Twin-Field Quantum Digital Signature with Fully Discrete Phase Randomization
Abstract
:1. Introduction
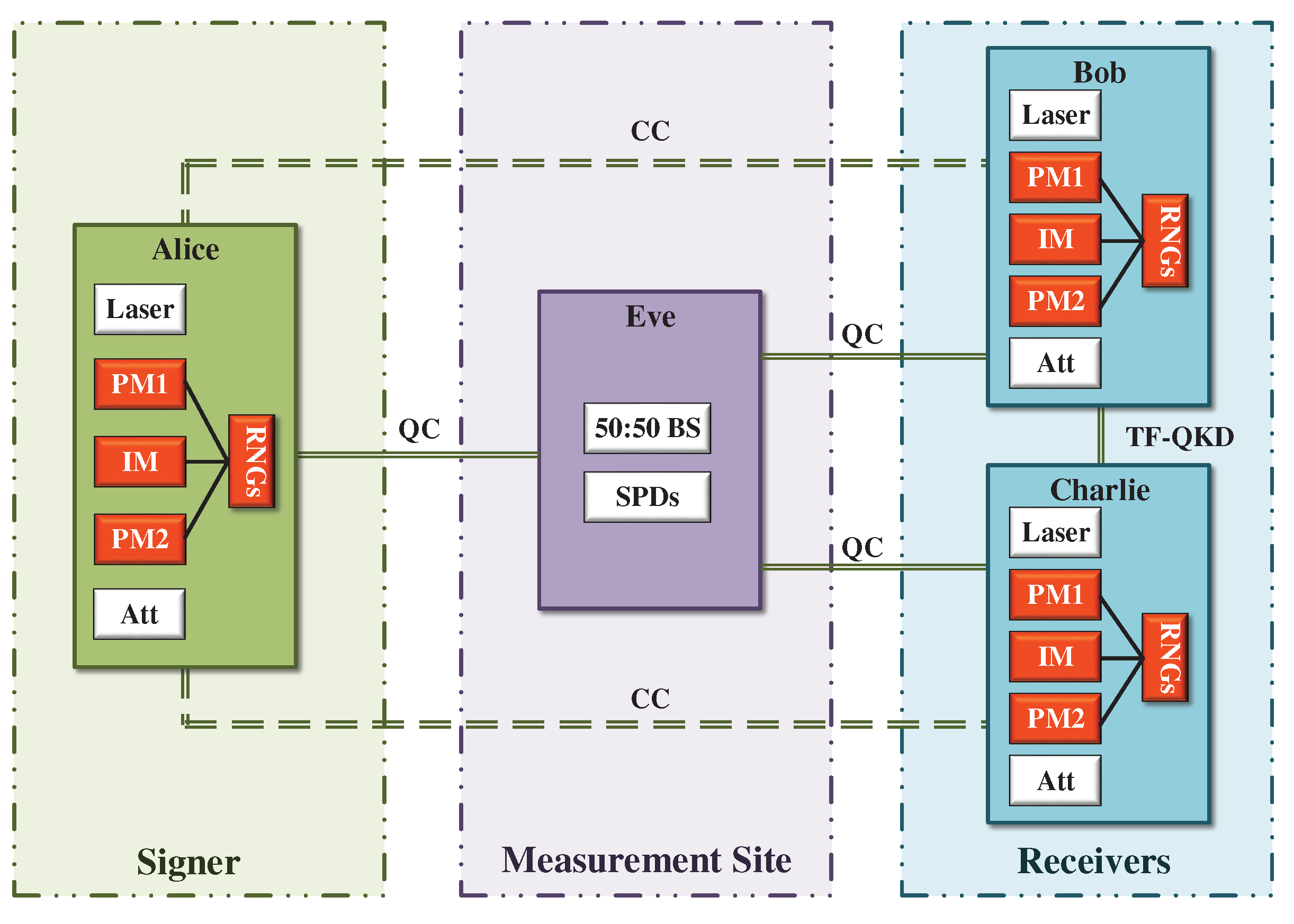
2. TF-QDS Protocol with Fully Discrete Phase Randomization
2.1. Distribution Stage
- (1)
- For each message or 1, Alice and Bob use the discrete-phase-randomized TF-KGP [45] to generate keys of length , Alice holds the key and Bob holds the key . Similarly, Alice and Charlie perform the discrete-phase-randomized TF-KGP [45] to generate keys and , respectively. The detailed steps for key distribution can be found in Section 3. Alice’s signature for m is .
- (2)
- For each m, Bob and Charlie perform the symmetrization of keys. That is, Bob (Charlie) randomly chooses half of the bits in his key (), called (), and then sends these bits to Charlie (Bob) using an authenticated classical channel. The remaining bits in () are named (). After the symmetrization of keys, Bob’s and Charlie’s keys are denoted as and respectively; therefore, Alice cannot distinguish whether a key is Bob’s or Charlie’s, which guarantees the security against repudiation. In addition, Bob (Charlie) can only obtain half of (), which guarantees the security against forging.
2.2. Messaging Stage
- (1)
- For signing a one-bit message m, Alice sends the signature declaration to Bob.
- (2)
- Bob checks and records the number of mismatches between the declaration and his key . Particularly, Bob separately calculates the number of mismatches for the key that received directly from Alice and the key that forwarded by Charlie. If the number of mismatches for both parts is fewer than , he accepts the signature, where is a small threshold determined by experimental parameters and a desired security level.
- (3)
- Bob then forwards to Charlie.
- (4)
- Charlie checks the number of mismatches between and . The verification method is similar to that performed by Bob, except with a different threshold , where . If the number of mismatches for and is fewer than , Charlie accepts as the original signature generated by Alice. It is worth noting that two different thresholds and are required to ensure the non-repudiation of QDS protocol.
3. TF-KGP
3.1. Preparation
3.2. Measurement
3.3. Sifting
3.4. Parameter Estimation
4. Security Analysis
4.1. Robustness
4.2. Non-Repudiation
4.3. Unforgeability
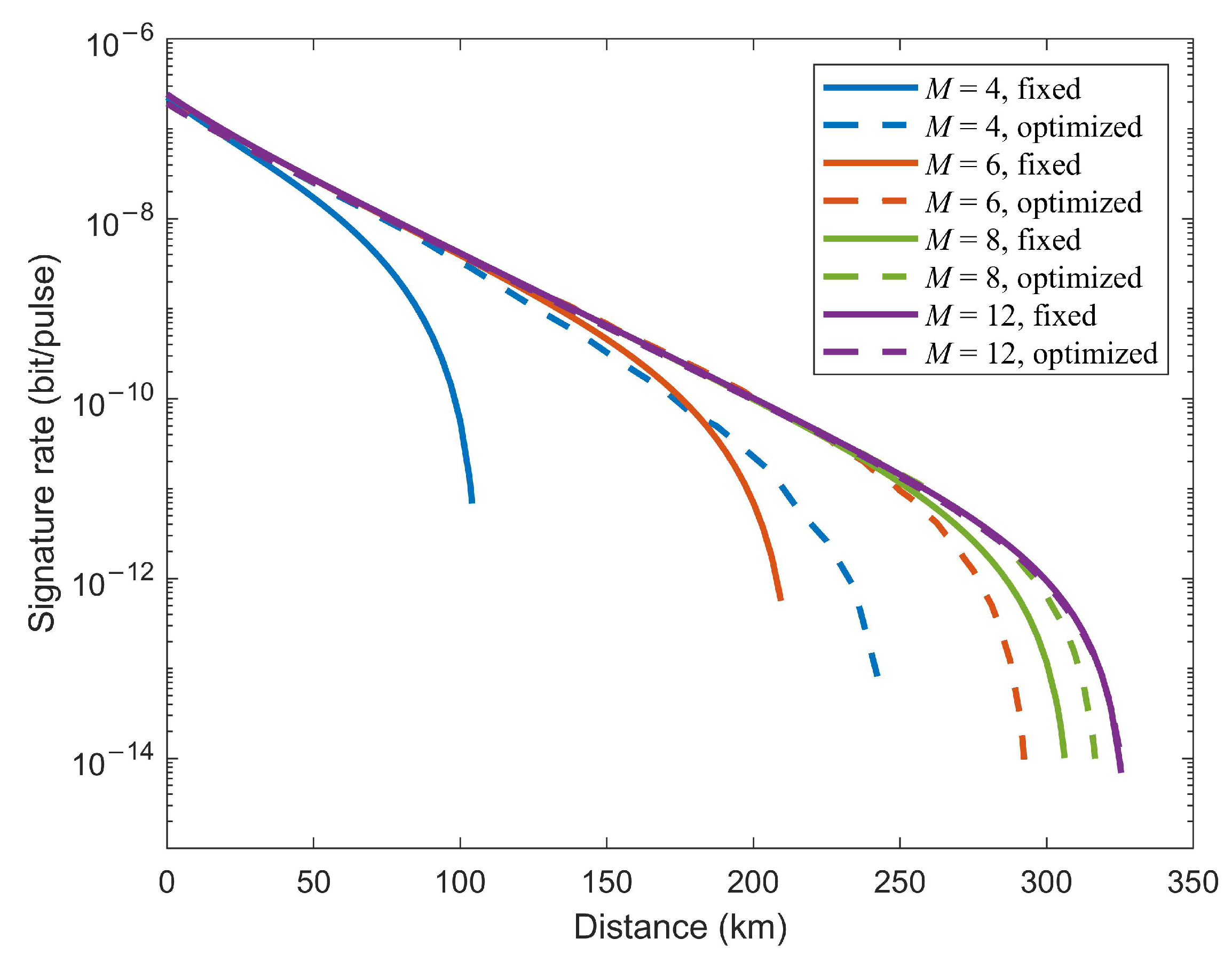
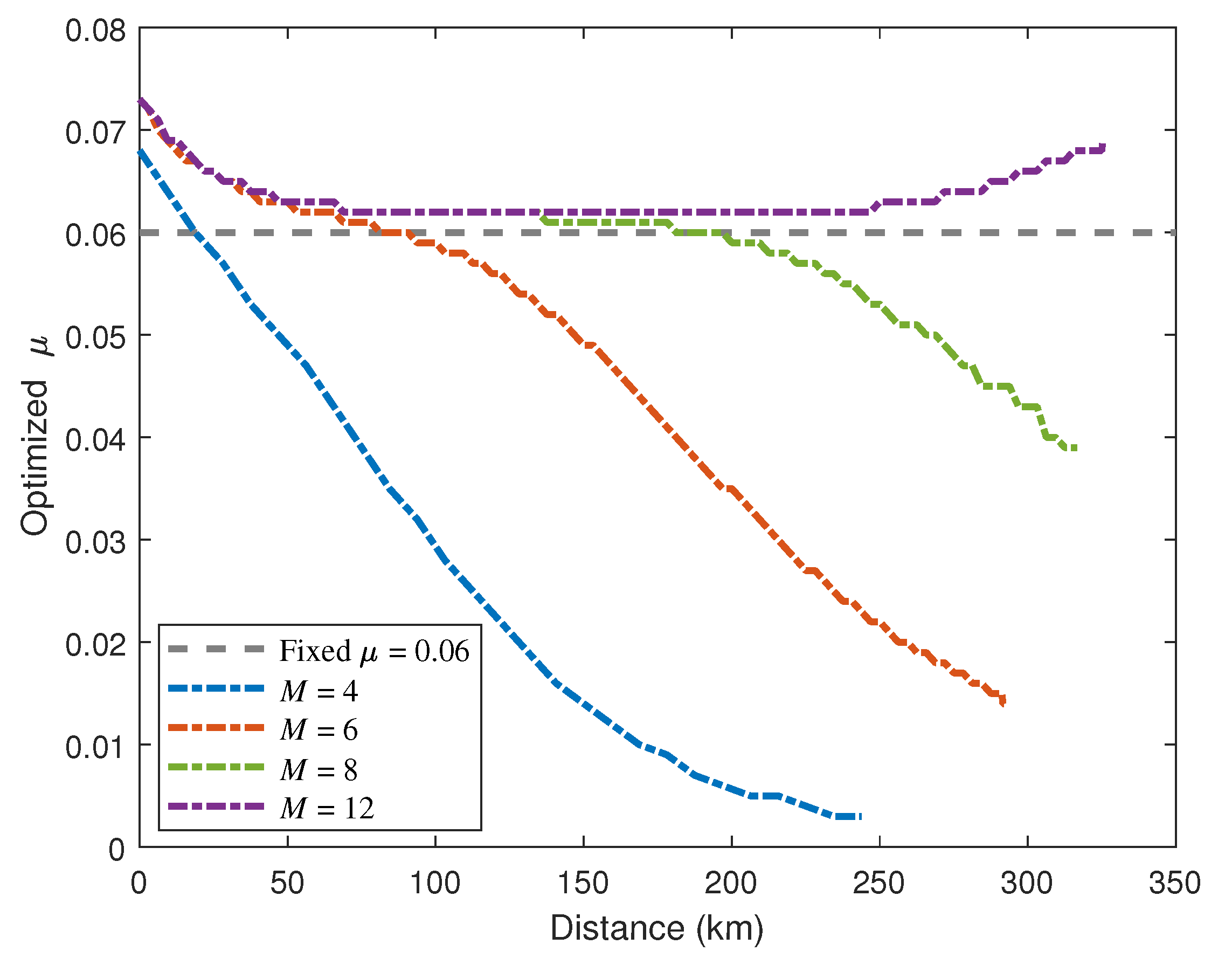
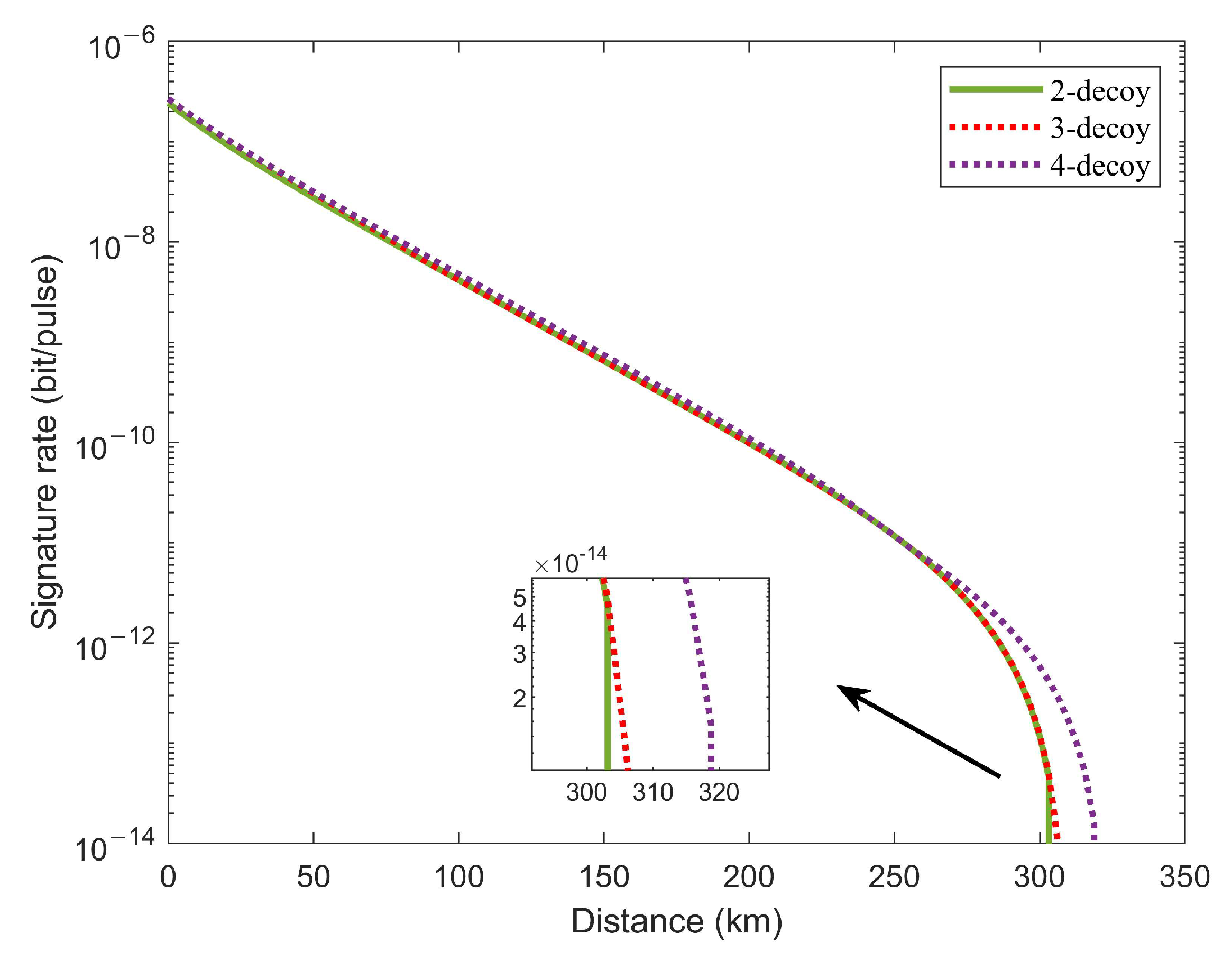
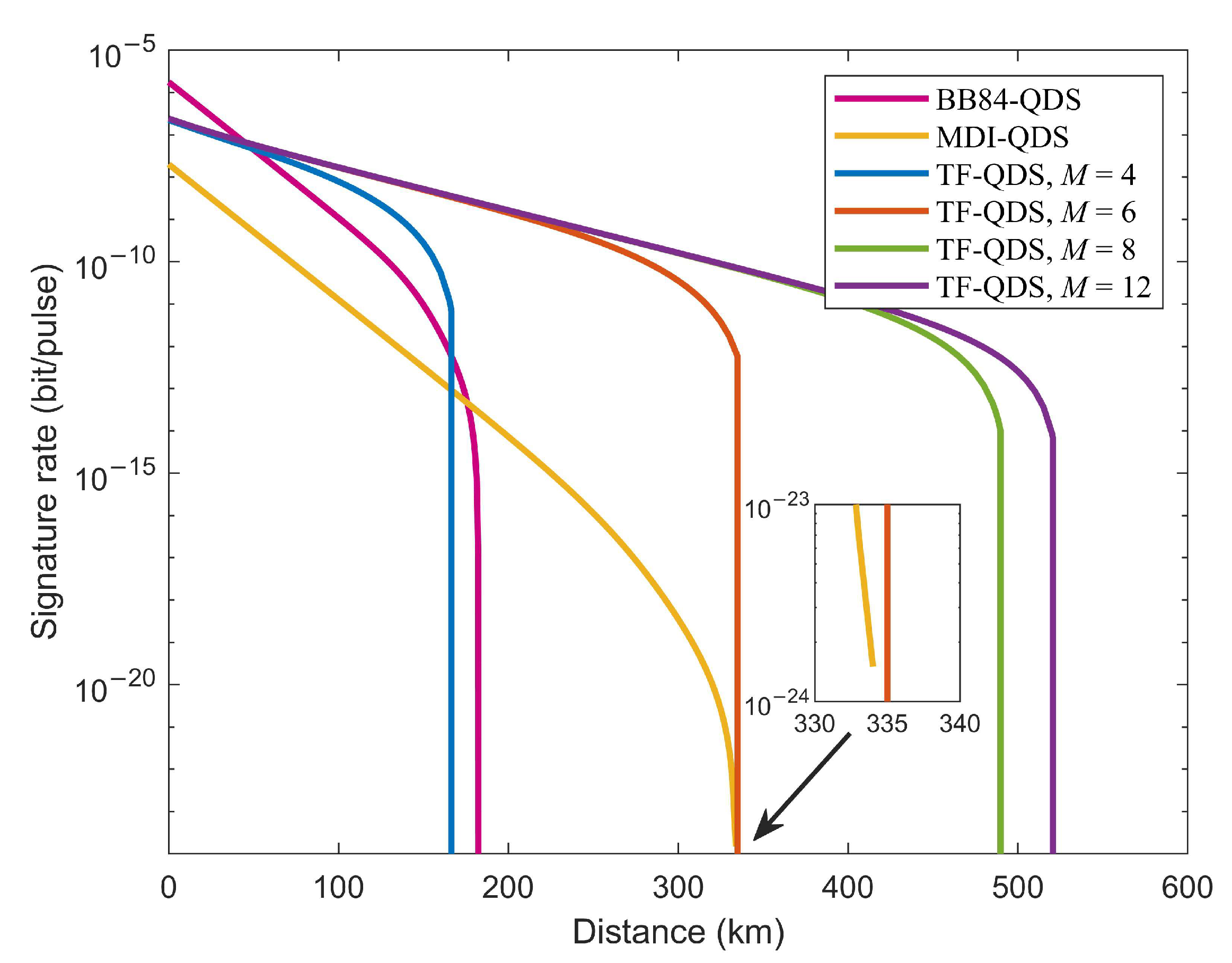
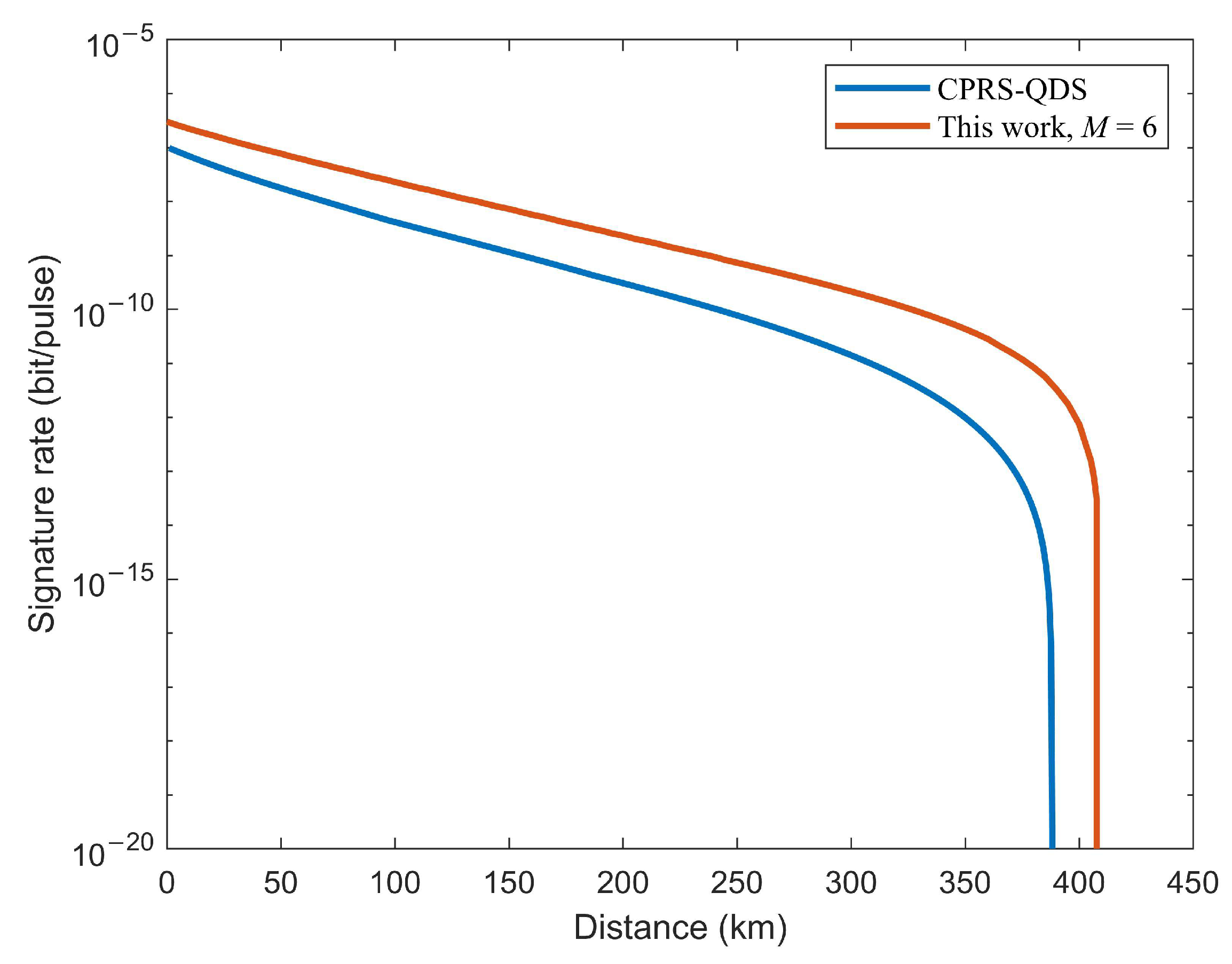
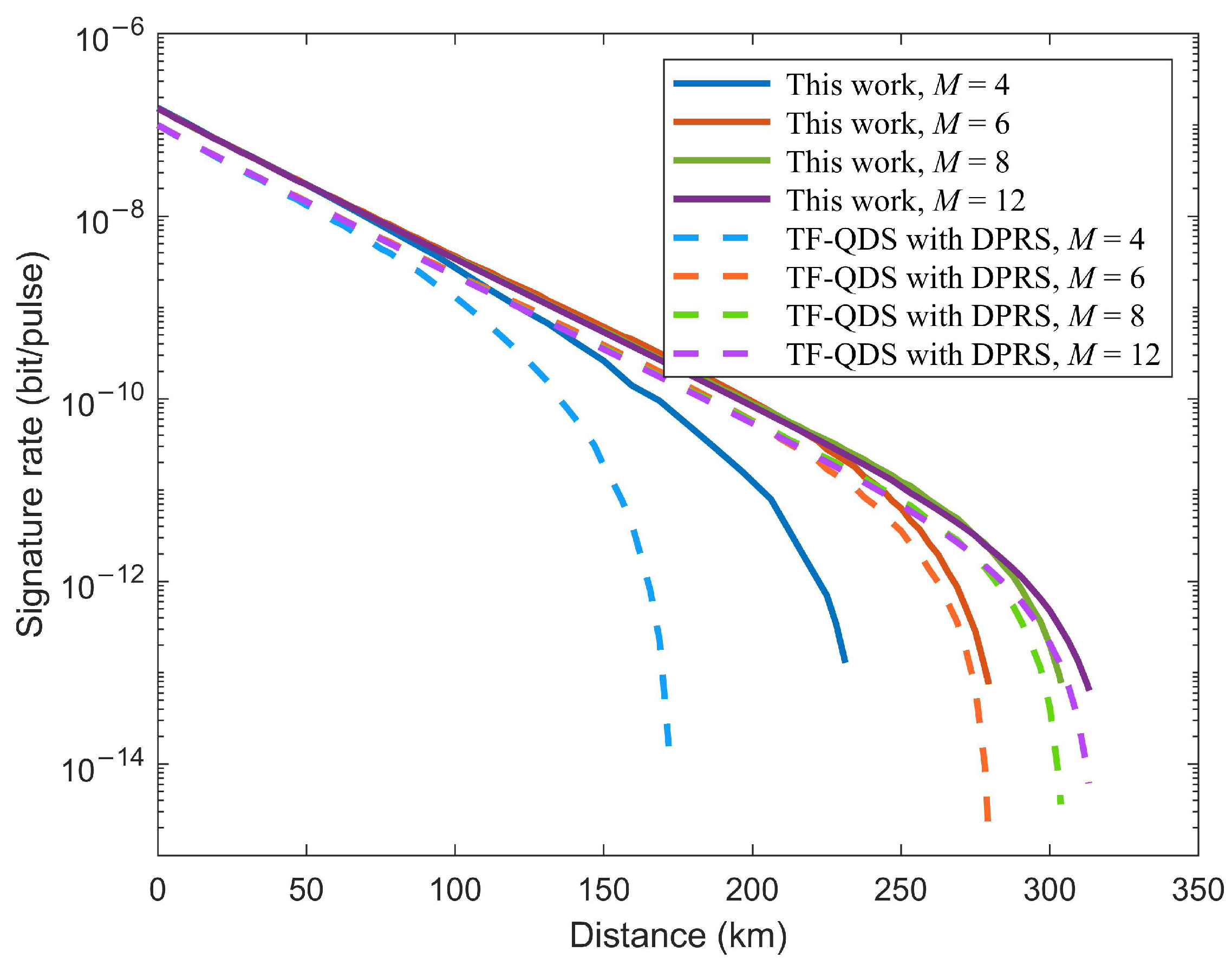
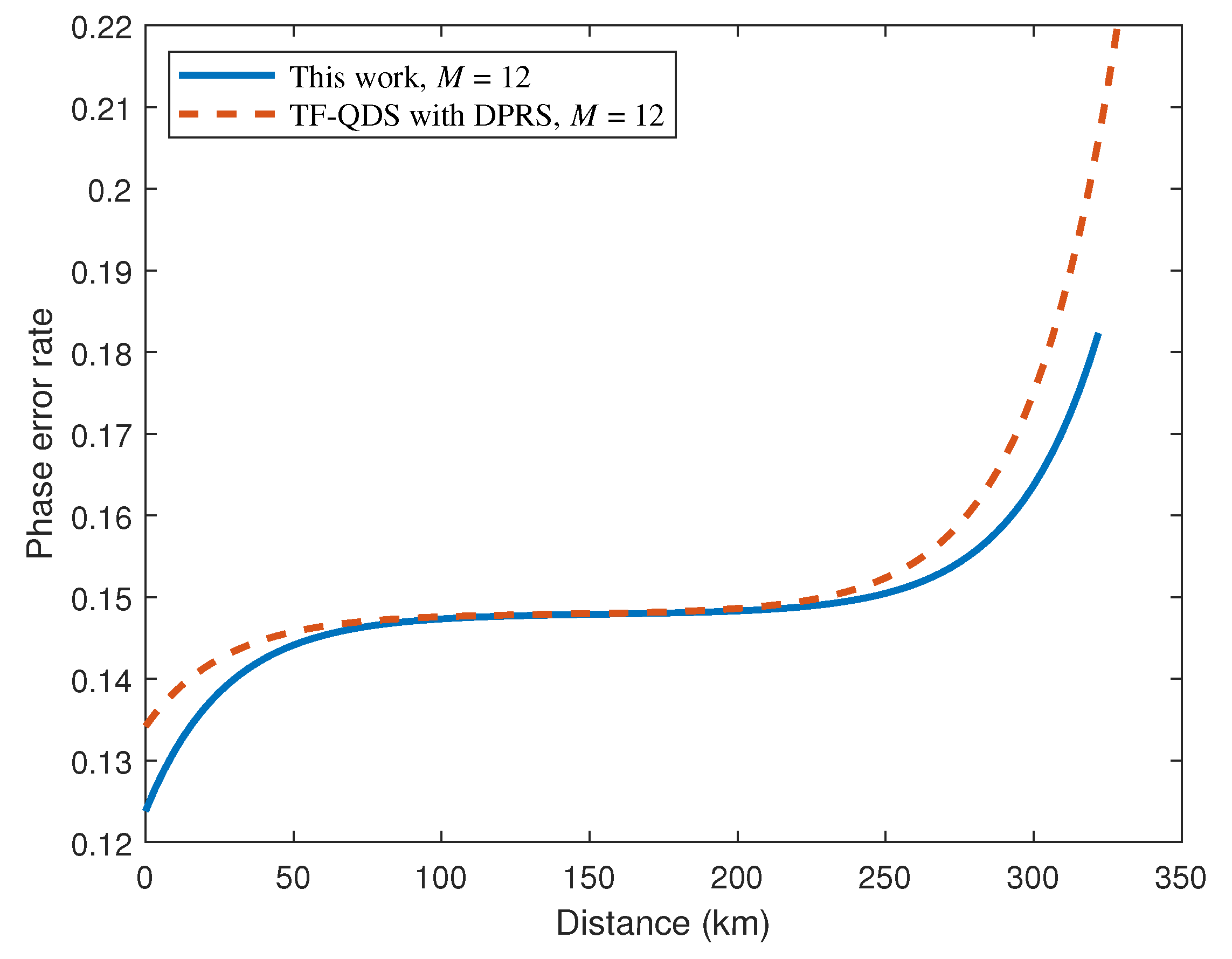
5. Numerical Simulation
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
Appendix A. Parameter Estimation
References
- Diffie, W.; Hellman, M.E. New directions in cryptography. In Secure Communications and Asymmetric Cryptosystems; Simmons, G.J., Ed.; Routledge: London, UK; New York, NY, USA, 2019; pp. 143–180. [Google Scholar]
- Shor, P.W. Algorithms for quantum computation: Discrete logarithms and factoring. In Proceedings of the 35th Annual Symposium on Foundations of Computer Science, Santa Fe, NM, USA, 20–22 November 1994; pp. 124–134. [Google Scholar]
- Nielsen, M.A.; Chuang, I.L. Quantum computation and quantum information. Am. J. Phys. 2002, 70, 558–559. [Google Scholar] [CrossRef] [Green Version]
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 2002, 74, 145. [Google Scholar] [CrossRef] [Green Version]
- Amiri, R.; Andersson, E. Unconditionally secure quantum signatures. Entropy 2015, 17, 5635–5659. [Google Scholar] [CrossRef] [Green Version]
- Gottesman, D.; Chuang, I. Quantum digital signatures. arXiv 2001, arXiv:quant-ph/0105032. [Google Scholar]
- Andersson, E.; Curty, M.; Jex, I. Experimentally realizable quantum comparison of coherent states and its applications. Phys. Rev. A 2006, 74, 022304. [Google Scholar] [CrossRef] [Green Version]
- Dunjko, V.; Wallden, P.; Andersson, E. Quantum digital signatures without quantum memory. Phys. Rev. Lett. 2014, 112, 040502. [Google Scholar] [CrossRef] [Green Version]
- Collins, R.J.; Donaldson, R.J.; Dunjko, V.; Wallden, P.; Clarke, P.J.; Andersson, E.; Jeffers, J.; Buller, G.S. Realization of Quantum Digital Signatures without the Requirement of Quantum Memory. Phys. Rev. Lett. 2014, 113, 040502. [Google Scholar] [CrossRef] [Green Version]
- Clarke, P.J.; Collins, R.J.; Dunjko, V.; Andersson, E.; Jeffers, J.; Buller, G.S. Experimental demonstration of quantum digital signatures using phase-encoded coherent states of light. Nat. Commun. 2012, 3, 1174. [Google Scholar] [CrossRef] [Green Version]
- Wallden, P.; Dunjko, V.; Kent, A.; Andersson, E. Quantum digital signatures with quantum-key-distribution components. Phys. Rev. A 2015, 91, 042304. [Google Scholar] [CrossRef] [Green Version]
- Donaldson, R.J.; Collins, R.J.; Kleczkowska, K.; Amiri, R.; Wallden, P.; Dunjko, V.; Jeffers, J.; Andersson, E.; Buller, G.S. Experimental demonstration of kilometer-range quantum digital signatures. Phys. Rev. A 2016, 93, 012329. [Google Scholar] [CrossRef] [Green Version]
- Amiri, R.; Wallden, P.; Kent, A.; Andersson, E. Secure quantum signatures using insecure quantum channels. Phys. Rev. A 2016, 93, 032325. [Google Scholar] [CrossRef] [Green Version]
- Yin, H.L.; Fu, Y.; Chen, Z.B. Practical quantum digital signature. Phys. Rev. A 2016, 93, 032316. [Google Scholar] [CrossRef] [Green Version]
- Zhang, C.M.; Zhu, Y.; Chen, J.J.; Wang, Q. Practical quantum digital signature with configurable decoy states. Quantum Inf. Process. 2020, 19, 151. [Google Scholar] [CrossRef]
- Puthoor, I.V.; Amiri, R.; Wallden, P.; Curty, M.; Andersson, E. Measurement-device-independent quantum digital signatures. Phys. Rev. A 2016, 94, 022328. [Google Scholar] [CrossRef] [Green Version]
- Yin, H.L.; Wang, W.L.; Tang, Y.L.; Zhao, Q.; Liu, H.; Sun, X.X.; Zhang, W.J.; Li, H.; Puthoor, T.V.; You, L.X.; et al. Experimental measurement-device-independent quantum digital signatures over a metropolitan network. Phys. Rev. A 2017, 95, 042338. [Google Scholar] [CrossRef] [Green Version]
- Roberts, G.L.; Lucamarini, M.; Yuan, Z.L.; Dynes, J.F.; Comandar, L.C.; Sharpe, A.W.; Shields, A.J.; Curty, M.; Puthoor, I.V.; Andersson, E. Experimental measurement-device-independent quantum digital signatures. Nat. Commun. 2017, 8, 1098. [Google Scholar] [CrossRef] [Green Version]
- Lo, H.K.; Ma, X.; Chen, K. Decoy state quantum key distribution. Phys. Rev. Lett. 2005, 94, 230504. [Google Scholar] [CrossRef] [Green Version]
- Ma, X.; Qi, B.; Zhao, Y.; Lo, H.K. Practical decoy state for quantum key distribution. Phys. Rev. A. 2005, 72, 012326. [Google Scholar] [CrossRef] [Green Version]
- Braunstein, S.L.; Pirandola, S. Side-channel-free quantum key distribution. Phys. Rev. Lett. 2012, 108, 130502. [Google Scholar] [CrossRef] [Green Version]
- Lo, H.K.; Curty, M.; Qi, B. Measurement-device-independent quantum key distribution. Phys. Rev. Lett. 2012, 108, 130503. [Google Scholar] [CrossRef] [Green Version]
- Ma, X.; Razavi, M. Alternative schemes for measurement-device-independent quantum key distribution. Phys. Rev. A 2012, 86, 062319. [Google Scholar] [CrossRef] [Green Version]
- Primaatmaja, I.W.; Lavie, E.; Goh, K.T.; Wang, C.; Lim, C.C.W. Versatile security analysis of measurement-device-independent quantum key distribution. Phys. Rev. A 2019, 99, 062332. [Google Scholar] [CrossRef] [Green Version]
- Pirandola, S.; García-Patrón, R.; Braunstein, S.L.; Lloyd, S. Direct and reverse secret-key capacities of a quantum channel. Phys. Rev. Lett. 2009, 102, 050503. [Google Scholar] [CrossRef] [PubMed] [Green Version]
- Pirandola, S.; Laurenza, R.; Ottaviani, C.; Banchi, L. Fundamental limits of repeaterless quantum communications. Nat. Commun. 2017, 8, 15043. [Google Scholar] [CrossRef] [Green Version]
- Lucamarini, M.; Yuan, Z.L.; Dynes, J.F.; Shields, A.J. Overcoming the rate–distance limit of quantum key distribution without quantum repeaters. Nature 2018, 557, 400–403. [Google Scholar] [CrossRef]
- Tamaki, K.; Lo, H.K.; Wang, W.Y.; Lucamarini, M. Information theoretic security of quantum key distribution overcoming the repeaterless secret key capacity bound. arXiv 2018, arXiv:1805.05511. [Google Scholar]
- Wang, X.B.; Yu, Z.W.; Hu, X.L. Twin-field quantum key distribution with large misalignment error. Phys. Rev. A 2018, 98, 062323. [Google Scholar] [CrossRef] [Green Version]
- Liu, Y.; Yu, Z.W.; Zhang, W.J.; Guan, J.Y.; Chen, J.P.; Zhang, C.; Hu, X.L.; Li, H.; Jiang, C.; Lin, J.; et al. Experimental Twin-Field Quantum Key Distribution through Sending or Not Sending. Phys. Rev. Lett. 2019, 123, 100505. [Google Scholar] [CrossRef] [Green Version]
- Jiang, C.; Yu, Z.W.; Hu, X.L.; Wang, X.B. Unconditional security of sending or not sending twin-field quantum key distribution with finite pulses. Phys. Rev. Appl. 2019, 12, 024061. [Google Scholar] [CrossRef] [Green Version]
- Ma, X.; Zeng, P.; Zhou, H.Y. Phase-Matching Quantum Key Distribution. Phys. Rev. X 2018, 8, 031043. [Google Scholar] [CrossRef] [Green Version]
- Lin, J.; Lütkenhaus, N. Simple security analysis of phase-matching measurement-device-independent quantum key distribution. Phys. Rev. A 2018, 98, 042332. [Google Scholar] [CrossRef] [Green Version]
- Wang, R.; Yin, Z.Q.; Lu, F.Y.; Wang, S.; Chen, W.; Zhang, C.M.; Huang, W.; Xu, B.J.; Guo, G.C.; Han, Z.F. Optimized protocol for twin-field quantum key distribution. Commun. Phys. 2020, 3, 149. [Google Scholar] [CrossRef]
- Cui, C.H.; Yin, Z.Q.; Wang, R.; Chen, W.; Wang, S.; Guo, G.C.; Han, Z.F. Twin-field quantum key distribution without phase postselection. Phys. Rev. Appl. 2019, 11, 034053. [Google Scholar] [CrossRef] [Green Version]
- Lu, F.Y.; Yin, Z.Q.; Wang, R.; Fan, G.J.; Wang, S.; He, D.Y.; Chen, W.; Huang, W.; Xu, B.J.; Guo, G.C. Practical issues of twin-field quantum key distribution. New J. Phys. 2019, 21, 123030. [Google Scholar] [CrossRef] [Green Version]
- Lu, F.Y.; Yin, Z.Q.; Cui, C.H.; Fan, G.J.; Wang, R.; Wang, S.; Chen, W.; He, D.Y.; Huang, W.; Xu, B.J.; et al. Improving the performance of twin-field quantum key distribution. Phys. Rev. A 2019, 100, 022306. [Google Scholar] [CrossRef] [Green Version]
- Curty, M.; Azuma, K.; Lo, H.K. Simple security proof of twin-field type quantum key distribution protocol. NPJ Quantum Inf. 2019, 5, 64. [Google Scholar] [CrossRef]
- Grasselli, F.; Curty, M. Practical decoy-state method for twin-field quantum key distribution. New J. Phys. 2019, 21, 073001. [Google Scholar] [CrossRef] [Green Version]
- Yu, Z.W.; Hu, X.L.; Jiang, C.; Xu, H.; Wang, X.B. Sending-or-not-sending twin-field quantum key distribution in practice. Sci. Rep. 2019, 9, 3080. [Google Scholar] [CrossRef] [Green Version]
- Teng, J.; Lu, F.Y.; Yin, Z.Q.; Fan, G.J.; Wang, R.; Wang, S.; Chen, W.; Huang, W.; Xu, B.J.; Guo, G.C. Twin-field quantum key distribution with passive-decoy state. New J. Phys. 2020, 22, 103017. [Google Scholar] [CrossRef]
- Yu, Y.; Wang, L.; Zhao, S.M.; Mao, Q.P. Decoy-state phase-matching quantum key distribution with source errors. Opt. Express 2021, 29, 2227–2243. [Google Scholar] [CrossRef]
- Cao, Z.; Zhang, Z.; Lo, H.K.; Ma, X. Discrete-phase-randomized coherent state source and its application in quantum key distribution. New J. Phys. 2015, 17, 053014. [Google Scholar] [CrossRef]
- Zhang, C.M.; Xu, Y.W.; Wang, R.; Wang, Q. Twin-field quantum key distribution with discrete-phase-randomized sources. Phys. Rev. Appl. 2020, 14, 064070. [Google Scholar] [CrossRef]
- Currás, L.G.; Wooltorton, L.; Razavi, M. Twin-field quantum key distribution with fully discrete phase randomization. Phys. Rev. Appl. 2021, 15, 014016. [Google Scholar] [CrossRef]
- Lim, C.C.W.; Curty, M.; Walenta, N.; Xu, F.H.; Zbinden, H. Concise security bounds for practical decoy-state quantum key distribution. Phys. Rev. A 2014, 89, 022307. [Google Scholar] [CrossRef] [Green Version]
- Tomamichel, M.; Renner, R. Uncertainty relation for smooth entropies. Phys. Rev. Lett. 2011, 106, 110506. [Google Scholar] [CrossRef]
- Pirandola, S.; Andersen, U.; Banchi, L.; Berta, M.; Bunandar, D.; Colbeck, R.; Englund, D.; Gehring, T.; Lupo, C.; Ottaviani, C.; et al. Advances in quantum cryptography. Adv. Opt. Photonics 2020, 12, 1012–1236. [Google Scholar] [CrossRef] [Green Version]
- Hoeffding, W. The Collected Works of Wassily Hoeffding; Springer: Berlin, Germany, 1994; pp. 409–426. [Google Scholar]
- Minder, M.; Pittaluga, M.; Roberts, G.L.; Lucamarini, M.; Dynes, J.F.; Yuan, Z.L.; Shields, A.L. Experimental quantum key distribution beyond the repeaterless secret key capacity. Nat. Photonics 2019, 13, 334–338. [Google Scholar] [CrossRef]
- Wang, X.B. Three-intensity decoy-state method for device-independent quantum key distribution with basis-dependent errors. Phys. Rev. A 2013, 87, 012320. [Google Scholar] [CrossRef] [Green Version]
| f | ||||
|---|---|---|---|---|
| 0.16 | 1.15 |
| Protocols | |||||
|---|---|---|---|---|---|
| R at 100 km | This work | ||||
| (bits/pulse) | TF-QDS with DPRS | ||||
| R at 200 km | This work | ||||
| (bits/pulse) | TF-QDS with DPRS | - | |||
| Distance | This work | 222.2 | 267.7 | 288.8 | 291.8 |
| (km) | TF-QDS with DPRS | 164.8 | 262.2 | 281.7 | 283.9 |
| Maximum | This work | 231.3 | 279.4 | 303.8 | 313.3 |
| distance (km) | TF-QDS with DPRS | 171.9 | 279.3 | 303.7 | 313.1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, J.; He, C.; Xie, J.; Liu, X.; Zhang, M. Twin-Field Quantum Digital Signature with Fully Discrete Phase Randomization. Entropy 2022, 24, 839. https://doi.org/10.3390/e24060839
Wu J, He C, Xie J, Liu X, Zhang M. Twin-Field Quantum Digital Signature with Fully Discrete Phase Randomization. Entropy. 2022; 24(6):839. https://doi.org/10.3390/e24060839
Chicago/Turabian StyleWu, Jiayao, Chen He, Jiahui Xie, Xiaopeng Liu, and Minghui Zhang. 2022. "Twin-Field Quantum Digital Signature with Fully Discrete Phase Randomization" Entropy 24, no. 6: 839. https://doi.org/10.3390/e24060839
APA StyleWu, J., He, C., Xie, J., Liu, X., & Zhang, M. (2022). Twin-Field Quantum Digital Signature with Fully Discrete Phase Randomization. Entropy, 24(6), 839. https://doi.org/10.3390/e24060839






