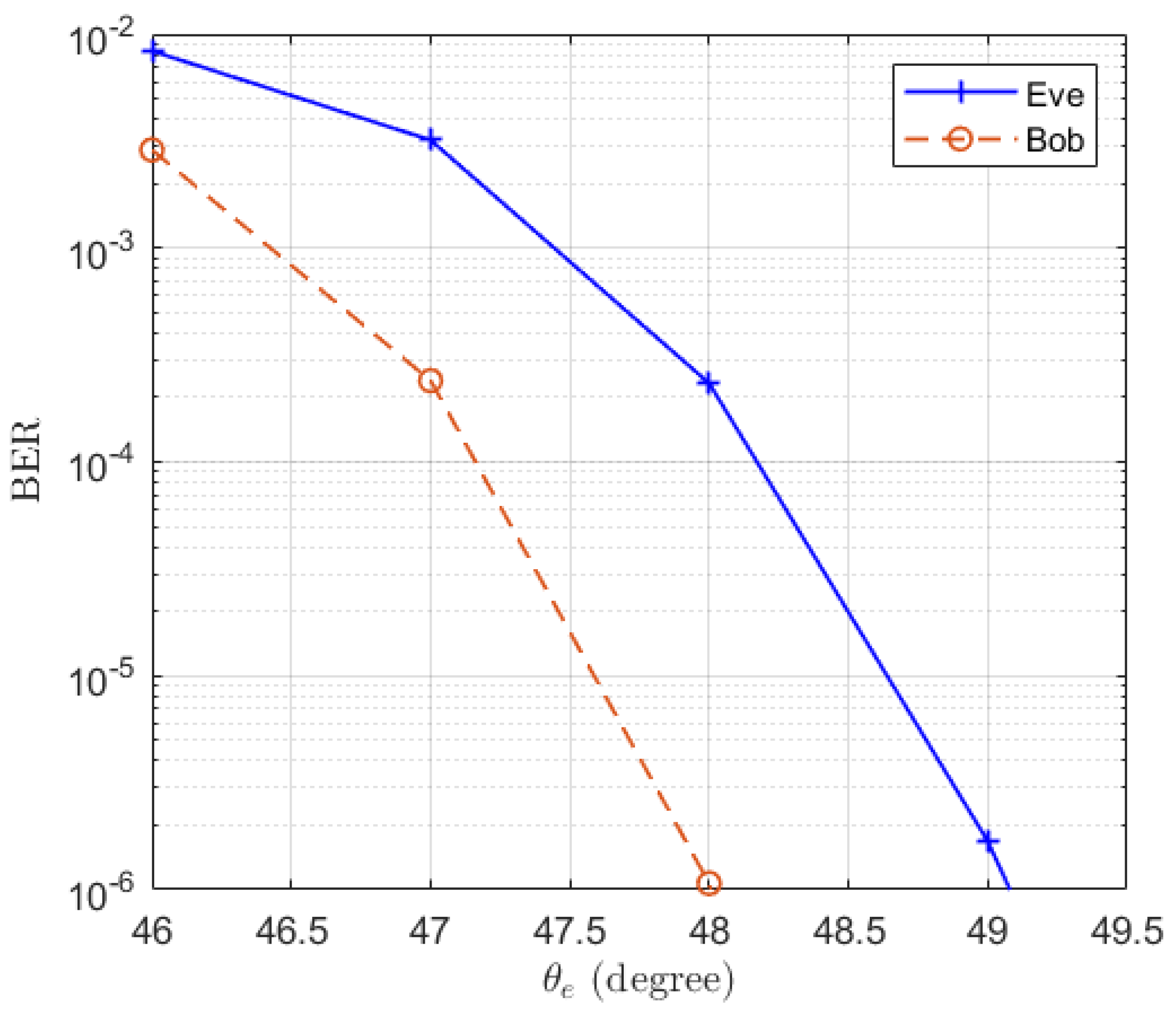
The corresponding BERs are also simulated and the results are presented in Figure 5. It is shown that the BER of Bob fluctuates around and the BER of Eve increases when increasing the distance between Eve and Bob. When there is 5° difference between Eve and Bob, the BER of Eve reaches . Particularly, we note that the BER of the case is lower than that of the case . This is in contrast to the trend exhibited by the expectation of in Figure 3. This is because when a MRC receiver is used at Eve, an increase in the number of receive antennas reduces the fading of the equivalent channel. Therefore, even though the average SINR of the case is smaller than that of the case , its BER is still better than that of the case, due to the diversity gain of the receive antenna array.
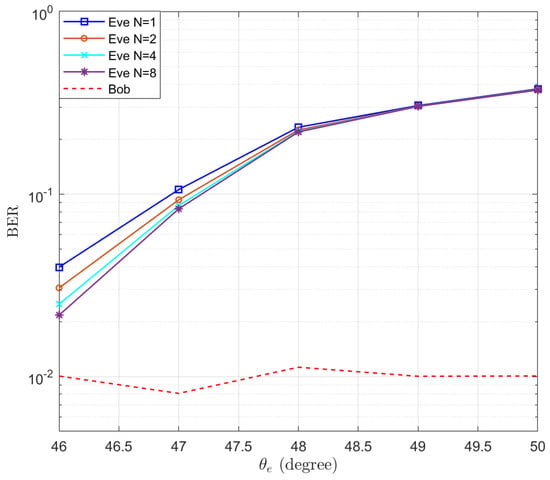
Figure 5.
The simulated BERs of Eve in the function of the location of Eve .
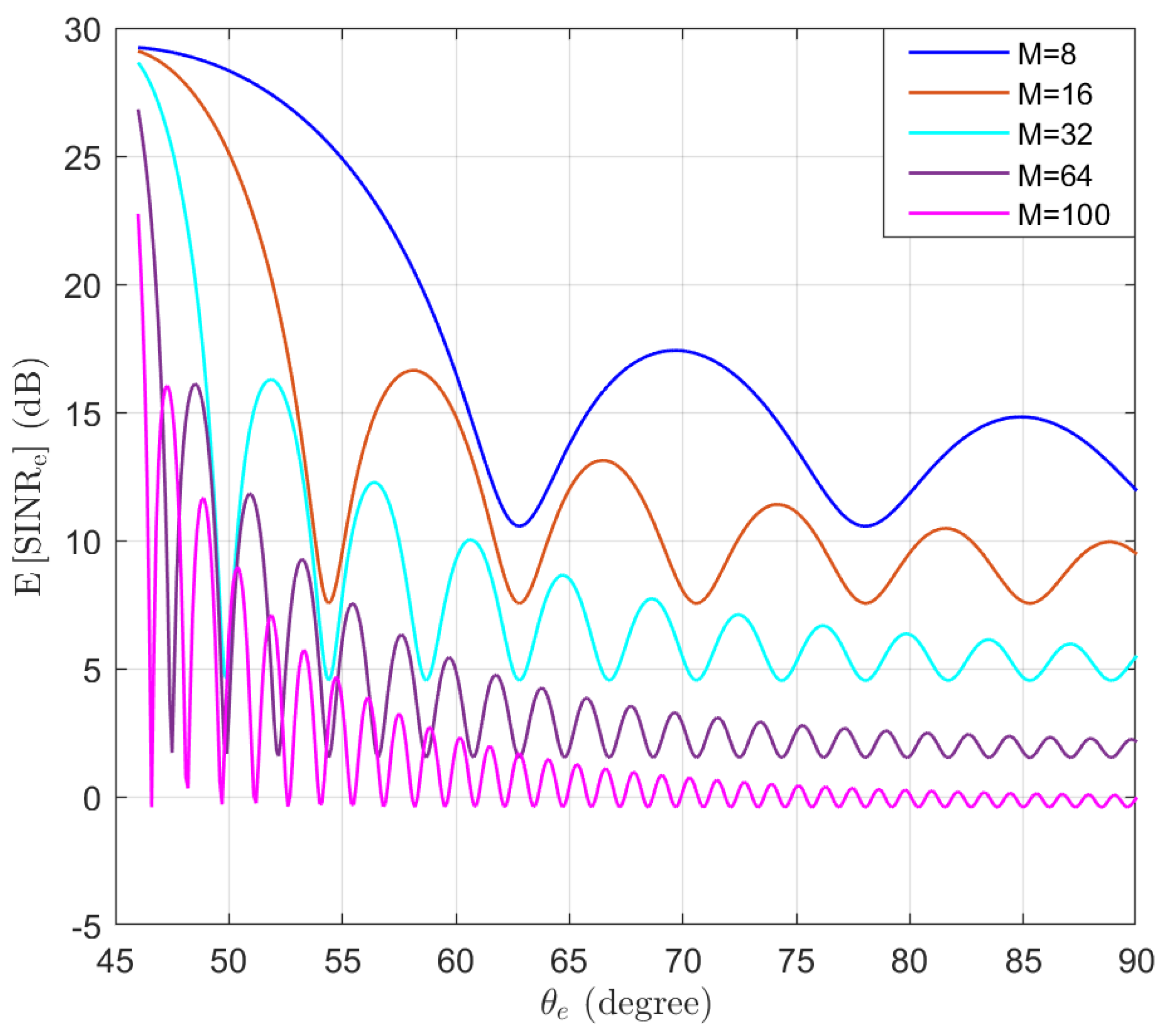
For comparison purposes, the expectation of without using AN is simulated in the function of the location of Eve , as shown in Figure 6. The shape of the beam can be observed for different M values. We note that as more antennas are used, the beam becomes narrower and the sidelobes become smaller.
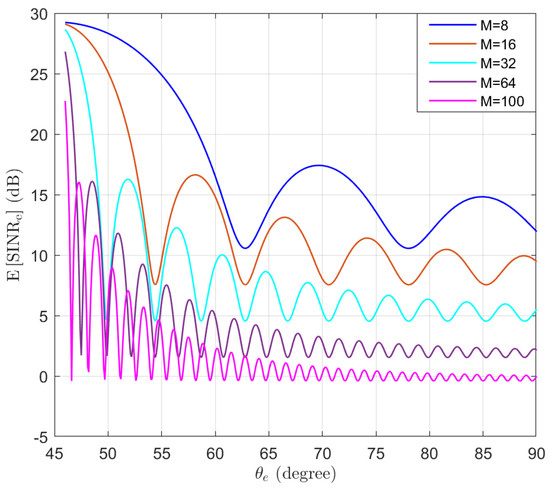
Figure 6.
The expectation of without using AN in the function of the location of Eve .
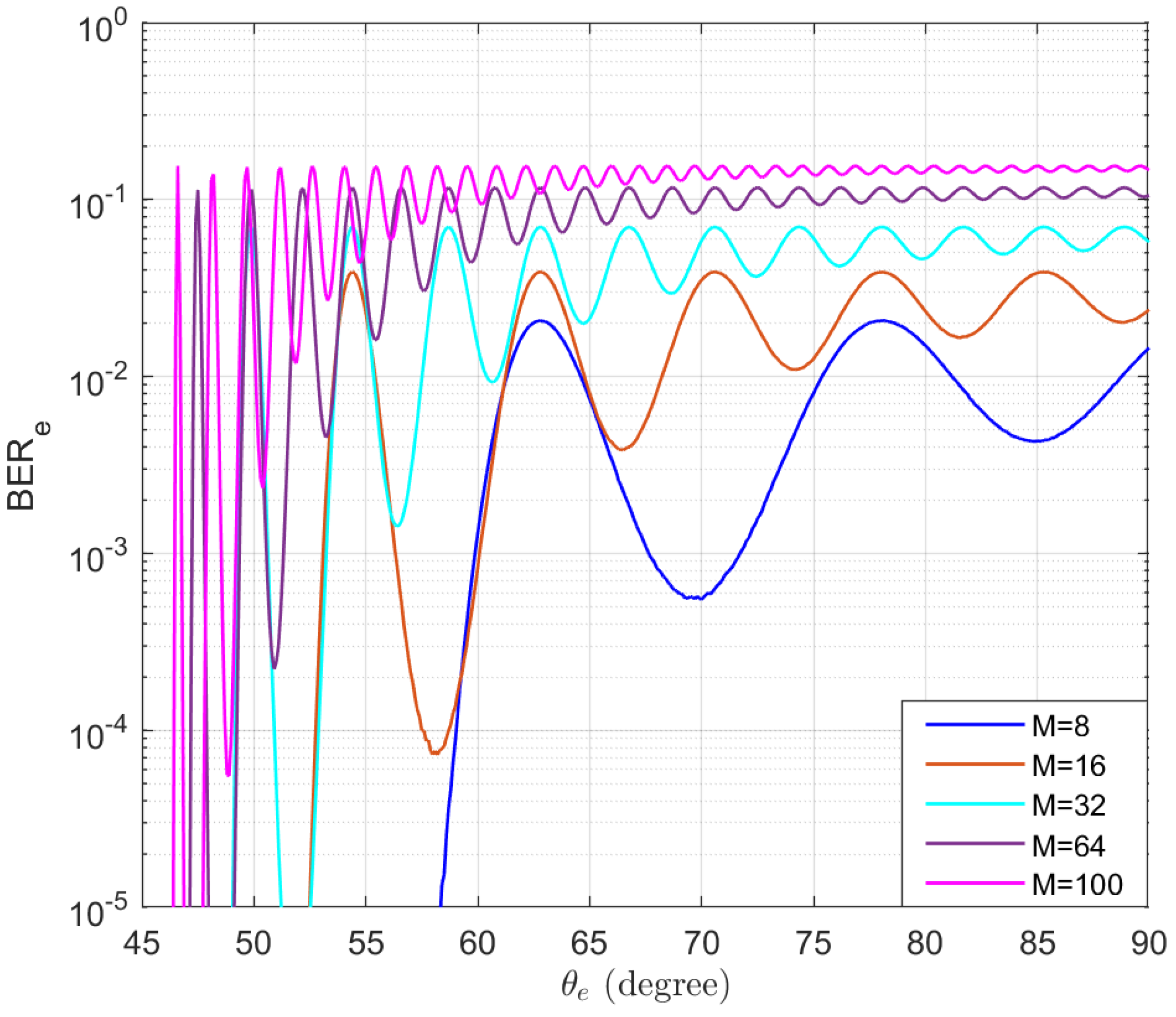
The BER performance of Eve without using AN is also simulated and the results are presented in Figure 7. It can be observed that when the number of antennas is relatively small, even if Bob and Eve are far apart, the BER of Eve remains at a low level, especially when Eve is on the peaks of the sidelobes. The results of this figure demonstrate the necessity of using AN to prevent eavesdropping.
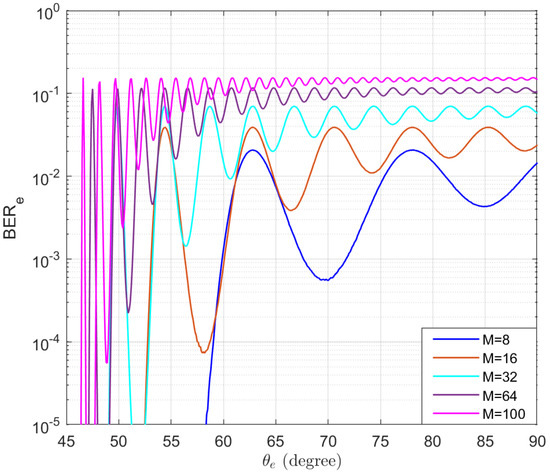
Figure 7.
The simulated BERs of Eve without using AN in the function of the location of Eve .
Moreover, the strategy for maximizing the ergodic secrecy rate [16] has also been simulated. The power allocation factors are optimized. The expectations of and are presented in Figure 8 and the BER results are shown in Figure 9. It can be observed that the difference in SINR between Bob and Eve has increased compared to Figure 3, but the BER of Eve decreases as the location of Eve becomes farther. This is because this strategy does not directly degrade the SINR of Eve.
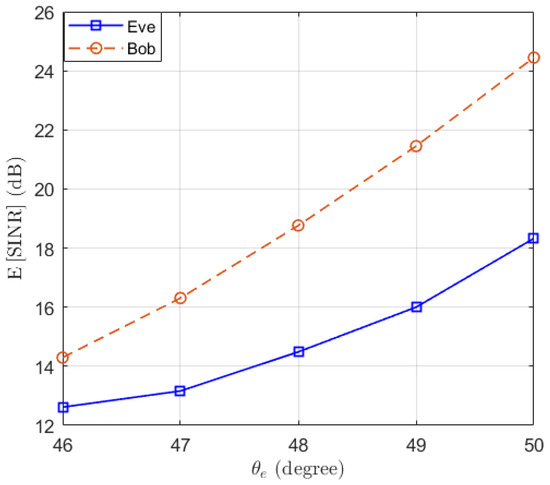
Figure 8.
The expectations of and when the ergodic secrecy rate is maximized in the function of the location of Eve .
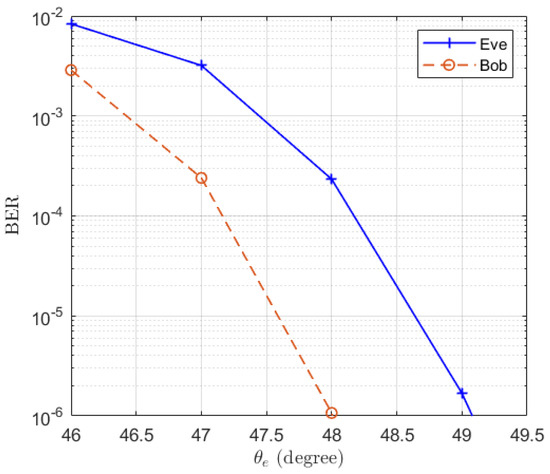
Figure 9.
The simulated BERs when the ergodic secrecy rate is maximized in the function of the location of Eve .
To clarify the impact of the Rician parameter, the case where dB is simulated to compare with the results of dB. The expectations of and are presented in Figure 10. We note that a higher value leads to a degradation in the performance of Eve. However, the trend of the eavesdropper’s SINR decreasing as the location moves away from the user remains unchanged. Hence, the proposed algorithm can be applied for LoS channels with different K-factors to degrade the SINR performance of an eavesdropper. An example of the K-factor for different scenarios can be found in ([46], Table 7.5–6).
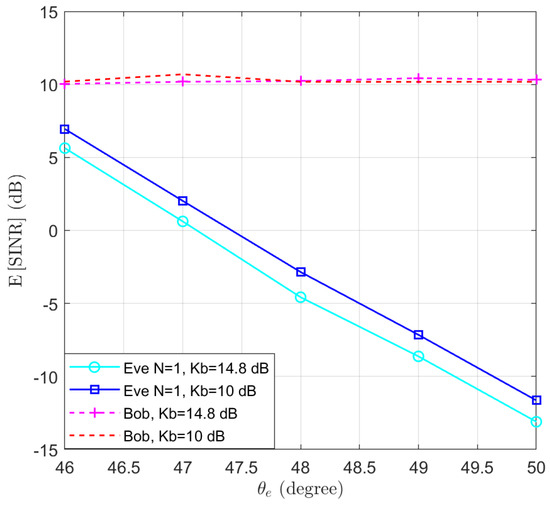
Figure 10.
The expectation of and for dB in the function of the location of Eve .
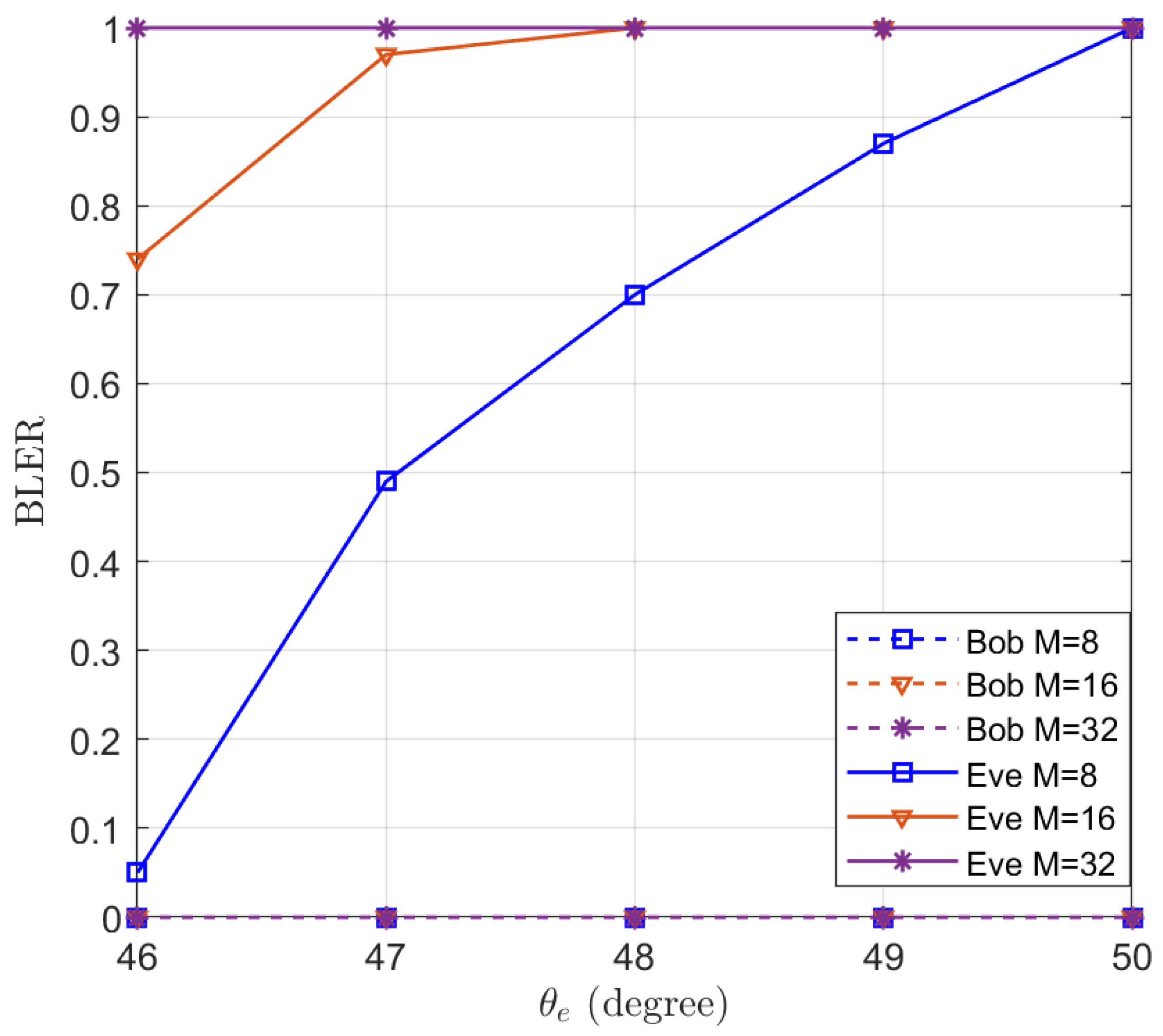
To illustrate the effectiveness of the proposed algorithm for minimizing the QoS of the eavesdropper, the BLER of Bob and Eve are simulated in Figure 11 using Polar code as the ECC. Polar code [32] is an emerging channel coding technique for 5th generation (5G) mobile communication systems [47]. Polar code has been adopted for enhanced mobile broadband (eMBB) control channels. We set the rate of the code , , and the length of information as 128. It can be seen from Figure 11 that the BLER of Bob remains 0 and the BLER of Eve increases with . When , the BLER of Eve reaches 1 for , which means that eavesdroppers beyond 5° cannot decode the information. When the number of antennas reaches 32, eavesdroppers beyond 1° also cannot decode the message.
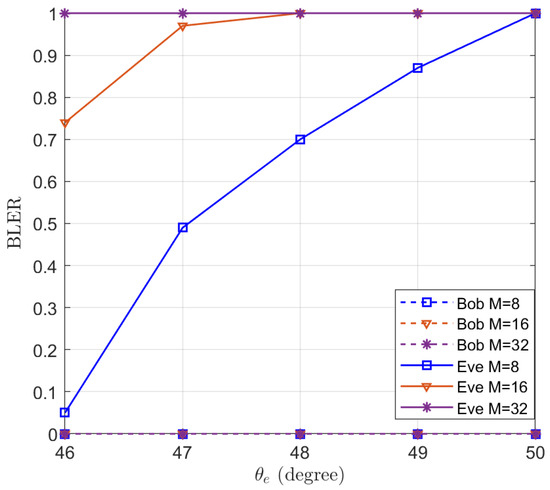
Figure 11.
The simulated BLERs of Bob and Eve in the function of the location of Eve .
In the case where the location of Eve is unknown to Alice, Alice can design beamforming schemes using the location of Eve that results in a sufficiently low BLER for Eve. In this way, the chosen location of Eve and more distant areas are protected. For the region between Bob and the chosen location of Eve, additional surveillance measures can be employed to prevent eavesdropping.
6. Conclusions
This work investigated the performance of AN-assisted location-based beamforming in Rician wiretap channels. Assuming that the location information of the legitimate user and the eavesdropper is available at the base station, AN is used to interfere with eavesdroppers. The influence of the AN has been considered for both the legitimate user and the eavesdropper. Closed-form PDF approximations of the SINRs are derived. Moreover, the expressions of the expectations of the SINRs and the BERs are deduced. A secure beamforming scheme is proposed to ensure a minimum SINR requirement for the legitimate user and minimize the SINR of the eavesdropper. Numerical results show that the proposed beamforming scheme can effectively degrade the performance of nearby eavesdroppers even with a small number of antennas. When the base station has eight antennas, the BLER of the eavesdropper reaches 1 when the eavesdropper is located 5° away from the legitimate user, while the BLER of the legitimate user remains 0. In the case where the location of the eavesdropper is unknown to the base station, the proposed beamforming scheme can still be used to minimize the area near the legitimate user with eavesdropping risk. When more antennas are used at the base station, the area with eavesdropping risk can be further reduced.
Author Contributions
H.F.: Conceptualization, methodology, software, validation, formal analysis, resources, writing—original draft preparation; X.Z.: software, validation, investigation, resources, writing—review and editing; L.P.: writing—review and editing, project administration, funding acquisition. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the National Key Research and Development Program of China under Grant 2022YFB4300300, the National Natural Science Foundation of China under Grants 62001106 and 62171120, the Guangdong Key Research and Development Program under Grant 2020B0303010001, the Jiangsu Provincial Key Laboratory of Network and Information Security No. BM2003201, and the Purple Mountain Laboratories for Network and Communication Security.
Data Availability Statement
The data presented in this study are available on request from the corresponding author.
Conflicts of Interest
The authors declare no conflict of interest. The funders had no role in the design of the study, in the collection, analyses, or interpretation of data, in the writing of the manuscript, or in the decision to publish the results.
References
- Zou, Y.; Zhu, J.; Wang, X.; Hanzo, L. A survey on wireless security: Technical challenges, recent advances, and future trends. Proc. IEEE 2016, 104, 1727–1765. [Google Scholar] [CrossRef]
- Wu, Y.; Khisti, A.; Xiao, C.; Caire, G.; Wong, K.K.; Gao, X. A Survey of Physical Layer Security Techniques for 5G Wireless Networks and Challenges Ahead. IEEE J. Sel. Areas Commun. 2018, 36, 679–695. [Google Scholar] [CrossRef]
- Sanenga, A.; Mapunda, G.A.; Jacob, T.M.L.; Marata, L.; Basutli, B.; Chuma, J.M. An Overview of Key Technologies in Physical Layer Security. Entropy 2020, 22, 1261. [Google Scholar] [CrossRef] [PubMed]
- Khisti, A.; Wornell, G.W. Secure transmission with multiple antennas I: The MISOME wiretap channel. IEEE Trans. Inf. Theory 2010, 56, 3088–3104. [Google Scholar] [CrossRef]
- Li, X.; Jin, S.; Suraweera, H.A.; Hou, J.; Gao, X. Statistical 3-D beamforming for large-scale MIMO downlink systems over Rician fading channels. IEEE Trans. Commun. 2016, 64, 1529–1543. [Google Scholar] [CrossRef]
- Goel, S.; Negi, R. Guaranteeing secrecy using artificial noise. IEEE Trans. Wirel. Commun. 2008, 7, 2180–2189. [Google Scholar] [CrossRef]
- Zhang, X.; Zhou, X.; McKay, M.R. On the design of artificial-noise-aided secure multi-antenna transmission in slow fading channels. IEEE Trans. Veh. Technol. 2013, 62, 2170–2181. [Google Scholar] [CrossRef]
- Shang, P.; Yu, W.; Zhang, K.; Jiang, X.Q.; Kim, S. Secrecy enhancing scheme for spatial modulation using antenna selection and artificial noise. Entropy 2019, 21, 626. [Google Scholar] [CrossRef]
- Joung, J.; Choi, J.; Jung, B.C.; Yu, S. Artificial noise injection and its power loading methods for secure space-time line coded systems. Entropy 2019, 21, 515. [Google Scholar] [CrossRef]
- Yang, N.; Elkashlan, M.; Duong, T.Q.; Yuan, J.; Malaney, R. Optimal Transmission With Artificial Noise in MISOME Wiretap Channels. IEEE Trans. Veh. Technol. 2016, 65, 2170–2181. [Google Scholar] [CrossRef]
- Bai, J.; Dong, T.; Zhang, Q.; Wang, S.; Li, N. Coordinated Beamforming and Artificial Noise in the Downlink Secure Multi-Cell MIMO Systems Under Imperfect CSI. IEEE Wireless Commun. Lett. 2020, 9, 1023–1026. [Google Scholar] [CrossRef]
- Ta, H.Q.; Cao, L.; Oh, H. Novel Noise Injection Scheme to Guarantee Zero Secrecy Outage under Imperfect CSI. Entropy 2023, 25, 1594. [Google Scholar] [CrossRef]
- Zappone, A.; Lin, P.H.; Jorswieck, E. Energy efficiency of confidential multi-antenna systems with artificial noise and statistical CSI. IEEE J. Sel. Topics Signal Process. 2016, 10, 1462–1477. [Google Scholar] [CrossRef]
- Hu, L.; Wu, B.; Tang, J.; Pan, F.; Wen, H. Outage constrained secrecy rate maximization using artificial-noise aided beamforming and cooperative jamming. In Proceedings of the 2016 IEEE International Conference on Communications (ICC), Kuala Lumpur, Malaysia, 22–27 May 2016; IEEE: Piscataway, NJ, USA, 2016; pp. 1–5. [Google Scholar]
- Wang, W.; Teh, K.C.; Li, K.H. Secrecy throughput maximization for MISO multi-eavesdropper wiretap channels. IEEE Trans. Inf. Forensics Secur. 2016, 12, 505–515. [Google Scholar] [CrossRef]
- Wang, W.; Chen, X.; You, L.; Yi, X.; Gao, X. Artificial noise assisted secure massive MIMO transmission exploiting statistical CSI. IEEE Commun. Lett. 2019, 23, 2386–2389. [Google Scholar] [CrossRef]
- Gu, Y.; Wu, Z.; Yin, Z.; Zhang, X. The Secrecy Capacity Optimization Artificial Noise: A New Type of Artificial Noise for Secure Communication in MIMO System. IEEE Access 2019, 7, 58353–58360. [Google Scholar] [CrossRef]
- Tugnait, J.K. Pilot spoofing attack detection and countermeasure. IEEE Trans. Commun. 2018, 66, 2093–2106. [Google Scholar] [CrossRef]
- Huang, K.W.; Wang, H.M.; Wu, Y.; Schober, R. Pilot spoofing attack by multiple eavesdroppers. IEEE Trans. Wirel. Commun. 2018, 17, 6433–6447. [Google Scholar] [CrossRef]
- Xiong, Q.; Liang, Y.C.; Li, K.H.; Gong, Y.; Han, S. Secure transmission against pilot spoofing attack: A two-way training-based scheme. IEEE Trans. Inf. Forensics Secur. 2016, 11, 1017–1026. [Google Scholar] [CrossRef]
- Xing, Z.; Wang, R.; Yuan, X.; Wu, J. Location Information Assisted Beamforming Design for Reconfigurable Intelligent Surface Aided Communication Systems. IEEE Trans. Wirel. Commun. 2023, 22, 7676–7695. [Google Scholar] [CrossRef]
- Yan, S.; Malaney, R. Location-based beamforming for enhancing secrecy in Rician wiretap channels. IEEE Trans. Wirel. Commun. 2015, 15, 2780–2791. [Google Scholar] [CrossRef]
- Liu, C.; Malaney, R. Location-based beamforming and physical layer security in Rician wiretap channels. IEEE Trans. Wirel. Commun. 2016, 15, 7847–7857. [Google Scholar] [CrossRef]
- Abdelreheem, A.; Mohamed, E.M.; Esmaiel, H. Location-Based Millimeter Wave Multi-Level Beamforming Using Compressive Sensing. IEEE Commun. Lett. 2018, 22, 185–188. [Google Scholar] [CrossRef]
- Lin, Y.; Jin, L.; Huang, K.; Zhong, Z.; Han, Q. Covert Threat Region Analysis of 3-D Location-Based Beamforming in Rician Channel. IEEE Wirel. Commun. Lett. 2022, 11, 1253–1257. [Google Scholar] [CrossRef]
- Lichtman, M.; Rao, R.; Marojevic, V.; Reed, J.; Jover, R.P. 5G NR jamming, spoofing, and sniffing: Threat assessment and mitigation. In Proceedings of the 2018 IEEE International Conference on Communications Workshops (ICC Workshops), Kansas City, MO, USA, 20–24 May 2018; pp. 1–6. [Google Scholar]
- Xu, W.; Li, B.; Tao, L.; Xiang, W. Artificial Noise Assisted Secure Transmission for Uplink of Massive MIMO Systems. IEEE Trans. Veh. Technol. 2021, 70, 6750–6762. [Google Scholar] [CrossRef]
- Hu, D.; Mu, P.; Zhang, W.; Wang, W. Minimization of Secrecy Outage Probability With Artificial-Noise-Aided Beamforming for MISO Wiretap Channels. IEEE Commun. Lett. 2020, 24, 401–404. [Google Scholar] [CrossRef]
- Yun, S.; Kang, J.M.; Kim, I.M.; Ha, J. Deep Artificial Noise: Deep Learning-Based Precoding Optimization for Artificial Noise Scheme. IEEE Trans. Veh. Technol. 2020, 69, 3465–3469. [Google Scholar] [CrossRef]
- Liao, W.C.; Chang, T.H.; Ma, W.K.; Chi, C.Y. QoS-based transmit beamforming in the presence of eavesdroppers: An optimized artificial-noise-aided approach. IEEE Trans. Signal Process. 2010, 59, 1202–1216. [Google Scholar] [CrossRef]
- Wang, J.; Han, S.; Xu, S.; Li, J. SNR-Outage-Based Robust Artificial Noise-Aided Beamforming for Correlated MISO Wiretap Channels Under Gaussian Channel Uncertainties. IEEE Syst. J. 2023, 17, 1569–1580. [Google Scholar] [CrossRef]
- Arikan, E. Channel polarization: A method for constructing capacity-achieving codes for symmetric binary-input memoryless channels. IEEE Trans. Inf. Theory 2009, 55, 3051–3073. [Google Scholar] [CrossRef]
- Suh, S.; Basu, A.; Schlottmann, C.; Hasler, P.E.; Barry, J.R. Low-power discrete Fourier transform for OFDM: A programmable analog approach. IEEE Trans. Circuits Syst. 2011, 58, 290–298. [Google Scholar] [CrossRef]
- Han, Y.; Jin, S.; Zhang, J.; Zhang, J.; Wong, K.K. DFT-based hybrid beamforming multiuser systems: Rate analysis and beam selection. IEEE J. Sel. Topics Signal Process. 2018, 12, 514–528. [Google Scholar] [CrossRef]
- Cui, M.; Wu, Z.; Lu, Y.; Wei, X.; Dai, L. Near-Field MIMO Communications for 6G: Fundamentals, Challenges, Potentials, and Future Directions. IEEE Commun. Mag. 2023, 61, 40–46. [Google Scholar] [CrossRef]
- Lu, H.; Zeng, Y. Near-Field Modeling and Performance Analysis for Multi-User Extremely Large-Scale MIMO Communication. IEEE Commun. Lett. 2022, 26, 277–281. [Google Scholar] [CrossRef]
- Shen, D.; Dai, L.; Su, X.; Suo, S. Multi-Beam Design for Near-Field Extremely Large-Scale RIS-Aided Wireless Communications. IEEE Trans. Green Commun. Netw. 2023, 7, 1542–1553. [Google Scholar] [CrossRef]
- Goldsmith, A. Wireless Communications; Cambridge University Press: Cambridge, UK, 2005. [Google Scholar]
- Aalo, V.; Zhang, J. Performance analysis of maximal ratio combining in the presence of multiple equal-power cochannel interferers in a Nakagami fading channel. IEEE Trans. Veh. Technol. 2001, 50, 497–503. [Google Scholar] [CrossRef]
- Wolfram. HypergeometricU. Available online: http://functions.wolfram.com/07.33.26.0007.01 (accessed on 18 October 2023).
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Academic Press Inc.: Cambridge, MA, USA, 2007. [Google Scholar]
- Wolfram. MeijerG. Available online: http://functions.wolfram.com/07.34.21.0085.01 (accessed on 19 October 2023).
- Atapattu, S.; Tellambura, C.; Jiang, H. A mixture Gamma distribution to model the SNR of wireless channels. IEEE Trans. Wirel. Commun. 2011, 10, 4193–4203. [Google Scholar] [CrossRef]
- Abramowitz, M.; Stegun, I.A. (Eds.) Handbook of Mathematical Functions: With Formulas, Graphs, and Mathematical Tables; Dover Publications: Mineola, NY, USA, 1972. [Google Scholar]
- Shin, H.; Lee, J.H. On the error probability of binary and M-ary signals in Nakagami-m fading channels. IEEE Trans. Commun. 2004, 52, 536–539. [Google Scholar] [CrossRef]
- 3rd Generation Partnership Project (3GPP). Study on Channel Model for Frequencies from 0.5 to 100 GHz (Release 16); Technical Specification Group Radio Access Network; Technical Report (TR) 38.901; ETSI: Sophia Antipolis, France, 2019. [Google Scholar]
- Dong, L.; Zhao, H.; Chen, Y.; Chen, D.; Wang, T.; Lu, L.; Zhang, B.; Hu, L.; Gu, L.; Li, B.; et al. Introduction on IMT-2020 5G trials in China. IEEE J. Sel. Areas Commun. 2017, 35, 1849–1866. [Google Scholar] [CrossRef]
Disclaimer/Publisher’s Note: The statements, opinions and data contained in all publications are solely those of the individual author(s) and contributor(s) and not of MDPI and/or the editor(s). MDPI and/or the editor(s) disclaim responsibility for any injury to people or property resulting from any ideas, methods, instructions or products referred to in the content. |
© 2023 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).