Abstract
In theory, high key and high plaintext sensitivities are a must for a cryptosystem to resist the chosen/known plaintext and the differential attacks. High plaintext sensitivity can be achieved by ensuring that each encrypted result is plaintext-dependent. In this work, we make detailed cryptanalysis on a published chaotic map-based image encryption system, where the encryption process is plaintext Image dependent. We show that some designing flaws make the published cryptosystem vulnerable to chosen-plaintext attack, and we then proposed an enhanced algorithm to overcome those flaws.
1. Introduction
With the rapid progress in digital technology and mobile devices, people have produced more and more user-generated information in these few years; besides texts, most of them are multimedia data, such as images and videos. With the increasing of information security and privacy protection issues, researchers have proposed lots of encryption algorithms [1] against unauthorized access to those user-generated media data.
As suggested in [2], the main techniques used to develop image encryption algorithms can roughly be divided into the following six categories: chaotic map, DNA computing, cellular automata, wavelet transmission, neural networks, and compressive sensing. The extreme initial value sensitivity and high randomness of the chaotic systems make the chaotic maps the most popular tool in digital image encryption algorithms. This is because the chaotic systems have some useful properties, like being ergodic, highly sensitive to initial conditions, and pseudo-randomness, which fit the essential requirements for building a practical cryptosystem [3]. Fridrich [4] proposed the first image encryption algorithm based on a chaotic map in 1998. After that, a large number of digital image encryption algorithms that were based on chaotic maps were proposed [3], and the references therein. Since Liu et al. addressed lots of the chaotic map-based image encryption algorithms published on signal processing and information technology-related Journals before 2019, our following discussions will mainly focus on related works [5,6,7,8,9,10] posted on the Entropy Journal, most recently.
In order to prevent an Image exchanging system from brute force and differential attacks, [5] presented a new image encryption mechanism, in which the Enhanced Logistic Map (ELM) and some simple encryption techniques, such as block scrambling, modified zigzag transformation, and chaotic-map based key generation, are used. The results of encryption are evaluated from six different security measures. The corresponding results demonstrate the security, reliability, efficiency, and flexibility of the proposed method. Sine-Tent map (STM) is intended in [7] to widen the chaotic range and to improve the shambolic performance of one-dimensional (1D) discrete chaotic maps. Based on STM, a novel double S-box based color image encryption algorithm is recommended, which offers better applicability in real-time image encryption. Notice that, in [7], the 256-bit hash value of a randomly sampled noise signal is applied to serve as the one-time initial values of the proposed system. Since there is only one operation, XOR, is used to diffuse the pixels; the encryption process can be executed very fast. [8] presents a chaotic-map based image encryption algorithm, where Logistic and Henon maps are used.
High key and high plaintext sensitivities are a must for a cryptosystem to resist the chosen/known plaintext and the differential attacks. High plaintext sensitivity can be achieved by ensuring that each encrypted result is plaintext-dependent. To reach this goal, [9] suggested that the surrounding of a plaintext image could be surrounded by a sequence generated from the SHA-256 hashed value of the corresponding plaintext. For conquering the same challenges, in [10], both the permutation and the diffusion stages of the proposed color image encryption scheme are related to the original plain image. For keeping high system efficiency, only one round of plaintext tied permutation and diffusion operations are performed for obtaining the cipher image. Moreover, the proposed approach can be applied to real-time image encryption directly since there is no need to send original image dependent security keys to the receiver. Our work is highly inspired by and related to [10]; we will explore it further in the next section.
In general, the analyses of encryption and decryption algorithms show that all of the algorithms, as mentioned above, have a good encryption effect, anti-attack ability, and high security. However, a minor designing flaw may make encryption algorithms vulnerable, even if they are chaotic-based. In the following, we will take the high plaintext sensitivity related work: “A simple Chaotic map-based Image Encryption System Using Both Plaintexts Related Permutation and Diffusion (CIES-UBPRPD)”, as proposed by Huang et al. [10], as an example to illustrate our above statement.
In a plain data-dependent cryptosystem, like CIES-UBPRPD, the cryptanalysis complexity is mostly increased. Therefore, the security level of the system will also be enhanced. Even though the experiments given in CIES-UBPRPD [10] showed lots of advantages when compared with conventional approaches, some designing flaws have been found by us. In this work, we first break a simplified version of CIES-UBPRPD with a chosen-plaintext attack, to demonstrate the effect of the discovered flaws. Subsequently, we make a few adjustments on CIES-UBPRPD and show that the modified version does relieve the defect of the original CIES-UBPRPD.
The rest of this paper is organized, as follows. Section 2 briefly describes the process of CIES-UBPRPD. In Section 3, we pointed out some design flaws of CIES-UBPRPD and demonstrated the effects of the weaknesses by issuing a chosen-plaintext attack against a simplified version of it. Afterwards, a modified version of CIES-UBPRPD is provided in Section 4. With the added supplements, the security level and the completeness of CIES-UBPRPD can be enlarged significantly. Some experimental results of the modified CIES-UBPRPD are presented in Section 5, in order to verify our previous claim, where the associated security analysis is also included. Finally, Section 6 concludes this writeup.
2. Related Work
In the original CIES-UBPRPD [10], all the arrays are started with index one, while in this work, we use an equivalent description but change all array indexes starting from zero. For the ease of discussion, except for the array indexes, most of our notations follow the usage that was adopted in [10].
2.1. The Involved Chaotic Maps
2.1.1. Generalized Arnold’s Cat Map
Arnold’s Cat Map (ACM) is a well-known two-dimensional chaotic system proposed by the Russian mathematician Vladimir I. Arnold [11]. ACM is usually replaced by its generalized form to achieve higher security and higher randomness, as shown in Equation (1):
where and denote the positions of the original pixel and the target pixel, and are the system parameters, while and are the image’s height and width, respectively. After obtaining the target position , from Equation (1), the two pixels that are located at and will swap their pixel values with each other.
2.1.2. Chebyshev Map
Chebyshev map [12] is a one-dimensional chaotic system that can be formulated, as shown in Equation (2):
where and is again one of the system parameters. For , chaotic behavior of Equation (2) holds. The initial value of the above equation is considered as part of the secret key. In CIES-UBPRPD, is fixed at 4.
2.2. Image Encryption Algorithm
On the bases of ACM and Chebyshev map, the above-mentioned Chaotic map-based Image Encryption System—CIES-UBPRPD—was proposed by Huang et al. [10], where the most eye-catching property of the algorithm is its plaintext data-dependent encryption process. The encryption process of the original CIES-UBPRPD consists of the following two stages:
2.2.1. Permutation Stage
Step 1. Iterate the Chebyshev map defined in Equation (2) times, discard the first terms to avoid the harmful effect, and obtain the chaotic sequence , which contains elements.
Step 2. Generate another sequence according to
where and denotes bitwise XOR operator.
Step 3. Calculate , , and based on the following equations:
where , , and represent the Red, Green, and Blue channels of the plain image , respectively.
Step 4. Calculate the system parameters by using the following equations:
where , , and are pairs of parameters used to permute , , and respectively. Moreover, mod (x, m) denotes the calculation of “x mod m”.
Step 5. Permute , , and using the following modified Cat Map with the corresponding parameters:
where and . The scanning sequence is started from left to right and from top to bottom. After , and are shuffled, we get the permuted image .
2.2.2. Diffusion Stage
Step 1. Transform , , and into three on-dimensional (1D) arrays , , and , respectively, by row-major ordering.
Step 2. Calculate the diffusion matrix according to
where .
Step 3. Calculate , , and by using the following equations:
where , and .
Step 4. Transform , and into three grayscale images with size , and then merge them into one color cipher image with size .
Notice that the permutation processes executed in Step 5 involved parameters , and , which are input (plaint) image data-dependent (cf. Equations (4) and (5)). Notice that, as pre-described in Section 1, the encryption process only includes one round permutation stage and diffusion stage. Conceptually and theoretically, if the encryption process of a cryptosystem is plaintext data-dependent, the associated cryptanalysis is much complicated. Therefore, the corresponding security level of the system is much enhanced, as compared with its data-independent counterpart.
2.3. Image Decryption Algorithm
Similarly, also from [10], the decryption process of the original CIES-UBPRPD consists of the following five steps:
Step 1. Transform , and into three 1D arrays , and , respectively, by row-major ordering.
Step 2. Calculate the diffusion matrix based on Equation (7).
Step 3. Calculate the system parameters by using the following equations:
Step 4. Reconstruct , and according to
where
and . Then transform these three arrays into 2D arrays , and , respectively.
Step 5. Reconstruct , and by using the Cat Maps defined in Equation (1), but now the scanning sequence is started from right to left and from bottom to top.
3. Cryptanalysis
Cryptanalysis is a must procedure for any cryptosystem to be applied to any real applications. We launched a few analyses on CIES-UBPRPD when we learned it from [10]. This section is organized, as follows. Section 3.1 reports the security weaknesses we found and Section 3.2 presents the attack that we used to break a simplified version of the original CIES-UBPRPD.
3.1. Security Weaknesses
3.1.1. Equivalent Classes in Keyspace
After detailed analyses of CIES-UBPRPD, we found that two secret key groups and could play indistinguishable roles to each other, in the original cryptosystem, if the following conditions are satisfied:
For demonstration, here we choose and , which satisfy all of the conditions given in Equation (14). First, we use to encrypt the benchmark image Lena (left, Figure 1) and obtain the corresponding cipher image (middle, Figure 1). Subsequently, we use to decrypt the cipher image and obtain the recovered image (right, Figure 1).
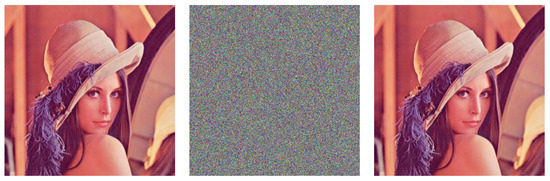
Figure 1.
An Example of the Problem of Equivalent Classes in Keyspace.
The above example implies that one can split the set of all keys into equivalence classes that are based on the conditions given in Equation (14), and the effects of keys belonging to the same equivalence classes will be indistinguishable to each other in CIES-UBPRPD. This property shrinks the effective keyspace from to (since , we can assume , and are of 40-bit long), which is far less than what [10] initially claimed.
3.1.2. Low Sensitivity to the Change of Plaintext
Once the secret key group is chosen, and the summation of pixel values in each channel is given, then the parameters used in the Cat Map are always fixed. Having the same settings means that the permutation mapping will be fixed no matter what the plain image is. Furthermore, there is no cross-channel interaction during permutation and diffusion stages in the original CIES-UBPRPD, which suggests that errors inside one channel will not propagate to the other channels.
Therefore, we can construct two similar plain images where only their R channels are different, but their sum of R channel remains the same. Additionally the corresponding cipher images of these two images will have no differences in G and B channels. This situation violates the diffusion property that a chaotic-map based cryptosystem is looking for.
For demonstration, we modify the standard Lena image by increasing the first-pixel value by 1 and decreasing the second-pixel value also by 1 in the R channel, and then compare the corresponding cipher image with that of the standard Lena image. The results are shown in Figure 2 and Table 1, the details of two widely used measures, number of pixels change rate (NPCR) and unified average changing intensity (UACI), will be given in Section 5.2.5.
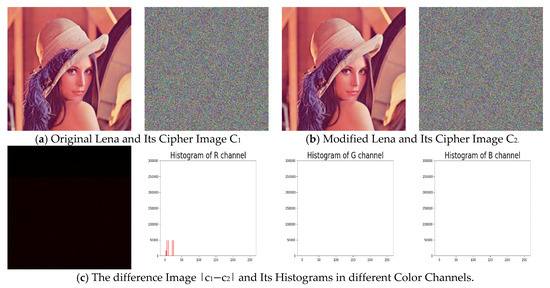
Figure 2.
An Illustration Example of the Low Sensitivity to the Change of Plaintext Image.

Table 1.
Number of pixels change rate (NPCR) and unified average changing intensity (UACI) Values Between the Two Cipher Images Given in Figure 2.
3.2. Chosen-Plaintext Attack
As stated by Bruce Schneier [13], in academic cryptography, a weakness or a break in a scheme is usually defined quite conservatively: it might require impractical amounts of time, memory, or known plaintexts. It also might require the attacker to be able to do things many real-world attackers cannot. For example, the attacker might need to choose particular plaintexts to be encrypted or even to ask for plaintexts to be encrypted while using several keys related to the secret key. Furthermore, it might only reveal a small amount of information, enough to prove the cryptosystem imperfect, but too little to be useful to real-world attackers. Finally, an attack might only apply to a weakened version of cryptographic tools, like a reduced-round block cipher, as a step towards breaking the full system.
Following the principles of cryptanalysis stated above, we now present a chosen-plaintext attack that works if the size of all images equals pixels.
3.2.1. Extraction of the Permutation Matrix
- Construct a special plain image , such that
- Encrypt using CIES-UBPRPD to obtain the corresponding cipher image . We denote the image after permutation stage as (an intermediate product during the execution of the whole encryption process).
- Let us use R channel as an example: select two different positions and , where and construct another special plain image , such thatwhere
- Encrypt to obtain its cipher image . From Section 3.1.2, we knew that and share the same parameters used in ACM; thus, they have the same permutation mapping. Let us denote the first position of different values that occurred in and , following the raster-scan order, as . It means that , such that , which means either or will be moved to the position after performing the permutation stage. This property reveals some information regarding the permutation behavior of CIES-UBPRPD. We define as a tuple of constraints.
- Choose a different or , repeat Step 3 to Step 4 several times and collect all of the produced constraint tuples, and then define the associated collection of constraint tuples as a set .
- Construct a matrix , by setting the chosen positions (a, b) and (x, y), used in Step 2, with different positive integers and all other positions with value 0. For example, assume there are two constraint tuples and in , we can now set , , , and .
- Using the brute-force searching algorithm, denoted as Algorithm 1 in the following, to find and for all of the above chosen plain images, where . In the specifically considered case, all of the images are of size , and are equivalent in the permutation stage. Actually, we do not need to know what exactly is, but only its last eight bits. If Algorithm 1 outputs more than one candidate pair, let us go back to Step 3 to collect more constrained tuples and iterate this step until only one pair is left.
- Making changes to G and B channels, repeat the procedures listed in Step 3 to Step 7 and obtain , , , and , where and .
- Extract , , and by usingWe denote these three values as , and , respectively, for convenience.
3.2.2. Extraction of the Diffusion Matrix
First, we convert above-mentioned into 1D array by row major ordering. We can now obtain the diffusion matrix , according to
where
, and is a 1D array transformed from by row major ordering. Notice that the first element of the diffusion matrix is not used in the cryptosystem, so we can just assign .
So far, we have already extracted , , and the diffusion matrix , which are all the required information for decrypting the cipher image.
3.2.3. Recovering the Original Plain Image
Assume that the cipher image is with the size , and the attacker already extracts , , , and the diffusion matrix according to the analyses given above. The attacker can decrypt using the following steps:
- Transform , , and into three 1D arrays , , and , respectively, in row major ordering.
- Calculate the required parameters, as follows.
- Reconstruct , and according towhereand . Subsequently, transform these three arrays into two-dimensional (2D) arrays , , and , respectively.
- Reconstruct , and by using ACM, but now the scanning sequence is from right to left and from bottom to top.
We rescale the standard Lena to and encrypt it with CIES-UBPRPD, and then crack the cipher image with the proposed chosen-plaintext attack. Figure 3 shows the simulation result.

Figure 3.
(Left) The Original Plaintext Image; (Middle) the Encrypted (or Ciphertext) Image; (Right) the Recovered Image After Launching the Proposed Chosen-plaintext Attack to the Ciphertext Image.
4. Improved CIES-UBPRPD Algorithm
4.1. The Weaknesses of the Original CIES-UBPRPD
We can crack the original CIES-UBPRPD by the chosen-plaintext attack comes from its following weaknesses:
- Misuse of the modulo operation. A value’s remainder divided by 256 equals to the last eight bits in its binary representation. This operation makes the last eight bits of the value more important than the rest parts. This unequal importance in bits gives us a large number of clues for finding the equivalent classes of parameters in CIES-UBPRPD.
- The parameters used in ACM are not very sensitive to the initial plain images. As we pointed out in Section 3.1.2, images that have the same , , and share the same system parameters. Thus, it is vulnerable to differential attacks.
- The diffusion matrix (process) depends only on secret keys, but not the plain images. Once we cracked one cipher image and extracted the diffusion matrix, we can use it to decrypt the other cipher images.
4.2. The Enhanced CIES-UBPRPD
In the enhanced encryption algorithm, instead of the summations of pixel values in each channel, the corresponding SHA-256 hashed values are used as one of the features of a plain image, and this replacement still makes the associated diffusion matrix plaintext-dependent. SHA-256 is a secure cryptographic hash that belongs to SHA-2 families. The hash value served as an external secret key; however, it is dangerous to reuse the same external key when encrypting the same image. Therefore, we add a random number with the precision of as an additional input to SHA-256 each time that we calculate the hash value. In this way, we can use the hashing output as a one-time key.
4.2.1. Secret Key Formulation
There are six secret keys in the proposed enhanced CIES-UBPRPD algorithm, including the external secret key that is generated from SHA-256, the initial value of Chebyshev map, and the four positive integers , , , and , where is a 256-bit binary number, , and . is then divided into 32 8-bit blocks as .
4.2.2. Image Encryption Algorithm
Permutation Stage
- Use as the initial value and iterate the Chebyshev map times, discard the first elements to avoid the harmful effect, and obtain the chaotic sequences , which contain 131 elements. That is,
- Generate another sequence by
- Calculate the parameters by following equations:
- Permute using the following three-dimensional (3D) cat map:where , and is used to indicate the color channel. The scanning sequence is from R channel to B channel, from left to right and from top to bottom. After this step, we get the permuted image .
Diffusion Stage
- Transform , , and into three 1D arrays , and by row-major ordering.
- Use as the new initial value and iterate the Chebyshev map times, discard the first n0 elements and generate another chaotic sequence , which contains elements. That is,
- Calculate the diffusion matrices , , and according to:
- Calculate , and by usingwhere and .
- Transform , and into three grayscale images with size , and then merge them into color cipher image with size .
Image Decryption Algorithm
- Transform , and into three 1D arrays , and respectively, by row-major ordering.
- Calculate the chaotic sequence in the same way as the encryption process.
- Calculate the parameters in the same way as the encryption process.
- Calculate the diffusion matrices , and in the same way as the encryption process.
- Reconstruct , and by usingwhere and . Subsequently, transform these three arrays into 2D arrays , and respectively.
- Reconstruct , and by using 3D cat map in Equation (15), but now the scanning sequence is from B channel to R channel, from right to left, and from bottom to top.
5. Experimental Results
5.1. Verification of Encryption and Decryption Algorithms
We apply the proposed algorithm to several testing images (all ) to demonstrate the algorithm’s performance. The secret keys are set, as follows: and . Figure 4 shows the encryption and decryption results. From the results, we can say that the cipher images are noise-like and irrelevant to the plain images.
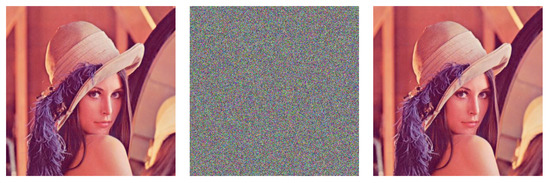

Figure 4.
The Testing Results of the Modified Encryption Scheme: (left) the Plaintext Images; (middle) the Ciphertext Images; and, (right) the Recovered Images.
5.2. Security Analyses
5.2.1. KeySpace Analysis
Keyspace is defined as the cardinality of the set of all possible keys. Having a large keyspace is an important factor for ensuring a cryptosystem to resist the brute force attack. The best-known attack complexity of SHA-256 is in the order of . The range of the rest keys are: and . If has the precision of , the keyspace of the proposed scheme can reach to , which is much larger than and enough to make the brute force attack invalid.
5.2.2. Histogram Analysis
An image’s histogram reflects the distribution of its pixels’ intensity values, which reveals some statistical information of the image to attackers. To against statistical attacks, the histogram of cipher images generated from a secure encryption system should be flat. The distributions of cipher images’ histograms are close to uniformly, indicating that the cipher images are nearly random, and it is rather tough to retrieve any useful statistical information from them, as we can see in Figure 5 and Figure 6.
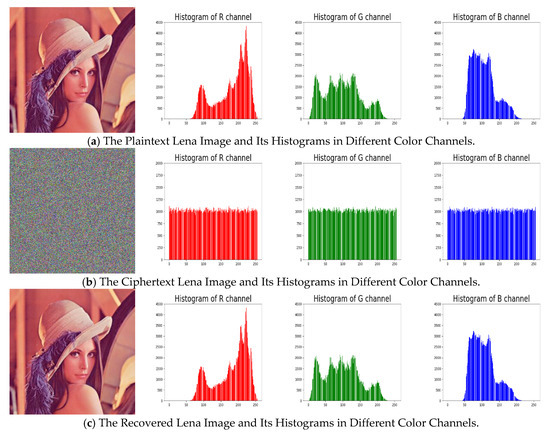
Figure 5.
The Original/Encrypted/Recovered Lena Images and the Corresponding Histograms in Different Color Channels.
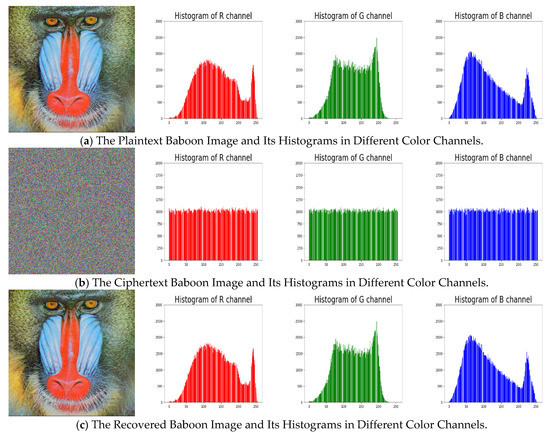
Figure 6.
The Original/Encrypted/Recovered Baboon Images and the Corresponding Histograms in Different Color Channels.
5.2.3. Correlation Analysis
In a natural image (or plain image), two adjacent pixels usually have strong correlation with each other. In contrast, the correlation coefficient of a cipher image should be decreased to zero in order to prevent statistical attacks. We use Equation (16) to measure the correlation of all adjacent pixels at horizontal, vertical, diagonal, and anti-diagonal directions:
Here,
and are the two adjacent pixel values and is the number of pairs of adjacent pixels.
The correlation coefficients of all plain images are close to 1, while those of cipher images are nearly 0, as shown in Table 2. Furthermore, we randomly select 2000 pairs of adjacent pixels at the four specific directions from the R channel of the standard Lena image and its corresponding cipher image, and then plot the scatter diagrams in Figure 7.

Table 2.
Correlation Coefficients of the Plain/Cipher Lena Images.
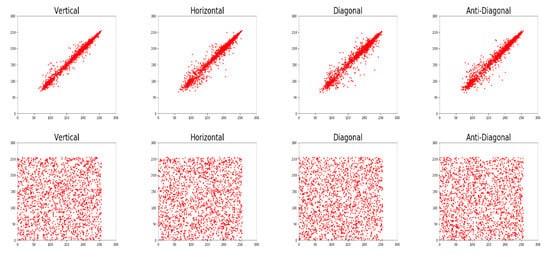
Figure 7.
The Scatter Diagrams of Randomly Select 2000 Pairs of Adjacent Pixels at Four Specific Directions from the R Channel of (top) the Plaintext and (bottom) the Ciphertext Lena images.
5.2.4. Key Sensitivity Analysis
A cryptosystem might suffer from differential attacks if cipher images that are generated from different keys are similar. Thus, a secure encryption algorithm should be highly sensitive to all keys, which means even a tiny change in the secret key will lead to a completely different cipher image.
Figure 4 illustrates the plain, cipher, and decrypted Lena images. We change , and by one bit (i.e., for and 1 for and ) to obtain six new cipher images, and the results are shown in Figure 8. Figure 9 shows the differential results between these six cipher images and the cipher image obtained in Figure 4b. Furthermore, we use the six one-bit difference key groups to decrypt Figure 4b, and the decrypting results are shown in Figure 10.
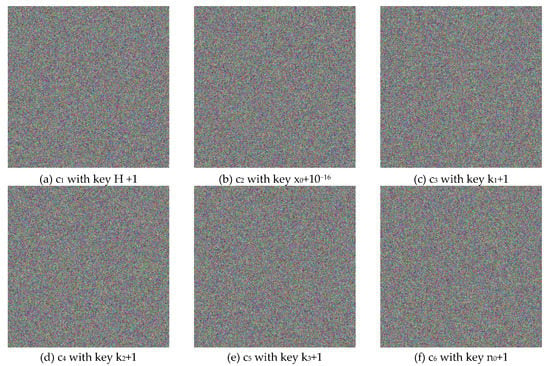
Figure 8.
The Six Ciphertext Images Obtained by Changing Single Bit of Different Secret Key Parameters.
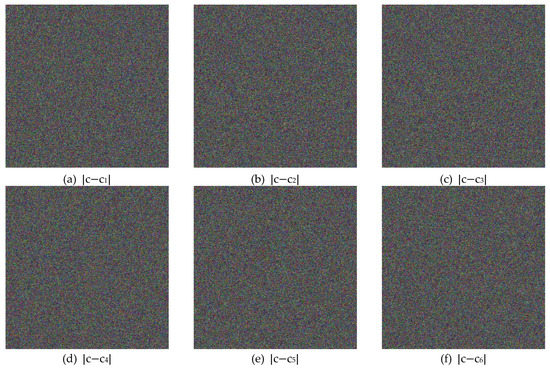
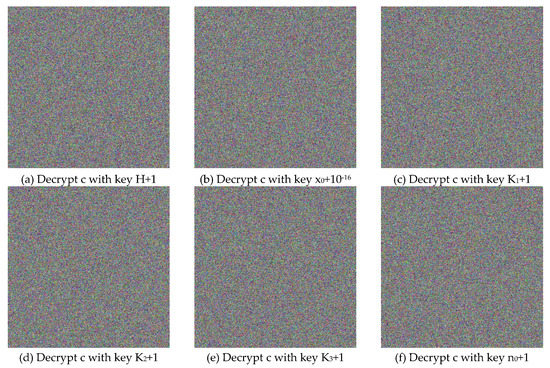
Figure 10.
The Decrypted Images of Figure 4b with the 1-bit Difference Keys, mentioned in Sub-Section 5.2.4.
5.2.5. Plaintext Sensitivity Analysis
Similar to key sensitivity, a secure encryption algorithm should also be very sensitive to plain images. We use NPCR (number of pixels change rate) and UACI (unified average changing intensity) to measure the difference between two cipher images, which are defined, as follows:
where
and and are two cipher images. The theoretical values of NPCR and UACI between two different cipher images are and , respectively.
We evaluate plaintext sensitivity, as follows. First, we randomly select from the keyspace, encrypt the test image and with it to get the cipher image . Second, we randomly select a position in , increasing each channel’s value by 1 in some places to obtain a modified image . Next, we encrypt to obtain a cipher image . Subsequently, calculate the NPCR and UACI values between and . Repeat this process 200 times and list the averaged NPCR and UACI values in Table 3. Both the averaged NPCR and UACI values for all tested images are very close to their theoretical optimal ones, which means the enhanced CIES-UBPRPD algorithm do sensitive to the plain input images, as shown in Table 3.

Table 3.
The Plaintext Sensitivity Analyzing Results, Measured in Terms of Averaged NPCR and UACI Values.
5.3. Robustness Analyses
Cipher images can easily be polluted during the transmission through a public channel, as pointed out by one of the anonymous reviewers; therefore, the robustness of a secure image encryption scheme is also an essential performance merit. For testing the robustness of the proposed image encryption scheme, the noise-adding attack and the partial occlusion attack in the ciphertext domain are investigated.
(a) Noise-adding Attack: the ciphered and the de-ciphered images that are presented in Figure 11 are obtained based on the enhanced CIES-UBPRPD, in which the testing ciphertext images have been contaminated by adding with different degrees of salt-and-pepper noises. For performance analysis, we employ the widely used Peak Signal-to-Noise Ratio (PSNR) to evaluate the algorithm’s restoring ability. That is
where,

Figure 11.
Robustness of the Proposed Approach Against the Noise-adding Attack.
O is the decrypted image obtained from the clean cipher image and D is the decrypted image obtained from the polluted cipher image. Generally, a higher PSNR indicates a better quality or ability of reconstruction. Table 4 shows the PSNRs of the proposed approach against the noise-adding attack.

Table 4.
Robustness of the Proposed Approach Against the Noise-adding Attack, in terms of Peak Signal-to-Noise Ratio (PSNR).
(b) Partial-occlusion Attack. The ciphered and the de-ciphered images that are presented in Figure 12 are obtained based on the enhanced CIES-UBPRPD, in which the testing ciphertext images have been contaminated by occluding some parts of them (i.e., zeroing out those pixel values) that are depicted by the black segments. Similar to the noise-adding attack, PSNR is used to evaluate the proposed approach’s restoring ability against this attack, as shown in Table 5.
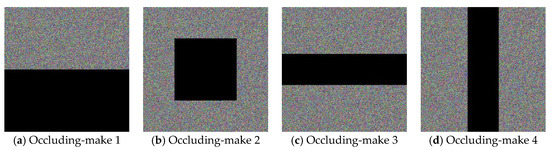

Figure 12.
Robustness of the Proposed Approach Against the Partial-occlusion Attack.

Table 5.
Robustness of the Proposed Approach Against the Partial-occlusion Attack, in terms of PSNR.
6. Discussions and Conclusions
6.1. Discussions
In the past few years, combining both compression and encryption in a single algorithm to reduce the complexity is a new tempting approach for securing data during transmission and storage [14,15,16,17,18]. This new approach aims to extend the functionality of compression algorithms to achieve both compression and encryption simultaneously in a single process without an additional encryption stage. Employing the new combined simultaneous compression-encryption approach highly reduces the required resources for encryption (computational and power resources), according to [15] and [18]. Owing to such an attractive property, lots of works are devoted to this topic [19,20,21,22,23], some of them are also chaotic map based. In [22], we proposed three techniques for enhancing various chaos-based joint compression and encryption (JCAE) schemes. They respectively improved the execution time, compression ratio, and estimation accuracy of three different chaos-based JCAE schemes. However, all of the above-mentioned works are plain image independent. Therefore, for enhancing the security level further, how to design an effective plain Image dependent JCAE scheme is one of our future research directions.
Since steganography can also be utilized to conceal the private information, such as to provide privacy protection of medical images, as pointed out by one of the anonymous reviewers, besides Image Encryption and Decryption, Image Steganography is another worthy of noticing area in the field of Image Security. Interested readers are referred to the following informative writeups, although it is not within the scope of this work [24,25].
6.2. Conclusions
In this paper, we make detailed cryptanalysis on a published chaotic map-based image encryption system, where the encryption process is plaintext Image dependent. We show that some designing weaknesses make the published cryptosystem vulnerable to chosen-plaintext attack, and we then proposed an enhanced algorithm to overcome those weaknesses.
In summary, we use the SHA-256 hash value instead of the sum of each channel as a “plaintext feature”, so the enhanced CIES-UBPRPD has higher plaintext sensitivity than its original counterpart. Moreover, the newly proposed encryption process includes the cross-channel interaction, which can resist the Chosen Plaintext Attack that we launched. Since the SHA-256 hash value also serves as an external key, making the improved Keyspace reaches to 2311, which is larger than the effective Keyspace 2120 of the original CIES-UBPRPD. Besides the security and the robustness, we also take the execution time into account to provide a full performance baseline for comparing the original and the proposed image encryption algorithms, as suggested by one of the anonymous reviewers. Since the calculation amount of the enhanced CIES-UBPRPD is larger than that of the original CIES-UBPRPD, as shown in Table 6, the execution time of the proposed algorithm will be slightly slower than that of its original counterpart. Our implementation is conducted on Intel Core i7-8700 CPU @ 3.2GHz and 32GB RAM with Windows 10 OS, and written in Python.

Table 6.
The Timing Performance Comparison of the Original and the Proposed Approaches.
The value of the proposed algorithm for practical usage in image security is justified, according to the security, the robustness, and the timing performance analyses. Finally, since the currently proposed chosen-plaintext attack can be only effective to all RGB-Colored images of size , finding an attack that can be applied to more general cases is one of the possible future extensions. We humbly hope that this paper will remind researchers to pay more attention when building their chaotic-based image encryption algorithms in the future.
Author Contributions
Conceptualization, C.-Y.L.; methodology, C.-Y.L.; software, C.-Y.L.; validation, C.-Y.L. and J.-L.W.; formal analysis, C.-Y.L.; investigation, C.-Y.L. and J.-L.W.; data curation, C.-Y.L.; writing—original draft preparation, C.-Y.L. and J.-L.W.; writing—review and editing, C.-Y.L. and J.-L.W.; visualization, C.-Y.L. and J.-L.W.; supervision, J.-L.W.; project administration, J.-L.W.; funding acquisition, J.-L.W. All authors have read and agreed to the published version of the manuscript.
Funding
This research was funded by the Ministry of Science and Technology, Taiwan, under the grant number: MOST 108-2221-E-002-103-my3.
Conflicts of Interest
The authors declare no conflict of interest.
References
- Kumari, M.; Gupta, S.; Sardana, P. A Survey of Image Encryption Algorithms. 3D Res. 2017, 8. [Google Scholar] [CrossRef]
- Liu, M.; Zhao, F.; Jiang, X.; Liu, X.; Liu, Y. A Novel Image Encryption Algorithm Based on Plaintext-related Hybrid Modulation Map. J. Internet Technol. 2019, 20, 2141–2155. [Google Scholar]
- Kyamakya, K.; Halang, W.A.; Unger, H.; Chedjou, J.C.; Rulkov, N.C.; Li, Z. (Eds.) Recent Advances in Nonlinear. In Dynamics and Synchronization: Theory and Applications, Studies in Computational Intelligence 254; Springer: Berlin, Heidelberg, 2009. [Google Scholar]
- Fridrich, J. Symmetric Ciphers Based on Two-Dimensional Chaotic Maps. Int. J. Bifurc. Chaos 1998, 8, 1259–1284. [Google Scholar] [CrossRef]
- Priya, R.; Vidhyapriya, R.; Seifedine, K.; Robertas, D.; Tomas, B. An Image Encryption Scheme Based on Block Scrambling, Modified Zigzag Transformation and Key Generation Using Enhanced Logistic-Tent Map. Entropy 2019, 21, 656. [Google Scholar] [CrossRef]
- Zhu, S.; Wang, G.; Zhu, C. A Secure and Fast Image Encryption Scheme based on Double Chaotic S-Boxes. Entropy 2019, 21, 790. [Google Scholar] [CrossRef]
- Liu, H.; Kadir, A.; Sun, X. Chaos-based fast colour image encryption scheme with true random number keys from environmental noise. IET Image Process. 2017, 11, 324–332. [Google Scholar] [CrossRef]
- Li, Q.; Qian, G. A New Image Encryption Algorithm Based on Chaotic Maps. In Proceedings of the 9th International Conference on Signal Processing Systems, Auckland, New Zealand, 27–30 November 2017; pp. 65–69. [Google Scholar]
- Zhu, S.; Zhu, C.; Wang, W. A New Image Encryption Algorithm Based on Chaos and Secure Hash SHA-256. Entropy 2018, 20, 716. [Google Scholar] [CrossRef]
- Huang, L.; Cai, S.; Xiao, M.; Xiong, X. A Simple Chaotic Map-Based Image Encryption System Using Both Plaintext Related Permutation and Diffusion. Entropy 2018, 20, 535. [Google Scholar] [CrossRef]
- Arnold, V.I.; Avez, A. Problèmes Ergodiques de la Mécanique Classique; Benjamin: New York, NY, USA, 1967. (In French) [Google Scholar]
- He, D.; He, C.; Jiang, L.-G.; Zhu, H.-W.; Hu, G.-R. Chaotic characteristics of a one-dimensional iterative map with infinite collapses. IEEE Trans. Circuits Syst. I Regul. Pap. 2001, 48, 900–906. [Google Scholar] [CrossRef]
- Schneier, B. A self-study course in block-cipher cryptanalysis. Cryptologia 2000, 24, 18–33. [Google Scholar] [CrossRef]
- Wu, C.-P.; Kuo, C.-C. Design of integrated multimedia compression and encryption systems. IEEE Trans. Multimed. 2005, 7, 828–839. [Google Scholar] [CrossRef]
- Grangetto, M.; Magli, E.; Olmo, G. Multimedia Selective Encryption by Means of Randomized Arithmetic Coding. IEEE Trans. Multimed. 2006, 8, 905–917. [Google Scholar] [CrossRef]
- Zhou, J.; Liang, Z.; Chen, Y.; Au, O.C. Security Analysis of Multimedia Encryption Schemes Based on Multiple Huffman Table. IEEE Signal Process. Lett. 2007, 14, 201–204. [Google Scholar] [CrossRef]
- Nagaraj, N.; Vaidya, P.G.; Bhat, K.G. Arithmetic coding as a non-linear dynamical system. Commun. Nonlinear Sci. Numer. Simul. 2009, 14, 1013–1020. [Google Scholar] [CrossRef]
- El-Arsh, H.Y.; Mohasseb, Y.Z. A New Light-Weight JPEG2000 Encryption Technique Based on Arithmetic Coding. In Proceedings of the MILCOM 2013—2013 IEEE Military Communications Conference, Institute of Electrical and Electronics Engineers (IEEE). San Diego, CA, USA, 18–20 November 2013; pp. 1844–1849. [Google Scholar]
- Mostafa, M.; Fakhr, M.W. Joint image compression and encryption based on compressed sensing and entropy coding. In Proceedings of the 2017 IEEE 13th International Colloquium on Signal Processing & its Applications (CSPA), Penang, Malaysia, 10–12 March 2017; pp. 129–134. [Google Scholar] [CrossRef]
- Guo, L.; Li, J.; Xue, Q. Joint image compression and encryption algorithm based on SPIHT and crossover operator. In Proceedings of the 2017 14th International Computer Conference on Wavelet Active Media Technology and Information Processing (ICCWAMTIP), Institute of Electrical and Electronics Engineers (IEEE). Chengdu, China, 15–17 December 2017; pp. 185–188. [Google Scholar]
- Shehata, A.E.R.; El-Arsh, H.Y. Lightweight Joint Compression-Encryption-Authentication-Integrity Framework Based on Arithmetic Coding. arXiv 2018, arXiv:1804.04300. [Google Scholar]
- Tsai, C.-J.; Wang, H.-C.; Wu, J.-L. Three Techniques for Enhancing Chaos-Based Joint Compression and Encryption Schemes. Entropy 2019, 21, 40. [Google Scholar] [CrossRef]
- Xie, Y.; Yu, J.; Guo, S.; Ding, Q.; Wang, E. Image Encryption Scheme with Compressed Sensing Based on New Three-Dimensional Chaotic System. Entropy 2019, 21, 819. [Google Scholar] [CrossRef]
- Liao, X.; Guo, S.; Yin, J.; Wang, H.; Li, X.; Sangaiah, A.K. New cubic reference table based image steganography. Multimed. Tools Appl. 2017, 77, 10033–10050. [Google Scholar] [CrossRef]
- Liao, X.; Yin, J.; Guo, S.; Li, X.; Sangaiah, A.K. Medical JPEG image steganography based on preserving inter-block dependencies. Comput. Electr. Eng. 2018, 67, 320–329. [Google Scholar] [CrossRef]
© 2020 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).