Enhancing of Self-Referenced Continuous-Variable Quantum Key Distribution with Virtual Photon Subtraction
Abstract
1. Introduction
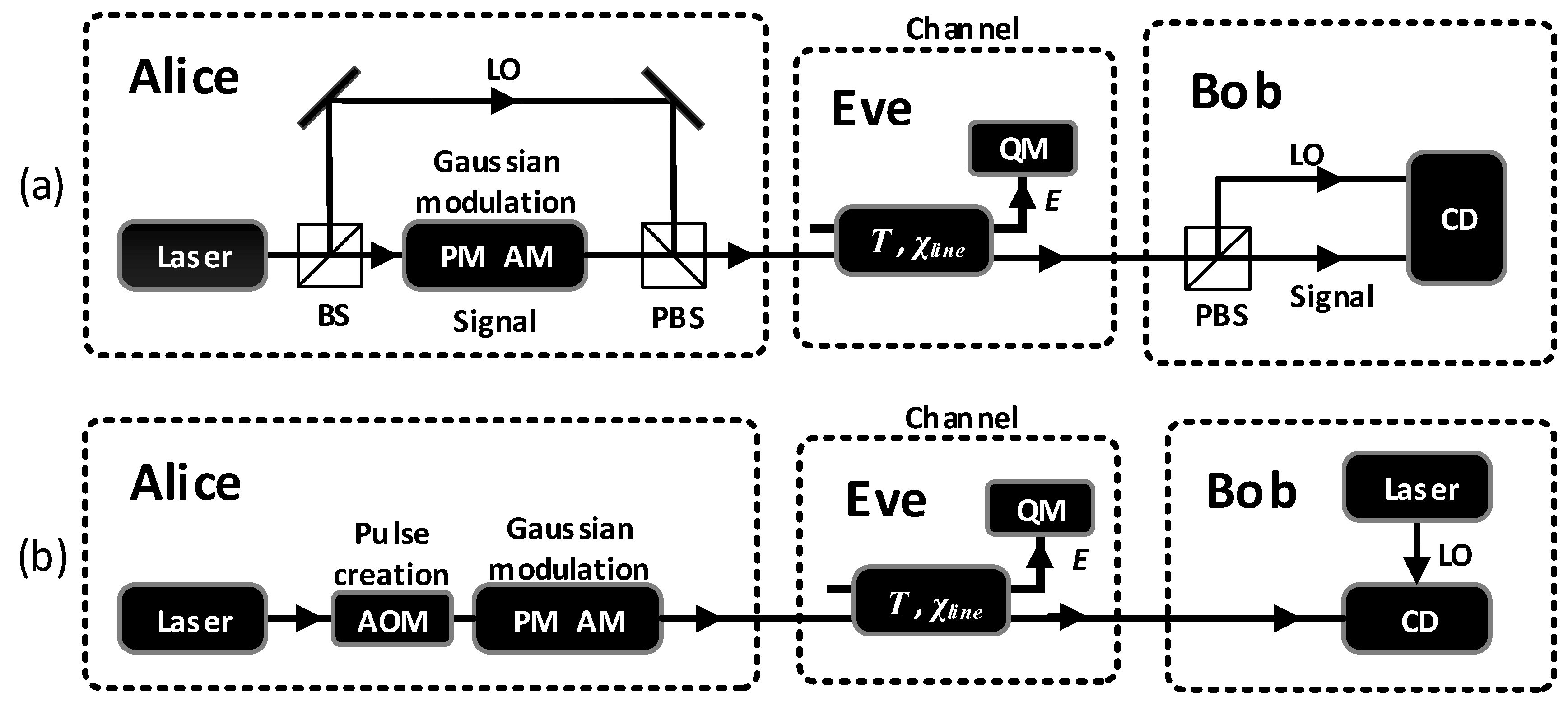
2. The Conventional Gaussian and the SR CV-QKD Scheme
- Step 1:
- Alice prepares the Gaussian modulated coherent state as the quantum signal pulse and the other coherent state as the reference pulse. Then, she sends these coherent states to Bob without sending the LO. The two independent Gaussian random variables () are both distributed as , while the mean quadrature values of the reference pulse are fixed to in Alice’s phase reference frame and are publicly known. The amplitude of the reference pulse () may be several orders of amplitude larger than and is much weaker than the amplitude of the LO.
- Step 2:
- Bob performs a homodyne detection on the received signal pulse and a heterodyne detection on the reference pulse in his own reference frame defined by the locally-generated LO. He obtains or as one of the quadratures of the signal pulse and and as both of the quadratures of the reference pulse.
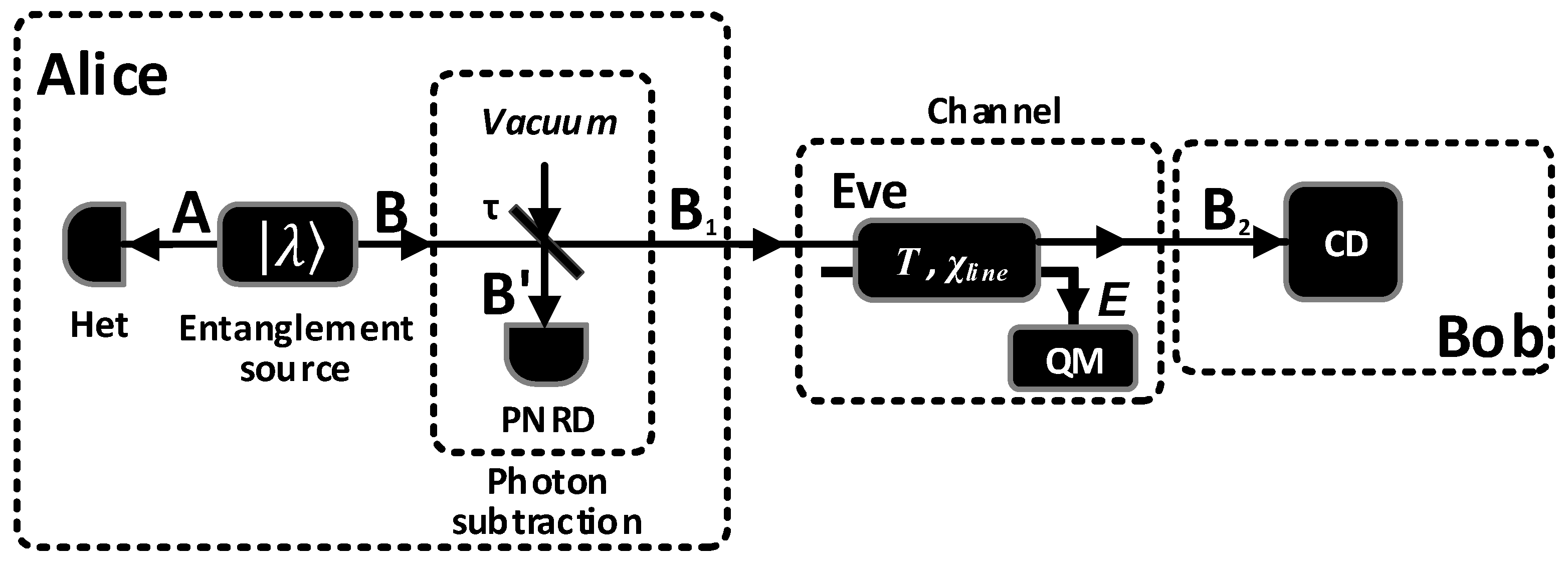
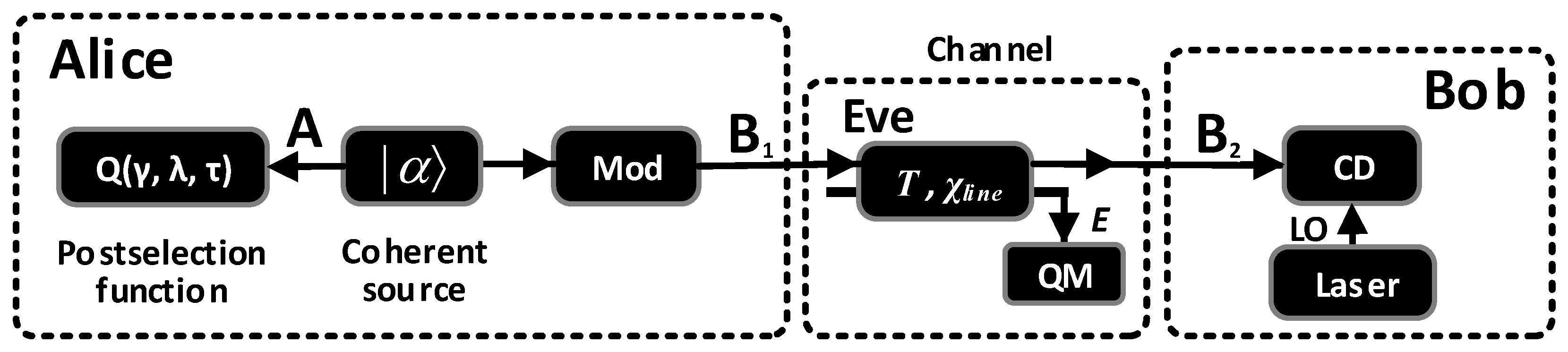
3. SR CV-QKD with Virtual Photon Subtraction
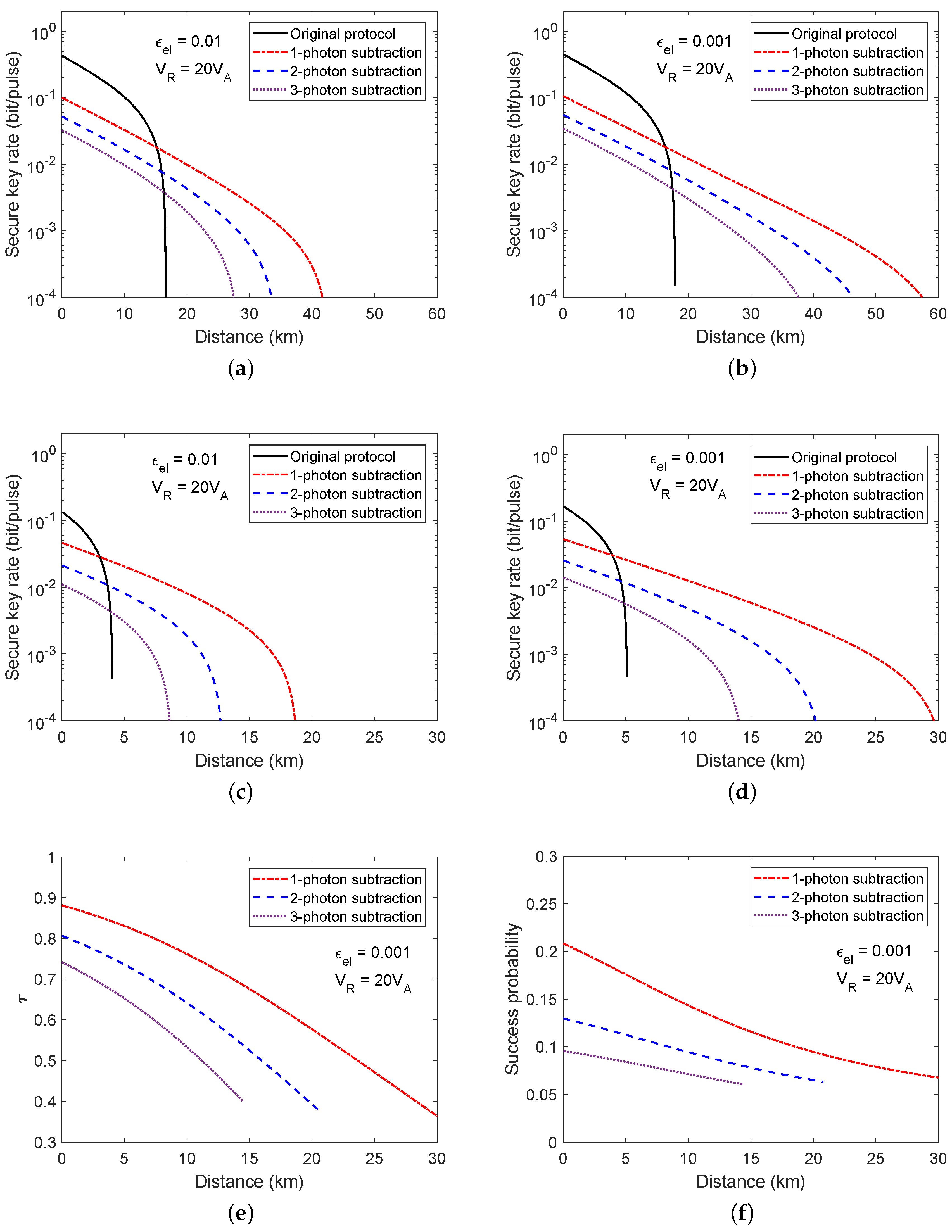
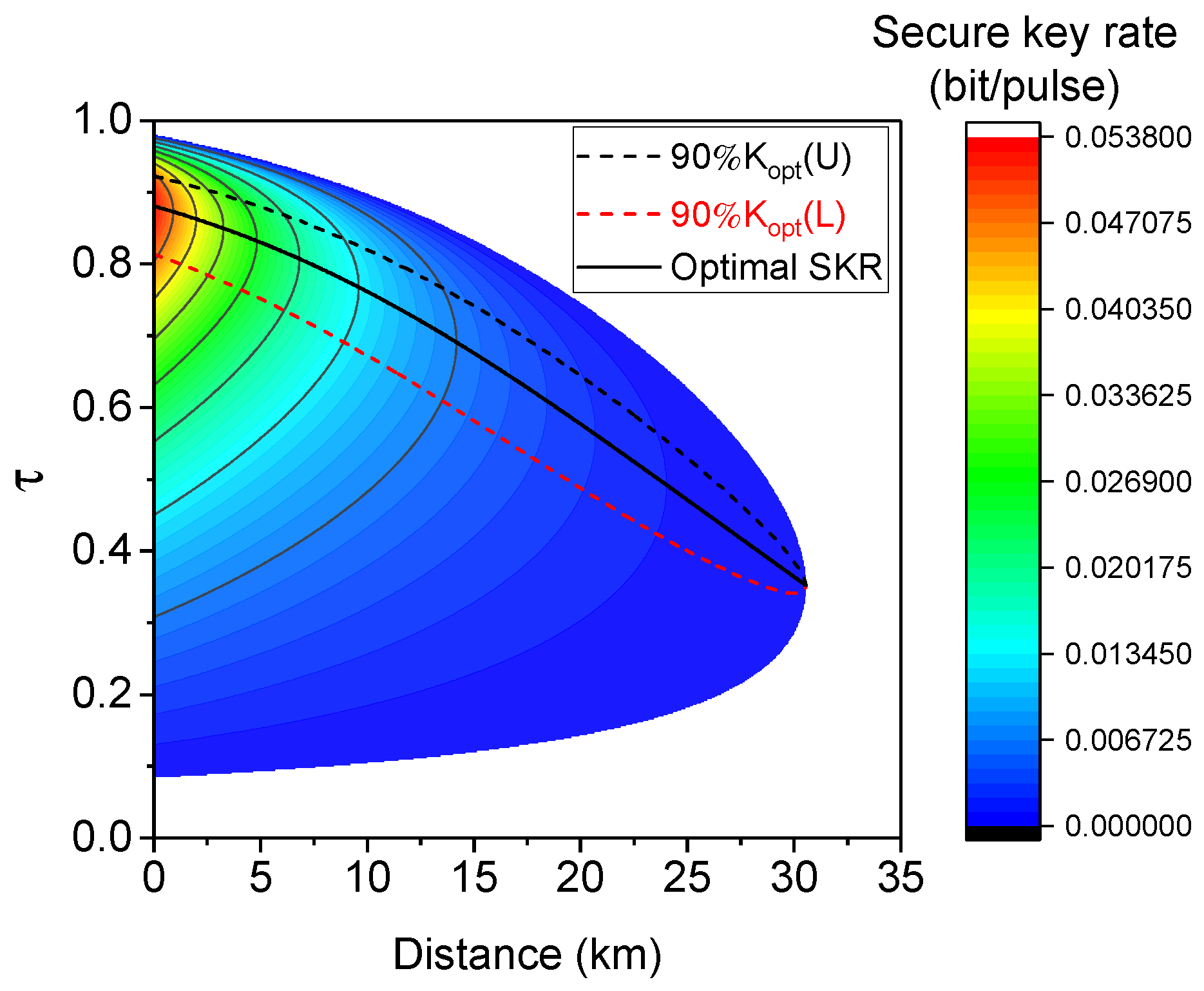
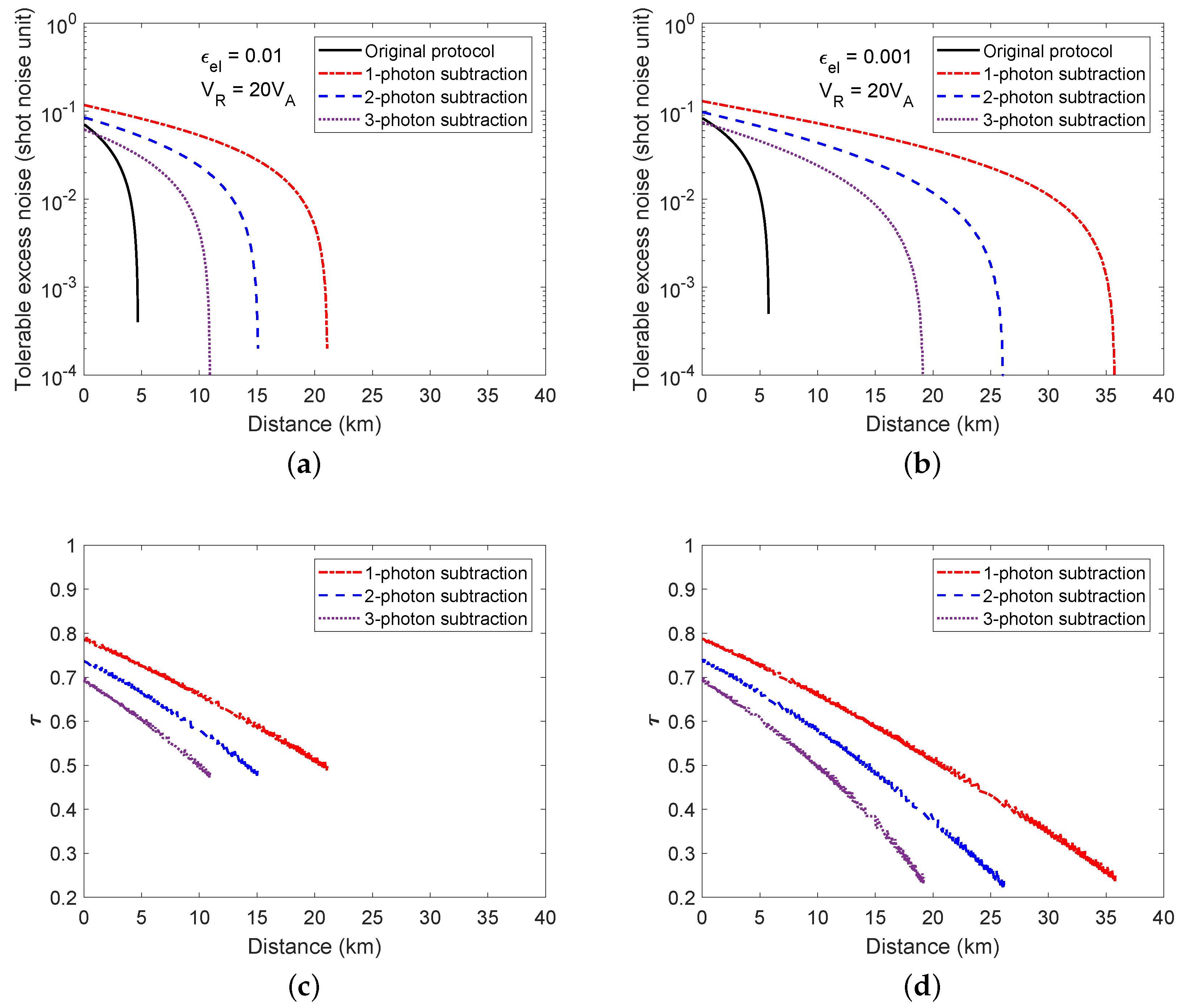
4. Performance Analysis
4.1. Individual Attacks
4.2. Collective Attacks
5. Conclusions
Author Contributions
Acknowledgments
Conflicts of Interest
References
- Bennett, C.H.; Brassard, G. Quantum cryptography: public key distribution and coin tossing. In Proceedings of IEEE International Conference on Computers, Systems and Signal Processing; IEEE Press: New York, NY, USA, 1984; pp. 175–179. [Google Scholar]
- Gisin, N.; Ribordy, G.; Tittel, W.; Zbinden, H. Quantum cryptography. Rev. Mod. Phys. 2002, 74, 145. [Google Scholar] [CrossRef]
- Scarani, V.; Bechmann-Pasquinucci, H.; Cerf, N.J.; Dušek, M.; Lütkenhaus, N.; Peev, M. The Security of Practical Quantum Key Distribution. Rev. Mod. Phys. 2009, 81, 1301. [Google Scholar] [CrossRef]
- Lo, H.-K.; Curty, M.; Tamaki, K. Secure Quantum Key Distribution. Nat. Photonics 2014, 8, 595. [Google Scholar] [CrossRef]
- Grosshans, F.; Grangier, P. Continuous Variable Quantum Cryptography Using Coherent States. Phys. Rev. Lett. 2002, 88, 057902. [Google Scholar] [CrossRef] [PubMed]
- Braunstein, S.L.; van Loock, P. Quantum information with continuous variables. Rev. Mod. Phys. 2005, 77, 513. [Google Scholar] [CrossRef]
- Wang, X.B.; Hiroshima, T.; Tomita, A.; Hayashi, M. Quantum information with gaussian states. Phys. Rep. 2007, 44, 1. [Google Scholar] [CrossRef]
- Weedbrook, C.; Pirandola, S.; García-Patrón, R.; Cerf, N.J.; Ralph, T.C.; Shapiro, J.H.; Lloyd, S. Gaussian quantum information. Rev. Mod. Phys. 2012, 84, 621. [Google Scholar] [CrossRef]
- Ma, H.-X.; Bao, W.-S.; Li, H.-W. Quantum hacking of two-way continuous-variable quantum key distribution using Trojan-horse attack. Chin. Phys. B 2016, 25, 080309. [Google Scholar] [CrossRef]
- Liu, W.-Q.; Peng, J.-Y.; Huang, P.; Huang, D.; Zeng, G.-H. Monitoring of continuous-variable quantum key distribution system in real environment. Opt. Express 2017, 25, 19429. [Google Scholar] [CrossRef] [PubMed]
- Huang, P.; Huang, J.-Z.; Wang, T.; Li, H.-S.; Huang, D.; Zeng, G.-H. Robust continuous-variable quantum key distribution against practical attacks. Phys. Rev. A 2017, 95, 052302. [Google Scholar] [CrossRef]
- Guo, Y.; Xie, C.L.; Liao, Q.; Zhao, W.; Zeng, G.H.; Huang, D. Entanglement-distillation attack on continuous-variable quantum key distribution in a turbulent atmospheric channel. Phys. Rev. A 2017, 96, 022320. [Google Scholar] [CrossRef]
- Guo, Y.; Xie, C.L.; Huang, P.; Zhang, L.; Huang, D.; Zeng, G.H. Channel-parameter estimation for satellite-to-submarine continuous-variable quantum key distribution. Phys. Rev. A 2018, 97, 052326. [Google Scholar] [CrossRef]
- Guo, Y.; Li, R.J.; Liao, Q.; Zhou, J.; Huang, D. Performance improvement of eight-state continuous-variable quantum key distribution with an optical amplifier. Phys. Lett. A 2018, 382, 372–381. [Google Scholar] [CrossRef]
- Grosshans, F. Collective attacks and unconditional security in continuous variable quantum key distribution. Phys. Rev. Lett. 2005, 94, 020504. [Google Scholar] [CrossRef] [PubMed]
- Navascues, M.; Acín, A. Security bounds for continuous variables quantum key distribution. Phys. Rev. Lett. 2005, 94, 020505. [Google Scholar] [CrossRef] [PubMed]
- Leverrier, A. Composable Security Proof for Continuous-Variable Quantum Key Distribution with Coherent States. Phys. Rev. Lett. 2015, 114, 070501. [Google Scholar] [CrossRef] [PubMed]
- Huang, J.-Z.; Weedbrook, C.; Yin, Z.-Q.; Wang, S.; Li, H.-W.; Chen, W.; Guo, G.-C.; Han, Z.-F. Quantum hacking of a continuous-variable quantum-key-distribution system using a wavelength attack. Phys. Rev. A 2013, 87, 062329. [Google Scholar] [CrossRef]
- Ma, X.-C.; Sun, S.-H.; Jiang, M.-S.; Liang, L.-M. Wavelength attack on practical continuous-variable quantum-key-distribution system with a heterodyne protocol. Phys. Rev. A 2013, 87, 052309. [Google Scholar] [CrossRef]
- Qin, H.; Kumar, R.; Alléaume, R. Saturation attack on continuous-variable quantum key distribution system. Proc. SPIE 2013, 8899, 88990N. [Google Scholar]
- Jouguet, P.; Kunz-Jacques, S.; Diamanti, E. Preventing Calibration Attacks on the Local Oscillator in Continuous-Variable Quantum Key Distribution. Phys. Rev. A 2013, 87, 062313. [Google Scholar] [CrossRef]
- Ma, X.-C.; Sun, S.-H.; Jiang, M.-S.; Liang, L.-M. Local oscillator fluctuation opens a loophole for Eve in practical continuous-variable quantum-key-distribution systems. Phys. Rev. A 2013, 88, 022339. [Google Scholar] [CrossRef]
- Soh, D.B.S.; Brif, C.; Coles, P.J.; Lütkenhaus, N.; Camacho, R.M.; Urayama, J.; Sarovar, M. Self-Referenced Continuous-Variable Quantum Key Distribution Protocol. Phys. Rev. X 2015, 5, 041010. [Google Scholar] [CrossRef]
- Qi, B.; Lougovski, P.; Pooser, R.; Grice, W.; Bobrek, M. Generating the Local Oscillator Locally in Continuous-Variable Quantum Key Distribution Based on Coherent Detection. Phys. Rev. X 2015, 5, 041009. [Google Scholar] [CrossRef]
- Huang, D.; Huang, P.; Lin, D.-K.; Wang, C.; Zeng, G.-H. High-speed continuous-variable quantum key distribution without sending a local oscillator. Opt. Lett. 2015, 40, 3695. [Google Scholar] [CrossRef] [PubMed]
- Marie, A.; Alléaume, R. Self-coherent phase reference sharing for continuous-variable quantum key distribution. Phys. Rev. A 2017, 95, 012316. [Google Scholar] [CrossRef]
- Opatrný, T.; Kurizki, G.; Welsch, D.-G. Improvement on teleportation of continuous variables by photon subtraction via conditional measurement. Phys. Rev. A 2000, 61, 032302. [Google Scholar] [CrossRef]
- Kim, M.S.; Park, E.; Knight, P.L.; Jeong, H. Nonclassicality of a photon-subtracted Gaussian field. Phys. Rev. A 2005, 71, 043805. [Google Scholar] [CrossRef]
- Kitagawa, A.; Takeoka, M.; Sasaki, M.; Chefles, A. Entanglement evaluation of non-Gaussian states generated by photon subtraction from squeezed states. Phys.Rev. A 2006, 73, 042310. [Google Scholar] [CrossRef]
- Navarrete-Benlloch, C.; García-Patrón, R.; Shapiro, J.H.; Cerf, N.J. Enhancing quantum entanglement by photon addition and subtraction. Phys. Rev. A 2012, 86, 012328. [Google Scholar] [CrossRef]
- Huang, P.; He, G.-Q.; Fang, J.; Zeng, G.H. Performance improvement of continuous-variable quantum key distribution via photon subtraction. Phys. Rev. A 2013, 87, 012317. [Google Scholar] [CrossRef]
- Guo, Y.; Liao, Q.; Wang, Y.-J.; Huang, D.; Huang, P.; Zeng, G.-H. Performance improvement of continuous-variable quantum key distribution with an entangled source in the middle via photon subtraction. Phys. Rev. A 2017, 95, 032304. [Google Scholar] [CrossRef]
- Li, Z.-Y.; Zhang, Y.-C.; Wang, X.-Y.; Xu, B.-J.; Peng, X.; Guo, H. Non-Gaussian postselection and virtual photon subtraction in continuous-variable quantum key distribution. Phys. Rev. A 2016, 93, 012310. [Google Scholar] [CrossRef]
- Liao, Q.; Guo, Y.; Huang, D.; Huang, P.; Zeng, G.-H. Long-distance continuous-variable quantum key distribution using non-Gaussian state-discrimination detection. New J. Phys. 2018, 20, 023015. [Google Scholar] [CrossRef]
- Zhao, Y.-J.; Zhang, Y.-C.; Li, Z.-Y.; Yu, S.; Guo, H. Improvement of two-way continuous-variable quantum key distribution with virtual photon subtraction. Quantum Inf. Process. 2017, 16, 184. [Google Scholar] [CrossRef]
- Zhao, Y.-J.; Zhang, Y.-C.; Xu, B.-J.; Yu, S.; Guo, H. Continuous-variable measurement-device-independent quantum key distribution with virtual photon subtraction. Phys. Rev. A 2018, 97, 042328. [Google Scholar] [CrossRef]
- Eisaman, M.D.; Fan, J.; Migdall, A.; Polyakov, S.V. Invited Review Article: Single-photon sources and detectors. Rev. Sci. Instrum. 2011, 82, 071101. [Google Scholar] [CrossRef] [PubMed]
- Navascués, M.; Grosshans, F.; Acín, A. Optimality of Gaussian Attacks in Continuous-Variable Quantum Cryptography. Phys. Rev. Lett. 2006, 97, 190502. [Google Scholar] [CrossRef] [PubMed]
- García-Patrón, R.; Cerf, N.J. Unconditional Optimality of Gaussian Attacks against Continuous-Variable Quantum Key Distribution. Phys. Rev. Lett. 2006, 97, 190503. [Google Scholar]
- Wolf, M.M.; Giedke, G.; Cirac, J.I. Extremality of Gaussian Quantum States. Phys. Rev. Lett. 2006, 96, 080502. [Google Scholar] [CrossRef] [PubMed]
- Huang, D.; Huang, P.; Lin, D.-K.; Zeng, G.-H. Long-distance continuous-variable quantum key distribution by controlling excess noise. Sci. Rep. 2016, 6, 19201. [Google Scholar] [CrossRef] [PubMed]
© 2018 by the authors. Licensee MDPI, Basel, Switzerland. This article is an open access article distributed under the terms and conditions of the Creative Commons Attribution (CC BY) license (http://creativecommons.org/licenses/by/4.0/).
Share and Cite
Zhong, H.; Wang, Y.; Wang, X.; Liao, Q.; Wu, X.; Guo, Y. Enhancing of Self-Referenced Continuous-Variable Quantum Key Distribution with Virtual Photon Subtraction. Entropy 2018, 20, 578. https://doi.org/10.3390/e20080578
Zhong H, Wang Y, Wang X, Liao Q, Wu X, Guo Y. Enhancing of Self-Referenced Continuous-Variable Quantum Key Distribution with Virtual Photon Subtraction. Entropy. 2018; 20(8):578. https://doi.org/10.3390/e20080578
Chicago/Turabian StyleZhong, Hai, Yijun Wang, Xudong Wang, Qin Liao, Xiaodong Wu, and Ying Guo. 2018. "Enhancing of Self-Referenced Continuous-Variable Quantum Key Distribution with Virtual Photon Subtraction" Entropy 20, no. 8: 578. https://doi.org/10.3390/e20080578
APA StyleZhong, H., Wang, Y., Wang, X., Liao, Q., Wu, X., & Guo, Y. (2018). Enhancing of Self-Referenced Continuous-Variable Quantum Key Distribution with Virtual Photon Subtraction. Entropy, 20(8), 578. https://doi.org/10.3390/e20080578




