Node Deployment Optimization for Wireless Sensor Networks Based on Virtual Force-Directed Particle Swarm Optimization Algorithm and Evidence Theory
Abstract
:1. Introduction
- A sensing probabilistic model is constructed. To aggregate the sensing probability in the circular area with radius R around the sensor node, the D-S evidence theory is applied. When there is a considerable evidence conflict, the typical D-S evidence theory aggregation rule does not conform to the real circumstances, and the result is not convincing. To address the concern, the priority factor is introduced to reassign the sensing probability.
- A virtual force-directed particle swarm optimization algorithm with sensing probabilities aggregated by D-S evidence (VF-PSO-DS for short) is proposed. The approach improves the virtual force-directed particle swarm optimization (VF-PSO) algorithm by considering sensing probability. The sensing probability is aggregated by D-S evidence, which guides the particle swarm evolution process and accelerates convergence.
2. Related Work
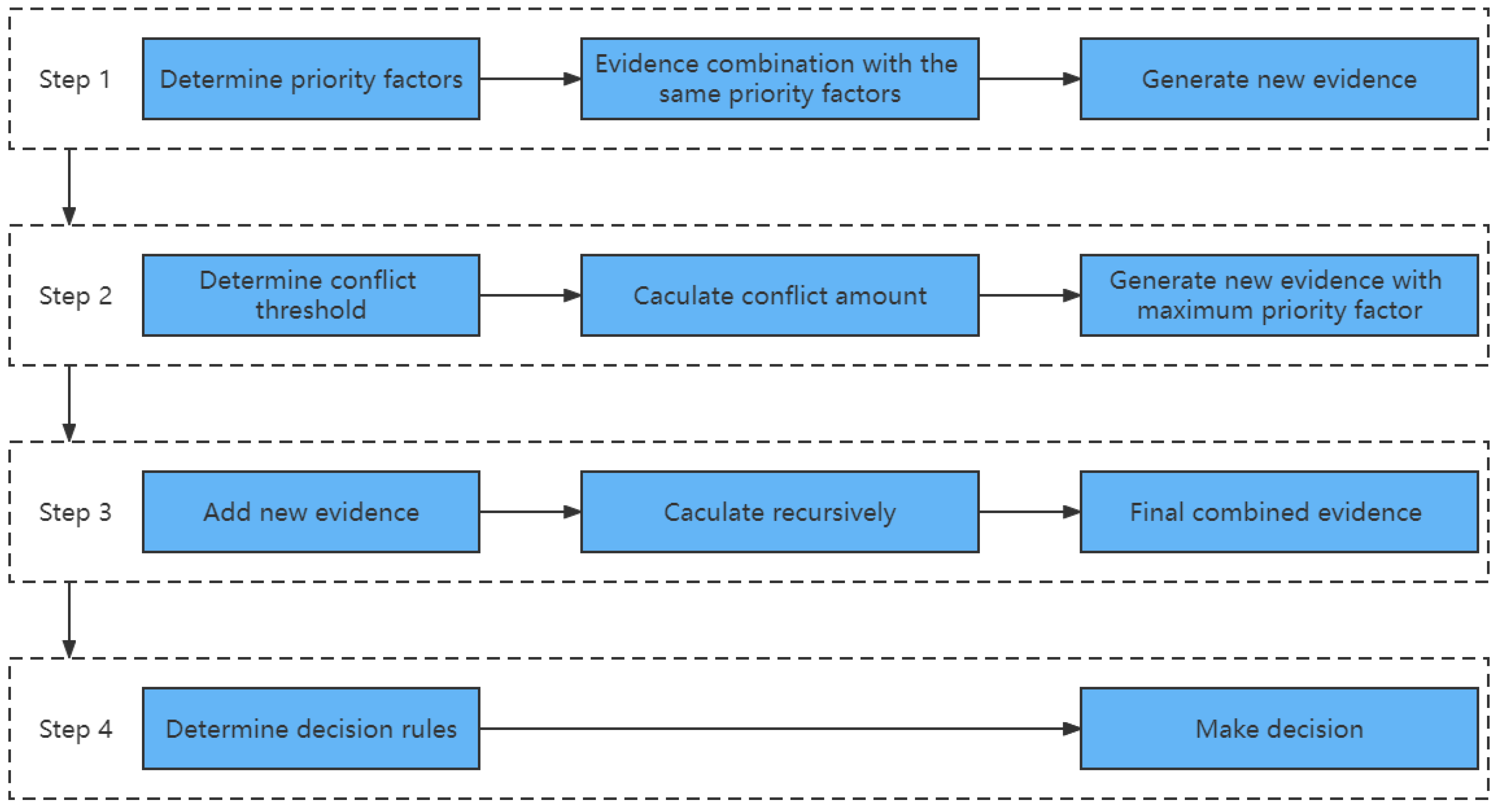
3. D-S Evidence Theory with Priority Factors
3.1. D-S Evidence Theory
3.2. The Problem with D-S Evidence Theory
3.3. Introduction of Priority Factors
3.3.1. Definition of Priority Factors
3.3.2. Determination of Priority Factors
3.4. D-S Evidence Aggregation Rules with Priority Factors
4. System Model
4.1. Sensing Probability Model
4.2. Area Coverage Model
5. Deployment Optimization Using Virtual Force-Directed Particle Swarm Algorithm
5.1. Virtual Force
5.2. Optimization Problem Formulation
5.3. The Process of Particle Swarm Optimization
5.4. Deployment Strategy
6. Simulation and Discussion
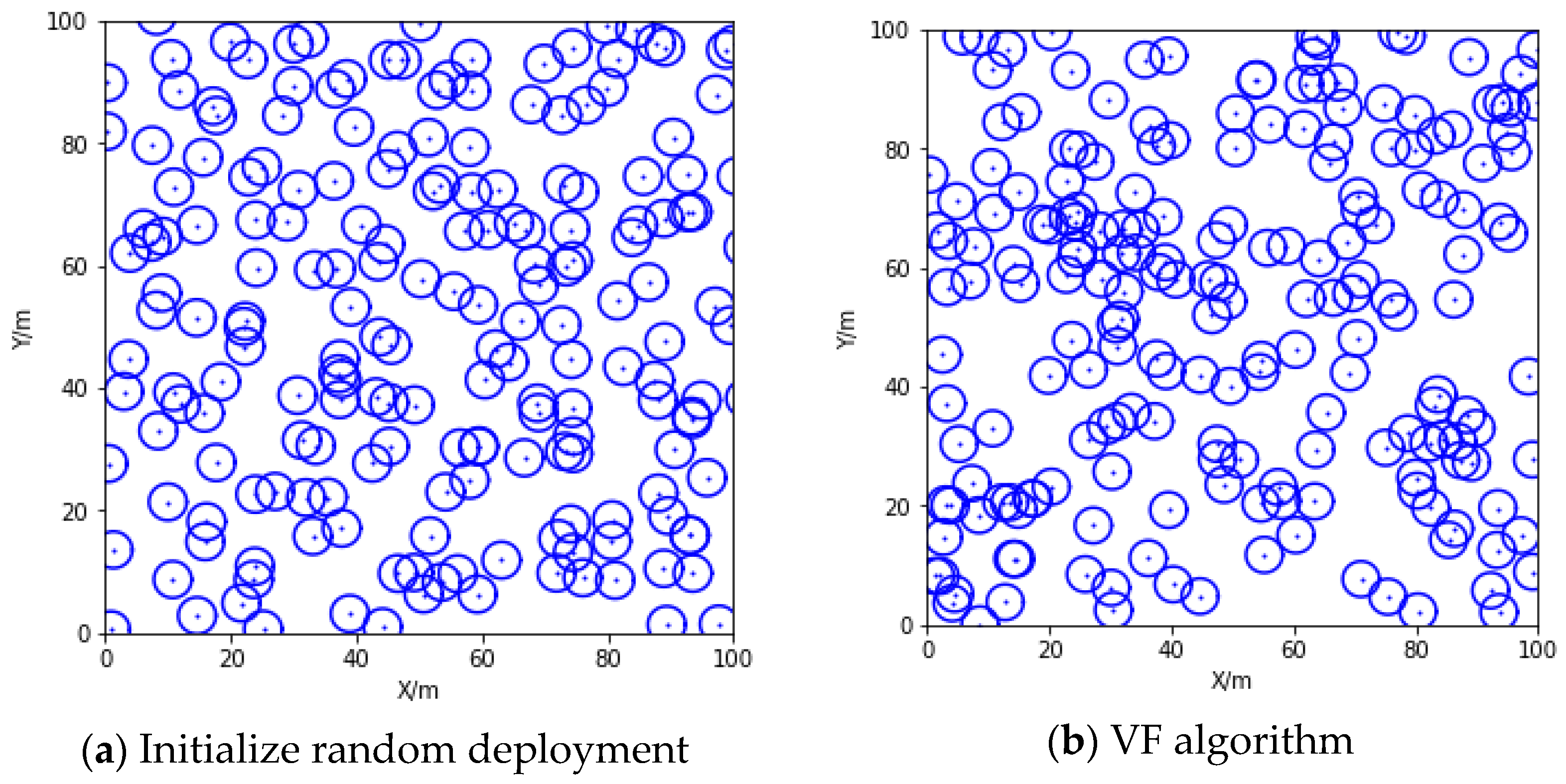
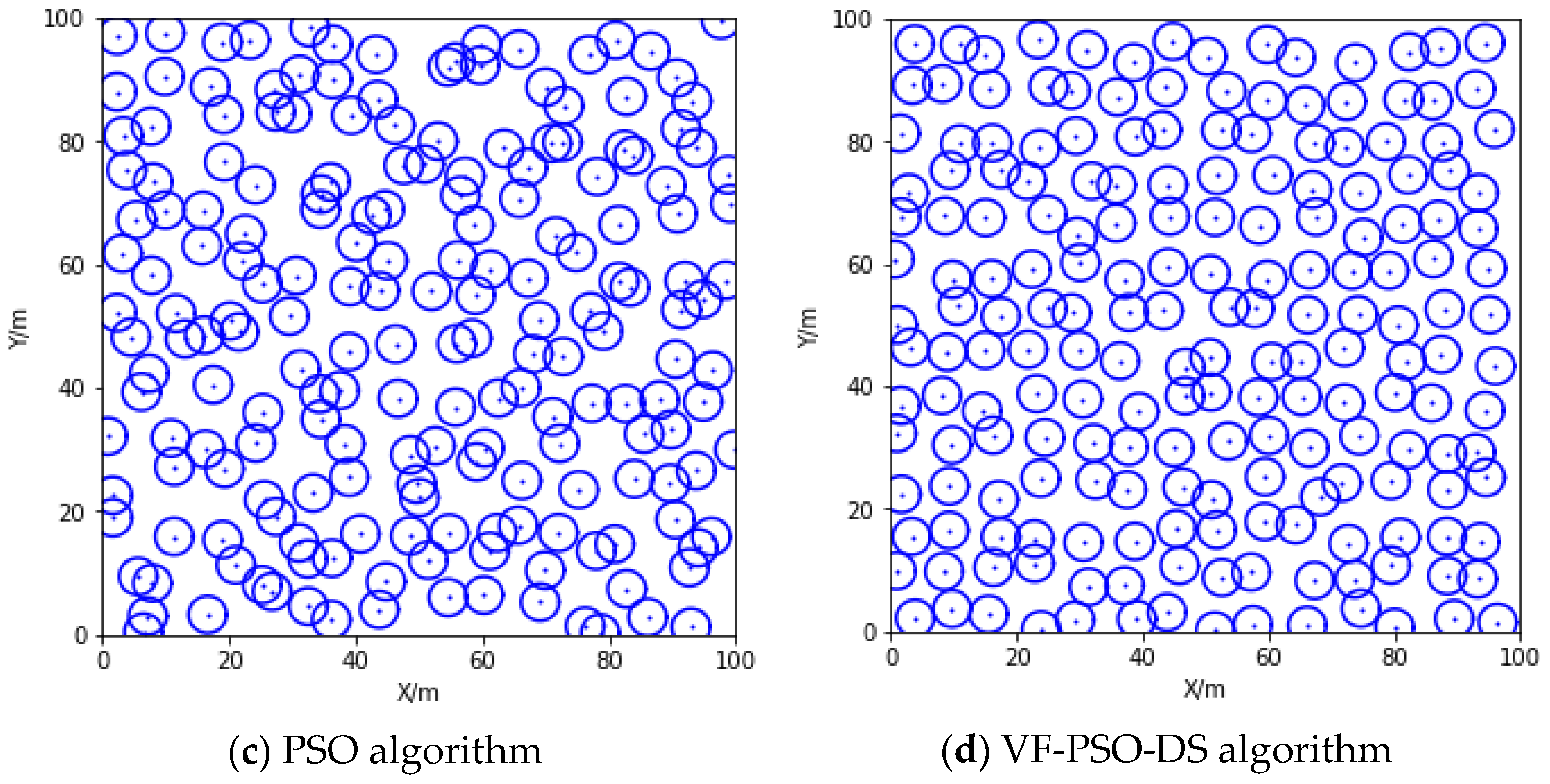
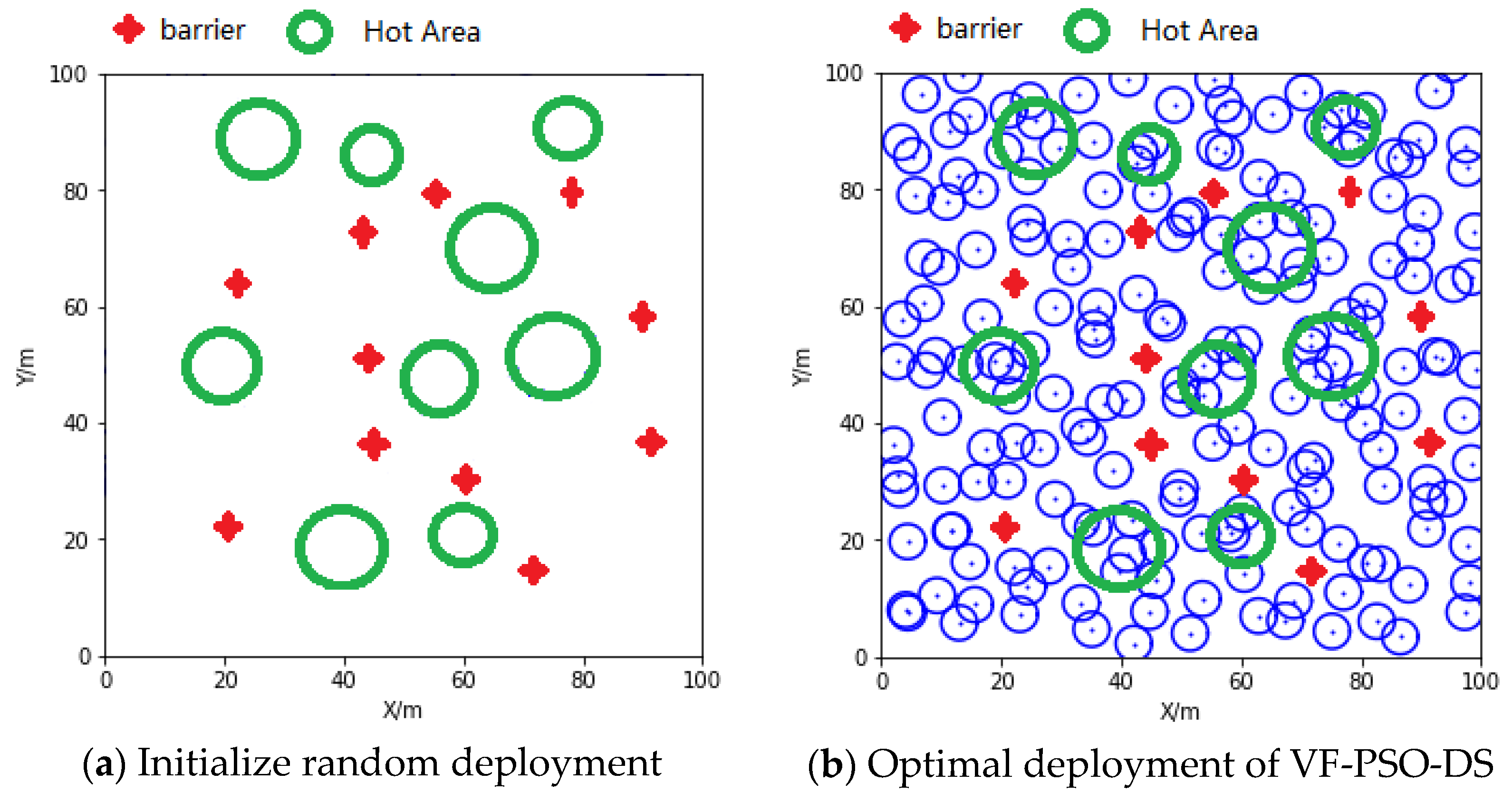
6.1. The Deployment Results
6.2. The Adaptability Tests
7. Conclusions
Author Contributions
Funding
Institutional Review Board Statement
Informed Consent Statement
Data Availability Statement
Acknowledgments
Conflicts of Interest
References
- Banimelhem, O.; Mowafi, M.; Aljoby, W. Genetic algorithm based node deployment in hybrid wireless sensor networks. Commun. Netw. 2013, 2013, 39564. [Google Scholar] [CrossRef] [Green Version]
- Wang, Y.; Hongmei, L.; Hengyang, H. Wireless sensor network deployment using an optimized artificial fish swarm algorithm. In Proceedings of the 2012 International Conference on Computer Science and Electronics Engineering, Hangzhou, China, 23–25 March 2012; Volume 2. [Google Scholar]
- Liu, X.; He, D. Ant colony optimization with greedy migration mechanism for node deployment in wireless sensor networks. J. Netw. Comput. Appl. 2014, 39, 310–318. [Google Scholar] [CrossRef]
- Li, Y.; Cao, J. WSN node optimal deployment algorithm based on adaptive binary particle swarm optimization. ASP Trans. Internet Things 2021, 1.1, 1–8. [Google Scholar] [CrossRef]
- Wang, X.; Wang, S.; Bi, D. Virtual Force-Directed Particle Swarm Optimization for Dynamic Deployment in Wireless Sensor Networks. In Advanced Intelligent Computing Theories and Applications; Springer: Berlin/Heidelberg, Germany, 2007. [Google Scholar]
- Runliang, D.; Nan, G. Optimizing Sensor Network Coverage and Regional Connectivity in Industrial IoT Systems. IEEE Syst. J. 2017, 11, 1351–1360. [Google Scholar]
- Hosseinzadeh, M.; Garone, E.; Schenato, L. A Distributed Method for Linear Programming Problems with Box Constraints and Time-Varying Inequalities. IEEE Control. Syst. Lett. 2019, 3, 404–409. [Google Scholar] [CrossRef]
- Kang, S.H. Energy Optimization in Cluster-Based Routing Protocols for Large-Area Wireless Sensor Networks. Symmetry 2019, 11, 37. [Google Scholar] [CrossRef] [Green Version]
- Liu, W.; Yang, S.; Sun, S.; Wei, S. A Node Deployment Optimization Method of WSN Based on Ant-Lion Optimization Algorithm. In Proceedings of the 2018 IEEE 4th International Symposium on Wireless Systems within the International Conferences on Intelligent Data Acquisition and Advanced Computing Systems (Idaacs-Sws), Lviv, Ukraine, 20–21 September 2018. [Google Scholar]
- Xiang, T.; Wang, H.; Shi, Y. Hybrid WSN Node Deployment Optimization Strategy Based on CS Algorithm. In Proceedings of the 2019 IEEE 3rd Information Technology, Networking, Electronic and Automation Control Conference (ITNEC), Chengdu, China, 15–17 March 2019. [Google Scholar]
- Xu, K.; Zhao, Z.; Luo, Y.; Hui, G.; Hu, L. An Energy-Efficient Clustering Routing Protocol Based on a High-QoS Node Deployment with an Inter-Cluster Routing Mechanism in WSNs. Sensors 2019, 19, 2752. [Google Scholar] [CrossRef] [Green Version]
- Redhu, S.; Rajesh, M.H. Cooperative Network Model for Joint Mobile Sink Scheduling and Dynamic Buffer Management Using Q-Learning. IEEE Trans. Netw. Serv. Manag. 2020, 17, 1853–1864. [Google Scholar] [CrossRef]
- García, L.; Parra, L.; Jimenez, J.M.; Parra, M.; Lloret, J.; Mauri, P.V.; Lorenz, P. Deployment Strategies of Soil Monitoring WSN for Precision Agriculture Irrigation Scheduling in Rural Areas. Sensors 2021, 21, 1693. [Google Scholar] [CrossRef]
- Tang, R.; Tao, Y.; Li, J.; Hu, Z.; Yuan, K.; Wu, Z.; Liu, S.; Wang, Y. A Novel 3D Node Deployment Inspired By Dusty Plasma Crystallization in UAV-Assisted Wireless Sensor Network Applications. Sensors 2021, 21, 7576. [Google Scholar] [CrossRef]
- Yu, X.; Huang, W.; Lan, J.; Qian, X. A Novel Virtual Force Approach for Node Deployment in Wireless Sensor Network. In Proceedings of the 2012 IEEE 8th International Conference on Distributed Computing In Sensor Systems, Washington, DC, USA, 16–18 May 2012. [Google Scholar]
- Xiaoping, R.; Zi-xing, C.; Zhao, L.; Wuyi, W. Performance Analysis of Virtual Force Models in Node Deployment Algorithm of WSN; Springer: Berlin/Heidelberg, Germany, 2012. [Google Scholar]
- Li, J.; Zhang, B.; Cui, L.; Chai, S. An Extended Virtual Force-Based Approach to Distributed Self-Deployment in Mobile Sensor Networks. Int. J. Distrib. Sens. Netw. 2012, 8, 417307. [Google Scholar] [CrossRef]
- Yu, X.; Liu, N.; Huang, W.; Qian, X.; Zhang, T. A Node Deployment Algorithm Based on Van Der Waals Force in Wireless Sensor Networks. Int. J. Distrib. Sens. Networks 2013, 9, 505710. [Google Scholar] [CrossRef]
- Ahmad, P.A.; Mahmuddin, M.; Omar, M.H. Node Placement Strategy in Wireless Sensor Network. Int. J. Mob. Comput. Multim. Commun. 2013, 5, 18–31. [Google Scholar] [CrossRef] [Green Version]
- Cheng-Chih, Y.; Wen, J.-H. A Hybrid Local Virtual Force Algorithm for Sensing Deployment in Wireless Sensor Network. In Proceedings of the 2013 Seventh International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing, Taichung, Taiwan, 3–5 July 2013. [Google Scholar]
- Deng, X.; Yu, Z.; Tang, R.; Qian, X.; Yuan, K.; Liu, S. An Optimized Node Deployment Solution Based on a Virtual Spring Force Algorithm for Wireless Sensor Network Applications. Sensors 2019, 19, 1817. [Google Scholar] [CrossRef] [Green Version]
- Yu, Z.; Tang, R.; Yuan, K.; Lin, H.; Qian, X.; Deng, X.; Liu, S. Investigation of Parameter Effects on Virtual-Spring-Force Algorithm for Wireless-Sensor-Network Applications. Sensors 2019, 19, 3082. [Google Scholar] [CrossRef] [Green Version]
- Li, Q.; Yi, Q.; Tang, R.; Qian, X.; Yuan, K.; Liu, S. A Hybrid Optimization from Two Virtual Physical Force Algorithms for Dynamic Node Deployment in WSN Applications. Sensors 2019, 19, 5108. [Google Scholar] [CrossRef] [Green Version]
- Fang, Y.; Cheng, B.; Kang, K.; Tan, H. A Self-adaptive Deployment Model of UAV Cluster for Emergency Communication Network. Int. J. Distrib. Sens. Netw. 2021, 17, 15501477211049327. [Google Scholar] [CrossRef]
- Zhao, S.; Wang, H.; Cheng, D. Power Distribution System Reliability Evaluation By D-S Evidence Inference and Bayesian Network Method. In Proceedings of the 2010 IEEE 11th International Conference on Probabilistic Methods Applied to Power Systems, Singapore, 14–17 June 2010. [Google Scholar]
- Feng, R.; Xu, X.; Zhou, X.; Wan, J. A Trust Evaluation Algorithm for Wireless Sensor Networks Based on Node Behaviors and D-S Evidence Theory. Sensors 2011, 11, 1345–1360. [Google Scholar] [CrossRef]
- Miao, C.; Huang, L.; Guo, W.; Xu, H. A Trustworthiness Evaluation Method for Wireless Sensor Nodes Based on D-S Evidence Theory. In International Conference on Wireless Algorithms, Systems, and Applications; Springer: Berlin/Heidelberg, Germany, 2013. [Google Scholar]
- Li, H.; Hua, X. Water Enviroment Monitoring System Based on Zigbee Technology. In Proceedings of the 2013 Third International Conference on Intelligent System Design and Engineering Applications, Hong Kong, China, 16–18 January 2013. [Google Scholar]
- Liu, P.T.; Gong, R.K.; Gong, Y.H.; Wang, C.H. A Gas Pipeline Leakage Diagnosis of Fusing BP Neural Network Basing on WSN and D-S Theory. Appl. Mech. Mater. 2014, 541, 1442–1446. [Google Scholar] [CrossRef]
- Zhao, Y.; Jia, R.; Jin, N.; He, Y. A Novel Method of Fleet Deployment Based on Route Risk Evaluation. Inf. Sci. 2016, 372, 731–744. [Google Scholar] [CrossRef]
- Song, X.; Gong, Y.; Jin, D.; Li, Q.; Jing, H. Coverage Hole Recovery Algorithm Based on Molecule Model in Heterogeneous WSNs. Int. J. Comput. Commun. Control 2017, 12, 562. [Google Scholar] [CrossRef]
- Sun, Z.; Zhang, Z.; Xiao, C.; Qu, G. D-S Evidence Theory Based Trust Ant Colony Routing in WSN. China Commun. 2018, 15, 27–41. [Google Scholar] [CrossRef]
- Song, X.; Gong, Y.; Jin, D.; Li, Q. Nodes Deployment Optimization Algorithm Based on Improved Evidence Theory of Underwater Wireless Sensor Networks. Photonic Netw. Commun. 2018, 37, 224–232. [Google Scholar] [CrossRef]
- He, L.; Wan, T.; Zhang, C.; Xia, F.; Wang, S.; Wang, Y. Network Situation Assessment of Host Node Based on Improved D-S Evidence Theory. J. Phys. Conf. Ser. 2021, 1738, 012091. [Google Scholar] [CrossRef]
- Du, Q.; Xu, L.; Zhao, H. DS evidence theory applied to fault diagnosis of generator based on embedded sensors. In Proceedings of the Third International Conference on Information Fusion, Paris, France, 10–13 July 2000; Volume 1. [Google Scholar]
- Li, Q.; Ma, D.; Zhang, J.; Fu, Z. Nodes Deployment Algorithm of Wireless Sensor Network. Comput. Meas. Control. 2013, 21, 1715–1717. [Google Scholar]
| Schemes | Constraints | ||||
|---|---|---|---|---|---|
| Energy | QoS | Network Lifetime | Network Connectivity | Sensing Coverage | |
| [6] | Y | Y | |||
| [7] | Y | Y | Y | ||
| [8] | Y | Y | |||
| [9] | Y | Y | |||
| [10] | Y | Y | |||
| [11] | Y | Y | |||
| [12] | Y | Y | |||
| [13] | Y | Y | |||
| [14] | Y | ||||
| VF | PSO | VF-PSO-DS | |
|---|---|---|---|
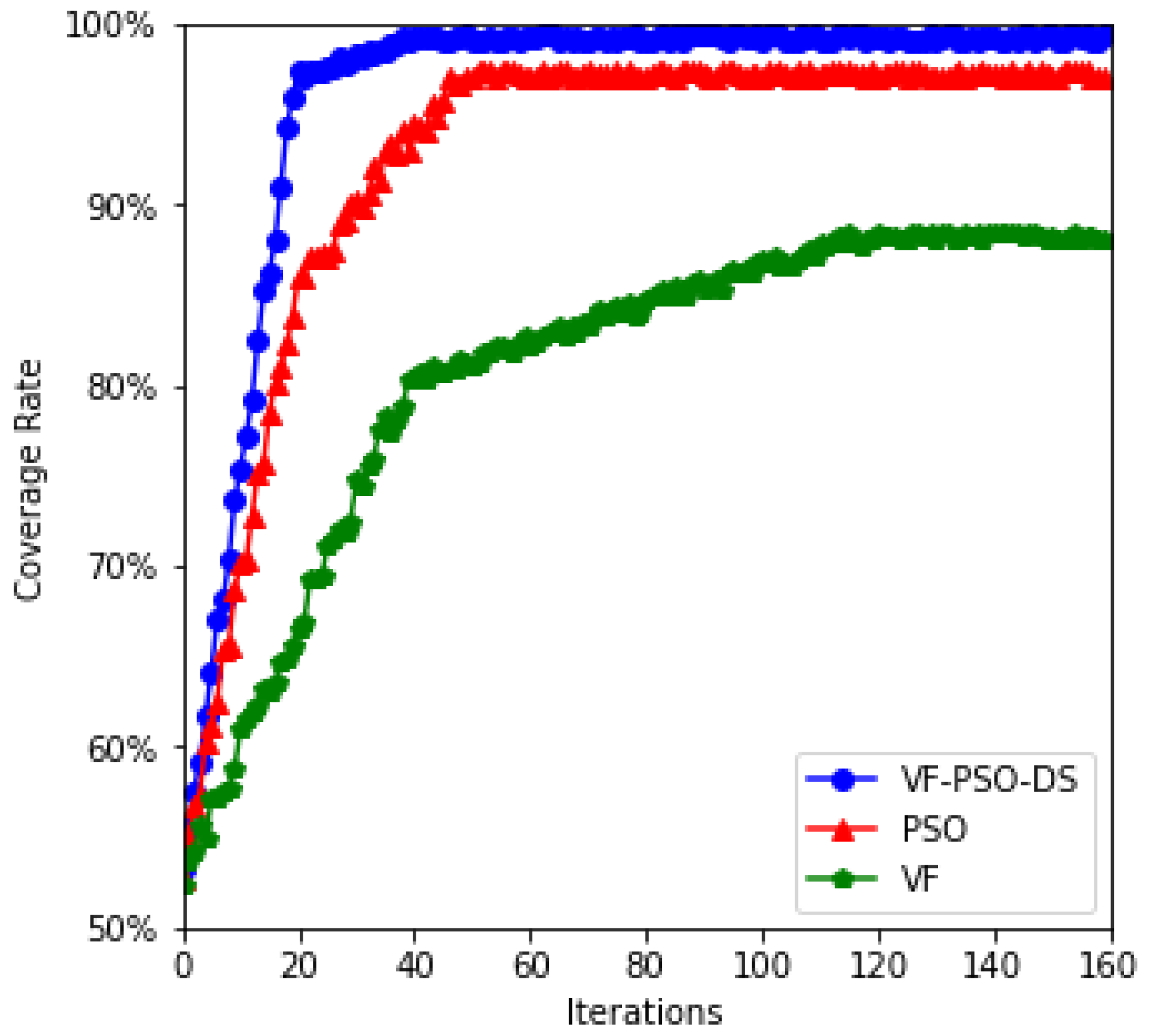
| Effective coverage (%) | 79.29 | 95.26 | 98.63 |
| Calculation time | 137.43 | 280.95 | 116.91 |
| Iterations | 161.48 | 140.33 | 40.59 |
| Number of Sensors | Initial Random Deployment | VF | VF-PSO-DS |
|---|---|---|---|
| 300 | 0.4123 | 0.5285 | 0.5524 |
| 350 | 0.4622 | 0.5551 | 0.5919 |
| 400 | 0.5275 | 0.6016 | 0.6693 |
| 450 | 0.5719 | 0.6582 | 0.6916 |
| 500 | 0.6236 | 0.6923 | 0.7372 |
| Number of Sensors | Moving Distance of VF | Moving Distance of VF-PSO-DS |
|---|---|---|
| 300 | 314.16 m | 256.19 m |
| 350 | 426.82 m | 358.27 m |
| 400 | 517.65 m | 399.23 m |
| 450 | 578.19 m | 451.96 m |
| 500 | 609.87 m | 512.25 m |
Publisher’s Note: MDPI stays neutral with regard to jurisdictional claims in published maps and institutional affiliations. |
© 2022 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (https://creativecommons.org/licenses/by/4.0/).
Share and Cite
Wu, L.; Qu, J.; Shi, H.; Li, P. Node Deployment Optimization for Wireless Sensor Networks Based on Virtual Force-Directed Particle Swarm Optimization Algorithm and Evidence Theory. Entropy 2022, 24, 1637. https://doi.org/10.3390/e24111637
Wu L, Qu J, Shi H, Li P. Node Deployment Optimization for Wireless Sensor Networks Based on Virtual Force-Directed Particle Swarm Optimization Algorithm and Evidence Theory. Entropy. 2022; 24(11):1637. https://doi.org/10.3390/e24111637
Chicago/Turabian StyleWu, Liangshun, Junsuo Qu, Haonan Shi, and Pengfei Li. 2022. "Node Deployment Optimization for Wireless Sensor Networks Based on Virtual Force-Directed Particle Swarm Optimization Algorithm and Evidence Theory" Entropy 24, no. 11: 1637. https://doi.org/10.3390/e24111637
APA StyleWu, L., Qu, J., Shi, H., & Li, P. (2022). Node Deployment Optimization for Wireless Sensor Networks Based on Virtual Force-Directed Particle Swarm Optimization Algorithm and Evidence Theory. Entropy, 24(11), 1637. https://doi.org/10.3390/e24111637








