Attack Algorithm for a Keystore-Based Secret Key Generation Method
Abstract
:1. Introduction
2. Key Generation and Management Based on Keystore Seed
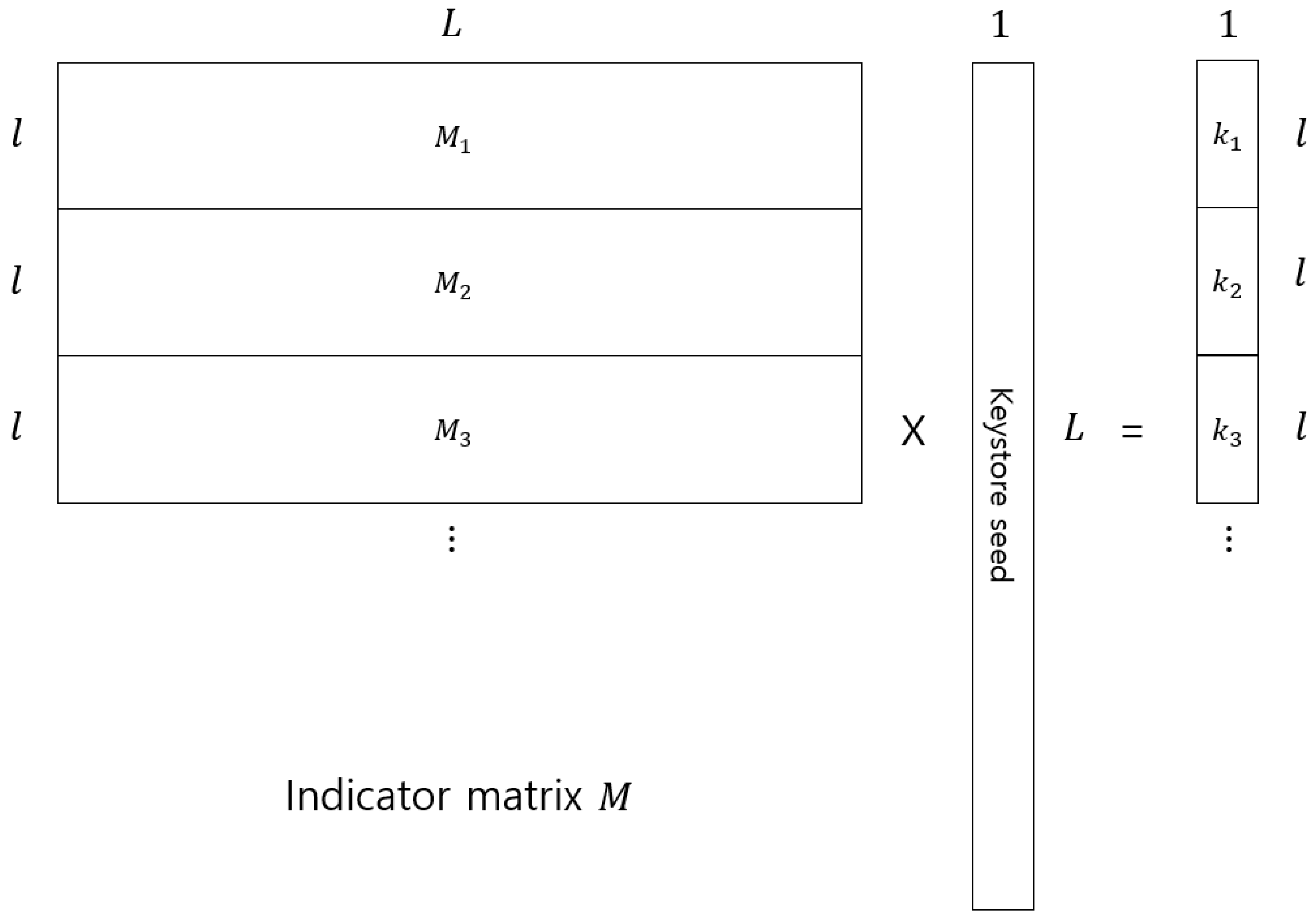
2.1. Key Generation
2.2. Key Management
- A file is encrypted using a key randomly selected from set .
- Attach the key index information into the encrypted file and send it.
- To decrypt an encrypted file, the encryption key is regenerated from the secure stored keystore seed and the received file using is decrypted using the attached key index information i.
2.3. Information-Theoretically -Secure Keystore
3. Linear Attack on Key Generation and Management
3.1. Linear Attack Algorithm
| Algorithm 1 Successful attack probability with R keys |
| Input: Variables Output: True if the indicator matrix rank is larger than or equal toL fori from 1 to Rdo Randomly select t integers in range of (0, ) indicator vector of of length l for j from 1 to do circular cyclic shift right once of end for if rank then return True end if end for |
3.2. Successful Linear Attack Probability
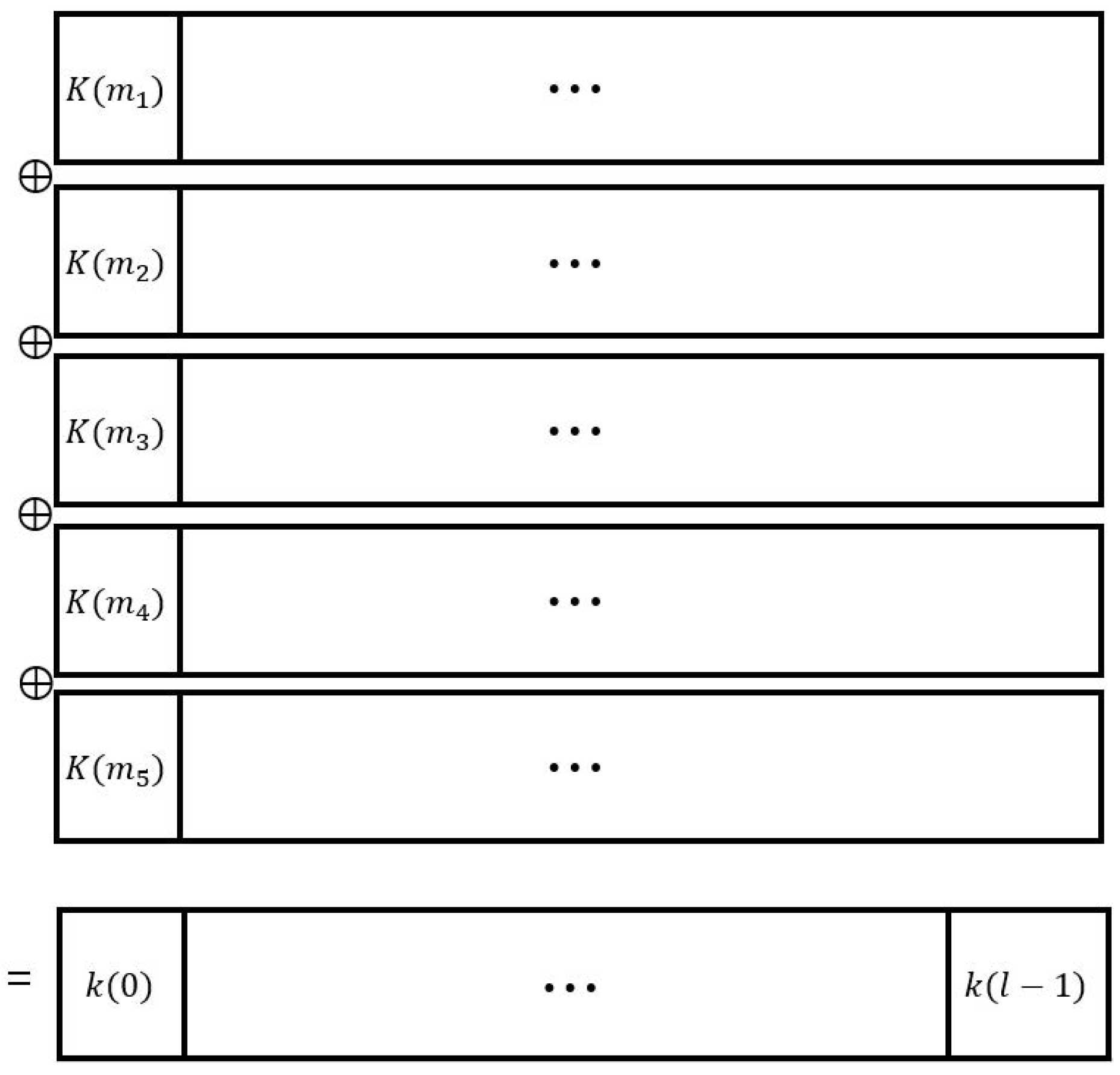
4. Information Theoretic Weakness of Modified Yang-Wu’s Schemes with Hashed Keys
5. Conclusions
Author Contributions
Funding
Conflicts of Interest
References
- Morris, R.; Thompson, K. Password security: A case history. Commun. ACM 1979, 22, 594–597. [Google Scholar] [CrossRef]
- Monrose, F.; Reiter, M.K.; Li, Q.; Wetzel, S. Cryptographic key generation from voice. In Proceedings of the 2001 IEEE Symposium on Security and Privacy, Oakland, CA, USA, 14–16 May 2001; pp. 202–213. [Google Scholar]
- Menezes, A.J.; van Oorschot, P.; Vanstone, S. Handbook of Applied Cryptography; CRC Press: Boca Raton, FL, USA, 1996. [Google Scholar]
- Yang, E.H.; Wu, X.W. Information-theoretically secure key generation and management. In Proceedings of the 2017 IEEE International Symposium on Information Theory (ISIT), Aachen, Germany, 25–30 June 2017; pp. 1529–1533. [Google Scholar]
- Wu, X.W.; Yang, E.H.; Wang, J.H. Lightweight security protocols for the Internet of Things. In Proceedings of the 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC), Montreal, QC, Canada, 8–13 October 2017. [Google Scholar]
- Bazm, M.-M.; Lacoste, M.; Sudholt, M.; Menaud, J.-M. Side Channels in the Cloud: Isolation Challenges, Attacks, and Countermeasures. 2017. Available online: https://hal.inria.fr/hal-01591808/ (accessed on 17 February 2019).
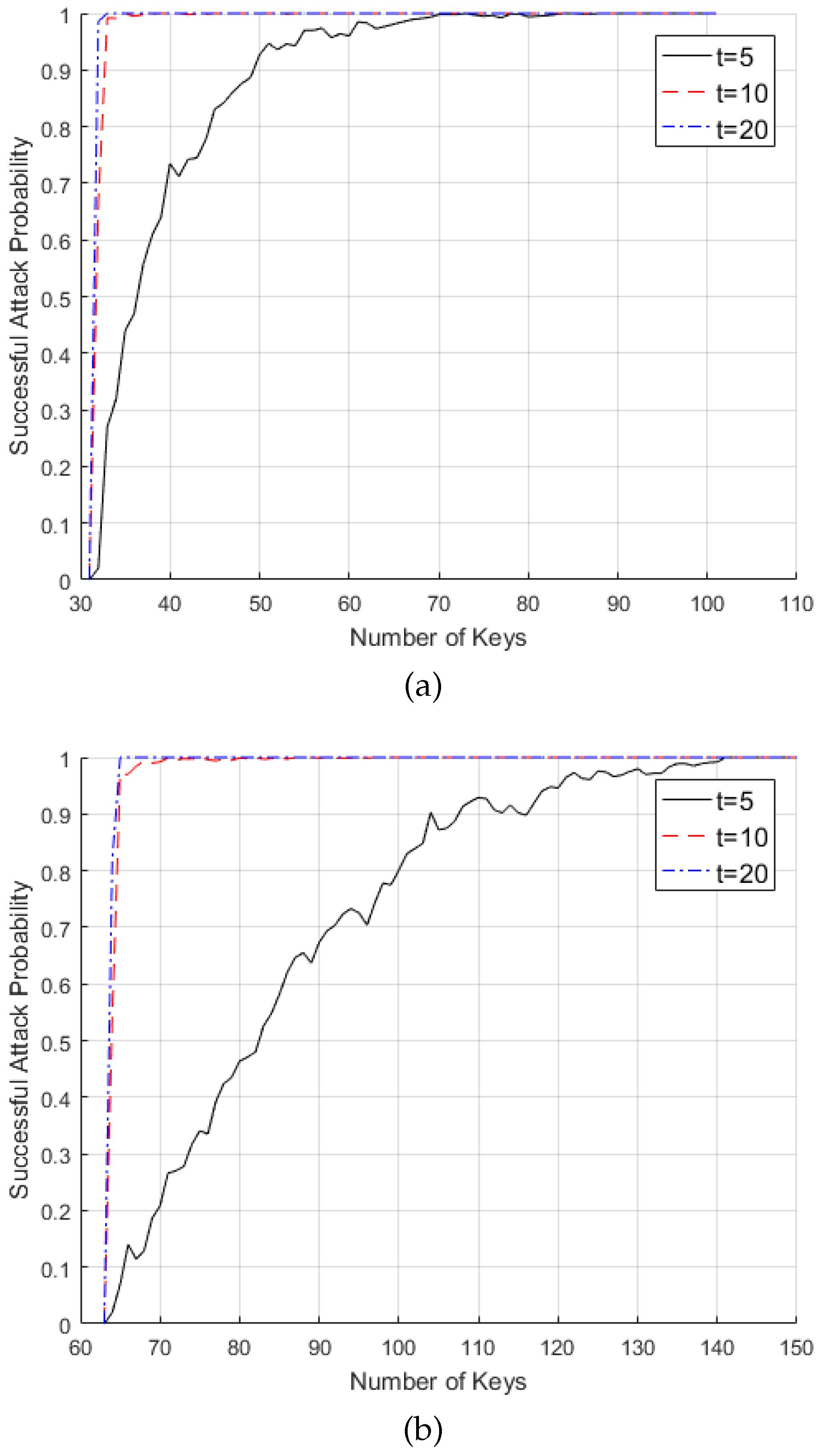
| Number of keys | |||
| 0.02 | 0.664 | 0.986 | |
| 0.735 | 1 | 1 | |
| 1 | 1 | 1 | |
| Number of keys | |||
| 0.02 | 0.540 | 0.820 | |
| 0.208 | 0.992 | 1 | |
| 0.801 | 1 | 1 | |
| 1 | 1 | 1 | |
© 2019 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Chae, S.; Kim, Y.-S.; No, J.-S.; Kim, Y.-H. Attack Algorithm for a Keystore-Based Secret Key Generation Method. Entropy 2019, 21, 212. https://doi.org/10.3390/e21020212
Chae S, Kim Y-S, No J-S, Kim Y-H. Attack Algorithm for a Keystore-Based Secret Key Generation Method. Entropy. 2019; 21(2):212. https://doi.org/10.3390/e21020212
Chicago/Turabian StyleChae, Seungjae, Young-Sik Kim, Jong-Seon No, and Young-Han Kim. 2019. "Attack Algorithm for a Keystore-Based Secret Key Generation Method" Entropy 21, no. 2: 212. https://doi.org/10.3390/e21020212
APA StyleChae, S., Kim, Y.-S., No, J.-S., & Kim, Y.-H. (2019). Attack Algorithm for a Keystore-Based Secret Key Generation Method. Entropy, 21(2), 212. https://doi.org/10.3390/e21020212






