Medical Image Authentication Method Based on the Wavelet Packet and Energy Entropy
Abstract
:1. Introduction
- (1)
- In the time–frequency data distribution, the energy of the detailed information is described. Then, the complexity weight of the energy is measured. Based on this, the local energy entropy is constructed.
- (2)
- From the perspective of energy, the local details of the data are mined and then the local energy entropy is normalized. The processed entropy is used as the feature of the authentication information.
- (3)
- The proposed authentication method combines the advantages of multiresolution analysis and the stability of local energy entropy. No noise is added in the authentication process. The integrity goal of the authentication is achieved.
2. Basic Theory
2.1. Basic Theory of Wavelet Packet Transform
2.2. Wavelet Packet Decomposition of Images
2.3. Theory of Energy Entropy
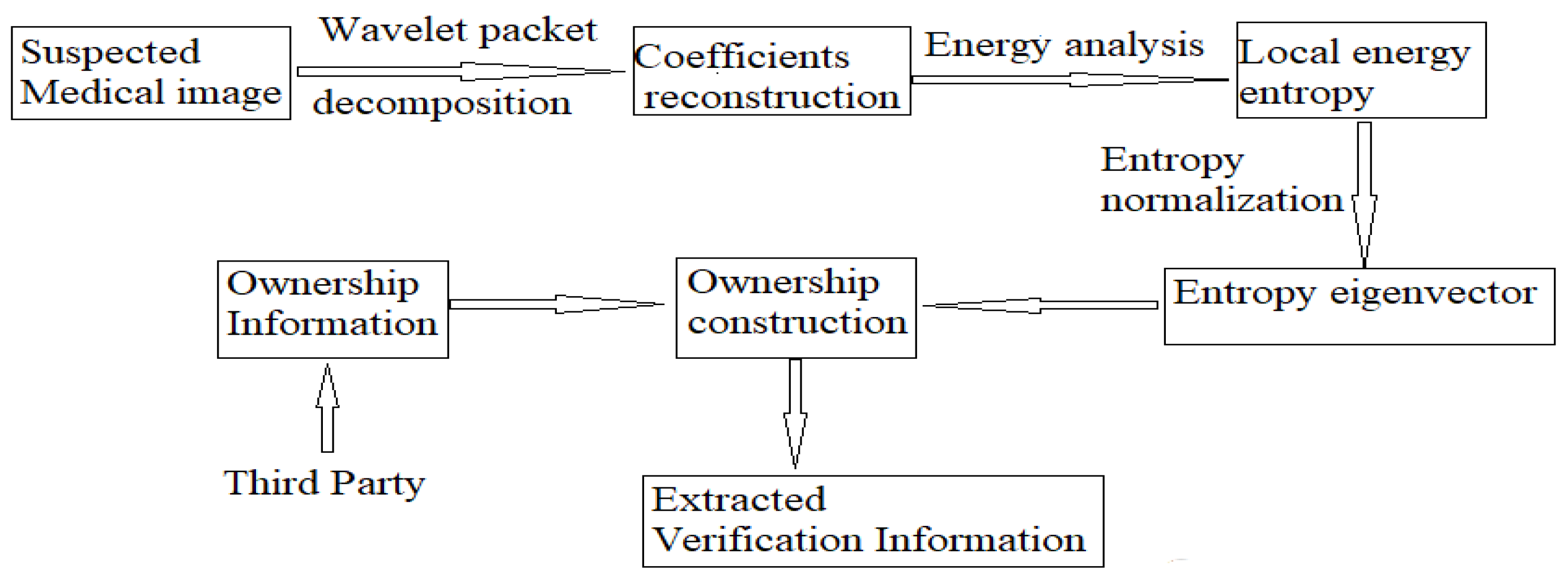
3. Authentication Scheme
3.1. Ownership Construction Phase
- Step 1: Extraction of robust features.
- Step 2: Construct feature vector.
- Step 3: Form authentication information and store authentication results.
3.2. Ownership Verification Phase
- Step1: Extraction of robust features.
- Step 2: Construct feature vector.
4. Analysis of Experimental Results
4.1. Correlation Test between Different Features
4.2. Analysis of Experimental Results
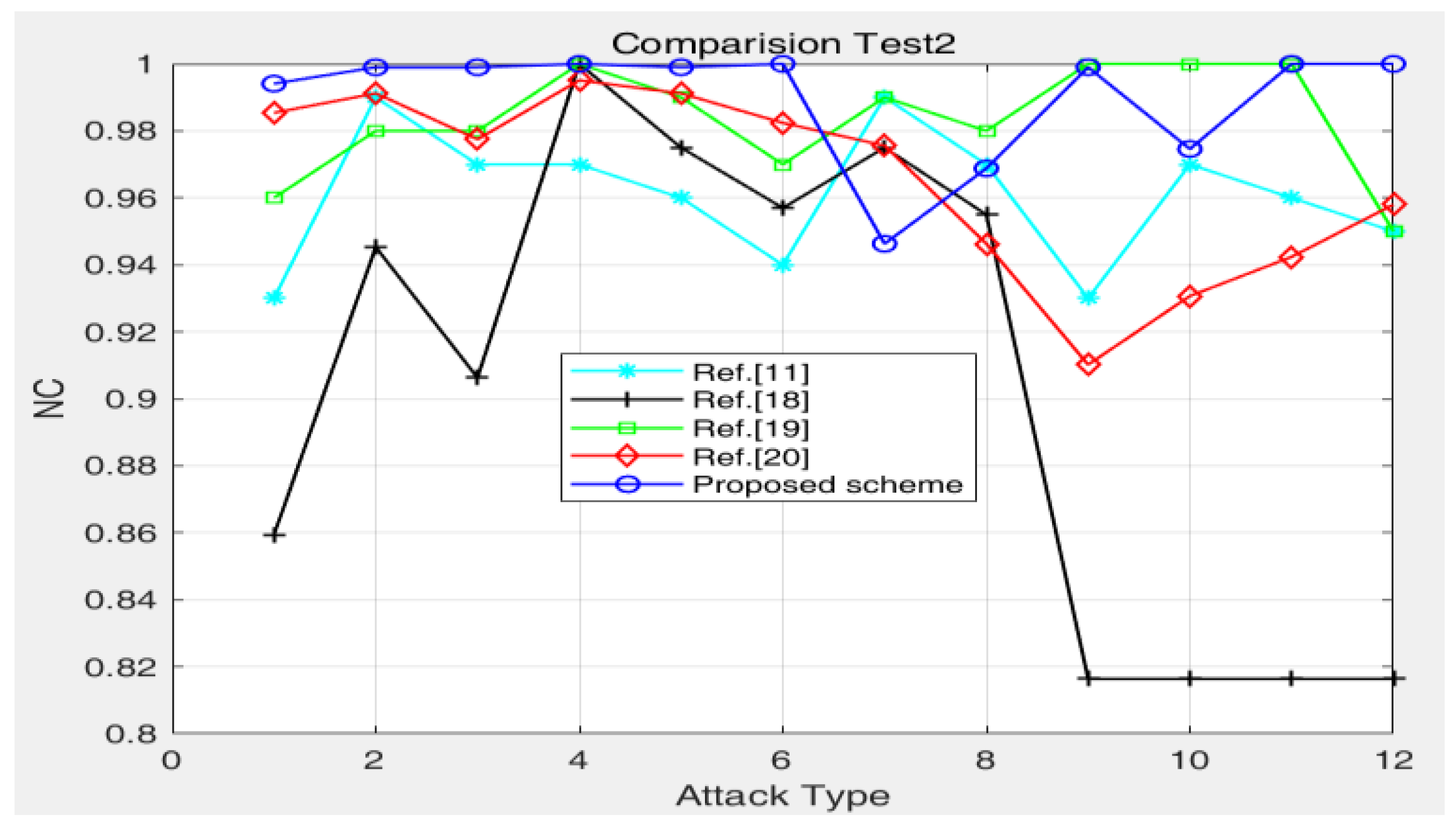
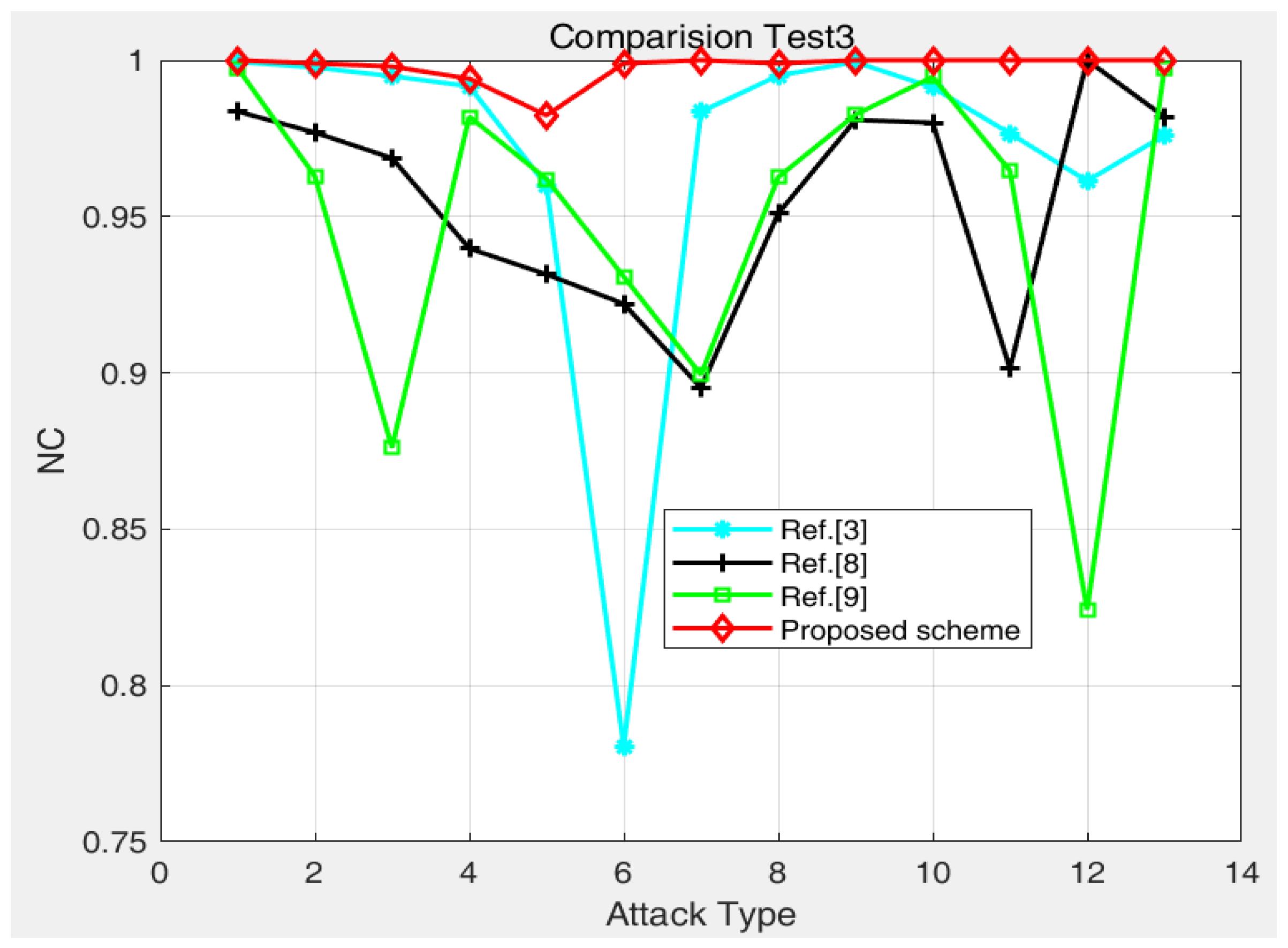
4.3. Algorithm Comparison Test
5. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Data Availability Statement
Conflicts of Interest
References
- Ashima, A.; Amitkumar, S. Watermarking techniques for medical data authentication: A survey. Multimed. Tools Appl. 2020, 13, 30165–30197. [Google Scholar]
- Singh, A.K.; Patna, N. Data Hiding: Current Trends, Innovation and Potential challenges. ACM Trans. Multimed. Comput. Commun. Appl. 2020, 16, 1–16. [Google Scholar] [CrossRef]
- Anand, A.; Singh, A.K. Joint Watermarking-Encryption-ECC for Patient Record Security in Wavelet Domain. IEEE Multimed. 2020, 3, 66–75. [Google Scholar] [CrossRef]
- Singh, A.K.; Thakur, A. Joint Encryption and Compression-Based Watermarking Technique for Security of Digital Documents. ACM Trans. Internet Technol. 2021, 1, 1–20. [Google Scholar] [CrossRef]
- Singh, A.K.; Chandan, K. Encryption-then-Compression based Copyright Protection Scheme for E-Governance. IEEE IT Prof. 2020, 3, 45–52. [Google Scholar] [CrossRef]
- Daihong, J.; Sai, Z.; Lei, D.; Yueming, D. Multi-scale generative adversarial network for image super-resolution. Soft Comput. 2022, 26, 3631–3641. [Google Scholar] [CrossRef]
- Solihah, G.; Shabir, A.; Parah, K. Reversible data hiding exploiting Huffman encoding with dual images for IoMT based healthcare. Comput. Commun. 2020, 163, 134–149. [Google Scholar]
- Anand, A.; Singh, A.K. An improved DWT-SVD domain watermarking for medical information security. Comput. Commun. 2020, 152, 72–80. [Google Scholar] [CrossRef]
- Thakur, S.; Singh, B.; Kumar, B. Improved DWT-SVD Based Medical Image Watermarking Through Hamming Code and Chaotic Encryption. Commun. Signal Process. 2020, 587, 897–905. [Google Scholar]
- Jinhua, L.; Shan, W.; Xinye, X. A Logarithmic Quantization-Based Image Watermarking Using Information Entropy in the Wavelet Domain. Entropy 2018, 945. [Google Scholar]
- Hu, Y.; Zhu, S. Zero-watermark algorithm based on PCA and chaotic scrambling. J. Zhejiang Univ. Eng. Sci. 2008, 4, 593–597. [Google Scholar]
- Hsieh, S.; Huang, B. A copyright protection scheme for gray-level images based on image secret sharing and wavelet transformation. In Proceedings of the International Computer Symposium, Las Vegas, NV, USA, 16–18 June 2004; pp. 661–666. [Google Scholar]
- Borra, S.; Thanki, R. A FRT-SVD based blind medical watermarking technique for telemedicine applications. Int. J. Digit. Crime Forensics 2019, 11, 13–33. [Google Scholar] [CrossRef]
- Farhan, M.; Sanjeev, K. Generating Visually coherent encrypted images with reversible data hiding in wavelet domain by fusing chaos and pairing function. Comput. Commun. 2020, 162, 12–30. [Google Scholar]
- Qin, C.; He, Z.; Yao, H. Visible watermark removal scheme based on reversible data hiding and image inpainting. Signal Process. Image Commun. 2018, 60, 160–172. [Google Scholar] [CrossRef]
- Pirbhulal, S.; Samuel, O.W.; Wu, W. A joint resource-aware and medical data security framework for wearable healthcare systems. Future Gener. Comput. Syst. 2019, 95, 382–391. [Google Scholar] [CrossRef]
- Hsu, C.; Hou, Y. Copyright protection scheme for digital images using visual cryptography and sampling methods. Opt. Eng. 2005, 44, 077003. [Google Scholar]
- Gao, S. An adaptive image zero-watermarking algorithm in DT-CWT domain. J. Sichuan Univ. Nat. Sci. Ed. 2008, 6, 493–497. [Google Scholar]
- Xiang, H.; Cao, H. A Zero-watermarking Algorithm Based on Chaotic Modulation. J. Image Graph. 2006, 5, 720–724. [Google Scholar]
- Tiankai, S.; Xingyuan, W.; Rong, B. A Hybrid Contourlet-Singular Value Decomposition Authentication Scheme Based on Chaos and Visual Cryptography for Medical Images. J. Comput. Theor. Nanosci. 2016, 13, 8885–8895. [Google Scholar]
- Andreas, P.; Andreas, U. Selective encryption of wavelet-packet encoded image data:efficiency and security. Multimed. Syst. 2003, 9, 279–287. [Google Scholar]
- Arcangelo, C.; Alfredo, D.S.; Vincenzo, L.; Francesco, P. On the Protection of fMRI Images in Multi-Domain Environments. In Proceedings of the IEEE 29th International Conference on Advanced Information Networking and Applicatins, Gwangju, Korea, 24–27 March 2015; Volume 224, pp. 476–481. [Google Scholar]
- Tiankai, S.; Xingyuan, W.; Da, L.; Daihong, J. Medical image security authentication method based on wavelet reconstruction and fractal dimension. Int. J. Distrib. Sens. Netw. 2021, 4, 1–9. [Google Scholar]














| Abdomen (b) Breast (c) Chest (d) Head | Breast | Adrenal | Head | Heart | Lung | |
|---|---|---|---|---|---|---|
| Abdomen | 1 | 0.2793 | 0.7334 | 0.7490 | 0.6777 | 0.7188 |
| Breast | 0.2793 | 1 | 0.1533 | 0.2412 | 0.2891 | 0.0156 |
| Adrenal | 0.7334 | 0.1533 | 1 | 0.7578 | 0.7471 | 0.8467 |
| Head | 0.7490 | 0.2412 | 0.7578 | 1 | 0.6748 | 0.7432 |
| Heart | 0.6777 | 0.2891 | 0.7471 | 0.6748 | 1 | 0.7246 |
| Lung | 0.7188 | 0.0156 | 0.8467 | 0.7432 | 0.7246 | 1 |
| Attack | Breast | Averaged Results of Six Test Images |
|---|---|---|
| JPEG (10) | 1 | 0.9952 |
| Salt-and-pepper noise (0.001) | 0.9980 | 0.9749 |
| Gaussian noise (0.005) | 0.9824 | 0.9819 |
| Rotation (10 degrees) | 1.0000 | 0.9968 |
| Scale scaling (200%) | 1 | 0.9924 |
| Sharpening | 0.9990 | 0.9938 |
| Multiplicative noise (0.01) | 1 | 0.9918 |
| Clipping (20%) | 0.9688 | 0.9637 |
| Median filtering 5 × 5 | 0.9990 | 0.9970 |
| Contrast enhancement | 0.9766 | 0.9852 |
| Brightness enhancement | 1 | 0.9853 |
| Attacks | Hsieh and Huang’s Scheme [12] | Hsu and Hou’s Scheme [17] | Tiankai’s Scheme [20] | Proposed Scheme |
|---|---|---|---|---|
| Sharpening | 0.752 | 0.819 | 0.9561 | 0.9990 |
| Median filtering | 0.843 | 0.938 | 0.9775 | 0.9990 |
| Resizing | 0.733 | 0.887 | 0.9521 | 1 |
| Noise addition | 0.723 | 0.761 | 0.9854 | 0.9941 |
| JPEG | 0.845 | 0.956 | 0.9912 | 0.9990 |
| Attack | Ref. [11] | Ref. [18] | Ref. [19] | Ref. [20] | Proposed Scheme |
|---|---|---|---|---|---|
| Gaussian noise | 0.9300 | 0.8594 | 0.9600 | 0.9854 | 0.9941 |
| Median filtering 5 × 5 | 0.9900 | 0.9453 | 0.9800 | 0.9912 | 0.9990 |
| Median filtering 7 × 7 | 0.9700 | 0.9063 | 0.9800 | 0.9775 | 0.9990 |
| JPEG (70) | 0.9700 | 1.0000 | 1.0000 | 0.9951 | 1 |
| JPEG (50) | 0.9600 | - | 0.9900 | 0.9912 | 0.9990 |
| JPEG (20) | 0.9400 | 0.9570 | 0.9700 | 0.9824 | 1 |
| Cropping (10%) | 0.9900 | - | - | 0.9756 | 0.9463 |
| Cropping (20%) | 0.9700 | - | - | 0.9463 | 0.9688 |
| Rotation attack (1 degree) | 0.9300 | 0.8164 | - | 0.9102 | 0.9990 |
| Rotation attack (2.5 degrees) | 0.9700 | - | - | 0.9307 | 0.9746 |
| Rotation attack (5 degrees) | 0.9600 | - | 1.0000 | 0.9424 | 1 |
| Rotation attack (10 degrees) | 0.9500 | - | 0.9500 | 0.9580 | 1 |
| Visibility | No | No | No | Yes | Yes |
| Attack | Noise Density | Ref. [3] | Ref. [8] | Ref. [9] | Proposed Scheme |
|---|---|---|---|---|---|
| Salt-and-pepper noise | 0.0001 | 0.9995 | 0.9836 | 0.9975 | 1 |
| Salt-and-pepper noise | 0.0005 | 0.9977 | 0.9769 | 0.9630 | 0.9990 |
| Salt-and-pepper noise | 0.001 | 0.9949 | 0.9687 | 0.8761 | 0.9980 |
| Gaussian noise | 0.001 | 0.9917 | 0.9398 | - | 0.9941 |
| Gaussian noise | 0.005 | 0.9599 | 0.9315 | - | 0.9824 |
| Rotation | 1 degree | 0.7806 | 0.9221 | 0.9308 | 0.9990 |
| JPEG compression | QF = 10 | 0.9835 | 0.8952 | 0.8994 | 1 |
| JPEG compression | QF = 50 | 0.9951 | 0.9510 | 0.9626 | 0.9990 |
| JPEG compression | QF = 90 | 0.9994 | 0.9809 | - | 1 |
| Speckle noise | 0.001 | 0.9913 | 0.9800 | 0.9947 | 1 |
| Speckle noise | 0.005 | 0.9766 | 0.9014 | - | 1 |
| Image scaling | 2 | 0.9614 | - | 0.8242 | 1 |
| Median filter | [11] | 0.9760 | 0.9819 | 0.9973 | 1 |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Sun, T.; Wang, X.; Zhang, K.; Jiang, D.; Lin, D.; Jv, X.; Ding, B.; Zhu, W. Medical Image Authentication Method Based on the Wavelet Packet and Energy Entropy. Entropy 2022, 24, 798. https://doi.org/10.3390/e24060798
Sun T, Wang X, Zhang K, Jiang D, Lin D, Jv X, Ding B, Zhu W. Medical Image Authentication Method Based on the Wavelet Packet and Energy Entropy. Entropy. 2022; 24(6):798. https://doi.org/10.3390/e24060798
Chicago/Turabian StyleSun, Tiankai, Xingyuan Wang, Kejun Zhang, Daihong Jiang, Da Lin, Xunguang Jv, Bin Ding, and Weidong Zhu. 2022. "Medical Image Authentication Method Based on the Wavelet Packet and Energy Entropy" Entropy 24, no. 6: 798. https://doi.org/10.3390/e24060798
APA StyleSun, T., Wang, X., Zhang, K., Jiang, D., Lin, D., Jv, X., Ding, B., & Zhu, W. (2022). Medical Image Authentication Method Based on the Wavelet Packet and Energy Entropy. Entropy, 24(6), 798. https://doi.org/10.3390/e24060798





