Secure Transmission in mmWave Wiretap Channels: On Sector Guard Zone and Blockages
Abstract
:1. Introduction
- According to the characteristics of mmWave beam pattern, both the main lobe and side lobe are taken into consideration. Specifically, a sector secrecy guard zone model is considered to achieve theoretical design and analysis. Depending on the locations of eavesdroppers detected by a transmitter, an adaptive transmission scheme is proposed which chooses two types of transmission strategies adaptively. The fist-type is direct transmission when there exists no eavesdroppers in the sector secrecy guard zone and the second-type is the AN assisted transmission when one or more eavesdroppers in the sector secrecy guard zone.
- Stochastic geometry is adopted in proposed mmWave wiretap network to characterize the random spatial locations of eavesdroppers. The closed-form expressions of secrecy outage probability (SOP),connection outage probability (COP) and secrecy throughput are derived in the proposed scheme. In addition, we provide a further insight of the system parameters, i.e., transmit power, power allocation factor, secrecy guard zone radius and central angle, blockage density, antenna gain, and the intensity of the eavesdroppers into secrecy performance.
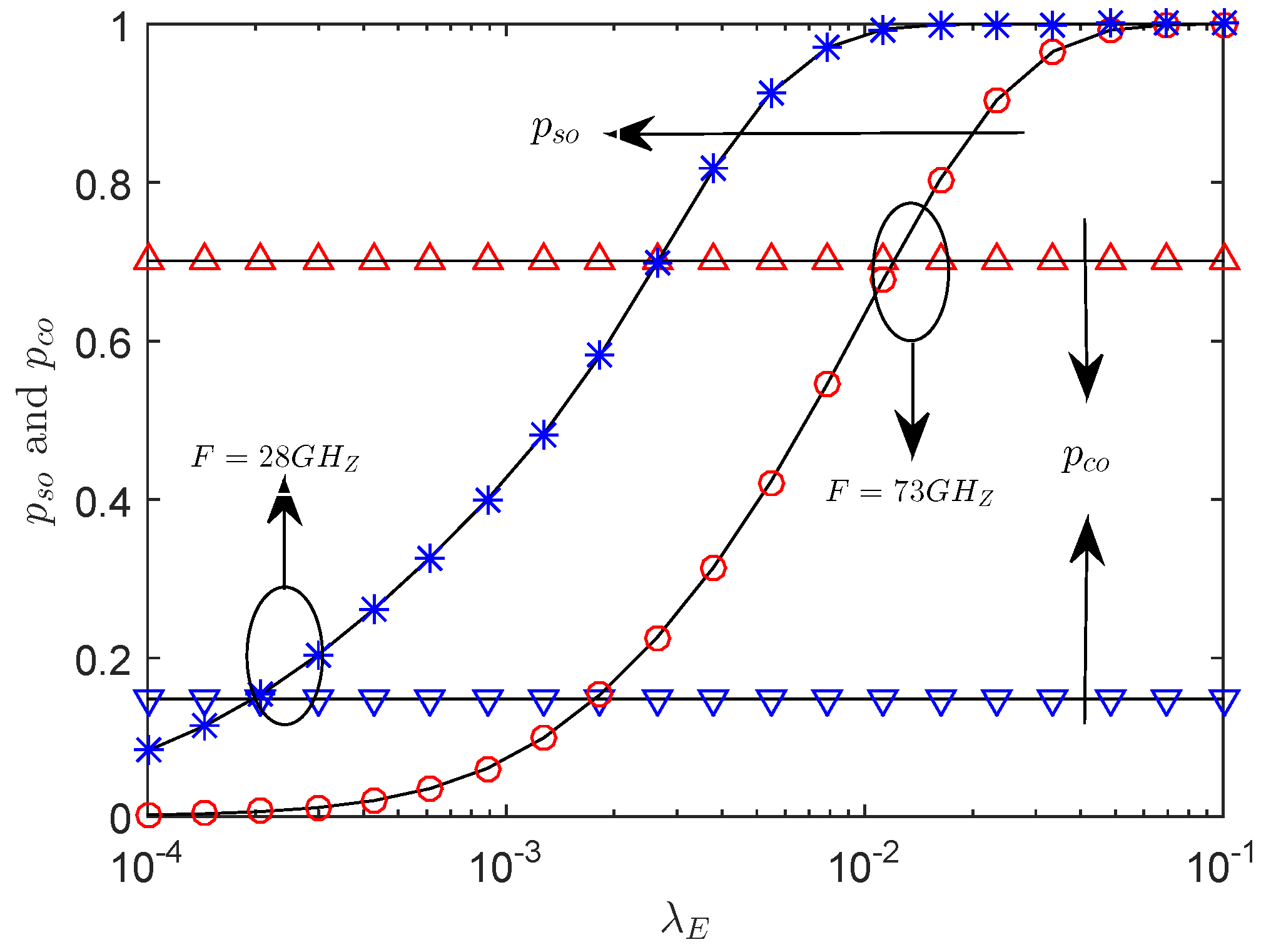
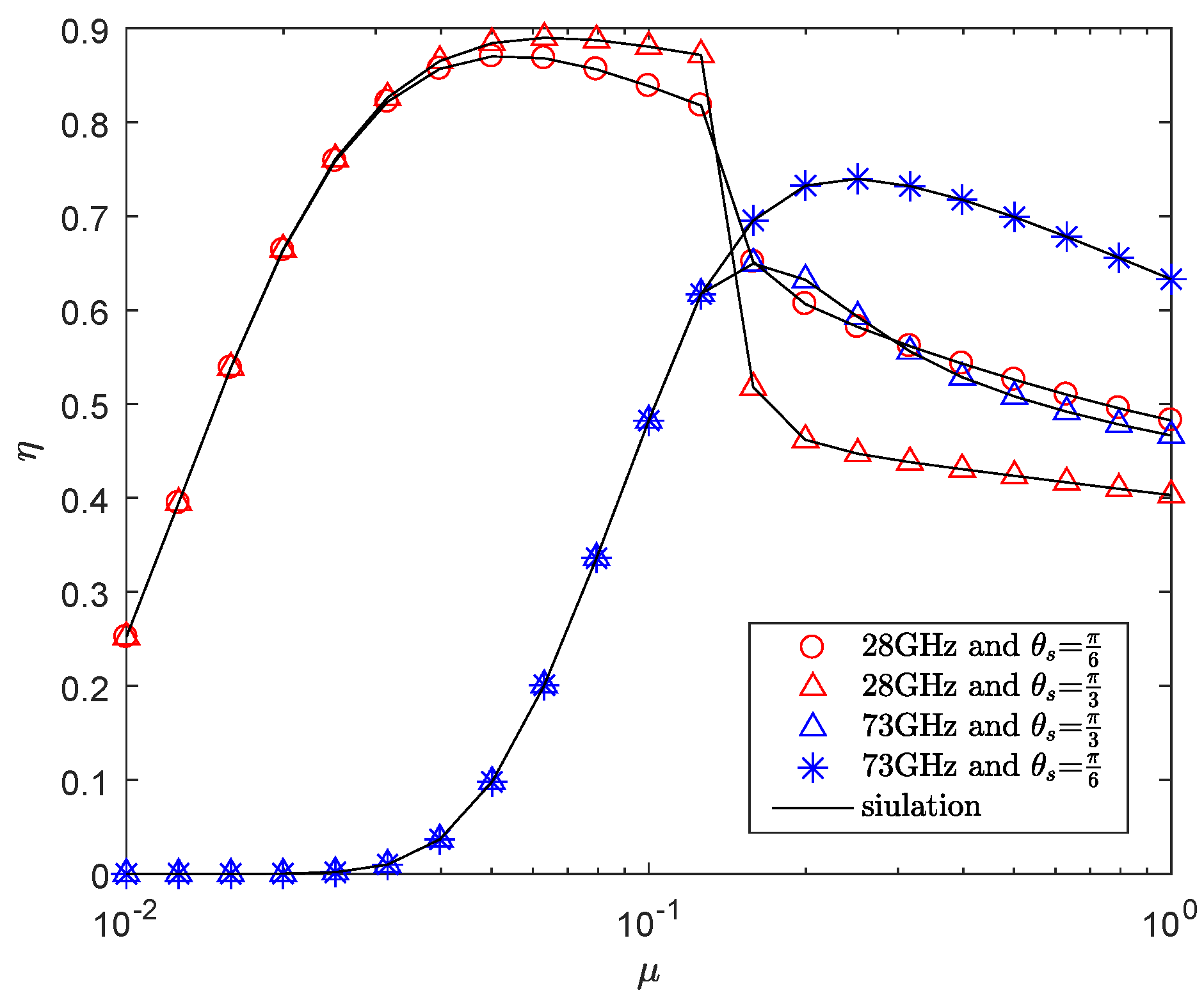
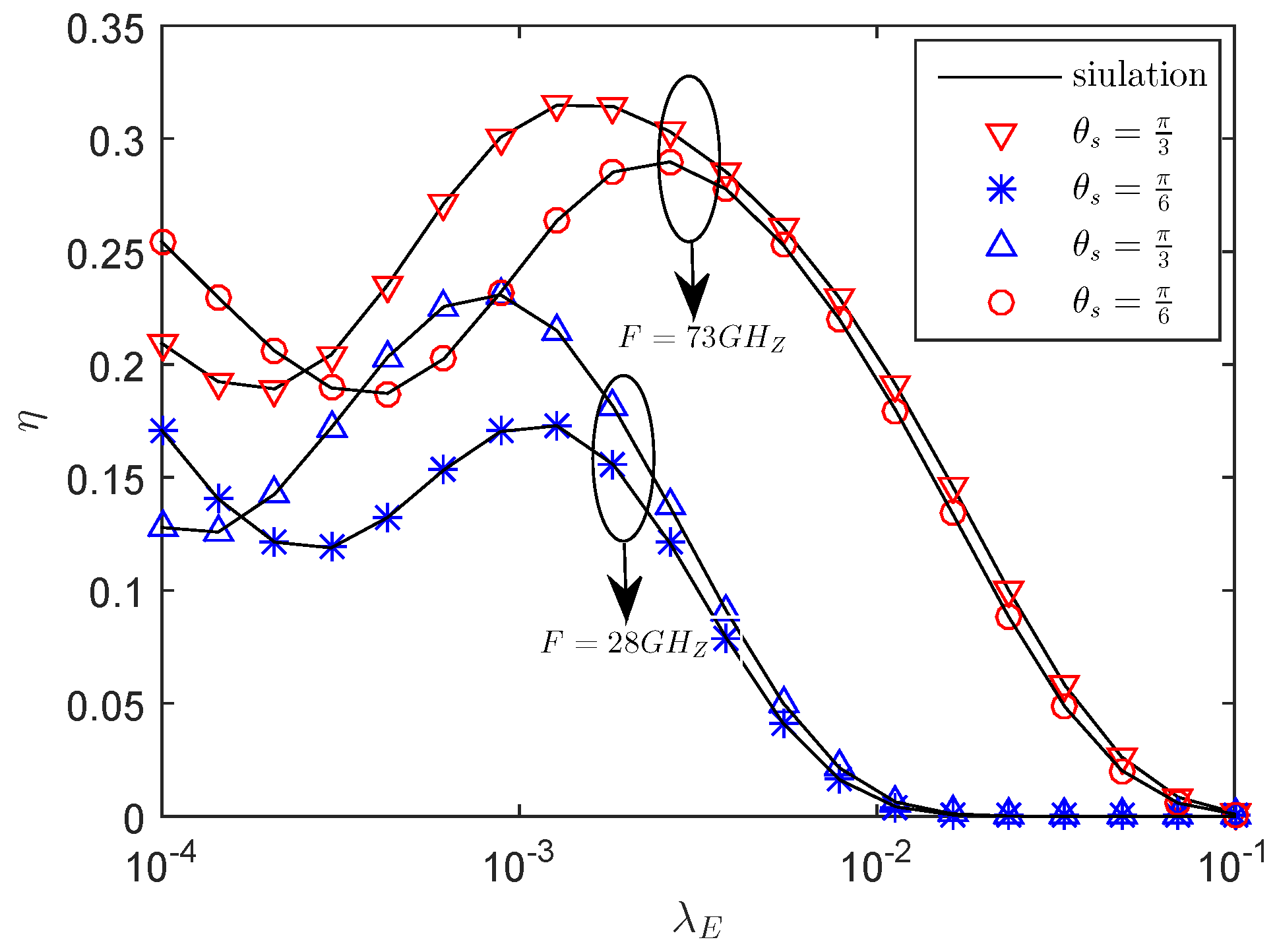
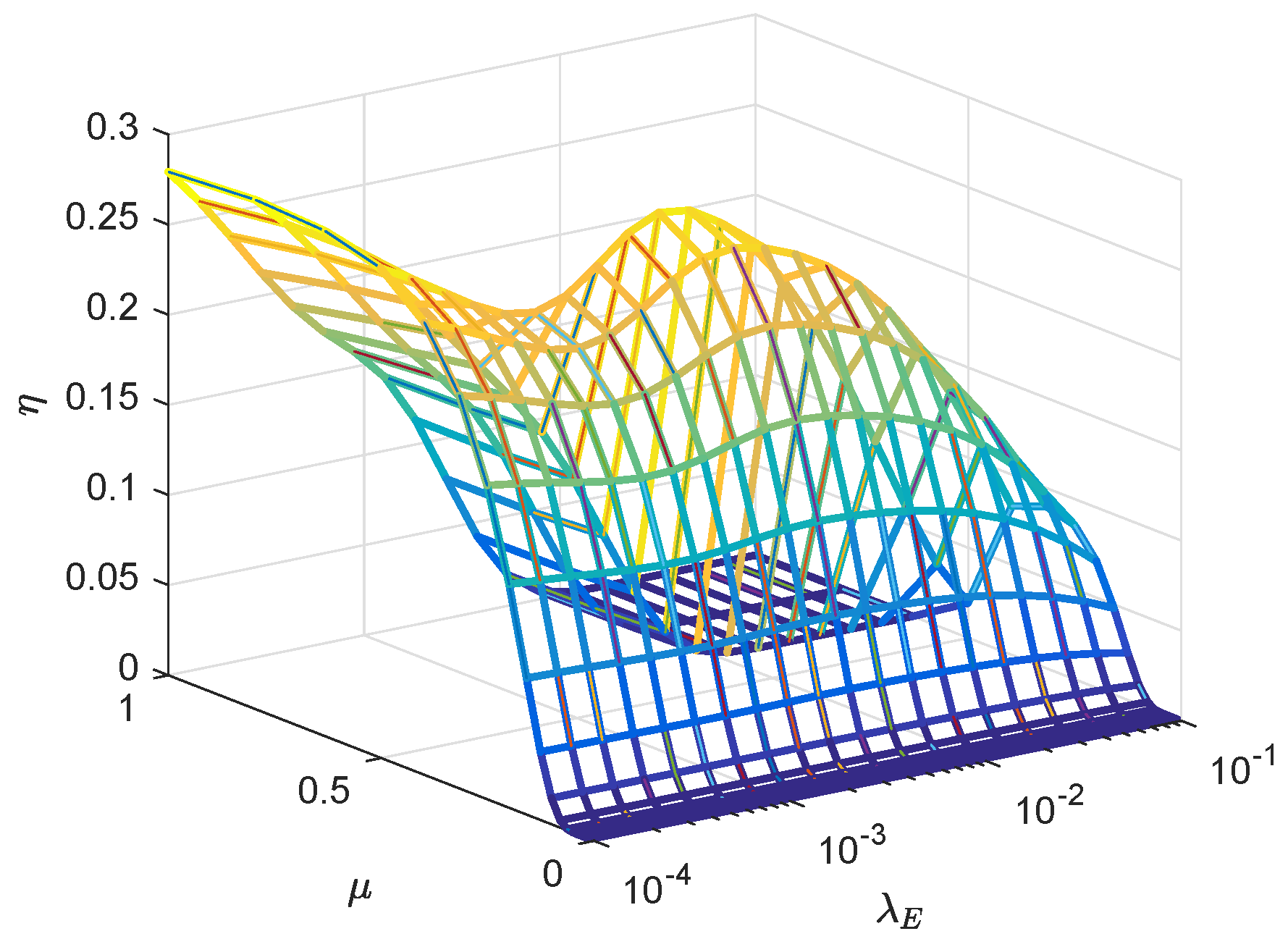
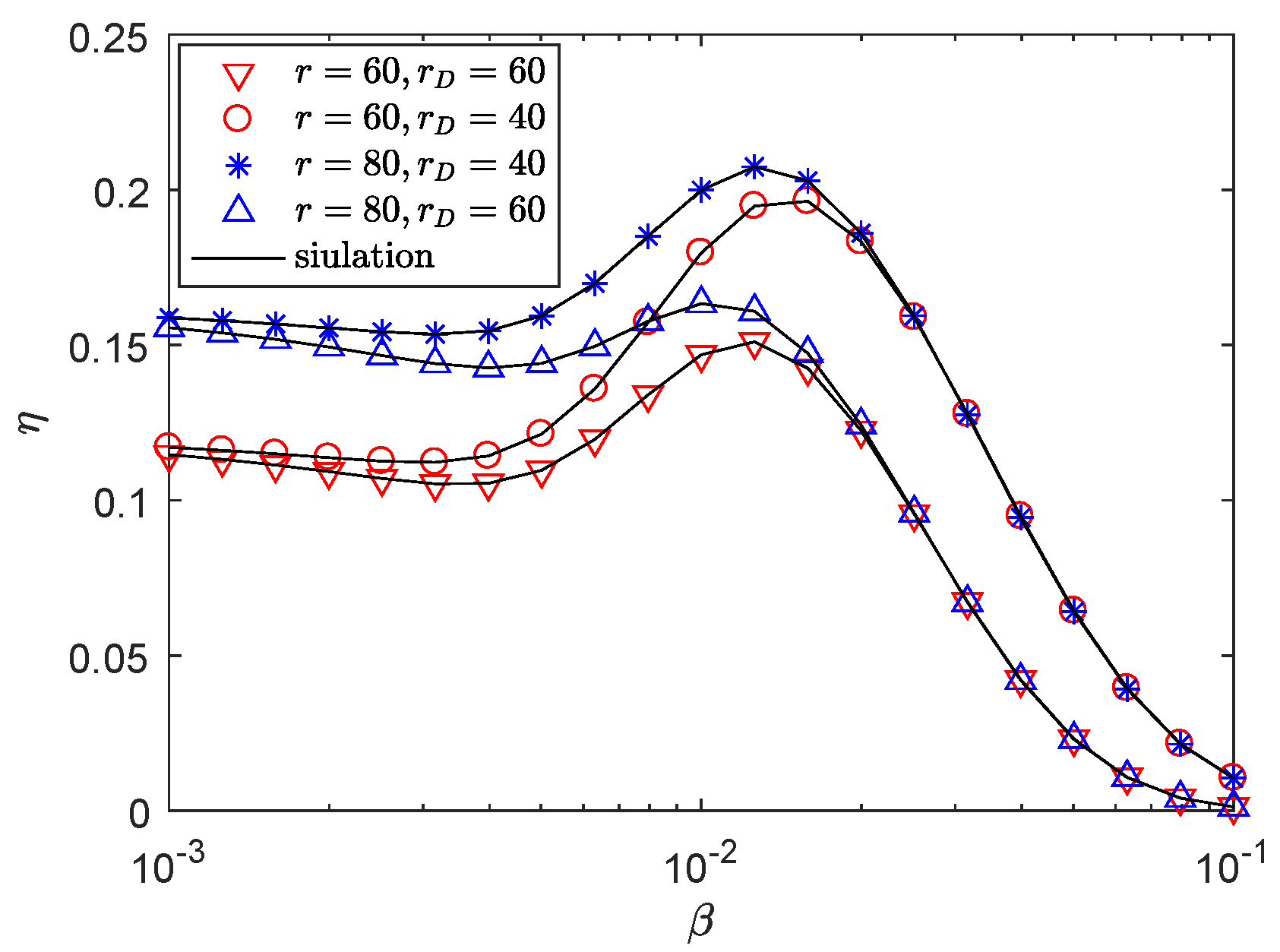
- The results show that enlarging the radius of sector secrecy guard zone improves secrecy performance. In addition, recruiting AN also enhances secrecy performance especially when the density of eavesdroppers is dense. In addition, blockage plays an important role in the transmission of mmWave, which can be utilized to improve secrecy performance. Furthermore, in our adaptive transmission scheme, increasing the density of eavesdroppers not always deteriorates the secrecy performance. Ultimately, simulations provide an easy choice of transmit power and power allocation factor for achieving higher secrecy throughput.
2. System Description and Performance Metrics
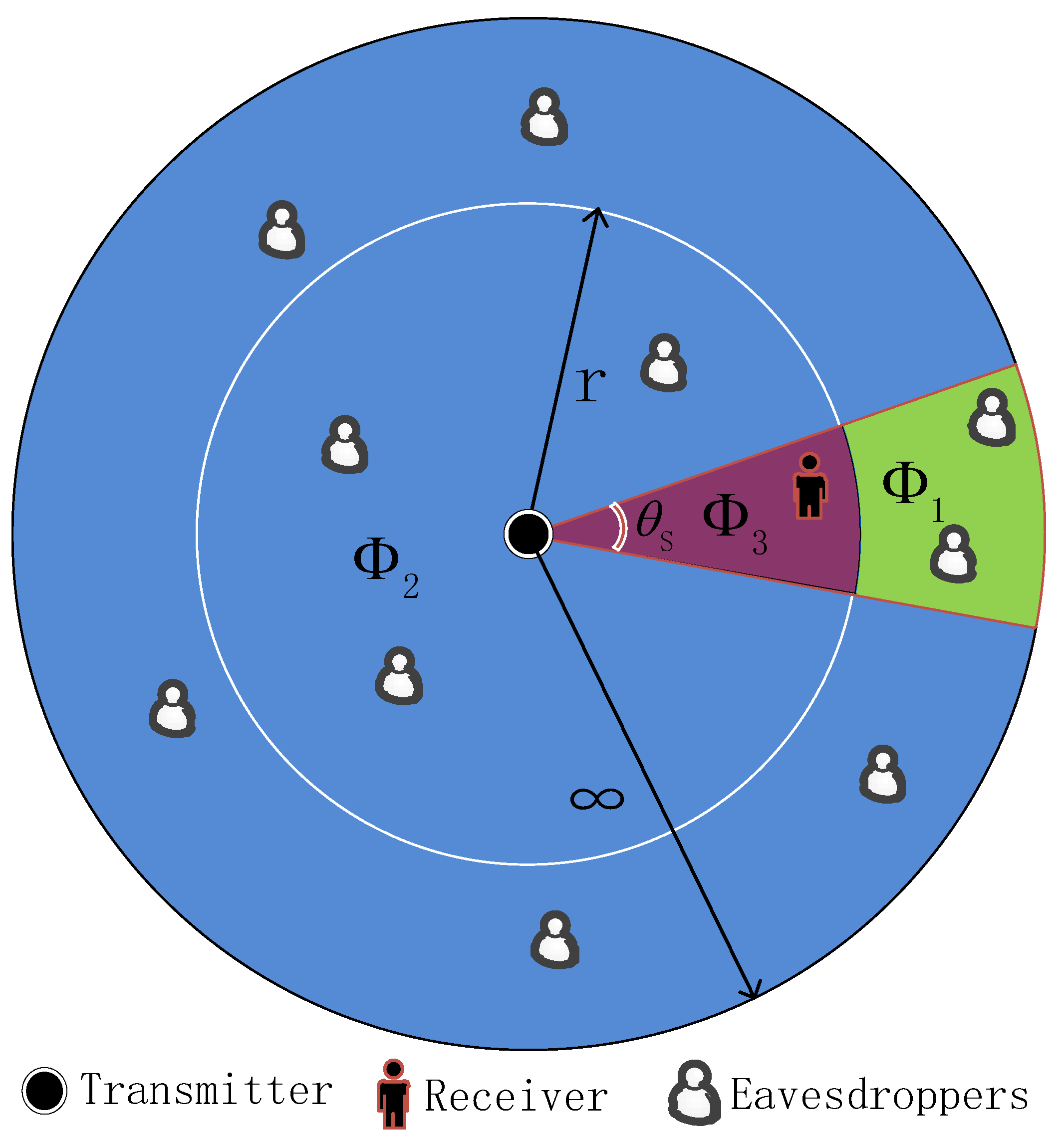
2.1. System Description
2.2. Performance Metrics
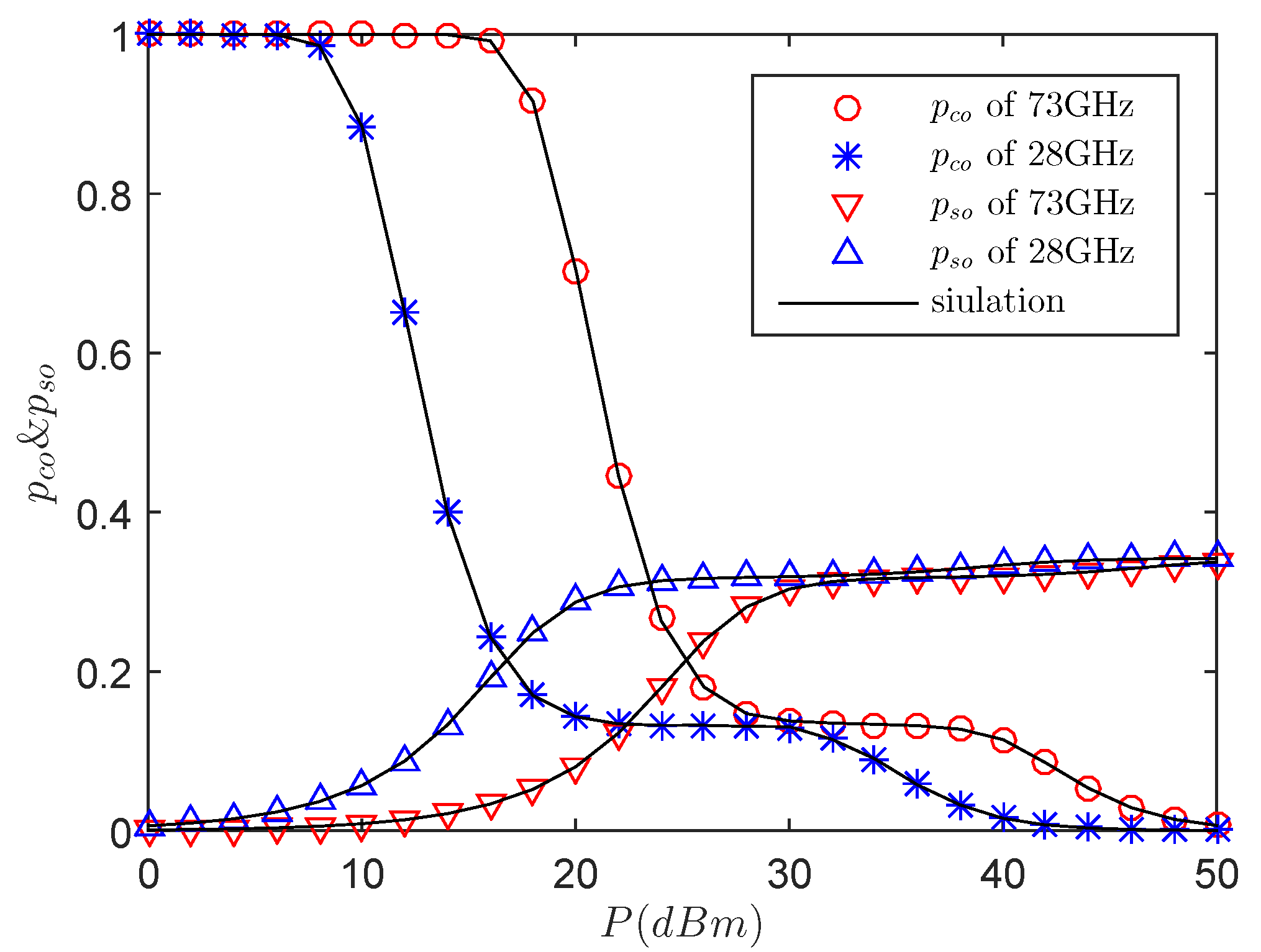
2.2.1. Secrecy Outage Probability and Connection Outage Probability
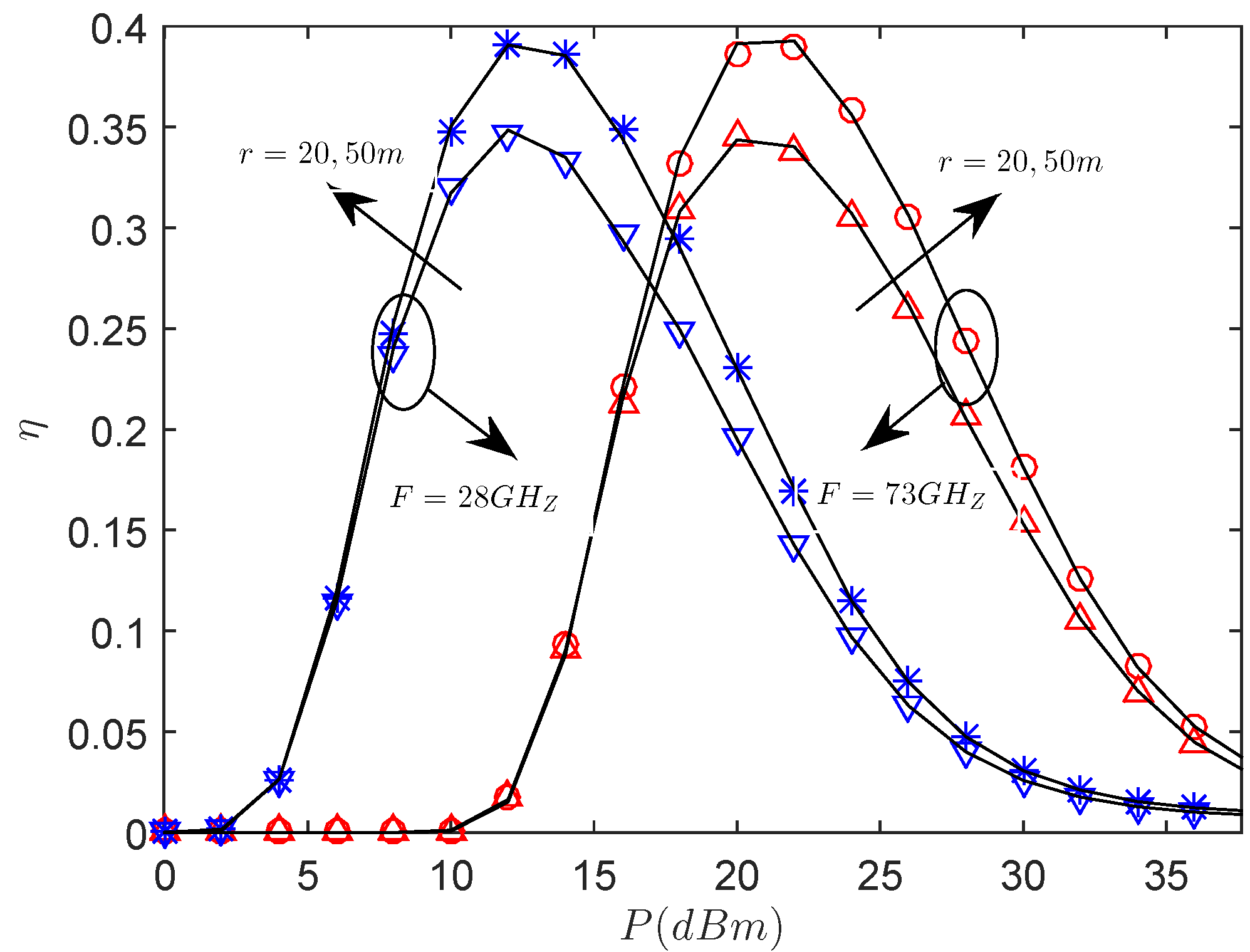
2.2.2. Secrecy Throughput
3. Secure Transmission Strategies
3.1. Eavesdroppers Are Detected Beyond the Sector Secrecy Guard Zone
3.2. Eavesdropper Is Detected in the Sector Secrecy Guard Zone
4. Performance Analysis
4.1. Direct Transmission
4.2. AN Assisted Transmission
4.3. Adaptive Transmission
5. Numerical Results
6. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Pi, Z.; Khan, F. An Introduction to Millimeter-Wave Mobile Broadband Systems. IEEE Commun. Mag. 2011, 49, 101–107. [Google Scholar] [CrossRef]
- Rangan, S.; Rappaport, T.S.; Erkip, E. Millimeter Wave Cellular Wireless Networks: Potentials and Challenges. Proc. IEEE 2014, 102, 366–385. [Google Scholar] [CrossRef]
- Gong, S.; Xing, C.; Fei, Z.; Ma, S. Millimeter-Wave Secrecy Beamforming Designs for Two-Way Amplify-and-Forward MIMO Relaying Networks. IEEE Trans. Veh. Technol. 2017, 66, 2059–2071. [Google Scholar] [CrossRef]
- Bai, T.; Alkhateeb, A.; Heath, R. Coverage and Capacity of Millimeter-Wave Cellular Networks. IEEE Commun. Mag. 2014, 52, 70–77. [Google Scholar]
- Bai, T.; Heath, R.W. Coverage Analysis for Millimeter Wave Cellular Networks with Blockage Effects. In Proceedings of the 2013 IEEE Global Conference on Signal and Information Processing, Austin, TX, USA, 3–5 December 2013; pp. 727–730. [Google Scholar]
- Yang, W.; Tao, L.; Sun, X.; Ma, R.; Cai, Y.; Zhang, T. Secure On-Off Transmission in MmWave Systems with Randomly Distributed Eavesdroppers. IEEE Access 2019, 7, 32681–32692. [Google Scholar] [CrossRef]
- Liu, Y.; Chen, H.; Wang, L. Physical Layer Security for Next Generation Wireless Networks: Theories, Technologies, and Challenges. IEEECommun. Surv. Tutor. 2017, 19, 347–376. [Google Scholar] [CrossRef]
- Xiang, Z.; Yang, W.; Pan, G.; Cai, Y.; Song, Y. Physical Layer Security in Cognitive Radio Inspired NOMA Network. IEEE J. Sel. Top. Signal Process. 2019, 1–14. [Google Scholar] [CrossRef]
- Tang, X.; Cai, Y.; Huang, Y.; Duong, T.; Yang, W. Secrecy Outage Analysis of Buffer-Aided Cooperative MIMO Relaying Systems. IEEE Trans. Veh. Technol. 2018, 67, 2035–2048. [Google Scholar] [CrossRef]
- Tang, X.; Cai, Y.; Deng, Y.; Huang, Y.; Yang, W. Energy-Constrained SWIPT Networks: Enhancing Physical Layer Security With FD Self-Jamming. IEEE Trans. Inf. Forensics Secur. 2019, 14, 212–222. [Google Scholar] [CrossRef]
- Jameel, F.; Wyne, S.; Kaddoum, G.; Duong, T.Q. A Comprehensive Survey on Cooperative Relaying and Jamming Strategies for Physical Layer Security. IEEE Commun. Surv. Tuts 2018. [Google Scholar] [CrossRef]
- Khisti, A.; Wornell, G. Secure Transmission with Multiple Antennas II: The MIMOME Wiretap Channel. IEEE Trans. Inf. Theory 2010, 56, 3088–3104. [Google Scholar] [CrossRef]
- Sun, X.; Yang, W.; Cai, Y.; Tao, L.; Liu, Y.; Huang, Y. Secure Transmissions in Wireless Information and Power Transfer Millimeter Wave Ultra-dense Networks. IEEE Trans. Inf. Forensics Secur. 2019, 14, 1817–1829. [Google Scholar] [CrossRef]
- Xiang, Z.; Yang, W.; Pan, G.; Cai, Y.; Sun, X. Secure Transmission in Non-Orthogonal Multiple Access Networks with an Untrusted Relay. IEEE Commun. Lett. (Early Access) 2019. [Google Scholar] [CrossRef]
- Yang, N.; Yan, S.; Member, S.; Yuan, J.; Member, S.; Malaney, R.; Subramanian, R.; Land, I.; Member, S. Artificial Noise: Transmission Optimization in Multi-Input Single-Output Wiretap Channels. IEEE Trans. Commun. 2015, 63, 1771–1783. [Google Scholar] [CrossRef]
- Li, W.; Ghogho, M.; Member, S.; Chen, B.; Xiong, C. Secure Communication via Sending Artificial Noise by the Receiver: Outage Secrecy Capacity/Region Analysis. IEEE Commun. Lett. 2012, 16, 1628–1631. [Google Scholar] [CrossRef]
- Romero-zurita, N.; Mclernon, D.; Ghogho, M.; Swami, A. PHY Layer Security Based on Protected Zone and Artificial Noise. IEEE Signal Process. Lett. 2013, 20, 487–490. [Google Scholar] [CrossRef]
- Chae, S.H.; Member, S.; Choi, W.; Member, S.; Lee, J.H.; Quek, T.Q.S.; Member, S. Enhanced Secrecy in Stochastic Wireless Networks: Artificial Noise With Secrecy Protected Zone. IEEE Trans. Inf. Forensics Secur. 2014, 9, 1617–1628. [Google Scholar] [CrossRef]
- Xu, X.; He, B.; Yang, W.; Zhou, X.; Cai, Y. Secure Transmission Design for Cognitive Radio Networks With Poisson Distributed Eavesdroppers. IEEE Trans. Inf. Forensics Secur. 2016, 11, 373–387. [Google Scholar] [CrossRef]
- Valliappan, N.; Heath, R.W.; Lozano, A. Antenna Subset Modulation for Secure Millimeter-wave Wireless Communication. IEEE Trans. Commun. 2013, 61, 3231–3245. [Google Scholar] [CrossRef]
- Yang, N.; Wang, L.; Geraci, G.; Elkashlan, M.; Yuan, J.; Renzo, M.D. Safeguarding 5G Wireless Communication Networks Using Physical Layer Security. IEEE Commun. Mag. 2015, 53, 20–27. [Google Scholar] [CrossRef]
- Barati, C.N.; Hosseini, S.A.; Rangan, S.; Liu, P.; Korakis, T.; Panwar, S.S.; Rappaport, T.S. Directional Cell Discovery in Millimeter Wave Cellular Networks. IEEE Trans. Wirel. Commun. 2015, 14, 6664–6678. [Google Scholar] [CrossRef]
- Vuppala, S.; Biswas, S.; Ratnarajah, T. An Analysis on Secure Communication in Millimeter/Micro-Wave Hybrid Networks. IEEE Trans. Commun. 2016, 64, 3507–3519. [Google Scholar] [CrossRef]
- Wang, L.; Elkashlan, M.; Duong, T.Q.; Heath, R.W. Secure Communication in Cellular Networks: The Benefits of Millimeter Wave Mobile Bbroadband. In Proceedings of the 2014 IEEE 15th International Workshop on Signal Processing Advances in Wireless Communications (SPAWC), Toronto, ON, Canada, 22–25 June 2014. [Google Scholar]
- Wang, C.; Wang, H.-M. Physical Layer Security in Millimeter Wave Cellular Networks. IEEE Trans. Wirel. Commun. 2016, 15, 5569–5585. [Google Scholar] [CrossRef]
- Zhu, Y.; Wang, L.; Wong, K.-K.; Heath, R.W. Secure Communications in Millimeter Wave Ad Hoc Networks. IEEE Trans. Wirel. Commun. 2017, 16, 3205–3217. [Google Scholar] [CrossRef]
- Ju, Y.; Wang, H.M.; Zheng, T.X.; Yin, Q. Secure Transmissions in Millimeter Wave Systems. IEEE Trans. Commun. 2017, 65, 2114–2127. [Google Scholar] [CrossRef]
- Zhang, X.; Zhou, X.; McKay, M.R. Enhancing Secrecywith Multi-Antenna Transmission in Wireless Ad Hoc Networks. IEEE Trans. Inf. Forensics Secur. 2013, 8, 1802–1814. [Google Scholar] [CrossRef]
- Andrews, J.G.; Bai, T.; Kulkarni, M.; Alkhateeb, A.; Gupta, A.; Heath, R.W. Modeling and Analyzing Millimeter Wave Cellular Systems. IEEE Trans. Commun. 2017, 65, 403–430. [Google Scholar] [CrossRef]
- Song, Y.; Yang, W.; Xiang, Z.; Cai, Y. Secure Transmission Design of Millimeter-Wave Wiretap Channel with Guard Zone and Artificial Noise. In Proceedings of the 2018 International Conference on Wireless Communications and Signal Processing (WCSP 2018), Hangzhou, China, 18–20 October 2018; pp. 1–6. [Google Scholar]
- Adhikary, A.; Safadi, E.A.; Member, S.; Samimi, M.K.; Wang, R.; Caire, G.; Rappaport, T.S.; Molisch, A.F. Joint Spatial Division and Multiplexing for mm-Wave Channels. IEEE J. Sel. Areas Commun. 2014, 32, 1239–1255. [Google Scholar] [CrossRef]
- Bai, T.; Heath, R.W. Coverage and Rate Analysis for Millimeter Wave Cellular Networks. IEEE Trans. Wirel. Commun. 2015, 14, 1100–1114. [Google Scholar] [CrossRef]
- Kong, L.; Vuppala, S.; Kaddoum, G. Secrecy Analysis of Random MIMO Wireless Networks Over α-μ Fading Channels. IEEE Trans. Veh. Technol. 2018, 67, 11654–11666. [Google Scholar] [CrossRef]
- Vuppala, S.; Tolossa, Y.J.; Kaddoum, G.; Abreu, G. On the Physical Layer Security Analysis of Hybrid Millimeter Wave Networks. IEEE Trans. Commun. 2018, 66, 1139–1152. [Google Scholar] [CrossRef]
- Turgut, E.; Gursoy, M.C. Coverage in Heterogeneous Downlink Millimeter Wave Cellular Networks. IEEE Trans. Commun. 2017, 65, 4463–4477. [Google Scholar] [CrossRef]
- Xu, X.; Yang, W.; Cai, Y.; Jin, S. On the Secure Spectral-Energy Efficiency Tradeoff in Random Cognitive Radio Networks. IEEE J. Sel. Areas Commun. 2016, 34, 2706–2722. [Google Scholar] [CrossRef]
- Tang, X.; Liu, R.; Spasojevíc, P.; Poor, V.H. On the Throughput of Secure Hybrid-ARQ Protocols for Gaussian Block-fading Channels. IEEE Trans. Inf. Theory 2009, 55, 1575–1591. [Google Scholar] [CrossRef]
- He, B.; Zhou, X.; Swindlehurst, A.L. On Secrecy Metrics for Physical Layer Security Over Quasi-Static Fading Channels. IEEE Trans. Wirel. Commun. 2016, 15, 6913–6924. [Google Scholar] [CrossRef]
- He, B.; She, Y.; Lau, V.K.N. Artificial noise injection for securing single-antenna systems. IEEE Trans. Veh. Technol. 2017, 66, 9577–9581. [Google Scholar] [CrossRef]
- Qin, H.; Sun, Y.; Chang, T.-H.; Chen, X.; Chi, C.-Y.; Zhao, M.; Wang, J. Power allocation and time-domain artificial noise design for wiretap OFDM with discrete inputs. IEEE Trans. Wirel. Commun. 2013, 12, 2717–2729. [Google Scholar] [CrossRef]
- Akitaya, T.; Asano, S.; Saba, T. Time-domain artificial noise generation technique using time-domain and frequency-domain processing for physical layer security in MIMO-OFDM systems. In Proceedings of the 2014 IEEE International Conference on Communications Workshops (ICC), Sydney, NSW, Australia, 10–14 June 2014; pp. 807–812. [Google Scholar]
- Gradshteyn, I.S.; Ryzhik, I.M. Table of Integrals, Series, and Products, 7th ed.; Academic Press: New York, NY, USA, 2007. [Google Scholar]
- Baccelli, F.; Baszczyszyn, B. Stochastic Geometry and Wireless Networks, Volume II: Applications; Now Publishers Inc.: Hanover, MA, USA, 2009. [Google Scholar]
- Haenggi, M.; Andrews, J.G.; Baccelli, F.; Dousse, O.; Franceschetti, M. Stochastic Geometry and Random Graphs for the Analysis and Design of Wireless Networks. IEEE J. Sel. Areas Commun. 2009, 27, 1029–1046. [Google Scholar] [CrossRef]
- MacCartney, G.R.; Rappaport, T.S.; Sun, S.; Deng, S. Indoor Office Wideband Millimeter-wave Propagation Measurements and Channel Models at 28 and 73 GHz for Ultra-Dense 5G Wireless Networks. IEEE Access 2015, 3, 2388–2424. [Google Scholar] [CrossRef]

© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Song, Y.; Yang, W.; Xiang, Z.; Liu, Y.; Cai, Y. Secure Transmission in mmWave Wiretap Channels: On Sector Guard Zone and Blockages. Entropy 2019, 21, 427. https://doi.org/10.3390/e21040427
Song Y, Yang W, Xiang Z, Liu Y, Cai Y. Secure Transmission in mmWave Wiretap Channels: On Sector Guard Zone and Blockages. Entropy. 2019; 21(4):427. https://doi.org/10.3390/e21040427
Chicago/Turabian StyleSong, Yi, Weiwei Yang, Zhongwu Xiang, Yiliang Liu, and Yueming Cai. 2019. "Secure Transmission in mmWave Wiretap Channels: On Sector Guard Zone and Blockages" Entropy 21, no. 4: 427. https://doi.org/10.3390/e21040427
APA StyleSong, Y., Yang, W., Xiang, Z., Liu, Y., & Cai, Y. (2019). Secure Transmission in mmWave Wiretap Channels: On Sector Guard Zone and Blockages. Entropy, 21(4), 427. https://doi.org/10.3390/e21040427




