Traceable Scheme of Public Key Encryption with Equality Test
Abstract
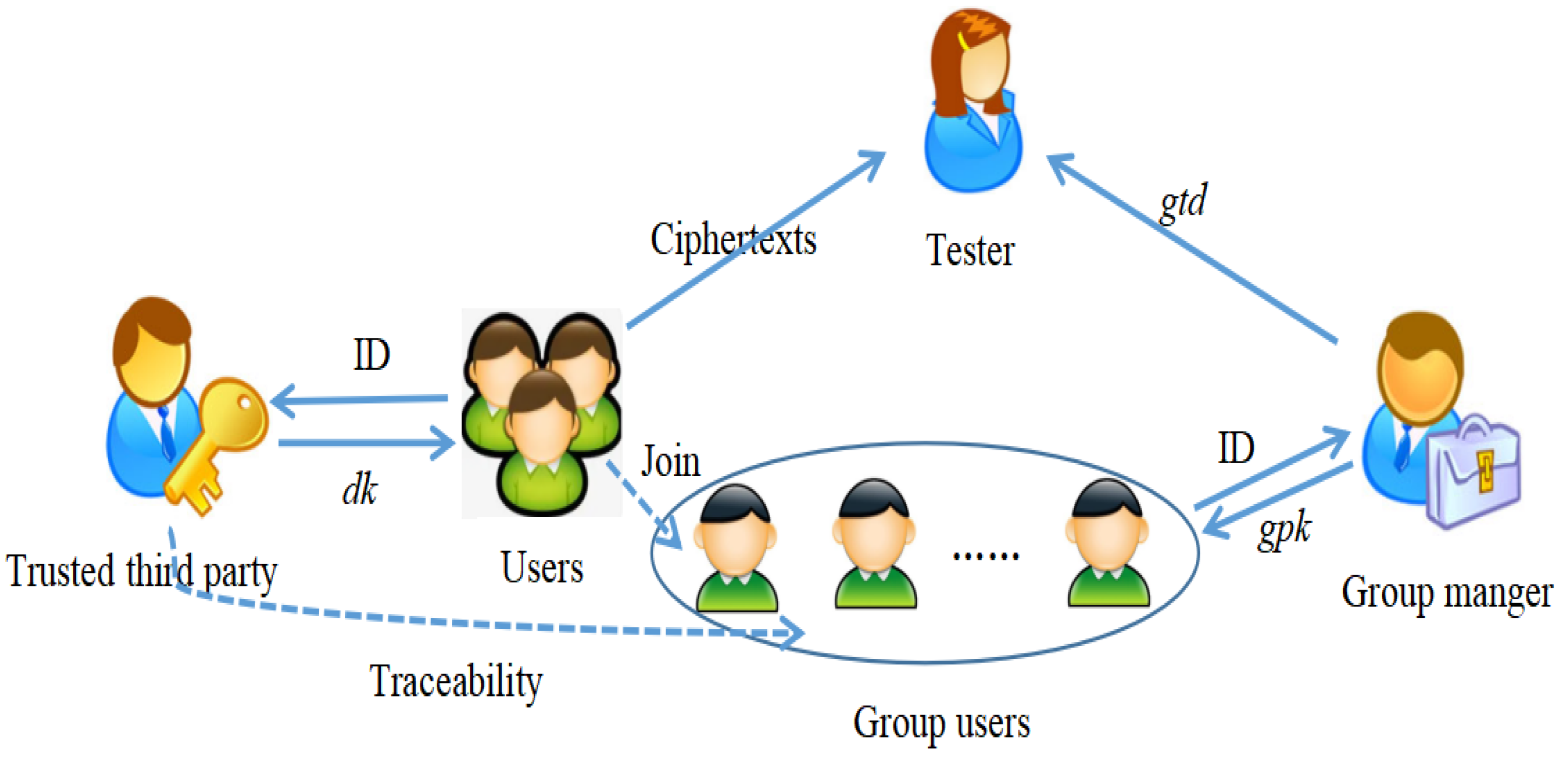
:1. Introduction
1.1. Related Work
1.2. Contributions
- We show that the GIBE algorithm is unable to compare ciphertexts, and has no equality test function without the secret key . To overcome these limitations, we combine the GIBE and PKEwET algorithms. Additionally, all of PKEwET algorithms are untraceable to the encrypted ciphertexts, the idea of traceability is introduced into the PKEwET algorithm, and we propose the traceable GIBE with an equality test scheme (T-GIBEwET).
- Two types of adversaries are described, and the security of the proposed scheme is proved in details from two types of adversaries. The presented scheme achieves a desirable security. With a trapdoor, the T-GIBEwET scheme can resist OW-CCA security. Without a trapdoor, the T-GIBEwET scheme can resist IND-CCA security.
- The performance of the T-GIBEwET scheme is discussed. Compared to existing equality test schemes, it is more efficient and more practical in many scenarios.
1.3. Outline of This Paper
2. Preliminaries
2.1. Decisional Bilinear Diffie–Hellman Assumption
- If , outputs .
- Otherwise, outputs .
2.2. Definition of PKEwET
- (1)
- KeyGen (): This procedure randomly selects , and outputs the public/secret key pair , where g is a generator of G.
- (2)
- Encrypt (): This procedure selects the numbers randomly. Then, it outputs the ciphertext as follows:Use r to compute:Output the ciphertext .
- (3)
- Decrypt(): Given and a ciphertext , the procedure runs as follows:If and , output M; otherwise, return ⊥.
- (4)
- Test(): Given the procedure runs as follows:Then, check whether holds. If yes, it means that and output 1. Otherwise, it means that and output 0.
2.3. Group ID-Based Encryption
- (1)
- Setup (l): With the security parameter l, this procedure exports system public parameters and .
- (2)
- KeyGengroup (): With system public parameters , this procedure exports the public key and secret key of group users.
- (3)
- Extract (): With a user’s identity , this procedure outputs the public key and secret key of users.
- (4)
- Join (): This algorithm is an interactive protocol between the group manager and the prospective user; it takes the group user’s as inputs, and outputs the group public key .
- (5)
- Encrypt (): This algorithm takes the public keys , of the group manager, of the user i, and the receiver’s public key and the message M as inputs, and outputs a ciphertext .
- (6)
- Decrypt (): This algorithm is run by the receiver; it takes the group public key , the receiver’s secret key , and the ciphertext as inputs, and outputs the message M or an error symbol ⊥.
2.4. System Models
- (1)
- Setup (l): With the security parameter l, this procedure exports the system public parameters and .
- (2)
- KeyGengroup (): With system public parameters , this procedure exports the public key and secret key of group users.
- (3)
- Extract (): With a user’s identity , this procedure outputs the public key and secret key of users.
- (4)
- Join (): This algorithm is an interactive protocol between the group manager and the prospective user; it takes the group user’s as inputs, and outputs the group public key .
- (5)
- Encrypt (): This algorithm takes the public keys and of the group manager, of the user i, the receiver’s public key , and the message M as inputs, and outputs a ciphertext .
- (6)
- Decrypt (): This algorithm is run by the receiver, it takes the group public key , the receiver’s secret key , and the ciphertext as inputs, and outputs the message M or an error symbol ⊥.
- (7)
- Trace (): This algorithm is run by the group manger; it takes group secret key , , , and a ciphertext as inputs, and outputs the user’s .
- (8)
- Auth (): This algorithm is run by the group manger, and outputs the group trapdoor .
- (9)
- Test (): This algorithm is run by the tester; it takes the two ciphertexts and as inputs, and outputs 1 or 0.
2.5. Security Models
- adversary: With a trapdoor, the adversary cannot recover the plaintext after receiving the challenge ciphertext.
- adversary: Without a trapdoor, the adversary cannot tell by which message is encrypted.
- (1)
- For any , Decrypt(Encrypt always holds.
- (2)
- For any ciphertexts and , if , it holds that
- (3)
- For any ciphertexts and , if , it holds that
2.6. Symbols
3. Our Constructions
- (1)
- Setup(l): With the security parameter l, this procedure exports the system public parameters . Choose hash functions: , , , ; here means the length of elements in . The master key is s.
- (2)
- KeyGengroup(): This procedure randomly selects , and outputs the group secret key .
- (3)
- Extract(): With a string , this procedure outputs the public key and secret key as follows:
- Outputs a public key .
- Outputs a secret key .
- (4)
- Join(): This procedure outputs the group public key for user .
- (5)
- Encrypt(): This procedure selects numbers randomly. Then, it outputs the ciphertext as follows:Use to compute:Output the ciphertext ,where:
- (6)
- Decrypt(): Given and a ciphertext , the procedure runs as follows:If and , output M; otherwise, return ⊥.
- (7)
- Trace(): Given , and a ciphertext , the procedure runs as follows:Then, check whether and holds. If yes, it means that is encrypted by .
- (8)
- The algorithm from the authorization function and test function:Suppose (resp. ) is a ciphertext of (resp. ).
- Auth(): Outputs the group trapdoor .
- Test():This procedure takes the inputs and and exports as follows:Use and to decide whether . If yes, output 1, which means . Otherwise, export 0, which means .
- (1)
- The first condition is easy to verify.
- (2)
- Considering the second condition, for any , , , , , , the following equalities hold.Given a group trapdoor and two ciphertexts and , we can compute as follows:Use to compute .Use to compute . If , then , which means
- (3)
- As for the third condition, we have the following fact:As in the above calculation, for any message , if , which means . Then, holds.
4. Security Analysis
- -query: maintains a list of 3-tuples in . When , ask for queries, and runs as follows:
- -
- If the query already in the list in the form of , outputs to .
- -
- Otherwise, generates randomly. Then, it outputs as follows:
- ∗
- If , chooses a random number and computes to .
- ∗
- Otherwise, computes to .
- -
- adds the tuple into the list.
- -query: maintains a list of 2-tuples in . chooses randomly, returns to , and adds the tuple to the list.
- -query: maintains a list of 2-tuples in . chooses randomly, returns to , and adds the tuple to the list.
- -query: maintains a list of 2-tuples in . chooses randomly, returns to , and adds the tuple to the list.
- -query: maintains a list of 2-tuples in . chooses randomly, returns to , and adds the tuple to the list.
- Extract Query(): When inputting , sends to . If , it means that . Then, sends ⊥ to .
- Encryption Query: runs an encryption algorithm and outputs .
- Decryption queries: With the to the decryption query, returns to as follows:
- -
- If , uses the private key and outputs the decryption query to .
- -
- Otherwise, outputs ⊥ to .
- Authorization Query: outputs the group trapdoor to .
- -query (), -query (), -query (), -query (), and -query () are the same as in Game .
- Extract Query(): Same as in Game .
- Encryption Query: outputs to as follows: chooses randomly, and performs the -query(), -query() to obtain , , the -query() to obtain , the -query() to obtain , the -query() to obtain . and the -query() to obtain .adds to the list, adds to the list, adds () to the list, and adds () to the list.
- Decryption queries: With the to the decryption query, returns to as follows: performs the to obtain answer , and performs the -query() to obtain answer . Then, performsThen, it verifies and . If the verification fails, it returns ⊥. Otherwise, outputs M to .
- Authorization Query: Same as in Game .
- The -query(), -query(), -query(), and -query() are the same as in Game .
- The -query() is the same as in Game , except that asks .
- Extract Query(): Same as in Game .
- Encryption Query: Same as in Game .
- Decryption Queries: Same as in Game .
- Authorization Query: Same as in Game .
- -query(), -query(), -query(), and -query() are same as in Game .
- -query() is same as in Game , except that asks
- Extract Query(): Same as in Game .
- Encryption Query: Same as in Game , except that for the query , selects randomly and outputs a ciphertext as follows:performs the -query() and -query() to obtain and , respectively, the -query() to obtain , the -query() to obtain , the -query() to obtain , and the -query() to obtain .adds to the list, adds to the list, and adds () to the list.
- Decryption queries: Same as in Game .
- Authorization Query: Same as in Game .
- -query: maintains a list of 3-tuples in . When asks for queries, runs as follows:
- -
- If the query is already in the list in the form of , outputs to .
- -
- Otherwise, generates randomly. Then, it outputs as follows:
- ∗
- If , chooses a random number and computes to .
- ∗
- Otherwise, computes to .
- -
- adds the tuple into the list.
- -query: maintains a list of 2-tuples in . chooses randomly, puts out to and adds the tuple to the list.
- -query: maintains a list of 2-tuples in . chooses randomly, puts out to and adds the tuple to the list.
- -query: maintains a list of 2-tuples in . chooses randomly, puts out to and adds the tuple to the list.
- -query: maintains a list of 2-tuples in . chooses randomly, returns to and adds the tuple to the list.
- Extract Query(): On input of the , sends to . If , which means , then sends ⊥ to .
- Encryption Query: runs the encryption algorithm and outputs .
- Decryption queries: With the in the decryption query, returns to as follows:
- -
- If , uses the private key and outputs the decryption query to .
- -
- Otherwise, outputs ⊥ to .
- Authorization Query: It is not allowed.
- does not appear in the decryption queries.
- In the authorization query, all of the group users cannot be authorized.
- -query(), -query(), -query(), -query(), and -query() are the same as in Game .
- Extract Query(): Same as in Game .
- Encryption Query: outputs to as follows:chooses randomly, and performs the -query() and -query() to obtain and , respectively, the -query() to obtain , the - query() to obtain , the -query() to obtain , and the -query() to obtain .adds to the list, adds to the list, adds () to the list, and adds () to the list.
- Decryption queries: With the to the decryption query, returns to as follows: performs the to obtain answer , and performs the -query() to obtain answer . Then, performsThen, and are verified. If the verification fails, it returns ⊥. Otherwise, outputs M to .
- Authorization Query: It is not allowed.
- does not appear in the decryption queries.
- In the authorization query, all of the group users cannot be authorized.
- -query(), -query(), -query(), and -query() are the same as in Game .
- -query() is the same as in Game , except that asks .
- Extract Query(): Same as in Game .
- Encryption Query: Same as in Game .
- Decryption Queries: Same as in Game .
- Authorization Query: Same as in Game .
- -query(), -query(), -query(), and -query() are the same as in Game .
- -query() is the same as in Game , except that asks for .
- Extract Query(): Same as in Game .
- Encryption Query: Same as in Game , except that for the query , selects randomly and outputs a ciphertext as follows:performs the -query() and -query() to obtain and , respectively, the -query() to obtain , the -query() to obtain , the -query() to obtain , and the -query() to obtain .adds to the list, adds to the list, adds () to the list, and adds () to the list.
- Decryption Queries: Same as in Game .
5. Performance Comparison
6. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Conflicts of Interest
Abbreviations
| IoT | Internet of Things |
| SE | Searchable Encryption |
| IBEwET | ID-Based Encryption with Equality Test |
| GIBE | Group ID-Based Encryption |
| T-GIBEwET | Traceable GIBE with Equality Test Scheme |
References
- Boneh, D.; Crescenzo, G.D.; Ostrovsky, R.; Persiano, G. Public key encryption with keyword search. In Proceedings of the International Conference on the Theory and Applications of Cryptographic Techniques, Interlaken, Switzerland, 13–17 April 2004; pp. 506–522. [Google Scholar]
- Curtmola, R.; Garay, J.A.; Kamara, S.; Ostrovsky, R. Searchable symmetric encryption: Improved definitions and efficient constructions. J. Comput. Secur. 2011, 19, 895–934. [Google Scholar] [CrossRef] [Green Version]
- Wang, C.; Cao, N.; Li, J.; Ren, K.; Lou, W. Secure ranked keyword search over encrypted cloud data. In Proceedings of the 2010 IEEE 30th International Conference on Distributed Computing Systems, Genova, Italy, 21–25 June 2010. [Google Scholar]
- Benaloh, J.; Chase, M.; Horvitz, E. Patient controlled encryption: Ensuring privacy of electronic medical records. In Proceedings of the 2009 ACM Workshop on Cloud Computing Security, Chicago, CA, USA, 9–13 November 2009; pp. 103–114. [Google Scholar]
- Ma, M.; He, D.; Kumar, N. Certificateless Searchable Public Key Encryption Scheme for Industrial Internet of Things. IEEE Trans. Ind. Inform. 2018, 14, 759–767. [Google Scholar] [CrossRef]
- Wang, Y.; Sun, S.F.; Wang, J. Achieving Searchable Encryption Scheme with Search Pattern Hidden. IEEE Trans. Serv. Comput. 2020. [Google Scholar] [CrossRef]
- Yang, G.; Tan, C.H.; Huang, Q. Probabilistic public key encryption with equality test. In Proceedings of the Cryptographers Track at the RSA Conference, San Francisco, CA, USA, 1–5 March 2010; Springer: Berlin, Germany, 2010; pp. 119–131. [Google Scholar]
- Tang, Q. Towards public key encryption scheme supporting equality test with fine-grained authorization. In Proceedings of the Australasian Conference on Information Security and Privacy, Melbourne, VIC, Australia, 11–13 July 2011; Springer: Berlin/Heidelberg, Germany, 2011; pp. 389–406. [Google Scholar]
- Tang, Q. Public key encryption schemes supporting equality test with authorisation of different granularity. Int. J. Appl. Cryptogr. 2012, 2, 304–321. [Google Scholar] [CrossRef]
- Tang, Q. Public key encryption supporting plaintext equality test and user-specified authorization. Secur. Commun. Netw. 2012, 5, 1351–1362. [Google Scholar] [CrossRef] [Green Version]
- Huang, K.; Tso, R.; Chen, Y. A New Public Key Encryption with Equality Test. In Proceedings of the International Conference on Network and System Security, New York, NY, USA, 3–5 November 2015; pp. 550–557. [Google Scholar]
- Huang, K.; Tso, R.; Chen, Y. PKE-AET: Public Key Encryption with Authorized Equality Test. Br. Comput. Soc. 2015, 2686–2697. [Google Scholar] [CrossRef]
- Huang, K.; Yu-Chi, C. Semantic Secure Public Key Encryption with Filtered Equality Test. In Proceedings of the 2015 12th International Joint Conference on e-Business and Telecommunications (ICETE), Alsace, France, 20–22 July 2015; pp. 327–334. [Google Scholar]
- Ma, S.; Zhang, M.; Huang, Q.; Yang, B. Public key encryption with delegated equality test in a multi-user setting. Comput. J. 2015, 58, 986–1002. [Google Scholar] [CrossRef] [Green Version]
- Huang, S.M.Q.; Zhang, M.; Yang, B. Efficient Public Key Encryption With Equality Test Supporting Flexible Authorization. IEEE Trans. Inf. Forensics Secur. 2015, 10, 458–470. [Google Scholar]
- Ma, S. Identity-based encryption with outsourced equality test in cloud computing. Inform. Sci. 2016, 328, 389–402. [Google Scholar] [CrossRef]
- Yang, M.; Wang, E. Identity-Based Encryption with Filtered Equality Test for Smart City Applications. Sensors 2019, 19, 3046. [Google Scholar]
- Wang, Y.; Pang, H.; Deng, R. Securing messaging services through efficient signcryption with designated equality test. Inf. Sci. 2019, 490, 146–165. [Google Scholar] [CrossRef]
- Duong, D.H.; Fukushima, K.; Kiyomoto, S.; Roy, P.S.; Susilo, W. Lattice-based public key encryption with equality test in standard model, revisited. arXiv 2020, arXiv:2005.03178. [Google Scholar]
- Lee, T.; San, L.; Seo, J.H.; Huaxiong, W. Semi-generic construction of public key encryption and identity-based encryption with equality test. Inf. Sci. 2016, 373, 419–440. [Google Scholar] [CrossRef]
- Lee, H.T.; Ling, S.; Seo, J.H.; Wang, H.; Youn, T.Y. Public Key Encryption with Equality Test in the Standard Model. Inf. Sci. 2020, 516, 89–108. [Google Scholar] [CrossRef]
- Huang, K.; Tso, R.; Chen, Y.C. Somewhat semantic secure public key encryption with filtered-equality-test in the standard model and its extension to searchable encryption. J. Comput. Syst. Sci. 2017, 89, 400–409. [Google Scholar] [CrossRef]
- Wang, Y.; Pang, H.; Tran, N.H. CCA Secure encryption supporting authorized equality test on ciphertexts in standard model and its applications. Inf. Sci. 2017, 414, 289–305. [Google Scholar] [CrossRef]
- Zhang, K.; Chen, J.; Lee, H. Efficient Public Key Encryption with Equality Test in The Standard Model. Theor. Comput. Sci. 2019, 755, 65–80. [Google Scholar] [CrossRef]
- Elhabob, R.; Zhao, Y.; Sella, I.; Xiong, H. Public Key Encryption with Equality Test for Heterogeneous Systems in Cloud Computing. KSII Trans. Internet Inf. Syst. 2019, 13, 4742–4770. [Google Scholar]
- Lin, X.J.; Qu, H.; Zhang, X. Public Key Encryption Supporting Equality Test and Flexible Authorization without Bilinear Pairings. Comput. Commun. 2021, 170, 190–199. [Google Scholar] [CrossRef]
- Zhu, H.; Wang, L.; Ahmad, H.; Niu, X. Pairing-free equality test over short ciphertexts. Int. J. Distrib. Sens. Netw. 2017, 13, 1550147717715605. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Choo, K. Efficient and secure identity-based encryption scheme with equality test in cloud computing. Future Gener. Comput. Syst. 2017, 73, 22–31. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Choo, K. Efficient Identity-Based Encryption Scheme with Equality Test in Smart City. IEEE Trans. Sustain. Comput. 2018, 3, 44–55. [Google Scholar] [CrossRef]
- Qu, H.; Zhen, Y.; Lin, X. Certificateless Public Key Encryption with Equality Test. Inf. Sci. 2018, 462, 76–92. [Google Scholar] [CrossRef]
- Elhabob, R.; Zhao, Y.; Hassan, A.; Xiong, H. PKE-ET-HS: Public Key Encryption with Equality Test for Heterogeneous Systems in IoT. Wirel. Pers. Commun. 2020, 113, 313–335. [Google Scholar] [CrossRef]
- Elhabob, R.; Zhao, Y.; Sella, I.; Xiong, H. An efficient certificateless public key cryptography with authorized equality test in IIoT. J. Ambient. Intell. Humaniz. Comput. 2020, 11, 1065–1083. [Google Scholar] [CrossRef]
- Wu, L.; Zhang, Y.; Choo, K.R.; He, D. Pairing-Free Identity-Based Encryption with Authorized Equality Test in Online Social Networks. Int. J. Found. Comput. Sci. 2019, 30, 647–664. [Google Scholar] [CrossRef]
- Lee, H.T.; Ling, S.; Seo, J.H.; Wang, H. Public Key Encryption with Equality Test from Generic Assumptions in the Random Oracle Model. Inf. Sci. 2019, 500, 15–33. [Google Scholar] [CrossRef]
- Ling, Y.; Ma, S.; Huang, Q. Group Public Key Encryption with Equality Test Against Offline Message Recovery Attack. Inf. Sci. 2020, 510, 16–32. [Google Scholar] [CrossRef]
- Zhu, H.; Wang, L.; Ahmad, H. Key-policy attribute-based encryption with equality test in cloud computing. IEEE Access 2017, 5, 20428–20439. [Google Scholar] [CrossRef]
- Wang, Q.; Peng, L.; Hu, X. Ciphertext-Policy Attribute-Based Encryption With Delegated Equality Test in Cloud Computing. IEEE Access 2018, 6, 760–771. [Google Scholar] [CrossRef]
- Eltayieb, N.; Elhabob, R.; Hassan, A. Fine-grained attribute-based encryption scheme supporting equality test. In Proceedings of the International Conference on Algorithms and Architectures for Parallel Processing, Guangzhou, China, 15–17 November 2018; Springer: Berlin, Germany, 2018; pp. 220–233. [Google Scholar]
- Sun, J.; Bao, Y.; Nie, X. Attribute-hiding predicate encryption with equality test in cloud computing. IEEE Access 2018, 6, 31621–31629. [Google Scholar] [CrossRef]
- Cui, Y.; Huang, Q.H.Q.J. Ciphertext-policy attribute-based encrypted data equality test and classification. Comput. J. 2019, 62, 1166–1177. [Google Scholar] [CrossRef]
- Lin, X.J.; Wang, Q.; Sun, L. Identity-based encryption with equality test and datestamp-based authorization mechanism. Theor. Comput. Sci. 2021, 117–132. [Google Scholar] [CrossRef]
- Luo, X.; Ren, Y.; Liu, J. Identity-based group encryption. In Proceedings of the Australasian Conference on Information Security and Privacy, Melbourne, Australia, 4–6 July 2016; Springer: Berlin, Germany, 2016; pp. 87–102. [Google Scholar]


| Symbol | Description |
|---|---|
| l | A security parameter |
| G | A cyclic group |
| g | The generator of G |
| M | The plaintext |
| The ciphertext | |
| The challenge ciphertext | |
| The message space | |
| Z | Set of integers |
| H | A hash function |
| s | The master key (keep it as a secret) |
| A user’s identity | |
| The group secret key (kept as a secret by group manager) | |
| The group public key (share to all users in the group) | |
| A user’s secret key (keep it as a secret) | |
| The adversary | |
| The simulator |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhu, H.; Xue, Q.; Li, T.; Xie, D. Traceable Scheme of Public Key Encryption with Equality Test. Entropy 2022, 24, 309. https://doi.org/10.3390/e24030309
Zhu H, Xue Q, Li T, Xie D. Traceable Scheme of Public Key Encryption with Equality Test. Entropy. 2022; 24(3):309. https://doi.org/10.3390/e24030309
Chicago/Turabian StyleZhu, Huijun, Qingji Xue, Tianfeng Li, and Dong Xie. 2022. "Traceable Scheme of Public Key Encryption with Equality Test" Entropy 24, no. 3: 309. https://doi.org/10.3390/e24030309
APA StyleZhu, H., Xue, Q., Li, T., & Xie, D. (2022). Traceable Scheme of Public Key Encryption with Equality Test. Entropy, 24(3), 309. https://doi.org/10.3390/e24030309





