1. Introduction
Ability to transmit information in an advanced way, impossible within the classical realm, is an important feature of quantum states, studied by quantum communication. However, during propagation through a quantum channel the states interact with the environment and part of the information becomes shared with it. Such information leakage is essential when security of quantum key distribution (QKD) [
1] is considered. Indeed, as follows from the Csiszár-Körner theorem [
2], secure key can be distilled from the partially correlated data when the mutual information between the trusted parties exceeds the upper bound on the information which is leaking to the untrusted channel, i.e., is available to a potential eavesdropper. Assessment of this quantity depends on the presumable effectiveness of measurement, which an eavesdropper is capable of. In the most feasible case of individual measurements on the leaking signal, which do not require efficient quantum memories, needed for more advanced collective measurements, the upper bound is given by the Shannon classical information [
3]. It was shown for continuous-variable (CV) [
4] squeezed signal states that controllable modulation allows reduction of information leakage to an untrusted noisy environment [
5] and its complete cancellation once the environment is purely lossy [
6] even when an eavesdropper is capable of collective attacks. In this paper we address the minimization of information leakage in the individual attacks case, derive the respective condition and study the properties of the mutual information in the regime of minimum information leakage as well as out of this regime. In the case of individual attacks, a generally noisy environment can be optimally modeled as an entangling quantum cloner [
7]. While such an eavesdropping attack can reach the bounds set by the Heisenberg uncertainty principle, it can be feasible with the current technology as it only requires a tunable two-mode squeezed vacuum (TMSV) source [
8] and homodyne detection. We evaluate the information accessible on the signal after the measurements on the cloner modes, assuming their joint as well as independent measurements, and show that optimality of either of the approaches differs depending on whether the modulated signal is below or above the shot noise, defined by the level of vacuum fluctuations. For the sub-shot-noise modulated signals we observe that the cloner is redundant, meaning the independent measurements on its modes are more efficient compared to the joint strategy. In this regime, the standard entangling cloner attack based on the joint treatment of the measurement outcomes from the cloner modes is not optimal anymore and the modes have to be optimally treated independently. On the other hand, for the above-shot-noise modulated signals the cloner is synergistic, when the joint strategy yields more information on the signal. In the regime, when the leakage is minimum, the two approaches are equivalent. Our results are essential for security of practical squeezed-state CV QKD systems against individual attacks as well as reveal nontrivial statistical properties of entangling cloner attacks.
2. CV QKD and Entangling Cloner
We consider the generalized Gaussian CV QKD protocol between the trusted parties Alice (
A) and Bob (
B) [
5] based on the arbitrary Gaussian quadrature modulation of arbitrarily quadrature-squeezed states belonging to a single mode of electromagnetic radiation. Field quadratures are real and imaginary parts of the annihilation and creation operators of a respective mode of the electromagnetic field, which can be introduced as
and
, from which follows the commutation relation for the quadrature operators,
. Introducing the variance of an observable
as
, one can obtain the quadrature variance of a vacuum or coherent state of light, being equal to one in the used definition and being referred to as the shot-noise unit (SNU). With no loss of generality assuming that the signal states are squeezed in x-quadrature, we denote their x-quadrature variance by
. The squeezed variance is then
, which represents the fact that the squeezed quadrature fluctuations are suppressed below the shot-noise level. Accordingly, the fluctuations of the complementary p-quadrature of a pure squeezed state have the variance
. The Gaussian modulation is applied by displacing the x-quadrature by value
and the p-quadrature by value
, both taken from the Gaussian distributions with variances
and
respectively. Then the overall variance of the signal entering the channel will be
in x-quadrature and
in p-quadrature (where
are the modulation variances of the respective quadratures).
The modulated states travel through an untrusted Gaussian channel (being the worst-case assumption in Gaussian CV QKD [
7]), typically characterized by transmission
and quadrature excess noise
. The channel parameters then explicitly define the strength of an eavesdropping attack in the channel (i.e., how much signal is lost and how much noise is added) and, together with the state preparation parameters, give the upper bound on the amount of information, which is leaking to the channel. If the channel excess noise
is defined with respect to the channel input, the variance on detection outcomes
on the channel output, measured by the remote trusted party Bob using a homodyne detector, reads
which is the result of coupling the noisy signal with variance
to vacuum with the coupling ratio
.
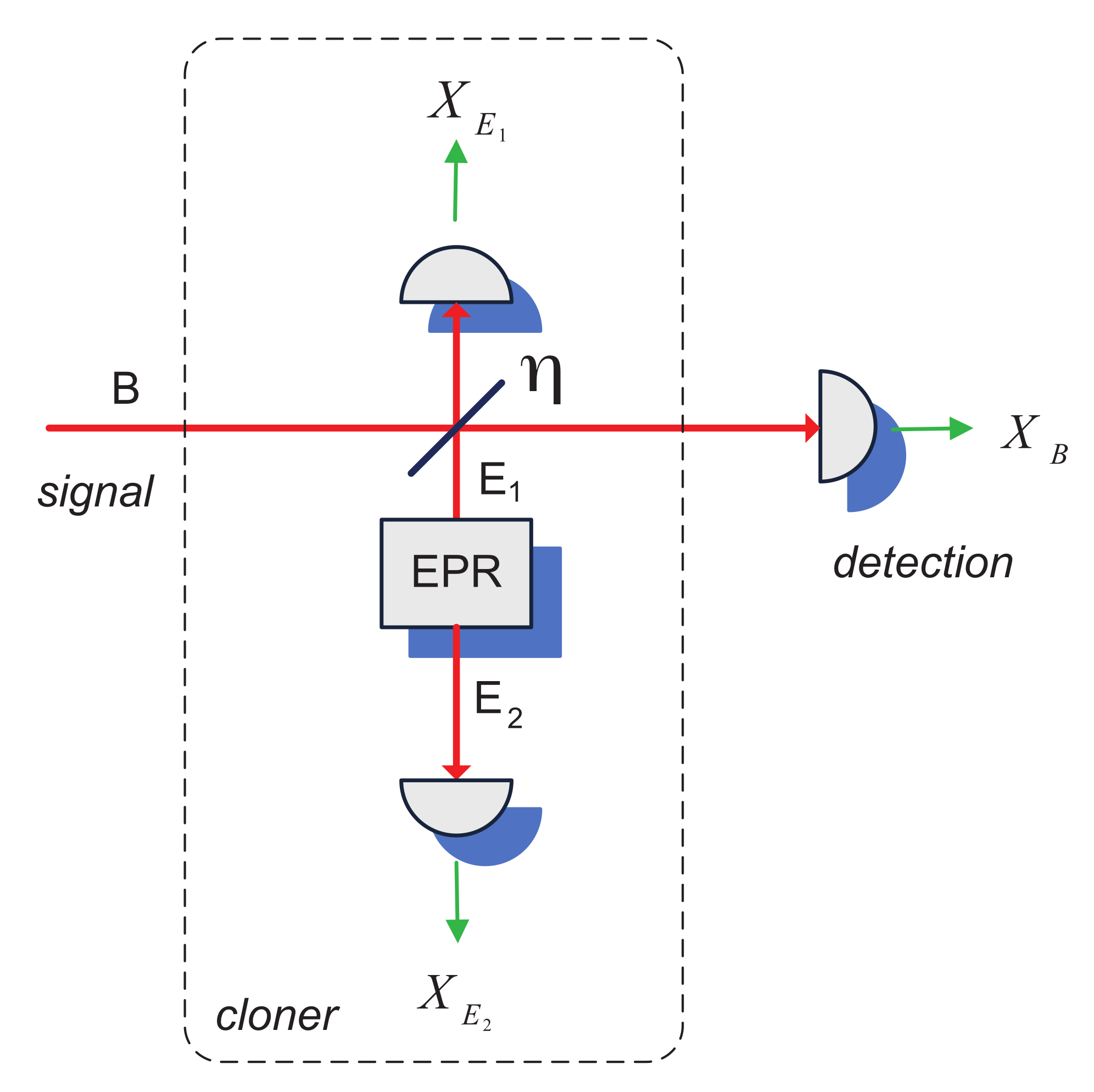
The optimal individual attack on the Gaussian CV QKD is the entangling cloner attack, which allows an eavesdropper to achieve the bound on the information about the key set by the Heisenberg uncertainty principle [
9]. The entangling cloner is a TMSV state with variance
N; one mode (
) of the cloner is coupled to the signal mode, as shown in
Figure 1, while another mode (
) is left intact. Both modes are then measured by an eavesdropper using homodyne detectors, resulting in outcomes
and
, which allows to minimize the uncertainty on the noise added to the signal by mode
, while the signal is measured by the remote party. Entangling cloner can therefore be seen as a purification of a thermal noise in mode
, coupled to the signal, or as a controllable noise addition to the signal after the measurement on mode
, thanks to the strong correlation between the two modes of the TMSV state (see more on security proofs and security analysis methods in CV QKD in the reviews [
10,
11]).
It is known [
9], that in order to mimic the actual channel parameters, the coupling
between the signal and the cloner mode has to be set to the actual channel transmittance, while the variance of the cloner modes has to be
. Then after the interaction between the signal and mode
, the variance of the data measured by Bob,
, is equivalent to (
1), corresponding to the given channel.
To evaluate the upper bound on the leaking information after the entangling cloner attack, we first derive the covariance matrix of the x-quadrature data
,
and
, measured on the signal mode
B and the cloner modes
and
, respectively, by the homodyne detectors. The elements of an x-quadrature covariance matrix are obtained as
, for
giving the quadrature variance of a given mode, and for
giving the quadrature covariance (correlation) between the modes
i and
j. Such x-quadrature covariance matrix of an entangling cloner in modes
with mode variance
N prior to interaction with the signal mode
B reads
with
p-quadrature matrix being the same up to the sign flip in the correlation (off-diagonal) term, corresponding to strong anti-correlation in
p-quadrature. Coupling
between the mode
B, containing the modulated signal with variance
V, and the noise mode
of TMSV with variance
N, can be modelled as a beamsplitter interaction, described by the input-output relation for quantum operators in the respective modes as
where
represents the transmittance and
represents the reflectance of a beamsplitter, similarly for the conjugate operators. The resulting covariance matrix then reads
which, in particular, reflects the fact that the mode
with variance
N remains intact (does not interact with the signal), while the initial TMSV correlation between the cloner modes
is scaled by
.
Considering the individual attacks, we analytically evaluate the accessible information in terms of the Shannon (classical) mutual information, defined for a pair of random variables as through the entropies of the form and the joint entropy of the form . For the Gaussian-distributed continuous variables X and Y, the mutual information can be expressed as (with no loss of generality assuming binary coding), where is the variance of variable X and is the conditional variance expressed through the variance of variable Y and the correlation (covariance) between the variables X and Y. We will also use an extension of the Shannon mutual information to the joint distribution of variables Y and Z in the form , where is the variance of X conditioned on Y and Z.
In the reverse reconciliation scenario (which is typically considered in CV QKD as it is much more robust against channel losses [
7], when the receiver (Bob) is the reference side of the protocol, the information accessible after a joint measurement on the cloner modes can be directly obtained from (
4) as
which is larger, than the information obtained from the measurement of only the mode
:
concerned with the replacement of
in the second term, which corresponds to replacement of
after the measurement on the mode
and represents the information advantage of the entangling cloner. Note that the information between the signal and the auxiliary mode
of the cloner, which reads
is also lower than (
5) for the physically valid parameters
.
When the channel noise is absent, i.e., , it means and the cloner is reduced to two uncorrelated vacuum modes, hence corresponding to the pure channel loss, in which case the measurement on has no effect on the information obtained from the measurement on .
3. Minimization of Information Leakage
The condition for minimizing information leakage was obtained in [
5] for the case of collective attacks, here we analytically derive this condition in the case of the individual ones. It can be directly obtained from the information leakage to the entangling cloner (
5) by taking its derivative by
V, which reads
As
is the convex function of
V in the physically valid region
, the minimum is reached when either
(channel is perfect), or
, meaning
. Therefore, in order to reach the minimum information leakage, the controllable quadrature modulation of the squeezed states, applied by the amplitude or phase modulator (for the amplitude or phase quadrature squeezed state respectively), has to be set in such a way, that the resulting modulated state has the shot-noise variance in the modulated squeezed quadrature. In the case of the noiseless channel
this means that the outputs of the beamsplitter, simulating the channel attenuation, are completely uncorrelated and the information leakage is fully removed [
6]. For the noisy channels
the residual correlations remain due to the noise and the minimum information leakage remains non-zero.
In the regime of the modulated state variance equal to a shot noise, i.e.,
, we obtain that the mutual information (
5) reads
It is straightforward to see by putting
to (
6), (
7) and comparing to (
9) that, in the regime of the minimum leakage, the information between the signal and the jointly measured cloner modes is equal to the sum of the mutual information quantities between the signal and each of the cloner modes:
From this, using the definition of Shannon conditional mutual information
through the conditional entropies of the form
and the conditional joint entropies of the form
, we obtain, that in the regime of minimum leakage
where
is the conditional mutual information between the modes
, conditioned by the measurement results at
B, i.e., in the regime of the minimum leakage the conditioning on the residual signal does not change the mutual information between the two cloner modes.
Indeed, we obtain the mutual information
between the modes of the entangling cloner from the elements of the
submatrix of the matrix (
4) as follows:
The conditional mutual information
can be obtained from the conditional covariance matrix
, containing variances of the form
,
, and the conditional correlation of the form
which contains the correlations
and
between either of the cloner modes and the signal mode
B.
We then obtain the resulting matrix as
and obtain the mutual information between the cloner modes conditioned on the signal mode
B as follows:
which is evidently the same as
given by (
12) when
.
In the next section we show the regimes of redundancy and synergy of the entangling cloner, when the equalities (
10), (
11) do not hold.
4. Redundancy and Synergy of an Entangling Cloner
Outside of the optimal regime of the minimum leakage from a Gaussian CV quantum channel, obtained in the previous Section, i.e., when
, one of the quantities in (
10) and (
11) exceeds another. Similar effect was previously discussed in neuro-science [
12] and information theory [
13,
14]. In particular, the situation when
is referred to as synergy, when jointly systems
provide more information on
B than separately. Alternatively, when the joint information is less than the sum of the individual ones, i.e.,
, the system
is called redundant in accessing the information on the system
B. In this terms, the optimal regime of the minimized leakage
is achieved when entangling cloner
is neither synergistic, nor redundant, while varying the modulated signal variance
V we access both redundancy and synergy regimes of an entangling cloner, used to optimally estimate the signal.
Importantly, this means that for the sub-shot-noise modulated signal
the optimality of the entangling cloner individual attack [
9], well-known in CV QKD and broadly used to study the security of the protocols, does not hold anymore. So do the security bounds set by the Heisenberg uncertainty principle, as the product of uncertainties of
knowing the outcomes of the measurements on the purifying system
E and the modulation
is below 1 SNU. It turns out, that in this regime a more efficient attack can be implemented by treating the measurement outcomes of the two modes of an entangling cloner separately.
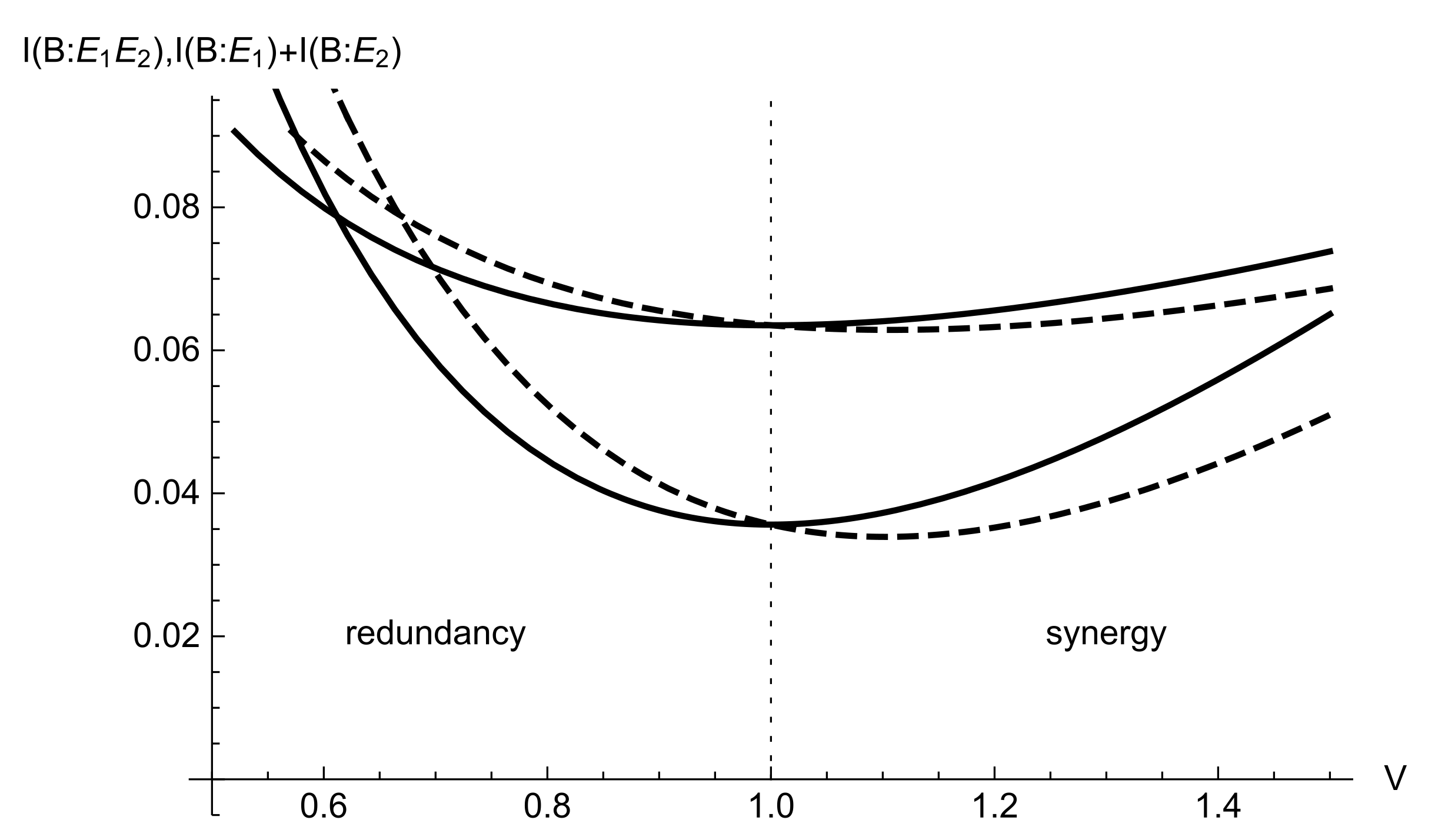
The typical regimes of an entangling cloner inferring a transmitted signal are given in
Figure 2 in terms of two types of mutual information analytically given by (
5)–(
7) with respect to the signal variance for different values of channel transmittance (cloner coupling ratio)
. It is evident from the graph that the joint information
is constantly minimized upon signal variance being equal to a shot-noise unit,
. When the signal remains squeezed (
) the redundancy of the cloner is observed, while as signal becomes more noisy than the shot noise,
, the synergy of the cloner takes place.
Similarly, we can revert the scheme and consider the communication between the cloner modes
and the role the measurement results on the mode
B take in this communication. Out of the minimum leakage regime
given by (
11), when the state in mode
B before the coupling
has shot-noise variance in the measured quadrature, the mutual information between the cloner modes can be increased on decreased by conditioning on the measurement results at
B. The typical dependencies of
and
, given by (
12) and (
15), i.e., before and after conditioning on
B, respectively, depending on the variance of the state in mode
B prior to the interaction with the cloner, are given in
Figure 3.
It is evident from the plots in
Figure 3, that, contrary to the mutual information quantities between the channel output and the cloner modes (joint or separate) given in
Figure 2, which are the convex functions of the modulated signal variance
V, the mutual information between the cloner modes
continuously increases with the increase of the signal variance
V if conditioned on the output of mode
B or continuously decreases without the conditioning. Indeed, the variance of mode
B then plays the role of an external noise, which either contributes to the mutual information once conditioning is performed, or does not, once the measurements on
B are not taken into account. We further extend the scheme to interaction between two entangling cloners and show how conditioning on an auxiliary cloner modes changes the mutual information between the modes of the main one.
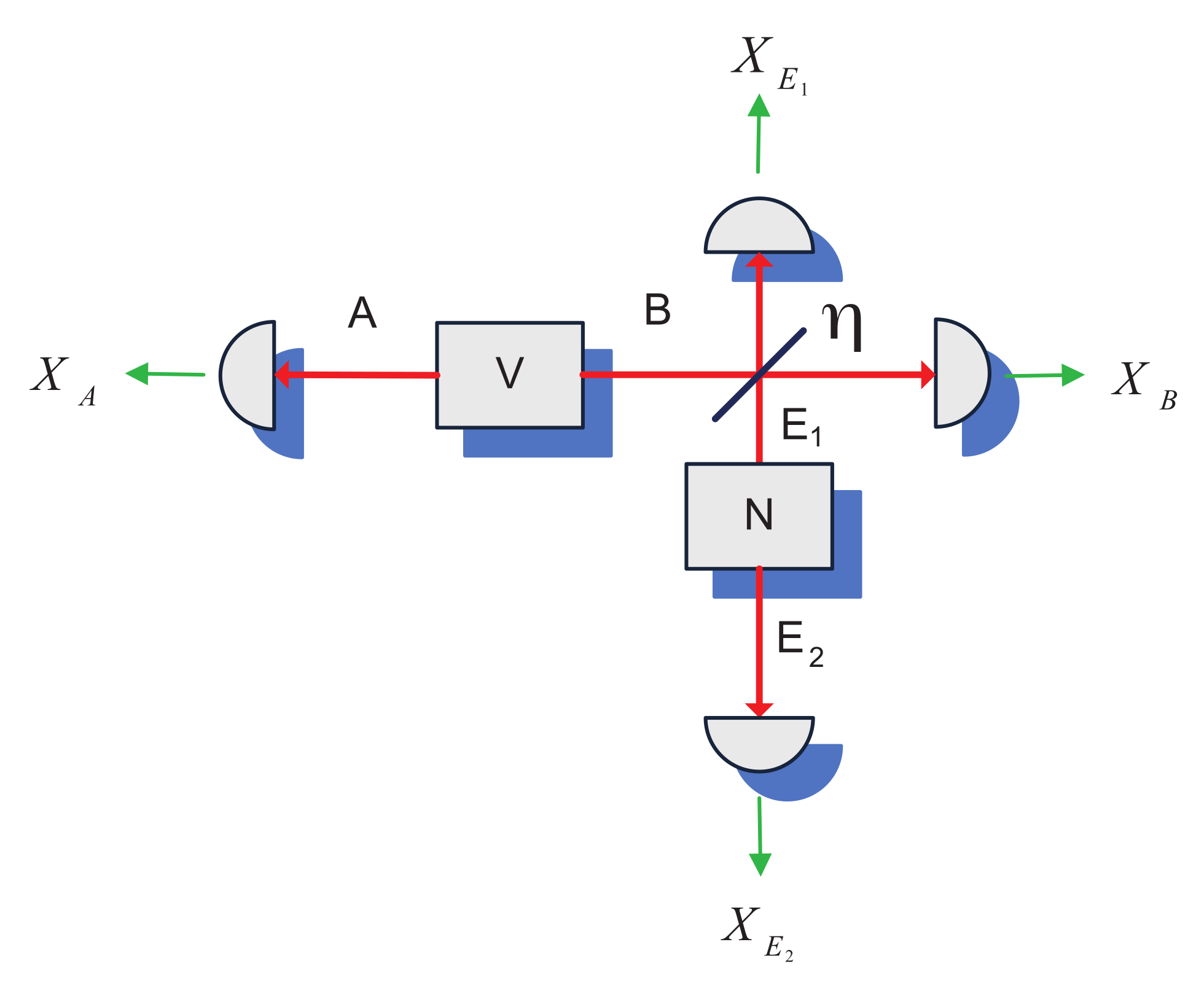
5. Two Interacting Entangling Cloners
To generalize the result of the effect of conditioning on the external noise in mode
B on the mutual information between the modes of an entangling cloner, we consider the scheme of two mutually interacting entangling cloners, as shown in
Figure 4.
Prior to interaction each of the cloners can be described in x-quadrature by a covariance matrix of the form (
2) with variances
N and
V. We consider the communication between the cloner modes
and
(which can be also seen as a purification of the modulation performed on a single mode
[
9]) and study the effect of conditioning on (using the knowledge of the quadrature values of) the auxiliary cloner modes
. We analytically derive the covariance matrices of the two cloners and obtain the respective mutual information quantities as discussed below.
After the coupling
between the modes
B and
the x-quadrature covariance matrices of the two cloners have the form
and their correlation matrix reads
Without the conditioning, the mutual information
between the cloner modes is given by (
12). After the conditioning performed on mode
B, the x-quadrature covariance matrix of the state in modes
has the form (
14) and the respective conditional mutual information
is given by (
15). As the variance
V of the cloner in modes
is always
(equality means the cloner reduces to two uncorrelated vacuum states), which is implied by the physicality constraint given by the Heisenberg uncertainty principle [
15], the mutual relation of those two mutual information quantities for the two-cloner scheme corresponds to the right part of the plot in
Figure 3. Hence, conditioning on the state in mode
B having variance larger than the shot noise level improves the mutual information between the cloner modes. Since the thermal state in mode
B, after it is split between modes
B and
by the beamsplitter
, introduces correlations between the two modes, the conditioning can be seen as application of additional controllable modulation to the mode
of the entangling cloner. Such additional modulation is known to improve the entangled resource for quantum communication [
16].
If instead of measurement and conditioning on mode
B, the measurement on mode
A is taken into account, the covariance matrix of the conditional state in modes
obtains the form (note that the mode
is not affected as it is not correlated to mode
A):
the resulting mutual information
is then exactly the same as
given by (
15). Hence, conditioning on either mode of the auxiliary cloner
improves the mutual information between the modes
due to the strong correlation between the modes
A and
B. Finally, if the measurements on both modes
is taken into account, the resulting conditional matrix reads
and the resulting mutual information
is exactly the same as
without any conditioning, given by (
12). Hence, conditioning on both modes of the auxiliary cloner cancels the positive effect of the additional correlations in modes
B and
.