1. Introduction
Nowadays, rapid developments of Internet and digital technologies have led to tremendous digital multimedia contents transmitting over Internet networks. Thus, protection on the contents of digital data has attracted serious concern from medical, military, and many other areas. Various image encryption methods have emerged by using cryptographic techniques [
1,
2,
3,
4]. Although there exists a view that AES is not suitable for image encryption, Zhang recently refuted it by using AES of cipher block chaining mode to encrypt images [
5].
The chaos-based encryption method has become one of the most ideal methods, since it has a lot of appropriate characteristics, e.g. high sensitivity on initial conditions, mixing property, ergodicity, complex behavior, etc. [
6,
7,
8]. As a result, a lot of researchers have presented plenty of image encryption schemes with a chaotic system [
9,
10,
11,
12,
13]. In [
14], Askar et al. proposed a chaotic economic map based image encryption method, whose simulation results indicated that the proposed algorithm could successfully encrypt and decrypt the images, and it had a good performance on security tests, except noise attacks analysis. By using a single round based hyper-chaotic system, Shaikh et al. presented a color image encryption method with bi-directional pixel diffusion [
15]. Additionally, Li et al. presented a "transforming-scrambling-diffusion” model based color image encryption method with a four-dimensional (4D) hyper-chaotic system, which could convert pixel values to gray format before scrambling [
16]. There is no doubt that some of the encryption methods in these chaos-based schemes still have weaknesses to some extent. However, different chaotic systems are neither superior nor inferior each other. A high-dimensional chaotic system has complex chaotic behaviors with high time cost, while a low-dimensional chaotic system is opposite [
17,
18,
19]. Hence, in this paper, a 6D hyper-chaotic system is employed as a pseudo-random numbers sequence generator for more complexity.
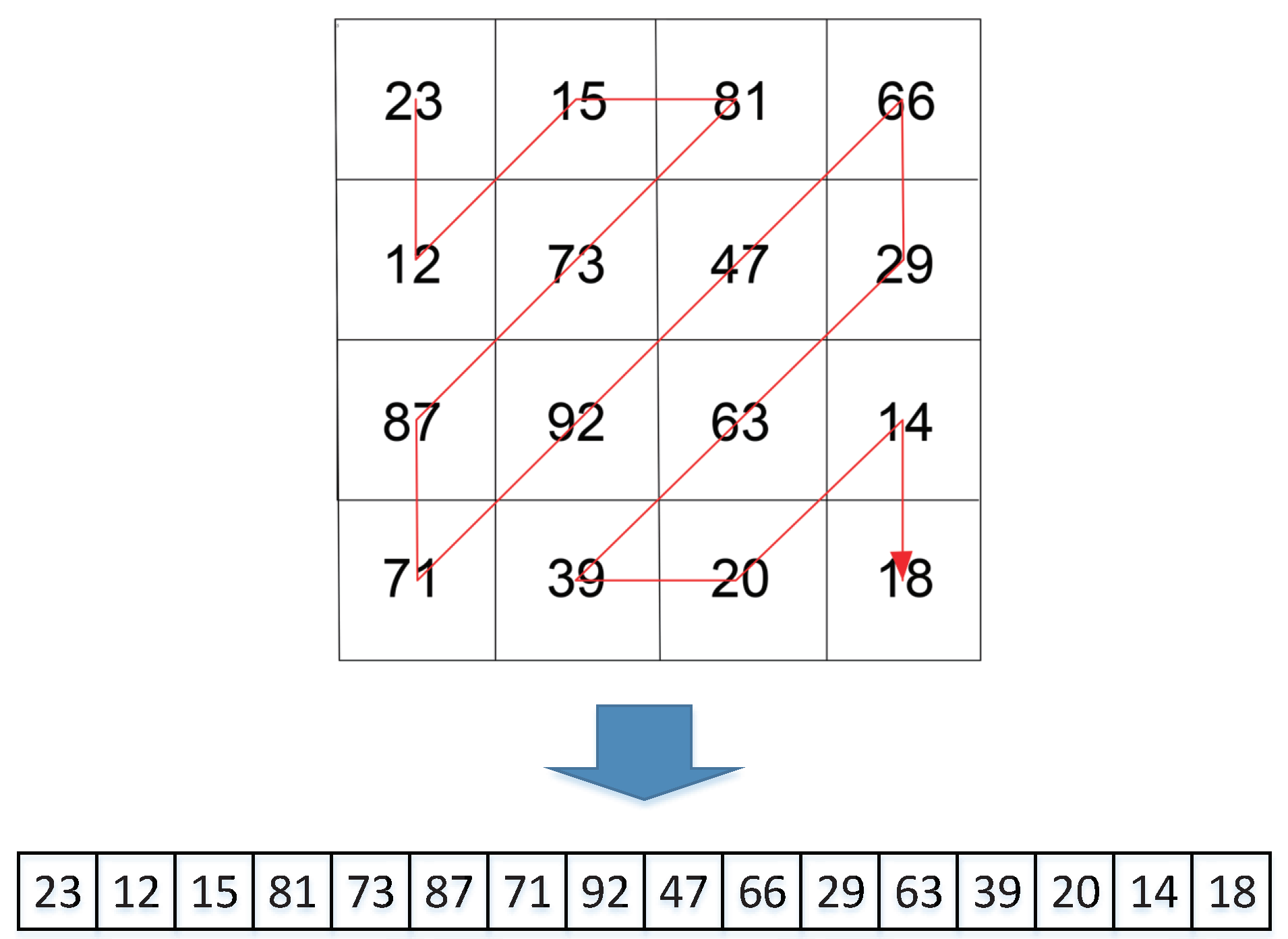
Zigzag is a common scrambling operation in image encryption [
20,
21]. In [
22], Li et al. presented a 3D logistic map based color image encryption method with Zigzag scramble; the experiments showed that this method had brute-force attack and statistical attack resistance, but differential attacks analysis was missing. While, Wang et al. proposed a color encryption method with a Zigzag transformation, which could change the start pixel from upper left corner to the other three corners in an image [
20]. Next year, Wang et al. [
23] presented another image encryption method, which introduced an extended Zigzag confusion for a non-square image. Additionally, in [
24], Zhao et al. proposed a novel color image encryption by combining Zigzag map and Hénon map together for permutation. However, these image encryption schemes implement Zigzag scramble on 2D images, which leads to some adjacent values in special positions of the image not being able to be scrambled, and different channels of a color image could not be scrambled, either. On the other hand, some image encryptions transformed 2D image to 3D cube [
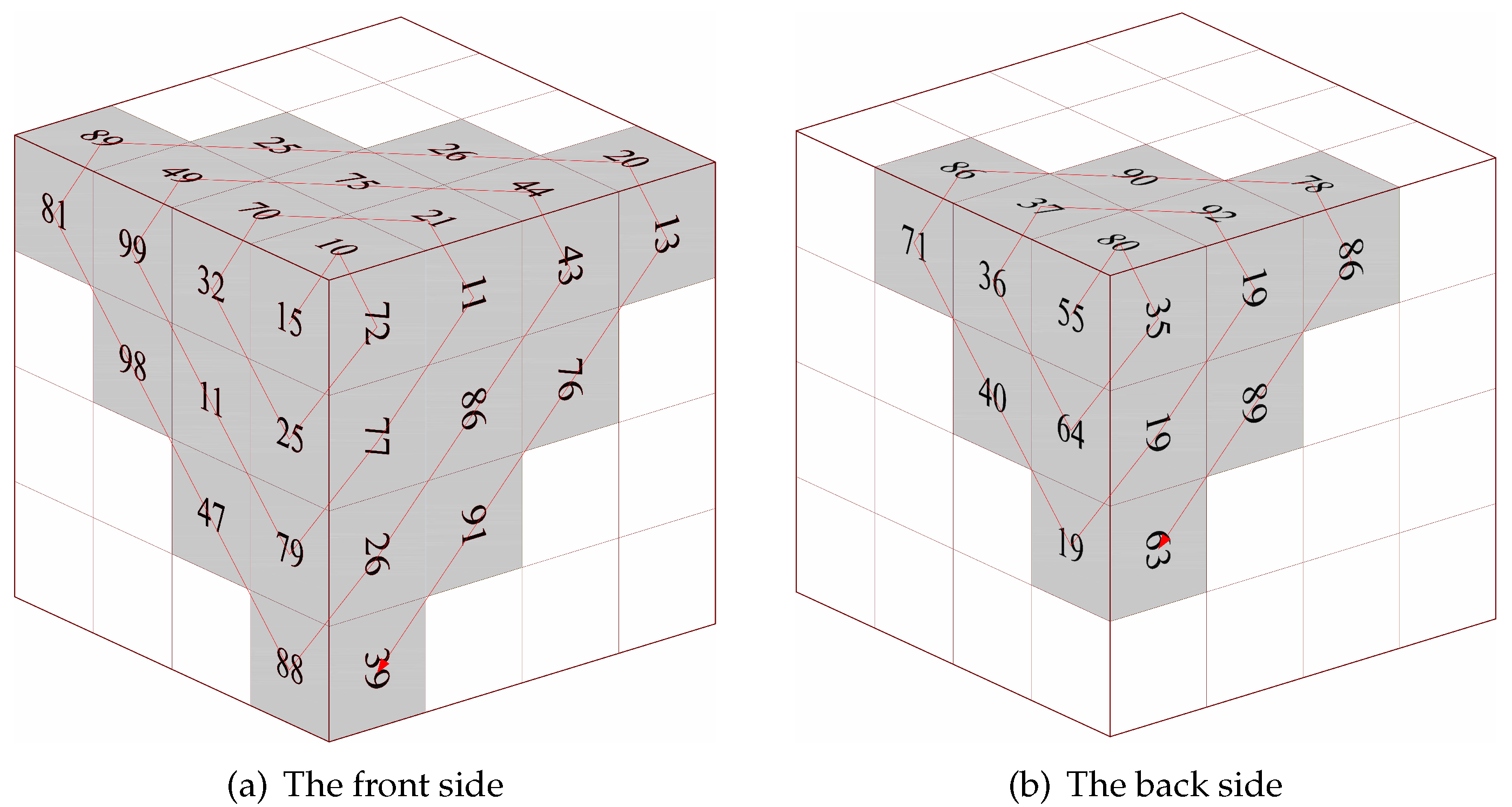
25], which gives out a new encryption inspiration on permutation, but most of them were focused on rotation, but not Zigzag. Therefore, Zigzag is utilized in diffusion on a 3D cube instead of scramble on 2D image to eliminate these drawbacks in this paper.
Deoxyribonucleic acid (DNA), a biological concept, has recently become a popular trend in the image encryption field [
26,
27]. By using DNA-based techniques, cipher images could obtain competitive entropy, correlation coefficients etc. [
4,
28,
29,
30,
31]. In [
29], Chai et al. presented a new diffusion mechanism that is based on the random numbers that are generated by plaintext image, and incorporated DNA encryption with four-wing hyper-chaotic system. Reference [
32] proposed an image encryption method using a spatial map based DNA sequence matrix. In general, the DNA-based encryption mechanism includes two steps: use DNA operation rules to convert pixels of plaintext image to DNA codon matrix and change chaotic sequence to DNA keys to generate cipher image with DNA codon matrix.
While unlike the two strands structure of DNA sequences, Ribonucleic acid (RNA) is a single strand structure. RNA could form double helixes with complementary base pairing. By using this feature, some new image encryption methods have been proposed. In [
33], Mahmud et al. presented an image encryption method by combining RNA with Genetic Algorithm (GA) through using a logistic map. In [
34], Abbasi et al. employed Chen’s chaotic system to encrypt an image with imperialist competition algorithm and RNA operations. Yadollahi et al. utilized the concepts of DNA and RNA to construct a two-phase image encryption method [
35]. While an image encryption method is presented by Wang et al. through using an one-dimensional (1D) chaotic system combined from Logistic and Sine map, extended Zigzag confusion, and RNA operation [
23]. However, all of these four schemes focus on gray image encryption. Although there is a color image experiment in [
23], it is realized by running the scheme three times in three channels.
Being motivated by above discussions, a novel color image encryption method, called HCZRNA, is proposed in this paper. At the beginning, a 6D hyper-chaotic system is employed to generate three pseudo-random matrices. Subsequently, one of the pseudo-random matrices is used to permute plaintext color image. Additionally, 3D transformed Zigzag diffusion is implemented on initial cipher image with the second pseudo-random matrix. After diffusion, an RNA operation is used to convert the diffused image to RNA codons array, and update this array through RNA codons tables that are generated by the third pseudo-random matrix. Finally, a cipher image is obtained.
The main contributions of this work is listed as follows:
A novel 6D hyper-chaotic system is employed in this paper to produce chaotic matrix for permutation, diffusion, and RNA operation.
A new 3D transformed Zigzag diffusion scheme is proposed to encrypt color images.
RNA operation is modified specifically for color images.
Extensive experiments and analyses demonstrate that the proposed HCZRNA could resist various types of attacks.
The rest of this paper is structured as follows:
Section 2 introduces the used 6D hyper-chaotic system, 3D Zigzag and RNA.
Section 3 presents the HCZRNA scheme and explains how initial values and pseudo-random matrix are generated in detail.
Section 4 reports and analyzes the experimental results. Finally,
Section 5 concludes this paper.
4. Experimental Results
The encryption and decryption schemes have been tested on four popular RGB color images in
Table 3. All of the experiments are conducted by MATLAB R2019b on 64-bit Windows 10 system, and the main hardware includes an Xeon(R) W-2223 @ 3.60 GHz CPU as well as 32 GB RAM.
For the controlling parameters setting in Equation (
1),
. Constants
in Equation (
2) are set as
and the initial constant of
T in Equation (
9) is 11. The security key can be set by users, so we set a 256-bit hexadecimal sequence that is shown below as the security key in all of the experiments. The key can also be optimized by some evolutionary optimizations, such as differential evolution and particle swarm optimization [
40,
41,
42,
43].
In order to demonstrate performance of proposed HCZRNA scheme, five state-of-the-art encryption schemes are employed for comparison: a Four-wing hyper-chaotic system based dynamic DNA encryption scheme [
29], an extended Zigzag confusion and RNA encryption based scheme [
23], a Hopfield chaotic neural network-based scheme [
44], a scheme with utilization of differences between two 1D chaotic maps [
45] and a scheme with 4D hyper-chaotic system and DNA encryption [
46].
4.1. Key Space
For an image encryption system, large enough key space is necessary to withstand a brute-force attack. In HCZRNA, a 256-bit security key is used to calculate the initial values of the hyper-chaotic system to generate the pseudo random matrices that could affect the outputs of permutation, diffusion, and RNA operations. As we know, different initial values in a hyper-chaotic system would get different pseudo random sequences, and each bit has two states, the security key has
different states, so it could generate
results of a hyper-chaotic system. Therefore, the key space of HCZRNA could be calculated as
. Theoretically, if the key space of an encryption scheme is larger than
, this scheme could resist violent crack by modern computers [
47]. Therefore, the proposed HCZRNA in this paper has a large enough key space to resist brute-force attack.
4.2. Sensitivity of Keys
The sensitivity test on keys refers to utilize slightly different keys to encrypt the same images. If an encryption is sensitive, the encryption with slight difference on keys would get completely different cipher images. To test the key sensitivity, we would use two different keys to encrypt four test images, one of these two keys is initial security key
, another key is
, which is one bit changed for
. These two keys are stated as follows, where the changed bits are shown in red:
By comparing two cipher images from the same plaintext image, the differences of cipher images that are encrypted from these two security keys are stated in
Table 4.
In the table, it is obvious that all of the differences between two cipher images are over , which reveals that, even with tiny changes in security keys, encryption by HCZRNA would also lead to extremely different outputs. Hence, HCZRNA satisfies sensitivity requirements.
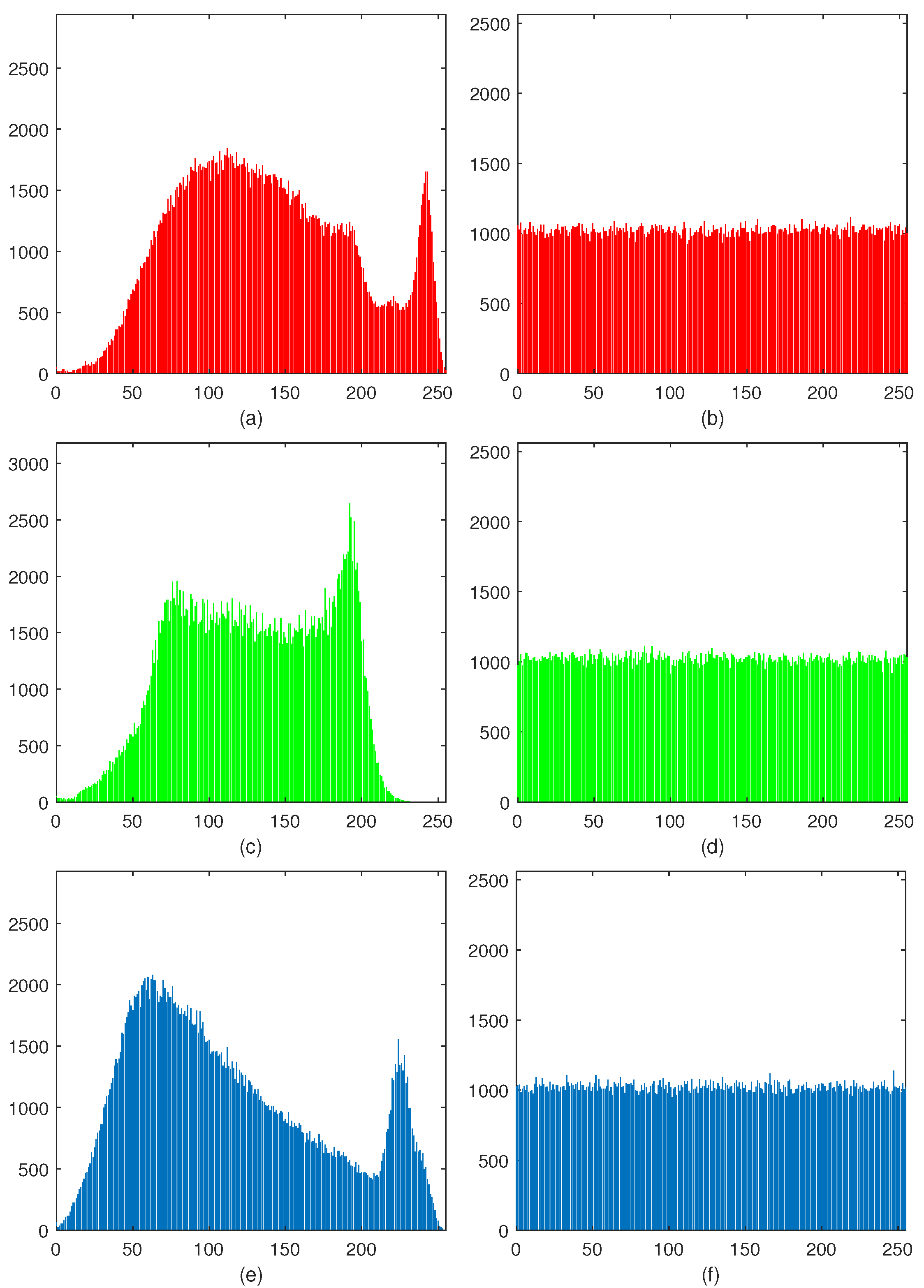
4.3. Histogram
Because a histogram reflects each pixel’s times in an image, histograms of meaningful images are fluctuated, while cipher images’ histogram should be flat and uniform. That is to say, if an encryption scheme is well-designed, the histograms of cipher images should be as flat as possible. For the proposed HCZRNA, a histogram of Baboon and its cipher image are placed in
Figure 9.
From this figure, it could find that histograms of all channels in plaintext image are fluctuated, while histograms of cipher image’s different channels are almost distributed in a narrow range, and their values are around 1000. For more accurate results, histogram statistics are introduced to evaluate the variance and standard deviation of plaintext and cipher images [
48,
49]. Variance is used to calculate the average difference in each gray level frequency with respect to mean value
, which could be formulated as Equation (
18).
where
represent the image’s height and width respectively,
x is the frequency of different gray levels of pixels in a image, and the
is the mean value of
xs. And
is the variance, the higher is
, the more fluctuate is the graphic histogram. Accordingly, if a encryption is well-designed, the
of encrypted image should be low.
As
is always very high in plaintext image, a standard deviation is used to evaluate histogram’s fluctuations, which is stated as Equation (
19).
where
is the standard deviation. For all test images,
Table 5 describes the results of histogram statistics.
In the table, the variances and standard deviations of plaintext images are very high, while they are extremely different in cipher images. All of these performances indicate that the proposed HCZRNA could effectively resist histogram attack.
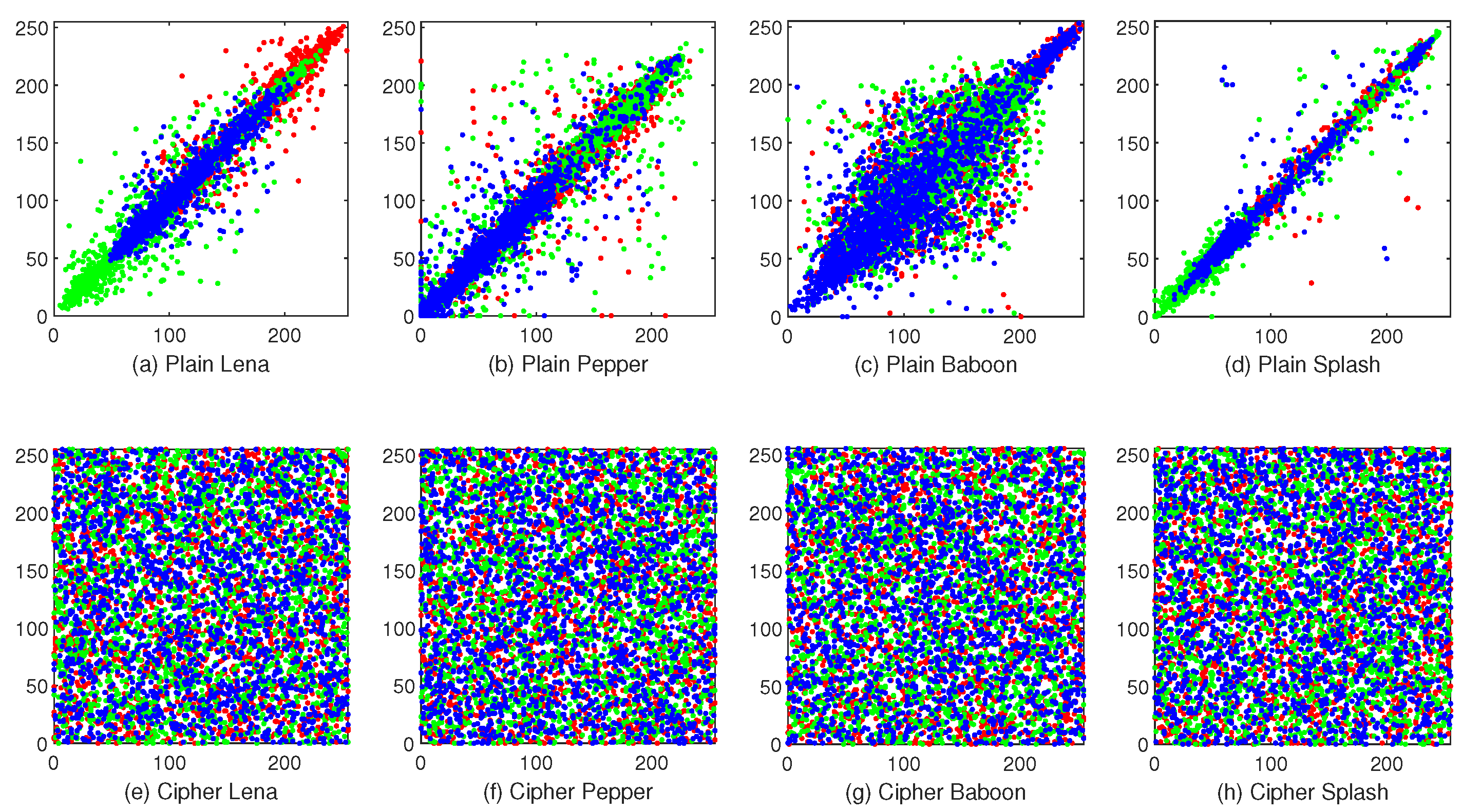
4.4. Correlation
The correlation test refers to adjacent pixels’ relationship. A meaningful image has high correlation because values of adjacent pixels are close to each other. This attribute could be utilized to crack. Therefore, a well-designed encryption scheme should have low enough correlations in three directions: horizontal, vertical, and diagonal directions. Given a pixel sequence that is represented by
and its adjacent pixel sequence
in an image, correlation between
X and
Y could be denoted as
in Equation (
20).
where
is
s mathematical expectation and
is standard deviation.
If X and Y are identical, would be a maximum of 1. On the contrary, would be close to 0 when X and Y have few correlations.
Figure 10 depicts the correlation test results. It is obvious that the adjacent pixels’ distributions in plaintext images are concentrated, while the distributions in the cipher images are opposite.
More accurately,
Table 6 provides correlation coefficients between plaintext images and cipher images. Additionally
Table 7 demonstrates comparisons with references [
44,
45]. Through this test, it could find that the correlation coefficients of the proposed HCZRNA are extremely close to 0, which means that HCZRNA could effectively break correlations existing in plaintext images. While the comparisons show that the proposed HCZRNA achieves the best results with [
44,
45] in all cases. This reveals that HCZRNA outperforms when compared schemes in terms of reducing correlations.
4.5. Information Entropy
Information Entropy shows the randomness and uncertainty of image’s pixels. If pixels in an image have uniform distribution, this image could resistant statistical attacks. Because there are 256 gray levels in each channel of color image, the Entropy calculation could be formulated as Equation (
21):
where
C denotes channels of color image and
is probability of gray level in whole channel.
The bigger , the bigger uncertainty of image. While the theoretical value of is 8.
Table 8 shows the entropies of all channels of plaintext color images and corresponding cipher images through encryptions by proposed HCZRNA. It is obvious that cipher images have increased entropies a lot from plaintext images and their entropies are very close to the theoretical value. Moreover, a comparison is held between HCZRNA and Refs. [
23,
29,
44,
45,
46], and the results are stated in
Table 9. Among all of the encryption schemes, the proposed HCZRNA achieves the highest entropies in four out of six cases. It could conclude that HCZRNA has the ability to resist statistical attack.
4.6. Differential Attack
The differential attack test is an important security test for image encryption, which reveals the influence on the cipher image caused by a minor change in pixels of plaintext image. If a tiny change on pixels in plaintext image leads to significant different cipher image, that is to say the encryption scheme could resist differential attack.
Two important indices are introduced to measure the ability of differential attack resistance, which is called the number of pixel change rate (NPCR) and the unified average changing intensity (UACI). Additionally, they are defined as Equations (
22) and (
23):
where
and
are two cipher images, and
means the pixel’s value at coordinate
in image
e.
denotes whether the same coordinate’s pixel values in
and
are independent or not, which could be formulated as Equation (
24):
For two random images, NPCR and UACI’s expected values are stated as:
and
for an 8-bit gray image [
30].
Hence, to realize the test, one bit would be changed on a random pixel in plaintext image. And both the plaintext image and changed image are encrypted to two different cipher images.
Table 10 lists the average results of ten times tests. It could find that all NPCR values and UACI values of cipher images’ different channels exceed the theoretical values. Additionally, comparisons with Refs. [
23,
29,
44,
45,
46] are shown in
Table 11 and
Table 12. Through the comparisons, the proposed HCZRNA encryption scheme has better performances on NPCR and UACI, which indicates that HCZRNA could resist differential attack well.
4.7. Robustness
It is unavoidable that there data loss or noise attack occur when cipher images are transmitting. Hence, a well-designed encryption and decryption scheme should resist contamination on cipher images to recover plaintext images without great changes.
To demonstrate robustness of proposed HCZRNA scheme,
,
, and
data lose tests and
,
, and
salt and pepper noise tests would presented in
Figure 11 and
Figure 12.
From the figures, the main information of plaintext images could be identified from decrypted images, which could conclude that HCZRNA has enough robustness for data loss and noise attacks. Here, the Mean Squared Error (MSE) and Peak Signal to Noise Ratio (PSNR) are also utilized to test robustness [
48,
49], which is formulated as Equation (
25).
where
P and
E represent two different images. MSE is used to evaluate the difference between two images, and PSNR depicts the ratio between the maximum possible power of a signal and the power of distorting noise that affects the quality of its representation. The lower the MSE, the higher PSNR, which indicates that two images have high similarity. Hence, under noise attacks, if the PSNR between the plaintext image and decrypted image is high, the encryption and decryption schemes are good enough.
Table 13 and
Table 14 present the results of plaintext image and decrypted image of Lena under data loss and salt and pepper noise attacks.
Through the results, we could find there are high MSEs and low PSNRs in these tables, which figures out that HCZRNA could resist attacks of data loss and noise.
4.8. Running Time
In HCZRNA, the pixels of image would be walked through multiple times in diffusion and RNA operation. Suppose that the size of RGB image is
. For the five parts of encryption processes that are listed in
Section 3.1, initial values of hyper-chaotic system are calculated from the security key, which costs
time complexity; the hyper-chaotic matrices are computed
times iterations; for permutation, reshape and sort operations are implemented three times; while the diffusion process walks through each pixel two times, which costs
; at last, as RNA operation walks through all 6-bit codons that are transformed from 8-bit pixels, the times of iteration are increased to
. Hence, the time complexity of HCZRNA could be calculated as
. Using the experiment environment that is listed in this section, the running times of encryption and decryption could be stated in
Table 15. Although the time costs of encryption and decryption are not very good, the time complexity is also a polynomial time, which could be tolerable. Additionally, the processes of RNA operation on different codons have no correlation with each other, which could improve computational time by computing RNA operation in parallel.