1. Introduction
With the vast improvement of network and communication technology, communications were improved significantly. Communication for multimedia content, especially the image content over the Internet has become more and more chronic. Nevertheless, the security of the multimedia has a serious risk in the progression of communication because of the openness and distribution of the Internet. So the public has to take great care in terms of confidentiality and security of multimedia communication [
1].
Among several protecting approaches, image encryption is one of the most efficient and frequent strategies for digital information protection. Now, greater and more new techniques are proposed for image encryption, which pursuits to reduce image content’s redundancy by means of distinctive operations, such as DNA-based encryption operations [
2] and chaos-based ciphers [
3,
4]. Many solo image encryption schemes were proposed by researchers to address the multiple-image encryption algorithms. The most widely used image encryption algorithms encompass chaotic-based image encryption [
5,
6,
7,
8,
9], image encryption in the transform domain [
10,
11,
12,
13], DNA-based image encryption [
14,
15], and evolutionary-based image encryption [
16].
The chaos system possesses a ramification of traits, which includes high sensitivity to initial conditions, determinacy, and ergodicity. Sequences produced by chaotic maps are habitually pseudo-random sequences, and their structures are very complicated and tough to be analyzed and foretold [
17,
18,
19]. The typical ciphers primarily based on a chaotic map may be partitioned into two degrees: diffusion and permutation. In exercise, researchers frequently combine permutation and diffusion to get more computational security.
Because of the sensitivity and pseudo-randomness of the chaos, the chaotic sequences generated with the help of chaotic systems are intermittent and complicated. Researchers mostly encrypt the image in an early stage through the chaotic structures obtained by the low dimensional chaotic system, such as the one introduced in [
20]. An image encryption technique with a new 1D chaotic system was proposed.
In [
21] the author introduced 2D Logistic-Sine chaotic map-based image encryption algorithm. However, these sequences generated through low dimensional chaotic structures, and due to the inadequacy of the small keyspace cannot withstand against brute force attacks and thus possess the low security.
Conversely, Hyper-chaotic systems own larger keyspace and extra complicated dynamic features. Thus, the hyper-chaotic-based system can compensate for the shortcomings of a small keyspace of the low dimensional chaotic system and are more appropriate for the image encryption. In [
22,
23] the authors proposed a hyper-chaotic systems and fuzzy cellular automata-based novel image encryption algorithm that has higher security.
Sajid et al. [
24] introduced a hybrid image encryption algorithm based on FSM and cellular automata accompanying DNA sequence. The algorithm has good results and also the concept of a local rule is appreciable with regards to algorithm efficiency. However, the shortcomings of the particular algorithm is its aimed for use only for grayscale images.
Huang et al. [
25] proposed 7 dimensional CNN hyper-chaos-based application of image encryption scheme. Based on the results, the authors claimed that the hyper-chaotic systems are better than the low dimensional chaotic systems that own small keyspace. Astonishing information density, and the massive parallelism characteristics of DNA sequences, pushed the researchers to introduce collective hyper-chaos and DNA methods. Such collective technology schemes can be proved to be highly efficient and secure multimedia encryption schemes [
26,
27,
28].
A new encryption algorithm for the color image was proposed in [
29] that employs the hash-256 function to amend the control parameters and initial values of the chaotic system. The red, green and the blue channels of the image arranged into vector array form of one-dimensional. Then by rendering to the chaotic sequence generated by Piecewise Linear Chaotic Map 1-D vector array get sorted.
Nonetheless, in the utmost chaotic-based image encryption schemes that were stated above, the permutation phase and diffusion phase are autonomous of the plain image. Because the cryptosystem is impervious to the plain images and secret keys, such structures have the security flaws and cannot resist chosen/known-plaintext attacks or differential attacks.
Table 1, listed some well known encryption algorithms that get successfully Cryptanalysis by the enlisted attack approach.
Therefore, after the analysis of above-mentioned papers, we proposed a novel three channel three rule (3C3R) color image encryption algorithm. We made three contributions to this paper with each having corresponding merits.
Firstly, for the red channel: a new block bit inversion (BBI) model was proposed. In every row simultaneous right and left two-bits selection is random and relies upon the integer value of a particular pixel and the block multiplier. The left and right direction bit selection efficiently lessen the pixel correlation among the plain and ciphered image.
Secondly, for the green channel: cellular automata-based confined rules structure with Von-Neumann (VN) and Rotated Von-Neumann (RVN) structure was applied. Each sub-matrix gets different structural rule based on the particular bit values. Except for the fact that in the rule selection every sub-matrix has a direct relation with the previous one.
Thirdly, for the blue channel: a novel mathematical model of bidirectional State Machine (SM)-based DNA rule generator (SM-DNA) was proposed. The proposed model efficiently generates a random rule for each block-matrix. In each block-matrix
and
bit used as an input for the rule selection of next block-matrix. That means the bit arrangement of every predecessor block-matrix is responsible for the rule selection of the next block-matrix. The remainder of the paper organized as comply with; in
Section 2: Literature survey/Preliminary work,
Section 3: Proposed Image encryption scheme.
Section 4: Experimental parameters and discussion while
Section 5: Security analysis with the following
Section 6: Conclusion and future work.
2. Literature Survey
A binary sequence
can be used to denote a non-negative decimal number (DN) by the following equation.
As in any image, the pixel values of each channel are the non-negative decimal numbers between 0 and 255, thus every pixel can be denoted by the binary sequence of 1-byte or 8-bits. Similarly, the whole image can also be decomposed into binary 8-bit-planes [
50]. In such case, the
bit-plane will comprise of all the
bits of the binary demonstration of every pixel. Among these 2
3 = 8 bit-planes, most left bit-plane contains the highest significant visual information of the plain image, while the right most bit-plane contains the least visual information.
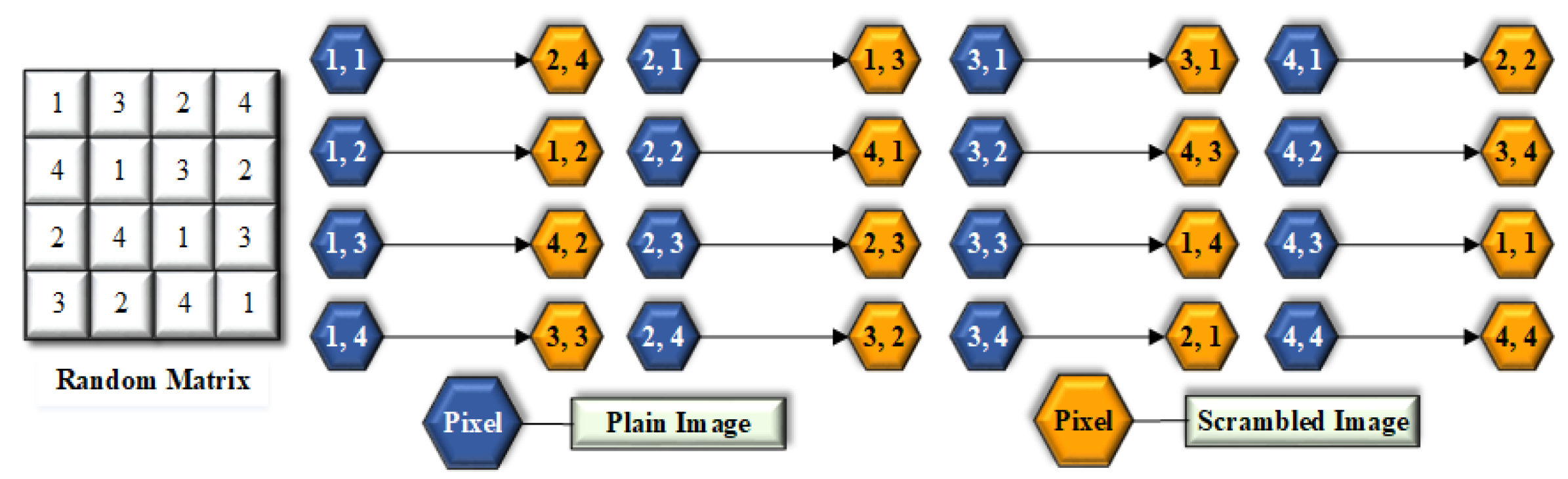
2.1. Scrambling Method
Scrambling is an easy and effective technique to lessen the correlation between the neighboring pixels. This paper introduced a one-to-one mapping for scrambling. Due to simultaneous changes of pixels in columns and rows, the proficiency of the algorithm enhanced enormously concerning time. The proposed algorithm has a one-to-one ratio between the pixels of scrambled image and the plain image, as displayed in
Figure 1.
The pseudo-code of the scrambling method for Encryption process is described in Algorithm 1, while in the decryption process the same procedure is applied but using reverse shifting, as described in Algorithm 2.
| Algorithm 1 Scrambling |
Encryption Process: Input: Generate matrix equal to the size of Plain image matrix . Output: size Scrambled matrix. Suppose for M = 4 and N = 4; ; ; ; A = Array sequence ; B = Array sequence ; I = for i in J = for j in = ; = ; = ; = ; = ; S = ; foriin range; do for j in range ; do m = = S end for end for T = forjin range; do = [ ]; for i in range ; do data.append.img a = shift end for end for forkin range 1 to N; do = ; end for S = ;
|
| Algorithm 2 Scrambling |
Decryption Process: Input: Random matrix and Cipher image matrix . Output: Descrambled matrix P. forjin range; do = [ ]; for i in range ; do data.append.img a = shift end for end for forkin range 1 to N; do ; end for
|
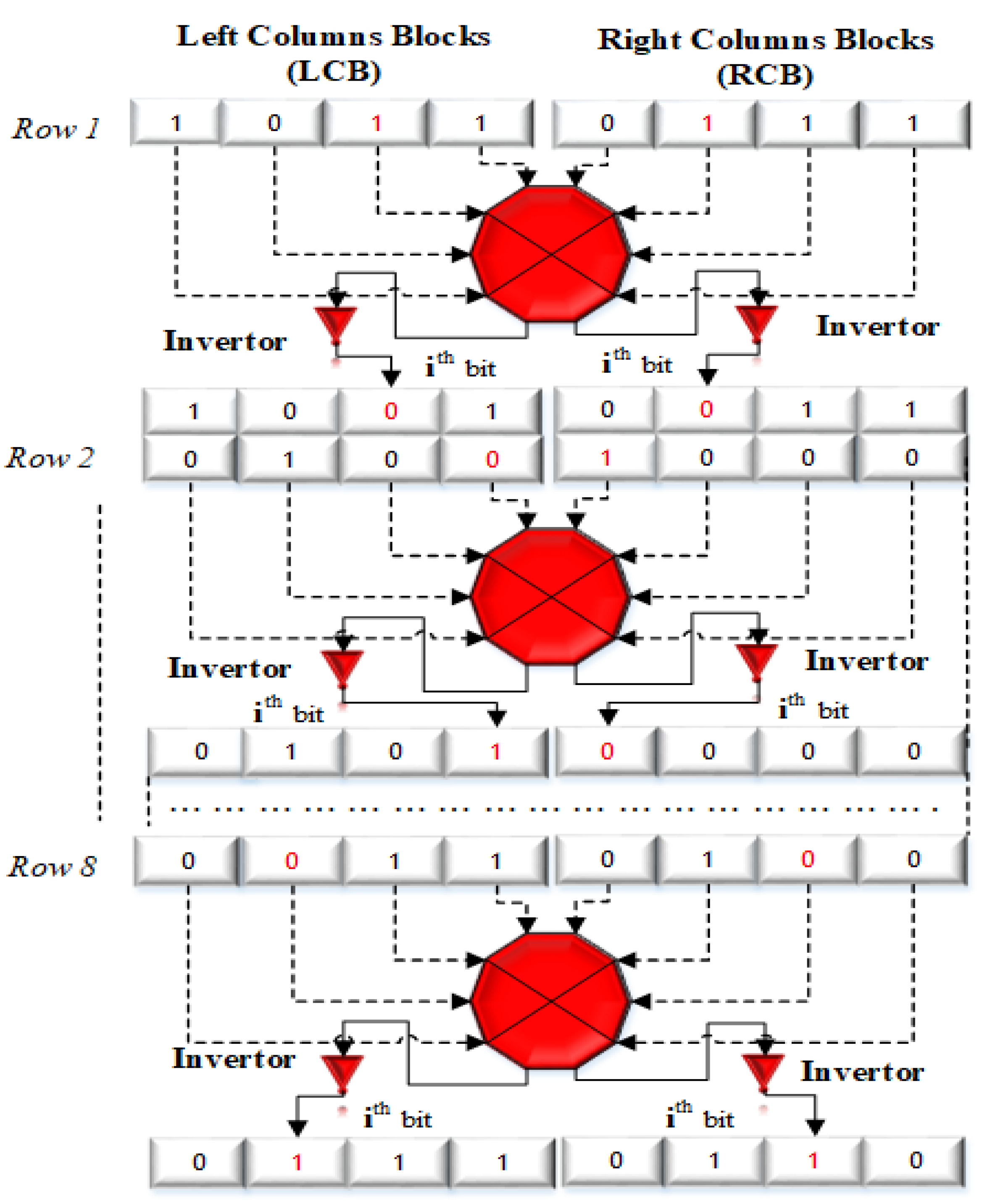
2.2. Novel Block Bit Inversion (BBI)
In this paper, we propose a novel blocked-based bit inversion technique to alter the pixel values. The
Figure 2 is the graphical illustration of the proposed
BBI structure for the image sub-matrix of the size
. Firstly, it divides the particular block matrix into two equal column blocks; labelled as Left bit Columns Blocks (LCB) and Right bit Columns Blocks (RCB). The purpose is to change the bits in every row and columns but in the opposite manner. It changes the particular bit
1 or
0 into opposite i.e.,
0 if it is
1 or else
1 if it is
0. For each pixel, the change in value occurs (either addition or subtraction) depending upon either its get converted into
1 from
0 or get converted to
0 from
1. As each bit has a unique value, so because of bit inversion following change occurs in pixels based on the particular bit location.
For example, we can see in
Figure 2 that for each binary blocks the bit selection is in opposite direction means
for left and right columns blocks. For the left columns block the selection of bit is from left to right
and for the right columns block the selection of bit is from right to left
. How its locate; is illustrated in
Figure 3. Like in main diagram for the 1
st row, 3
rd bit is selected for the inversion in left columns block which is actually 6
th while counting from right to left. In same passion, for the right columns block, 3
rd bit is selected that is actually 6
th when counting from left to right. So selection is the same for 3
rd bit but direction is opposite as
. Thus, to select the particular bit in the novel BBI model, the formula efficiently locate the right and left block bits by proceeding only by the left to the right direction. The starting bit selection for each
blocks is based on the following formula.
Here , where P is the pixel value of particular pixel, n is the block number multiplier to change the 1st bit for each block, B is the byte (8 bits), is the mod function that returns the remainder between 0 to 7 because of B is one byte (8-bits), and is the particular row number range from 1 to 8.
For better understanding, Let suppose the decimal value of
P for the 1
st sub-matrix came
183, so the value of left columns block (
) for the
1st row
or
= 1 can be gotten as follows.
Likewise, for the 2
nd row of this 1
st sub-block matrix,
or
Ri = 2 the inverting bit will be;
Similarly, for the
,
,
to up to
rows for every
, desired inverting bit can be gotten through the formula. Alternatively, the formula of the bit selection for the right blocks is as follows.
As an example, in the above case after putting values.
Similarly, for the 2
nd row, the bit will be following.
First of all, an initial configuration matrix of
is generated by the hash value of the key. Based on the above-mentioned formula of
and
, bit inversion is done over the initial configuration matrix
and later this updated initial configuration matrix
is XORed with the first plain matrix. The general equation of XORing the updated
with the plain image matrices is as follows.
where
; where
N is the entire number of sub-matrices of the red channel. While
is the particular updated matrix,
is the plain image sub-matrix of the red channel, and
is the updated initial configuration matrix. Similarly, for the 2
nd sub-matrix bit inversion is performed over the updated initial configuration matrix of 1
st block stage and then XORed with the second sub-matrix of the plain image as follows.
For the decryption phase, the reverse process to get back the plain image matrix is as follows.
where
and
N is the total number of sub-matrices.
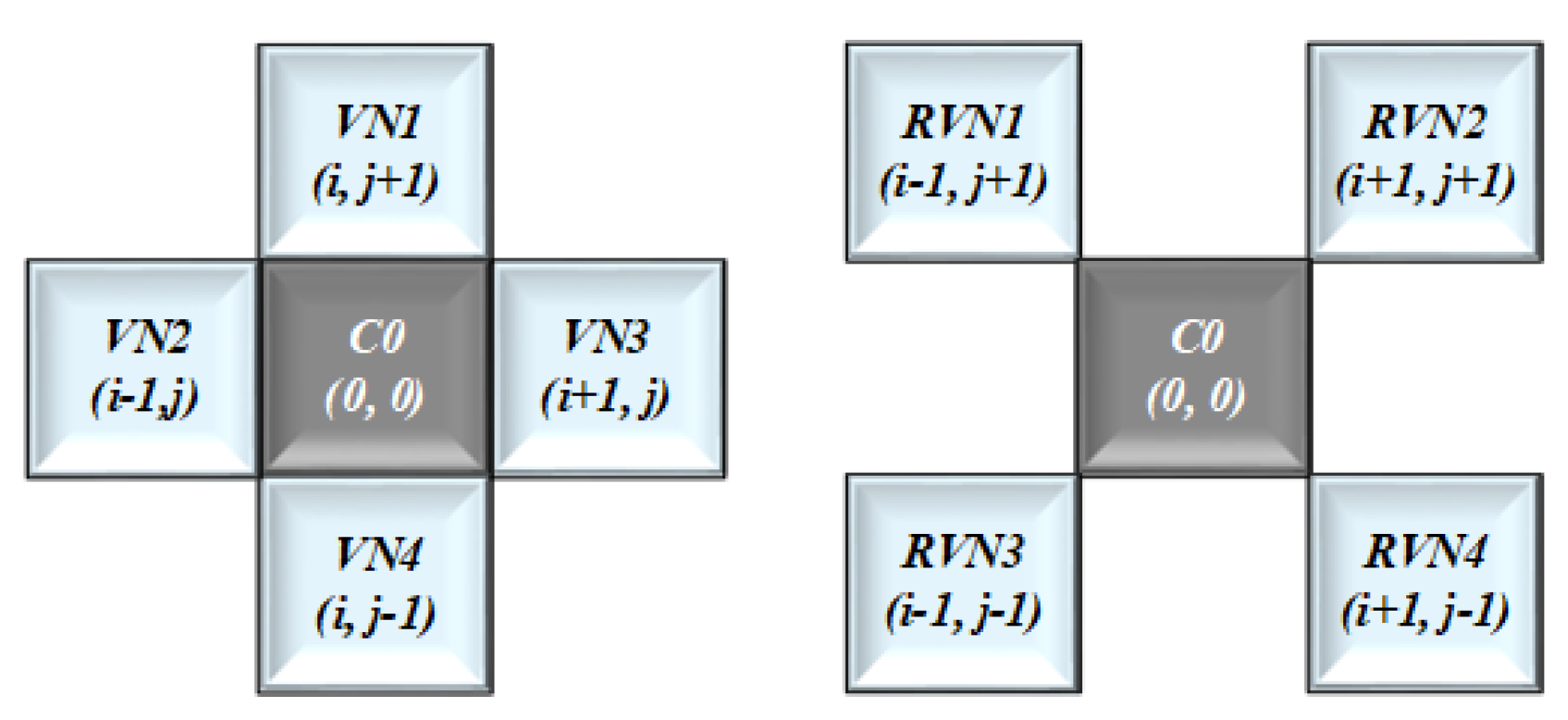
2.3. Two-Dimensional Cellular Automata
In this paper, a 2D-CA with VN and RVN structure was implemented as shown in
Figure 4. Also, in cellular matrix form, every cell can have one of the two possible states that is either
1 or
0. In cellular representation every cell has its neighboring cells. The cell with VN neighbors or a radius equivalent to
1 can be represented in equation form as follow:
In this Equation (
7),
is the Boolean function or a state transition function that takes to the new state, where
. Like VN, the cell with Rotated VN neighbors can be represented as follow.
So, to get the combined structure of VN and RVN, We merged these two equations as follows.
We represent these
9 state variable with
:
, as shown in
Table 2. For the green channel as the bit depth or intensity is
28 so, we mapped the above mentioned
8 state variables with these eight bits as
=
, while excluding the central state variable
represented as
.
Finally, the confined rule structure is based on the following equation.
In this updated form of Equation (
10);
,
,
,
,
,
,
, and
are the state variables that can have the values either
1 or
0. Therefore, the particular state variable will contribute in the XOR operation or state update process only if its respective bit will be equivalent to
1, otherwise it will not take part in the state update process.
Thus, the structural combination of above direction variables based on the binary value of decimal number is employed to elect which and whom cells/cell will take part in the state update process. Hence different binary representation means different confined rule equation for the matrix update process of each succeeding matrix. The general formula of the confined rules is given below.
In this formula
=
count ,
=
count ,
is the initial configuration matrix for the green channel that we got from the reserved hash (SHA-512) values for the green channel.
F is the highest value of pixel that is 255. Whereas,
T is the total number of blocks. For clear demonstration, let suppose we have the initial configuration matrix
with a size
as given in
Table 3.
From the ASCII table as the value of
1 is
49 and the value of
0 is
48, so the decimal value for the confined rule structure of the
1st sub-matrix can be found as follows.
Now converting this
27 into the binary form
[00011011]2. As in this binary representation only
4 bits are
1, So only these
4 cells will participate in the XOR operation of 1
st sub-matrix. To find those specific
four cells we now put this binary value in Equation (
10).
So Equation (
12) will be simplified as follows.
This updated Equation (
13) has four state variables that are
= 1,
= 1,
= 1 and
= 1. So, only these four cells will contribute in the state update process of the 1
st sub-matrix. From
Table 2 we can see
is actually
,
is actually
,
is actually
, while
is actually
. Hence, by means of these confined rules structure, the processing power, computation time, efficiency and the security can be improved immensely.
The initial configuration matrix gets updated based on these confined rules mapping and then XORed with the particular plain image sub-matrix to acquire the updated matrix.
Here
is the updated matrix,
is the updated initial configuration based on confined rules, and
is the plain image matrix. In decryption process the reverse equation to get back the original plain sub-matrix will be as follows.
2.4. DNA Sequence
DNA molecule contain the genetic information that is used for the purpose of reproduction, functioning and growth of all living organism. Any DNA sequence comprised of four nucleic acid bases: Adenine (A), Cytosine (C), Guanine (G), and Thymine (T). These bases follow the principle of Watson–Crick, that is A and T are complementary, so are C and G same as in the binary system, 1 and 0 are complementary.
Likewise, the case of two-bits binary
11 and
00 are also complementary. Usually in DNA sequence every base is represented by the two-bits as 11, 10, 01 and 00 to represent these four bases T, G, C, and A respectively. There are basically
24 different kinds of DNA coding schemes. Nonetheless, out of those, only eight kinds fulfill the Watson–Crick complementary principle [
51], which are given in
Table 4. Please note that, like DNA encoding, the DNA decoding rules are just the inverse process of the DNA encoding rule.
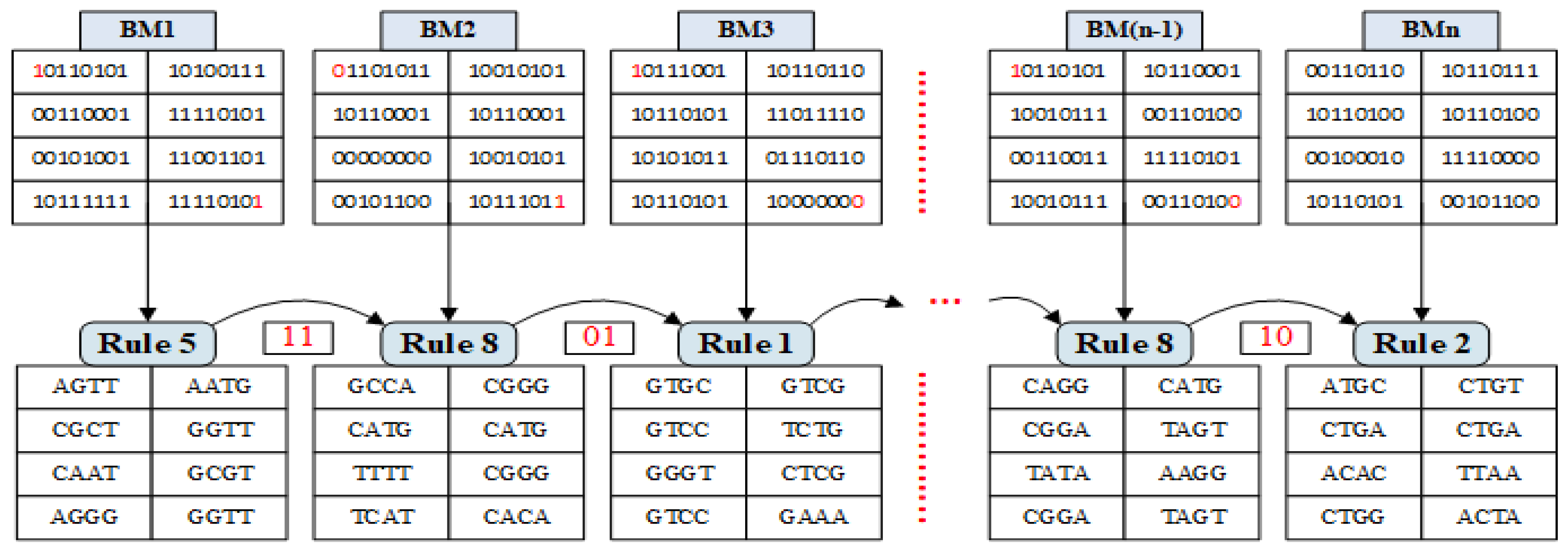
In this paper, we propose a new bidirectional mathematical model of DNA rule generator based on two bits of input as shown in
Figure 5. The working principle of this model is based on Automaton state machine, so it is called the
SM-DNA rule generator. SM-DNA generates random DNA rules faster than the chaotic serious-based rules selection method.
The pixel value of image matrix was converted into binary, then divided into sub-matrices form. We used and bits as an input. SM-DNA select random DNA rule for each block matrix. In our case, the first and last bit of every sub-block matrix was used as an input. The proposed SM-DNA model has eight states and each state represents one rule. Each state has 22 possible output states that take to next or previous state, so it means 84 = 4096 different rules combination, while rule transition from one to another depends solely on the following 4 combinations, either 11, 10, 01 or 00. For 00 it moves anti-clockwise direction and for 01, 10 and 11 it moves clockwise direction.
For ease of implementation binary matrix of the image was converted into
sub-matrices. SM-DNA allocated random DNA conversion rule to each sub-matrix very efficiently and quickly. For more clear understanding, working principle illustration is given in
Figure 6 with a total of
N binary sub-block matrices termed as
. So the general formula of SM-DNA described as follows.
where
kth and
nth are the two particular bits of own choice to serve as an input for the rule selection, that is
and
in our case. Suppose
is our first block matrix and also suppose the
P1 and
P2 value came out
109 and
207, respectively. So DNA starting rule for the 1st sub-block matrix can be gotten as follows.
So,
Rule 5 will be the starting rule that will be used for binary to DNA conversion of 1
st sub-block matrix.
For the 2
nd sub-block matrix
and
bit of 1
st block matrix will be used that are
1,1. So, the
Rule 8 is the conversion rule for 2
nd sub-block matrix.
As input bits of the 2
nd sub-block matrix are
0,0, So it went to state
7. Thus,
Rule 7 will be the conversion rule for the 3
rd sub-block matrix.
Similarly, all the sub-block matrices were converted into DNA sequences based on rules generated by SM-DNA as shown in
Figure 6. Remember that for the
sub-block matrix the
sub-block matrix will decide the rule. From security prospective as rule selection based on two bits inputs so it is very difficult to predict that out of 32-bits, which two-bits are working as an input. Thus its difficult to guess the rule selection without getting adequate information about the working principle of SM-DNA.
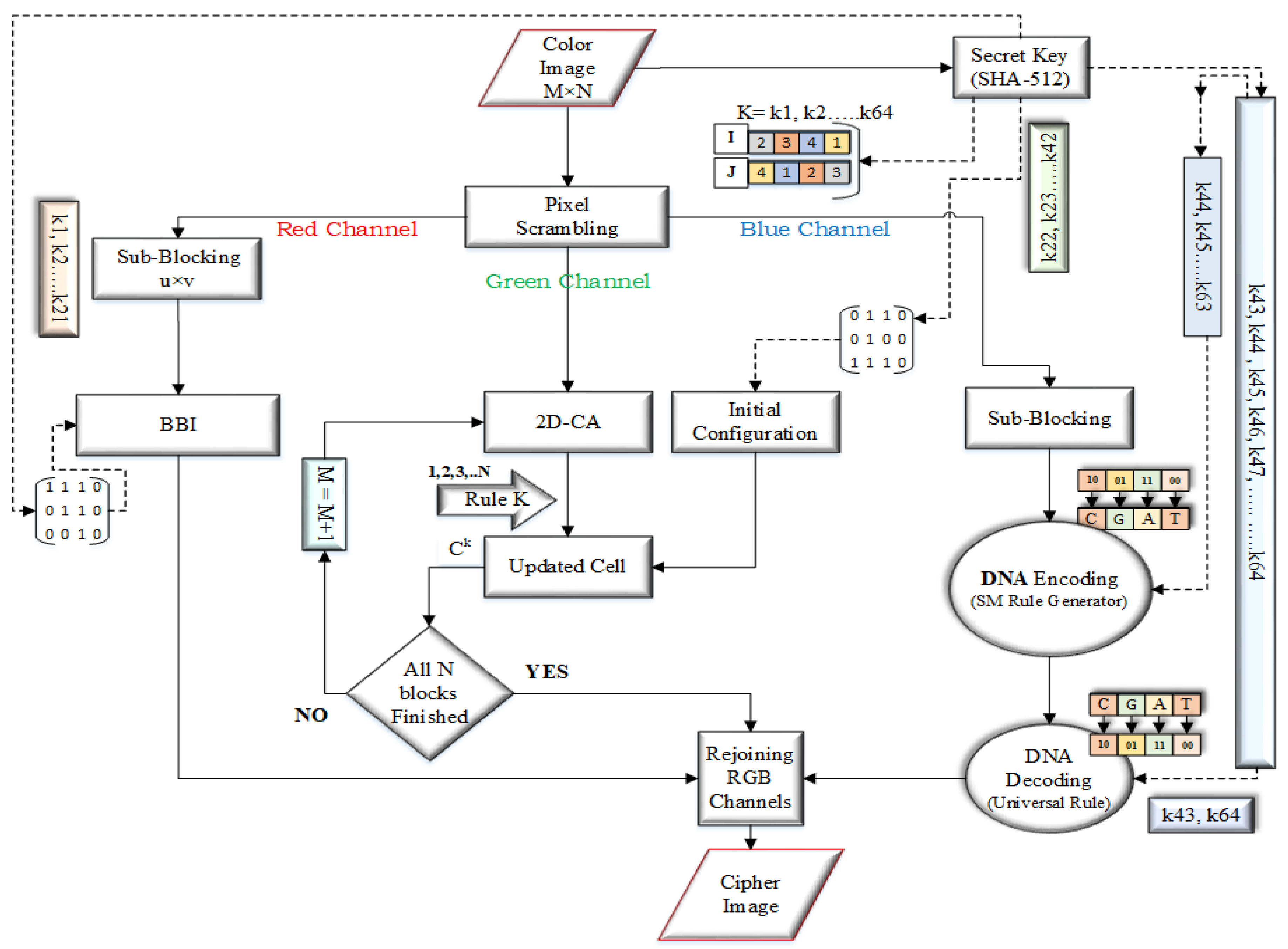
3. Proposed Encryption Method
The general block diagram of the proposed image encryption method is shown in
Figure 7. The proposed encryption method deal with the binary bit-planes of each channel. The detailed encryption steps are given below.
Step 1: Get the double hash-value of the image by using SHA-512. Hexadecimal forms of the key string will be gotten. Split the key string into three parts i.e.,
,
and
hexadecimal pairs to use in the formulas and initial configuration matrices of red, green and blue channels as follows.
Step 2: Take the color image
, where
M and
N denote the rows and columns of the image, respectively. Scramble as described in the scrambling portion, while the hexadecimal form of a key was used as a seed to generate array sequence by
. For the two rounds of sequences, the seed values are set through the following equations.
The integer values for two round from the
of the stream gotten by the following formula.
For the two rounds of array sequence the initial state can be set by the following way.
where,
termed as rounds and it will generate two initial values
,
and
,
respectively.
Step 3: Split the scrambled color image
into respective three channels R, G and B channels and we can get the three components,
,
and
as given below.
Here
,
and
are the
pixel values of the red, green and blue channels respectively, whereas
. Transformed the pixel values of each channel into the binary windows as given below.
Now split the window matrix into size sub-blocks, where = M and = N.
Step 4: Take the
block of
with a size
and split it into two equal columns block e.g.,
and
; termed as LCB and RCB. By using formula get the starting bit for the 1
st block-matrix and apply block bit inversion as described in
Section 2.2.
Step 5: Take the green channel
and apply the Cellular Automata as described in
Section 2.3.
Step 6: Take the blue channel
of size
divide it into the
size sub-blocks matrices as given below. While
and
, and apply DNA conversion as described in
Section 2.4.
With SM-DNA convert every binary block matrix into DNA matrix based on allocated rule of SM-DNA as follows.
Join all these DNA sub-block matrices into a single matrix as described below.
Get the universal
rule through following formula.
Convert the whole DNA sequence matrix back into binary form through this universal rule.
Step 7: Add the random matrix of the scrambling part to the pixel values of each channel as described below.
where
denotes cipher value of particular pixel,
denotes encrypted value of the pixel,
denotes the Random matrix,
, and
.
Step 8: Rejoin all the channels to get the cipher image.
5. Security Analysis and Test
5.1. Security Keyspace
The keyspace represents the entire number of likely combinations of the security key. The most common attack is the Brute-force attack in which an attacker endeavors to predict the accurate security key by overly searching the keyspace of the encryption algorithm. Thus, in order to withstand against the Brute-force attack, an adequately huge keyspace is one of the main factor that can guarantee more security [
52].
For resisting the best attack, secure hash algorithm (SHA-512) uses a keyspace of
2256. The comparison of keyspace and approach along with testing parameters of the proposed algorithm is given in
Table 6.
Moreover, the SM-DNA possible rules combination
84 can also be taken as keyspace. Except for the fact that the hash keys for generating initial configuration matrices for each channel and in their particular rule generating formulas are
222,
222,
221, and
25 respectively. So, the overall keyspace of the proposed algorithm is
which is very large as compared to
2128. To calculate the computational load, let’s the fastest computer computes
computations in
1 second and
(days)
(h)
(min)
(s) [
57]. So, to compute
computations, a total of following years required.
This huge computation load is sufficient enough to break the crypto-system. The computational load also proved that the 3C3R can effectively withstand against the brute-force attacks.
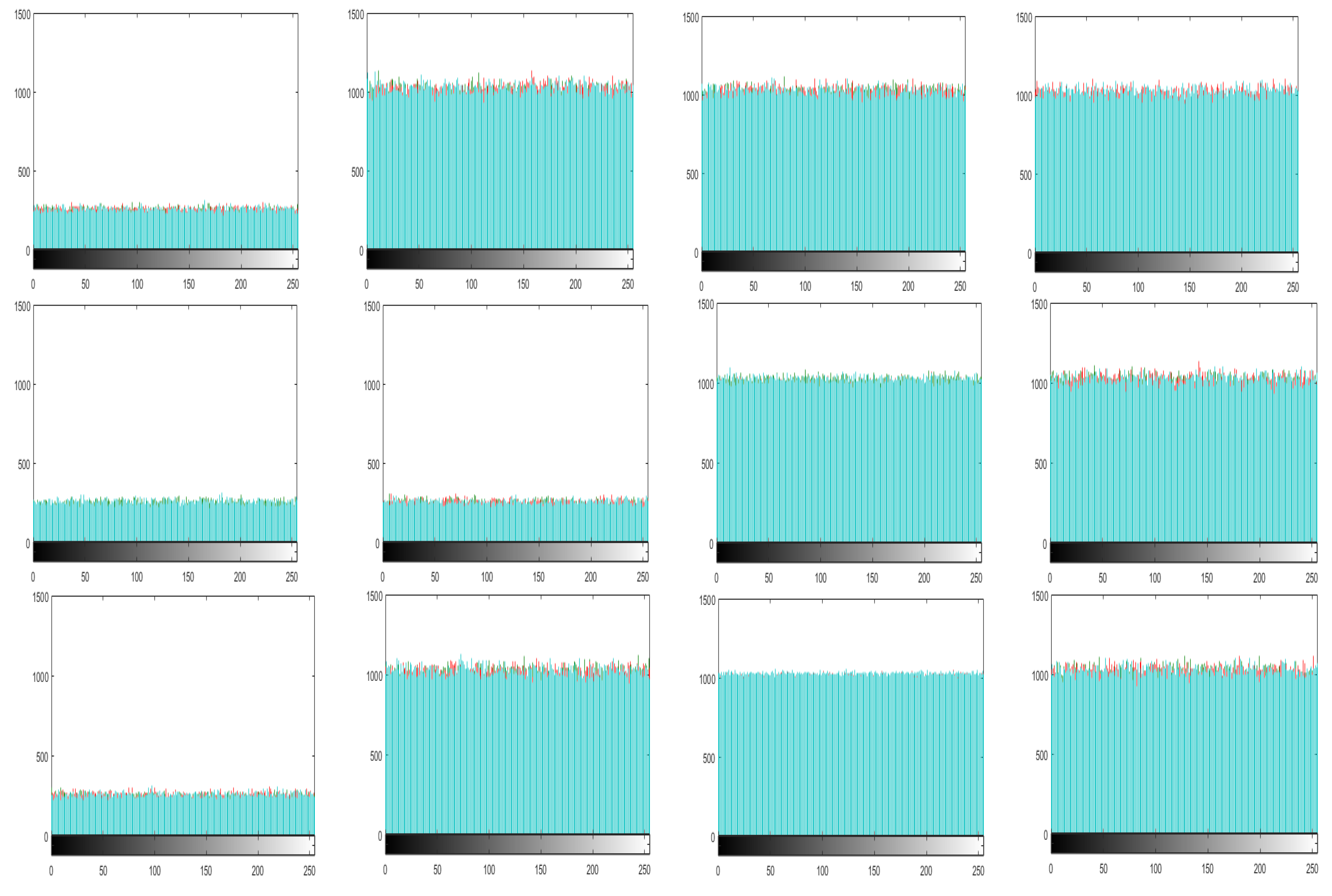
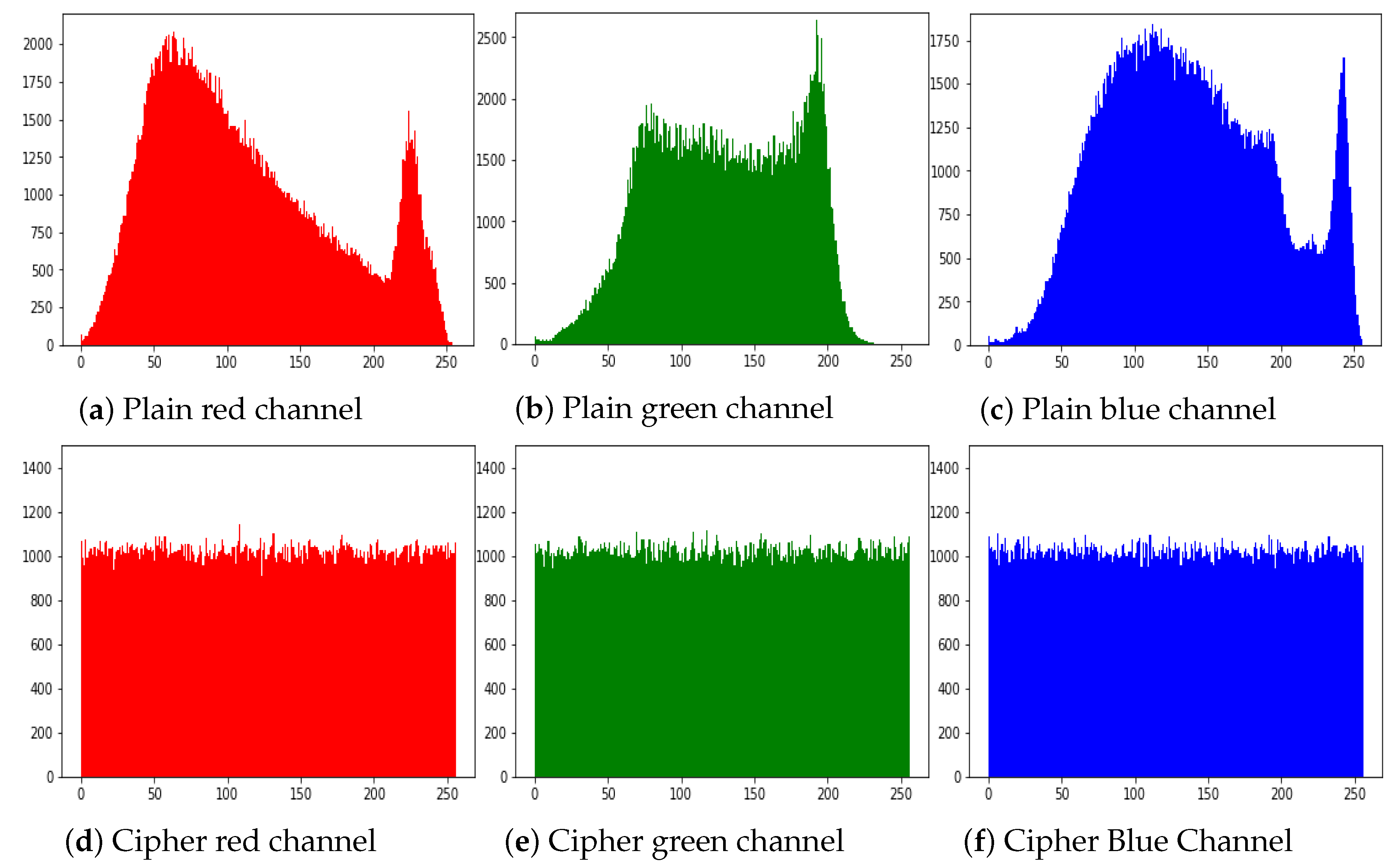
5.2. Histogram Analysis
The histogram of an image demonstrate the distribution of the pixel values. An intruders usually recover the meaningful information from the fluctuating histogram of the encrypted image. So, in order to prevent an intruder from recovering such information, it is important that the histogram of the cipher-image should have no statistical resemblance to the plain image and also should have uniform distribution. The histograms of the ciphered images of all the test images are shown in
Figure 10. While
Figure 11 shows the histogram of RGB channels of the plain image and its corresponding cipher image. The histogram of the each RGB channel of the cipher image is almost uniform. Moreover, by computing the variance of histogram, we evaluated the uniformity of our ciphered images. The lesser the variance means the higher is the uniformity of the encrypted images [
58,
59,
60,
61].
Table 7 listed the histogram variances of the plain images (R,G,B) and encrypted images along with a comparison with the other methods. From the table, we can see that in most of the test images the histogram variance of the proposed algorithm is less as than from Ref. [
62] and Ref. [
49]. This proved that the
3C3R has better security in comparison to those algorithms.
5.3. Pixel Correlation Analysis
Pixel correlation analysis is another test used to find the relationship of neighboring pixels in the plain image and the ciphered image. A good encryption algorithm aims to minimize the relationship among the neighboring pixels with regards to prevent the leakage of actual information.
The correlation coefficient
Cr(x,y) between the two neighboring pixels can be calculated by the following formulas.
In above equations (
w, z) is the gray values of neighboring pixels,
Covariance(w,z) is the covariance,
P is the total number of pixels selected from the image, while
E(w) is the mean and
D(w) is the variance.
Figure 12 displays the pixels of the plain image and ciphered image of the proposed algorithm in horizontal (H), vertical (V) and diagonal (D) distribution. In
Table 8 and
Table 9 the pixel correlation comparison was done with some previous algorithms.
Table 8 shows a comparison of
8K pairs of neighboring pixels that are randomly selected from the plain image and the ciphered image in the H, V, and D directions to perform pixel correlation analysis. Whereas,
Table 9 shows a correlation comparison of
1K random pixels of the Lena image. Whereas,
Table 10 listed the pixel correlation values of the different test images.
We casually selected the pixel pairs in the horizontal, vertical and diagonal axes, respectively. From
Table 9 it is obvious that in term of overall correlation, proposed
3C3R and Ref. [
63] are performing well, while in term of diagonal values our algorithm, Refs. [
63,
64,
65] are giving satisfactory values. While the overall and in terms of
UACI and
NPCR, the proposed
3C3R outperformed.
Similarly, for
8K random pixels the Refs. [
55,
58,
66,
68,
70] are giving good results but the proposed
3C3R is also performing well in regards to vertical and diagonal direction.
5.4. Key Sensitivity Analysis
Because of the enhanced computational power, the current era’s encryption algorithms should not have key length less than 100 bits or (
). Such key length can withstand against the exhaustive key search attack (brute force attack). The keyspace of the proposed encryption method is
, which has high ability to resist the brute-force attack. Except for the fact that the key should also be extremely sensitive to the bit change. If the secret key will not be subtle enough, then a slight change in the actual secret keys can also properly recover the original image. Also, the secret key may perverted and as a result the actual keyspace may less than the theoretical one [
60,
61,
78].
So, to check the sensitivity of the proposed algorithm towards the key, experiment has performed by changing one bit in the key with respect to the actual key as shown below.
Keyo = “40 CD 74 4F 66 82 BD 0A CF 73 57 9A 5D C3 53 DB 3A 29 5D 3A 2D 87 03 56 6C 8A CF 9B E8 AA 68 8E 87 62 1E 8F 5F 3D 07 37 63 C4 6E 93 FF 7B 1A 2B 04 76 C3 BB 84 08 F2 A2 E8 AF AB 48 08 7B B9 C4”.
Key1 = “40 CD 74 4F 66 82 BD 0A CF 73 57 9A 5D C3 53 DB 3A 29 5D 3A 2D 87 03 56 6C 8A CF 9B E8 AA 68 8E 87 62 1E 8F 5F 3D 07 37 63 C4 6E 93 FF 7B 1A 2B 04 76 C3 BB 84 08 F2 A2 E8 AF AB 48 08 7B B9 C5”.
Key2 = “50 CD 74 4F 66 82 BD 0A CF 73 57 9A 5D C3 53 DB 3A 29 5D 3A 2D 87 03 56 6C 8A CF 9B E8 AA 68 8E 87 62 1E 8F 5F 3D 07 37 63 C4 6E 93 FF 7B 1A 2B 04 76 C3 BB 84 08 F2 A2 E8 AF AB 48 08 7B B9 C4”.
Keyo is the actual key while
Key1,
Key2 are the one-bit changed keys from LSB (Right) and MSB (left) bit respectively.
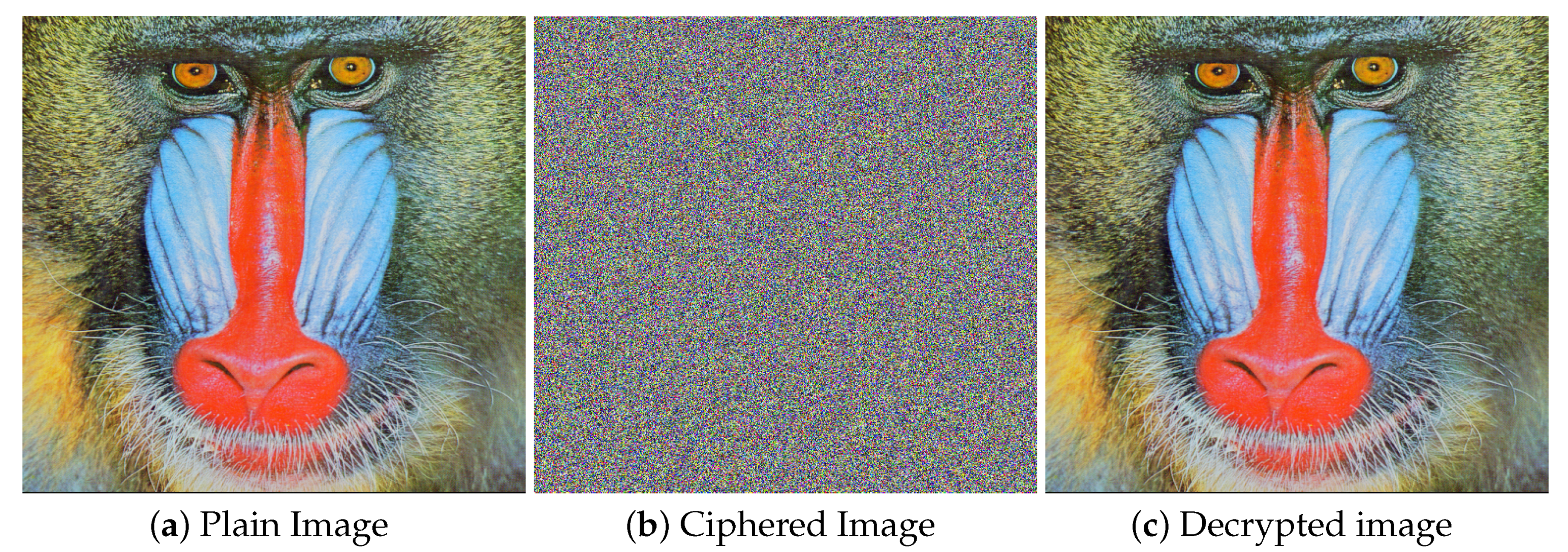
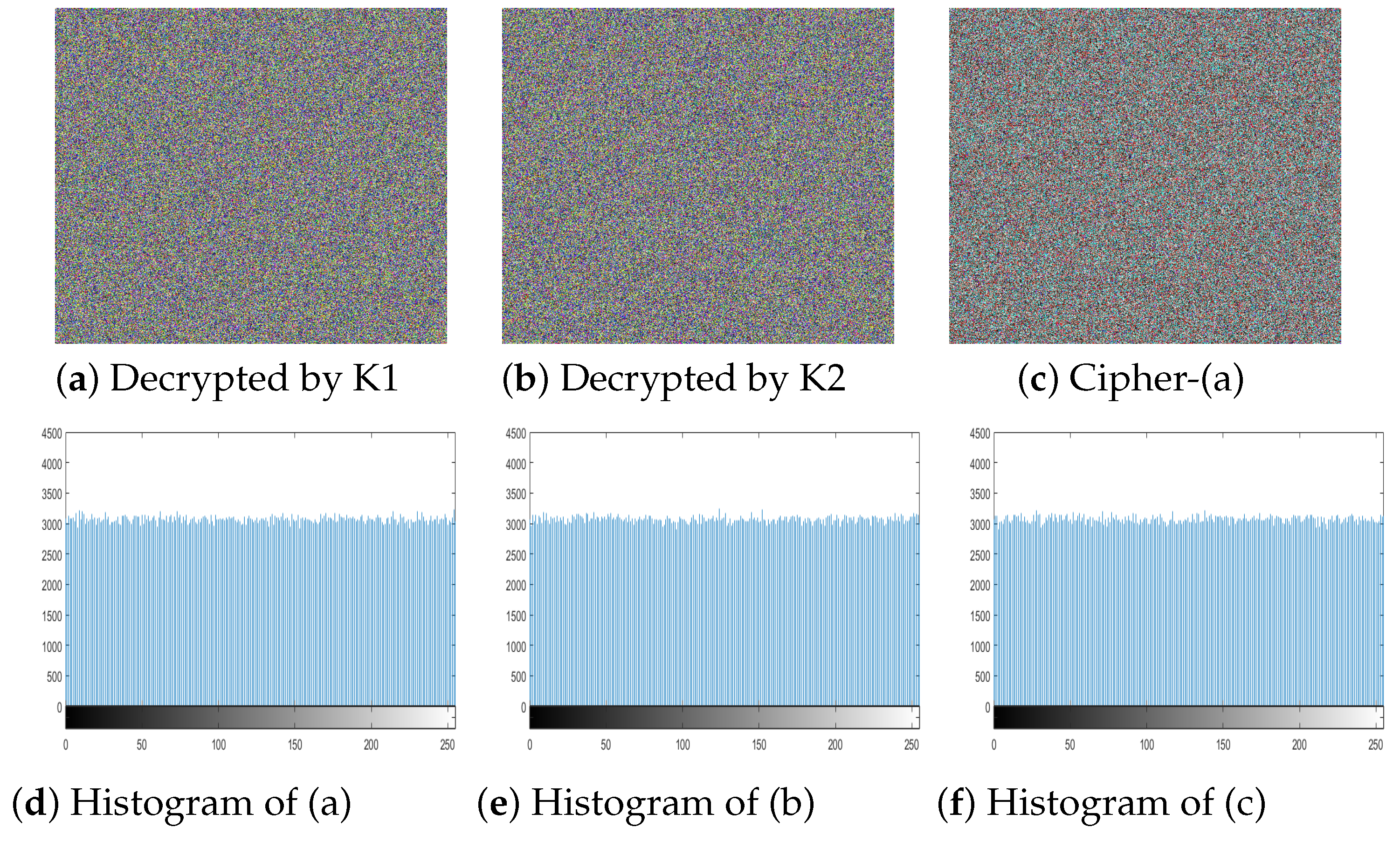
Figure 13a,b show the decrypted image by
Key1 and
Key2 respectively. Both
Key1 and
Key2 are one bit different from the actual key but the decrypted image is still like noise giving no useful information. The
Figure 13c is the subtracted image of the actual cipher and the decrypted image of
Key1. The histogram of particular three resultant images is given in
Figure 13d–f respectively. The subsequent uniform histograms proved that the proposed
3C3R is very sensitive to key change even one-bit change leads towards totally different cipher image.
5.5. Differential Attack
Normally, hackers; to extract useful information create little modification in the plain image and then by using the encryption methodology they encrypt the identical images afore and afterwards these slight changes. Through this method, they attempt to find out the association among the plain images and the cipher images. Thus, we employed the number of pixel change rate
(NPCR) and unified average changing intensity
(UACI) to measure the robustness of the proposed algorithm against such attacks. The
NPCR and
UACI can be calculated by the following way.
Here
U1,
U2 are two different ciphered images before and after one pixel of the plain image is changed, while
is the height and width of the test image. Whereas,
I(r, c) can be defined as
In the above equation, I depict the difference between U1 and U2.
Table 11 listed the NPCR and the UACI values of different test images along the comparison with some earlier algorithms. From the table values, we can see the test results of the
Lena and
pepper images of our
3C3R giving
NPCR ≥
99.97 and
UACI ≥
33.46. NPCR is high from Refs. [
28,
58,
59,
79,
80], while it is comparable to [
81]. Similarly, UACI is also comparable with the Refs. [
59,
79,
81]. Thus the proposed
3C3R has satisfactory security values.
5.6. Known and Chosen Plain Text Analysis
Most commonly, four kind of cryptanalsis attacks can be performed to crack the image encryption algorithms that are chosen-cipher-text attack, chosen-plaintext attack, cipher-text only attack, and known-plaintext attack [
82]. Some famous image encryption algorithms given in
Table 1 have already been broken with these attacks.
The cryptanalysis model, where the attackers choose plaintext to obtain the corresponding cipher-text is called chosen-plain text attack. By examining the plaintext and the corresponding cipher-text, they try to presume some hidden useful information. Finally, by using that information they try to recover the original images [
85,
86].
The chosen-plaintext attack is the most powerful, and if the encryption may resist this attack, it has adequate security level to withstand the other three attacks. The proposed algorithm 3C3R has satisfactory security level against known and chosen plaintext attacks.
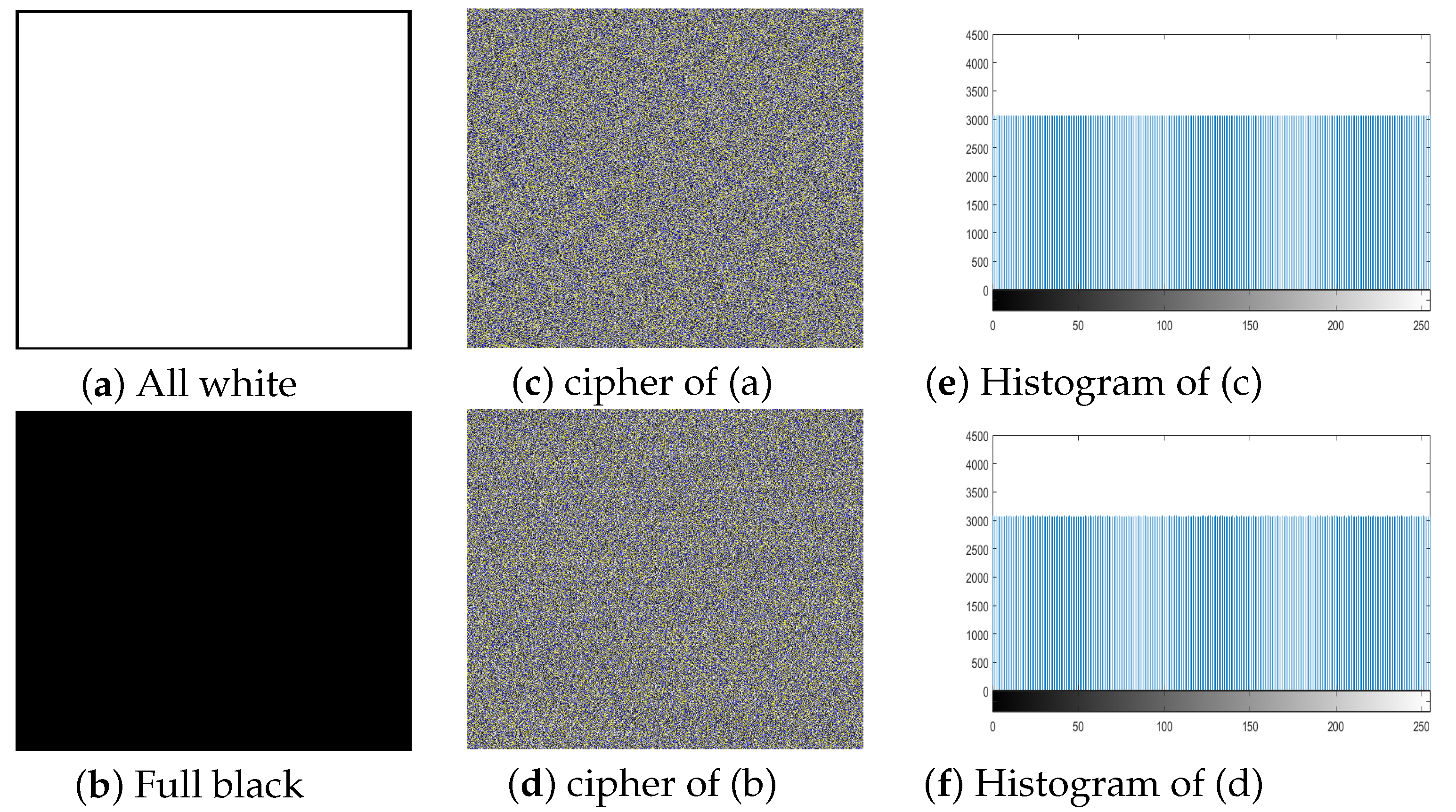
We can see the cumulative entropy
(R,G,B) value is
8.00. In Table 15 comparison of the entropy values was also given, the value is higher from Refs. [
82,
87,
88,
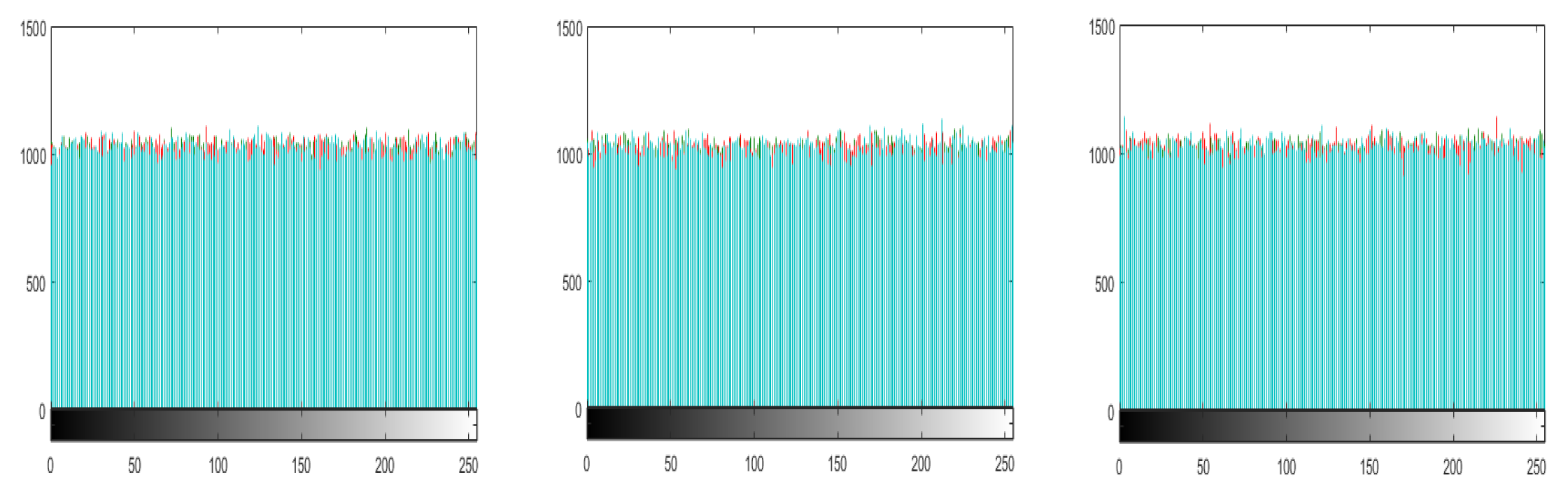
89]. The proposed algorithms give the ideal all channels entropy values for all white, full black image and is given in Table 16. The proof of ideal entropy value is visible in the histogram of the ciphered image generated by our
3C3R of all white and full black, and was given in
Figure 14. The histogram of all white, full black and Playboy image is almost entirely flat. Furthermore, we created two special color images SP
image1 and SP
image2 respectively of size
. SP
image1 is the color image with all pixels’ values
0 except one pixel located at (252, 252) in R channel is 1. Similarly SP
image2 is the color image with all pixels’ values
1 except one pixel located at (252, 252) in R channel is 0. We made plaintext sensitivity analysis and the results are given in
Table 12. The average values of NPCR and UACI are closed to the theoretical value. Thus on the bases of this test we can say that
3C3R is robust against such attacks and can keep the image more secure.
5.7. Robustness against Occlusion Attack
In image processing, PSNR and MSE are the most widely used parameters to test the encryption quality. The PSNR and MSE values can be calculated as follows.
where
is the mean square error of red, blue and green channel, between the cipher image
and original image
, while
M and
N is the height and width of the image respectively.
Another way is quality checking at the receiver side, such as after passing through a noisy medium cipher, an image may get blurred or lose some data. Therefore, a trustworthy encryption scheme should be able to recuperate the original image without losing too much substantial information.
Figure 15a–f shows the different test images with different cropped portion. While
Figure 15g–l are the retrieved images, we can see the retrieved images are easily recognizable and carry good information even after clipping 1/2. While the less clipping gave a much better result.
Table 13 listed the PSNR and MSE comparison with [
29] of test image Lena with different proportion of cropping. The values show that our algorithm performs better when increased the clipping portion while values are comparable for the less clipping.
Measuring the difference between the cipher image and original image is another way to evaluate the quality of the color images. So, for this purpose the PSNR can be viewed as a security evaluation parameter. The encryption effect is consider better if the value of PSNR is lower.
Table 14 listed the PSNR value between
and
images. The comparison was also made with some well-known algorithms and values are listed in the particular table. We can see from the table that the PSNR value for the different test images is
8.10 that is lower than Refs. [
15,
23,
46,
90,
91] except the test image baboon in which Ref. [
15] gave the lowest PSNR value between plain image and ciphered image. Thus, based on the PSNR value test, we can say that our
3C3R performs very well and can guaranty more security in comparison to other algorithms.
5.8. Local and Shannon Information Entropy
The information entropy defines the degree of disorder or chaos in an encryption system through the gray value probability. IE for the image can be defined as follow:
Let an information source be a
, then
can be computed as follows.
Here
depicts the probability of the symbol
. The ideal IE value for the image with gray intensity level of 2
8 is
8 [
93]. So, it means the closer the IE value, the more is the randomness of an image, and as a result less information will be revealed by the particular encryption scheme.
Table 15 and
Table 16 enlisted the entropy value of some famous test images and their comparison with some earlier encryption algorithms. The table values are the evidence of
IE ≥
7.996, that is close enough to the ideal value
8.0. While for Playboy, full white and Full black
3C3R achieved the ideal value
IE = 8.00. IE values of all the test images are higher than Refs. [
82,
87,
88,
89].
In [
94] a new image uncertainty test introduced by means of Shannon entropy over the native image-blocks. The
(k, TP) Shannon entropy measure concerning local image blocks can be calculated by the following method:
Step 1: Select the non-overlapping image blocks randomly i.e., with TP Pixels within the ciphered or test image I with intensity scales L.
Step 2: Compute Shannon entropy for all
by using Equation (
44).
Step 3: Calculate the Shannon entropy sample mean over these
k image blocks
by the following equation.
The local Shannon entropy value was calculated for the ciphered images. Firstly, non-overlapping image blocks with
and
TP =
1936 pixels are randomly selected from the ciphered images. As the experiential value of local Shannon entropy must fall within the confidence interval i.e.,
[7.9019, 7.9030], concerning the
-level sureness equal to the 0.05.
Table 16 listed the Shannon entropy and global entropy values and also the comparison of Shannon entropy with Ref. [
95]. The Shannon entropy value of the ciphered image of the proposed
3C3R fully falls within the desired range. Thus, based on the ideal
IE values, we can say the ciphered image generated by the proposed
3C3R carries more haphazardness and as a result, assures more security.
5.9. Gray Value Degree (GVD) Analysis
The gray difference degree or GVD is another statistical test of haphazardness that can be found by comparing the plain image and the ciphered image. The ideal value is
1, so closer the value the better is the security. GVD can be computed by the following Equation;
whereas
symbolizes the gray score at position
and
is as given below.
The average neighborhood gray difference of the whole image can be computed as follows.
In these equations,
and
, denotes the average neighborhood gray value; but the former represents after encrypting and the later represents before encryption. The final GVD value termed as gray value degree and it will be
1 if the two images are completely different or else it will be
0, if the two images are same. The GVD score of the plain and encrypted images of
USC-SIPI database are shown in
Table 17. The GVD score for most of the test images is GVD ≥
0.907 for each R, G and B channel which shows that the plain and encrypted images are entirely different. The listed results also show that
3C3R ensures more security for images as compared to Refs. [
29,
69,
97] except for the image
4.1.04 in which Ref. [
29] has the higher value as compared to
3C3R.
5.10. Performance Comparison
Performance and encryption time are an important characteristic of any image encryption algorithm. Like in the Chaos-based encryption schemes, number of permutation and diffusion rounds have a direct impact over the encryption time. Similarly for color image rule processing scheme over the RGB channels has a direct relation with the encryption time. Because of the parallel processing characteristics of cellular automata and DNA sequence the proposed
3C3R takes less encryption time as compared to chaos-based schemes.
Table 18 enlisted the time comparison of our
3C3R with the Refs. [
79,
81,
98,
99] that possess a satisfactory security level. The least encryption and decryption time was taken by the proposed
3C3R shows that our algorithm gives satisfactory results with minimum times. Except that
Table 19 listed the comparison with the recently introduced algorithms. The table values in bold fonts clearly concludes that our
3C3R overall performing much better than Refs. [
56,
62,
76,
91]. Hence, our
3C3R assures better image security.