1. Introduction
Large Intelligent surfaces (LIS) are a promising technology for beyond fifth-generation (B5G) systems, given the number of papers emphasizing their advantages, whether compared to relays [
1] or even when used to enhance the power of millimeter wave technologies [
2]. Furthermore, reflecting signals with extreme precision and without power consumption can reduce the interference and improve the signal-to-noise ratio at the receiver, especially when the direct path between transmitter and destination is weak and needs to be strengthened.
In addition, known as large reflecting surfaces, they have recently been studied as a solution for different modulation schemes and communication channels. Their performance metrics show their significant potential for mobile communications. For example, Yang et al. [
3] proposed a transmission protocol to reduce the channel estimation overhead when adjacent cells share the same reflection coefficients. In addition, optimization methods are used to allocate the transmit power and maximize the achievable rate in an orthogonal frequency division multiplexing (OFDM) scheme under frequency-selective channels.
In [
4], Basar presented a mathematical framework to obtain the signal-to-noise ratio and derive the symbol error probability of an LIS-aided communication system, with or without knowledge of the channel phases. The author also proposed an access point sending signals directly to the users aided by a LIS system. Wymeersch et al. [
2] emphasized that, although there are already other techniques for high frequencies (0.1 to 1 THz), these technologies are limited by multipath propagation and obstacles presented in the environment. In this case, LIS can control the physical propagation environment, decrease energy consumption, and simplify location and mapping systems, creating a line-of-sight (LoS) path between transmitter and receiver.
In [
5], the authors presented solutions for the adjustment of the LIS elements’ phases, which optimizes the channel capacity and the precoder applied on the transmitter side. Elbir et al. [
6] developed a deep learning framework to obtain the channel state information (CSI) in a massive multiuser MIMO system aided by a LIS. The authors estimated each user’s composite channel and the direct path through a convolutional neural network whose inputs are the received pilot signals. Lin et al. [
7] performed channel estimation by applying Lagrange multipliers and a dual ascent-based scheme iteratively. They also found a closed-form solution for Cramer–Rao lower bounds and proposed a method that improves the accuracy of the classical least-square method. Taha et al. [
8] presented an energy-efficient architecture where all the LIS’s elements are passive except for a few distributed active elements that are arranged in a non-uniform manner. The reflector array applies deep learning models to obtain the optimal matrices of phase shifts.
Although an LIS is usually a panel of reflectors physically organized in planar shapes, Hu et al. [
9] proposed alternative structures with a three-dimensional spatial configuration with spherical surfaces. In addition to broader coverage, they have a more straightforward positioning system when compared to the conventional planar arrays.
LIS must be large in far-field communications to compete with classic massive MIMO systems and compensate for multipath propagation and electromagnetic interference. Besides that, optimizing the phase shifts associated with each element of the LIS is a great challenge. Therefore, in [
10], Najafi et al. proposed an optimization method based on the physical modeling of the propagation and clusterization of a thousand reflectors into small subsets, also known as tiles. Based on concepts from radar communications, they modeled the impact of each tile on the overall channel, calculated the associated electric and magnetic fields, and showed that it is possible to optimize the operation of the LIS to maximize some quality of service (QoS) criteria.
On the other hand, Garcia et al. [
11] focused on near-field environments and established a relation between the array size and the Fresnel zones. The punctual approximation of the scattering characterization presented dependence on the second and third-order moments of the distance. On the contrary, for far-field, the dependence is given for the fourth power. Kishk et al. [
12] employed some stochastic geometry tools to analyze the effect of the large-scale deployment of LIS on the performance of cellular networks in the presence of blockages surfaces. They established a relation between the density of LIS panels and blockages.
Mukherjee [
13] explores the idea of integrating LIS with mobile edge computing (MEC) technology that intends to leave computing involved in processing the received signal to a cloud server and describes how these technologies can mutually benefit and create a framework competitive for 6G. Finally, Malandrino et al. [
14] analyze the possible benefits of using intelligent and reflective surfaces to increase the privacy and security of mobile communications through secrecy rate, considering that passive eavesdroppers are involved in the system, in addition to legitimate users.
In addition to the works related to optimal estimation and power control in transmission systems aided by LIS, it has become a trend to compute the channel’s capacity in the face of eavesdroppers. The question to answer is: “Does such a system offer the physical layer security that prevents an intruder from receiving a signal not intended for him?” The secrecy outage probability metric can answer this question since it means the probability that the instantaneous secrecy capacity is less than or equal to a given capacity threshold. Below are some works that, like ours, are concerned with information security in systems assisted by LIS.
2. System Model
As shown in
Figure 1, this study considers a base station (BS) equipped with an antenna array of
K antennas transmitting the same signal to a unique single antenna user, the destination. Additionally, a large intelligent surface system with
N reflecting elements aids the system. Both channels BS to LIS and LIS to the user are modeled by the Nakagami-
m distribution. There is a direct link between the user and the BS and between an eavesdropper and the BS whose channel is also Nakagami-
m distributed. The signal that arrives at the destination antenna is given by
where
is the link between the source and the LIS,
is the link between the LIS and the destination and
is the direct link between the source and the destination. The term
is a diagonal matrix, whose elements are the phase shifts
applied by the LIS to the incident electromagnetic waves. The LIS’s phases,
, are assumed continuous in the interval of 0 to
radians. The term
represents the precoded signal, where the data symbol is
and the optimal precoding vector is applied by BS, according to the MRT (maximum ratio transmission) criterion, i.e.,
Finally, the term
is additive white Gaussian noise (AWGN) with zero mean and unit variance. Suppose that there is no LoS in the direct link and that it is modeled as a complex normal random variable, with zero mean and variance
. Additionally, the magnitude of the channels
with
are Nakagami-
m distributed with probability density function (PDF) given by
In this work, the parameters
and
refer to the shape and spread of the Nakagami-
m PDF, respectively. The distribution of the phases is not specified since, for this model, these phases are not relevant. Then, the overall channel, including the LIS and the antenna array, can be defined as
whose representation in scalar form is
Perfect phase cancelling occurs when
. Therefore, in this scenario, it follows that
. However, the task of removing the overall channel phase is unfeasible. Some residual phase noise is left behind, in this case,
, where
is the phase noise, which, in this work, is modeled as a Von Mises random variable with concentration parameter
. Therefore, the overall channel can be written as
It is expected that there is no phase error in the best case analysis, but this situation is entirely unfeasible. However, it is possible to estimate an optimal phase adjustment matrix that provides a performance as good as possible, so it is expected that, on average, the phase errors are zero. The zero mean Von Mises circular distribution can be proper to model the phases of each antenna’s fading coefficients [
20]. It has nonzero support in the interval −
and
and a concentration parameter
associated with the quality of the phase adjustment promoted by the LIS and the efficiency of the channel estimation method.
The moment-generating function (MGF) of the Von Mises distribution is useful since a complex exponential represents the phase adjustments. With the MGF, it is possible to calculate the statistical moments associated with the channel coefficients.
Let X be a Von Mises random variable; therefore, its MGF is given by . Since the zero mean Von Mises distribution is symmetric about zero, then the imaginary part of the MGF , and the real part is , where is the modified Bessel function of first kind and order p.
Considering that the precoder is the normalized hermitian of the overall channel, the SNR of the desired link is
Assuming, as an approximation that
is Gamma distributed, then its statistical moments,
and
can be estimated as
where
and
are the shape and rate parameters, while
and
are the expected value and variance of
, respectively, as shown throughout
Appendix A.
The assumption that the distribution of
is Gamma distributed can be assessed using the Hellinger distance. According to Beran [
21], the Hellinger distance between two arbitrary discrete probability distributions
and
can be obtained as
where
is the number of samples available to calculate the distance. The Hellinger distance is limited in the interval
and can be considered as an absolute metric.
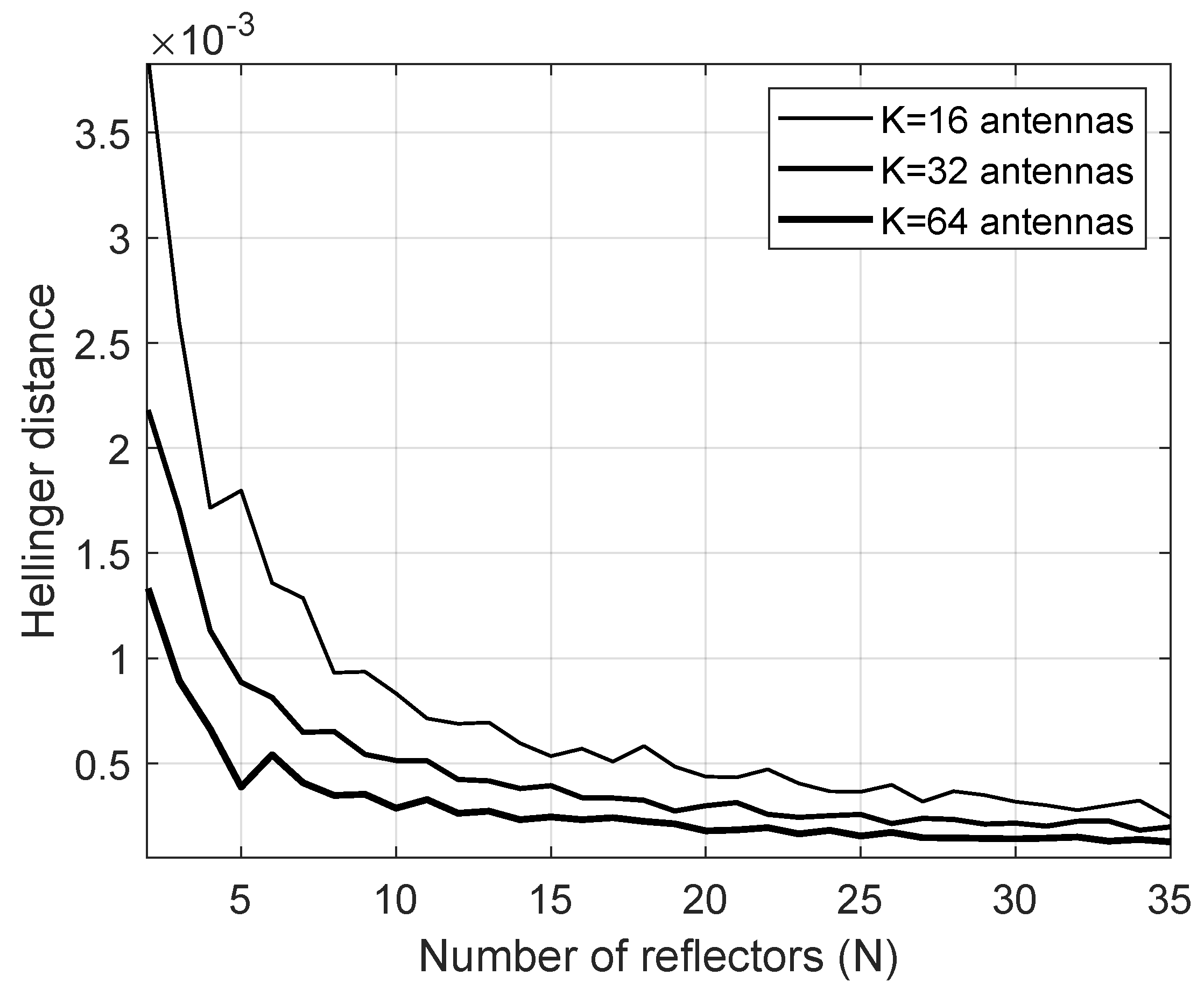
In
Figure 2, the realizations of a Monte Carlo simulation of the channels involved in the system are used to compose a histogram that approximates the PDF of the overall channel that is compared to the Gamma distribution predicted by the approximation proposed in this study. To perform the analysis,
iterations were performed with unit variance for all channels, Von Mises concentration parameter
and the Nakagami parameter
. The results show that the Hellinger distance decreases when
N and
K increase. In the last case, for
, the decrease is even more pronounced. Therefore, this accurate approximation motivates us to formulate the problem further.
4. Numerical Results
This section analyzes the accuracy of the proposed approximations and discusses the improvements in capacity provided by LIS. In unspecified cases, this study adopts, by default, the Nakagami-m shape parameters . The spread parameters were chosen to make the variances , the Von Mises concentration parameter , antennas at the source, the size of the M-QAM constellation is , and the number of iterations is for each Monte Carlo simulation.
For each iteration of the Monte Carlo method, we generate the coefficients
of (
6), the magnitudes are generated using the Nakagami-
m distribution and the phase errors with the Von Mises distribution. Given the coefficients, it is easy to estimate the bit error rate, spectral efficiency, and the SOP in each realization of the random variables and approximating the simulated results by the mean value of these quantities. We compare each of the simulated results in several iterations with the theoretical formulas described in terms of channel parameters.
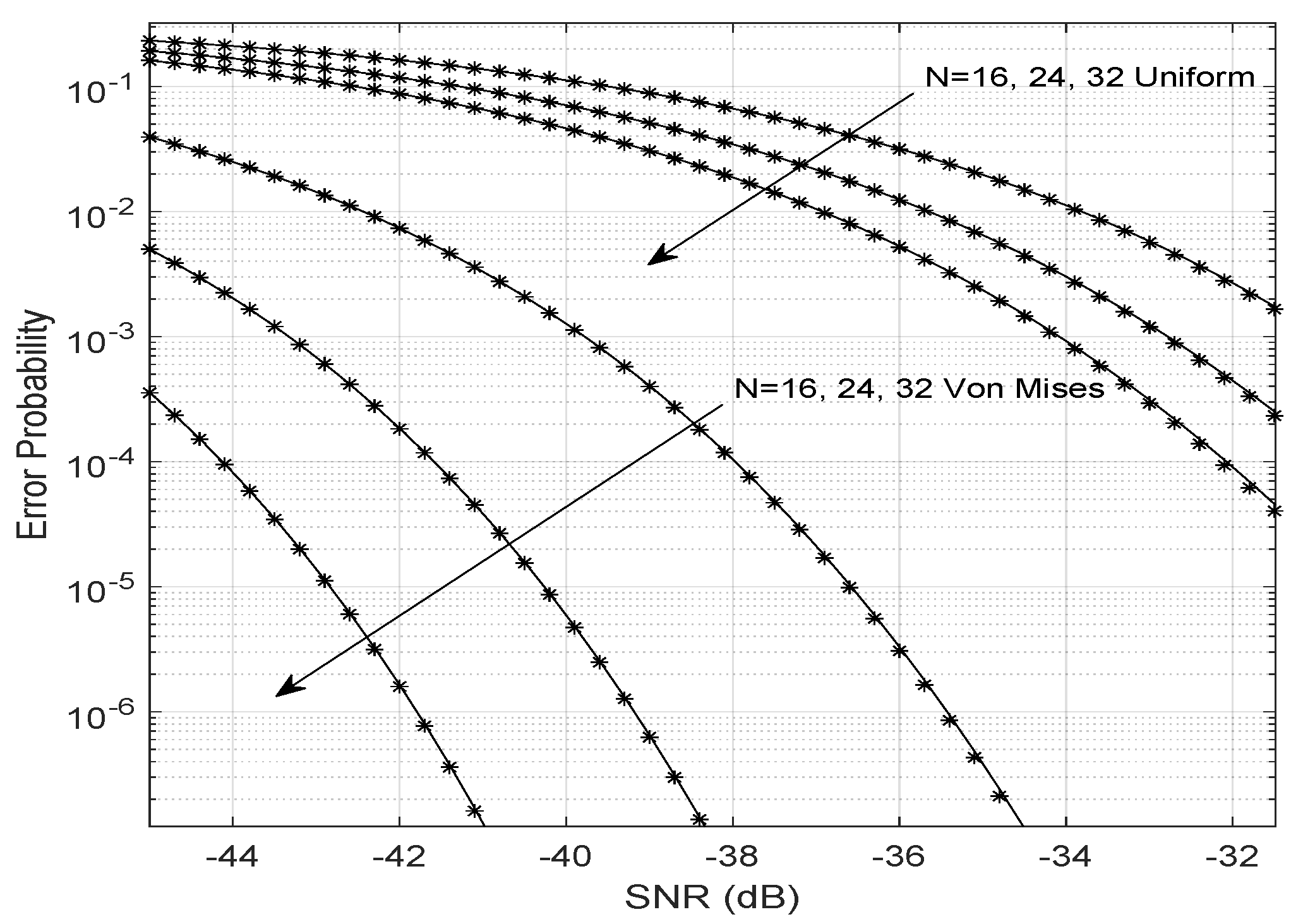
Figure 3 shows the simulated and theoretical BERs considering the Von Mises and uniformly distributed phase errors. The theoretical BER is obtained assuming that the overall fading channel has a Gamma distribution. Note that the larger the number of reflectors,
N, the smaller the error probability for any SNR value. When the phase errors are uniformly distributed (
), the error probability is higher than in the Von Mises scenario. This result shows the importance of accurately estimating the phases and channel gains and choosing the optimization method to find the best LIS phase shifts. Uniformly distributed phase noise indicates that the algorithm has equal chances to present significant phase errors (close to
) or small phase errors (close to zero). That implies greater bit error probabilities, which can be compensated only with a large number of antennas at the transmitter or with a large number of reflectors at the LIS.
In its turn,
Figure 4 confirms that large reflecting surfaces can produce an LoS link between the transmitter and the user even in a far-field Rayleigh fading channel. However, in a near-field scenario, a stronger LoS link (higher Nakagami-
parameter) implies a lower probability of error.
Even in weak LoS scenarios, LIS can decrease the probability of bit error by creating an LoS that is the result of beamforming toward the target user.
Figure 3 shows that, for an environment with a fixed value of
m, the increase in the number of reflectors (
N), or the improvement of the phase adjustment performed by the LIS (related to the concentration parameter
) can reduce the bit error rate in an aided LIS system.
The upper bound (
15) for the error probability proposed by Ferreira et al. [
19] is very close to the bit error rate as shown in
Figure 5, even when the fading coefficients are Nakagami-
m distributed.
Regarding spectral efficiency, this study considers two scenarios. The first one has uniformly distributed phase noise, and the second one has a Von Mises distributed phase, as shown in
Figure 6. Notably, the spectral efficiency increases when the LIS has a more significant number of reflectors, thus indicating a better sharing of the spectrum for the transmission of signals for a multiuser scenario. Moreover, the efficiency is higher for the case in which the phase errors have a Von Mises distribution and lower when the phase errors are uniformly distributed, which means that the phase adjustment of the LIS is a highly relevant factor in improving the spectral efficiency, reinforcing the importance of channel estimation and choice of the phase correction applied to reflectors. When the phase error distribution is more concentrated around zero (higher
values), then the spectral efficiency is higher. Using an array of antennas on the base station can be a good choice to achieve better spectrum sharing in diverse scenarios. It is also remarkable that the result predicted by the formula proposed for the spectral efficiency is very close to the results obtained by the Monte Carlo simulation.
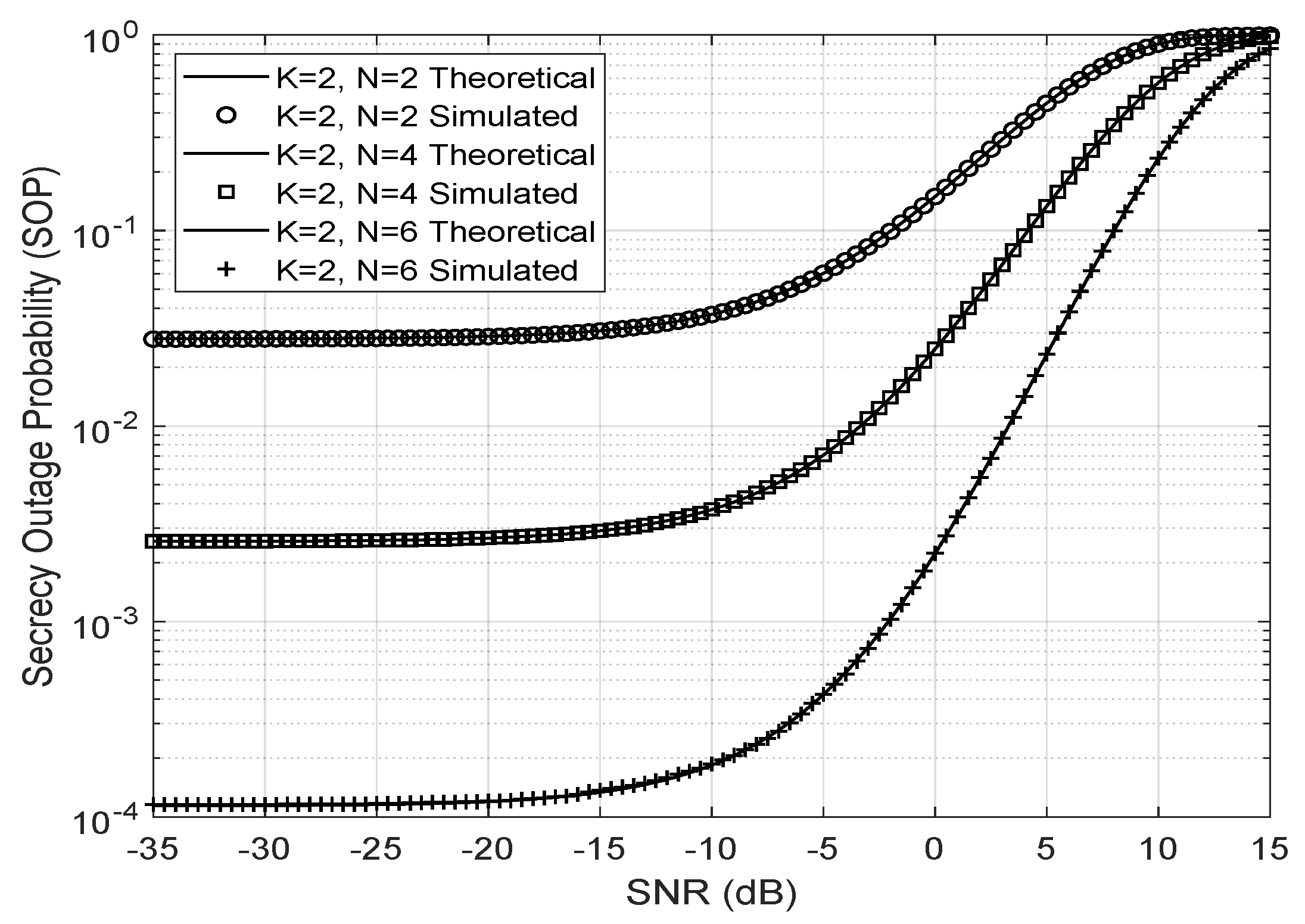
In
Figure 7, the secrecy outage probability for a Nakagami-
eavesdropper link with
and
is shown. The sum was truncated up to the index 1000, and the number of iterations used was
to generate the Gamma distributed random SNR with parameters
and
, the Von Mises concentration parameter
,
antennas, unity variance, and Nakagami-
m fading distribution for all channels between the antennas, the LIS, and the user. The larger the number of reflectors or the SNR, then the greater is the SOP.
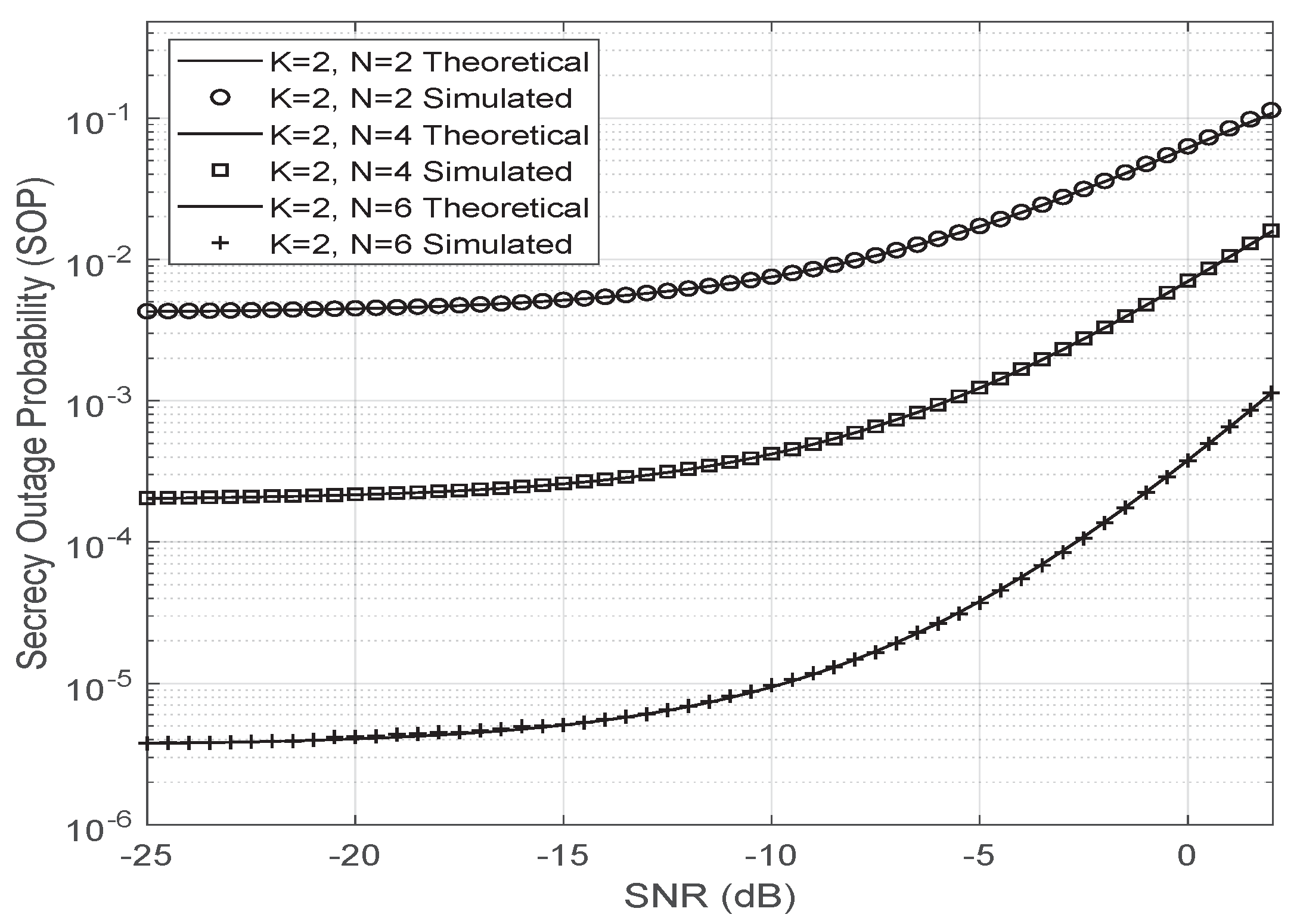
The first-order approximation of the SOP, considering that the Nakagami-
m parameters are
and
for all the channels in the system model, is also close to the simulated result as shown in
Figure 8.