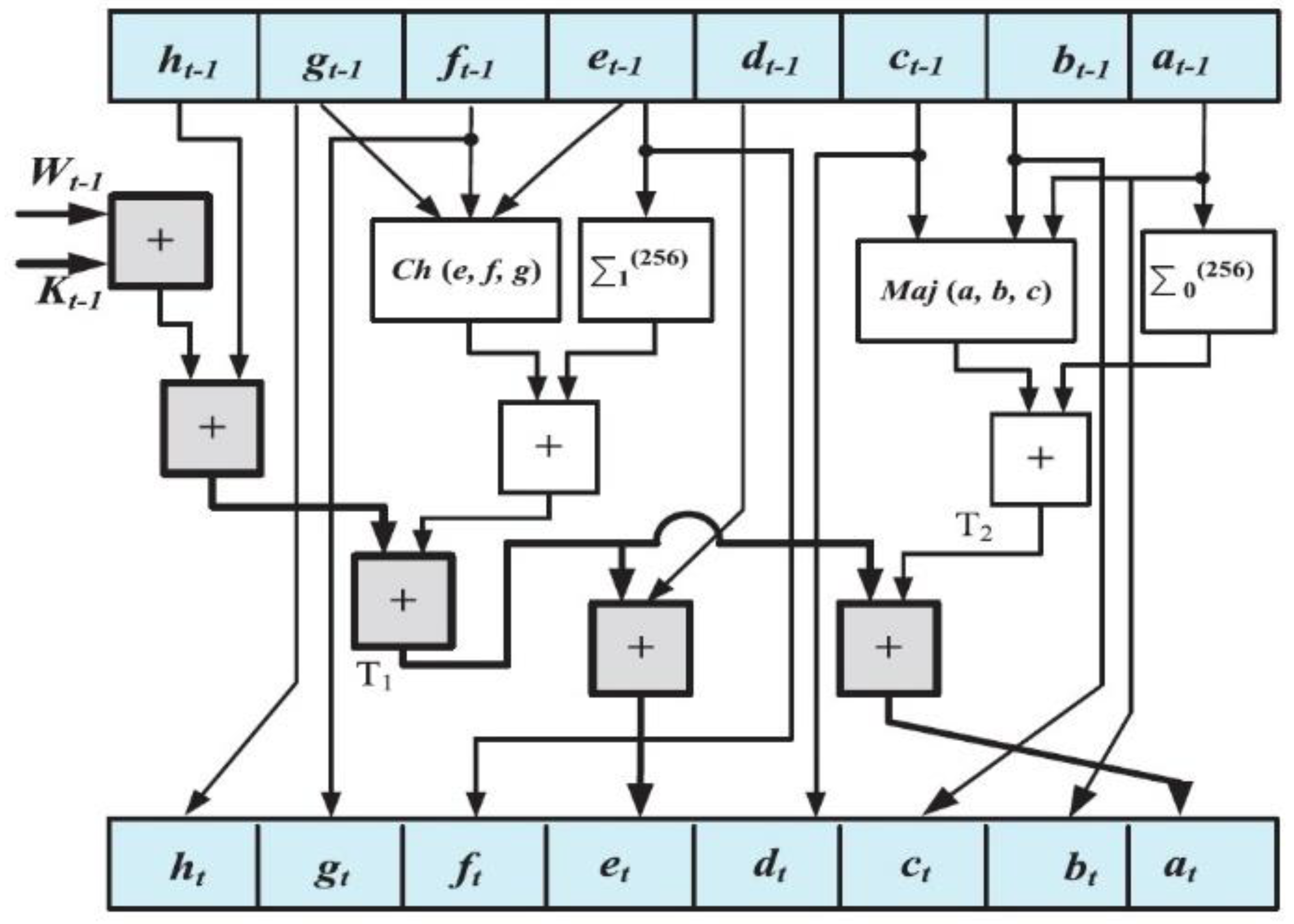
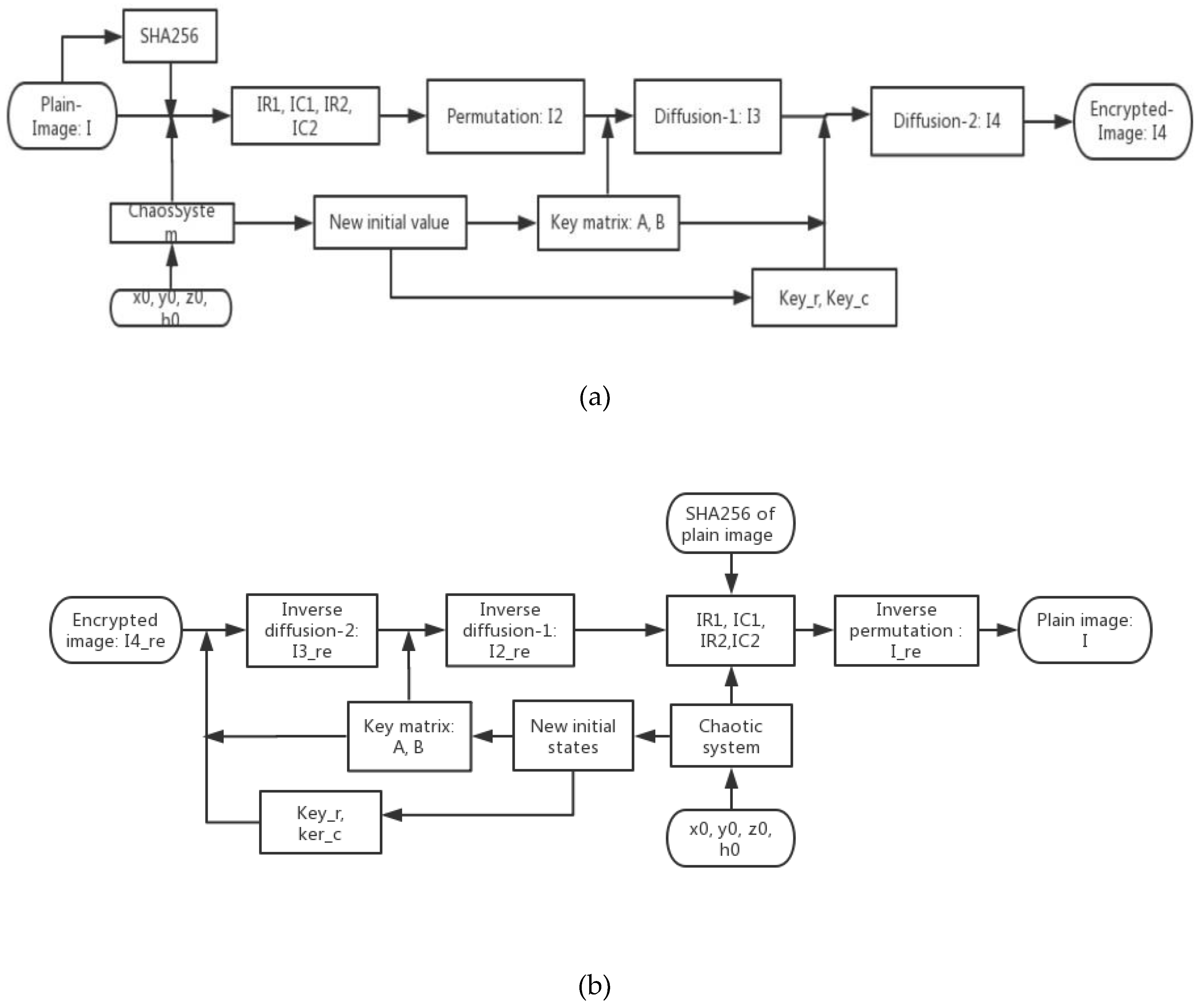
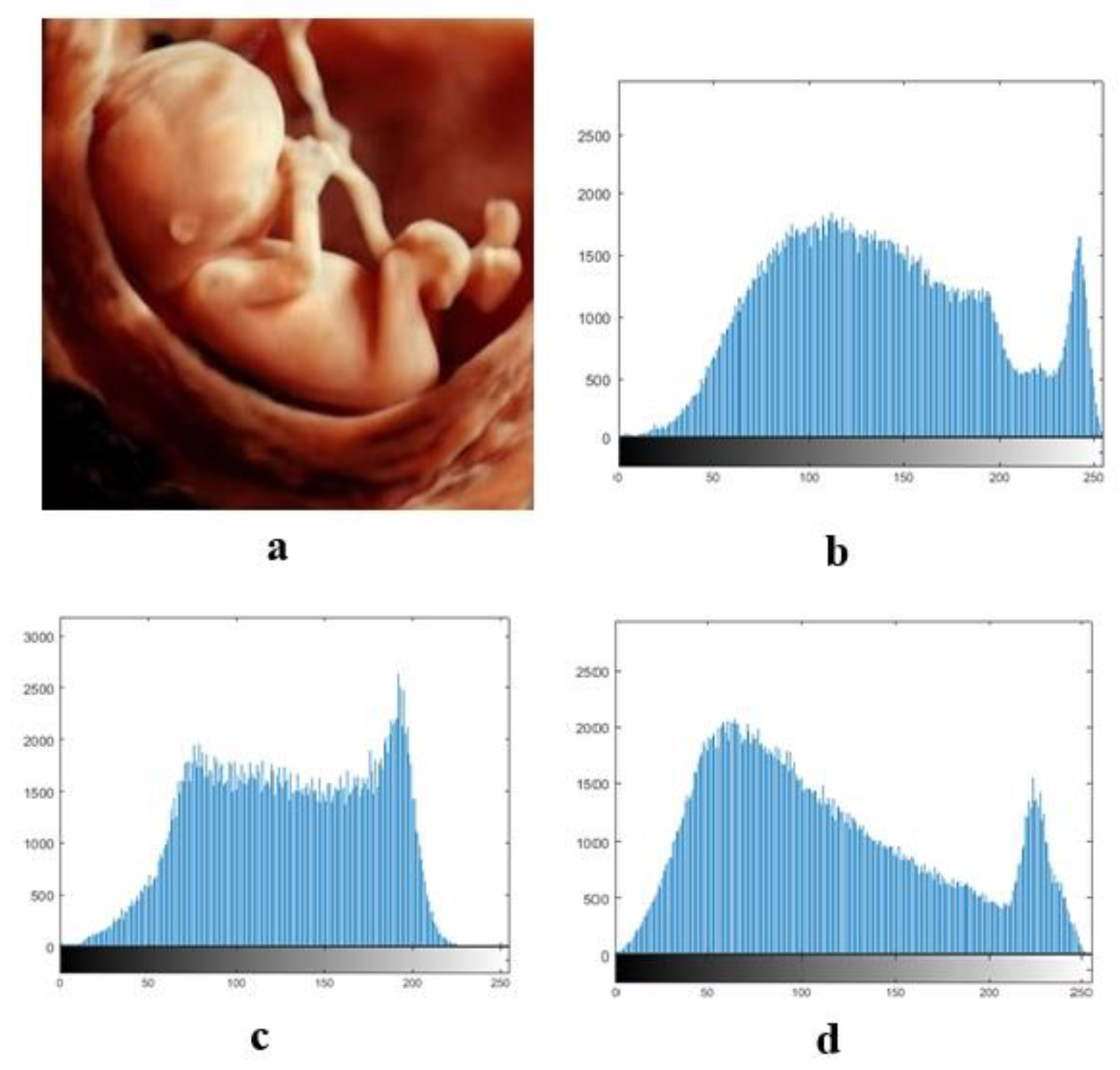
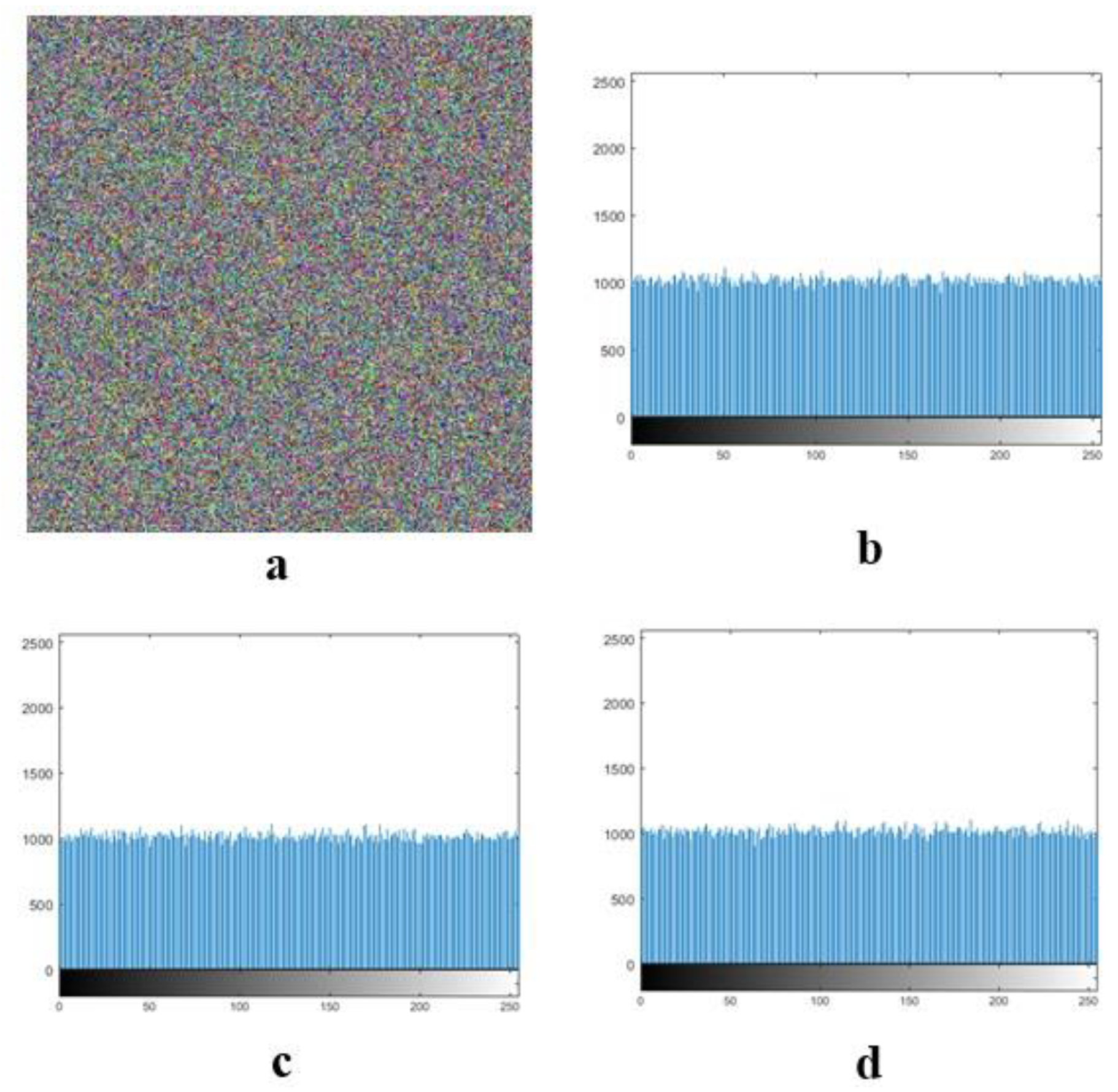
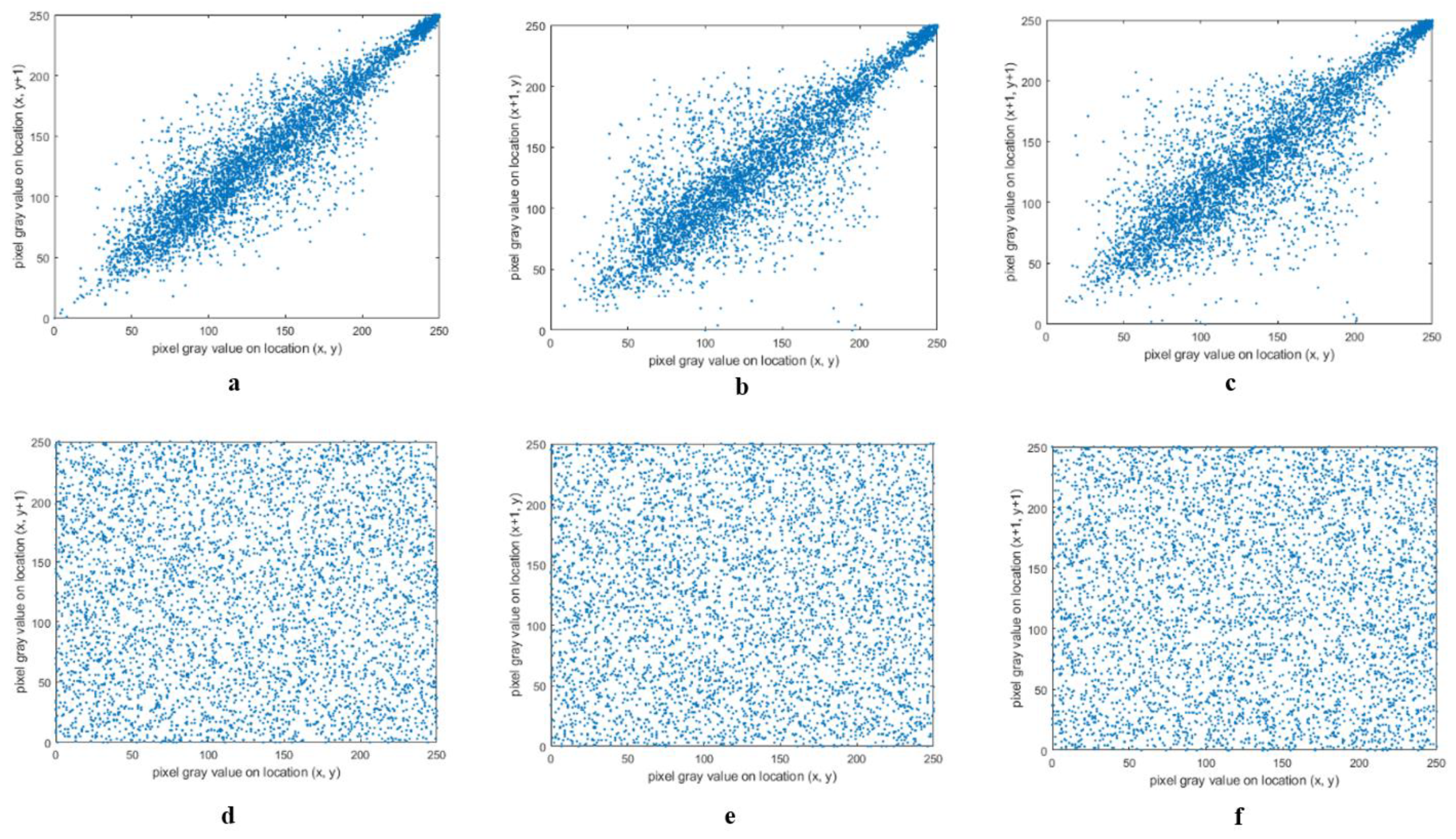
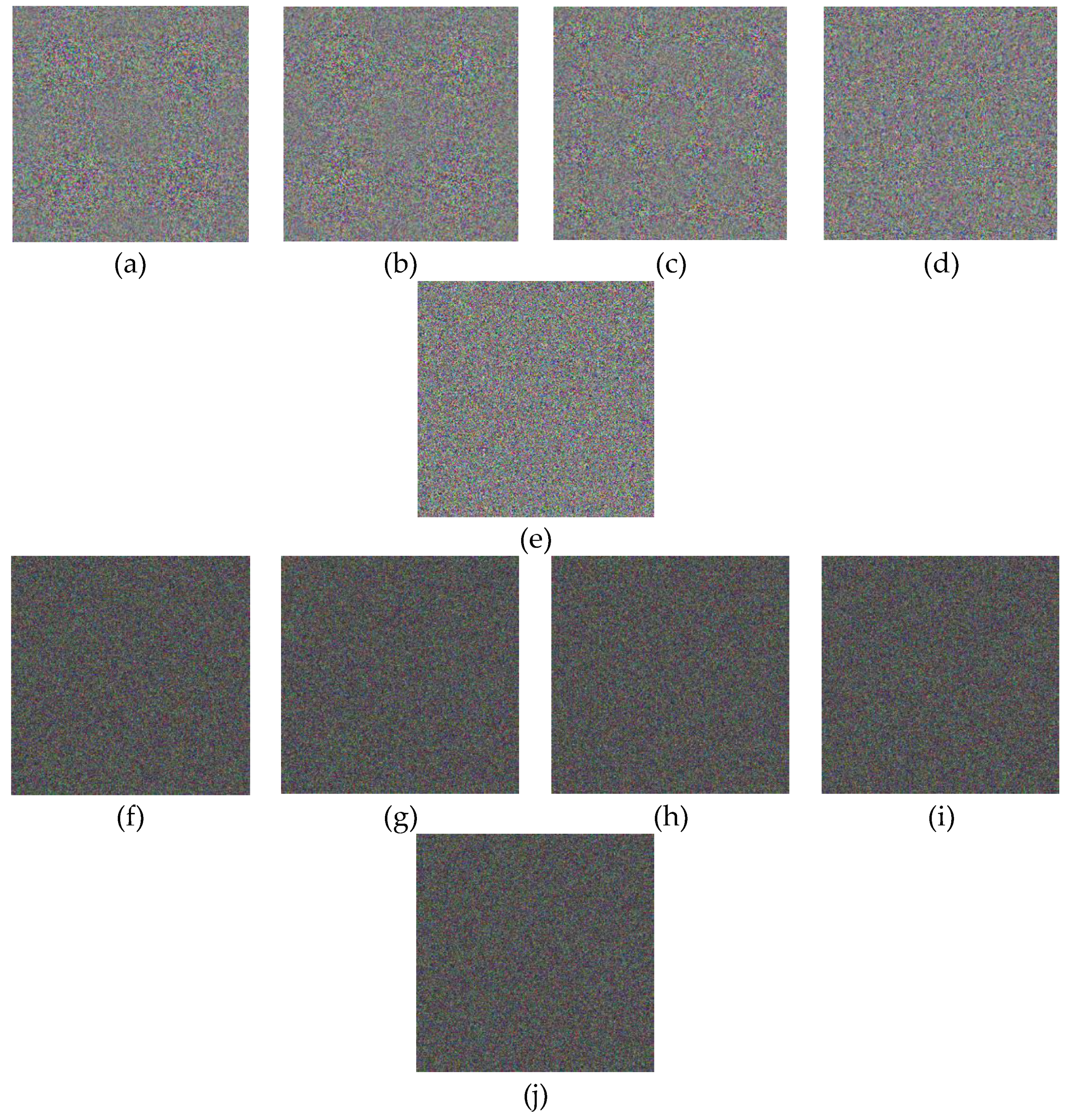
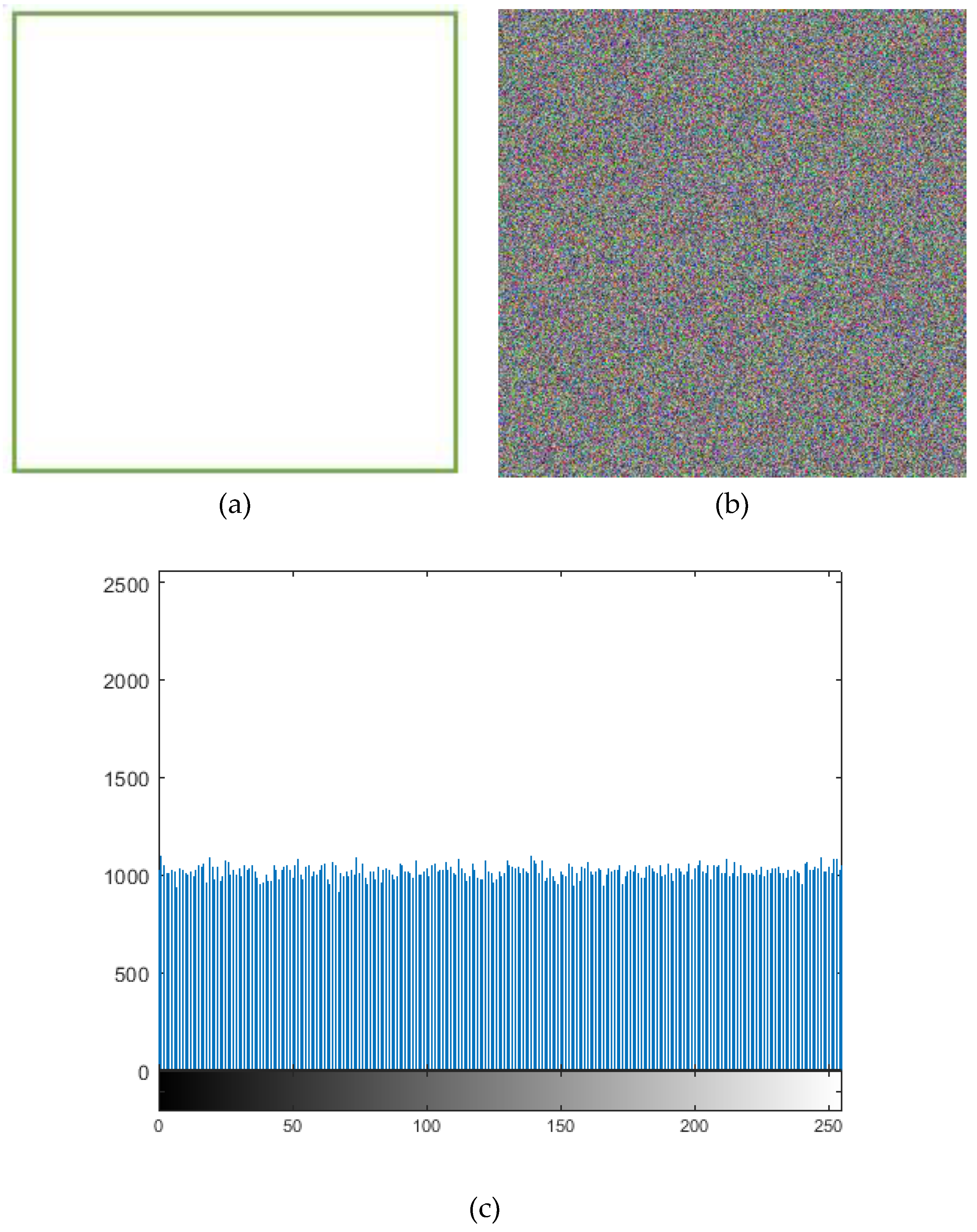
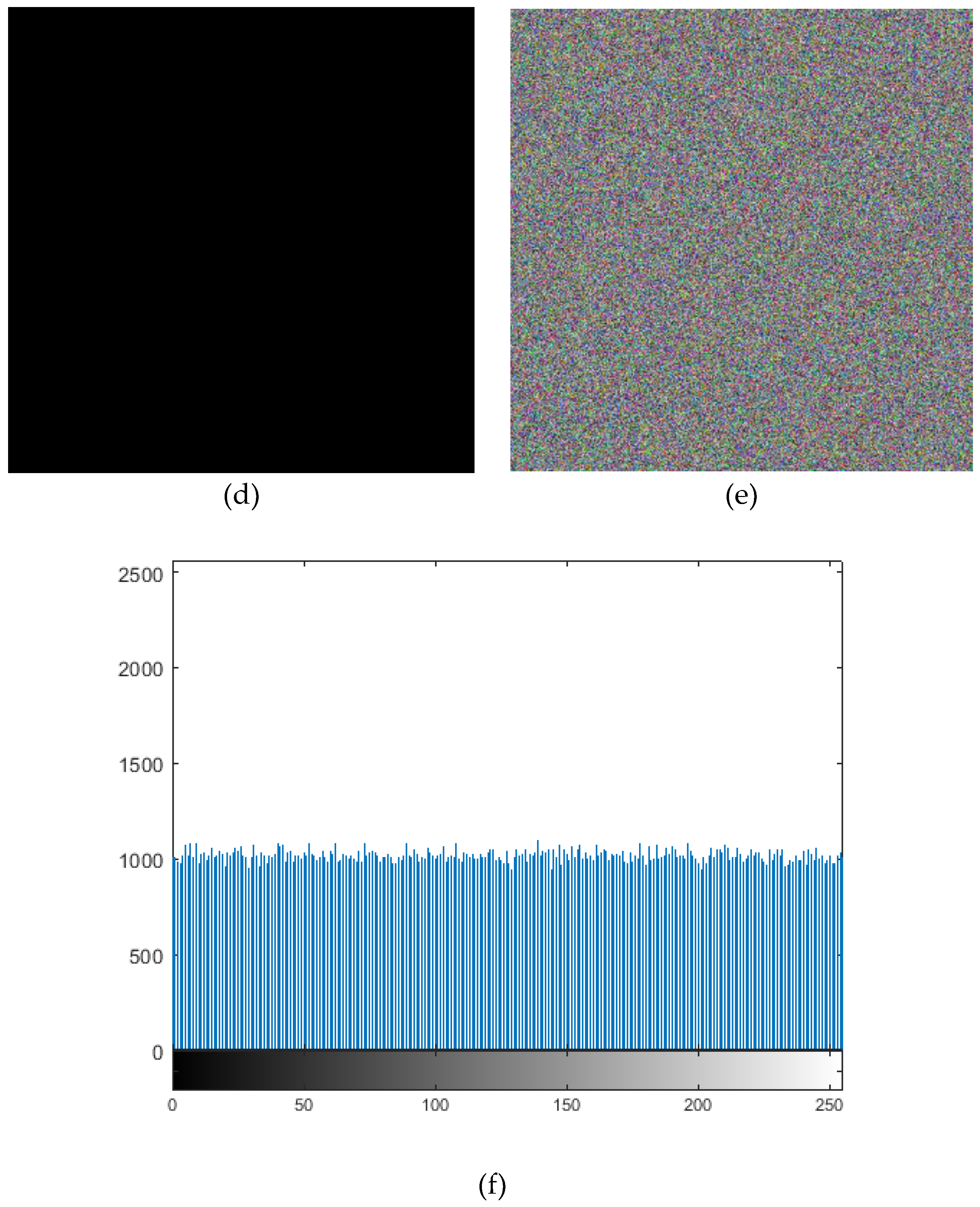
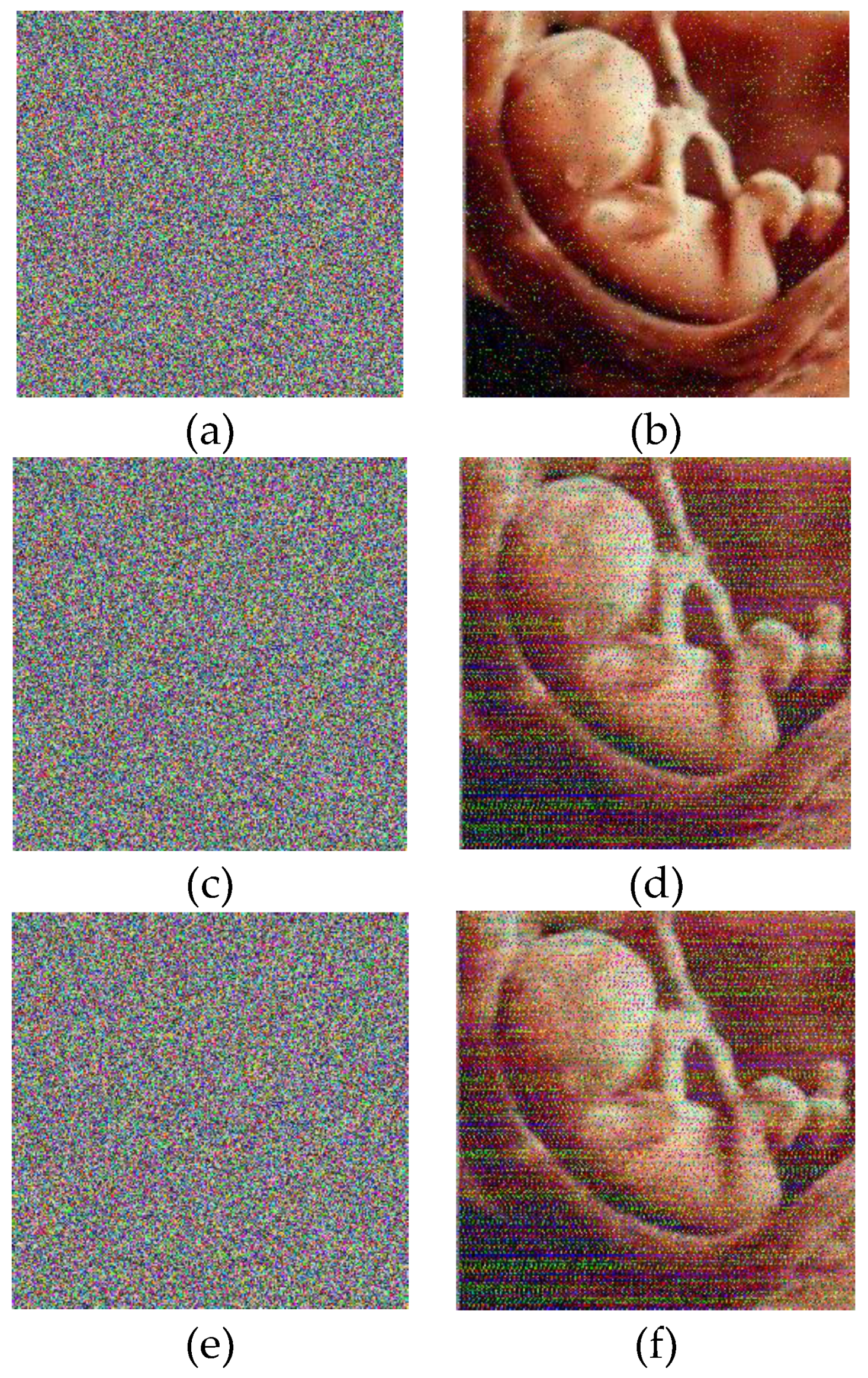
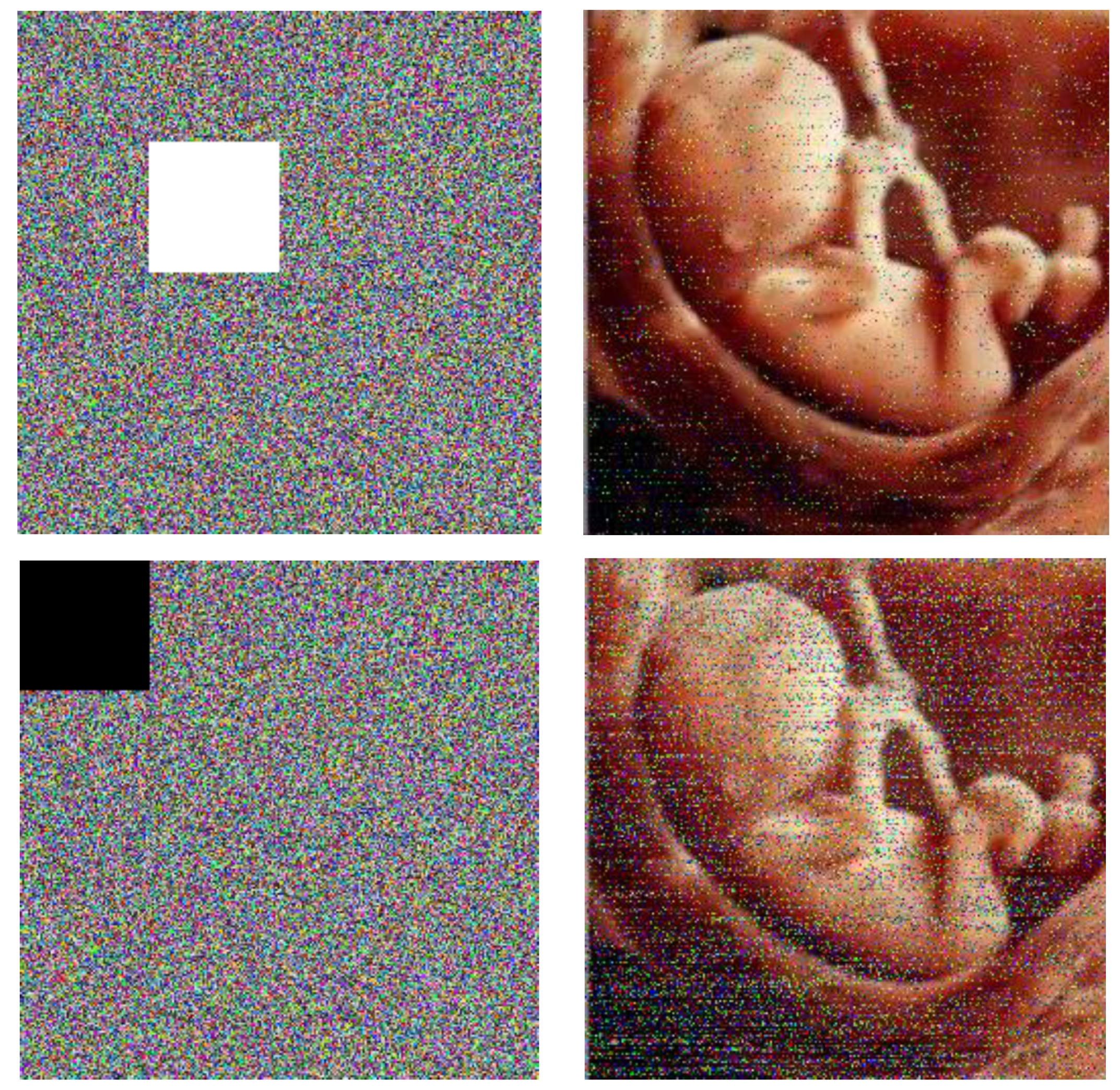
The confidentiality of patient information is one of the vital security aspects of electronic health services. For example, the confidentiality of patients’ medical records is necessary. In addition, the methods of protection should be improved due to the rapid advancement of technologies for accessing the personal information of individuals. The security and privacy of medical image transferring is one of the acute subjects that should be seriously considered in telecare medical information systems (TMIS). In the past years, medical images were grayscale, but today, color images have entered the medical arena, and they can show more accurate information about body conditions. Color images that are acquired by new scanners using the Medipix3RX chip technology are very important in the medical arena. Image-data transferring from a position to another via an unsafe network are usually determined in qualifications of privacy, validity, totality, and confidentiality. Therefore, more significance should be given to the security of the sensitive data that are included in medical images by DICOM (digital imaging communication in medicine). In this textuality, many problems using various cryptographic techniques have been proposed in the literature to overcome this problem [
1,
2,
3,
4]. In their paper, Abdel-Nabi and Al-Haj proposed a hybrid encryption algorithm using watermarking that offers high embedding capabilities for medical images. The proposed algorithm is a combination of reversible data-caching techniques with standard encryption techniques for ensuring the security requirements for transferred and stored medical images [
5]. In their paper, Abdmouleh et al. presented a partial cryptographic approach that was based on the digital wavelet transform (DWT) and was JPEG2000 compliant to ensure the safe transfer and storage of medical images [
6]. Lakshmi et al. presented a similar algorithm using a discrete wavelet transform (DWT), with the difference being that they used a fuzzy chaotic map for the watermarking [
7]. In their paper, Cao et al. presented a medical image encryption algorithm using edge maps that were derived from a source image. The algorithm consists of three parts: Bit-plane decomposition, a random-sequence generator, and permutation [
8]. Ismail et al. presented the double-humped (DH) logistic map to produce pseudorandom numbers keys (PRNG) in their paper. The generalized parameter that is added to the map provides more control on the map chaotic range [
9]. Jeong et al. proposed a new medical image encrypting method using a 2D chaotic map and C-MLCA in their article. The 2D chaotic map is a construction with self- guarding attributes, which moves the location of the pixel and encrypts the image [
10]. In their method, Ke et al. offered an encryption algorithm that was based on reversible data using the MSB-based prediction [
11]. In their study, Nematzadeh et al. proposed an encryption method for medical images based on a hybrid pattern of the improved genetic algorithm (IGA) and paired map lattices. First, the assumed way employs a paired map lattice to produce a some of secure cipher-images as a primitive population of the IGA. Then, it exerts the IGA to both increase the entropy of the cipher images and reduce the algorithm’s calculations time [
12]. In their paper, Singh et al. proposed a medical image encryption scheme algorithm using the improved ElGamal encryption technique. Their proposed method made a new contribution since the necessity for separate calculations for encoding plain messages to elliptic curve coordinates was removed. The algorithm using the improved version of the ElGamal encryption scheme is designed to encrypt medical images [
13]. Suganya and Amudha’s proposed method uses two encryption algorithms, namely, RC4 and AES, which are the stream cipher and block cipher algorithms, respectively. The main objective of this method is to provide integrity control for medical images, although they are encrypted. Experimental security analysis is conducted using 8-bit ultrasound images and 16-bit positron emission tomography (PET) images [
14]. The chaos systems that have become popular today have been used in many types of research. For example: Liang and Qi investigated mechanical analysis of generates the Chen chaotic system to the extensile Kolmogorov system. In Hu et al.’s research, the Chen chaotic system is designed as a pseudorandom sequence producer. In their research, Wang et al. used the memristor chaotic systems (MCSs). Gong et al. provided a method for image encryption based on hyper-chaotic system and discrete fractional random transform. Michail et al.’s research was based on chaotic systems and hash functions to implement totally self-checking (TSC). James et al., in their research based on chaotic systems and hash functions, discussed the performance of SHA-3 256- bit core. Ahmad and Das, based on chaos and hash algorithms, discussed Hardware performance analysis of SHA-256 and SHA-512 algorithms on FPGAs. In their research, Xu et al. improved chaotic cryptosystem based on circular bit shift and XOR operations. Pareek and Patidar, in their research, designed medical image protection based on genetic algorithm and chaotic system. Hua et al., in their study, designed medical image encryption using hash algorithm high-speed scrambling [
15,
16,
17,
18,
19,
20,
21,
22,
23,
24]. Also, Chai et al. designed a color image encryption method based on dynamic DNA encryption and chaotic system [
25] and Ma et al. provided a new method of plaintext-related and chaos-based image encryption [
26]. Niyat et al. offered an image encryption algorithm with the rule of cellular automata (CA). CA is a self- establishing construction with a group of cells in which any cell is updated based on certain regulation that are to depend on a limited number of neighboring cells [
27]. Chen et al. designed an image encryption method based on hyperchaotic system in the turner transfigure domain. The RGB ingredients of the main color image are encrypted into 1D circulation. [
28]. The method in [
5] focused on the embedding capacity, but no results are given with respect to other criteria, such as the correlation coefficients entropy, the number of pixel change rate (NPCR), or the uniform average change intensity (UACI). The methods in [
6,
7] are based on the digital wavelet transform (DWT) and allow for safe transport, but they do not provide suitable results with respect to the correlation coefficients. The results that were obtained in [
8] are only suitable for the NPCR, and other values are not suitable. In the method in [
9], the values that are obtained are appropriate, but they are only suitable for grayscale images. The results of the methods in [
10,
11,
12] are only suitable with respect to their correlation coefficients, but there are no improvements with respect other criteria. The results that are obtained in [
13,
14] are only suitable with respect to entropy. The methods in [
27,
28] perform well in color images encrypting and can be used to encrypt medical images. Nevertheless, our method is better in terms of the correlation coefficients, the entropy, the NPCR, and the UACI.