Artificial Noise Injection and Its Power Loading Methods for Secure Space-Time Line Coded Systems
Abstract
1. Introduction
2. Proposed Secure STLC with AN
- : a secure STLC mode with AN,
- : a jamming mode without data transmission.
3. Power Control for AN
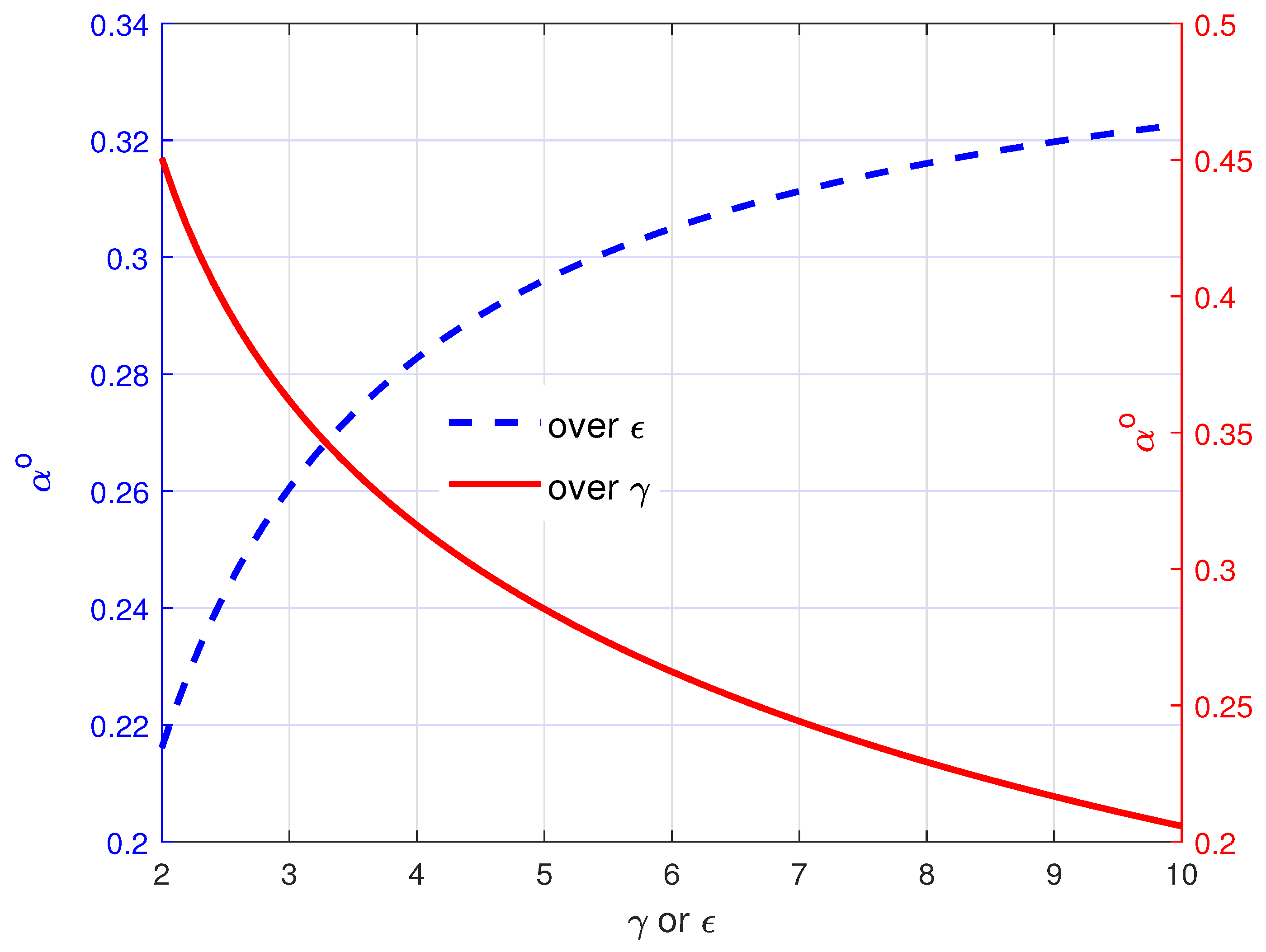
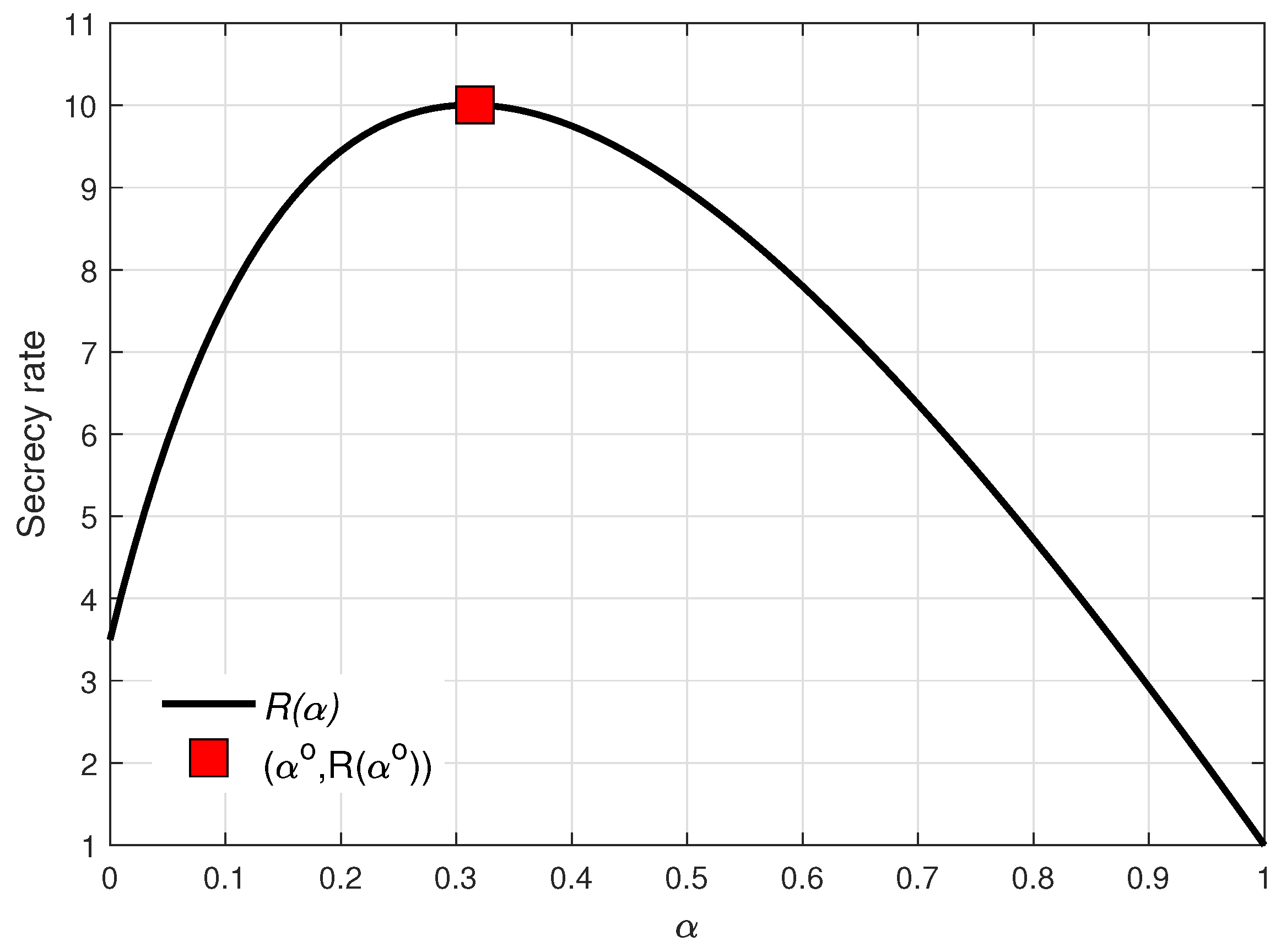
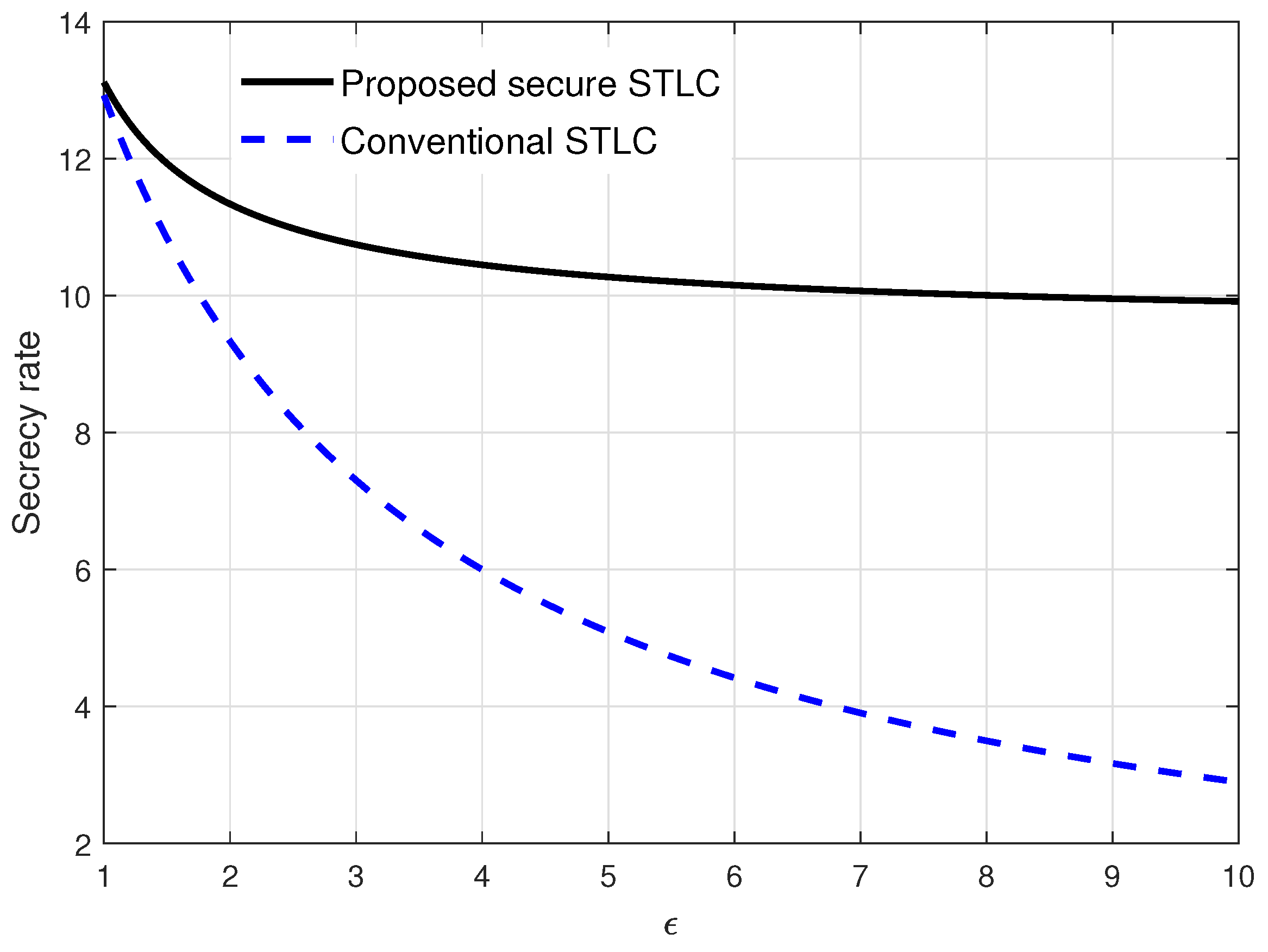
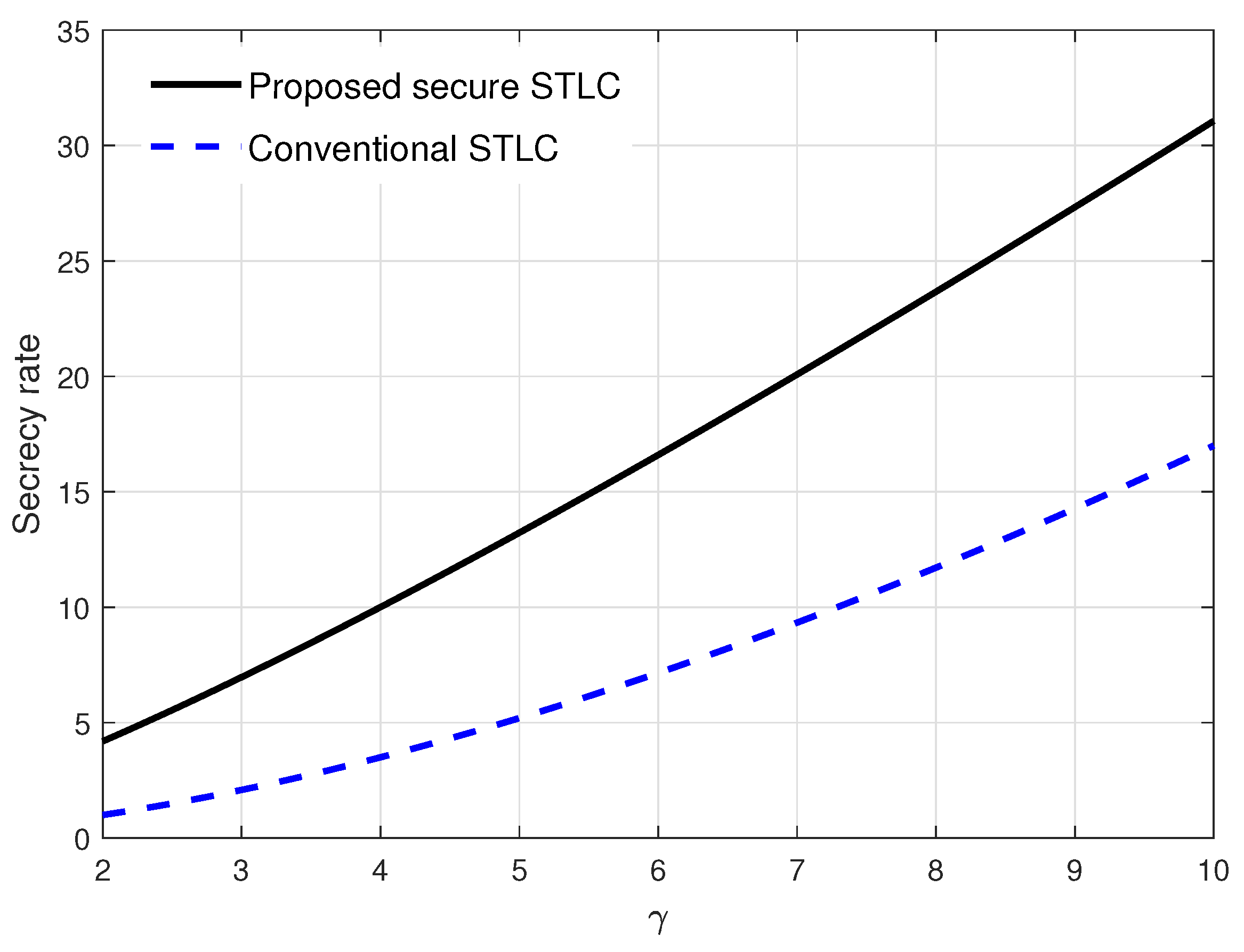
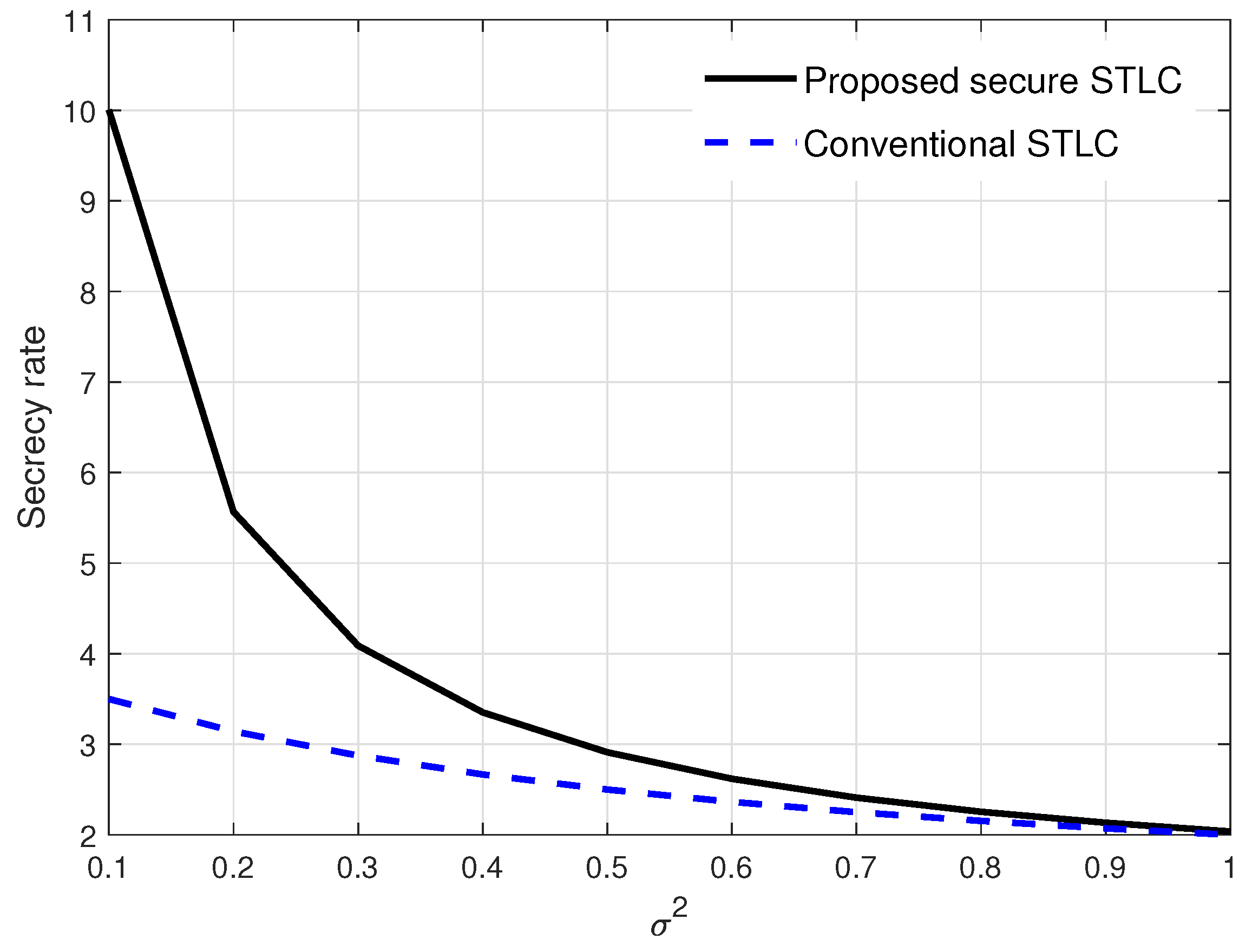
4. Numerical Results
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Wyner, A.D. The wire-tap channel. Bell Syst. Tech. J. 1975, 54, 1355–1387. [Google Scholar] [CrossRef]
- Leung-Yan-Cheong, S.K.; Hellman, M.E. The Gaussian Wire-Tap Channel. IEEE Trans. Inf. Theory 1978, IT-24, 451–456. [Google Scholar] [CrossRef]
- Liu, Y.; Chen, H.H.; Wang, L. Physical layer security for next generation wireless networks: Theories, technologies, and challenges. IEEE Commun. Surv. Tutor. 2017, 19, 347–376. [Google Scholar] [CrossRef]
- Zhang, J.; Yuen, C.; Wen, C.K.; Jin, S.; Wong, K.K.; Zhu, H. Large system secrecy rate analysis for SWIPT MIMO wiretap channels. IEEE Trans. Inf. Forensics Secur. 2016, 11, 74–85. [Google Scholar] [CrossRef]
- Guo, C.; Liao, B.; Feng, D.; He, C.; Ma, X. Minimum secrecy throughput maximization in wireless powered secure communications. IEEE Trans. Veh. Technol. 2018, 67, 2571–2581. [Google Scholar] [CrossRef]
- Zhu, J.; Schober, R.; Bhargava, V.K. Linear precoding of data and artificial noise in secure massive MIMO systems. IEEE Trans. Wirel. Commun. 2016, 15, 2245–2261. [Google Scholar] [CrossRef]
- Wu, Y.; Schober, R.; Ng, D.W.K.; Xiao, C.; Caire, G. Secure massive MIMO transmission with an active eavesdropper. IEEE Trans. Inf. Theory 2016, 62, 3880–3900. [Google Scholar] [CrossRef]
- Zhu, Y.; Wang, L.; Wong, K.K.; Heath, R.W. Secure communications in millimeter wave Ad Hoc networks. IEEE Trans. Wirel. Commun. 2017, 16, 3205–3217. [Google Scholar] [CrossRef]
- Zhu, Y.; Zheng, G.; Fitch, M. Secrecy rate analysis of UAV-enabled mmWave networks using Matérn hardcore point processes. IEEE J. Select. Areas Commun. 2018, 36, 1397–1409. [Google Scholar] [CrossRef]
- Li, A.; Wu, Q.; Zhang, R. UAV-enabled cooperative jamming for improving secrecy of ground wiretap channel. IEEE Wirel. Commun. Lett. 2019, 8, 181–184. [Google Scholar] [CrossRef]
- Kang, H.; Joung, J.; Ahn, J.; Kang, J. Secrecy-aware altitude optimization for quasi-static UAV base station without eavesdropper location information. IEEE Commun. Lett. 2019, 23, 851–854. [Google Scholar] [CrossRef]
- Tang, J.; Chen, G.; Coon, J.P. Secrecy performance analysis of wireless communications in the presence of UAV jammer and randomly located UAV eavesdroppers. IEEE Trans. Inf. Forensics Secur. 2019. (early access article). [Google Scholar] [CrossRef]
- Tseng, S.; Chen, Y.; Chiu, P.; Chi, H. Jamming resilient cross-layer resource allocation in uplink HARQ-based SIMO OFDMA video transmission systems. IEEE Access 2017, 5, 24908–24919. [Google Scholar] [CrossRef]
- Dou, Z.; Si, G.; Lin, Y.; Wang, M. An adaptive resource allocation model with anti-jamming in IoT network. IEEE Access 2019, 5, 1–9. [Google Scholar] [CrossRef]
- Geraci, G.; Al-nahari, A.Y.; Yuan, J.; Collings, I.B. Linear precoding for broadcast channels with confidential messages under transmit-side channel correlation. IEEE Commun. Lett. 2013, 17, 1164–1167. [Google Scholar] [CrossRef]
- Zhang, J.; Yuen, C.; Wen, C.K.; Jin, S.; Gao, X. Ergodic secrecy sum-rate for multiuser downlink transmission via regularized channel inversion: Large system analysis. IEEE Commun. Lett. 2014, 18, 1627–1630. [Google Scholar] [CrossRef]
- Fakoorian, S.A.A.; Swindlehurst, A.L. MIMO interference channel with confidential messages: Achievable secrecy rates and precoder design. IEEE Trans. Inf. Forensics Secur. 2011, 6, 640–649. [Google Scholar] [CrossRef]
- Zheng, G.; Choo, L.C.; Wong, K.K. Optimal cooperative jamming to enhance physical layer security using relays. IEEE Trans. Signal Process. 2011, 59, 1317–1322. [Google Scholar] [CrossRef]
- Chen, X.; Zhong, C.; Yuen, C.; Chen, H.H. Multi-antenna relay aided wireless physical layer security. IEEE Commun. Mag. 2015, 53, 40–46. [Google Scholar] [CrossRef]
- Tran Tin, P.; The Hung, D.; Nguyen, T.N.; Duy, T.T.; Voznak, M. Secrecy performance enhancement for underlay cognitive radio networks employing cooperative multi-hop transmission with and without presence of hardware impairments. Entropy 2019, 21, 217. [Google Scholar] [CrossRef]
- Thangaraj, A.; Dihidar, S.; Calderbank, A.; McLaughlin, S.; Merolla, J.M. Applications of LDPC codes to the wiretap channel. IEEE Trans. Inf. Theory 2007, 53, 2933–2945. [Google Scholar] [CrossRef]
- Andersson, M.; Schaefer, R.; Oechtering, T.; Skoglund, M. Polar coding for bidirectional broadcast channels with common and confidential messages. IEEE J. Sel. Areas Commun. 2013, 31, 1901–1908. [Google Scholar] [CrossRef]
- He, X.; Yener, A. Providing secrecy with structured codes: Two-user Gaussian channels. IEEE Trans. Inf. Theory 2014, 60, 2121–2138. [Google Scholar] [CrossRef]
- Negi, R.; Goel, S. Secret communication using artificial noise. In Proceedings of the IEEE 62nd Vehicular Technology Conference, Dallas, TX, USA, 28 September 2005; pp. 1906–1910. [Google Scholar]
- Goel, S.; Negi, R. Guaranteeing secrecy using artificial noise. IEEE Trans. Commun. 2008, 7, 2180–2189. [Google Scholar] [CrossRef]
- Mukherjee, A.; Swindlehurst, A.L. Robust beamforming for security in MIMO wiretap channels with imperfect CSI. IEEE Trans. Signal Process. 2011, 59, 351–361. [Google Scholar] [CrossRef]
- Allen, T.; Tajer, A.; Al-Dhahir, N. Secure Alamouti MAC transmissions. IEEE Trans. Wirel. Commun. 2017, 16, 3674–3687. [Google Scholar] [CrossRef]
- Fakoorian, S.A.A.; Jafarkhani, H.; Swindlehurst, A.L. Secure space-time block coding via artificial noise alignment. In Proceedings of the Conference Record of the Forty Fifth Asilomar Conference on Signals, Systems and Computers (ASILOMAR), Pacific Grove, CA, USA, 6–9 November 2011; pp. 651–655. [Google Scholar]
- Wang, H.M.; Wang, C.; Ng, D.W.K. Artificial noise assisted secure transmission under training and feedback. IEEE Trans. Signal Process. 2015, 63, 6285–6298. [Google Scholar] [CrossRef]
- Hyadi, A.; Rezki, Z.; Alouini, M. An overview of physical layer security in wireless communication systems with CSIT uncertainty. IEEE Access 2016, 4, 6121–6132. [Google Scholar] [CrossRef]
- Joung, J. Space-Time Line Code. IEEE Access 2018, 6, 1023–1041. [Google Scholar] [CrossRef]
- Alamouti, S.M. A simple transmitter diversity scheme for wireless communications. IEEE J. Sel. Areas Commun. 1998, 16, 1451–1458. [Google Scholar] [CrossRef]
- Joung, J. Space-Time Line Code for Massive MIMO and Multiuser Systems with Antenna Allocation. IEEE Access 2018, 6, 962–979. [Google Scholar] [CrossRef]
- Joung, J.; Jeong, E.R. Multiuser space-time line code with optimal and suboptimal power allocation methods. IEEE Access 2018, 6, 51766–51775. [Google Scholar] [CrossRef]
- Joung, J. Energy efficient space-time line coded regenerative two-way relay under per-antenna power constraints. IEEE Access 2018, 6, 47026–47035. [Google Scholar] [CrossRef]
- Joung, J.; Choi, J. Space-time line code with power allocation for regenerative two-way relay systems. IEEE Trans. Veh. Technol. 2019. (early access article). [Google Scholar] [CrossRef]
- Joung, J.; Choi, J. Uneven power amplifier shuffling for space-time line code (STLC) systems. IEEE Access 2018, 6, 58491–58500. [Google Scholar] [CrossRef]
- Joung, J.; Jung, B.C. Machine learning based blind decoding for space-time line code (STLC) systems. IEEE Trans. Veh. Technol. 2019. (early access article). [Google Scholar] [CrossRef]
- Cordeschi, N.; Amendola, D.; Shojafar, M.; Enzo, B. Distributed and adaptive resource management in cloud-assisted cognitive radio vehicular networks with hard reliability guarantees. Veh. Commun. 2015, 2, 1–12. [Google Scholar] [CrossRef]

© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Joung, J.; Choi, J.; Jung, B.C.; Yu, S. Artificial Noise Injection and Its Power Loading Methods for Secure Space-Time Line Coded Systems. Entropy 2019, 21, 515. https://doi.org/10.3390/e21050515
Joung J, Choi J, Jung BC, Yu S. Artificial Noise Injection and Its Power Loading Methods for Secure Space-Time Line Coded Systems. Entropy. 2019; 21(5):515. https://doi.org/10.3390/e21050515
Chicago/Turabian StyleJoung, Jingon, Jihoon Choi, Bang Chul Jung, and Sungwook Yu. 2019. "Artificial Noise Injection and Its Power Loading Methods for Secure Space-Time Line Coded Systems" Entropy 21, no. 5: 515. https://doi.org/10.3390/e21050515
APA StyleJoung, J., Choi, J., Jung, B. C., & Yu, S. (2019). Artificial Noise Injection and Its Power Loading Methods for Secure Space-Time Line Coded Systems. Entropy, 21(5), 515. https://doi.org/10.3390/e21050515






